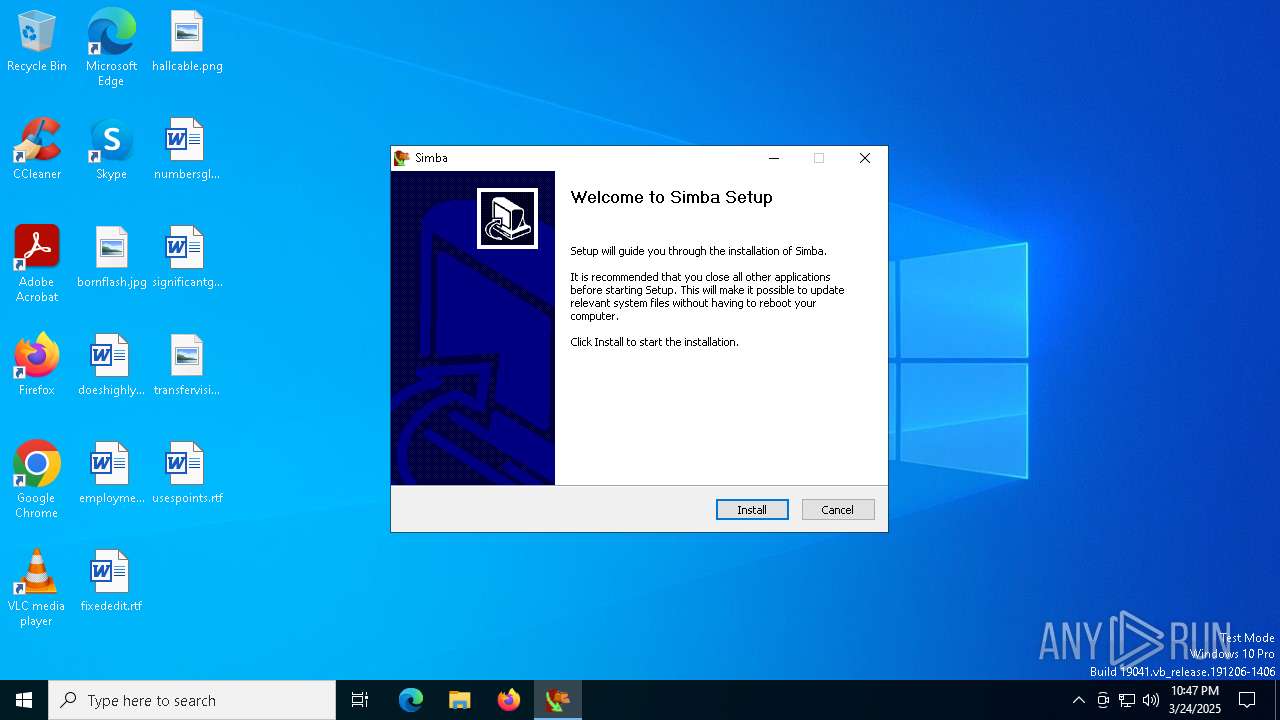
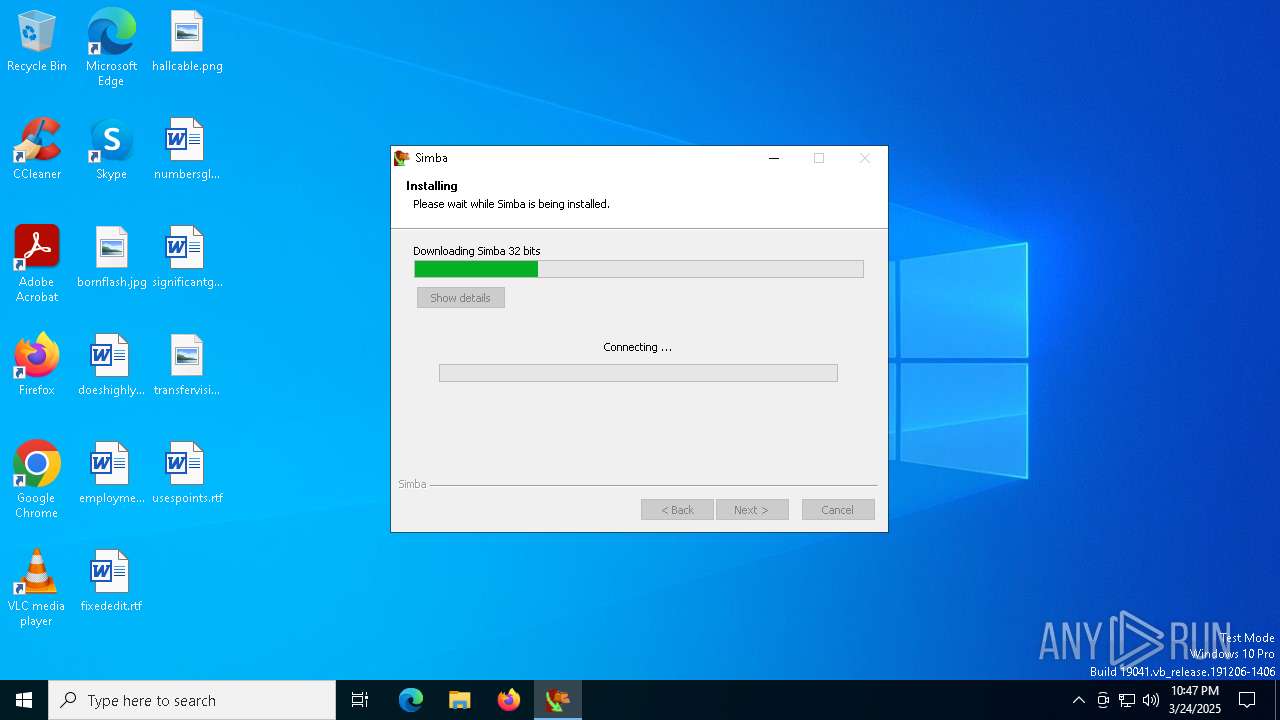
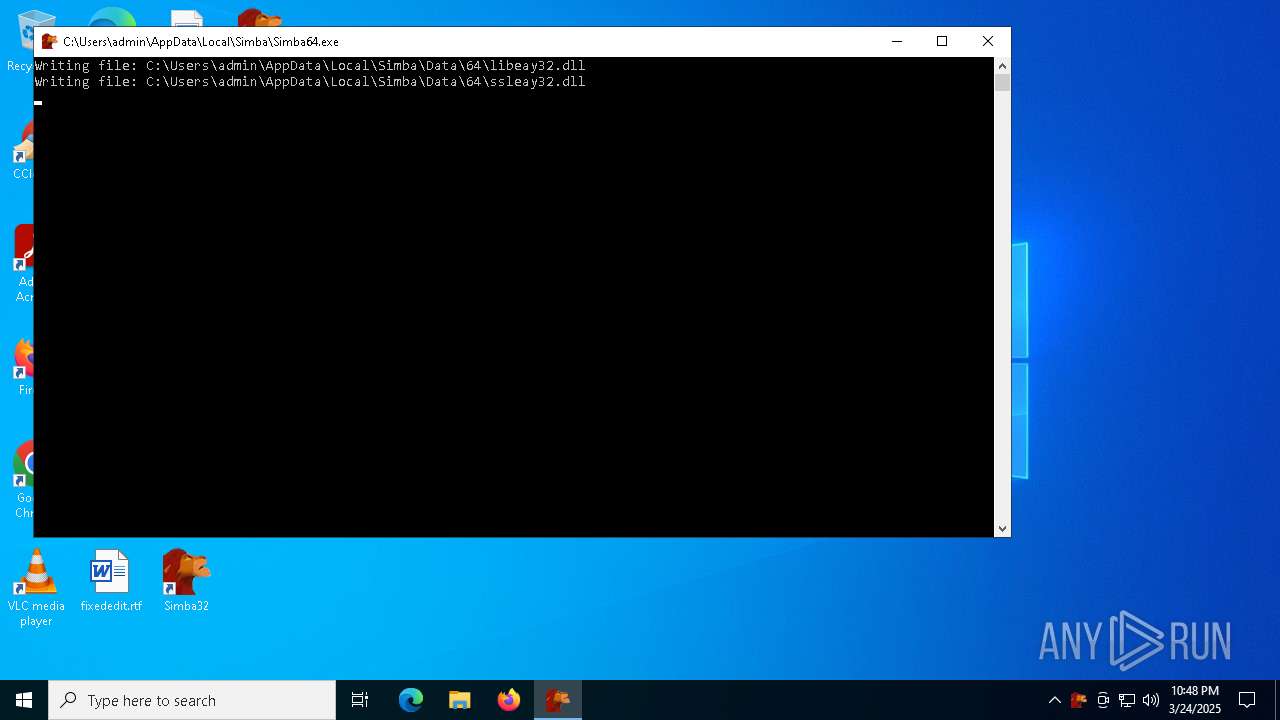
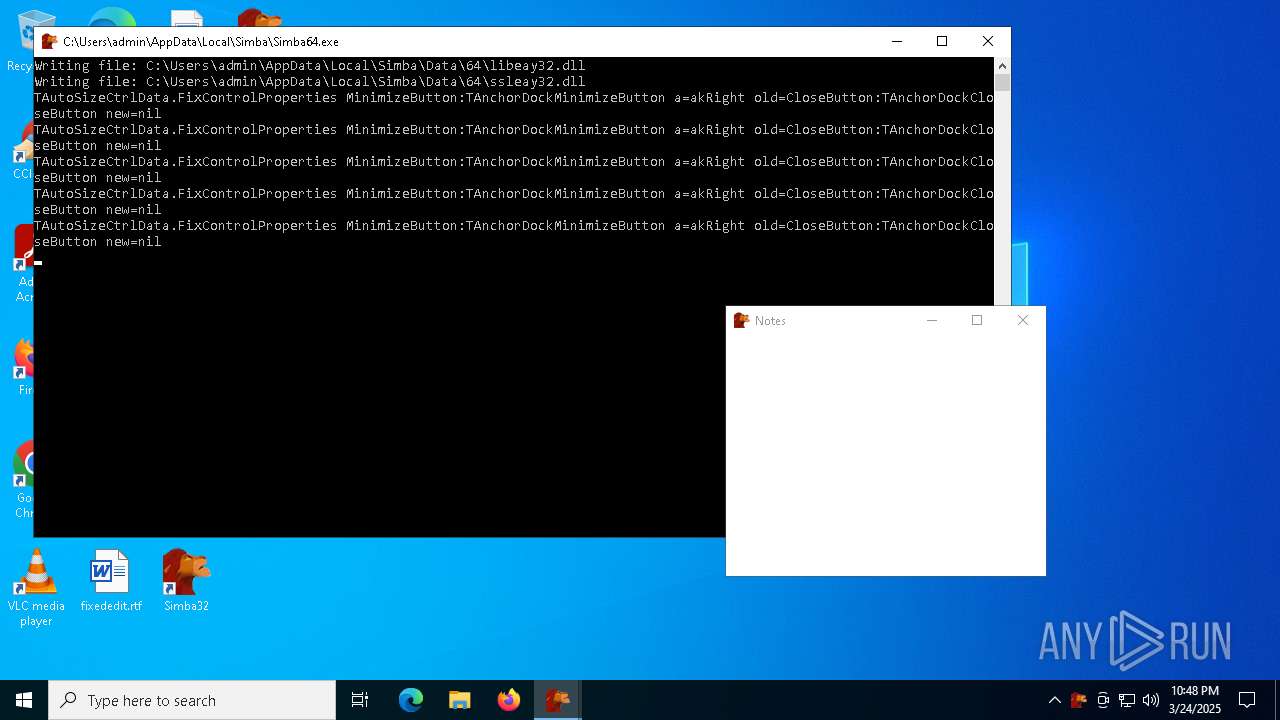
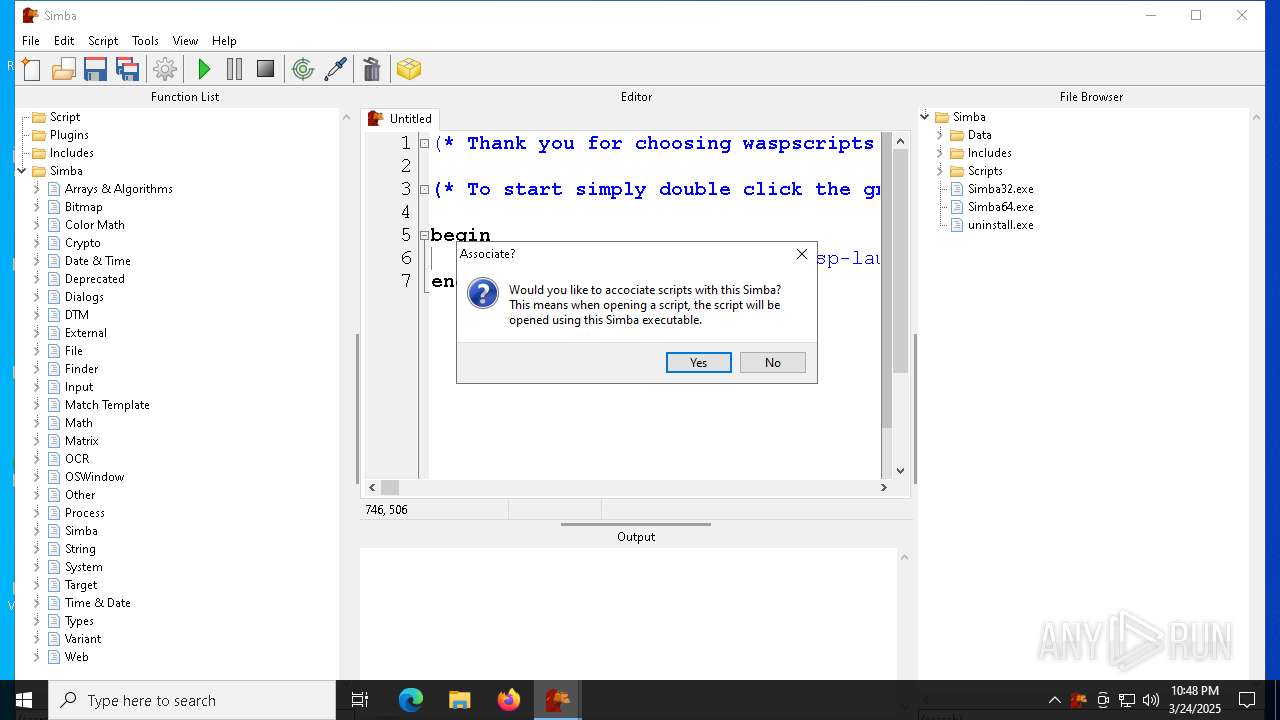
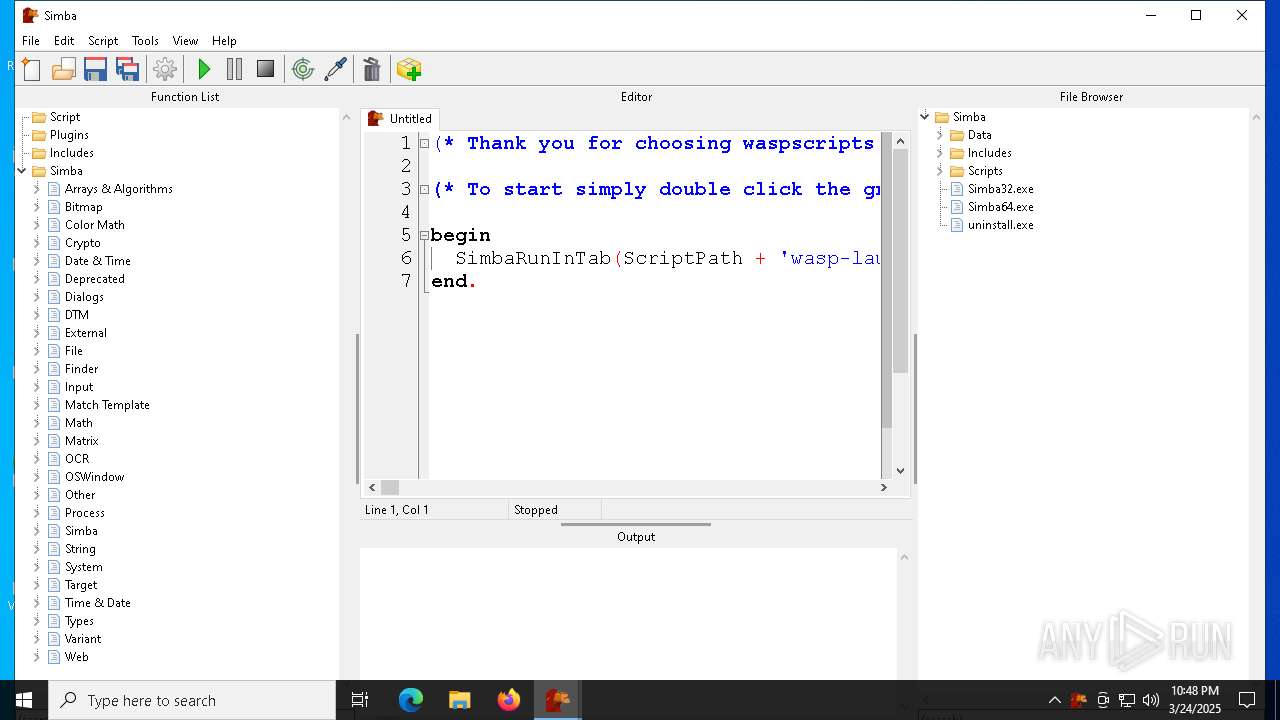
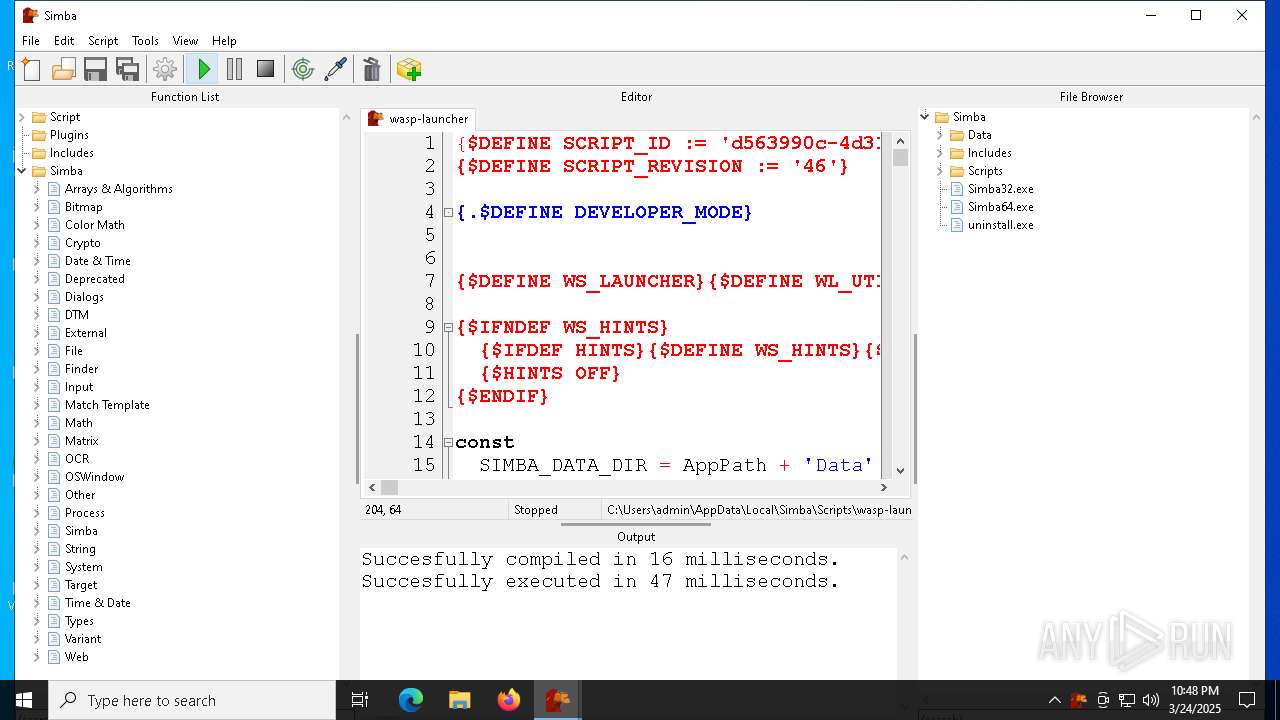
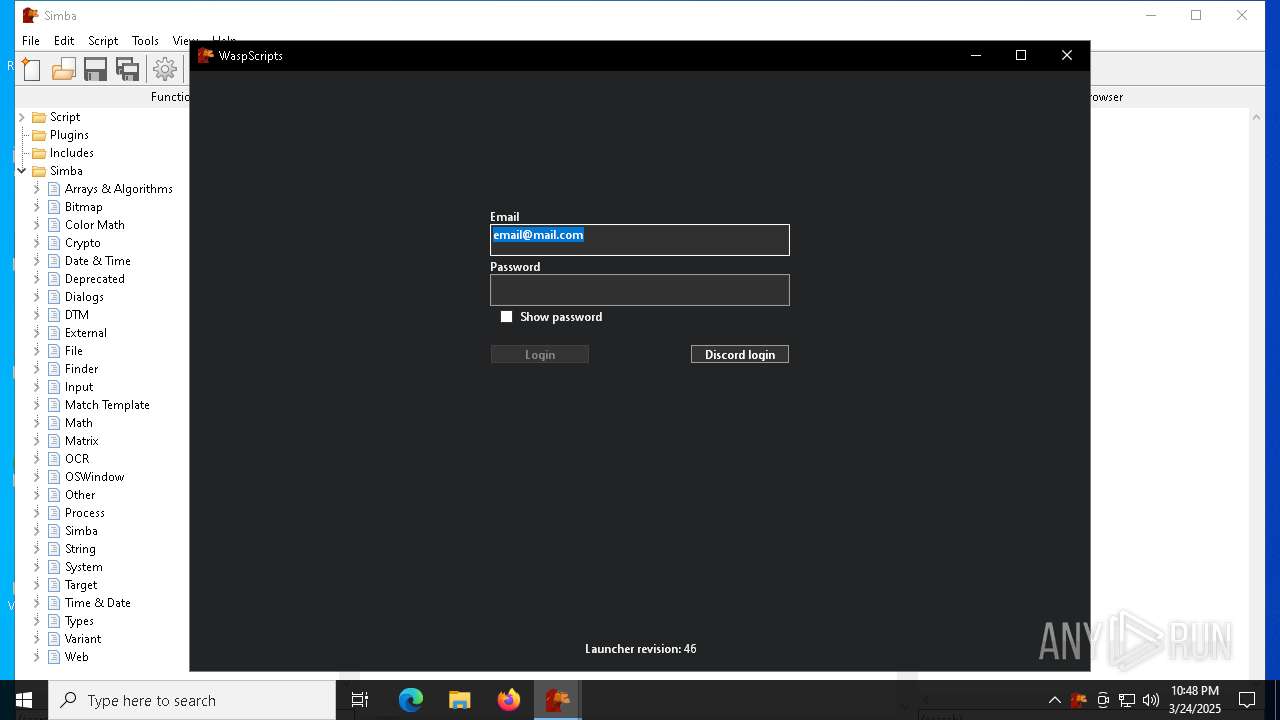
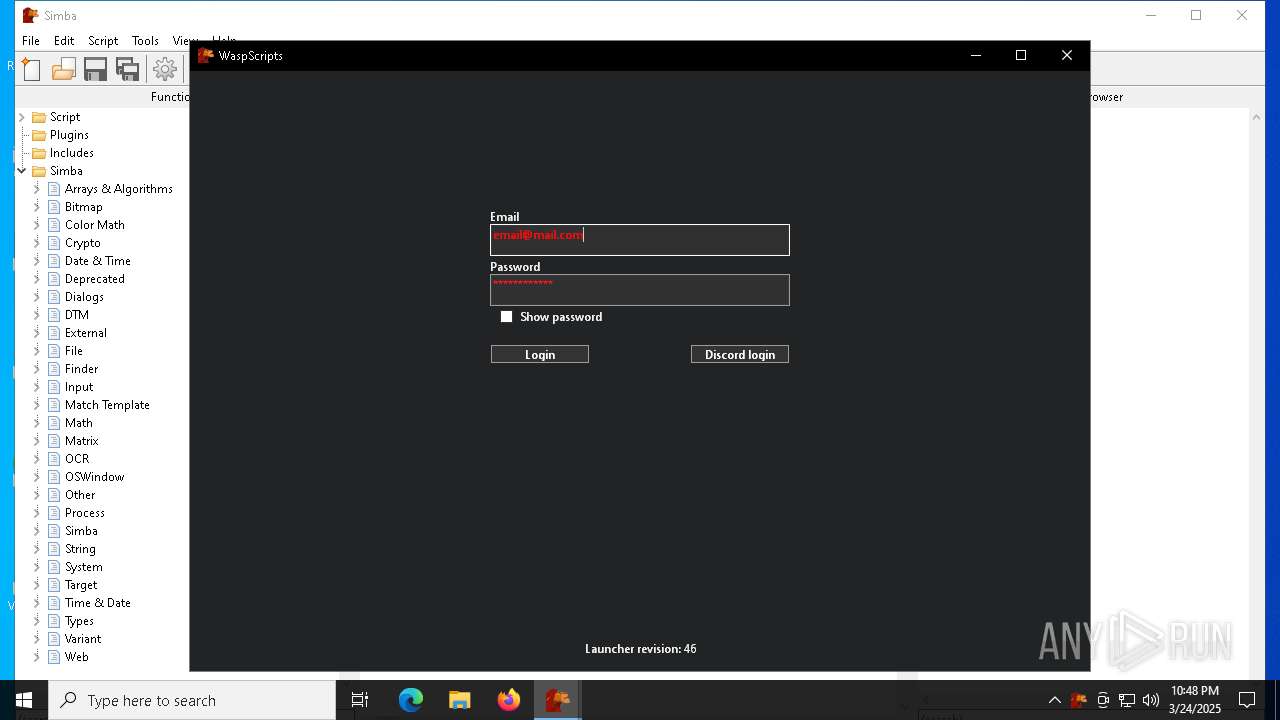
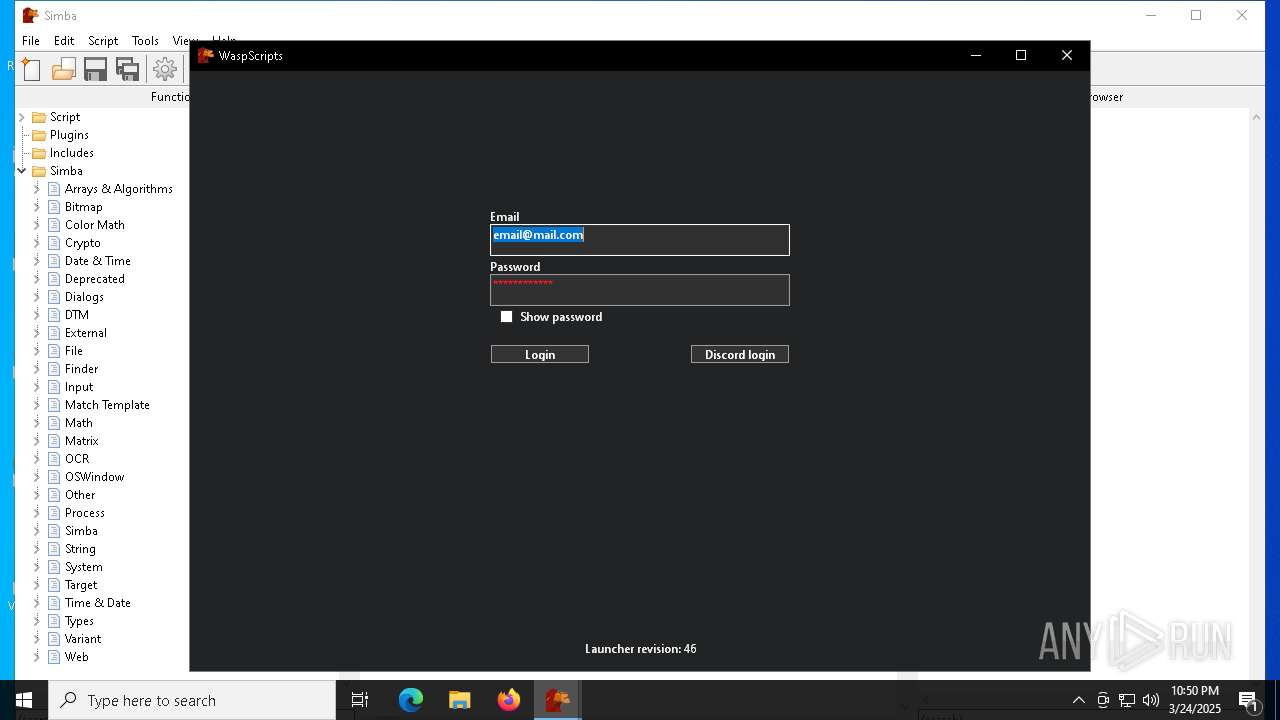
| File name: | simba-setup.exe |
| Full analysis: | https://app.any.run/tasks/19f203b0-5345-46c6-a14b-ae287480087e |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 22:47:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 001590A8B198DC4C73165710CADB3666 |
| SHA1: | 4F1E1D32767F6141957B80E8BC39BEF90761D2FF |
| SHA256: | 387F66E7AF1D2C2CE05E65552D77F817B240EE5B9A38752646ACE9F2C2B7E760 |
| SSDEEP: | 6144:yfhBxRPxGhHfOdB0prjc32EAIPRFyPM2tKnrBPxGC:S1RPIhHfOdB09jcGEzjudKVPIC |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- simba-setup.exe (PID: 4892)
- Simba64.exe (PID: 8048)
Reads security settings of Internet Explorer
- simba-setup.exe (PID: 4892)
- Simba64.exe (PID: 8048)
- Simba64.exe (PID: 6436)
- ShellExperienceHost.exe (PID: 7388)
There is functionality for taking screenshot (YARA)
- simba-setup.exe (PID: 4892)
The process creates files with name similar to system file names
- simba-setup.exe (PID: 4892)
Application launched itself
- Simba64.exe (PID: 8048)
- Simba64.exe (PID: 6436)
Malware-specific behavior (creating "System.dll" in Temp)
- simba-setup.exe (PID: 4892)
Reads the date of Windows installation
- Simba64.exe (PID: 8048)
Creates a software uninstall entry
- simba-setup.exe (PID: 4892)
Executes application which crashes
- Simba64.exe (PID: 7476)
INFO
The sample compiled with english language support
- simba-setup.exe (PID: 4892)
- Simba64.exe (PID: 8048)
- msedge.exe (PID: 968)
Reads the computer name
- simba-setup.exe (PID: 4892)
- Simba64.exe (PID: 8048)
- Simba64.exe (PID: 6436)
- identity_helper.exe (PID: 208)
- ShellExperienceHost.exe (PID: 7388)
- identity_helper.exe (PID: 6644)
Checks supported languages
- simba-setup.exe (PID: 4892)
- Simba64.exe (PID: 8048)
- Simba64.exe (PID: 2616)
- Simba64.exe (PID: 6436)
- Simba64.exe (PID: 8156)
- Simba64.exe (PID: 7476)
- identity_helper.exe (PID: 6644)
- ShellExperienceHost.exe (PID: 7388)
- identity_helper.exe (PID: 208)
Create files in a temporary directory
- simba-setup.exe (PID: 4892)
Reads the machine GUID from the registry
- simba-setup.exe (PID: 4892)
- Simba64.exe (PID: 8048)
- Simba64.exe (PID: 6436)
Reads the software policy settings
- simba-setup.exe (PID: 4892)
- BackgroundTransferHost.exe (PID: 8076)
- slui.exe (PID: 5776)
- slui.exe (PID: 7264)
Checks proxy server information
- simba-setup.exe (PID: 4892)
- BackgroundTransferHost.exe (PID: 8076)
- slui.exe (PID: 5776)
Creates files or folders in the user directory
- simba-setup.exe (PID: 4892)
- BackgroundTransferHost.exe (PID: 8076)
- Simba64.exe (PID: 8048)
- Simba64.exe (PID: 6436)
- Simba64.exe (PID: 7476)
- WerFault.exe (PID: 7672)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 7864)
- BackgroundTransferHost.exe (PID: 672)
- BackgroundTransferHost.exe (PID: 7388)
- BackgroundTransferHost.exe (PID: 8076)
- BackgroundTransferHost.exe (PID: 5892)
Process checks computer location settings
- Simba64.exe (PID: 8048)
Compiled with Borland Delphi (YARA)
- Simba64.exe (PID: 8048)
Application launched itself
- msedge.exe (PID: 5084)
- msedge.exe (PID: 1276)
- msedge.exe (PID: 6108)
Reads Environment values
- identity_helper.exe (PID: 208)
- identity_helper.exe (PID: 6644)
Manual execution by a user
- msedge.exe (PID: 5084)
Executable content was dropped or overwritten
- msedge.exe (PID: 968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | SRL |
| FileDescription: | Application |
| FileVersion: | 2.0.0.0 |
| LegalCopyright: | SRL |
| ProductName: | Simba |
Total processes
229
Monitored processes
86
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6344 --field-trial-handle=2336,i,9296055523355158678,11530612865369433805,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 672 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6924 --field-trial-handle=2336,i,9296055523355158678,11530612865369433805,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3536 --field-trial-handle=2336,i,9296055523355158678,11530612865369433805,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2512 --field-trial-handle=2336,i,9296055523355158678,11530612865369433805,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x310,0x314,0x318,0x308,0x320,0x7ffc89c25fd8,0x7ffc89c25fe4,0x7ffc89c25ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 968 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4188 --field-trial-handle=2128,i,14644423439469008498,14867537847347559822,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2228 --field-trial-handle=2128,i,14644423439469008498,14867537847347559822,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3980 --field-trial-handle=2128,i,14644423439469008498,14867537847347559822,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
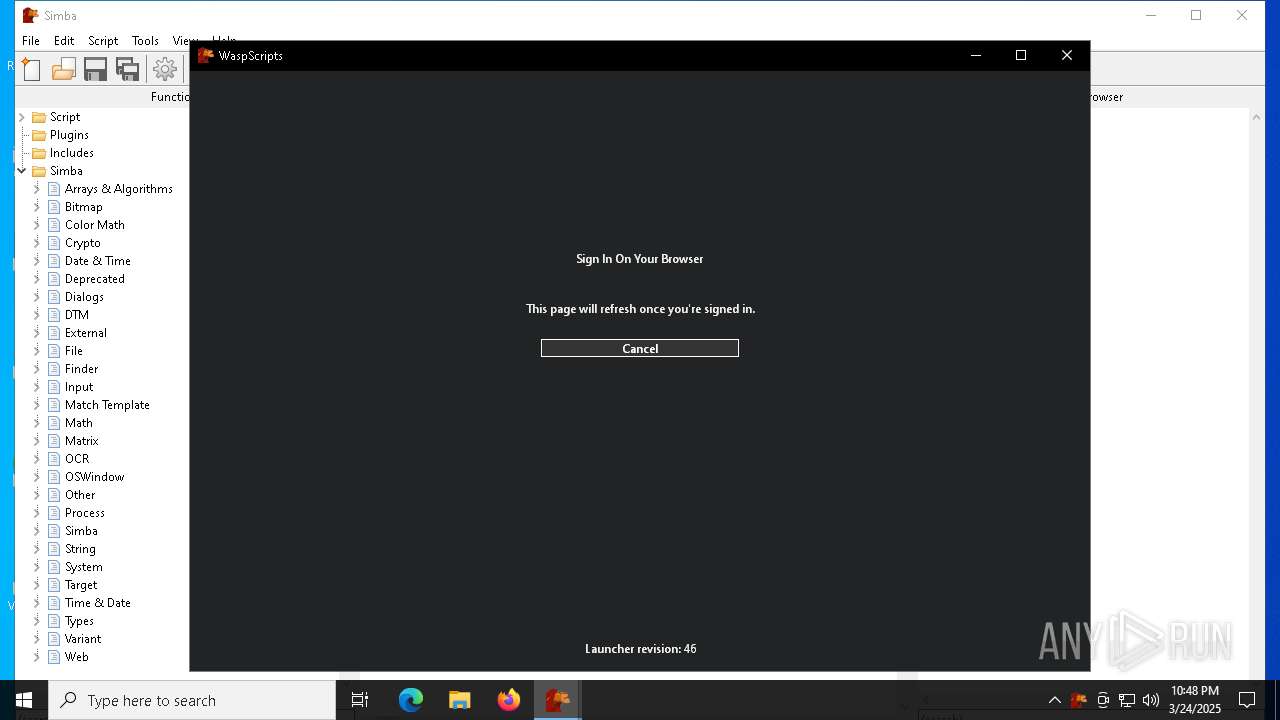
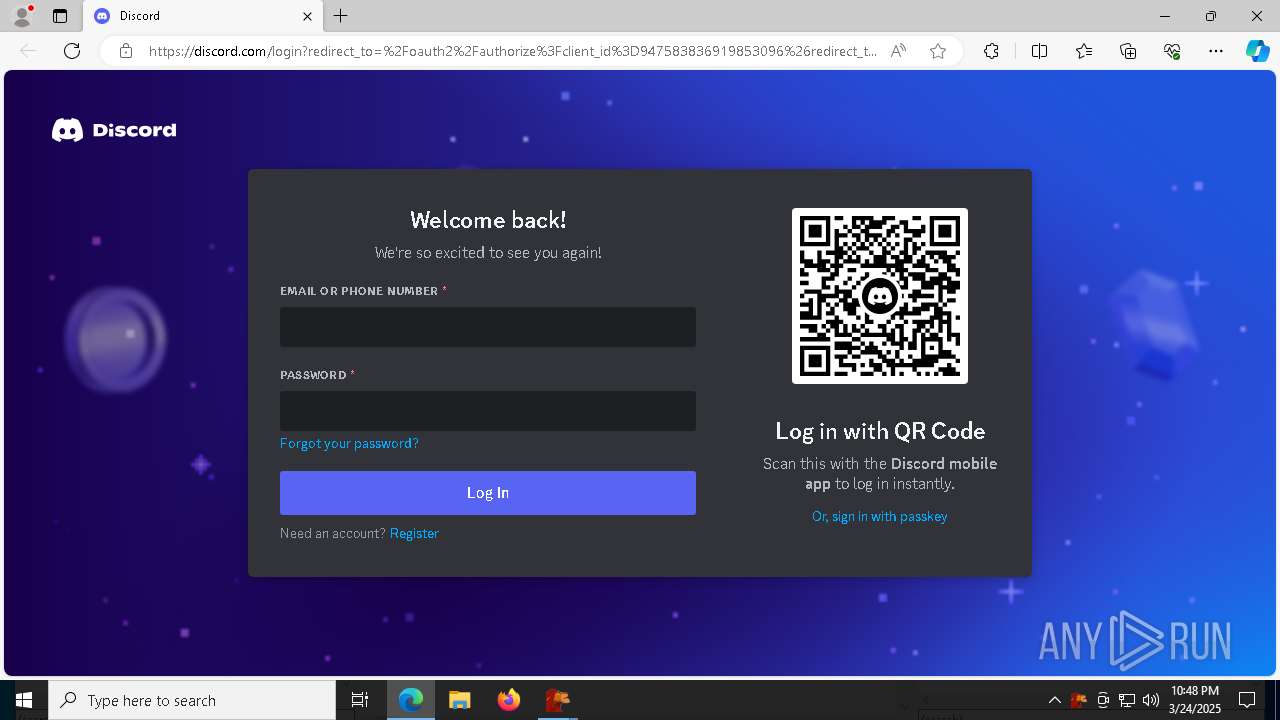
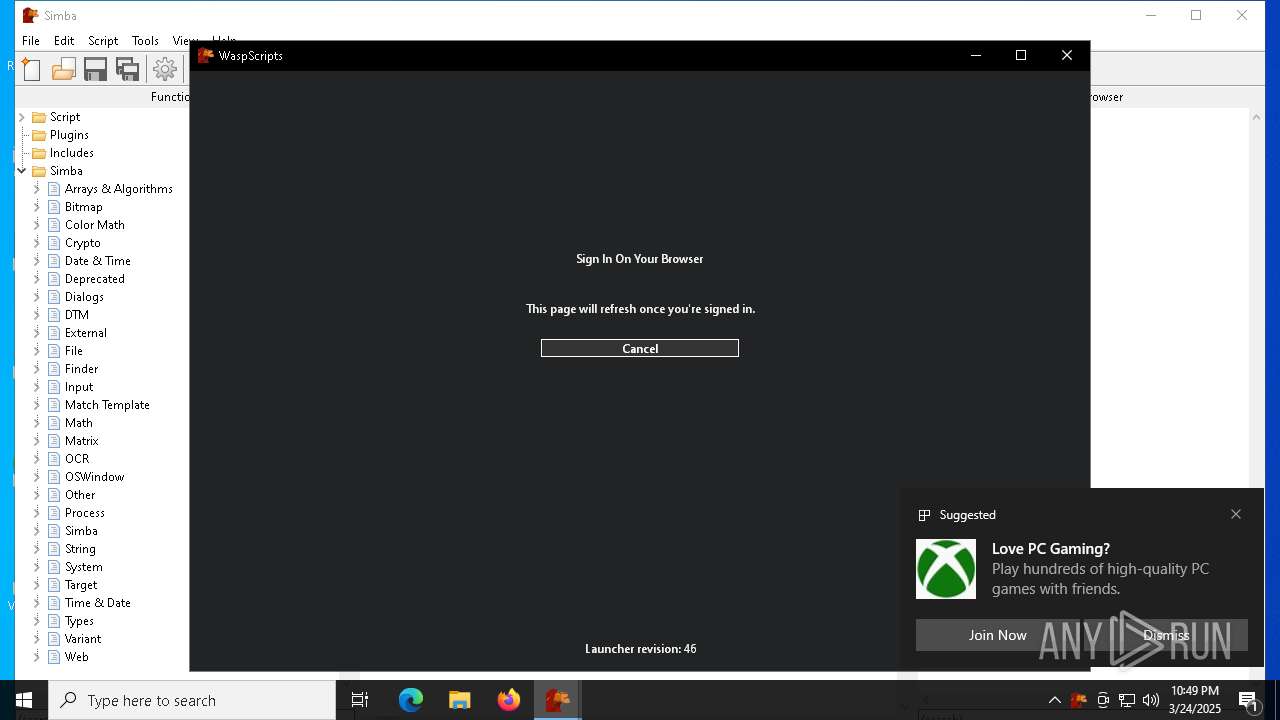
| 1276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://db.waspscripts.com/auth/v1/authorize?provider=discord&redirect_to=http%3A%2F%2Flocalhost%3A5217%2F&scopes=identify%20email%20guilds%20guilds.members.read&code_challenge=LRhCeTaZJmIMMDL_2YruI0oObHo0gVxbvp5qhqSe6Bg&code_challenge_method=s256 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | Simba64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
16 543
Read events
16 474
Write events
66
Delete events
3
Modification events
| (PID) Process: | (4892) simba-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4892) simba-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4892) simba-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7864) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7864) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7864) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8076) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8076) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8076) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (672) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
34
Suspicious files
547
Text files
111
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4892 | simba-setup.exe | C:\Users\admin\AppData\Local\Simba\Simba32.exe | — | |
MD5:— | SHA256:— | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\Local\Temp\nsyBFF7.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\Local\Temp\nsyBFF7.tmp\InstallOptions.dll | executable | |
MD5:D1EEFB07ABC2577DFB92EB2E95A975E4 | SHA256:89DD7D646278D8BFC41D5446BDC348B9A9AFAA832ABF02C1396272BB7AC7262A | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D9CA54E0FA212456E1DB00704A97658E | binary | |
MD5:275815EAB675DB64F289333EFFD006C4 | SHA256:472BD7C7C3C2BEC478926FCD98CADCCE3D83E824CA0085027865768451601749 | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\Local\Simba\Data\default.simba | text | |
MD5:29633510DA0714586D27F3F5B64F219A | SHA256:41099C861BA50A6BD59D8513D165C67BAB7A689E4B53BF5B77C4782D5E66C23E | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:9243562A066395834AE5E0596058BF7C | SHA256:75BB1FE5606B9934B75FEF72D3B18E22B812AA6A72F5F5F071EB5410FDA4E721 | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\Local\Temp\nsyBFF7.tmp\modern-header.bmp | image | |
MD5:A410C98B413D579A449128E104EDD6A9 | SHA256:84E6DDD4C4DB69686BB38ACC244BEAF91B2F6E562D18F5A658DE9ECB9E359F2D | |||
| 8076 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\80fd2c65-419e-4e55-ab3d-0a790c5ed077.down_data | — | |
MD5:— | SHA256:— | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\Simba-Win64[1].exe | executable | |
MD5:6CB0CD22C2A188D07E15A0BB22BD49ED | SHA256:CCC783E710A9124586E1008795D57A287A20E2EB7B6922DBAA34EA8470F73E9C | |||
| 4892 | simba-setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:91824A29958C3AABDE668AD861788AF0 | SHA256:53BB14FBDAC4A4B69ACA2E372D1B84EE2936A36C21A5EA82D085DE38ED891588 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
102
DNS requests
74
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4892 | simba-setup.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.54.122:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4892 | simba-setup.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
4892 | simba-setup.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CECoW9cIBGAf3CpJj3Tw5qfI%3D | unknown | — | — | whitelisted |
4892 | simba-setup.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
4892 | simba-setup.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
4892 | simba-setup.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
3956 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7520 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1743005673&P2=404&P3=2&P4=CQzlomuvexYu%2bTdzxGPMFbLLW0V0HMKiNWzw6zuHQRejNSgVr0s%2f%2flMmMYiB4J1kGkdB9B2Aumo0w64zZWaX5w%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 95.101.54.122:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4892 | simba-setup.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
4892 | simba-setup.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
900 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
900 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
900 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
900 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
900 | msedge.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
900 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
900 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
900 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
900 | msedge.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |