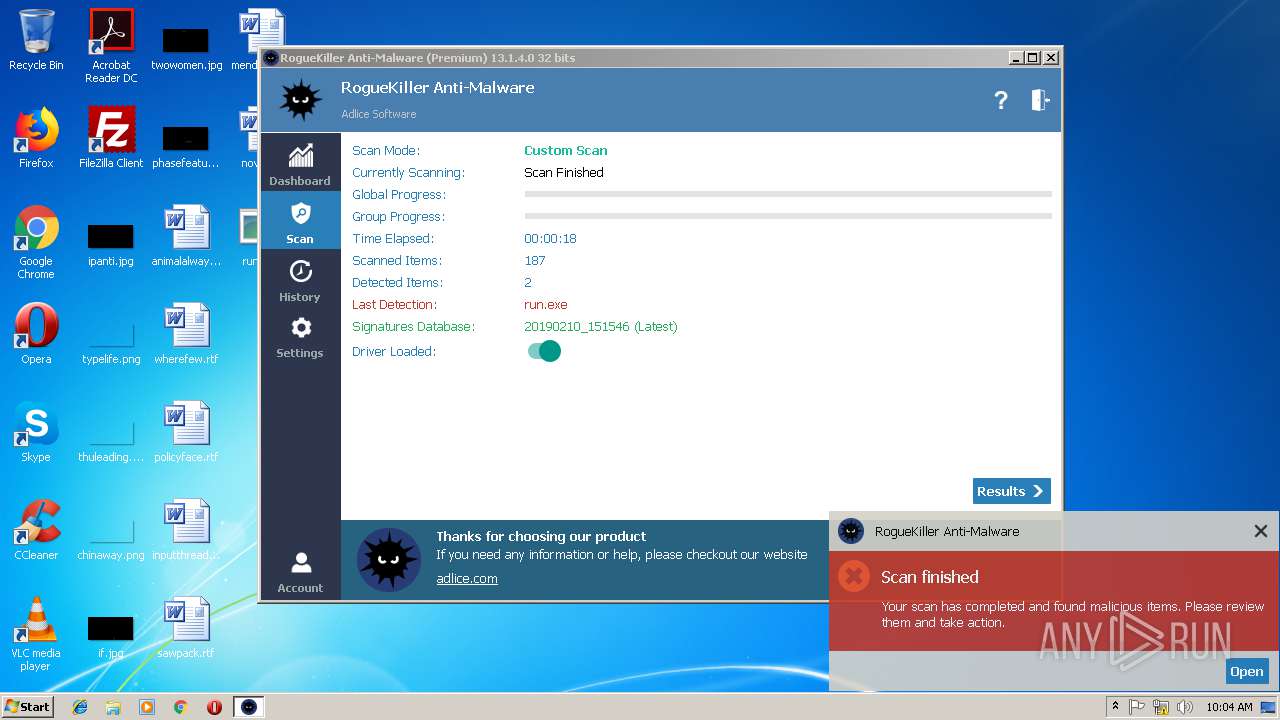
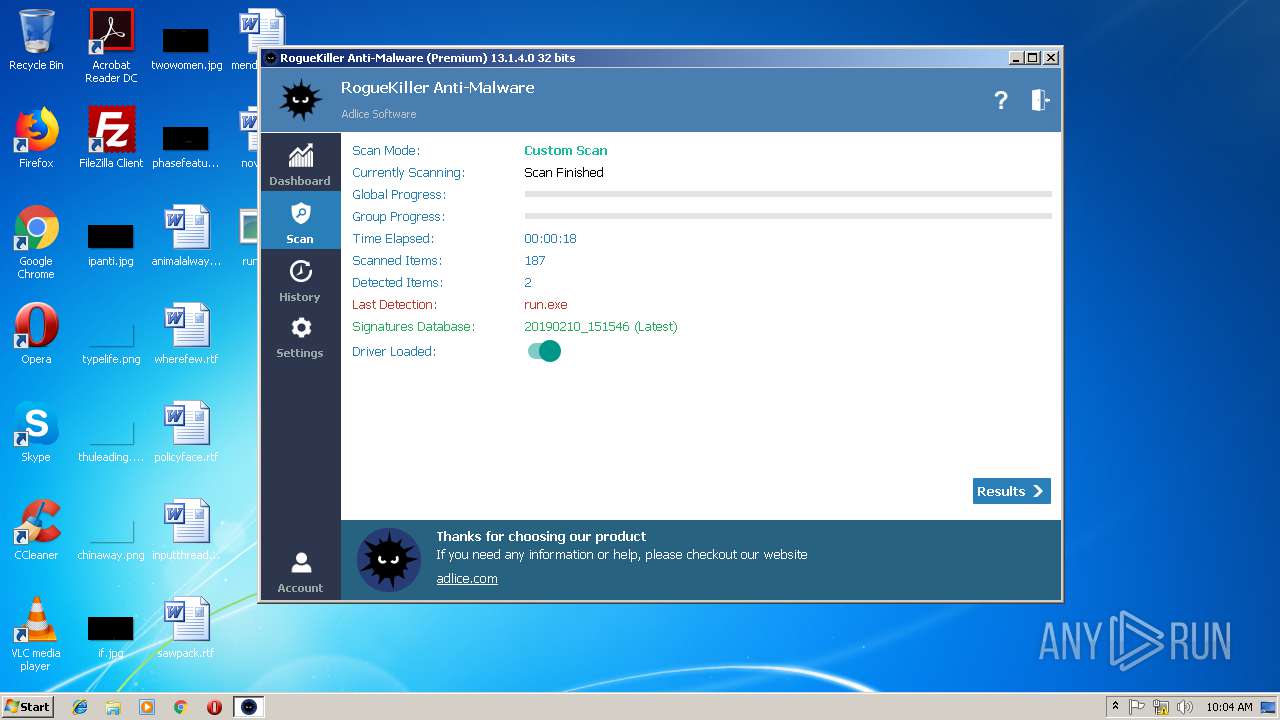
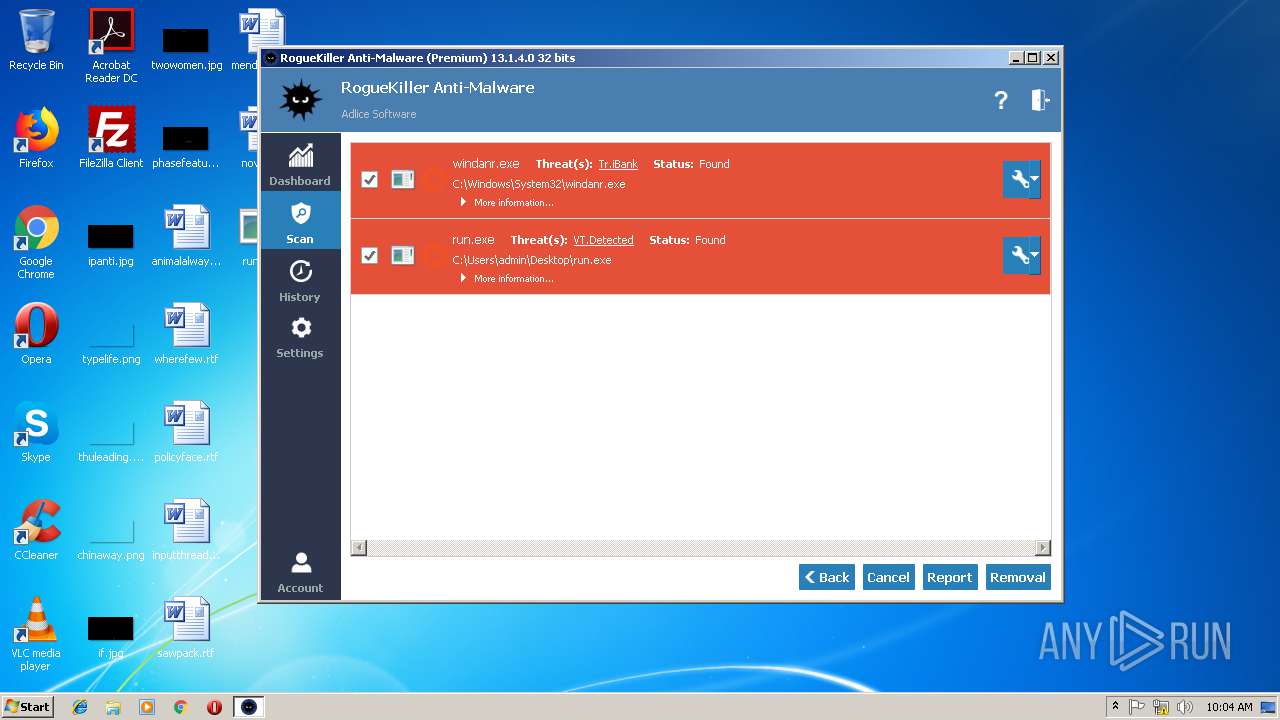
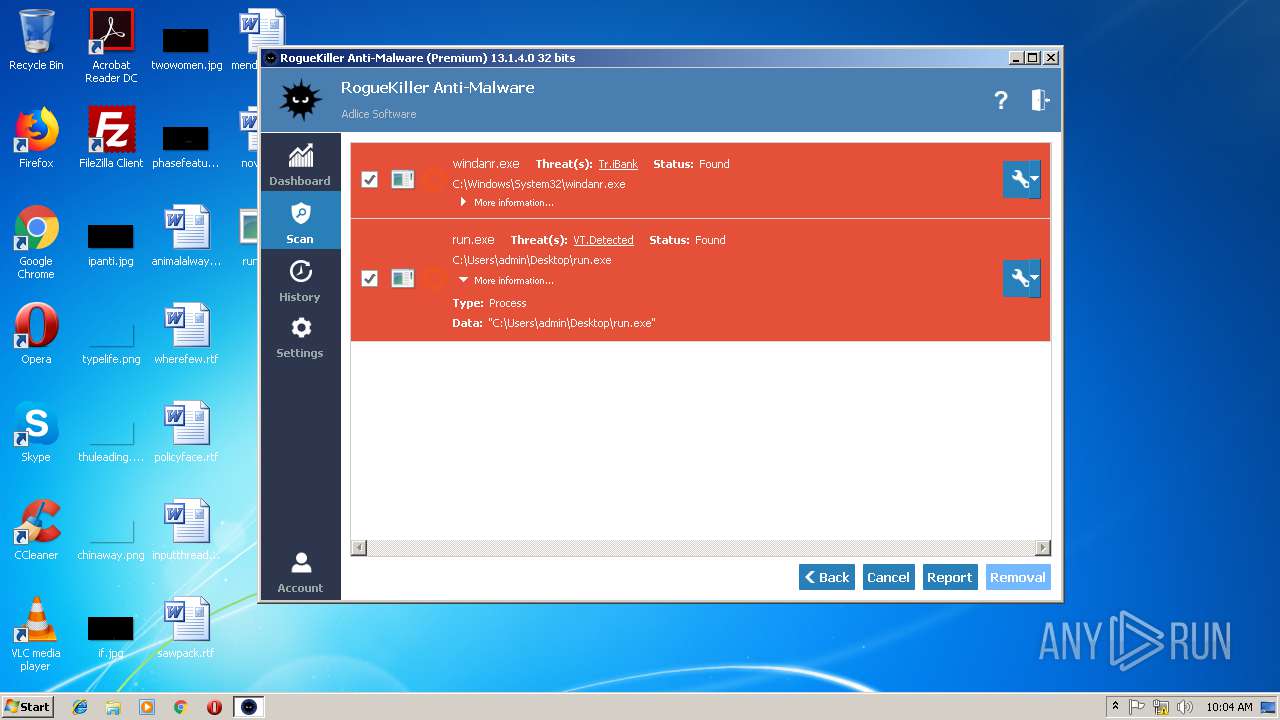
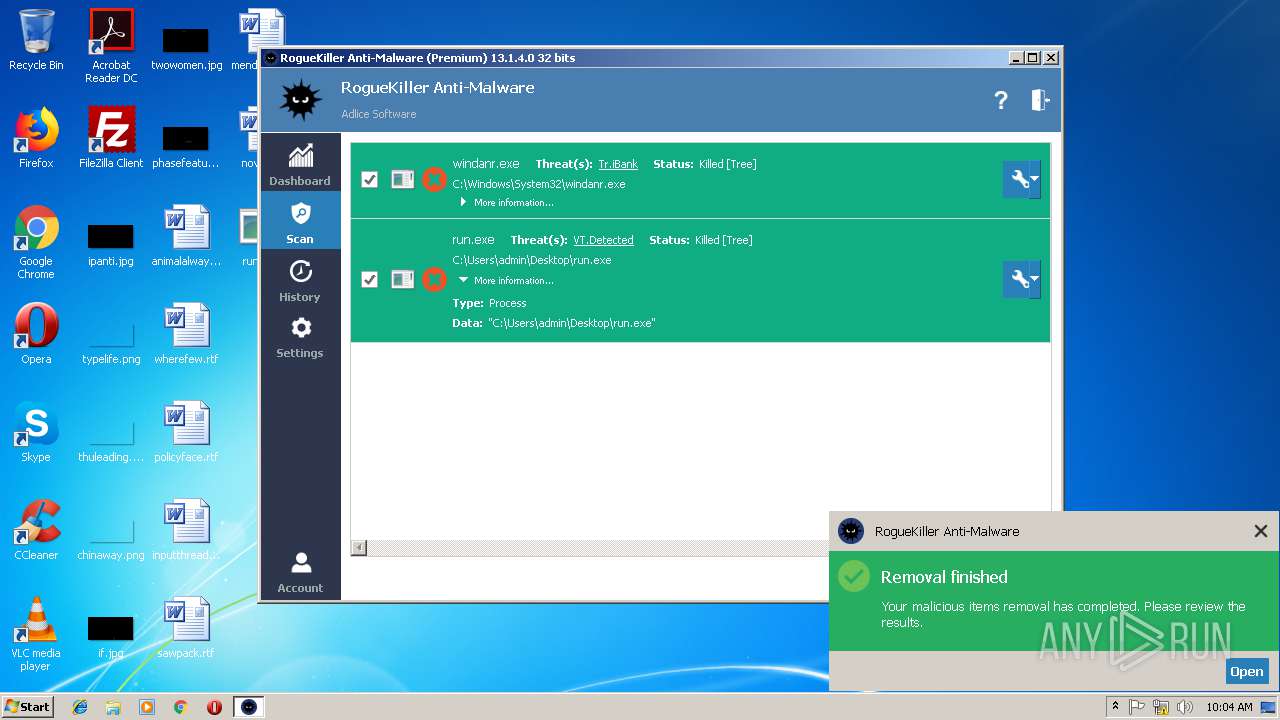
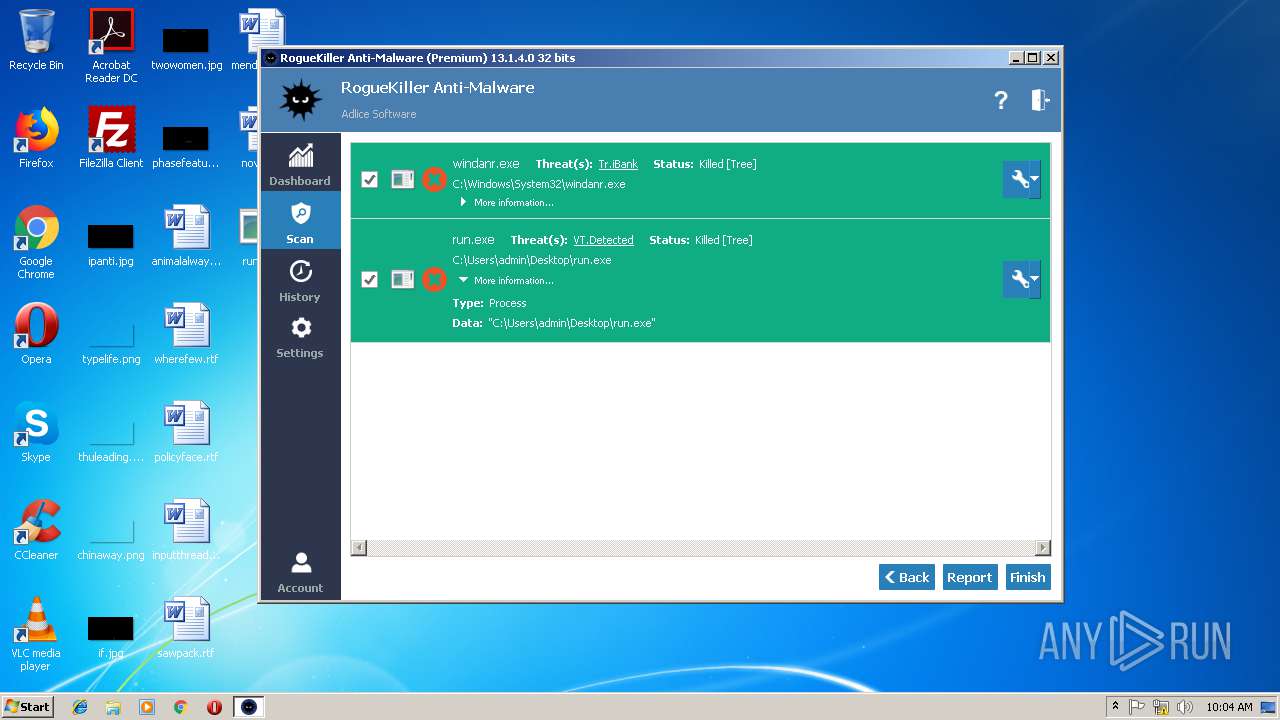
| File name: | run.exe |
| Full analysis: | https://app.any.run/tasks/b07c1781-db7c-475f-92e8-2bb0aa5cf743 |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 10:01:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | ABDE5FAA32C7E1E3F72D4A8414A90595 |
| SHA1: | 313FCF073C359BDD87699BD8871F7434FABB3912 |
| SHA256: | 3796F002F650AE13823881B997FB32695C43F4C0B24A9DBA2C2ABEF488EA90E8 |
| SSDEEP: | 1536:2ds5hj1XKppZu1qvklwM17MNoTFnxcOiI2U/RE3uJc01DQa+sxbIfCq9bTj8jwje:2dasqy4VwwPsxwutD6 |
MALICIOUS
Application was dropped or rewritten from another process
- RogueKiller_portable32.exe (PID: 3532)
- RogueKiller_portable32.exe (PID: 2196)
Loads the Task Scheduler DLL interface
- RogueKiller_portable32.exe (PID: 2196)
Loads the Task Scheduler COM API
- RogueKiller_portable32.exe (PID: 2196)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3404)
- RogueKiller_portable32.exe (PID: 2196)
Low-level read access rights to disk partition
- RogueKiller_portable32.exe (PID: 2196)
Starts Internet Explorer
- RogueKiller_portable32.exe (PID: 2196)
Creates files in the program directory
- RogueKiller_portable32.exe (PID: 2196)
Creates files in the driver directory
- RogueKiller_portable32.exe (PID: 2196)
Creates or modifies windows services
- RogueKiller_portable32.exe (PID: 2196)
Removes files from Windows directory
- RogueKiller_portable32.exe (PID: 2196)
Creates files in the Windows directory
- RogueKiller_portable32.exe (PID: 2196)
INFO
Application launched itself
- chrome.exe (PID: 3404)
- iexplore.exe (PID: 3828)
Reads settings of System Certificates
- chrome.exe (PID: 3404)
- RogueKiller_portable32.exe (PID: 2196)
Reads Internet Cache Settings
- chrome.exe (PID: 3404)
- iexplore.exe (PID: 120)
Changes internet zones settings
- iexplore.exe (PID: 3828)
Creates files in the user directory
- iexplore.exe (PID: 120)
Reads internet explorer settings
- iexplore.exe (PID: 120)
Changes settings of System certificates
- iexplore.exe (PID: 120)
Adds / modifies Windows certificates
- iexplore.exe (PID: 120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (81) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.2) |
| .exe | | | Win32 Executable (generic) (4.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.2) |
| .exe | | | Generic Win/DOS Executable (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:03:07 14:11:10+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 1335296 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14746e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | burun_crypted.exe |
| LegalCopyright: | |
| OriginalFileName: | burun_crypted.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Mar-2018 13:11:10 |
| FileDescription: | - |
| FileVersion: | 0.0.0.0 |
| InternalName: | burun_crypted.exe |
| LegalCopyright: | - |
| OriginalFilename: | burun_crypted.exe |
| ProductVersion: | 0.0.0.0 |
| Assembly Version: | 0.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 07-Mar-2018 13:11:10 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00145474 | 0x00146000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 2.63229 |
.rsrc | 0x00148000 | 0x000004F0 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.7354 |
.reloc | 0x0014A000 | 0x0000000C | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0159202 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
52
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3828 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x70fe00b0,0x70fe00c0,0x70fe00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,17170333904607081527,6615956900840194279,131072 --enable-features=PasswordImport --service-pipe-token=A39092A314A87960878B9F6491D3D0C8 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=A39092A314A87960878B9F6491D3D0C8 --renderer-client-id=3 --mojo-platform-channel-handle=2116 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2196 | "C:\Users\admin\Downloads\RogueKiller_portable32.exe" | C:\Users\admin\Downloads\RogueKiller_portable32.exe | chrome.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,17170333904607081527,6615956900840194279,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=0719E7CFF4BB17162F342DB320807D11 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=0719E7CFF4BB17162F342DB320807D11 --renderer-client-id=7 --mojo-platform-channel-handle=3832 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=980,17170333904607081527,6615956900840194279,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=A90DEC7C08B4E509C0B629B9A944A198 --mojo-platform-channel-handle=1008 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,17170333904607081527,6615956900840194279,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=A8E680276206AC333532FCDFD0D527B9 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=A8E680276206AC333532FCDFD0D527B9 --renderer-client-id=6 --mojo-platform-channel-handle=2744 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3084 | "C:\Users\admin\Desktop\run.exe" | C:\Users\admin\Desktop\run.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,17170333904607081527,6615956900840194279,131072 --enable-features=PasswordImport --service-pipe-token=96B5EA4FCA894EBD9E141B4508EBFAB2 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=96B5EA4FCA894EBD9E141B4508EBFAB2 --renderer-client-id=5 --mojo-platform-channel-handle=1776 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
997
Read events
856
Write events
137
Delete events
4
Modification events
| (PID) Process: | (3452) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3404-13194352947126250 |
Value: 259 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3404-13194352947126250 |
Value: 259 | |||
| (PID) Process: | (3404) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
4
Suspicious files
81
Text files
118
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\73e7ee4c-d2f6-45ae-8226-bad75183417c.tmp | — | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\e1ea4de1-4191-45c4-a084-1c7de1716820.tmp | — | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF24de1c.TMP | text | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3404 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF24de2b.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
48
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3828 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3404 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
3404 | chrome.exe | 216.58.207.74:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3404 | chrome.exe | 216.58.206.4:443 | www.google.com | Google Inc. | US | whitelisted |
3404 | chrome.exe | 172.217.23.174:443 | apis.google.com | Google Inc. | US | whitelisted |
3404 | chrome.exe | 172.217.23.142:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3404 | chrome.exe | 178.33.106.117:443 | download.adlice.com | OVH SAS | FR | suspicious |
2196 | RogueKiller_portable32.exe | 178.33.106.117:443 | download.adlice.com | OVH SAS | FR | suspicious |
3828 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
120 | iexplore.exe | 104.27.165.26:443 | adlice.com | Cloudflare Inc | US | shared |
120 | iexplore.exe | 104.19.197.151:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.de |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
download.adlice.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|
RogueKiller_portable32.exe | libpng warning: iCCP: known incorrect sRGB profile
|