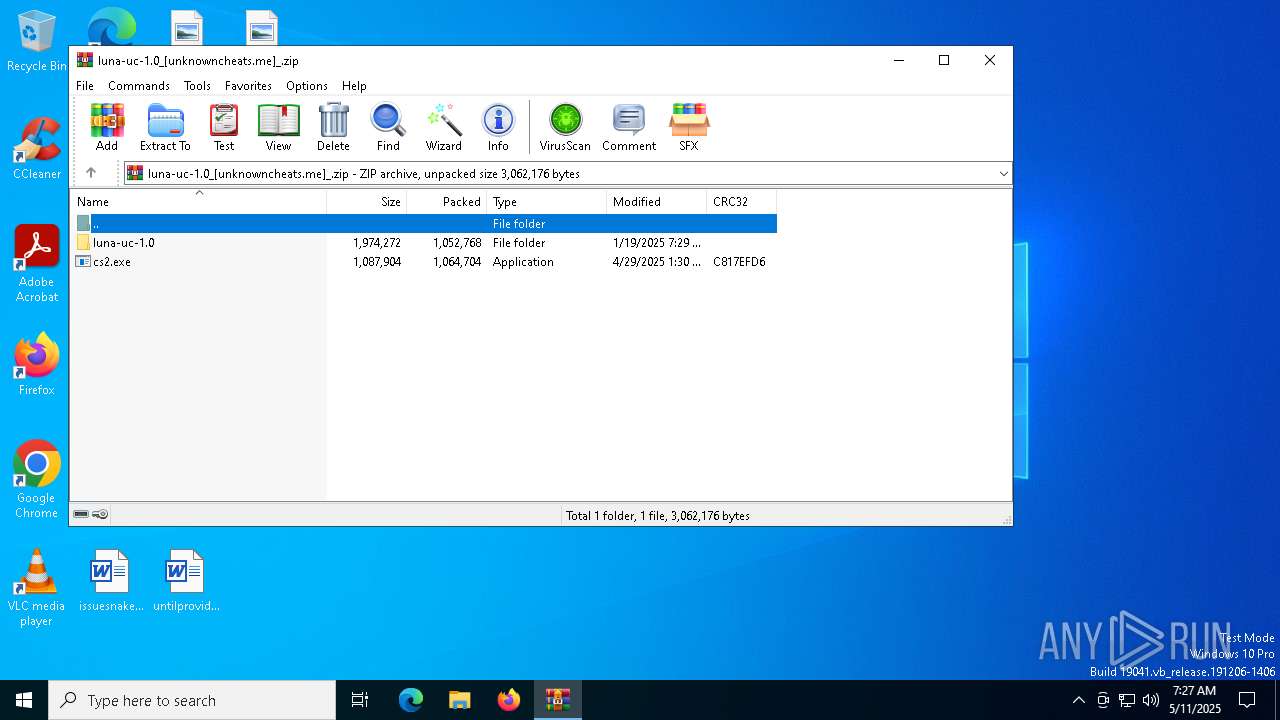
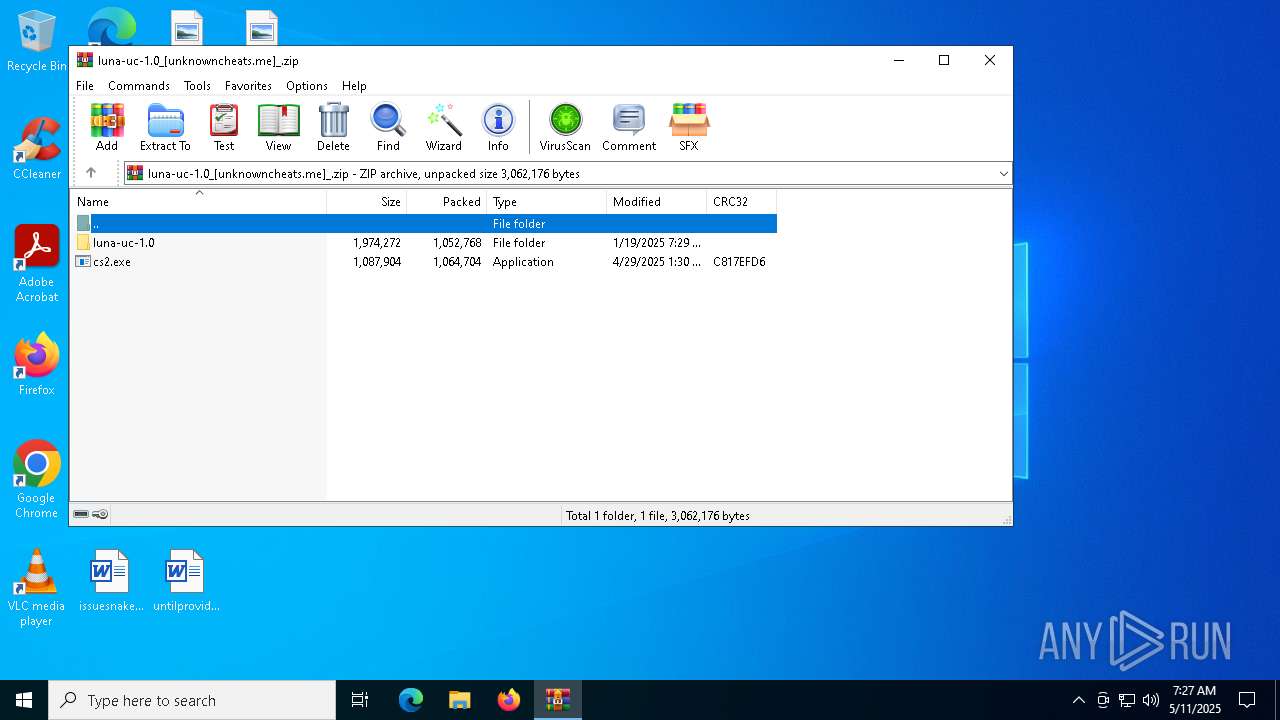
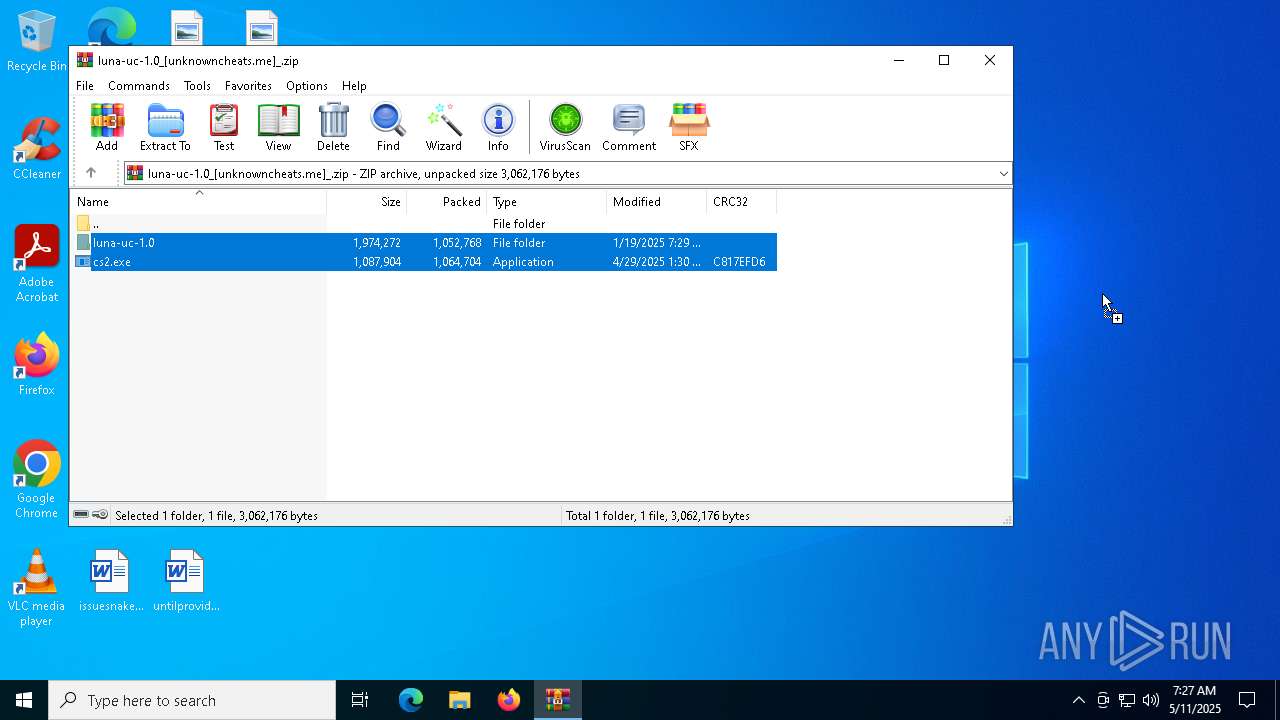
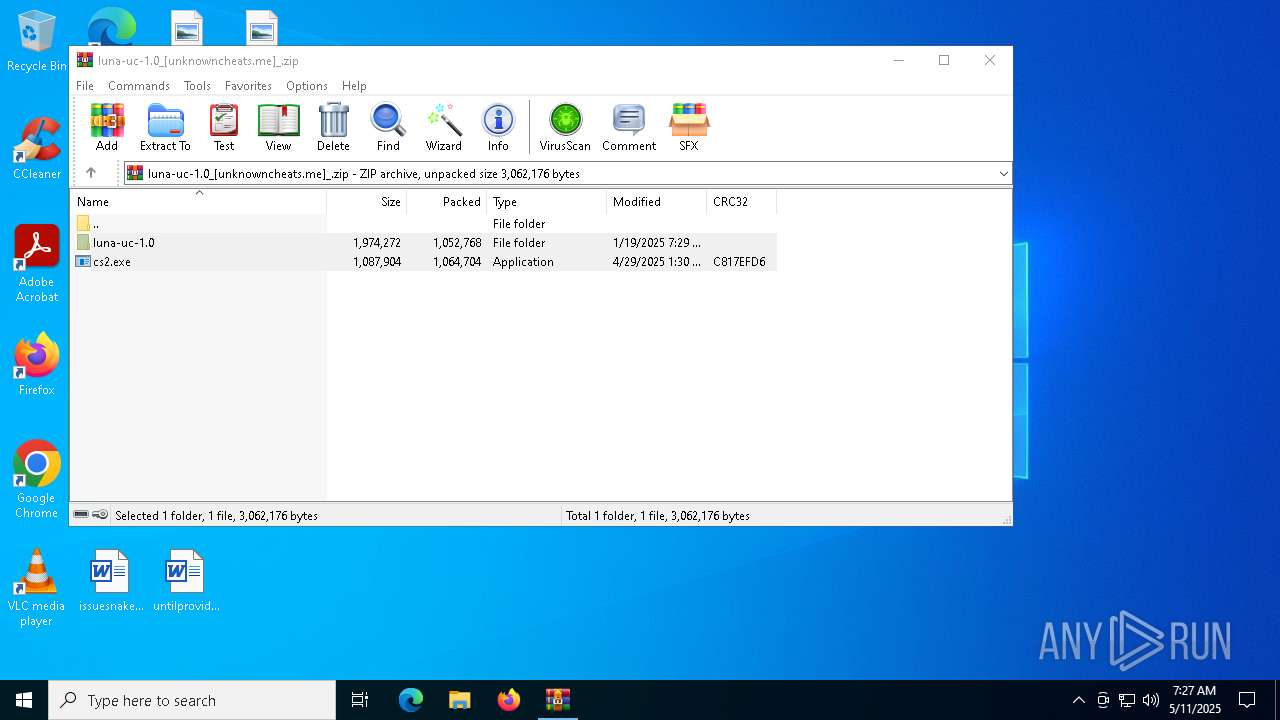
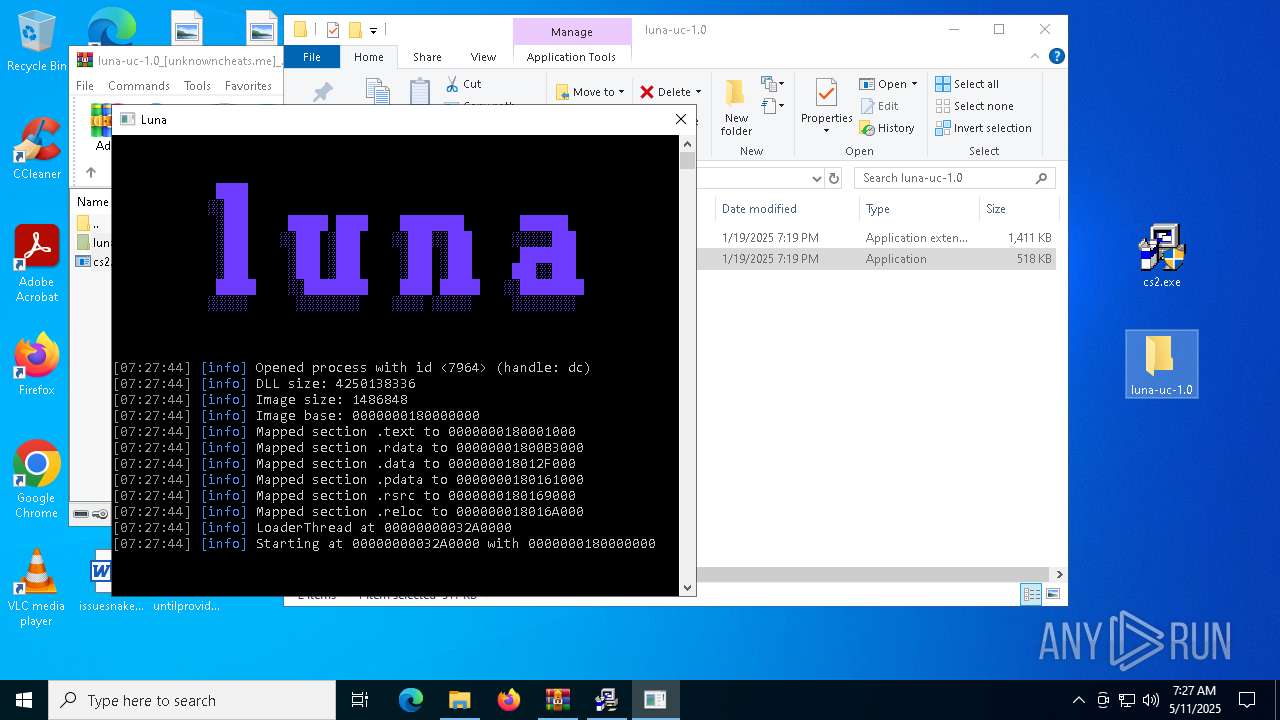
| File name: | luna-uc-1.0_[unknowncheats.me]_.zip |
| Full analysis: | https://app.any.run/tasks/e96421c5-abe4-4a07-871e-0acd3ae8419f |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 07:26:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 8CEFC365038948CFAA27E659844A299C |
| SHA1: | CE2712DBA0B5DC4519901644D3AFB943B44C5FDC |
| SHA256: | 3847020E6E3497E24624B903639F43B964D98E6979E17207307055478E0F6F6B |
| SSDEEP: | 98304:SS/o5rvDHrw2YzmwANS+6Um8jpRh4gochiS8O2yFphJmm0bVgD7Q0bJKQWZxvczb:pbe |
MALICIOUS
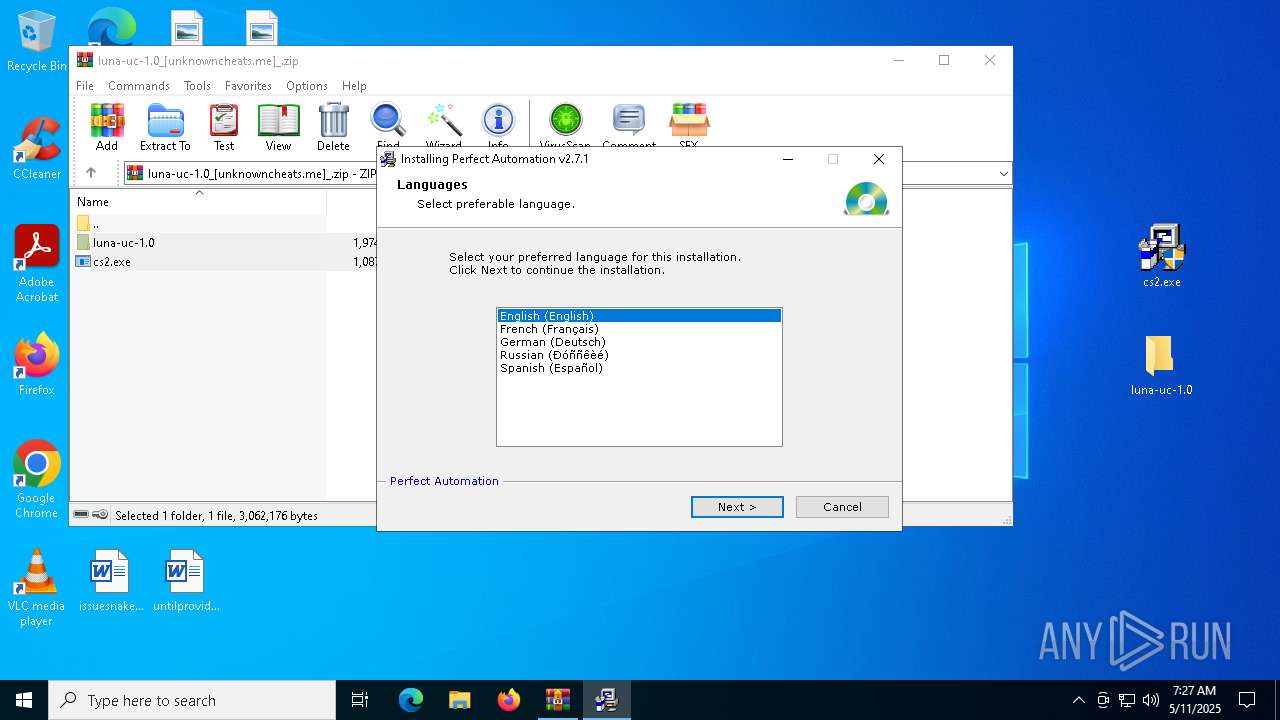
Executing a file with an untrusted certificate
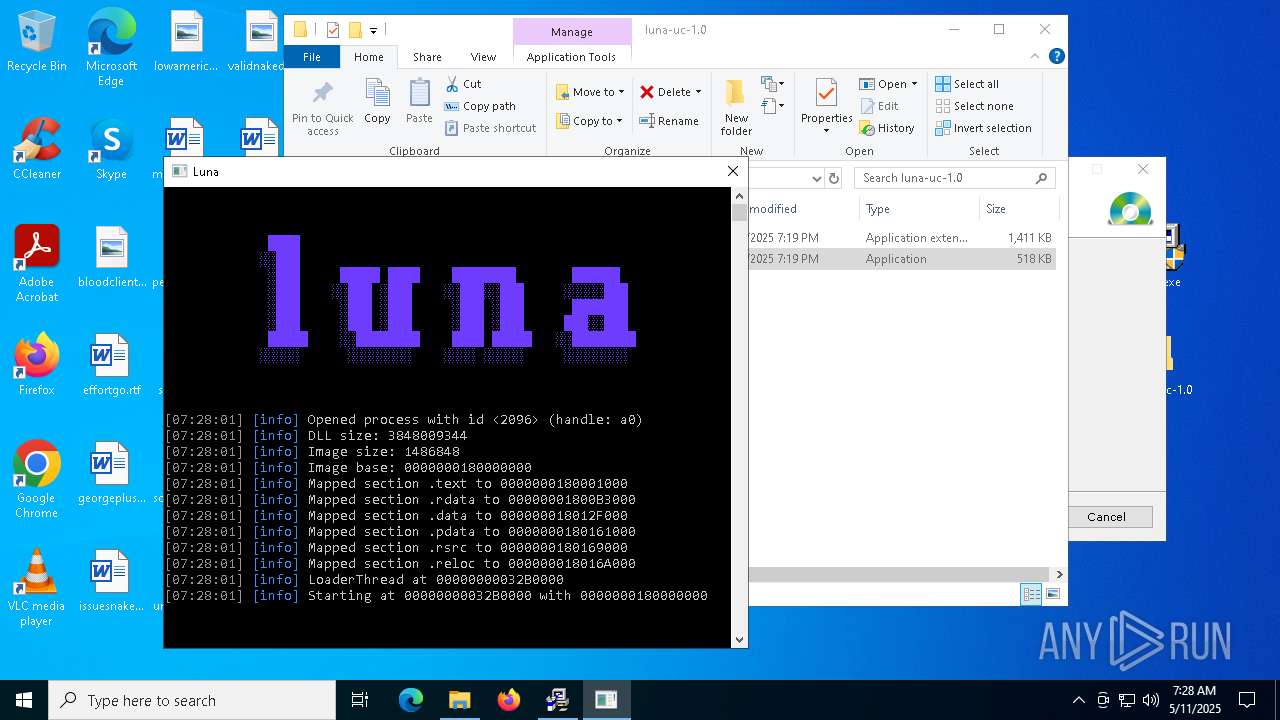
- cs2.exe (PID: 7964)
- cs2.exe (PID: 7916)
- cs2.exe (PID: 2096)
- cs2.exe (PID: 3268)
Generic archive extractor
- WinRAR.exe (PID: 6724)
SUSPICIOUS
Executable content was dropped or overwritten
- cs2.exe (PID: 7964)
- cs2.exe (PID: 2096)
Executes application which crashes
- cs2.exe (PID: 7964)
- cs2.exe (PID: 2096)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6724)
- cs2.exe (PID: 7964)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6724)
Checks supported languages
- cs2.exe (PID: 7964)
- luna.exe (PID: 8132)
- luna.exe (PID: 6112)
- cs2.exe (PID: 2096)
- luna.exe (PID: 7520)
Manual execution by a user
- cs2.exe (PID: 7916)
- cs2.exe (PID: 7964)
- luna.exe (PID: 8084)
- luna.exe (PID: 6112)
- luna.exe (PID: 6300)
- luna.exe (PID: 8132)
- cs2.exe (PID: 2096)
- cs2.exe (PID: 3268)
- luna.exe (PID: 7240)
- luna.exe (PID: 7520)
Create files in a temporary directory
- cs2.exe (PID: 7964)
- cs2.exe (PID: 2096)
Reads the computer name
- cs2.exe (PID: 7964)
- cs2.exe (PID: 2096)
Creates files or folders in the user directory
- WerFault.exe (PID: 4996)
- WerFault.exe (PID: 7376)
Reads the software policy settings
- slui.exe (PID: 7264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:19 20:29:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | luna-uc-1.0/ |
Total processes
156
Monitored processes
20
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | luna.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | "C:\Users\admin\Desktop\cs2.exe" | C:\Users\admin\Desktop\cs2.exe | explorer.exe | ||||||||||||
User: admin Company: Gentee, Inc. Integrity Level: HIGH Description: pautomation Setup Exit code: 3221225477 Version: 2.7.1 Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\Desktop\cs2.exe" | C:\Users\admin\Desktop\cs2.exe | — | explorer.exe | |||||||||||
User: admin Company: Gentee, Inc. Integrity Level: MEDIUM Description: pautomation Setup Exit code: 3221226540 Version: 2.7.1 Modules
| |||||||||||||||
| 4996 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7964 -s 1088 | C:\Windows\SysWOW64\WerFault.exe | — | cs2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | luna.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6112 | "C:\Users\admin\Desktop\luna-uc-1.0\luna.exe" | C:\Users\admin\Desktop\luna-uc-1.0\luna.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6300 | "C:\Users\admin\Desktop\luna-uc-1.0\luna.exe" | C:\Users\admin\Desktop\luna-uc-1.0\luna.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6724 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\luna-uc-1.0_[unknowncheats.me]_.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7216 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7240 | "C:\Users\admin\Desktop\luna-uc-1.0\luna.exe" | C:\Users\admin\Desktop\luna-uc-1.0\luna.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
6 208
Read events
6 178
Write events
24
Delete events
6
Modification events
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\luna-uc-1.0_[unknowncheats.me]_.zip | |||
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4996) WerFault.exe | Key: | \REGISTRY\A\{8fd2aa79-ca54-340d-f49b-155649e3e511}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (4996) WerFault.exe | Key: | \REGISTRY\A\{8fd2aa79-ca54-340d-f49b-155649e3e511}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
6
Suspicious files
10
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4996 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cs2.exe_2391509e58be89abcba8cbdca66ae46075a45329_7c33a770_865624f9-1764-4dc3-b285-c0160efd25d3\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7376 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cs2.exe_ea385912c2328c4d4d50c16dc78a295777b93881_7c33a770_f454dd6d-200e-4604-9303-2e1151465c82\Report.wer | — | |
MD5:— | SHA256:— | |||
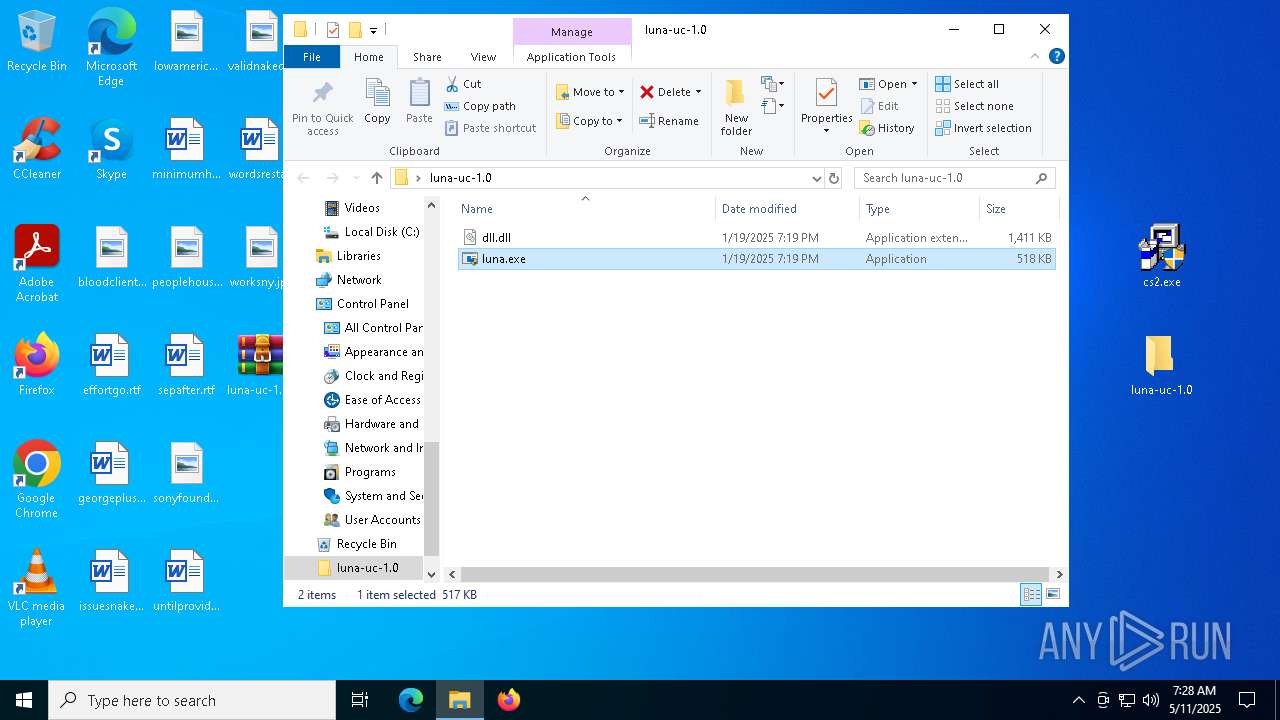
| 6724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6724.25921\luna-uc-1.0\luna.exe | executable | |
MD5:68E63604EE559B588891F90BD6B53159 | SHA256:A271BF3E6EAA1704DE4E829246CE3E8D12EDDD0F8D26B664F3F6235AE07CBA89 | |||
| 6724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6724.25921\luna-uc-1.0\dll.dll | executable | |
MD5:55E171A0CC60C70967B671A7C0394539 | SHA256:900E13A2D49EA541A877593BE75F1D13E2DD45B3E827F153023C04C47E9792F6 | |||
| 7964 | cs2.exe | C:\Users\admin\AppData\Local\Temp\genteeFA\4default - 1.bmp | image | |
MD5:14A455E9EEF9FE7FEA4DE14D579A3E84 | SHA256:B666E6BD71EFF3547FB2F5580AC61C64527F6F9BE6A2178FA00F80E32431460A | |||
| 7964 | cs2.exe | C:\Users\admin\AppData\Local\Temp\genteeFA\setup_temp.gea | binary | |
MD5:83488ADFF316DCC82A0A104751523C53 | SHA256:A973057AA052D7F83189451712D53AD0F60BA6A629D43EDCACE4B593DF59A96B | |||
| 7964 | cs2.exe | C:\Users\admin\AppData\Local\Temp\genteert.dll | executable | |
MD5:F1D0C343E43B8D4F026BD4C59099812F | SHA256:AEDB5E44C3865767F8CD803342C21658575C7349F4EE26882D2052F16C5ADCF9 | |||
| 7964 | cs2.exe | C:\Users\admin\AppData\Local\Temp\genteeFA\guig.dll | executable | |
MD5:8757CD8C68B85D668F15BEFC13251D5E | SHA256:96D1906EF8F1AC224830DA79BC9492AA21FFBACD4CAA4FB44CC64DEDF09047A2 | |||
| 6724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6724.25921\cs2.exe | executable | |
MD5:C452D47FBBE0DF86F30908B32842539D | SHA256:B3F5752541186BAE8A929DAFD06F95DE7E006A064CA411DD135B4047A018D5EB | |||
| 4996 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5B7C.tmp.WERInternalMetadata.xml | binary | |
MD5:8D90CEA421D36C668077DA828DD4C74A | SHA256:F5440ED6ED0B3D5DD9598092AD21902437124AA0970AB2075EB4A8B516AFEBA1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
20
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7784 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7784 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |