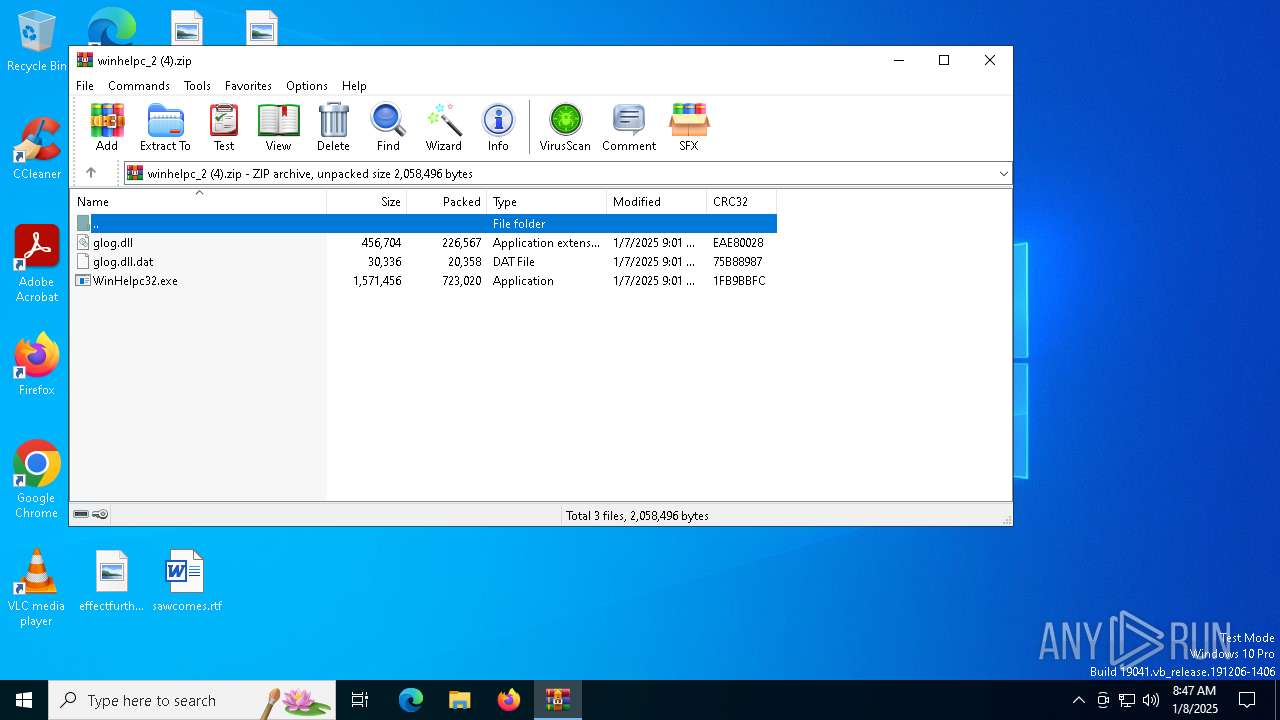
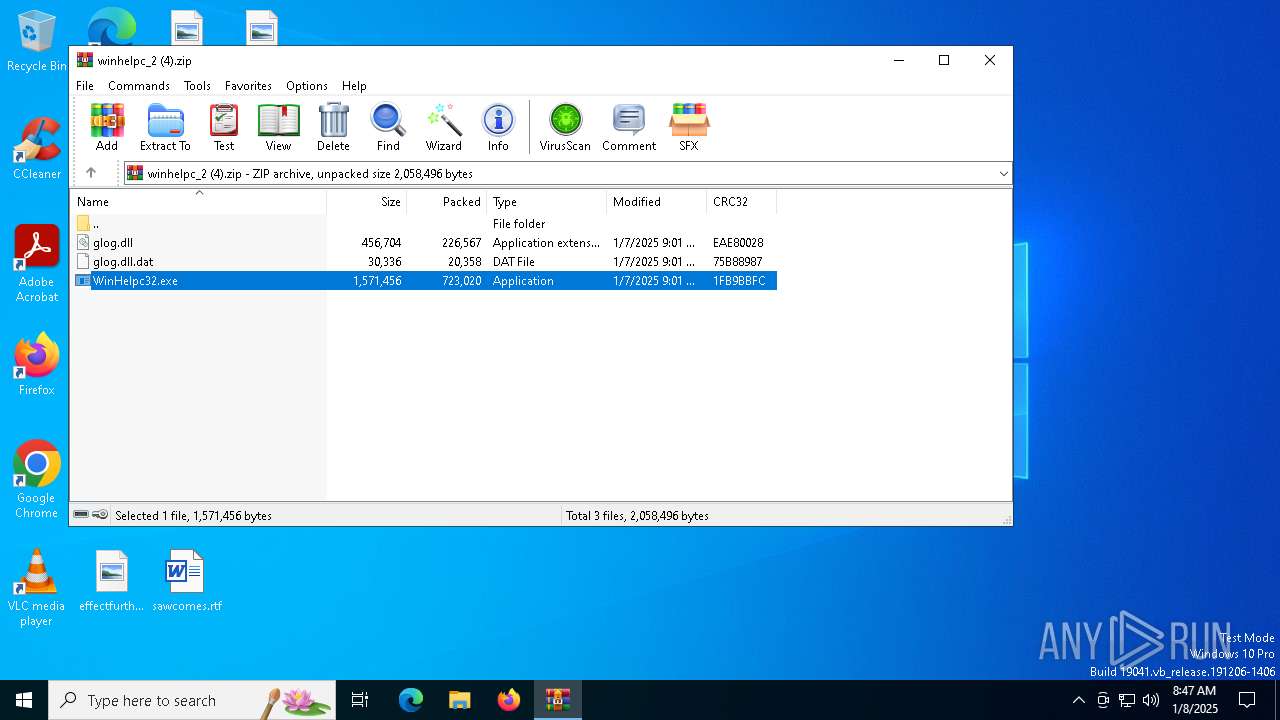
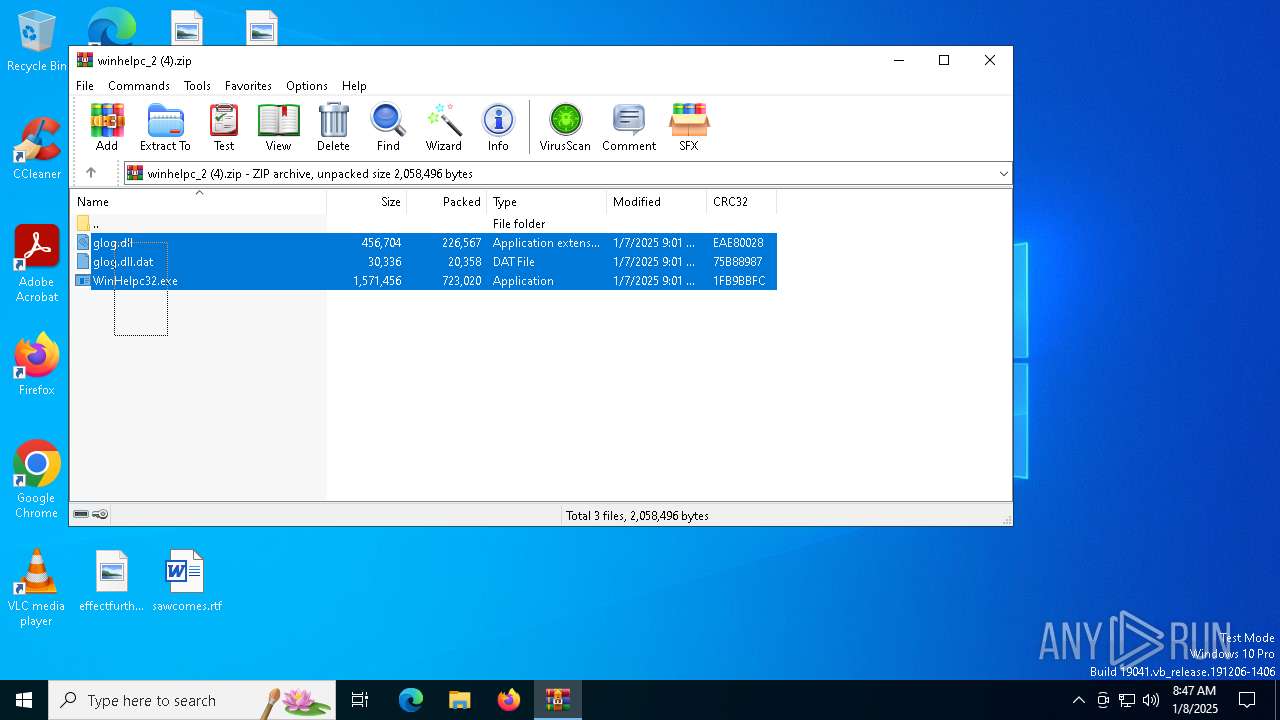
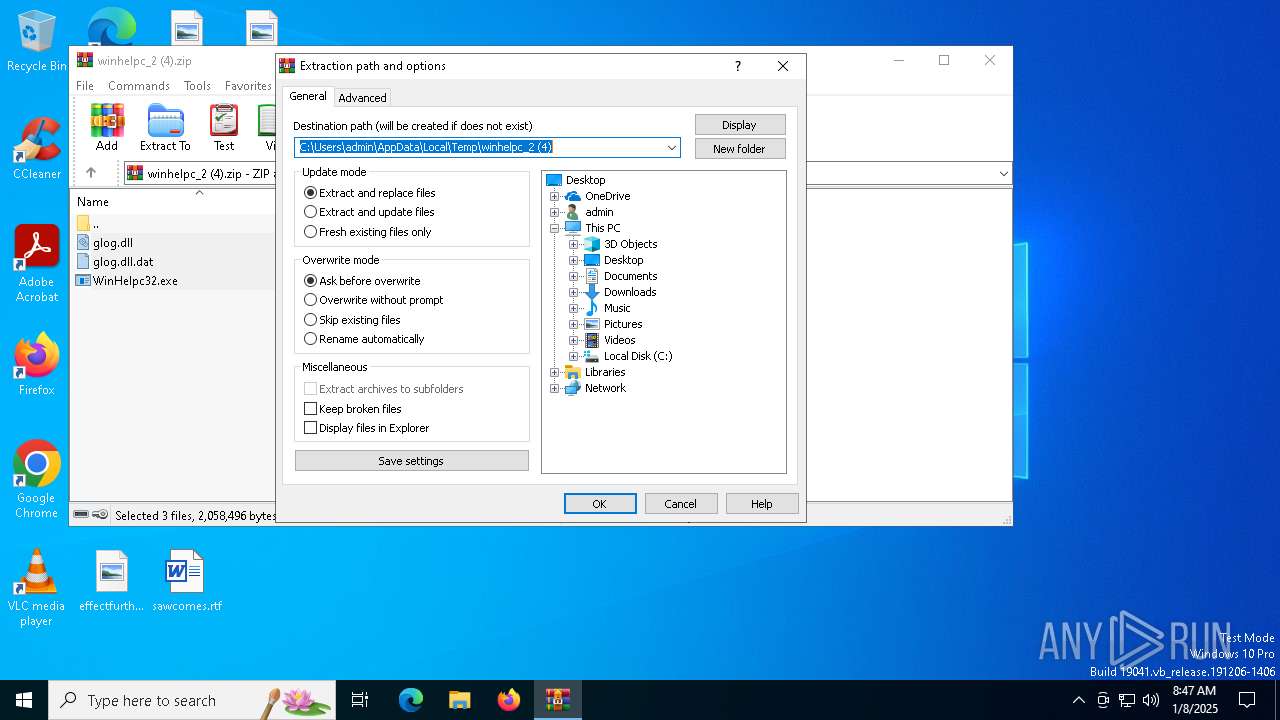
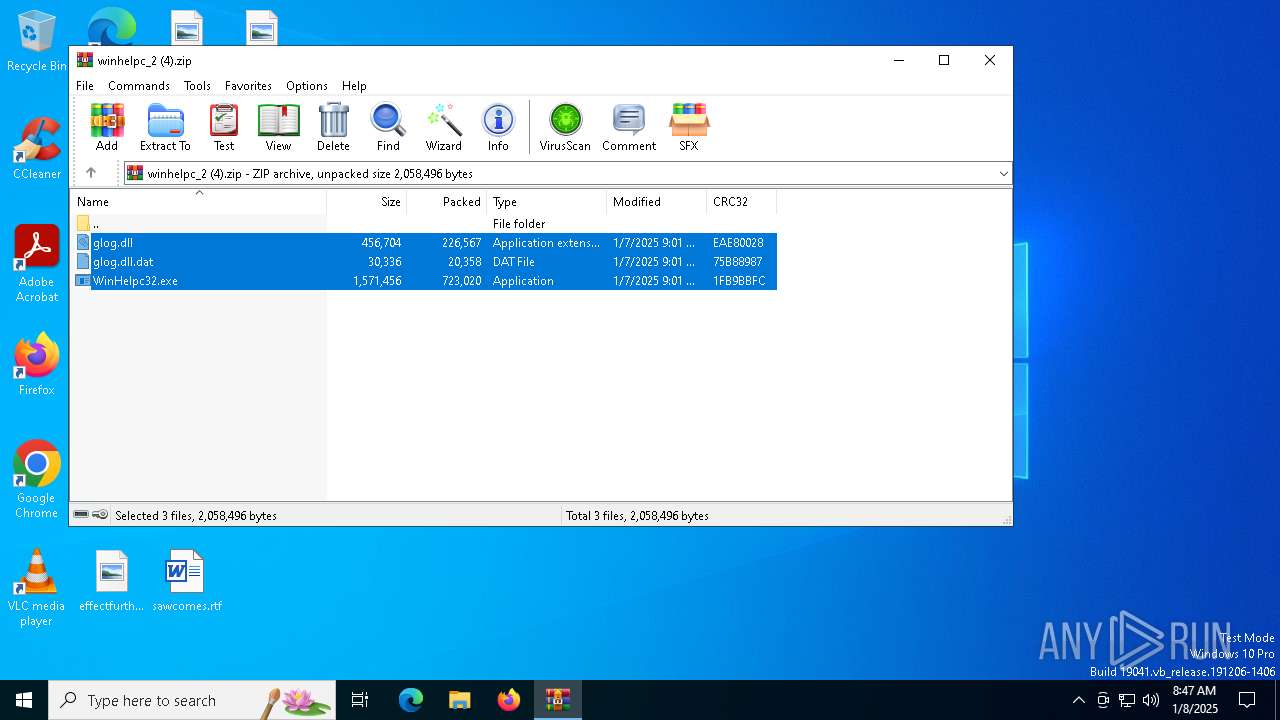
| File name: | winhelpc_2 (4).zip |
| Full analysis: | https://app.any.run/tasks/d5eb6f76-eb4e-440c-bbd0-53a9520f3a35 |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2025, 08:47:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F53359E64CE69CDC6B28DF5AEBF0A508 |
| SHA1: | CAC0E1B1FE7F04685FF0B2C3DA7D39076E90CBE6 |
| SHA256: | 384A218C3695C58242AE98637295E3D18DFD77CFE6B1A466FA2D287949D17573 |
| SSDEEP: | 49152:fEAuMxPAsYdfQxxxi/vJRA3gfkKLwb58W0VX7mTeIsCehRqEeVq1gCHsuJEgXZOU:fbHxPHYdQ1i/vk3WbLA5/0VXYsRpeVq9 |
MALICIOUS
Adds path to the Windows Defender exclusion list
- WinHelpc32.exe (PID: 6868)
- WinHelpc32.exe (PID: 6272)
- WinHelpc32.exe (PID: 4724)
Known privilege escalation attack
- dllhost.exe (PID: 3608)
SUSPICIOUS
Script adds exclusion path to Windows Defender
- WinHelpc32.exe (PID: 6868)
- WinHelpc32.exe (PID: 4724)
- WinHelpc32.exe (PID: 6272)
Starts POWERSHELL.EXE for commands execution
- WinHelpc32.exe (PID: 6868)
- WinHelpc32.exe (PID: 6272)
- WinHelpc32.exe (PID: 4724)
Executable content was dropped or overwritten
- WinHelpc32.exe (PID: 6272)
Executes as Windows Service
- WinHelpc32.exe (PID: 4724)
Connects to unusual port
- svchost.exe (PID: 4520)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6380)
The sample compiled with chinese language support
- WinRAR.exe (PID: 6380)
- WinHelpc32.exe (PID: 6272)
Manual execution by a user
- WinHelpc32.exe (PID: 6868)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6888)
- powershell.exe (PID: 3092)
- powershell.exe (PID: 1512)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6888)
- powershell.exe (PID: 3092)
- powershell.exe (PID: 1512)
Reads the machine GUID from the registry
- WinHelpc32.exe (PID: 6868)
The sample compiled with english language support
- WinRAR.exe (PID: 6380)
- WinHelpc32.exe (PID: 6272)
The process uses the downloaded file
- WinRAR.exe (PID: 6380)
- powershell.exe (PID: 6888)
- dllhost.exe (PID: 3608)
- powershell.exe (PID: 3092)
- powershell.exe (PID: 1512)
Checks supported languages
- WinHelpc32.exe (PID: 6868)
- WinHelpc32.exe (PID: 6272)
- WinHelpc32.exe (PID: 4724)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 3608)
Reads the computer name
- WinHelpc32.exe (PID: 6868)
- WinHelpc32.exe (PID: 6272)
UPX packer has been detected
- WinHelpc32.exe (PID: 6272)
- svchost.exe (PID: 4520)
- dllhost.exe (PID: 4592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:07 12:01:36 |
| ZipCRC: | 0xeae80028 |
| ZipCompressedSize: | 226567 |
| ZipUncompressedSize: | 456704 |
| ZipFileName: | glog.dll |
Total processes
140
Monitored processes
13
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1512 | powershell.exe -Command "Add-Mppreference -ExclusionPath 'C:\Program Files (x86)', 'C:\' -Force" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | WinHelpc32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2828 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3092 | powershell.exe -Command "Add-Mppreference -ExclusionPath 'C:\Program Files (x86)', 'C:\' -Force" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | WinHelpc32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4520 | C:\WINDOWS\SysWOW64\svchost.exe -k netsvcs | C:\Windows\SysWOW64\svchost.exe | WinHelpc32.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4592 | C:\WINDOWS\SysWOW64\dllhost.exe -ks | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\WinHelpc32.exe -svc | C:\Windows\WinHelpc32.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Guangzhou Shirui Electronics Integrity Level: SYSTEM Description: EasiAgent Exit code: 0 Version: 0.0.1.134- (0c185a7) Modules
| |||||||||||||||
| 6252 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | "C:\Users\admin\Desktop\WinHelpc32.exe" -Install | C:\Users\admin\Desktop\WinHelpc32.exe | dllhost.exe | ||||||||||||
User: admin Company: Guangzhou Shirui Electronics Integrity Level: HIGH Description: EasiAgent Exit code: 0 Version: 0.0.1.134- (0c185a7) Modules
| |||||||||||||||
| 6380 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\winhelpc_2 (4).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
18 302
Read events
18 278
Write events
11
Delete events
13
Modification events
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\winhelpc_2 (4).zip | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
6
Suspicious files
5
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gml2v0q1.0wt.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_g0yhr4qi.02d.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_c2ep5ft4.rab.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ndlxoz1n.3nc.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xvzwhum1.z3i.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6380 | WinRAR.exe | C:\Users\admin\Desktop\WinHelpc32.exe | executable | |
MD5:4DF31CD1A0EDE3A4D35E720C81F8F970 | SHA256:B5B2D5F9800ECF5A4D542C3B3C0812D2FB0F6FFE4333424797D2DBC13EF7739A | |||
| 6380 | WinRAR.exe | C:\Users\admin\Desktop\glog.dll.dat | binary | |
MD5:57D67E031DBBBB5B246CED1B67B1B78E | SHA256:00F7DE081E270C8703EDB63D46B9DF2AC58C693D96F14C0D7872C889A1623481 | |||
| 6380 | WinRAR.exe | C:\Users\admin\Desktop\glog.dll | executable | |
MD5:C6DA87C29D5A9898423569362D23A3B9 | SHA256:D3E40FCAC762A36AEE12F2369132D1246BF967CC17585F21BC632875B14DC3AD | |||
| 6888 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:DA68FCDE3836F9167AAD3019F8C87E66 | SHA256:EEB8BBC0BCF3781DD0658AFFA90EFE4A3C56BD7701EAFD591066B744915B0084 | |||
| 1512 | powershell.exe | C:\Windows\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:F635E297DE14F37227C9A3926C7A9917 | SHA256:26D2601B5C6E3CEE93F2BC6313794899D8734A0D57C34C83F66748F8A7536C58 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
42
DNS requests
18
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4536 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3976 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4520 | svchost.exe | 8.217.47.21:63115 | — | Alibaba US Technology Co., Ltd. | HK | unknown |
4824 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4824 | SIHClient.exe | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
dns.msftncsi.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
206.23.85.13.in-addr.arpa |
| unknown |
d.3.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.8.0.4.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
login.live.com |
| whitelisted |