| File name: | sqlcomplete.com |
| Full analysis: | https://app.any.run/tasks/9e65096e-cfc0-4d1c-a9ce-d46018eb1655 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 05:04:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | D41DDFAE3C6662EC9A662D9F240B221B |
| SHA1: | 34577FA37DCA4492C97AF137A2EFF4BBF1ECB1C8 |
| SHA256: | 37F2288A214F33AC406B1DE0CFDBA65008D6BA8F4F8E5B0F17E2573EB3883759 |
| SSDEEP: | 6144:nD4O1AUC8ITfD/xlEXUVZNUiaJ94GnEdXskbt:Df09TfDgXUVZNpaX4ddXskbt |
MALICIOUS
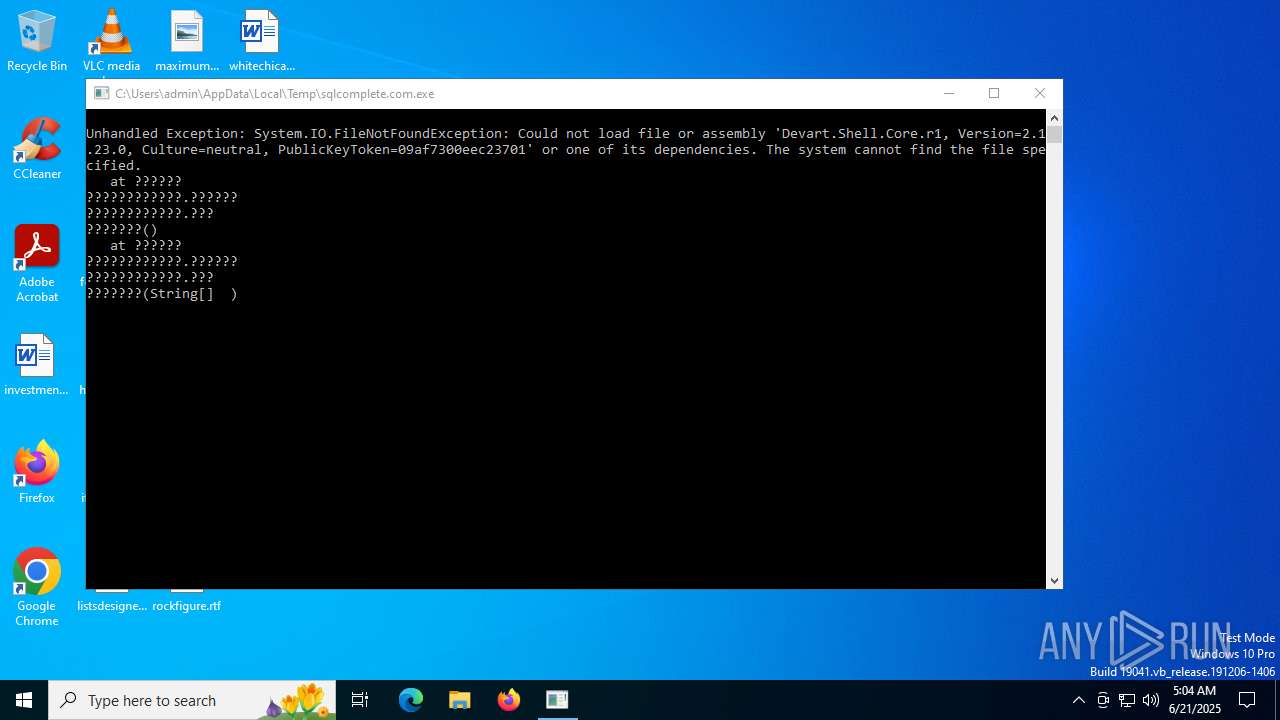
Executing a file with an untrusted certificate
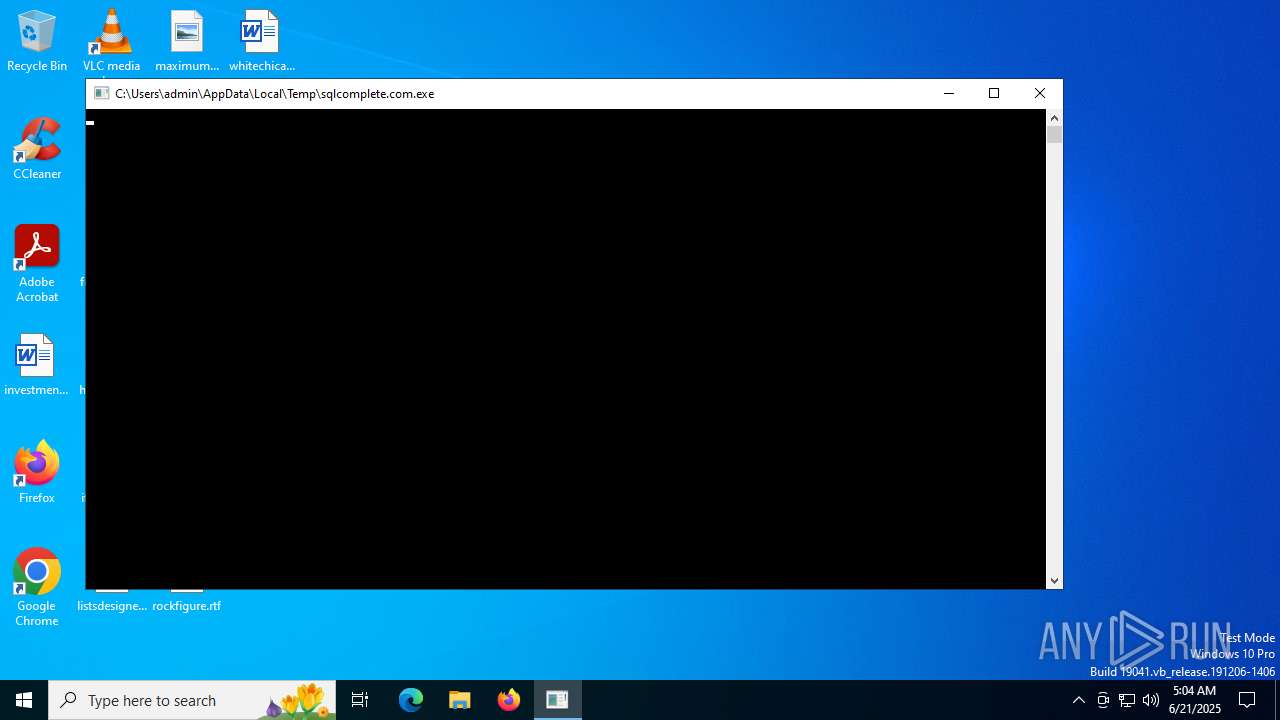
- sqlcomplete.com.exe (PID: 2076)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- sqlcomplete.com.exe (PID: 2076)
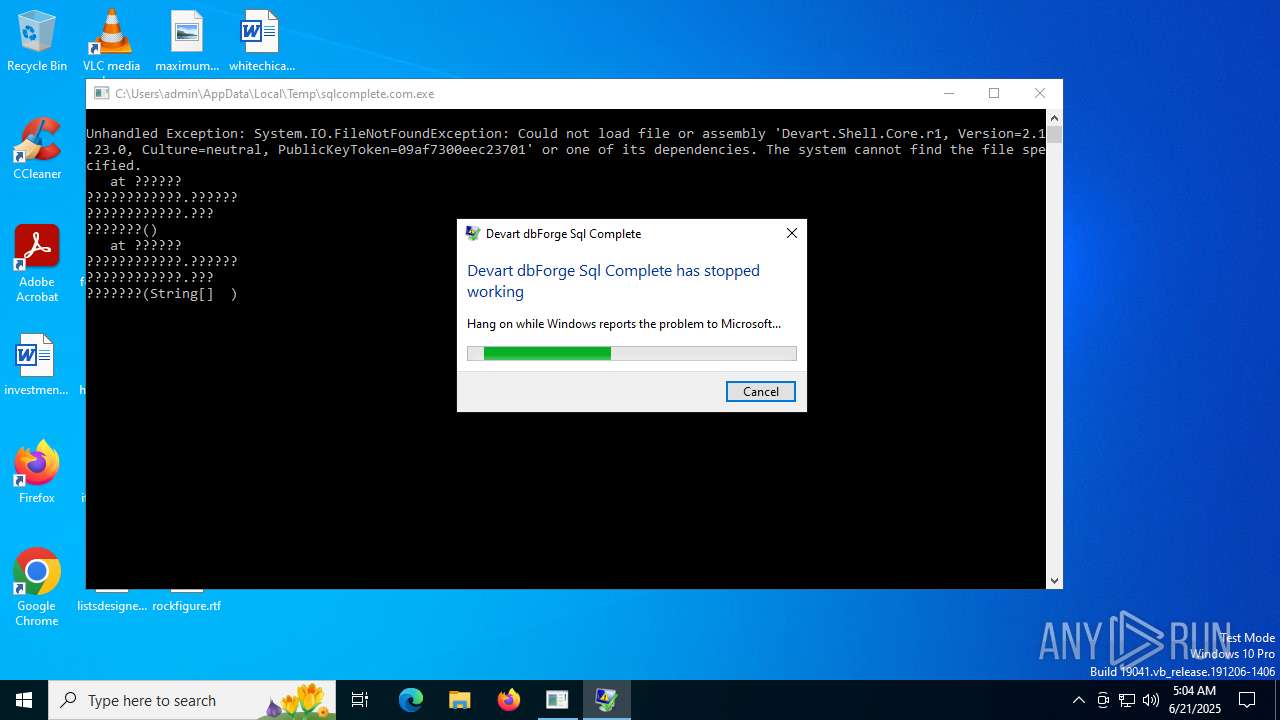
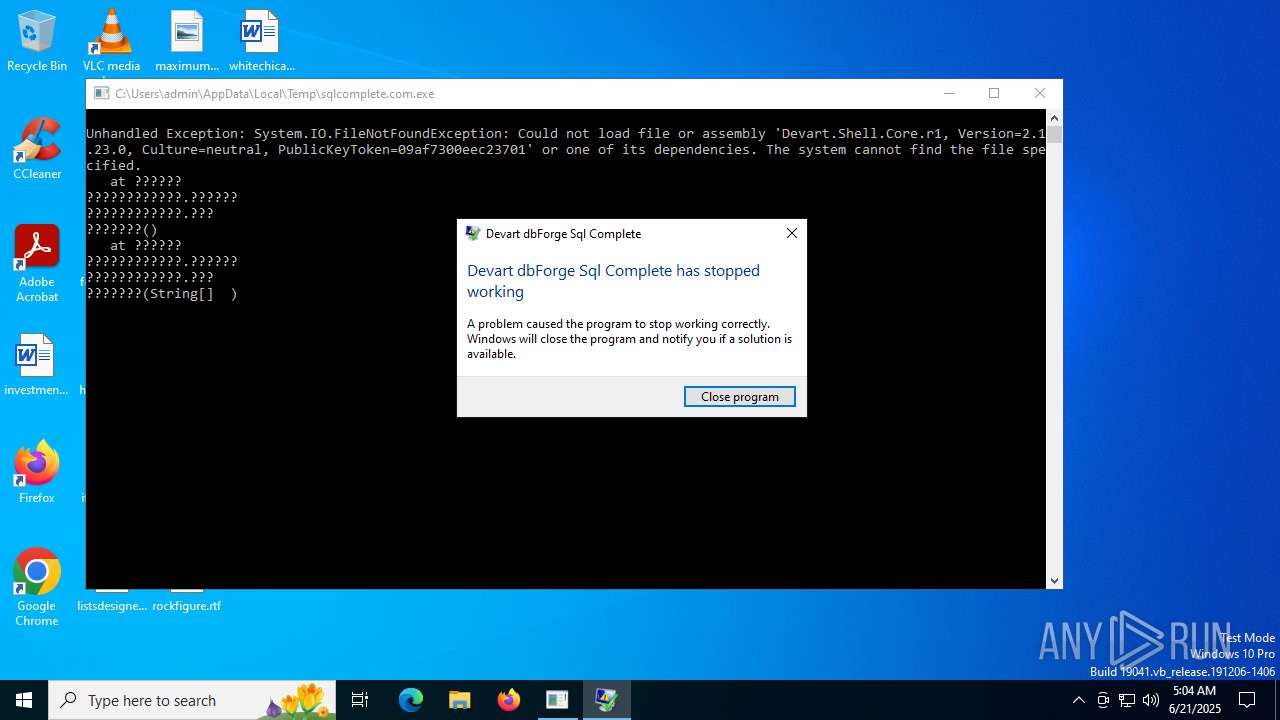
Executes application which crashes
- sqlcomplete.com.exe (PID: 2076)
INFO
Creates files in the program directory
- sqlcomplete.com.exe (PID: 2076)
Reads the computer name
- sqlcomplete.com.exe (PID: 2076)
Creates files or folders in the user directory
- sqlcomplete.com.exe (PID: 2076)
- WerFault.exe (PID: 6936)
Checks supported languages
- sqlcomplete.com.exe (PID: 2076)
Reads the machine GUID from the registry
- sqlcomplete.com.exe (PID: 2076)
Checks proxy server information
- WerFault.exe (PID: 6936)
Reads the software policy settings
- WerFault.exe (PID: 6936)
.NET Reactor protector has been detected
- sqlcomplete.com.exe (PID: 2076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (47.7) |
|---|---|---|
| .scr | | | Windows screen saver (22.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.3) |
| .exe | | | Win32 Executable (generic) (7.7) |
| .exe | | | Win16/32 Executable Delphi generic (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:12:29 18:09:43+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 851968 |
| InitializedDataSize: | 2560 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd1ebe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 6.14.7.0 |
| ProductVersionNumber: | 6.14.7.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Devart |
| FileDescription: | Devart dbForge Sql Complete |
| FileVersion: | 6.14.7.0 |
| InternalName: | sqlcompletecmd.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFileName: | sqlcompletecmd.exe |
| ProductName: | dbForge SQL Complete |
| ProductVersion: | 6.14.7.0 |
| AssemblyVersion: | 6.14.7.0 |
Total processes
140
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2076 | "C:\Users\admin\AppData\Local\Temp\sqlcomplete.com.exe" | C:\Users\admin\AppData\Local\Temp\sqlcomplete.com.exe | explorer.exe | ||||||||||||
User: admin Company: Devart Integrity Level: MEDIUM Description: Devart dbForge Sql Complete Exit code: 3762504530 Version: 6.14.7.0 Modules
| |||||||||||||||
| 2664 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sqlcomplete.com.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6936 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2076 -s 1828 | C:\Windows\SysWOW64\WerFault.exe | sqlcomplete.com.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 537
Read events
5 536
Write events
1
Delete events
0
Modification events
| (PID) Process: | (2076) sqlcomplete.com.exe | Key: | HKEY_CLASSES_ROOT\CID\{79006A00-4300-7200-5600-420044006700} |
| Operation: | write | Name: | 1 |
Value: ntWFcN+1Xp49AkVGS0Dzo2pDNZun06mjrrzAYBYnuRuoIE63n63Z80jZ2FZZLjUkzeYZrgORlf3M3+loBUDL0xNwHRSRYZnTQM6QSMUD4MIYd75uySZd7X4TNJ0xOVr4nIVaB6ap5fKIv5P5CnThS9ZZt8RC/iP0itTp2scwut+oM9PnrsyDpf0HKBy9IChgcjzeAxIkTZEr3LfRzUs/TLj1mS1HWs2Cq7MIEGdaNyP7oi4IPH24DsQuUvEBSW8gO7SBr7W+mWc+58Rbo3oZq8ZCdl5UlR7UySv6bfAKU7J8d4228iWXrOK6gnILAeQat02rAv9ds+dewjn6JkdpB1Hz2XmNJyNDib6bmczXO69ZVPym6gLyYsq5V5A2O5ufe0T6/RZvsrlSwpZTckTpbwZTAp2tGalsJ3mSWwnsN98Tc3sO6nLPPYbEJ/65nC+NZ28nfwCvFmlJ9QqCjL5BHShLJJpQ0wYWxvrVY3+7WeK3uq4jMw+SeR1sxn24ZzDQ | |||
Executable files
0
Suspicious files
5
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6936 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_sqlcomplete.com._a6fb66e811adbb1533d5b2e1769350425af59cb6_6ad155de_e45bf48f-b6a1-4e9a-9905-747cb05ebfaa\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6936 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\sqlcomplete.com.exe.2076.dmp | — | |
MD5:— | SHA256:— | |||
| 2076 | sqlcomplete.com.exe | C:\Users\admin\AppData\Local\Temp:{79006A00-4300-7200-5600-420044006700} | text | |
MD5:822FFF7B8969668DD564DE56407CE88F | SHA256:8067E47E796B1F83C7F1FBCD26B6C7E60D25E20E5B267E986F39C20096860599 | |||
| 6936 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:D310523737A0D4D05066857AC157F458 | SHA256:0A0520D498306689AFA3CAC09ACE82E09229108FC9FABA5A906291D077004484 | |||
| 6936 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5FE5.tmp.xml | xml | |
MD5:32B8BD15B23C3EEF74B01A75F7977E7A | SHA256:C4BE2BF302C3CA147C9E37362E0671FDB715BA43A3F0E003C26576C86A220574 | |||
| 6936 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5EC9.tmp.dmp | binary | |
MD5:FDC776CF2CC26D420FFFD4DAD69482FA | SHA256:24B25532E8D6949C4A53C56AD32F0C5ED73EE879FDFA866971FE2EC7CB46E517 | |||
| 6936 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5FC4.tmp.WERInternalMetadata.xml | xml | |
MD5:B6A06A0404F1B9C98E5AC4C7EF7DBBB4 | SHA256:292468395E71A2C2F1CE7E0D28C99D7248C89BE5E4081206623DD37A87931291 | |||
| 6936 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:0F7B8F6A846AA9CA52FA562DDDCDB5ED | SHA256:AFF90E65A81289B80D1FCC5E71B3D88E5D1AAFE22CE358EB6E28A56D1845263D | |||
| 6936 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:5A8BA5A6B4740F6D69E27903B317008C | SHA256:79437ACEA473F327D0B86BE79EB6353757D81E457DFCFD1EA4B3069192C159DD | |||
| 6936 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:F9BC9B223DE9C799EA1426C77FD6BDAC | SHA256:0425E2043E16E0FF806F5128F9C4C26C29B4D2A7A4E82BA5A2306221608F62D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6936 | WerFault.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6936 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6160 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5904 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5904 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5476 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6936 | WerFault.exe | 104.208.16.94:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6936 | WerFault.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
6936 | WerFault.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6160 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6160 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |