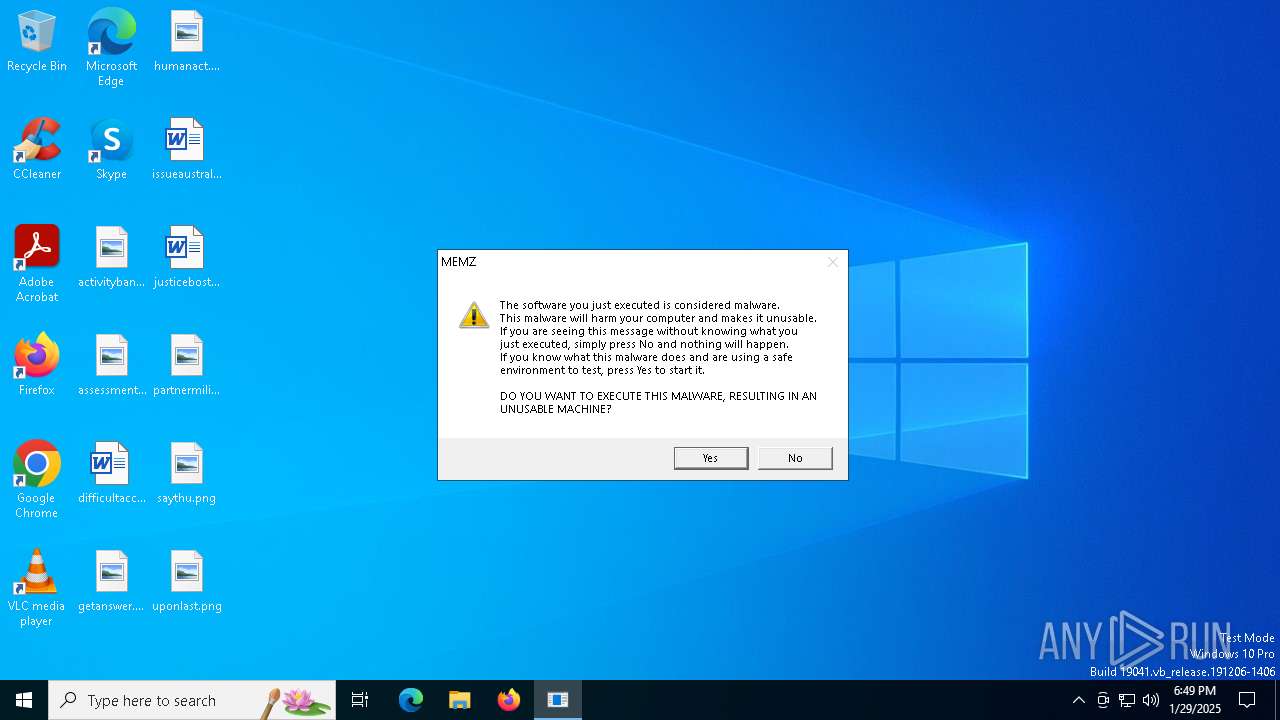
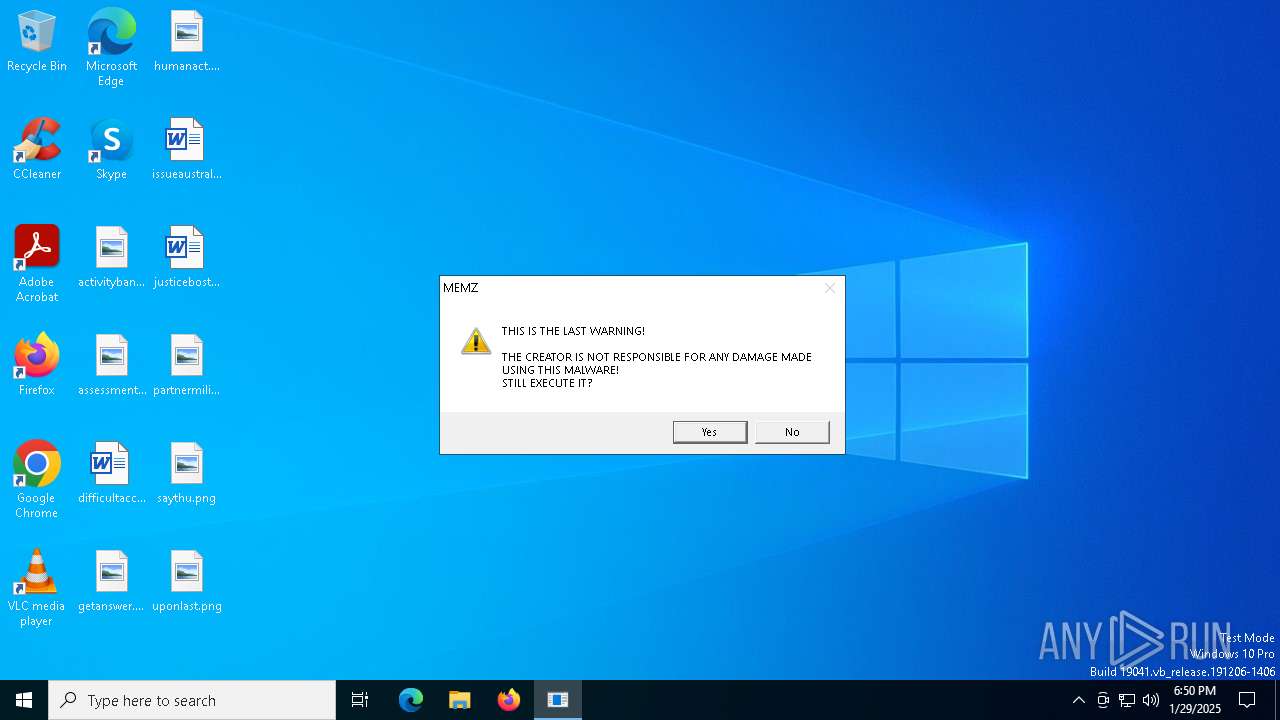
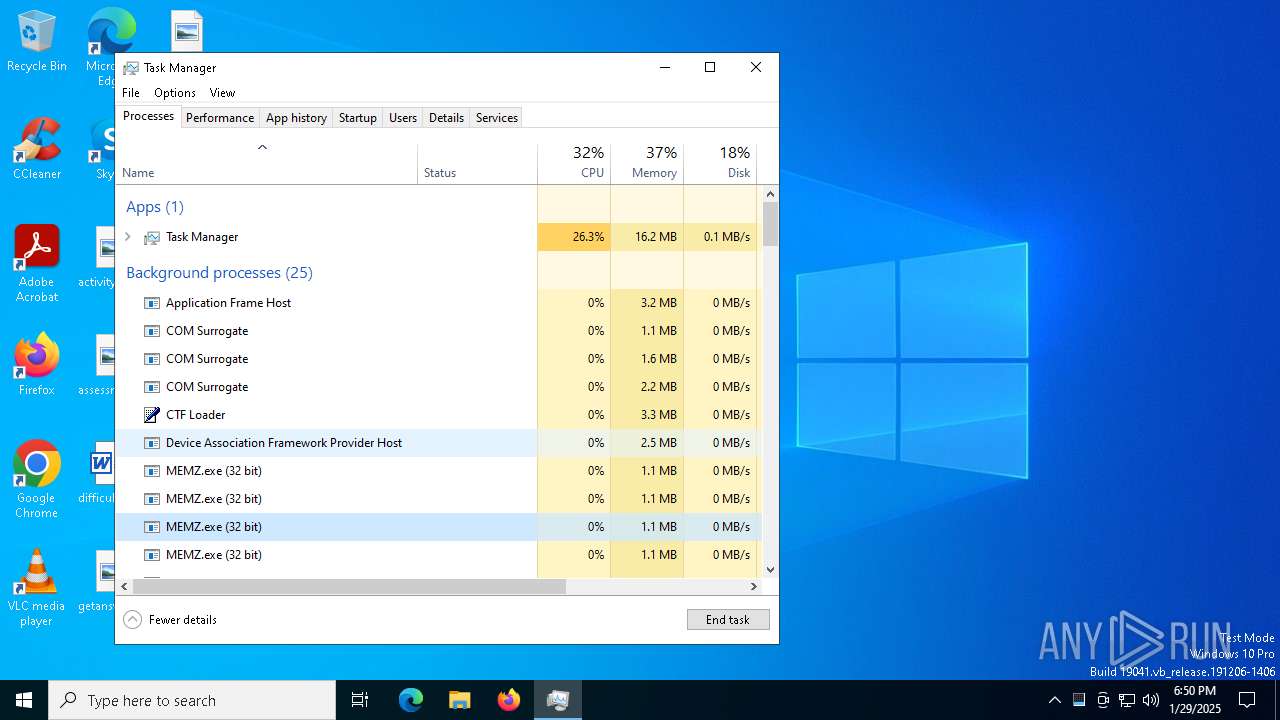
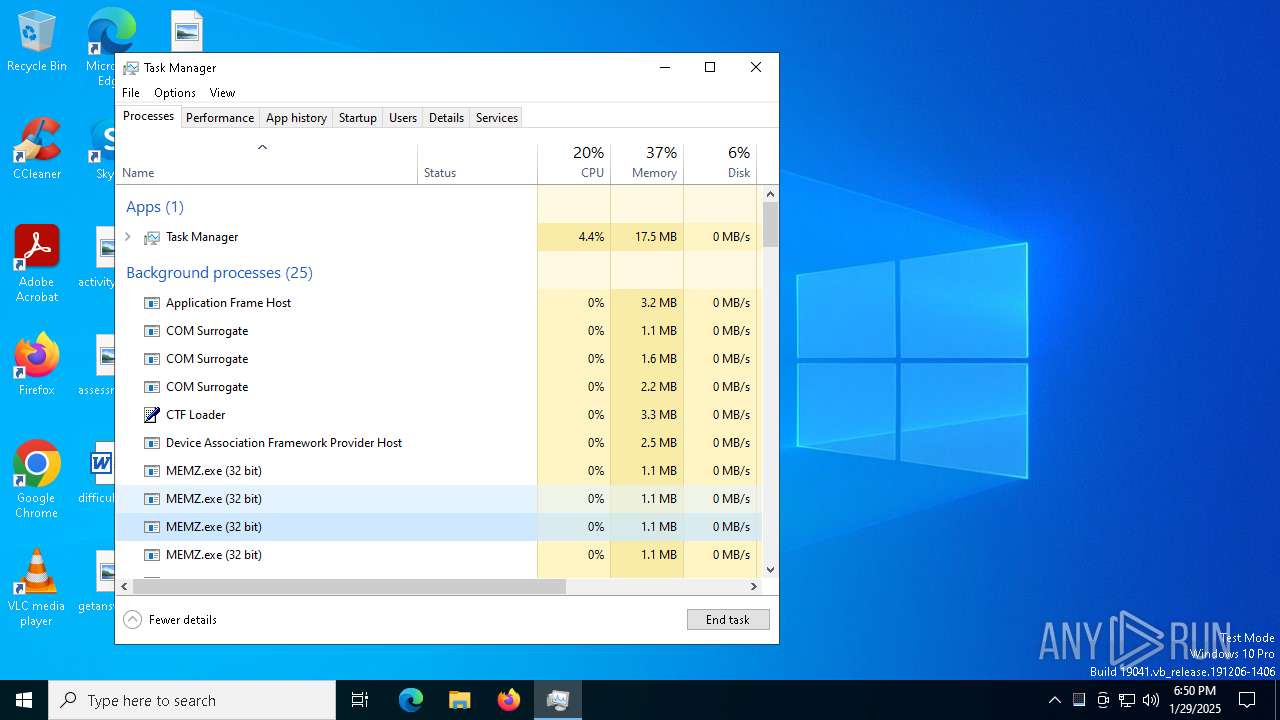
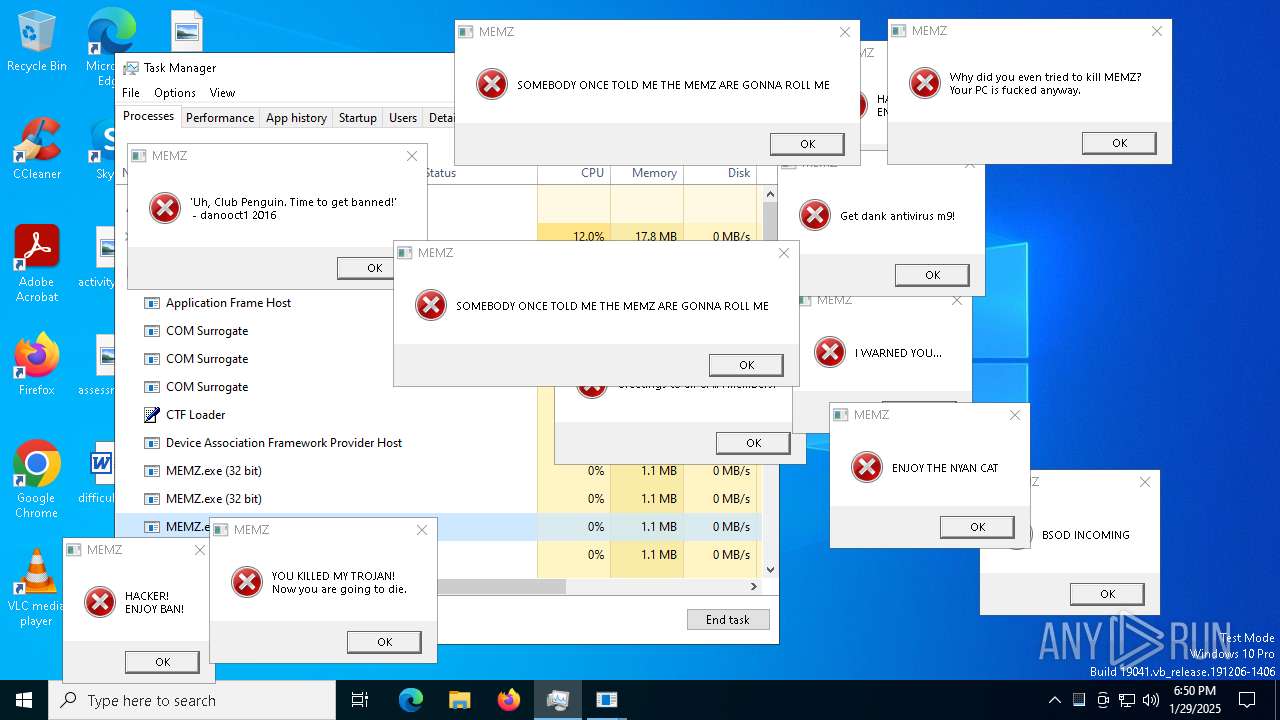
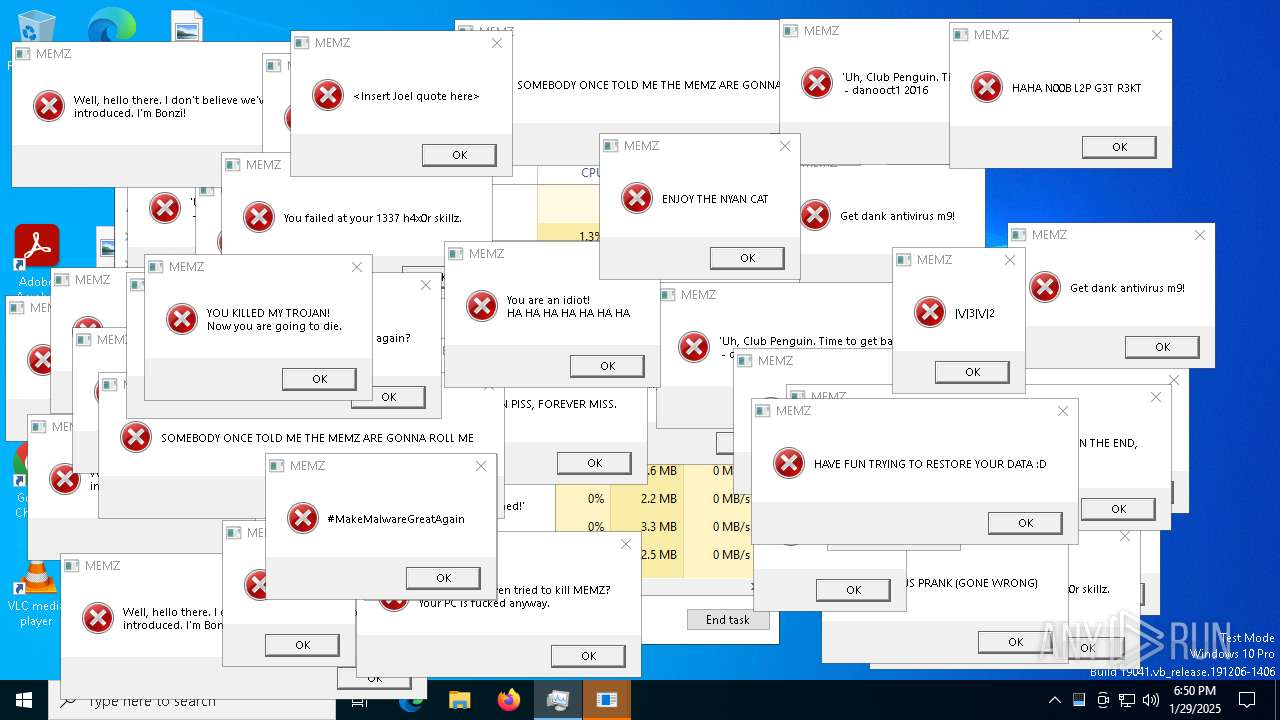
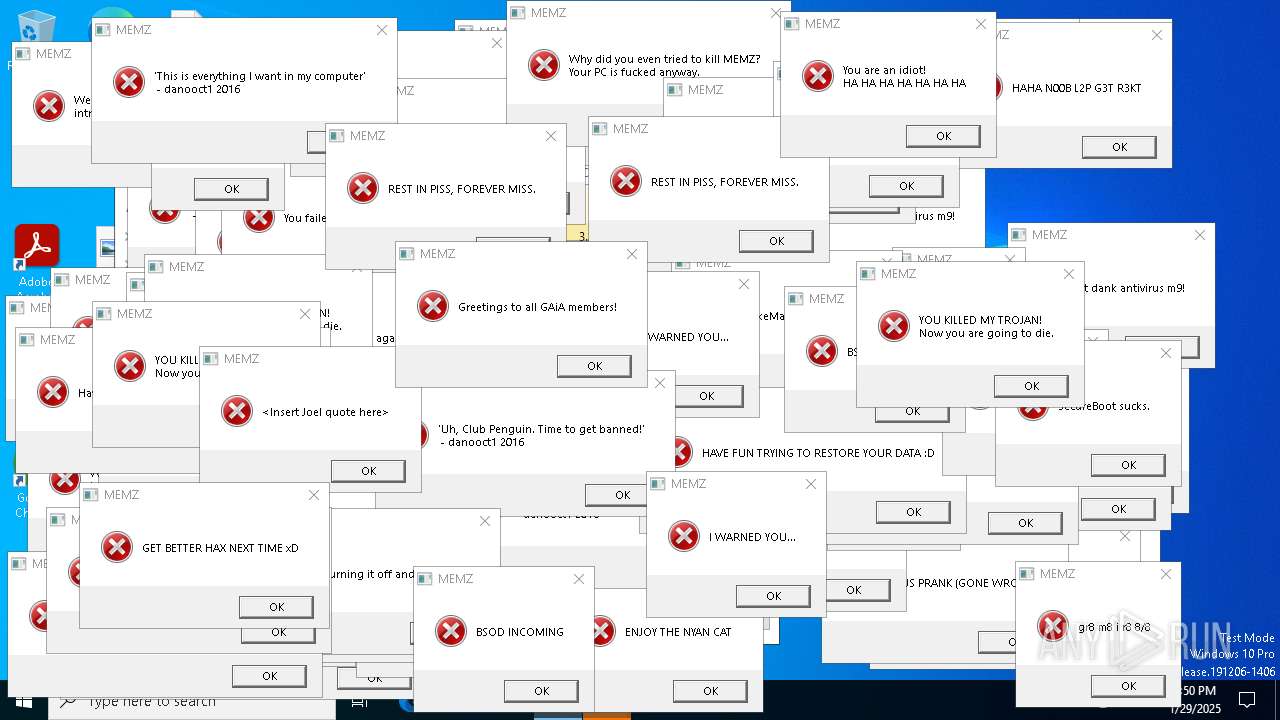
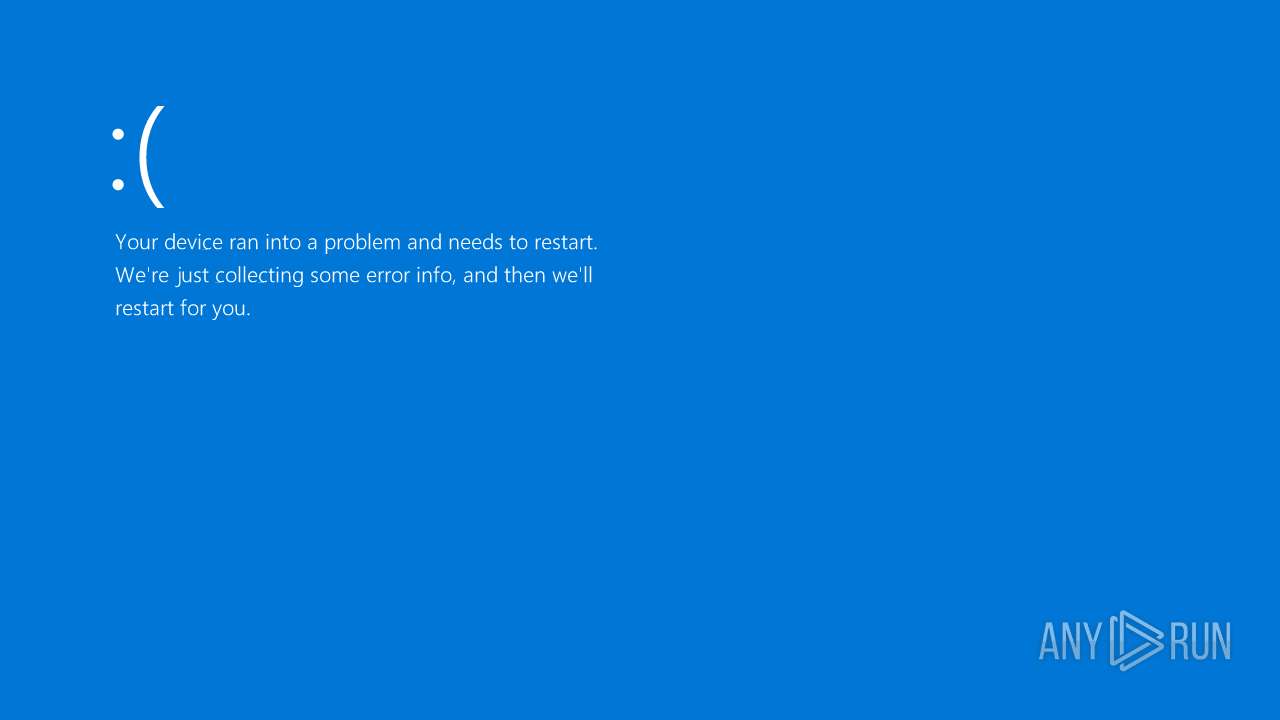
| File name: | MEMZ.exe |
| Full analysis: | https://app.any.run/tasks/e757bae1-19f5-4f39-ac2b-8ea316881275 |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2025, 18:49:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 1D5AD9C8D3FEE874D0FEB8BFAC220A11 |
| SHA1: | CA6D3F7E6C784155F664A9179CA64E4034DF9595 |
| SHA256: | 3872C12D31FC9825E8661AC01ECEE2572460677AFBC7093F920A8436A42E28FF |
| SSDEEP: | 192:M2WgyvSW8gRc6olcIEiwqZKBkDFR43xWTM3LHf26gFrcx3sNqa:JWgnSmFlcIqq3agmLH+6gF23sNj |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- MEMZ.exe (PID: 6744)
- MEMZ.exe (PID: 2324)
- MEMZ.exe (PID: 6720)
- MEMZ.exe (PID: 6760)
- MEMZ.exe (PID: 6784)
- MEMZ.exe (PID: 6804)
Application launched itself
- MEMZ.exe (PID: 2324)
Reads security settings of Internet Explorer
- MEMZ.exe (PID: 2324)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 2808)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2284)
INFO
Checks supported languages
- MEMZ.exe (PID: 6828)
- MEMZ.exe (PID: 6804)
- MEMZ.exe (PID: 6784)
- MEMZ.exe (PID: 6744)
- MEMZ.exe (PID: 6720)
- MEMZ.exe (PID: 6760)
- MEMZ.exe (PID: 2324)
- OfficeClickToRun.exe (PID: 2980)
- PLUGScheduler.exe (PID: 2284)
Process checks computer location settings
- MEMZ.exe (PID: 2324)
Reads the computer name
- MEMZ.exe (PID: 2324)
- MEMZ.exe (PID: 6744)
- MEMZ.exe (PID: 6720)
- MEMZ.exe (PID: 6784)
- MEMZ.exe (PID: 6760)
Manual execution by a user
- Taskmgr.exe (PID: 7128)
- Taskmgr.exe (PID: 1412)
- svchost.exe (PID: 2260)
- svchost.exe (PID: 2404)
- svchost.exe (PID: 2304)
- svchost.exe (PID: 2316)
- svchost.exe (PID: 2476)
- svchost.exe (PID: 2484)
- svchost.exe (PID: 2496)
- spoolsv.exe (PID: 2664)
- svchost.exe (PID: 2524)
- svchost.exe (PID: 2956)
- OfficeClickToRun.exe (PID: 2980)
- svchost.exe (PID: 2988)
- svchost.exe (PID: 1144)
- svchost.exe (PID: 2720)
- svchost.exe (PID: 2528)
- svchost.exe (PID: 2808)
- svchost.exe (PID: 3120)
- svchost.exe (PID: 3296)
- svchost.exe (PID: 3148)
- svchost.exe (PID: 2752)
- svchost.exe (PID: 2916)
- svchost.exe (PID: 2924)
- svchost.exe (PID: 2860)
- svchost.exe (PID: 3644)
- svchost.exe (PID: 3652)
- svchost.exe (PID: 4064)
- svchost.exe (PID: 3916)
- svchost.exe (PID: 3952)
- svchost.exe (PID: 2788)
- svchost.exe (PID: 3032)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 4124)
- svchost.exe (PID: 4312)
- svchost.exe (PID: 4600)
- svchost.exe (PID: 5292)
- svchost.exe (PID: 6072)
- svchost.exe (PID: 2976)
- svchost.exe (PID: 3824)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 1412)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 6760)
- MEMZ.exe (PID: 6720)
- MEMZ.exe (PID: 6784)
- OfficeClickToRun.exe (PID: 2980)
Reads the time zone
- svchost.exe (PID: 2956)
Checks proxy server information
- OfficeClickToRun.exe (PID: 2980)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 2980)
Disables trace logs
- svchost.exe (PID: 3296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:03:19 03:33:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 3584 |
| InitializedDataSize: | 11776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x122d |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
237
Monitored processes
50
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1144 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s LanmanServer | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1412 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | C:\WINDOWS\system32\svchost.exe -k appmodel -p -s StateRepository | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2304 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Users\admin\AppData\Local\Temp\MEMZ.exe" | C:\Users\admin\AppData\Local\Temp\MEMZ.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2324 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2404 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s ShellHWDetection | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2476 | C:\WINDOWS\system32\svchost.exe -k LocalSystemNetworkRestricted -p -s fhsvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 724
Read events
29 921
Write events
16 788
Delete events
15
Modification events
| (PID) Process: | (1412) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (1412) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AA6C15F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AA6C15F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000AB6C15F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028AB6C15F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050AB6C15F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AA6C15F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070AB6C15F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088AB6C15F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8AB6C15F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8AB6C15F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0AB6C15F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010AC6C15F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AA6C15F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040AC6C15F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068AC6C15F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090AC6C15F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8AC6C15F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8AC6C15F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8AC6C15F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028AB6C15F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020AD6C15F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050AB6C15F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AA6C15F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070AB6C15F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088AB6C15F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8AB6C15F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8AB6C15F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AA6C15F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AE6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AE6C15F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (2860) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Winmgmt\Parameters |
| Operation: | write | Name: | ServiceDllUnloadOnStop |
Value: 1 | |||
| (PID) Process: | (2916) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\iphlpsvc\DaMultisite |
| Operation: | delete value | Name: | SelectedSite |
Value: | |||
| (PID) Process: | (2916) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\iphlpsvc\DaMultisite |
| Operation: | delete value | Name: | SelectionMethod |
Value: | |||
| (PID) Process: | (2260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModel\StateRepositoryStatus |
| Operation: | write | Name: | ServiceLastKnownStatus |
Value: 2 | |||
| (PID) Process: | (2260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModel\StateRepositoryStatus |
| Operation: | write | Name: | CheckpointLastPerformed |
Value: DD9068D77E72DB01 | |||
| (PID) Process: | (2260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModel\StateRepositoryStatus |
| Operation: | write | Name: | DeploymentDatabaseStatisticsLastUpdated |
Value: D3BC6FD77E72DB01 | |||
| (PID) Process: | (2260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModel\StateRepositoryStatus |
| Operation: | write | Name: | MaintenanceLastPerformed |
Value: A99949D77E72DB01 | |||
| (PID) Process: | (2260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\AppModel\StateRepository\Cache\Metadata |
| Operation: | write | Name: | LastChangeId |
Value: 0000000000000000 | |||
Executable files
0
Suspicious files
55
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | svchost.exe | C:\Windows\System32\sru\SRUDB.dat | — | |
MD5:— | SHA256:— | |||
| 1412 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 2284 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.044.etl | binary | |
MD5:079890A8EC8D5CB6523FCEC2209780AA | SHA256:0E12D2D76DD738CE196BED522E35F75E2CC91294F78CDDCBE8CE7787AAA70049 | |||
| 2260 | svchost.exe | C:\ProgramData\Microsoft\Windows\AppRepository\StateRepository-Deployment.srd-wal | binary | |
MD5:8FBCA71656AF5D201E036FD1F600C7C3 | SHA256:289055B82E21EC693069EF1F07CC437CDE214F5299A667C0E9843EFA84F53793 | |||
| 2260 | svchost.exe | C:\ProgramData\Microsoft\Windows\AppRepository\StateRepository-Deployment.srd-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4064 | svchost.exe | C:\ProgramData\regid.1991-06.com.microsoft\regid.1991-06.com.microsoft_Windows-10-Pro.swidtag | xml | |
MD5:CAB432C4918E1CFF493C9668B2338104 | SHA256:2CE9E3A7CF26A6706D8078C732D8211AEB76E9FAA5C6D3A026E32B077EDF23DF | |||
| 2484 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Microsoft\Windows\DeliveryOptimization\Logs\dosvc.20250129_185144_172.etl | binary | |
MD5:5B58DD13043FD4A8594DFF5F9A4B27EB | SHA256:1A476BE60696AD82DC3C712B149C99D5876D638B79A3154EE645C047E7ED3244 | |||
| 2260 | svchost.exe | C:\ProgramData\Microsoft\Windows\AppRepository\StateRepository-Machine.srd-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4312 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\ConnectedDevicesPlatform\CDPGlobalSettings.cdp | text | |
MD5:036467EBC61C495B6110E957AB9A854D | SHA256:1719A987C02B03127A3A9B7A443ABD9D66AF9A76D324BEF72CC75540E67EFD01 | |||
| 2284 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.041.etl | binary | |
MD5:44A0E917AD0C126931B1BCD959285A9A | SHA256:DDFBE47E7DFD6D8B7517F2F6FF9808ECF3C0A25F588A9F96D04F4E2B4A578573 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
40
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6884 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6884 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4876 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.21:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 69.192.162.125:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2632 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6884 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |