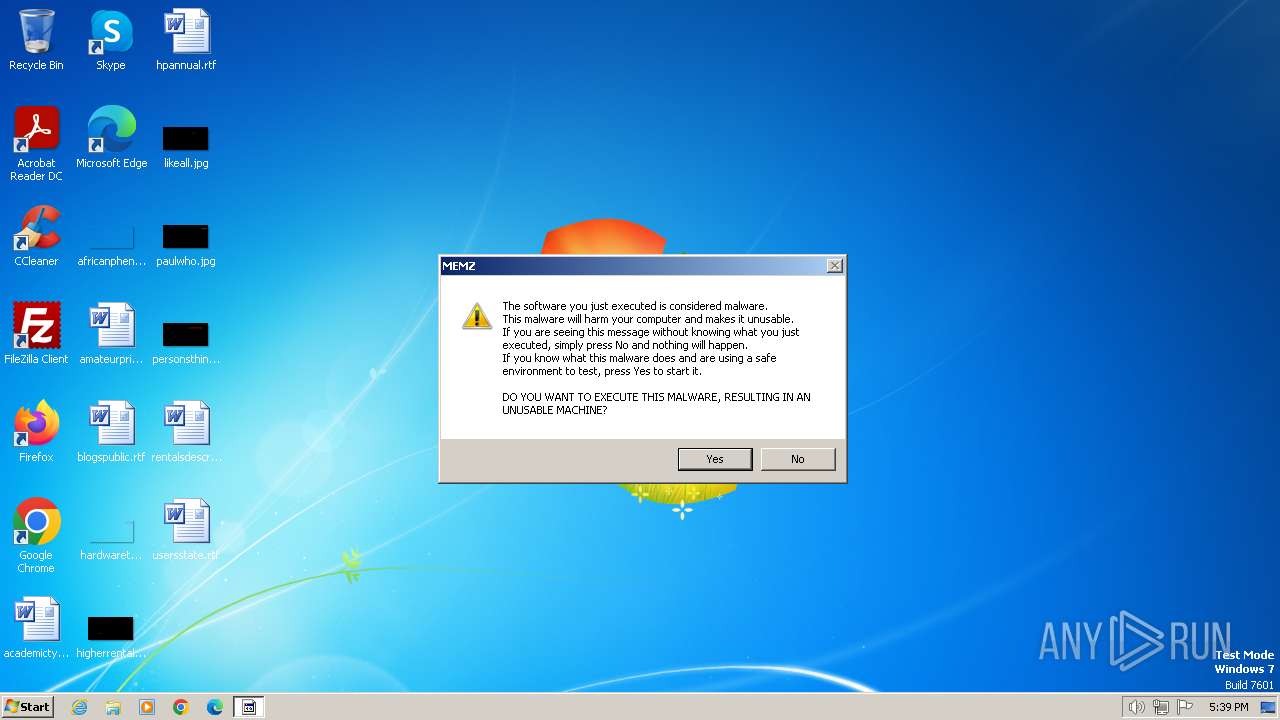
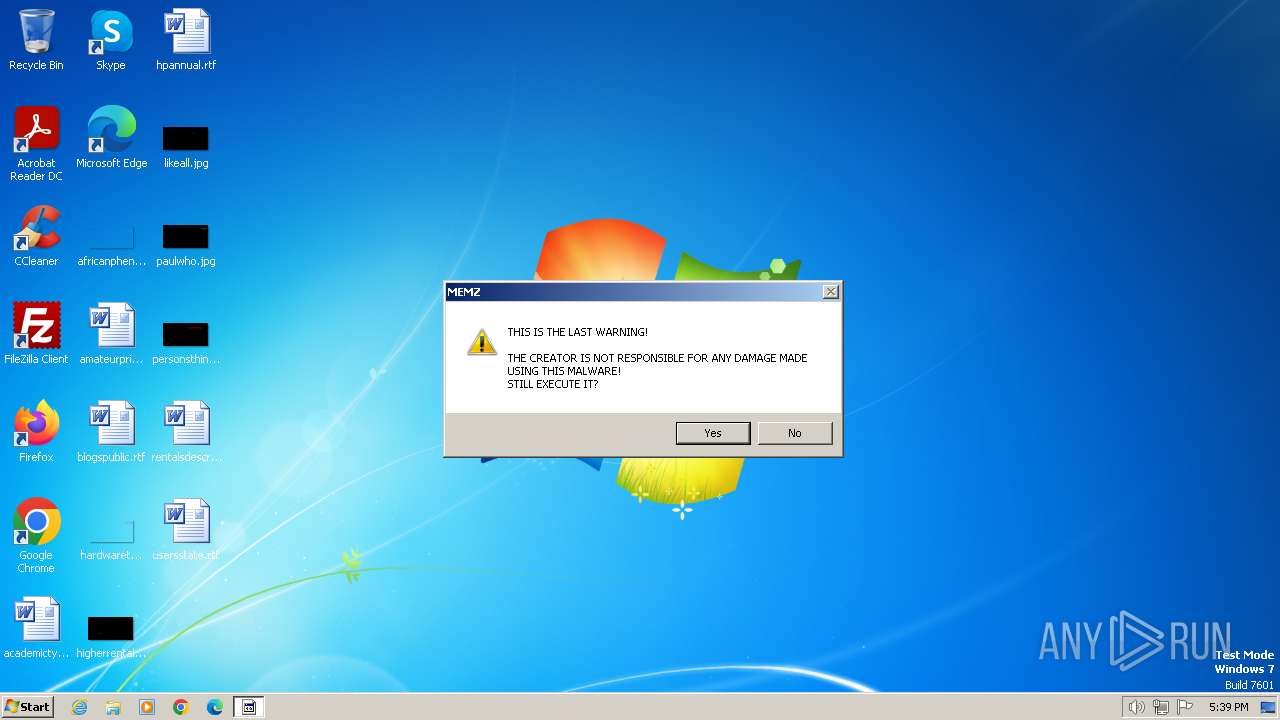
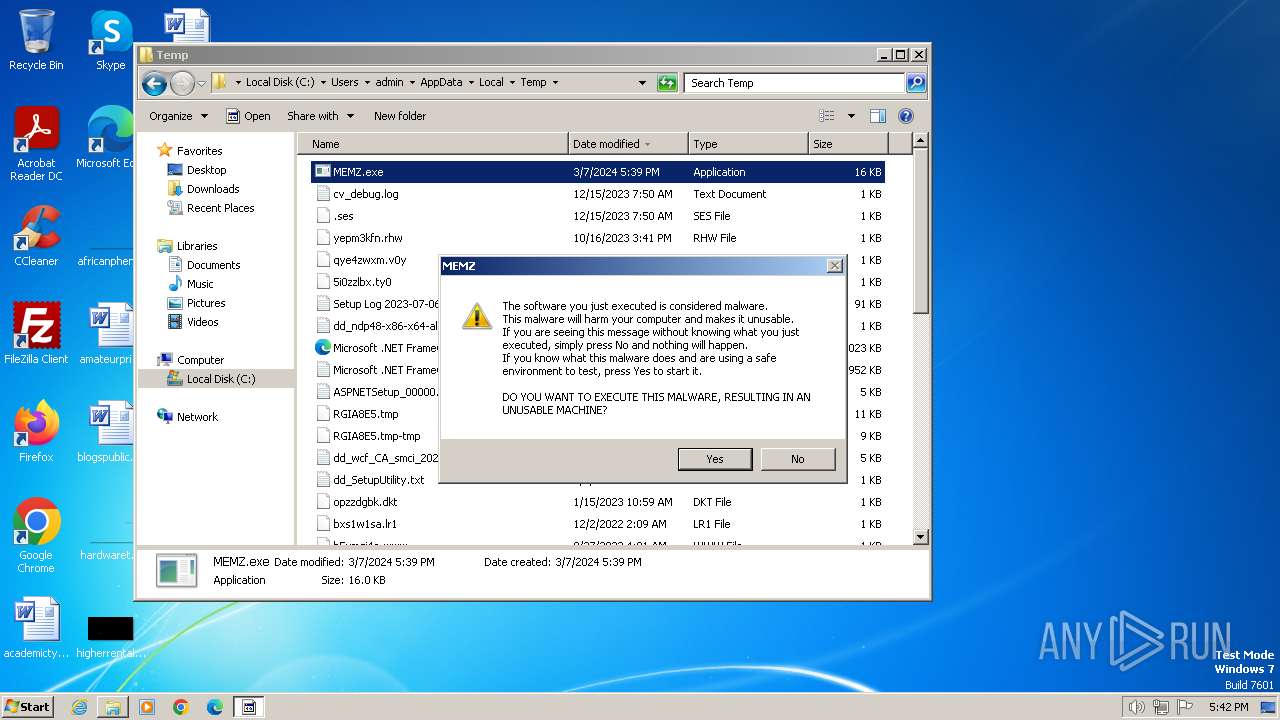
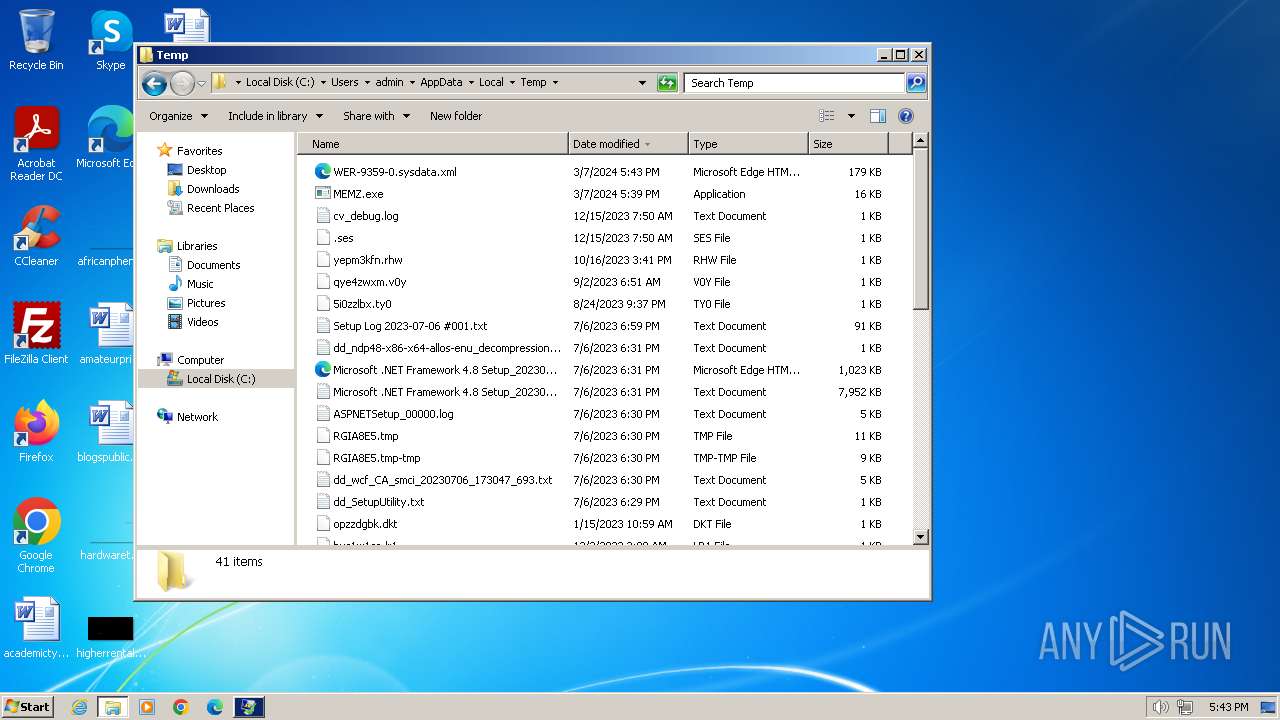
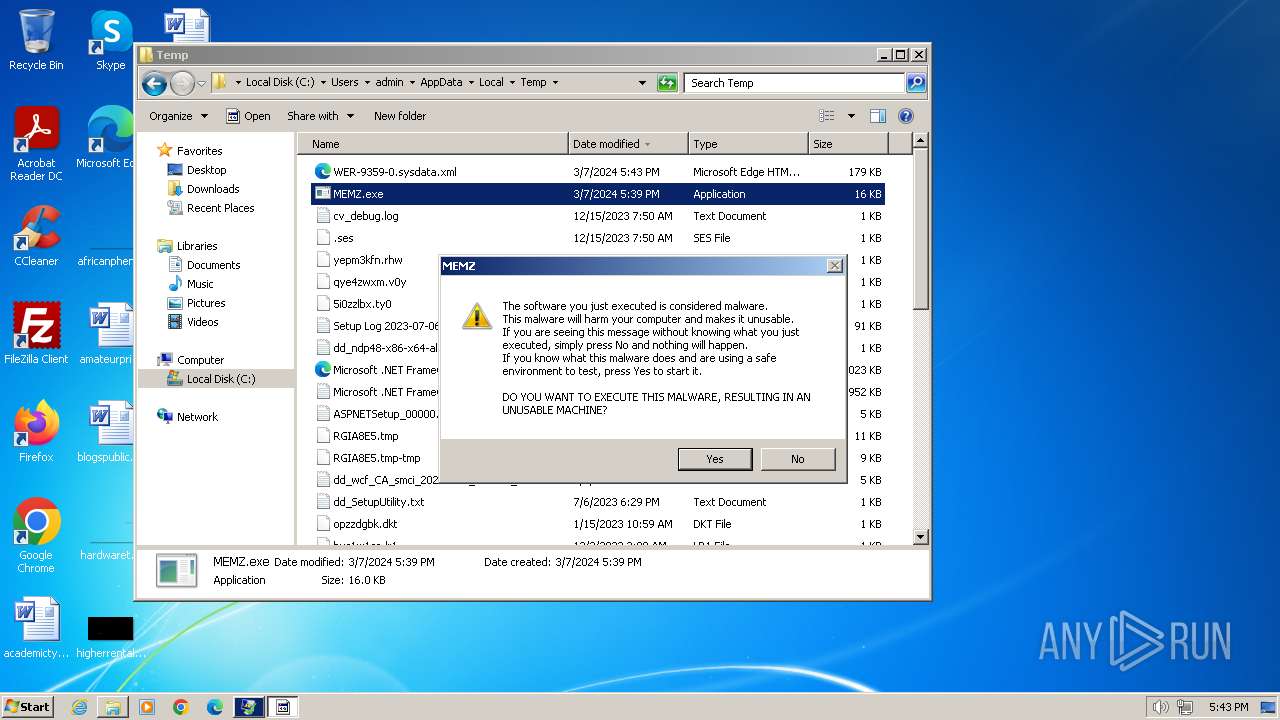
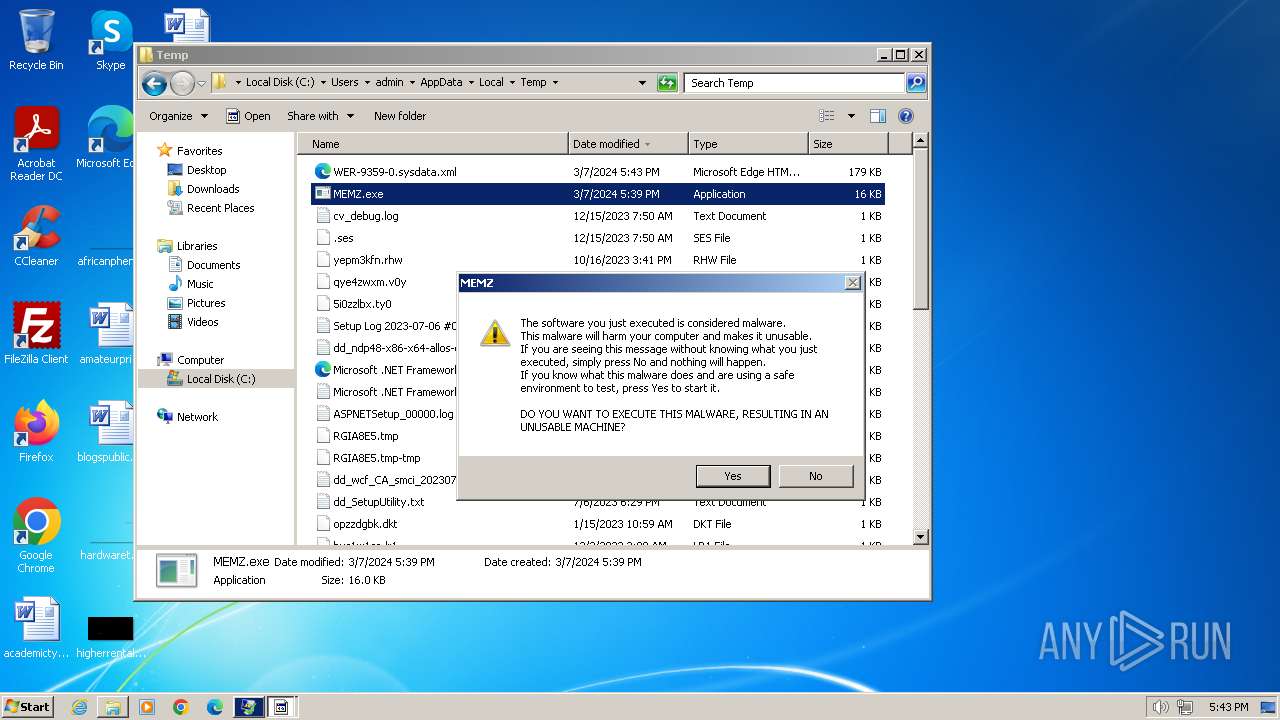
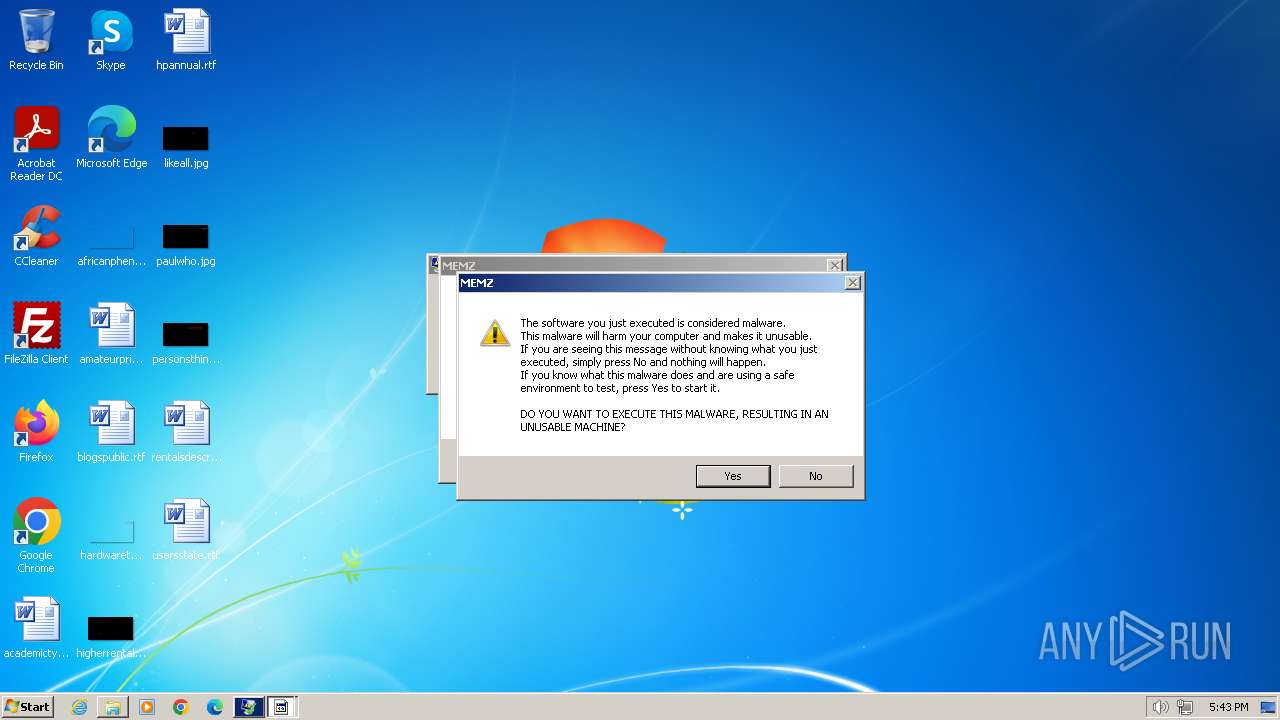
| File name: | MEMZ.exe |
| Full analysis: | https://app.any.run/tasks/b71871b1-389b-49ea-83d9-2db568ed0063 |
| Verdict: | Malicious activity |
| Analysis date: | March 07, 2024, 17:39:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1D5AD9C8D3FEE874D0FEB8BFAC220A11 |
| SHA1: | CA6D3F7E6C784155F664A9179CA64E4034DF9595 |
| SHA256: | 3872C12D31FC9825E8661AC01ECEE2572460677AFBC7093F920A8436A42E28FF |
| SSDEEP: | 192:M2WgyvSW8gRc6olcIEiwqZKBkDFR43xWTM3LHf26gFrcx3sNqa:JWgnSmFlcIqq3agmLH+6gF23sNj |
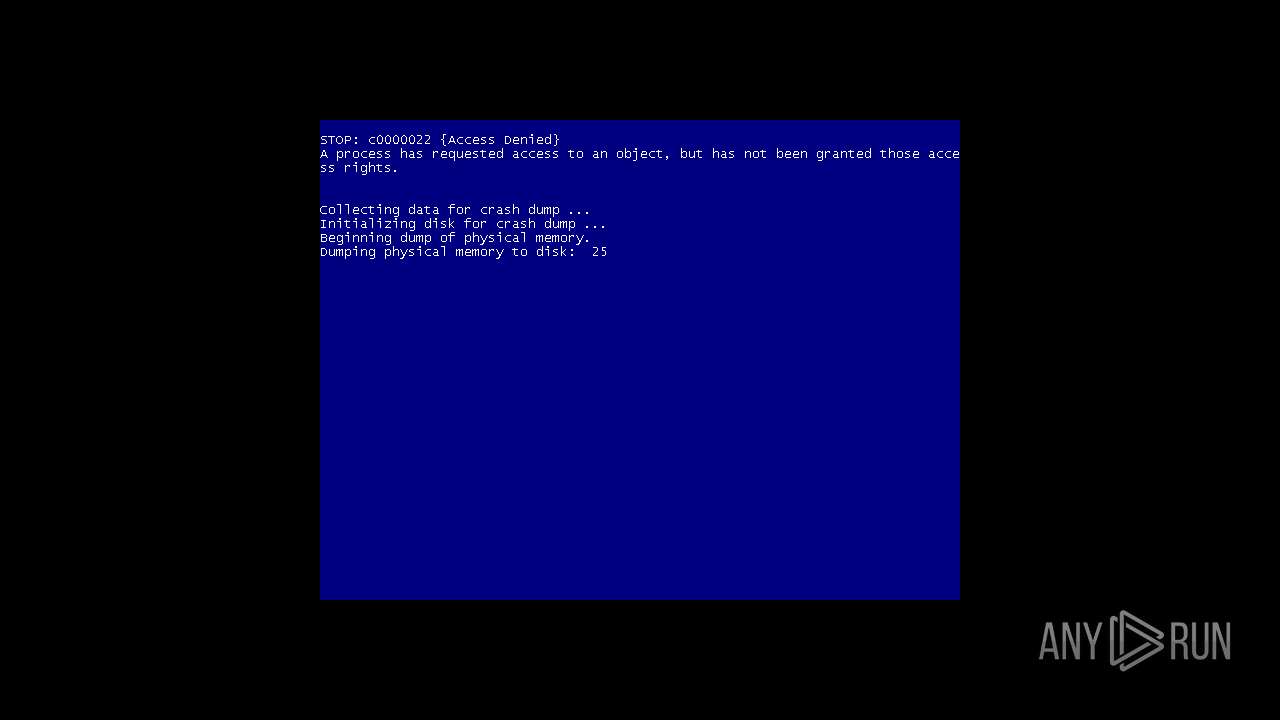
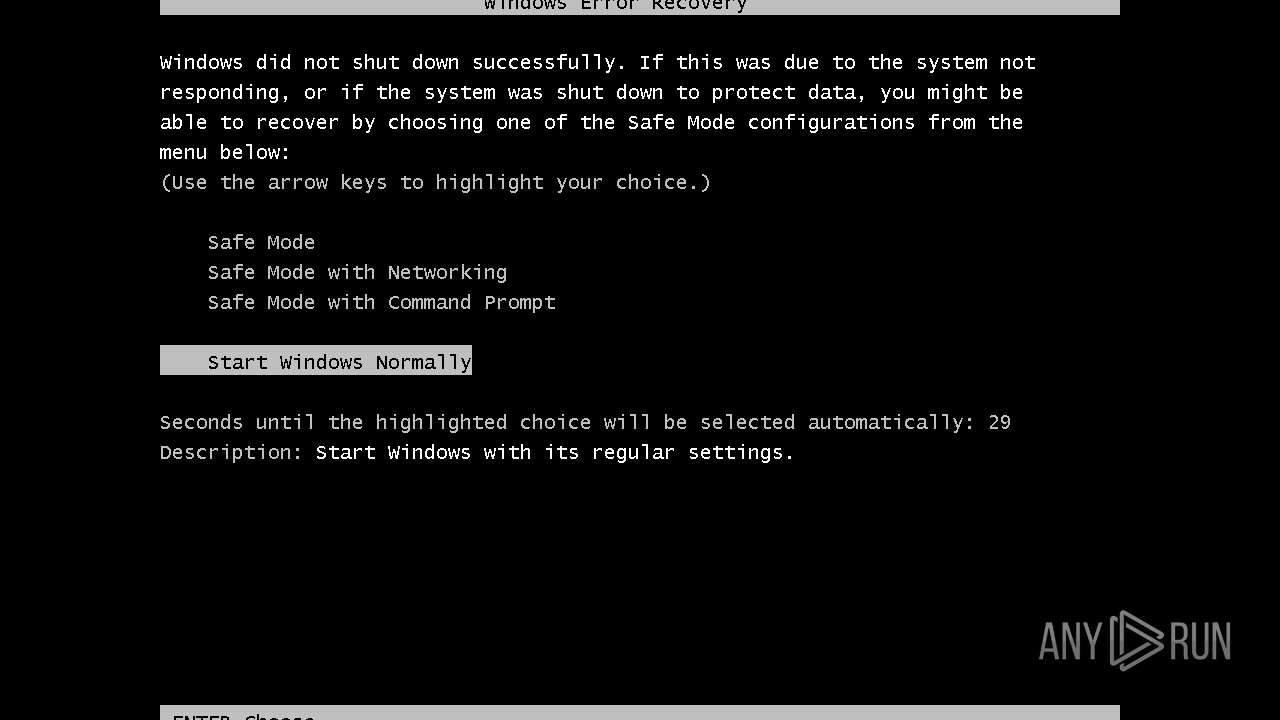
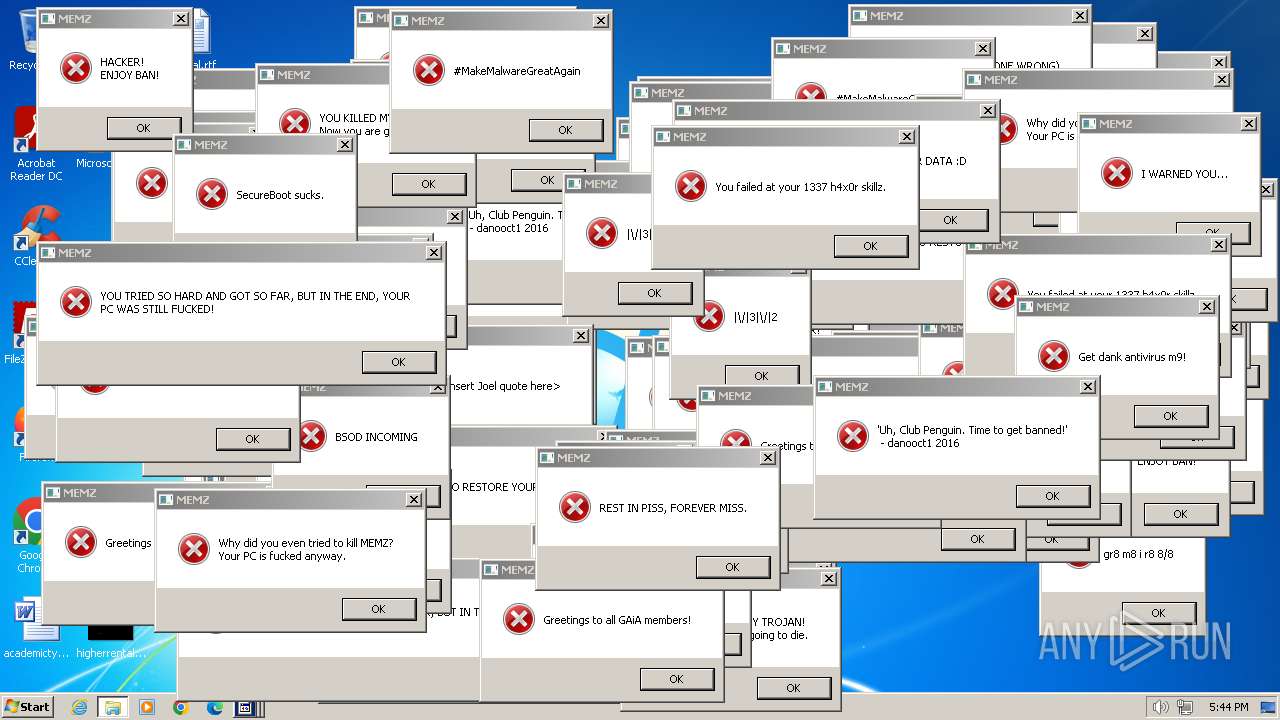
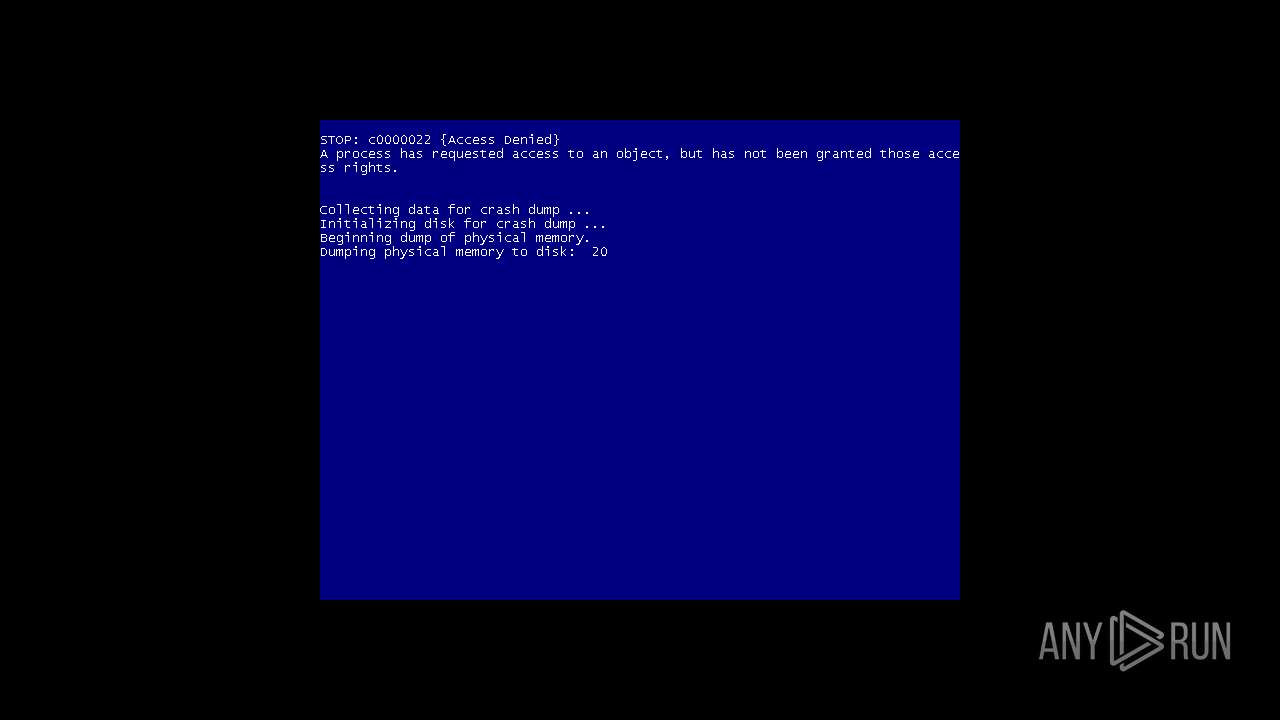
MALICIOUS
Drops the executable file immediately after the start
- MEMZ.exe (PID: 4052)
SUSPICIOUS
Reads security settings of Internet Explorer
- MEMZ.exe (PID: 4052)
- MEMZ.exe (PID: 3112)
- MEMZ.exe (PID: 3224)
- MEMZ.exe (PID: 3248)
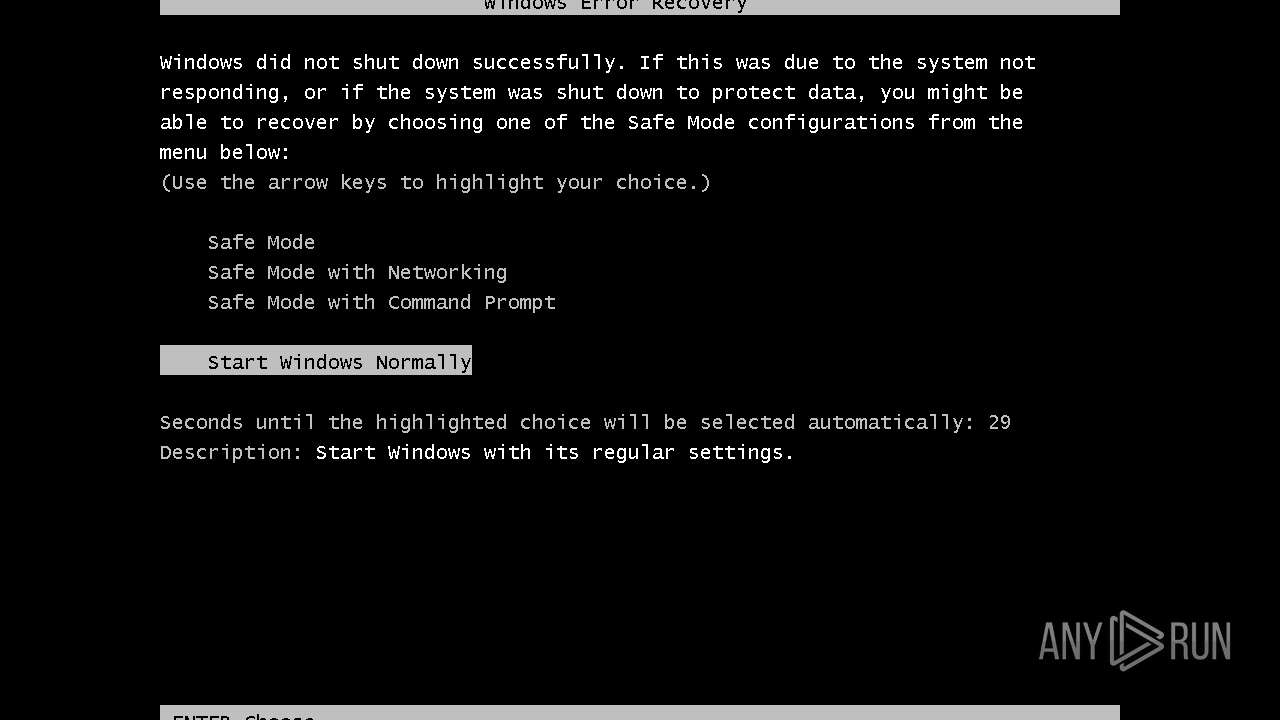
Application launched itself
- MEMZ.exe (PID: 4052)
- MEMZ.exe (PID: 3112)
- WerFault.exe (PID: 2076)
- MEMZ.exe (PID: 3224)
- MEMZ.exe (PID: 3248)
Reads the Internet Settings
- MEMZ.exe (PID: 4052)
- MEMZ.exe (PID: 3112)
- sipnotify.exe (PID: 2036)
- runonce.exe (PID: 340)
- MEMZ.exe (PID: 3224)
- MEMZ.exe (PID: 3248)
The process executes via Task Scheduler
- ctfmon.exe (PID: 2044)
- sipnotify.exe (PID: 2036)
Non-standard symbols in registry
- WerFault.exe (PID: 2084)
Reads settings of System Certificates
- sipnotify.exe (PID: 2036)
INFO
Checks supported languages
- MEMZ.exe (PID: 4052)
- MEMZ.exe (PID: 3720)
- MEMZ.exe (PID: 3708)
- MEMZ.exe (PID: 3660)
- MEMZ.exe (PID: 2044)
- MEMZ.exe (PID: 3972)
- MEMZ.exe (PID: 3736)
- wmpnscfg.exe (PID: 2752)
- MEMZ.exe (PID: 3112)
- MEMZ.exe (PID: 268)
- MEMZ.exe (PID: 752)
- MEMZ.exe (PID: 572)
- MEMZ.exe (PID: 2736)
- MEMZ.exe (PID: 2028)
- MEMZ.exe (PID: 4084)
- IMEKLMG.EXE (PID: 2180)
- IMEKLMG.EXE (PID: 2192)
- wmpnscfg.exe (PID: 2580)
- wmpnscfg.exe (PID: 2600)
- wmpnscfg.exe (PID: 2800)
- MEMZ.exe (PID: 3224)
- MEMZ.exe (PID: 3248)
- MEMZ.exe (PID: 3348)
- MEMZ.exe (PID: 3372)
- MEMZ.exe (PID: 3388)
- MEMZ.exe (PID: 3428)
- MEMZ.exe (PID: 3452)
- MEMZ.exe (PID: 3464)
- MEMZ.exe (PID: 3324)
- MEMZ.exe (PID: 3336)
- MEMZ.exe (PID: 3360)
- MEMZ.exe (PID: 3416)
- MEMZ.exe (PID: 3440)
- MEMZ.exe (PID: 3480)
Reads the computer name
- MEMZ.exe (PID: 4052)
- wmpnscfg.exe (PID: 2752)
- MEMZ.exe (PID: 3112)
- IMEKLMG.EXE (PID: 2192)
- IMEKLMG.EXE (PID: 2180)
- wmpnscfg.exe (PID: 2580)
- wmpnscfg.exe (PID: 2600)
- wmpnscfg.exe (PID: 2800)
- MEMZ.exe (PID: 3248)
- MEMZ.exe (PID: 3224)
Manual execution by a user
- wmpnscfg.exe (PID: 2752)
- MEMZ.exe (PID: 3112)
- explorer.exe (PID: 3488)
- explorer.exe (PID: 2408)
- runonce.exe (PID: 340)
- IMEKLMG.EXE (PID: 2180)
- IMEKLMG.EXE (PID: 2192)
- wmpnscfg.exe (PID: 2600)
- wmpnscfg.exe (PID: 2800)
- MEMZ.exe (PID: 3248)
- wmpnscfg.exe (PID: 2580)
- MEMZ.exe (PID: 3224)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 3736)
- MEMZ.exe (PID: 3720)
- MEMZ.exe (PID: 3972)
- MEMZ.exe (PID: 2044)
- MEMZ.exe (PID: 3708)
- MEMZ.exe (PID: 3336)
- MEMZ.exe (PID: 3360)
- MEMZ.exe (PID: 3324)
- MEMZ.exe (PID: 3348)
- MEMZ.exe (PID: 3372)
Create files in a temporary directory
- WerFault.exe (PID: 2084)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2192)
- IMEKLMG.EXE (PID: 2180)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 2036)
- runonce.exe (PID: 340)
Reads the software policy settings
- sipnotify.exe (PID: 2036)
Reads the time zone
- runonce.exe (PID: 340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:03:19 03:33:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 3584 |
| InitializedDataSize: | 11776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x122d |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
122
Monitored processes
41
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\AppData\Local\Temp\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 340 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | "C:\Users\admin\AppData\Local\Temp\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 752 | "C:\Users\admin\AppData\Local\Temp\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2028 | "C:\Users\admin\AppData\Local\Temp\MEMZ.exe" /main | C:\Users\admin\AppData\Local\Temp\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 2036 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\AppData\Local\Temp\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2044 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2076 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2084 | C:\Windows\System32\WerFault.exe -k -q | C:\Windows\System32\WerFault.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
18 736
Read events
18 493
Write events
224
Delete events
19
Modification events
| (PID) Process: | (4052) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4052) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4052) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4052) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3112) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3112) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3112) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3112) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2044) ctfmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | internat.exe |
Value: | |||
| (PID) Process: | (340) runonce.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | *WerKernelReporting |
Value: %SYSTEMROOT%\SYSTEM32\WerFault.exe -k -rq | |||
Executable files
0
Suspicious files
3
Text files
6
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2084 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\Kernel_0_0_cab_0824c301\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2036 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
| 2036 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\en-us.html | html | |
MD5:9752942B57692148B9F614CF4C119A36 | SHA256:E31B834DD53FA6815F396FC09C726636ABF98F3367F0CF1590EF5EB3801C75D1 | |||
| 2036 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\main.jpg | image | |
MD5:B342ACE63F77961249A084C61EABC884 | SHA256:E5067BBA2095B5DA7C3171EC116E9A92337E24E471339B0860A160076EFE49B9 | |||
| 2036 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\microsoft-logo.png | image | |
MD5:B7C73A0CFBA68CC70C35EF9C63703CE4 | SHA256:1D8B27A0266FF526CF95447F3701592A908848467D37C09A00A2516C1F29A013 | |||
| 2036 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:E8A970BA6CE386EED9A5E724F26212A6 | SHA256:7E06107D585D8FC7870998F3856DCC3E35800AA97E4406AAB83BC8444B6CBDE3 | |||
| 2036 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
| 2084 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERC269.tmp.cab.tmp | binary | |
MD5:9A4BA7C3D8C5883CCC9AC8BAAF0EA69C | SHA256:4839C88A3D8E2D25A2ACFAAEFAB1EA720D9BA30146A8B86588AB3A6570520A4F | |||
| 2084 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERC267.tmp.cab.tmp | binary | |
MD5:9A4BA7C3D8C5883CCC9AC8BAAF0EA69C | SHA256:4839C88A3D8E2D25A2ACFAAEFAB1EA720D9BA30146A8B86588AB3A6570520A4F | |||
| 2084 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER-9359-0.sysdata.xml | xml | |
MD5:B7E38B5A83FC38998EEA25968B42554E | SHA256:5CB3B571D015C8DF84D1842C2D5E5F872829FBEF998EE36BC67C4A38342B95DF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2036 | sipnotify.exe | HEAD | 200 | 2.23.65.216:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133543069887340000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1132 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2036 | sipnotify.exe | 2.23.65.216:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |