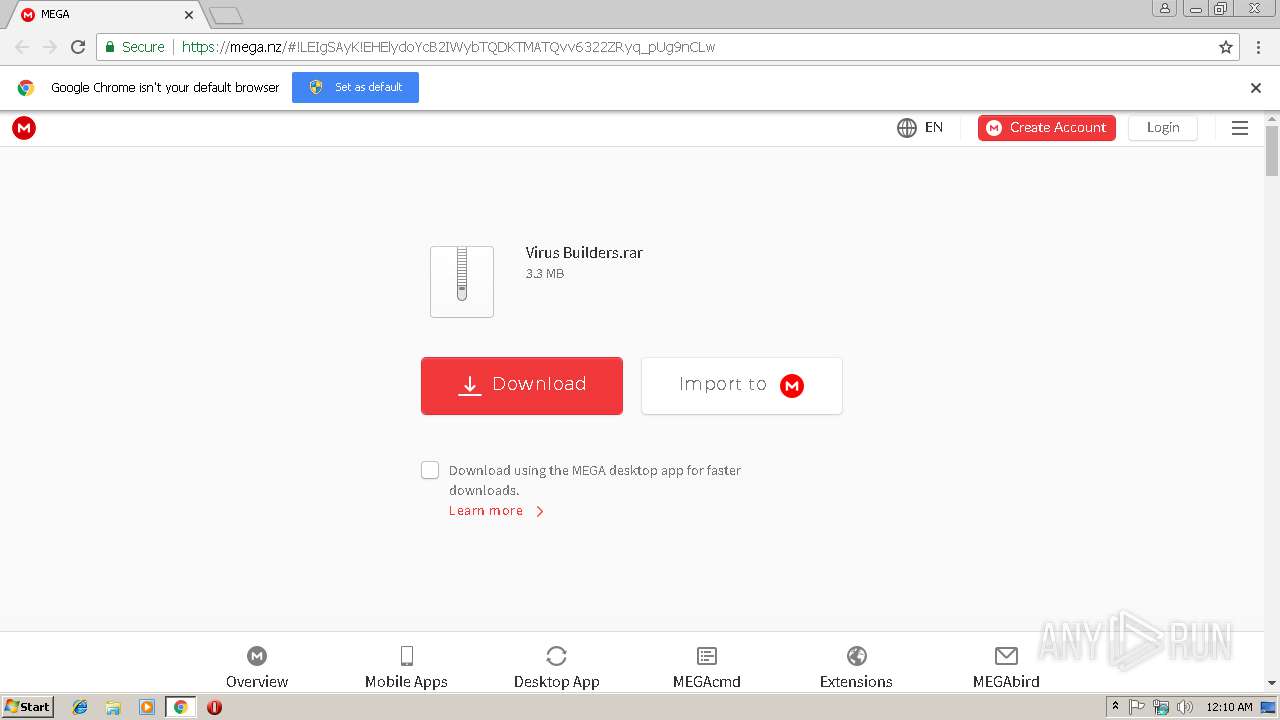
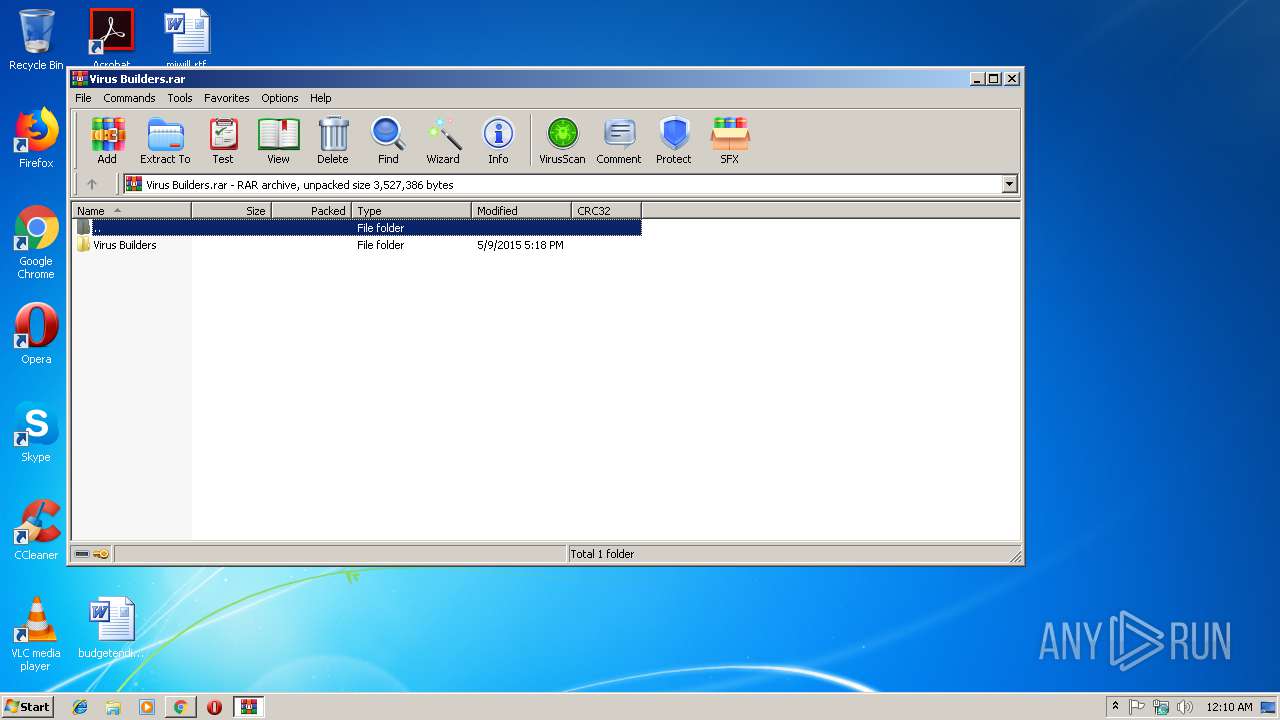
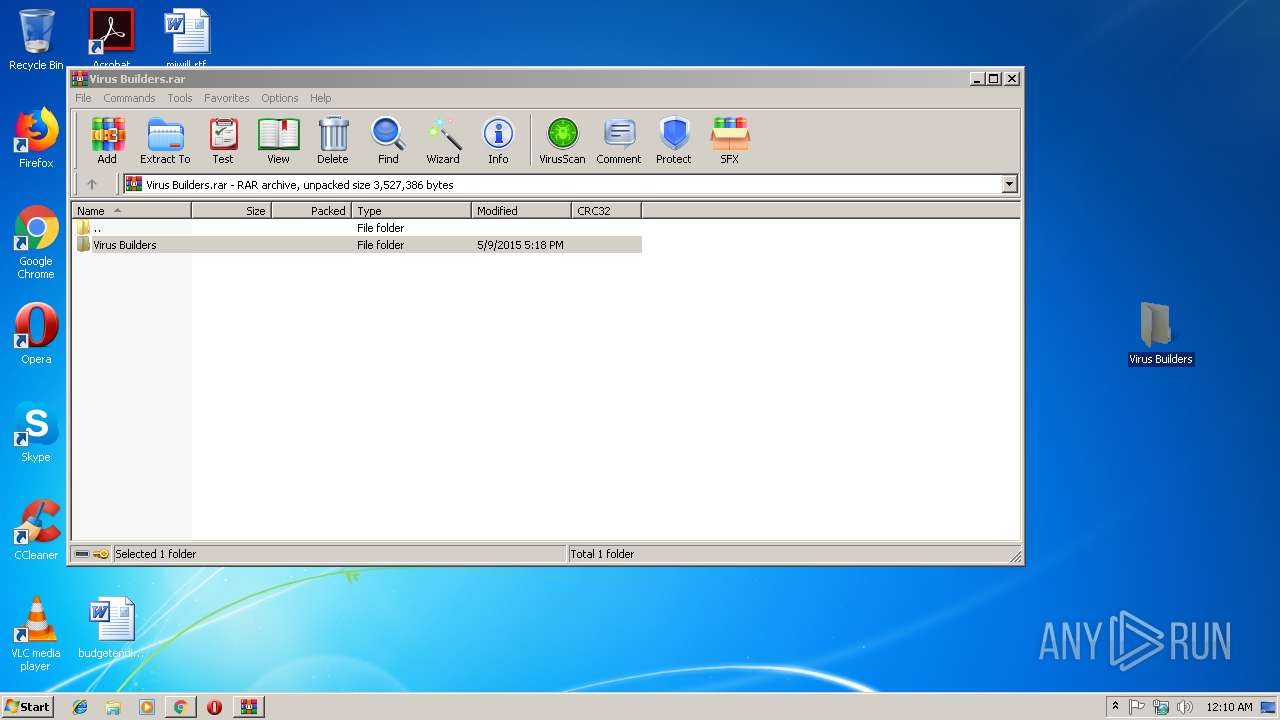
| URL: | https://mega.nz/#!LEIgSAyK!EHElydoYcB2IWybTQDKTMATQvv6322ZRyq_pUg9nCLw |
| Full analysis: | https://app.any.run/tasks/ffc79d33-c048-44cc-afb5-b742e1759bd2 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2019, 00:09:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E97FFC9DE818F8261ED40FF2973F22D4 |
| SHA1: | 70B42BB73EC947E62C884B94A07EF025B331BF2F |
| SHA256: | 38CFDA27D284F80AEF6F4A495573EA43C5C1F0C0CBF7685786D50400DABF5F3B |
| SSDEEP: | 3:N8X/iGEewIBwXTcHy60CUU6afS8:29FjwXTcSuZ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1828)
Application was dropped or rewritten from another process
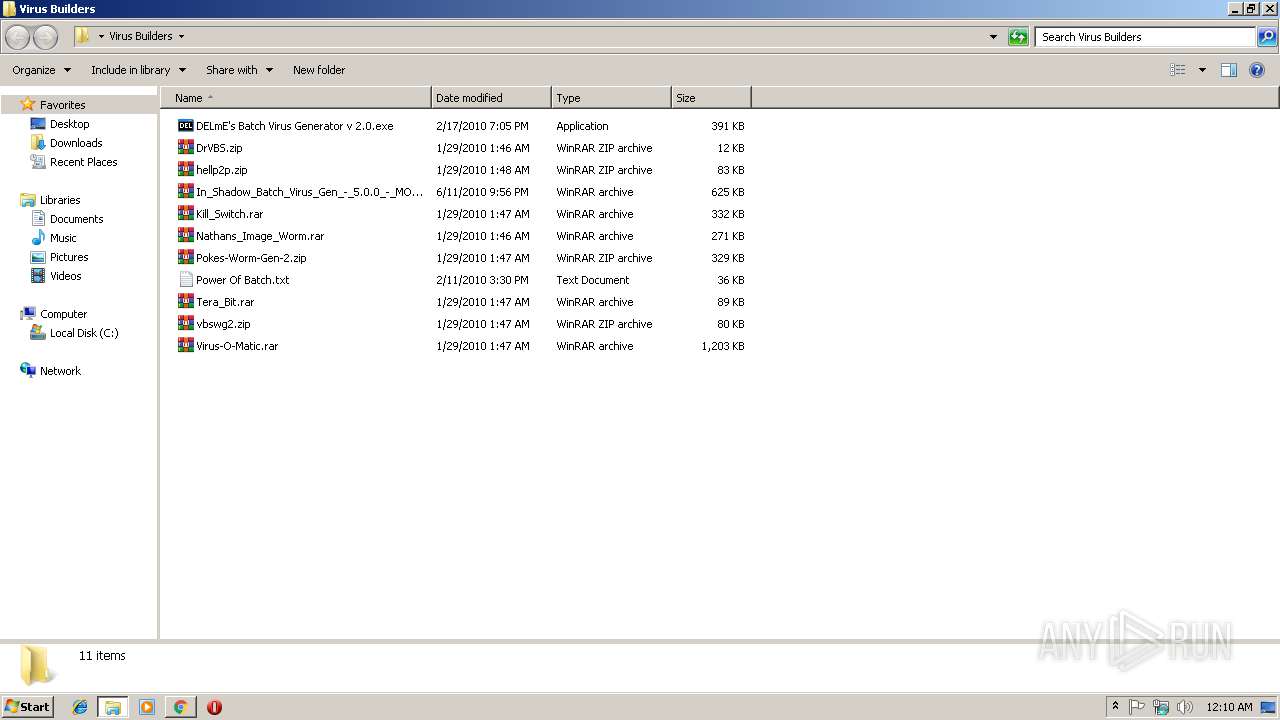
- In Shadow Batch Virus Gen - 5.0.0 - MOD.exe (PID: 3020)
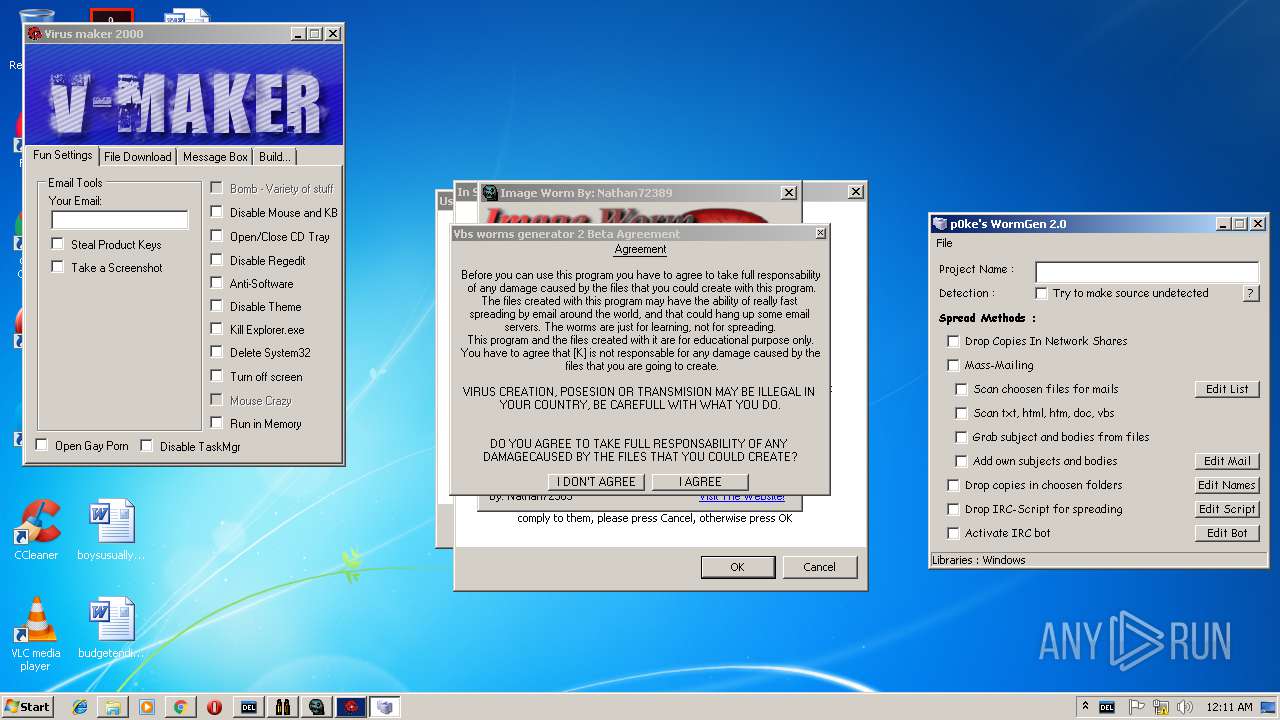
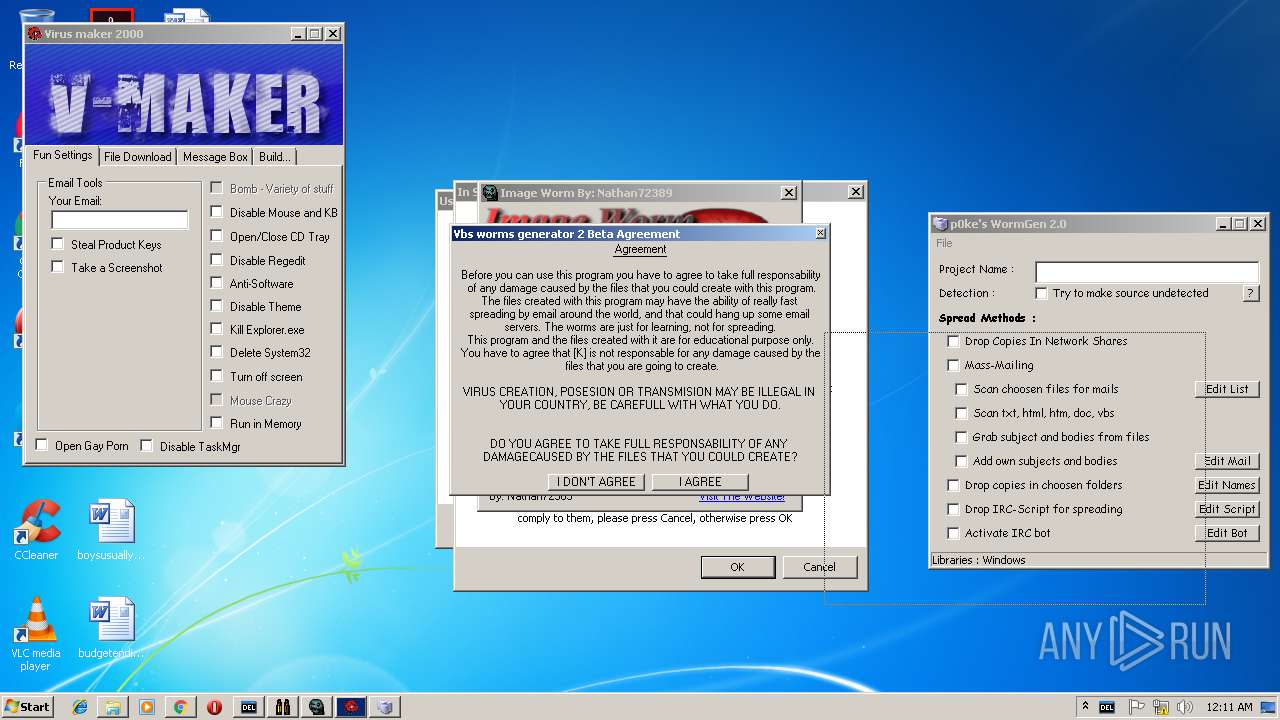
- Image Worm.exe (PID: 3144)
- Virus-O-Matic.exe (PID: 3992)
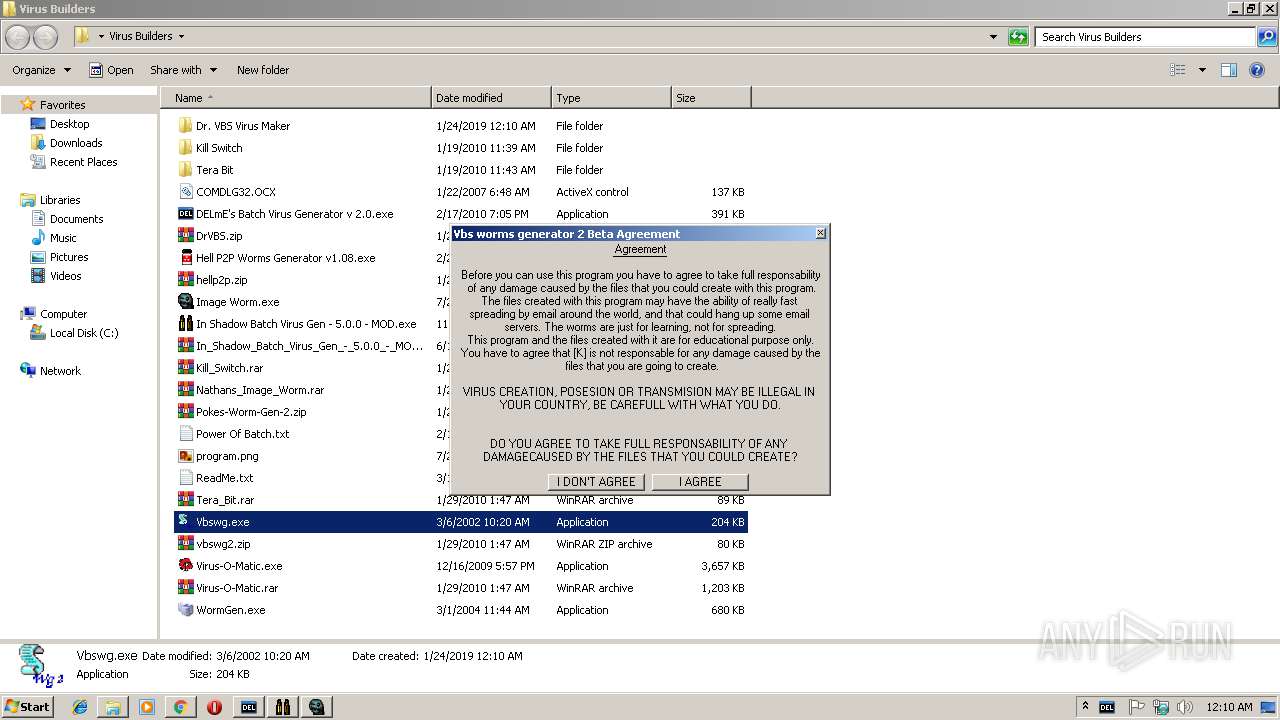
- Vbswg.exe (PID: 2304)
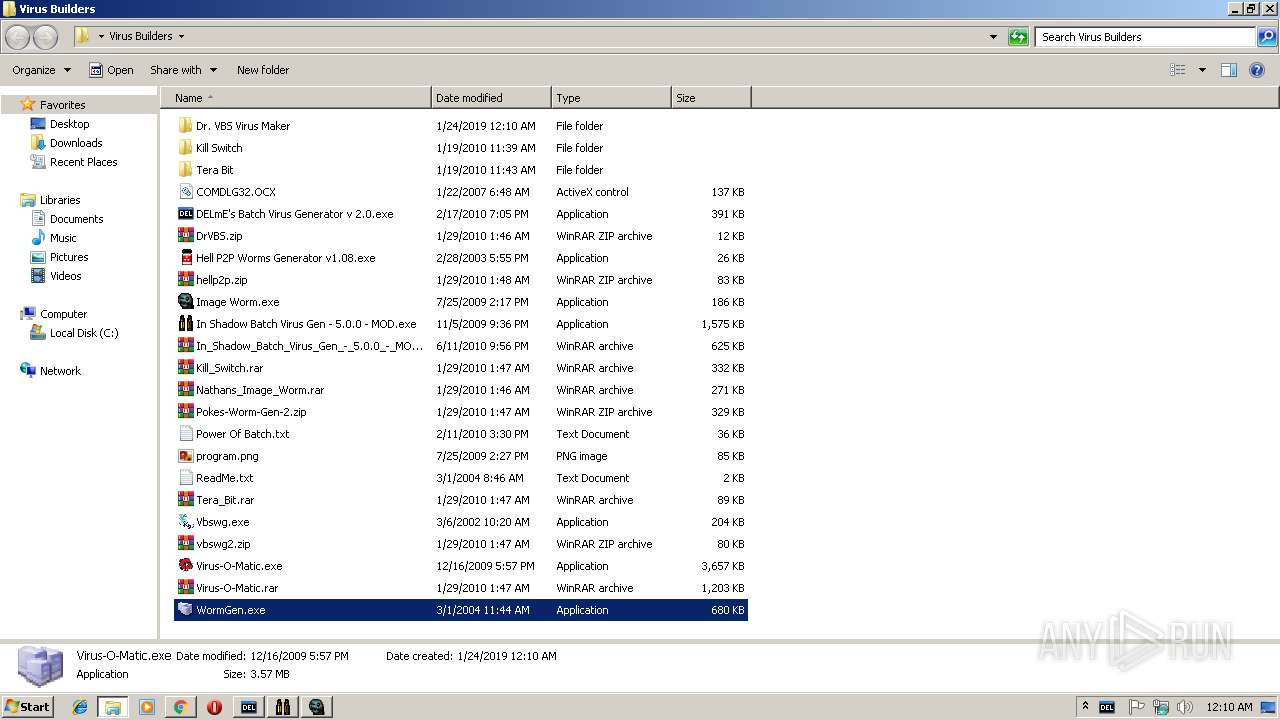
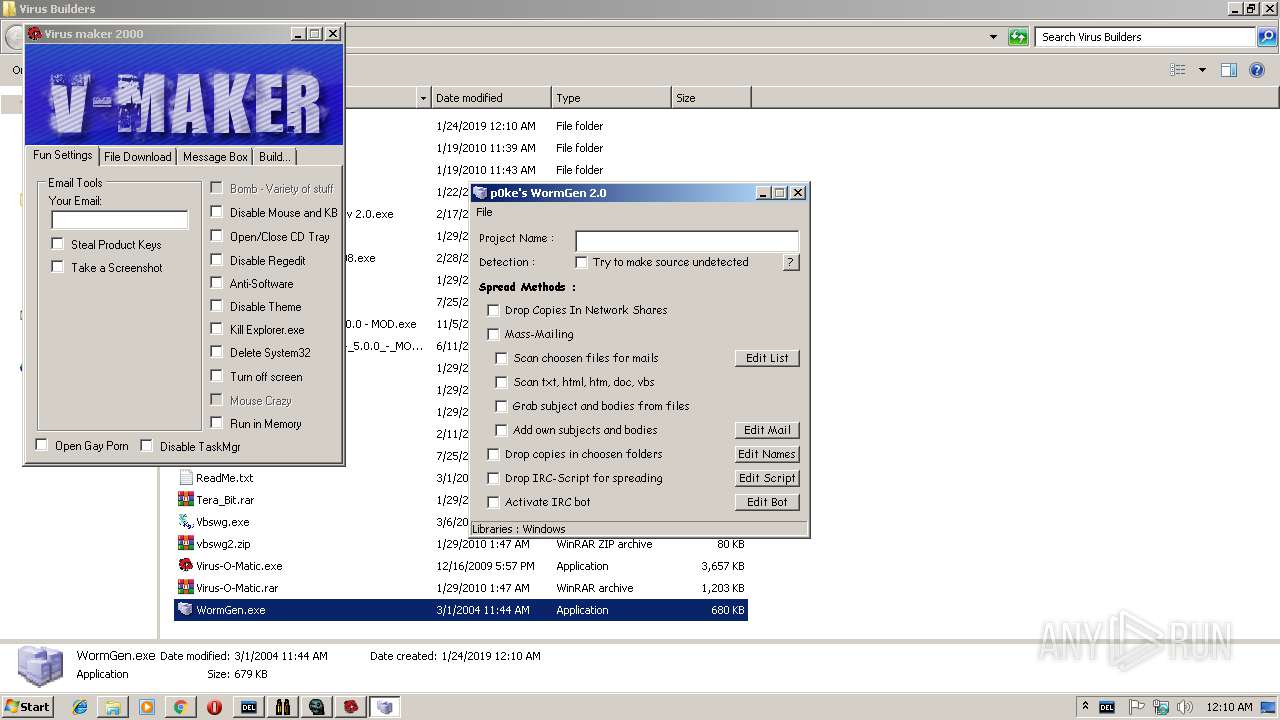
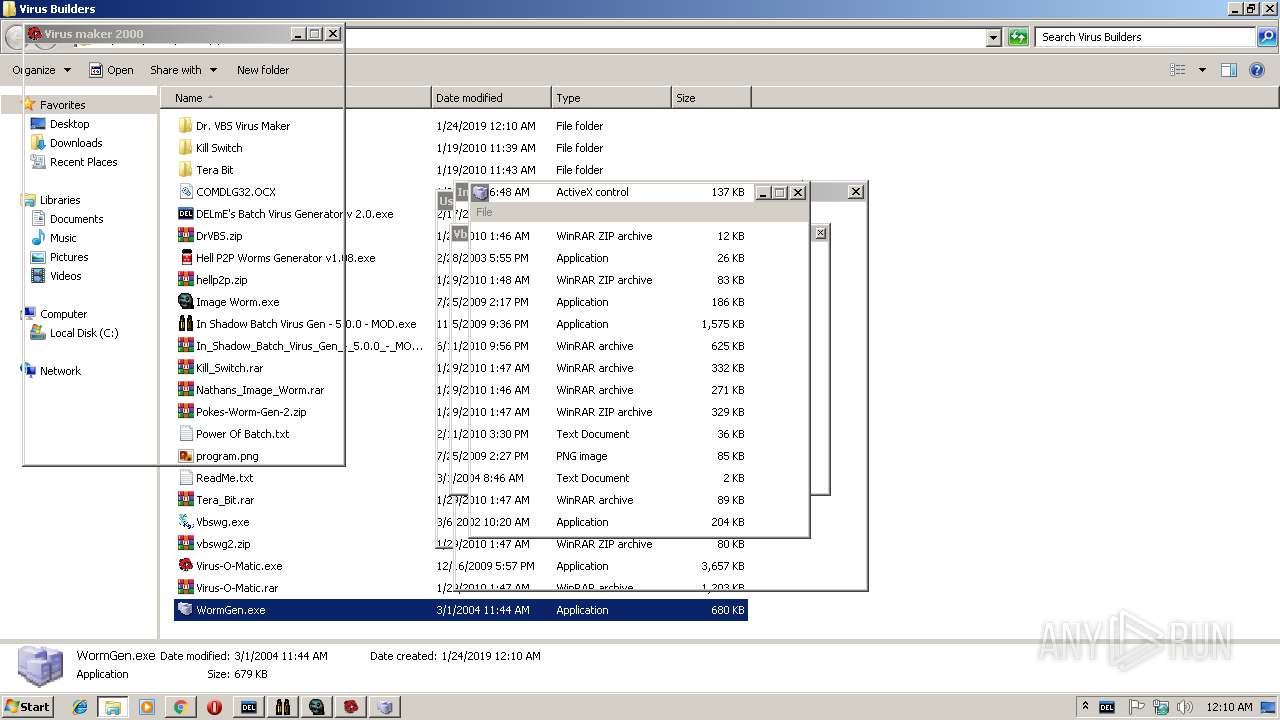
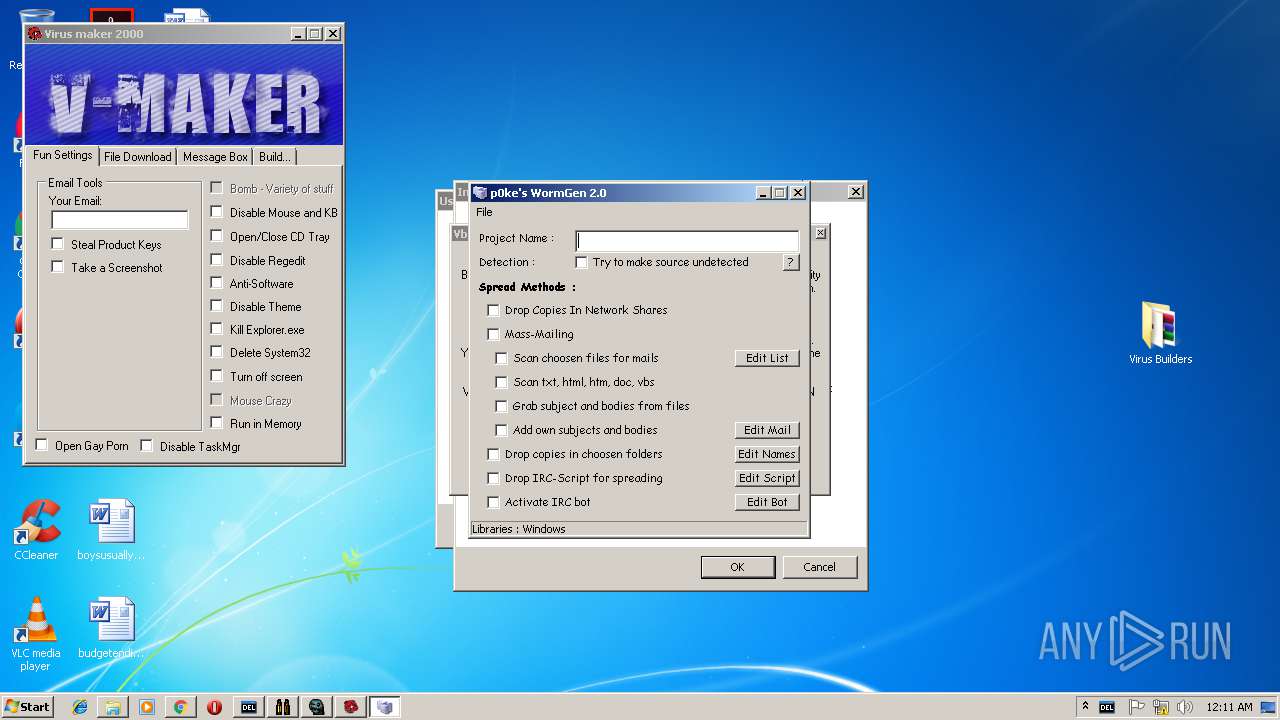
- WormGen.exe (PID: 2684)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2512)
INFO
Application launched itself
- chrome.exe (PID: 2844)
Reads settings of System Certificates
- chrome.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
17
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1828 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | "C:\Users\admin\Desktop\Virus Builders\Vbswg.exe" | C:\Users\admin\Desktop\Virus Builders\Vbswg.exe | — | explorer.exe | |||||||||||
User: admin Company: VIRII ARGENTINA Integrity Level: MEDIUM Exit code: 0 Version: 2.00 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=932,6446415706175171745,7615301987602728214,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=51410015BF360A8BEB97A8B904672170 --mojo-platform-channel-handle=4060 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=932,6446415706175171745,7615301987602728214,131072 --enable-features=PasswordImport --service-pipe-token=51ED6FA61BDC52E740339FBF3FD5FF58 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=51ED6FA61BDC52E740339FBF3FD5FF58 --renderer-client-id=4 --mojo-platform-channel-handle=1888 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
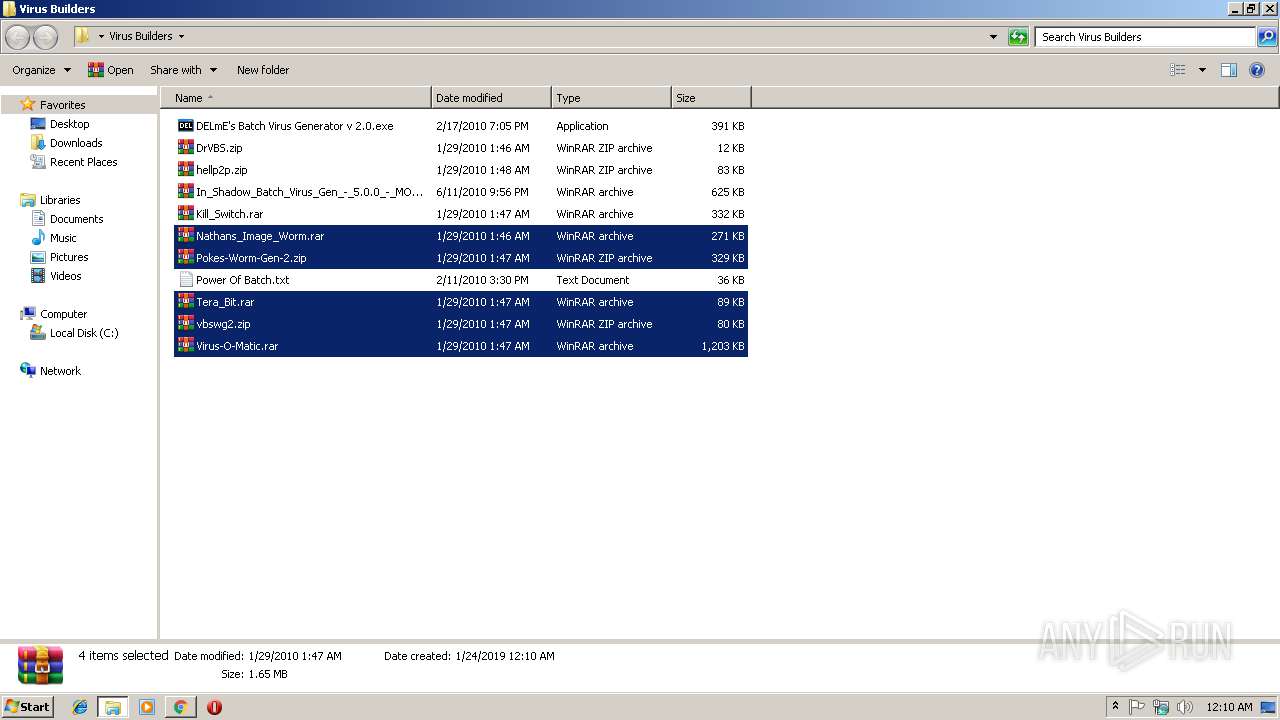
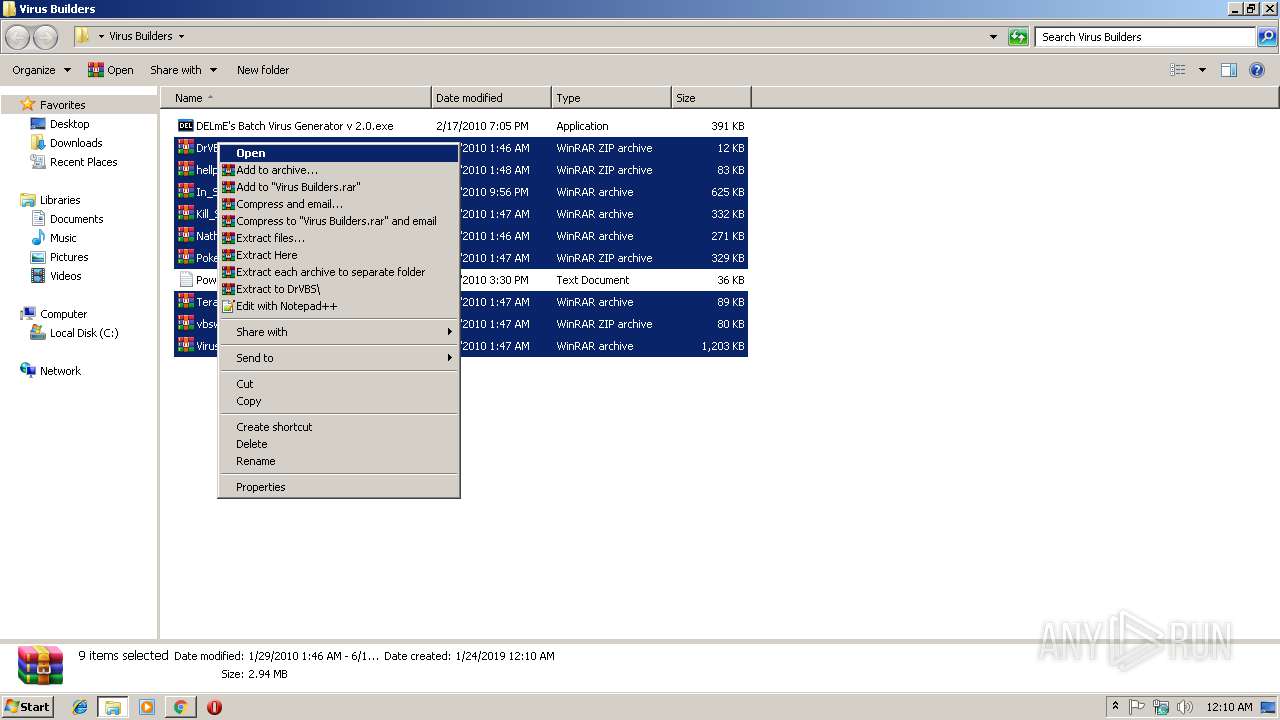
| 2512 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver "-an=C:\Users\admin\Desktop\Virus Builders\DrVBS.zip" "-an=C:\Users\admin\Desktop\Virus Builders\hellp2p.zip" "-an=C:\Users\admin\Desktop\Virus Builders\In_Shadow_Batch_Virus_Gen_-_5.0.0_-_MOD.rar" "-an=C:\Users\admin\Desktop\Virus Builders\Kill_Switch.rar" "-an=C:\Users\admin\Desktop\Virus Builders\Nathans_Image_Worm.rar" "-an=C:\Users\admin\Desktop\Virus Builders\Pokes-Worm-Gen-2.zip" "-an=C:\Users\admin\Desktop\Virus Builders\Tera_Bit.rar" "-an=C:\Users\admin\Desktop\Virus Builders\vbswg2.zip" -- "C:\Users\admin\Desktop\Virus Builders\Virus-O-Matic.rar" "C:\Users\admin\Desktop\Virus Builders\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Virus Builders.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2616 | "C:\Users\admin\Desktop\Virus Builders\DELmE's Batch Virus Generator v 2.0.exe" | C:\Users\admin\Desktop\Virus Builders\DELmE's Batch Virus Generator v 2.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 0, 0 Modules
| |||||||||||||||
| 2684 | "C:\Users\admin\Desktop\Virus Builders\WormGen.exe" | C:\Users\admin\Desktop\Virus Builders\WormGen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2844 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://mega.nz/#!LEIgSAyK!EHElydoYcB2IWybTQDKTMATQvv6322ZRyq_pUg9nCLw | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2848 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 771
Read events
1 691
Write events
77
Delete events
3
Modification events
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2872) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2844-13192762207085125 |
Value: 259 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2844-13192762207085125 |
Value: 259 | |||
| (PID) Process: | (2844) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
12
Suspicious files
38
Text files
78
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\af315013-3a99-47bb-9c68-f28a7f916bfa.tmp | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\baf06579-838e-4e8a-8e3b-b829e6daeb50.tmp | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1991f5.TMP | text | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF199224.TMP | text | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF199224.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
22
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2844 | chrome.exe | 216.58.205.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 31.216.148.10:443 | mega.nz | Datacenter Luxembourg S.A. | LU | unknown |
2844 | chrome.exe | 172.217.16.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 172.217.22.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 31.216.148.11:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
2844 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
2844 | chrome.exe | 172.217.16.174:443 | clients1.google.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 89.44.168.78:443 | gfs270n368.userstorage.mega.co.nz | Datacenter Luxembourg S.A. | LU | suspicious |
2844 | chrome.exe | 216.58.205.238:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2844 | chrome.exe | 172.217.22.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mega.nz |
| whitelisted |
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
eu.static.mega.co.nz |
| shared |
g.api.mega.co.nz |
| shared |
clients1.google.com |
| whitelisted |
gfs270n368.userstorage.mega.co.nz |
| suspicious |
sb-ssl.google.com |
| whitelisted |