| File name: | Bootstrapper.exe |
| Full analysis: | https://app.any.run/tasks/069a938d-4461-4d3e-a691-65e87bf3aeed |
| Verdict: | Malicious activity |
| Analysis date: | March 07, 2025, 18:38:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 15 sections |
| MD5: | F2A6133B7F38FC49F792AE799D1B4750 |
| SHA1: | 6BEF46DDDE325F45A0E9FF123112C96BBD47C795 |
| SHA256: | 37BDE6655E1272E159B9C2E3A7EEE3F4E9A837C0F04240645D3991D112287F8D |
| SSDEEP: | 98304:bRFl0PK8mmQNzHX2QYoSoOM/jaOh54B8aaLgq1riLkZIlftafd1QQuc4jbqTiZSL:wu |
MALICIOUS
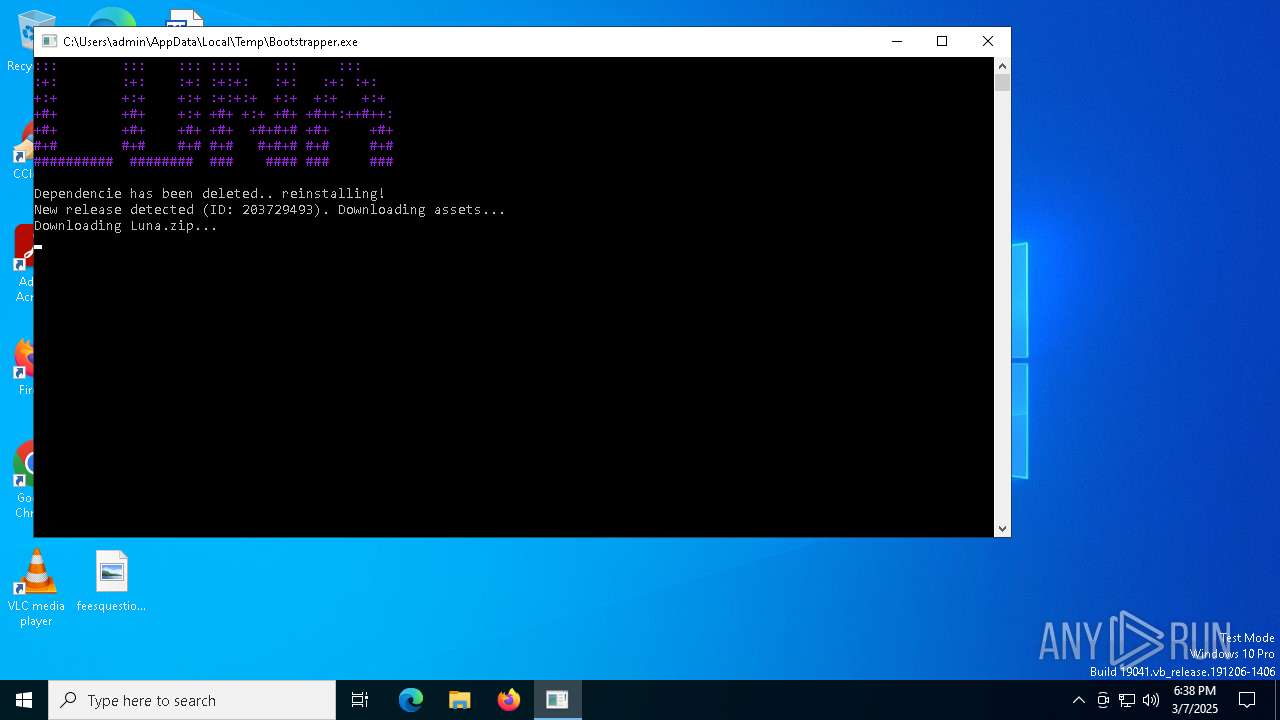
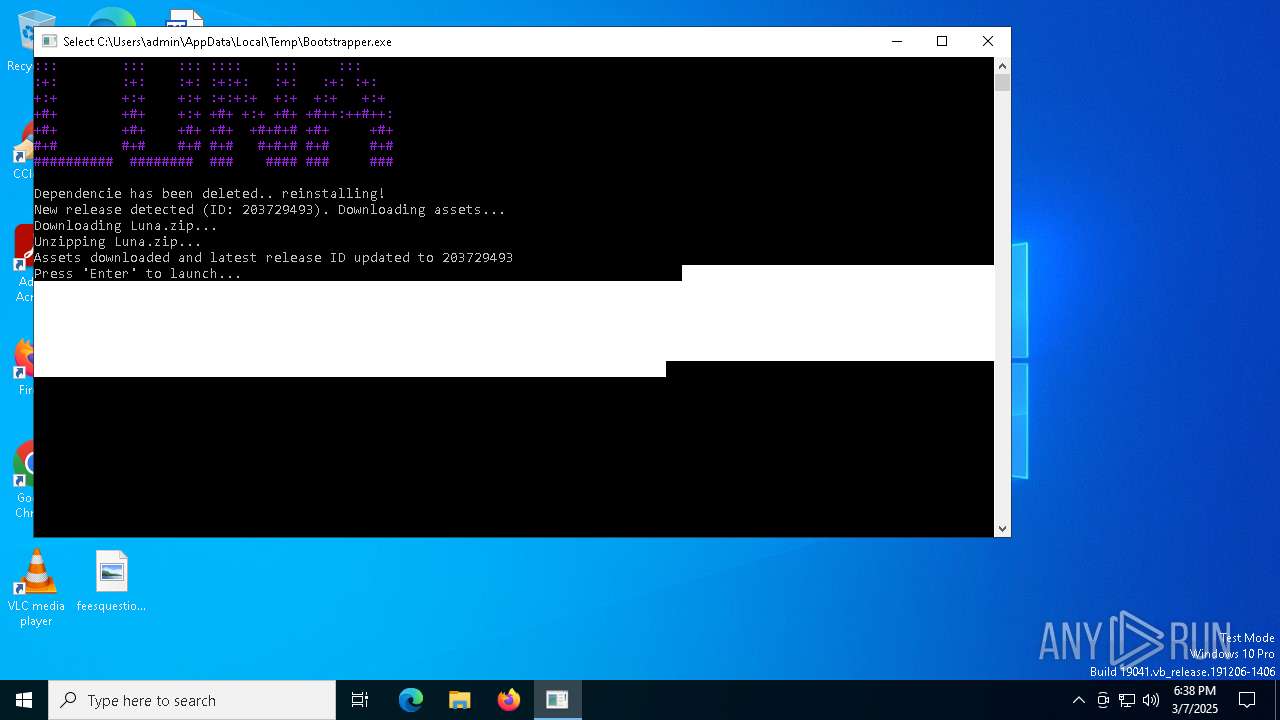
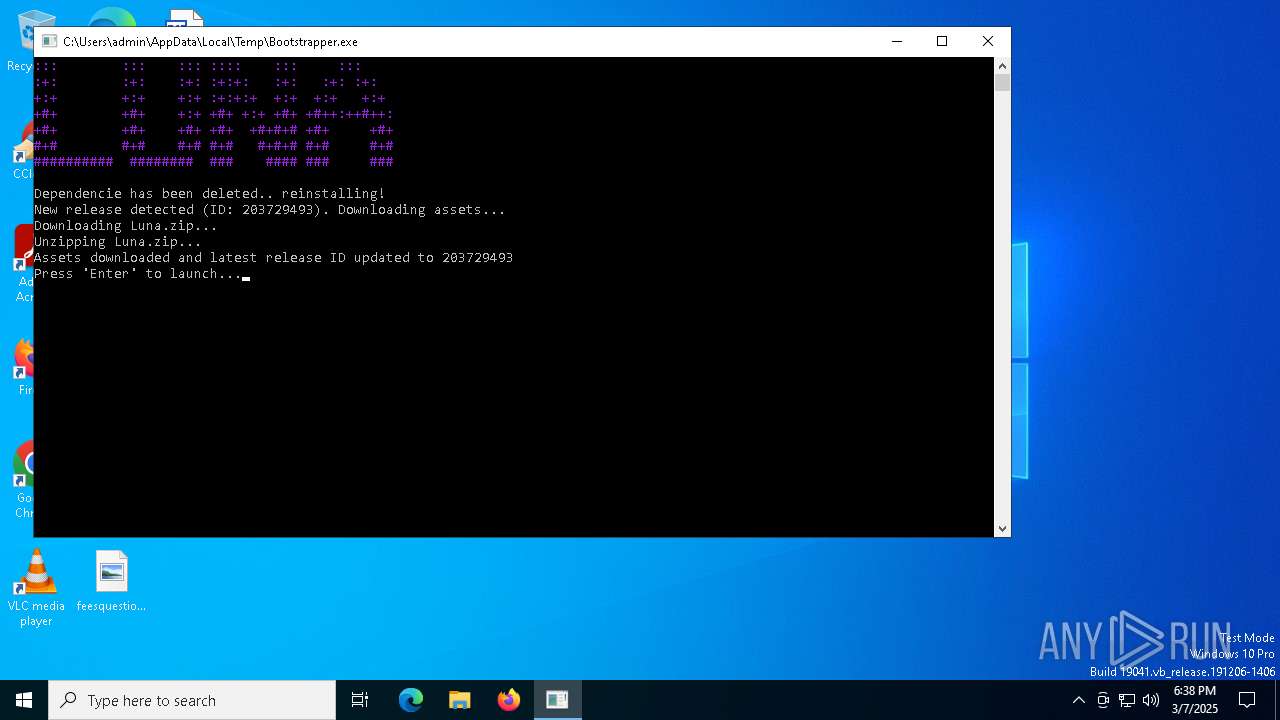
SLIVERFOX has been found (auto)
- Bootstrapper.exe (PID: 300)
SUSPICIOUS
Application launched itself
- Luna.exe (PID: 7356)
Executable content was dropped or overwritten
- Bootstrapper.exe (PID: 300)
- Luna.exe (PID: 7420)
- MicrosoftEdgeUpdate.exe (PID: 7528)
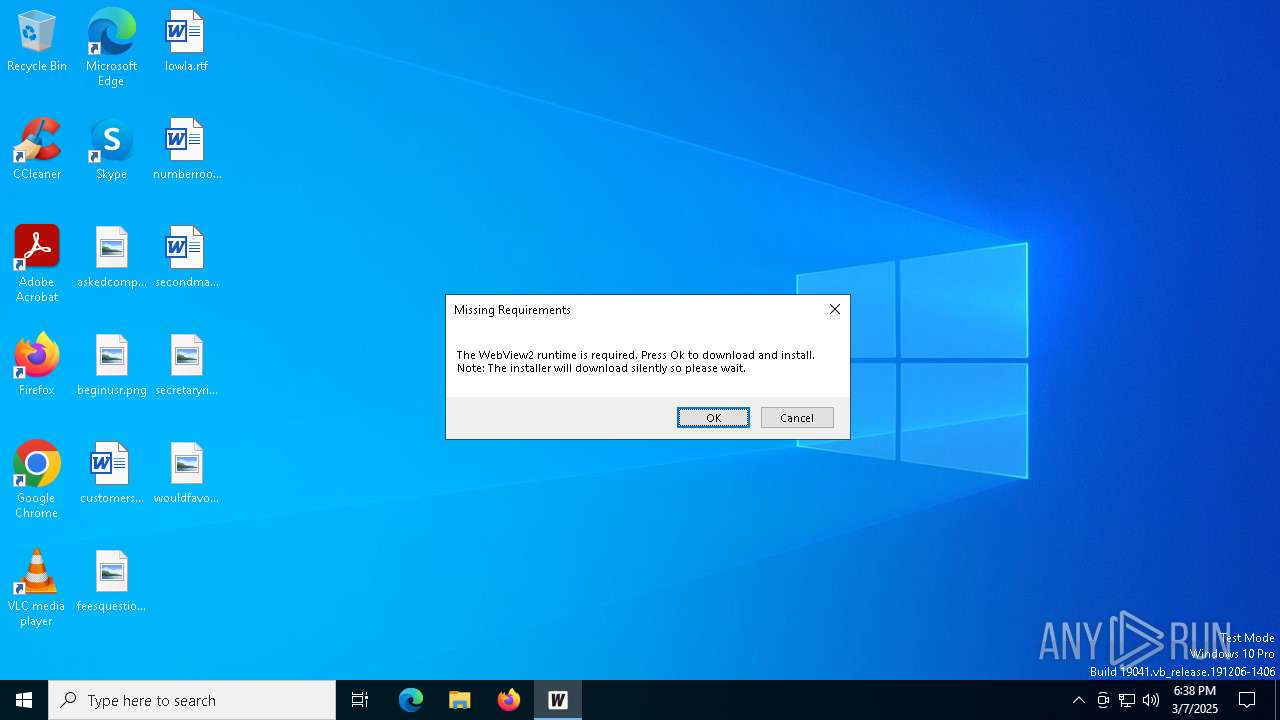
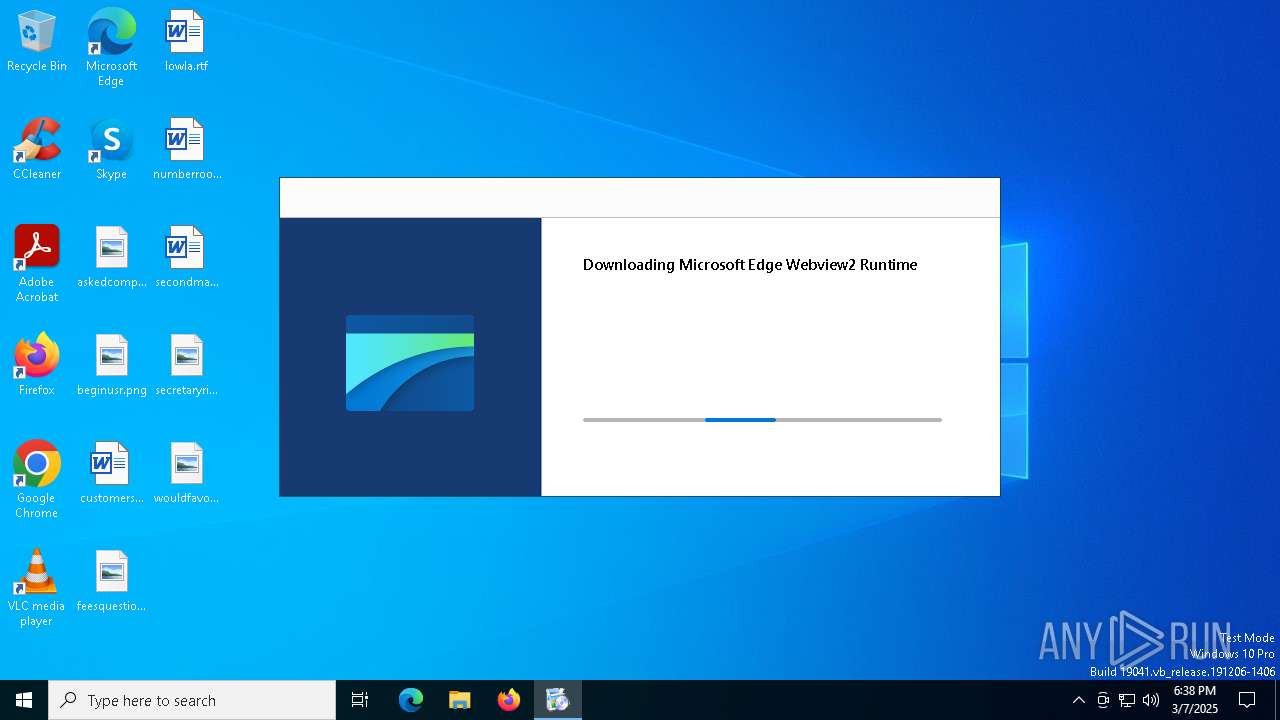
- MicrosoftEdgeWebview2Setup.exe (PID: 7504)
Process drops legitimate windows executable
- MicrosoftEdgeUpdate.exe (PID: 7528)
- Luna.exe (PID: 7420)
- MicrosoftEdgeWebview2Setup.exe (PID: 7504)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 7528)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 7504)
- MicrosoftEdgeUpdate.exe (PID: 7528)
Found regular expressions for crypto-addresses (YARA)
- Luna.exe (PID: 7356)
INFO
Reads the machine GUID from the registry
- Bootstrapper.exe (PID: 300)
Reads the software policy settings
- Bootstrapper.exe (PID: 300)
Reads the computer name
- Bootstrapper.exe (PID: 300)
Checks supported languages
- Bootstrapper.exe (PID: 300)
Create files in a temporary directory
- Bootstrapper.exe (PID: 300)
- Luna.exe (PID: 7356)
- Luna.exe (PID: 7420)
- MicrosoftEdgeWebview2Setup.exe (PID: 7504)
- MicrosoftEdgeUpdate.exe (PID: 7528)
The sample compiled with english language support
- Luna.exe (PID: 7420)
- MicrosoftEdgeUpdate.exe (PID: 7528)
- MicrosoftEdgeWebview2Setup.exe (PID: 7504)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 7528)
- MicrosoftEdgeUpdate.exe (PID: 7780)
Application based on Golang
- Luna.exe (PID: 7356)
Detects GO elliptic curve encryption (YARA)
- Luna.exe (PID: 7356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2955264 |
| InitializedDataSize: | 321536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x74760 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
146
Monitored processes
15
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Users\admin\AppData\Local\Temp\Bootstrapper.exe" | C:\Users\admin\AppData\Local\Temp\Bootstrapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1676 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2100 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Bootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7356 | luna\Luna.exe | C:\Users\admin\AppData\Local\Temp\luna\Luna.exe | Bootstrapper.exe | ||||||||||||
User: admin Company: Luna Integrity Level: MEDIUM Description: Luna Modules
| |||||||||||||||
| 7420 | C:\Users\admin\AppData\Local\Temp\luna\Luna.exe | C:\Users\admin\AppData\Local\Temp\luna\Luna.exe | Luna.exe | ||||||||||||
User: admin Company: Luna Integrity Level: MEDIUM Description: Luna Modules
| |||||||||||||||
| 7504 | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | Luna.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Setup Version: 1.3.195.43 Modules
| |||||||||||||||
| 7528 | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\MicrosoftEdgeUpdate.exe /installsource taggedmi /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.43 Modules
| |||||||||||||||
| 7556 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /regserver | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
| 7580 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
Total events
13 531
Read events
12 264
Write events
1 233
Delete events
34
Modification events
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | delete value | Name: | eulaaccepted |
Value: | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | path |
Value: C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UninstallCmdLine |
Value: "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /uninstall | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | pv |
Value: 1.3.195.43 | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | name |
Value: Microsoft Edge Update | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | pv |
Value: 1.3.195.43 | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Microsoft Edge Update |
Value: "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateCore.exe" | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | edgeupdate_task_name_c |
Value: MicrosoftEdgeUpdateTaskUserS-1-5-21-1693682860-607145093-2874071422-1001Core{A0274ACE-758D-45F2-96EE-ADF41E50C5CC} | |||
| (PID) Process: | (7528) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | edgeupdate_task_name_ua |
Value: MicrosoftEdgeUpdateTaskUserS-1-5-21-1693682860-607145093-2874071422-1001UA{57179283-63EB-4444-9359-8DC848A0BC1D} | |||
| (PID) Process: | (7580) MicrosoftEdgeUpdateComRegisterShell64.exe | Key: | HKEY_CLASSES_ROOT\CLSID\{60B746FF-B482-4E3E-92AF-4C285E3E71A3}\InprocHandler32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
Executable files
204
Suspicious files
5
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7504 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\msedgeupdate.dll | executable | |
MD5:40CD707DD3011A9845FF9C42256EA7E3 | SHA256:9F4C7072716E0BE1BE08207A7024A5E41162E288E677D805BE8E5469A8BD4909 | |||
| 7504 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\MicrosoftEdgeUpdateComRegisterShell64.exe | executable | |
MD5:714C34FE6098B45A3303C611C4323EAE | SHA256:FBF495968C4A385FF0790E6B65D26610EF917A2B36A5387EFF7AE79D7A980AC5 | |||
| 300 | Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\luna\Luna.exe | executable | |
MD5:9226E1FCF799F5B1D0DBAD674C3856DD | SHA256:5981E0CE9D4ECCA3F5E23A994E223C2686E035E2A753E277F3F30C425426DE43 | |||
| 7420 | Luna.exe | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | executable | |
MD5:B49D269A231BCF719D6DE10F6DCF0692 | SHA256:BDE514014B95C447301D9060A221EFB439C3C1F5DB53415F080D4419DB75B27E | |||
| 7504 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\MicrosoftEdgeUpdateBroker.exe | executable | |
MD5:E5DE2B67B2B629859949DB28D614FAAB | SHA256:8C86A415557DA686214675A02A94964F07C2166C811C61542776F4BF920555CA | |||
| 7504 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\MicrosoftEdgeUpdate.exe | executable | |
MD5:70CC35C7FB88D650902E7A5611219931 | SHA256:7ECA199201273F0BCFF1E26778CB535E69C74A69064E7759FF8DAD86954D42B1 | |||
| 7504 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\psmachine.dll | executable | |
MD5:6708BC8A0A25C258EC65FCA66D7B64CE | SHA256:810796F10921B714F9AE42F97B3E601DCCB1F9B27E0C5CF59C7BA46C2FAACF19 | |||
| 7504 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUF426.tmp\MicrosoftEdgeUpdateOnDemand.exe | executable | |
MD5:A8652F75AD0579D14FB45BB5A6C98D23 | SHA256:E41E92F37BFDE77799E947FCE1D6E9378B4C53FB4B86905F64622691C30AD1E5 | |||
| 300 | Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\luna\Luna.dll | executable | |
MD5:3A87FB61F757BC7F8AAA333663A55C78 | SHA256:5EA93E328A9D7CB9230ACDDC01B38DC09F3B94792F81F9DB8CA3D30185A94C74 | |||
| 300 | Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\downloads\Luna.zip | compressed | |
MD5:BAC8D83B1C753768720DF2E31B840B9F | SHA256:0759BDF6D5B3AC8C59F1B14265ABE5341537DE86CA863BE072218C0119987CD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1052 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7864 | svchost.exe | HEAD | 200 | 23.50.131.74:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/b7450c20-0f92-41df-9f93-8574ad303ce3?P1=1741977531&P2=404&P3=2&P4=NLnQUJrstO4MSEAXz4fwG0ryRJCeAvvxyQb1d31%2bHAkSjXnHQG%2fsieAZNFAYmOsFne3YpYtt93zq%2bkcUk09HDw%3d%3d | unknown | — | — | whitelisted |
7864 | svchost.exe | GET | — | 23.50.131.74:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/b7450c20-0f92-41df-9f93-8574ad303ce3?P1=1741977531&P2=404&P3=2&P4=NLnQUJrstO4MSEAXz4fwG0ryRJCeAvvxyQb1d31%2bHAkSjXnHQG%2fsieAZNFAYmOsFne3YpYtt93zq%2bkcUk09HDw%3d%3d | unknown | — | — | whitelisted |
8104 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8104 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
300 | Bootstrapper.exe | 140.82.121.6:443 | api.github.com | GITHUB | US | whitelisted |
300 | Bootstrapper.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
300 | Bootstrapper.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1052 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.github.com |
| whitelisted |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7864 | svchost.exe | Misc activity | ET INFO Packed Executable Download |