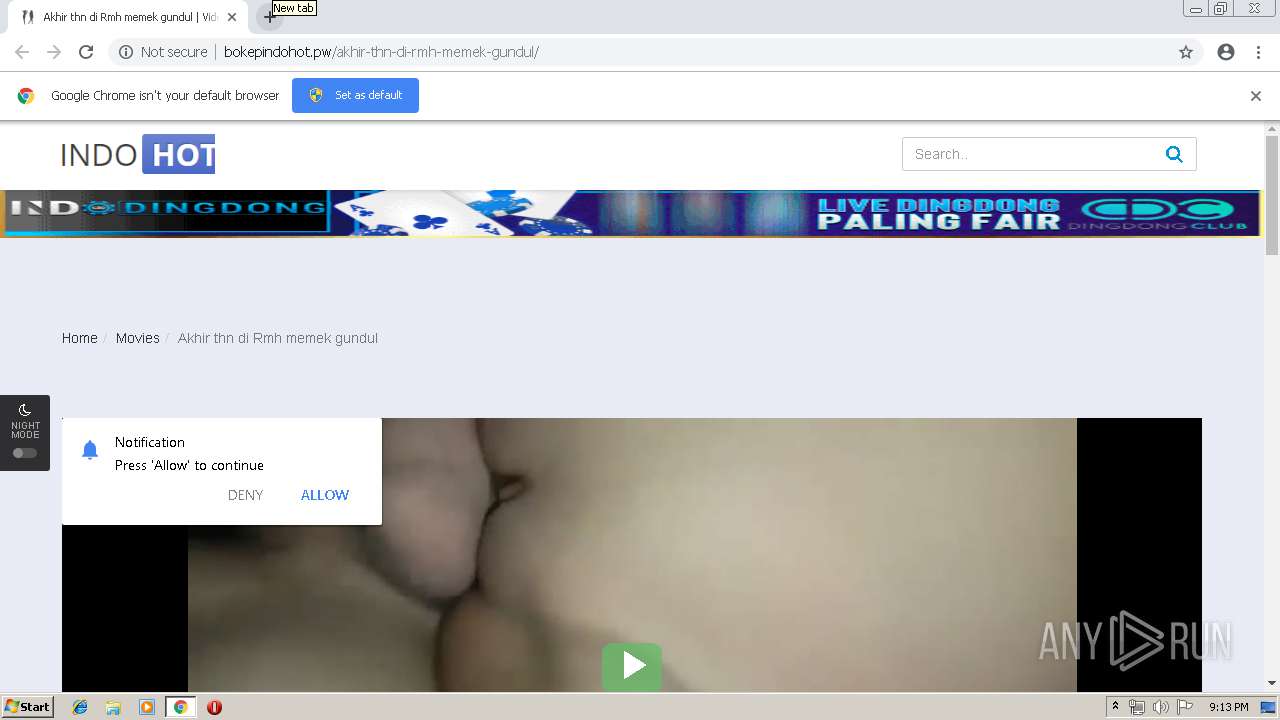
| URL: | http://bokepindohot.pw/akhir-thn-di-rmh-memek-gundul/ |
| Full analysis: | https://app.any.run/tasks/c1b0c8e0-9165-41db-b7c6-5992f64753f6 |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2019, 20:12:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A93C84B5394B48461D75B97EB0AE9388 |
| SHA1: | DA750E20203F2B8929FA8C22CD6594F224F15C2C |
| SHA256: | 3795CA7DEC6B6610865520F2788F3522B04391CEF2DA1AB2B7E22FB92B3DB473 |
| SSDEEP: | 3:N1KcqmXRDNM9JYNI99OYL+K:CcqYeHYeH1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2500)
INFO
Application launched itself
- chrome.exe (PID: 2500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
69
Monitored processes
37
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13853625086844595868 --mojo-platform-channel-handle=7156 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=7570123800898200112 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7570123800898200112 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=7324 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=17690115300962028631 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17690115300962028631 --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2800 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=14539850698657224298 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14539850698657224298 --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6588 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=1928788862835680509 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1928788862835680509 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2212 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10177731926244541586 --mojo-platform-channel-handle=4264 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=14609058388320895787 --mojo-platform-channel-handle=944 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=2437381911578306513 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2437381911578306513 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5456 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=9808107122485168075 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9808107122485168075 --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=7392 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9037503199192391013,17441929269186721718,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=13214406997096287140 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13214406997096287140 --renderer-client-id=13 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5624 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
563
Read events
476
Write events
83
Delete events
4
Modification events
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2500-13202338353113375 |
Value: 259 | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (2500) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
182
Text files
172
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\46d32b03-a50e-421c-8635-ce311b35b710.tmp | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2500 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
113
DNS requests
66
Threats
40
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/akhir-thn-di-rmh-memek-gundul/ | US | html | 11.0 Kb | whitelisted |
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/wp-content/themes/PsyPlay1.2.1sEEhd/css/main.css?ver=1.2.1%20Autoembed%20by%20goldregister | US | text | 21.5 Kb | whitelisted |
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/wp-content/themes/PsyPlay1.2.1sEEhd/css/custom.css?ver=1.2.1%20Autoembed%20by%20goldregister | US | text | 1.89 Kb | whitelisted |
2500 | chrome.exe | GET | 200 | 172.217.16.129:80 | http://2.bp.blogspot.com/-ExIjRkqW520/XLGLbZo1l4I/AAAAAAAADo4/agZ7130o-8w-Bcn8R8VRg1oc_gnYN_t7ACLcBGAs/s1600/duniavegas88com.gif | US | image | 478 Kb | whitelisted |
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/wp-content/cache/fvm/1557853694/out/header-c99c14b7.min.css | US | text | 4.73 Kb | whitelisted |
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/wp-content/cache/fvm/1557853694/out/header-63ab0886.min.js | US | text | 480 b | whitelisted |
2500 | chrome.exe | GET | 200 | 172.217.16.129:80 | http://2.bp.blogspot.com/-jFNySLSYlrQ/XLGMB8sYA4I/AAAAAAAADpA/KhIcXHrlUHcjypSJRs1iG4UfhyeMaVyfACLcBGAs/s1600/qqdingdongcom.gif | US | image | 409 Kb | whitelisted |
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/wp-content/themes/PsyPlay1.2.1sEEhd/js/jquery.idTabs.min.js?ver=1.2.1%20Autoembed%20by%20goldregister | US | text | 937 b | whitelisted |
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/wp-content/themes/PsyPlay1.2.1sEEhd/js/psyplay.custom.min.js?ver=1.2.1%20Autoembed%20by%20goldregister | US | text | 1.13 Kb | whitelisted |
2500 | chrome.exe | GET | 200 | 104.248.150.156:80 | http://bokepindohot.pw/wp-content/themes/PsyPlay1.2.1sEEhd/css/jquery.qtip.min.css?ver=1.2.1%20Autoembed%20by%20goldregister | US | text | 2.10 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.217.16.129:80 | 2.bp.blogspot.com | Google Inc. | US | whitelisted |
2500 | chrome.exe | 172.217.23.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
— | — | 143.204.98.107:80 | xslt.alexa.com | — | US | whitelisted |
2500 | chrome.exe | 157.240.1.23:443 | connect.facebook.net | Facebook, Inc. | US | whitelisted |
2500 | chrome.exe | 46.105.201.240:80 | s10.histats.com | OVH SAS | FR | suspicious |
2500 | chrome.exe | 172.217.22.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2500 | chrome.exe | 216.58.208.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
2500 | chrome.exe | 104.248.150.156:80 | bokepindohot.pw | — | US | suspicious |
2500 | chrome.exe | 216.58.206.10:80 | ajax.googleapis.com | Google Inc. | US | whitelisted |
2500 | chrome.exe | 172.217.16.129:80 | 2.bp.blogspot.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
bokepindohot.pw |
| whitelisted |
accounts.google.com |
| shared |
ajax.googleapis.com |
| whitelisted |
2.bp.blogspot.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
xslt.alexa.com |
| whitelisted |
gratisan.pw |
| suspicious |
vidoza.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1068 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2500 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |