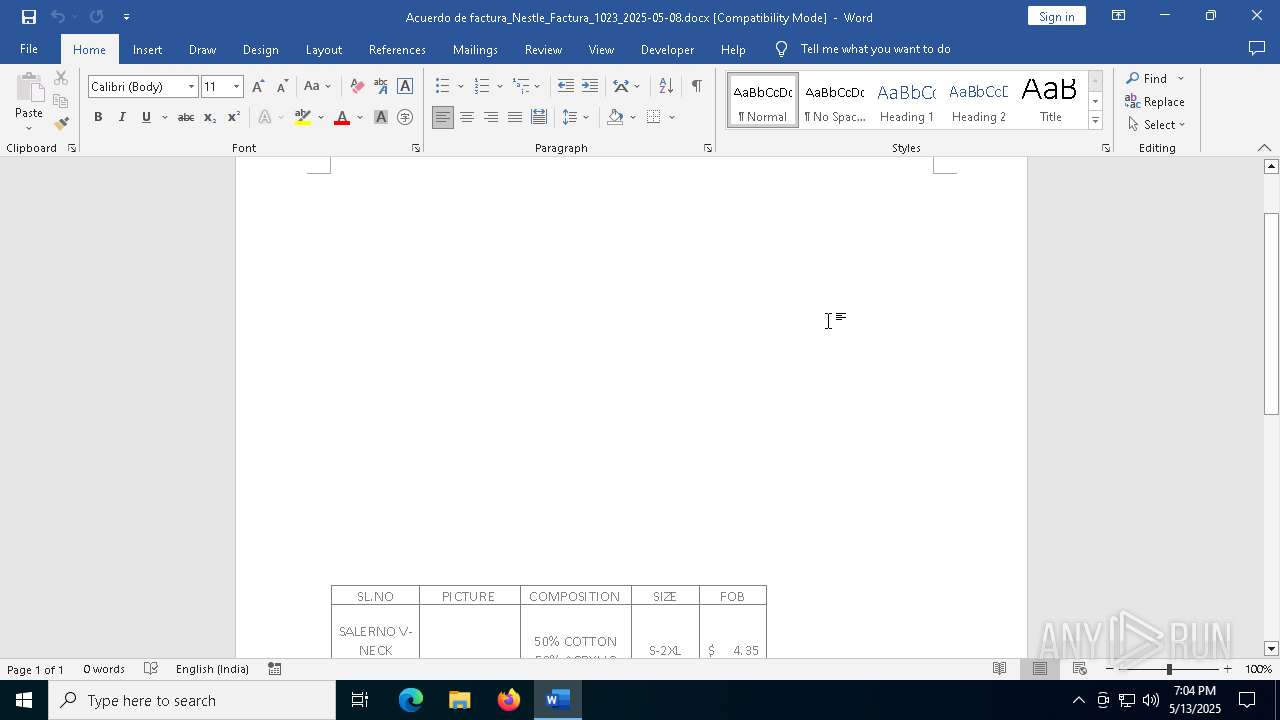
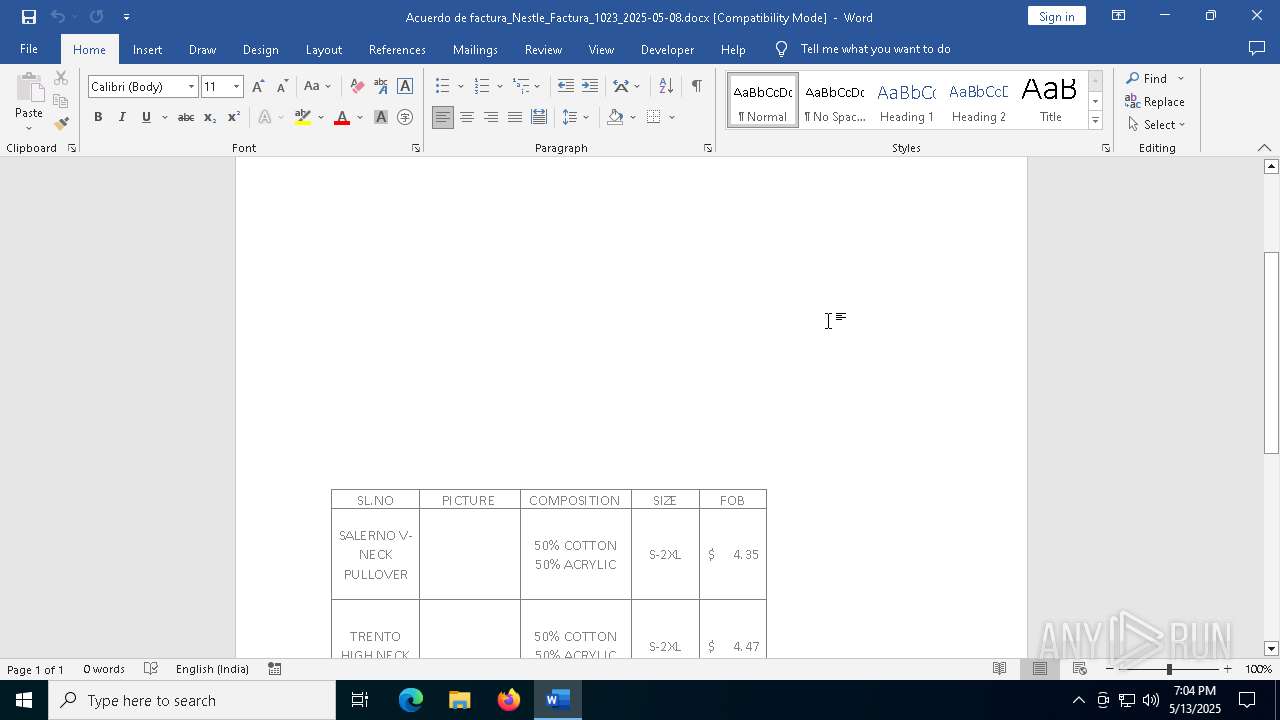
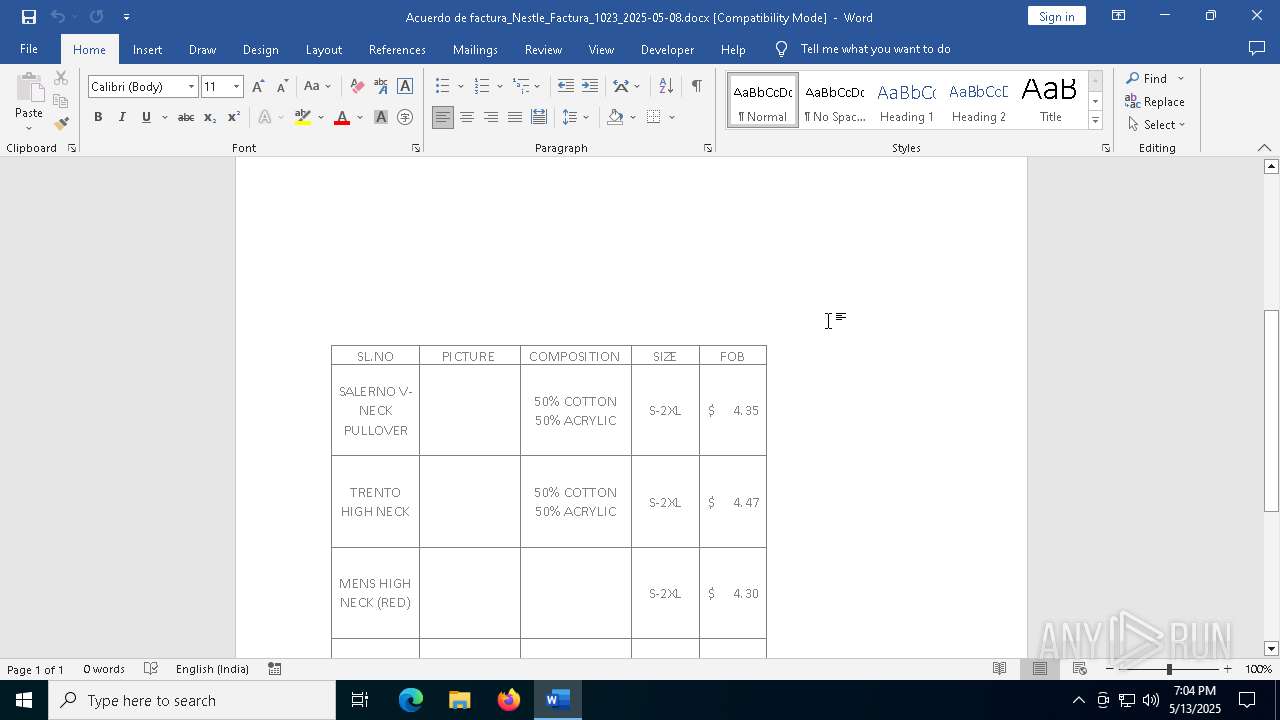
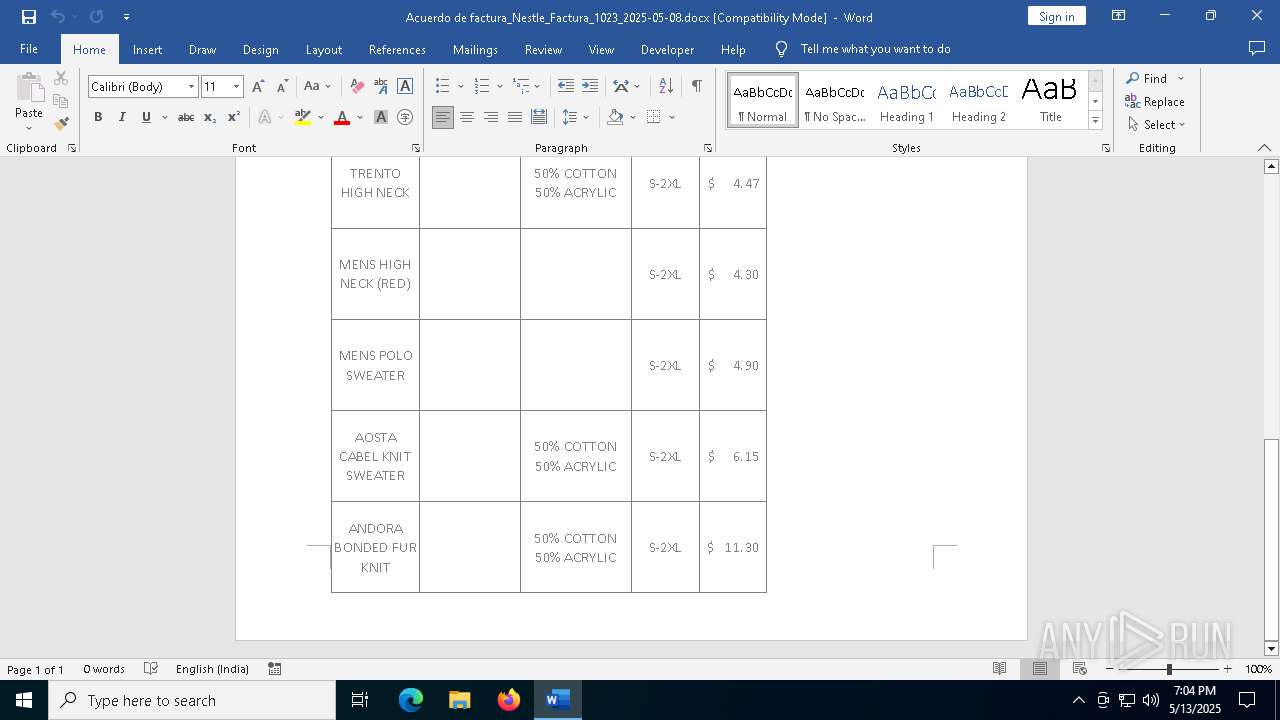
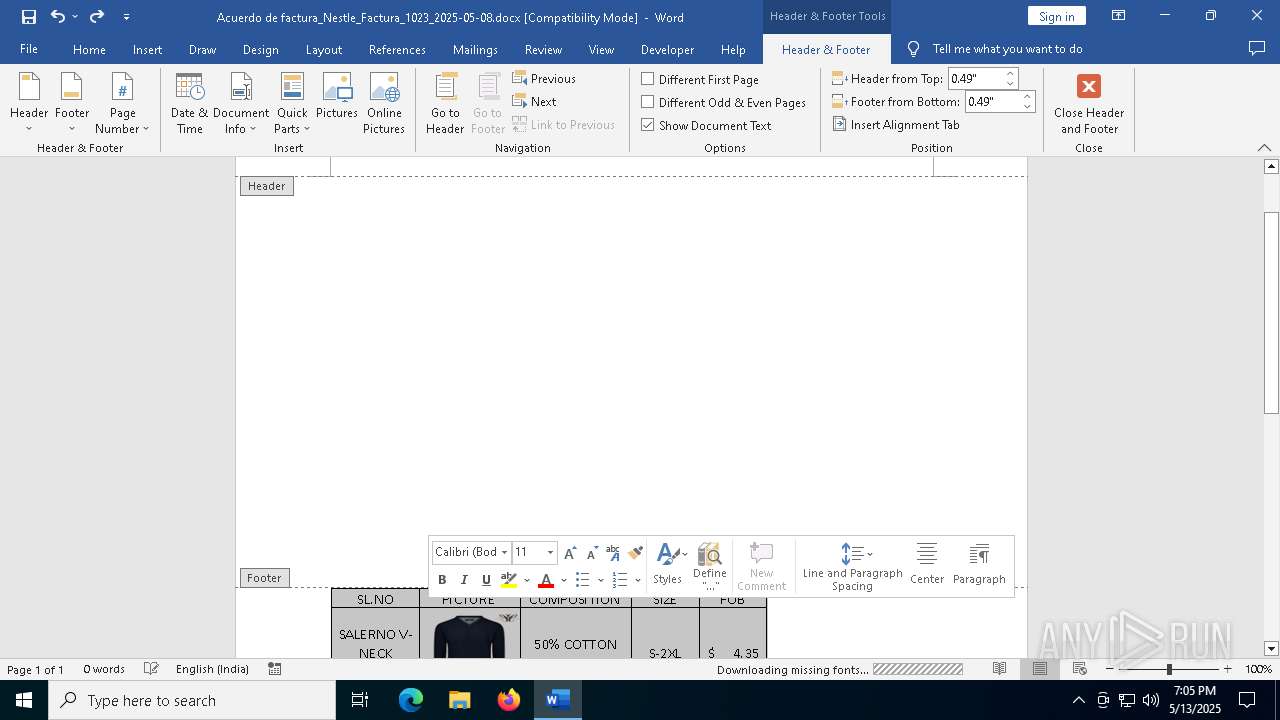
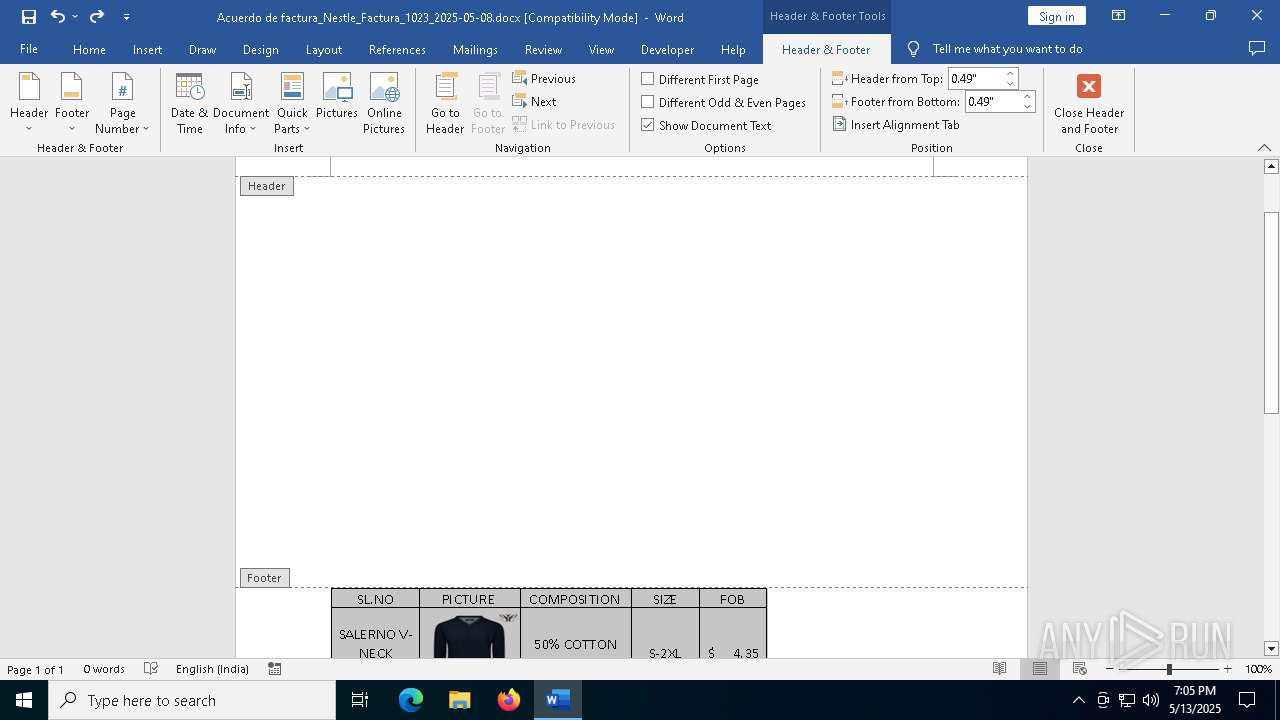
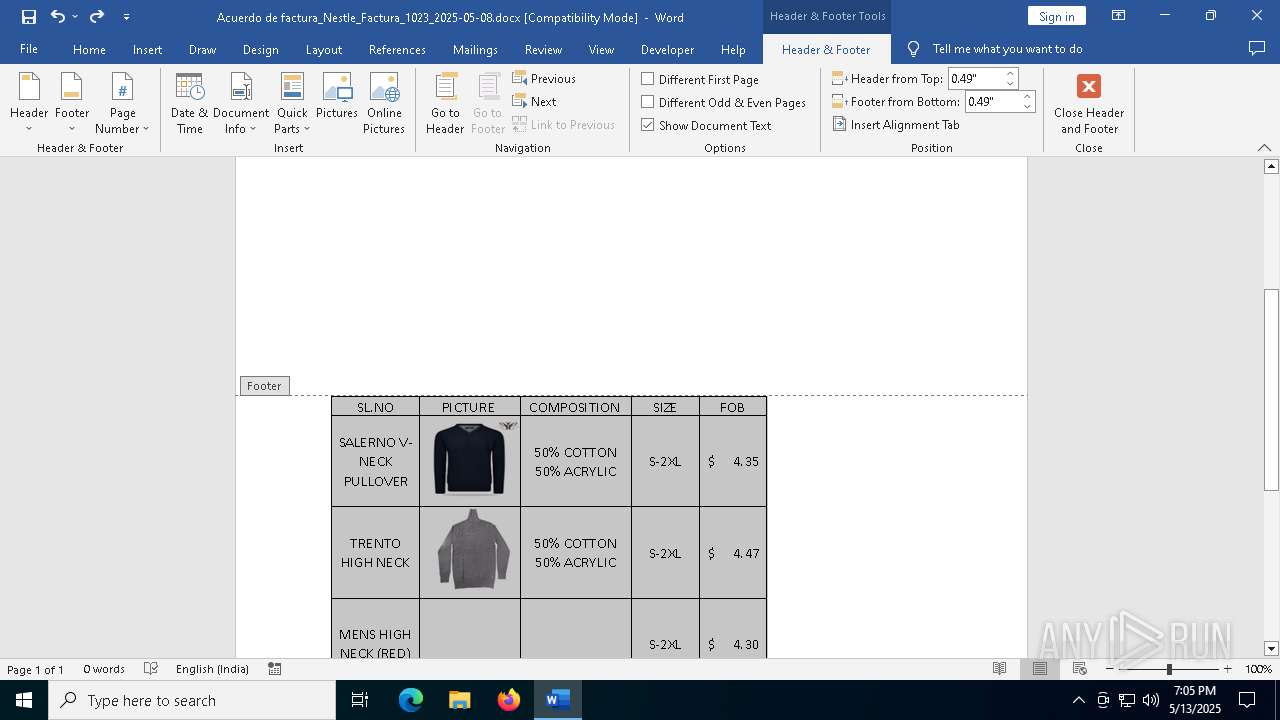
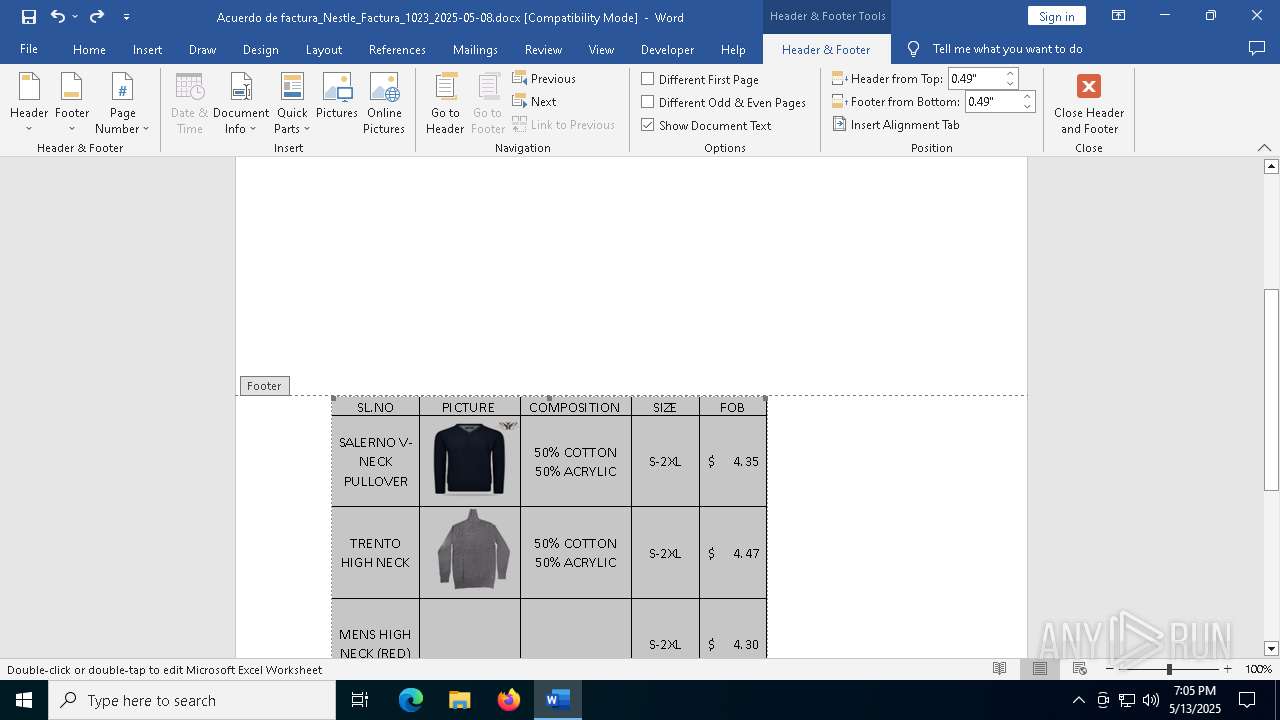
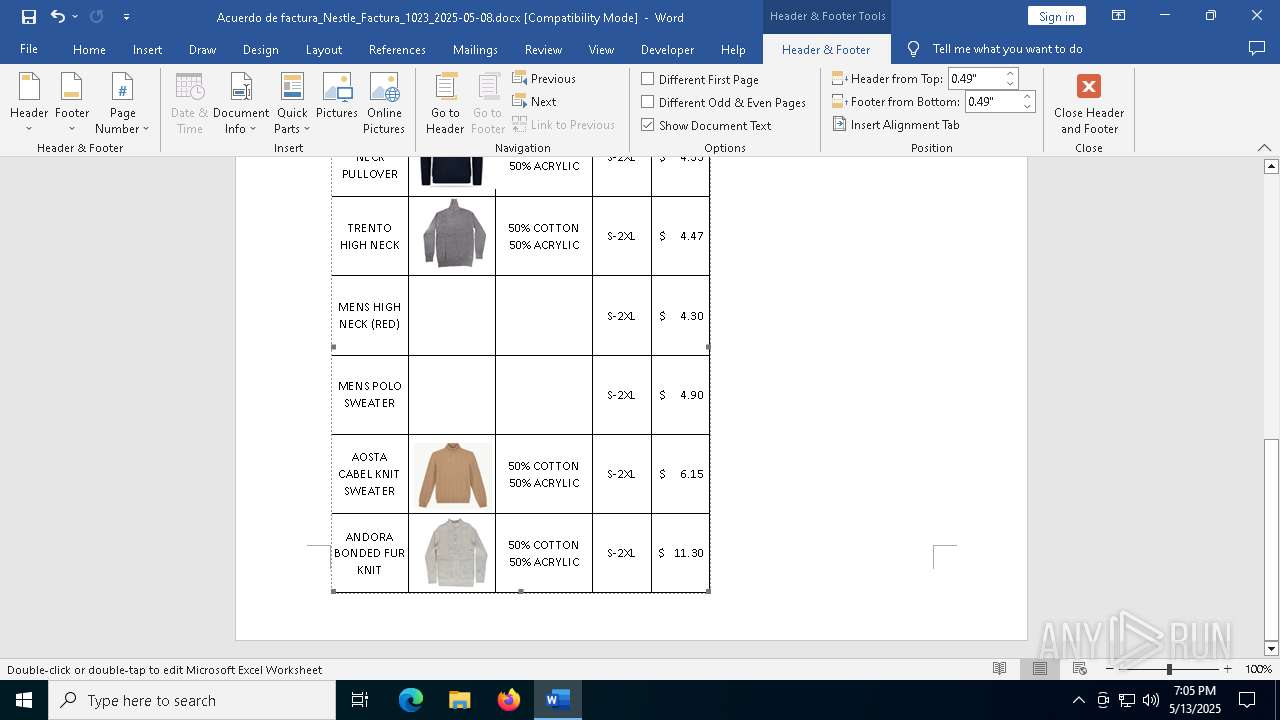
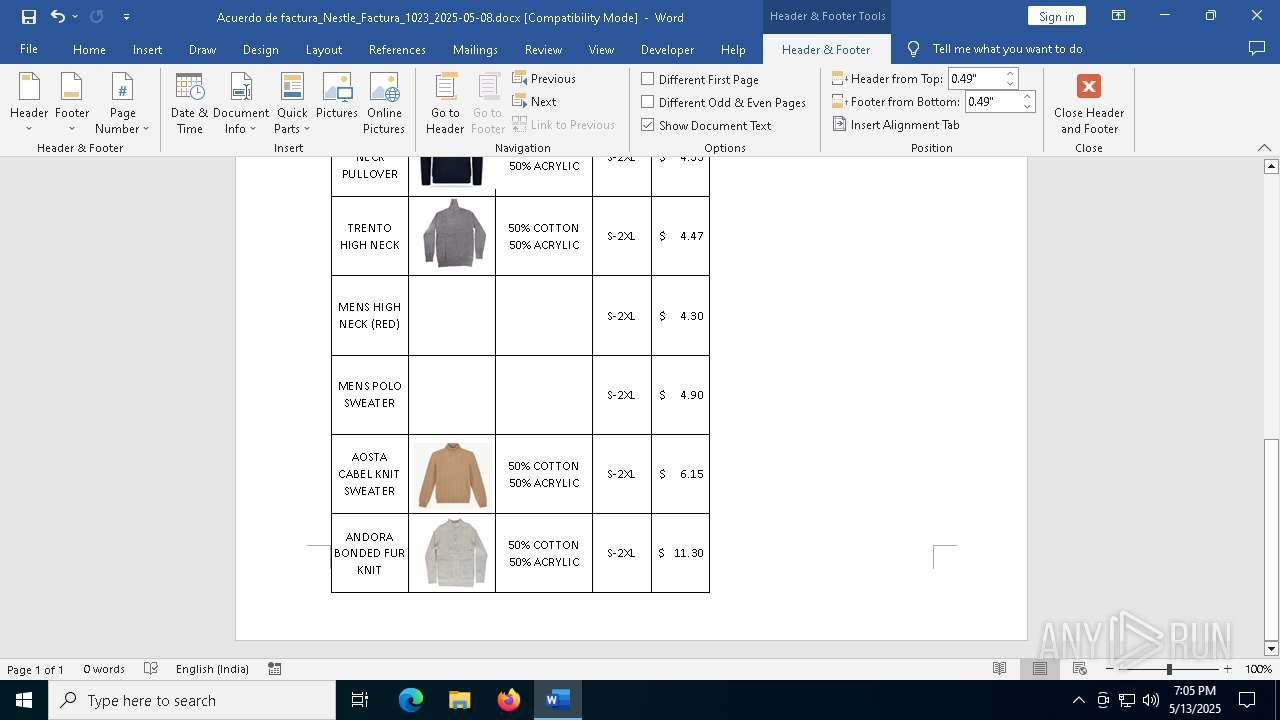
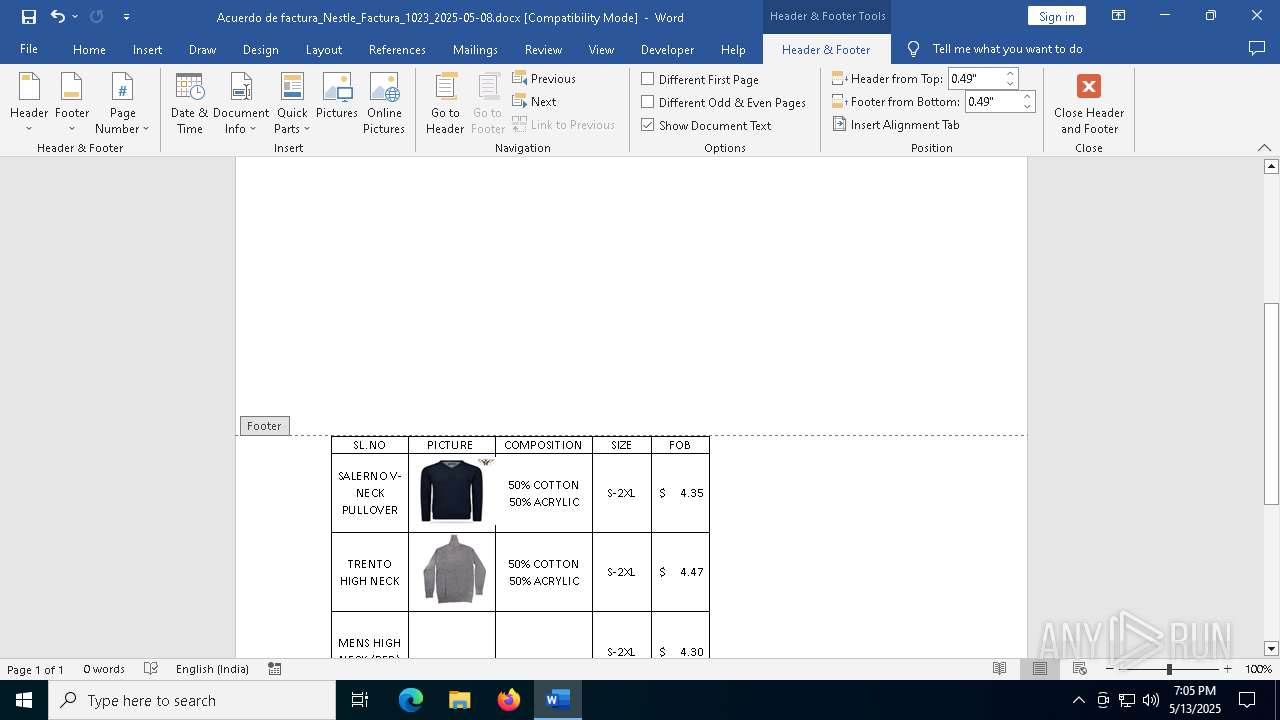
| File name: | Acuerdo de factura_Nestle_Factura_1023_2025-05-08.docx |
| Full analysis: | https://app.any.run/tasks/d7caadcd-c68e-47a2-8d3d-d7b4e66d3ca8 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2025, 19:03:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 662885BCE19148D2AF66D25448D64D56 |
| SHA1: | 2997039AA8500512FF56C7ABDB6F61DA94A5A942 |
| SHA256: | 37CBD57F32AA750A1CAEB8CB387E8405F7B905F775DE8038C86FAA89252B05F8 |
| SSDEEP: | 12288:4VHEpdPceD/7bi2Eq3WMCqwhMNvNpilTZuzU0:4VHEpdPceD/7u2Eq3WMCqwhMN/iGzU0 |
MALICIOUS
EXPLOIT has been detected (SURICATA)
- WINWORD.EXE (PID: 5380)
SUSPICIOUS
Connects to the server without a host name
- WINWORD.EXE (PID: 5380)
INFO
Reads security settings of Internet Explorer
- splwow64.exe (PID: 7864)
Reads the software policy settings
- slui.exe (PID: 7604)
- slui.exe (PID: 7472)
Checks proxy server information
- slui.exe (PID: 7472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:13 18:37:40 |
| ZipCRC: | 0xf5c0e2b4 |
| ZipCompressedSize: | 432 |
| ZipUncompressedSize: | 2503 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | Grizli777 |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
| Keywords: | - |
| LastModifiedBy: | 91974 |
| RevisionNumber: | 2 |
| CreateDate: | 2025:05:12 13:49:00Z |
| ModifyDate: | 2025:05:12 13:50:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | 91974 |
| Description: | - |
Total processes
141
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5380 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Acuerdo de factura_Nestle_Factura_1023_2025-05-08.docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7472 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7572 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7604 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7864 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7888 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "8AC7808B-3B1A-4127-AC6D-A5DC1A1A9F06" "69A9E490-64CC-48B1-AA31-45D417E6F9FA" "5380" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
17 272
Read events
16 839
Write events
396
Delete events
37
Modification events
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\word\AudienceList |
| Operation: | write | Name: | Automation |
Value: ofy5bfmdisx6r201 | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\word\AudienceList |
| Operation: | write | Name: | Dogfood |
Value: offbp6lldxtzgk01 | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\word\AudienceList |
| Operation: | write | Name: | Microsoft |
Value: of14iikgwda45r01 | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\word\AudienceList |
| Operation: | write | Name: | Insiders |
Value: ofdibw53ukclan01 | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\word\AudienceList |
| Operation: | write | Name: | Production |
Value: ofxkhgd4x4oixy01 | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\FileIO |
| Operation: | write | Name: | CacheId |
Value: {9DFDE5A9-9BF3-4501-B8A9-226418F884CC} | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\FileIO |
| Operation: | write | Name: | MetadataReplicationCompleted |
Value: 1 | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\FileIO |
| Operation: | delete value | Name: | CentralTableFileName |
Value: | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\FileIO |
| Operation: | write | Name: | CentralTableFileName |
Value: CentralTable.accdb | |||
| (PID) Process: | (5380) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\FileIO |
| Operation: | write | Name: | ExpungeFilesIfDiskFullLastRunTime |
Value: | |||
Executable files
33
Suspicious files
142
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$uerdo de factura_Nestle_Factura_1023_2025-05-08.docx | binary | |
MD5:6507F191849BB130FE4150EE887F1A7C | SHA256:DBE46D42F795A59E4321A5E5C3868A7B57CF0F5CE8F6FC8F5BCD1164E4A338E6 | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:5C1EC24F1932035CC32CB493BD6A1B87 | SHA256:C713C9F4DADCC0CD813D4484B2CE028D02F9FC721ADAE641DDE02F58D94BDAE9 | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:90FDE71FB516AFCD323E099BC7E06C22 | SHA256:C60DE3F1F664E080A59258E580BDA4CB220CD458E4D464D297E24C3CD753F3B8 | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:7C23DDCE781505BC449377869F23596A | SHA256:EE06119F22EB5137F86010A6F28B22B6A43EC7382A5DEF8782E84F381C0BB80F | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:F8E6D91F1CF1BFC920BACA8F118914FD | SHA256:37BA130CF63BA271EA06FE01CB8B365F3D5D0D86864BFE2A1AF22467C4BDCDA4 | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\68B004A6-86B0-48EF-B3C7-277637C7D287 | xml | |
MD5:34E6E4D0475007566F9F0BFEB93B5AB4 | SHA256:7D0FE6CCF9439FC42196F2F0A47DAA3DF5012CFB2AF07C1ADF88D3C668189CEE | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\ResourceInfoCache\07fc2a8c43a1d1f16572d21e959a4847e306edae.temp | binary | |
MD5:B0B39B162D6BFF4415EBB7D9C33CCCB6 | SHA256:540C54A650B402AAB18921C5B3C734AF147C756BD92AC8DD82D2124A1BB7B2FA | |||
| 5380 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\ResourceInfoCache\data.json | binary | |
MD5:B0B39B162D6BFF4415EBB7D9C33CCCB6 | SHA256:540C54A650B402AAB18921C5B3C734AF147C756BD92AC8DD82D2124A1BB7B2FA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
72
DNS requests
31
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5380 | WINWORD.EXE | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5380 | WINWORD.EXE | GET | 200 | 184.24.77.65:80 | http://e6.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBTUejiAQejpjQc4fOz2ttjyD6VkMQQUDcXM%2FZvuFAWhTDCCpT5eisNYCdICEgZdFHqjfO0hVu7qFE7GwZq4gQ%3D%3D | unknown | — | — | whitelisted |
5380 | WINWORD.EXE | HEAD | 200 | 107.173.47.153:80 | http://107.173.47.153/xampp/broda/brs/greatnessachievementsforbetterthings_______greatnessachievementsforbetterthings________greatnessachievementsforbetterthings.doc | unknown | — | — | unknown |
5380 | WINWORD.EXE | GET | 200 | 107.173.47.153:80 | http://107.173.47.153/xampp/broda/brs/greatnessachievementsforbetterthings_______greatnessachievementsforbetterthings________greatnessachievementsforbetterthings.doc | unknown | — | — | unknown |
5380 | WINWORD.EXE | HEAD | 200 | 107.173.47.153:80 | http://107.173.47.153/xampp/broda/brs/greatnessachievementsforbetterthings_______greatnessachievementsforbetterthings________greatnessachievementsforbetterthings.doc | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5380 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.180:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5380 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5380 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5380 | WINWORD.EXE | 2.16.10.172:443 | omex.cdn.office.net | Akamai International B.V. | AT | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
l1k.ir |
| unknown |
x1.c.lencr.org |
| whitelisted |
e6.o.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5380 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
5380 | WINWORD.EXE | Misc Attack | EXPLOIT [ANY.RUN] Obfuscated RTF document including the CLSID of the Equation Editor (CVE-2017-11882) |
5380 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
5380 | WINWORD.EXE | Potentially Bad Traffic | ET HUNTING Microsoft Office User-Agent Requesting A Doc File |
5380 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
5380 | WINWORD.EXE | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |