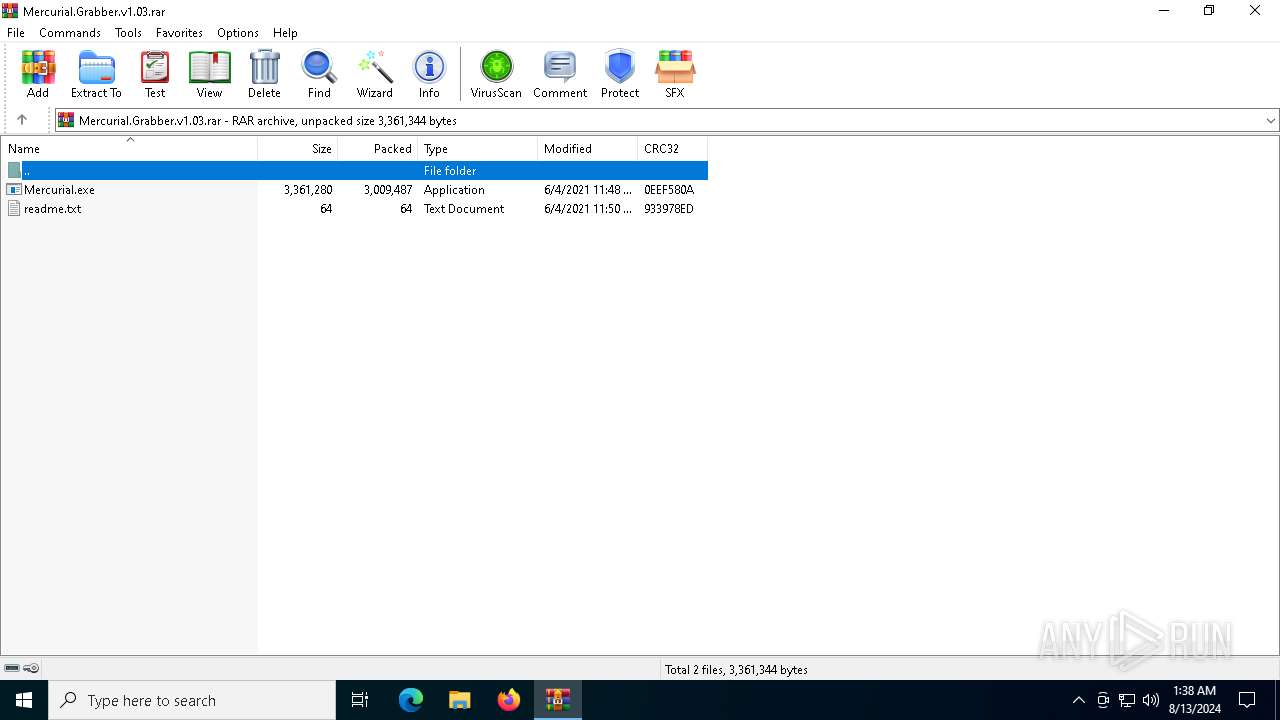
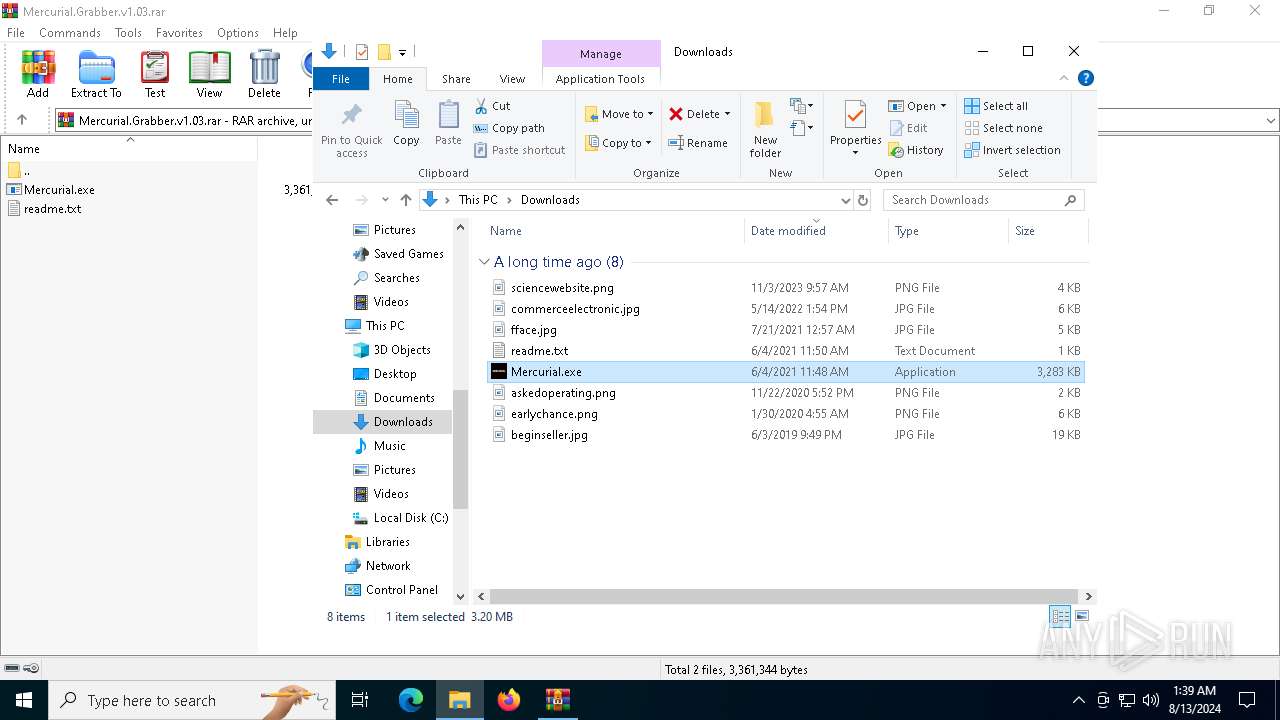
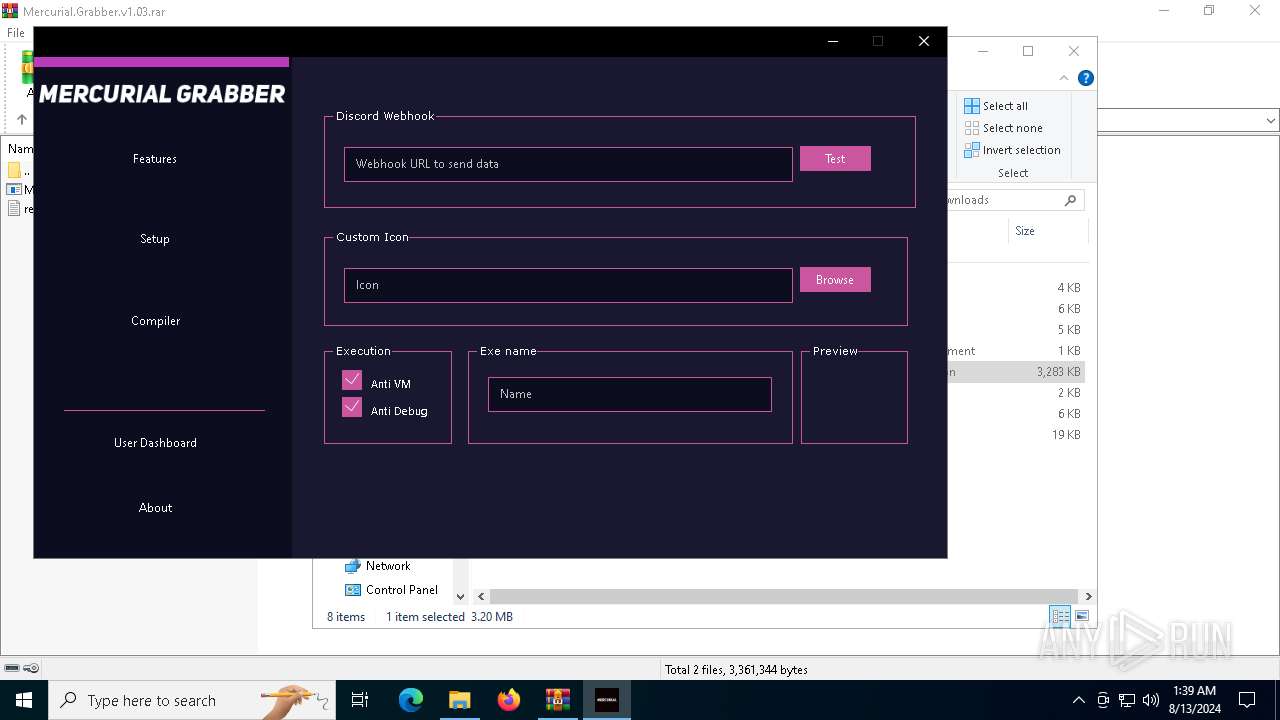
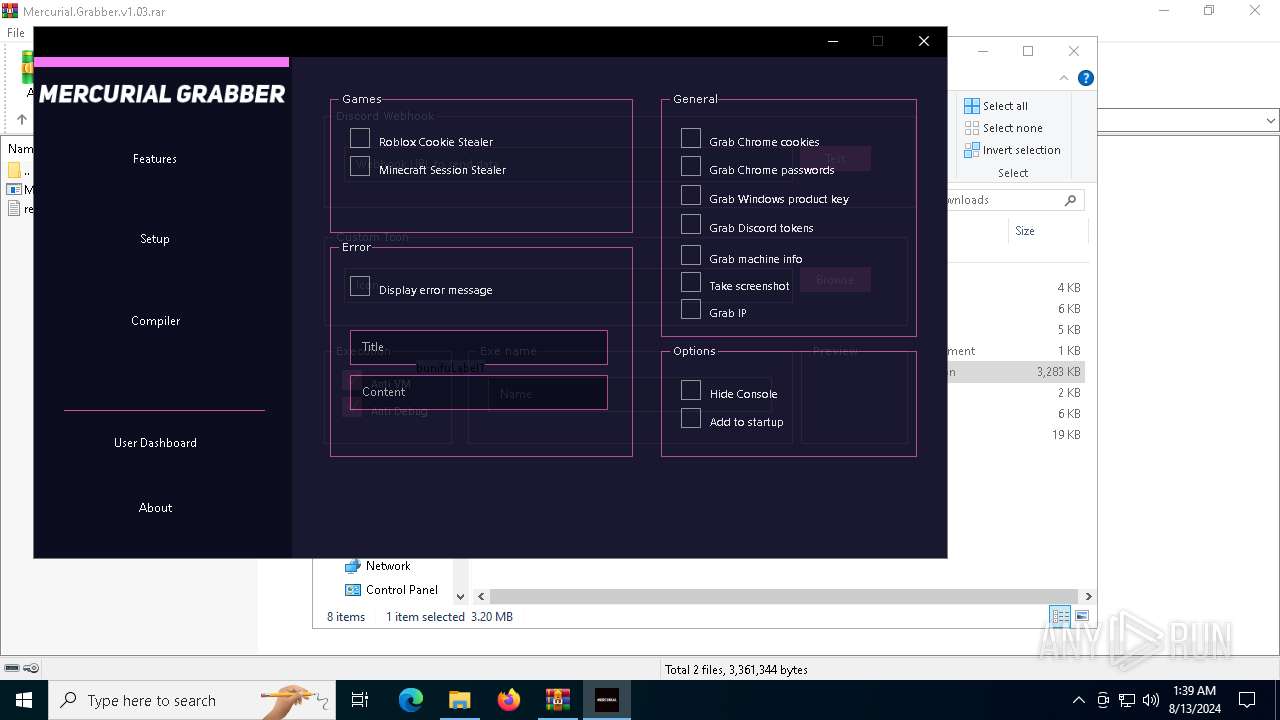
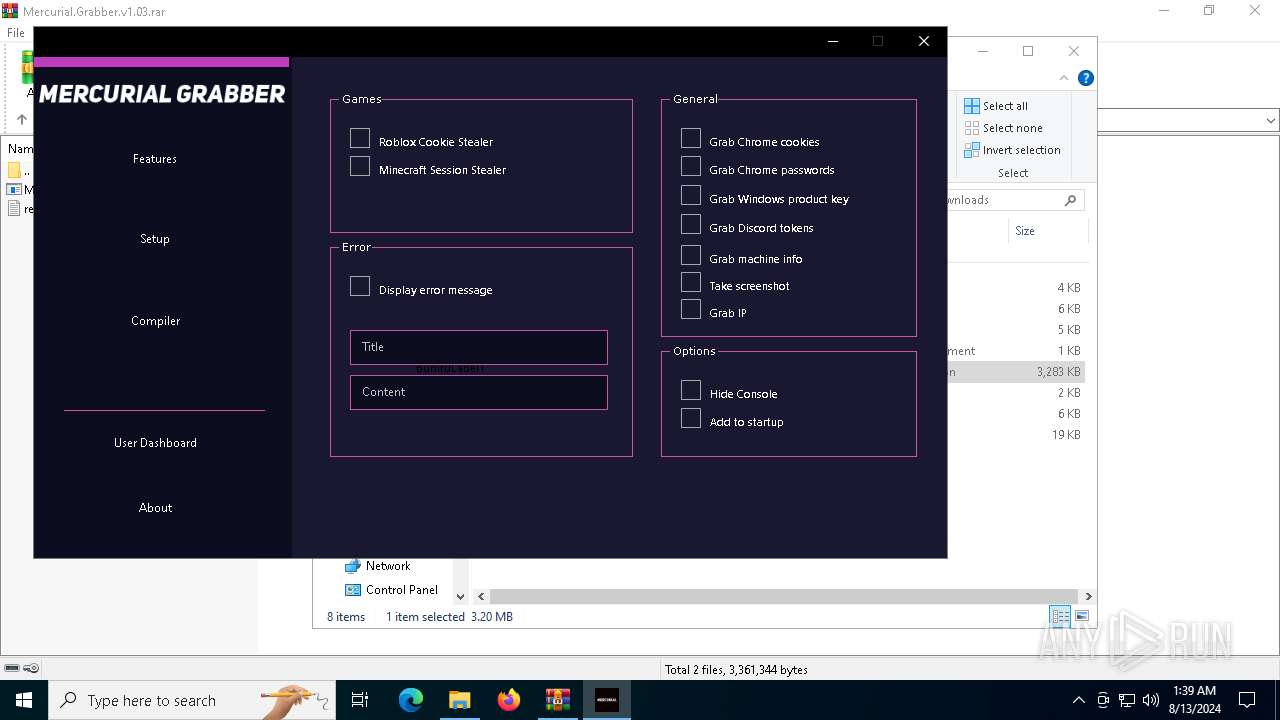
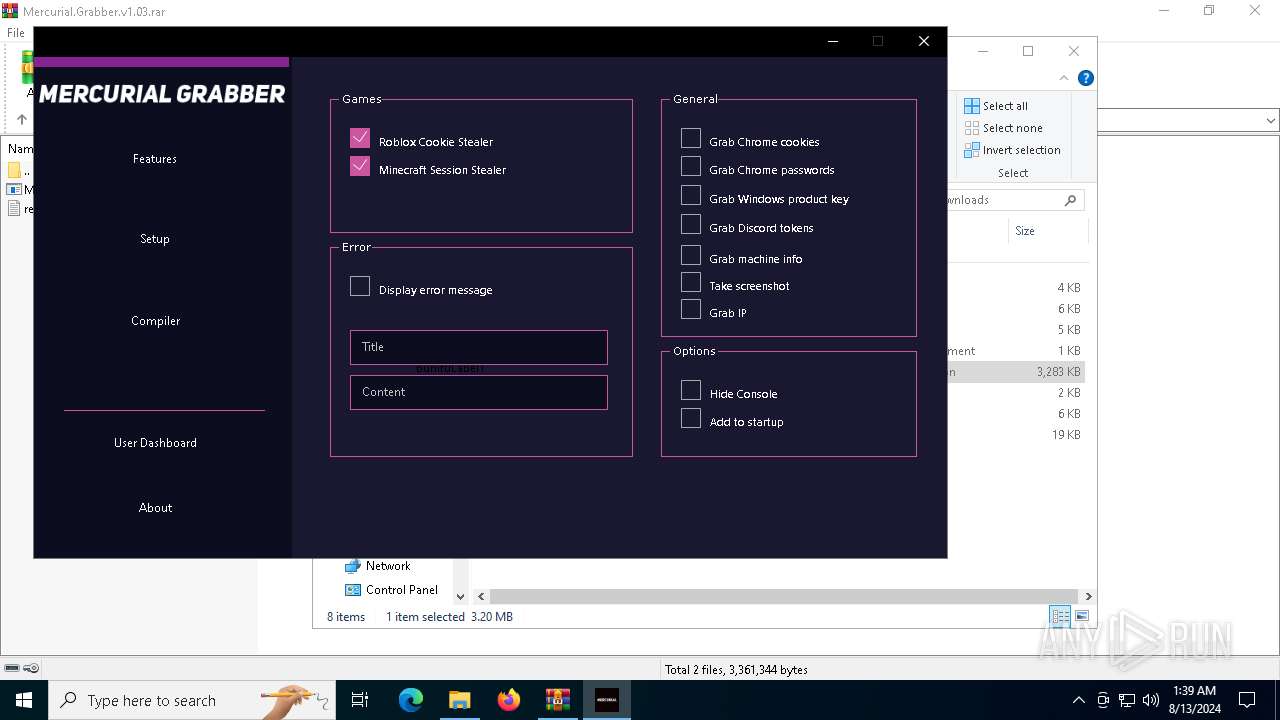
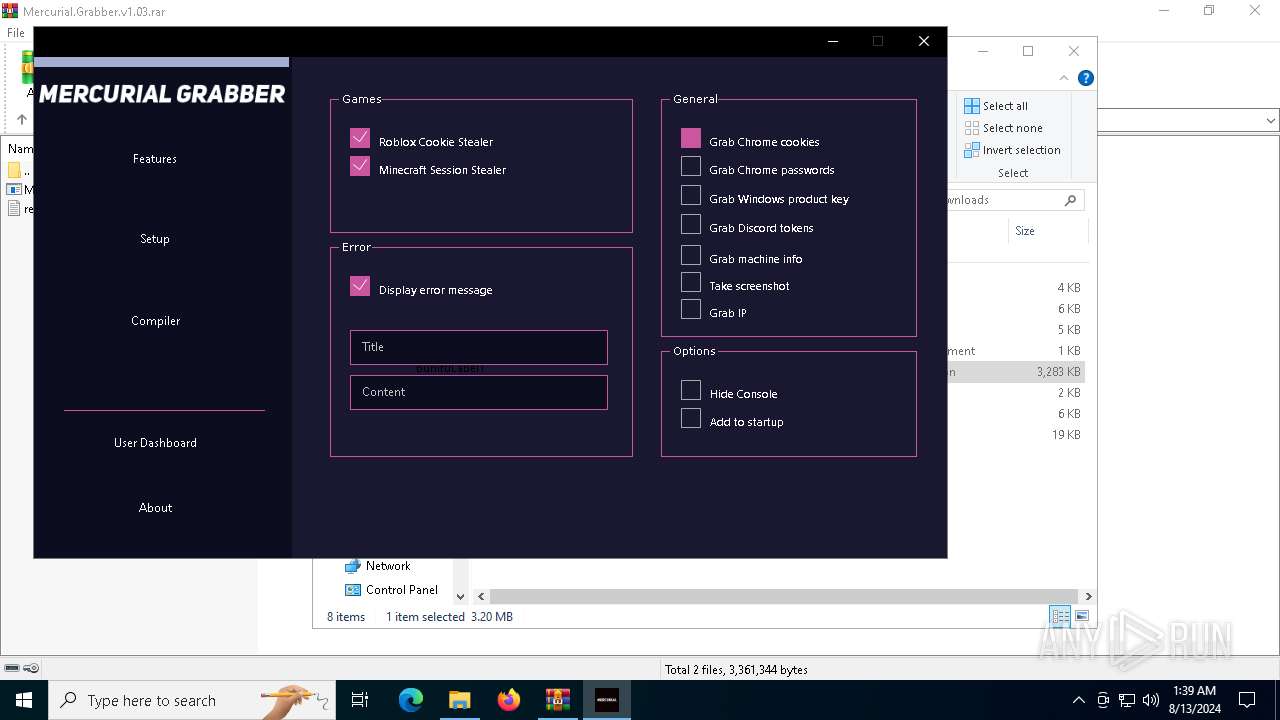
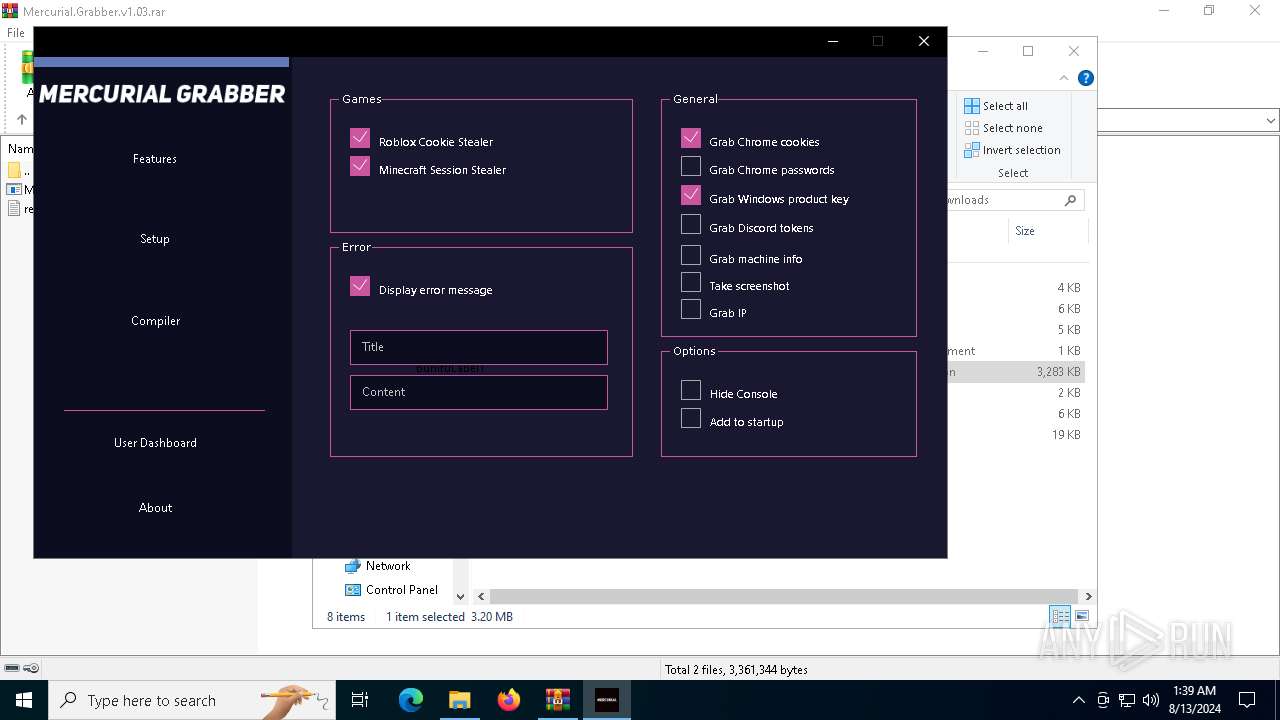
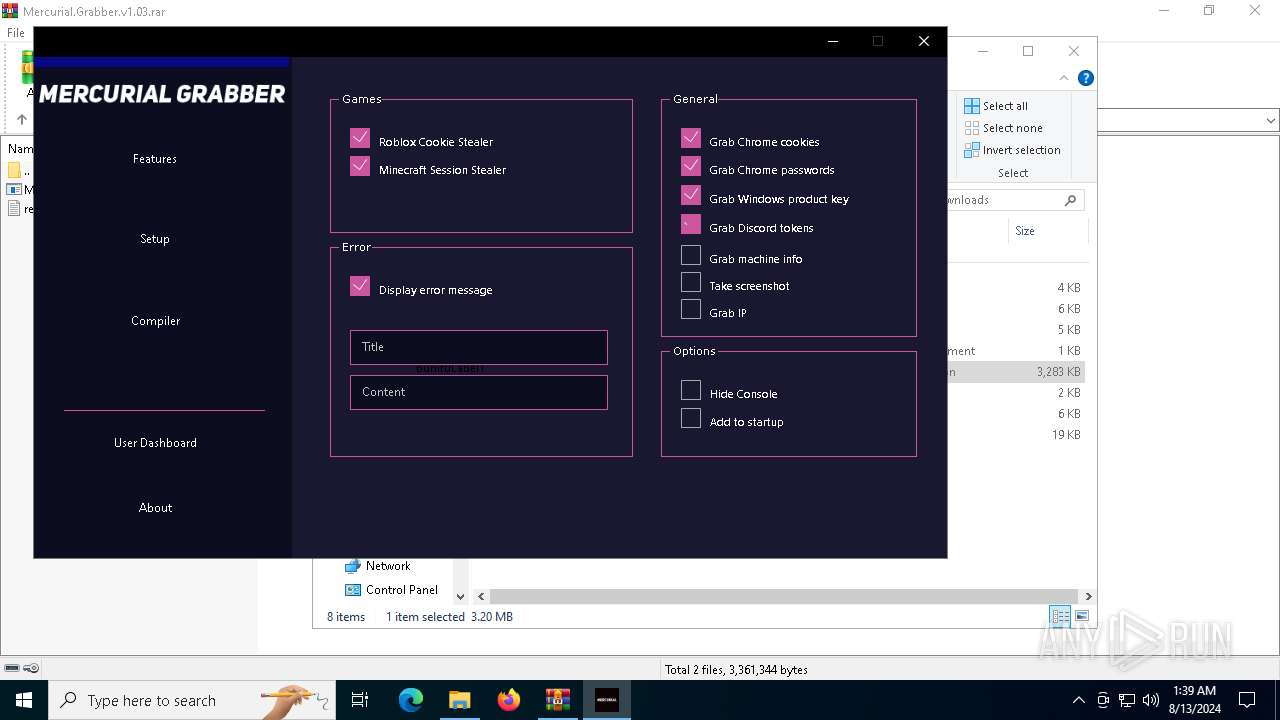
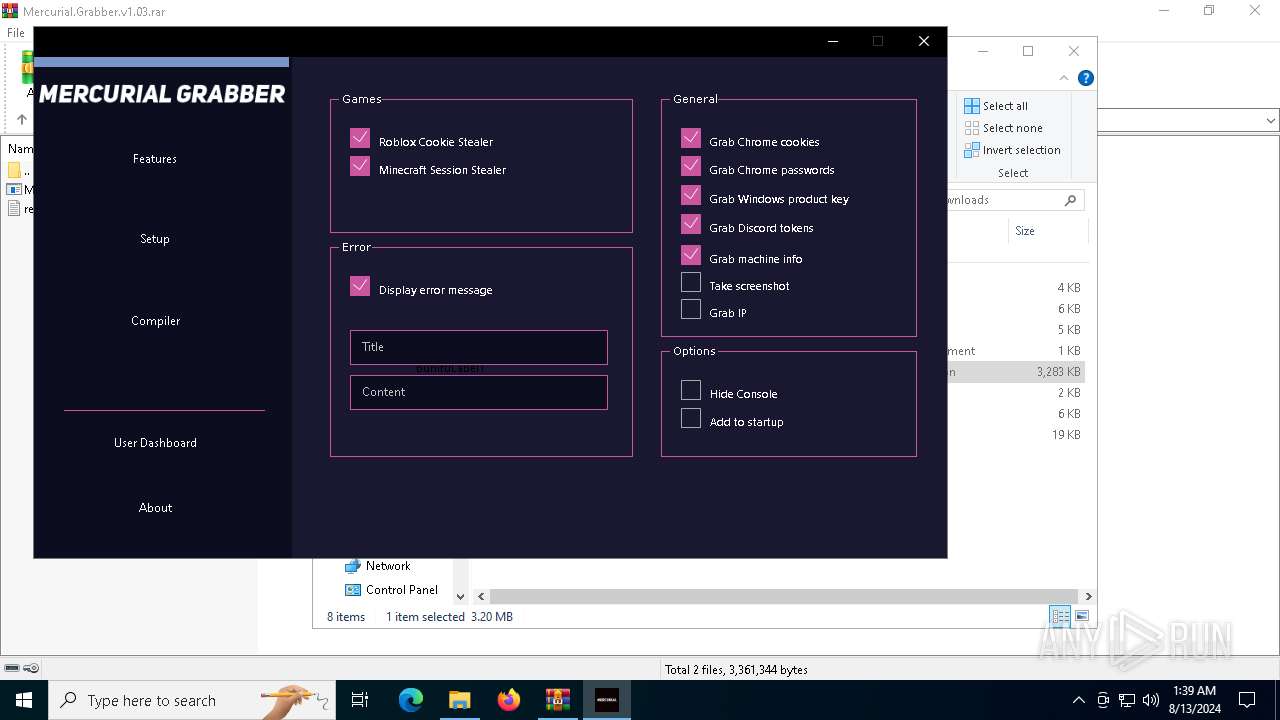
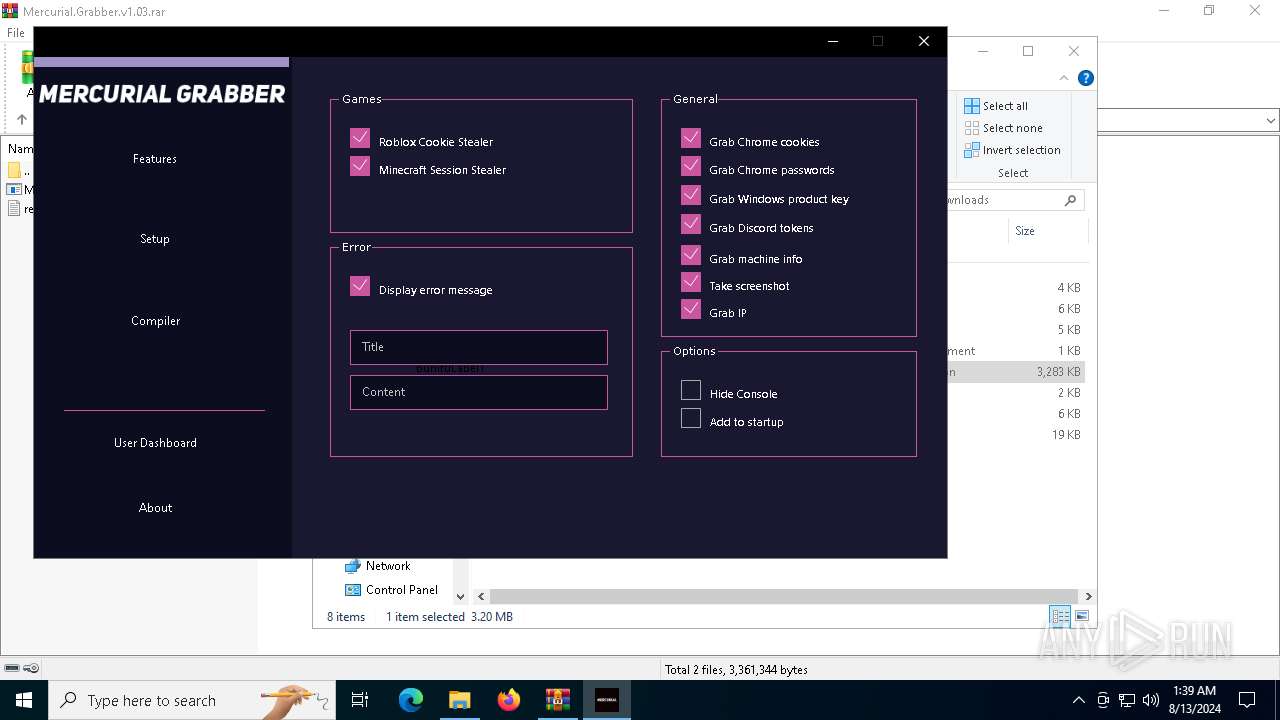
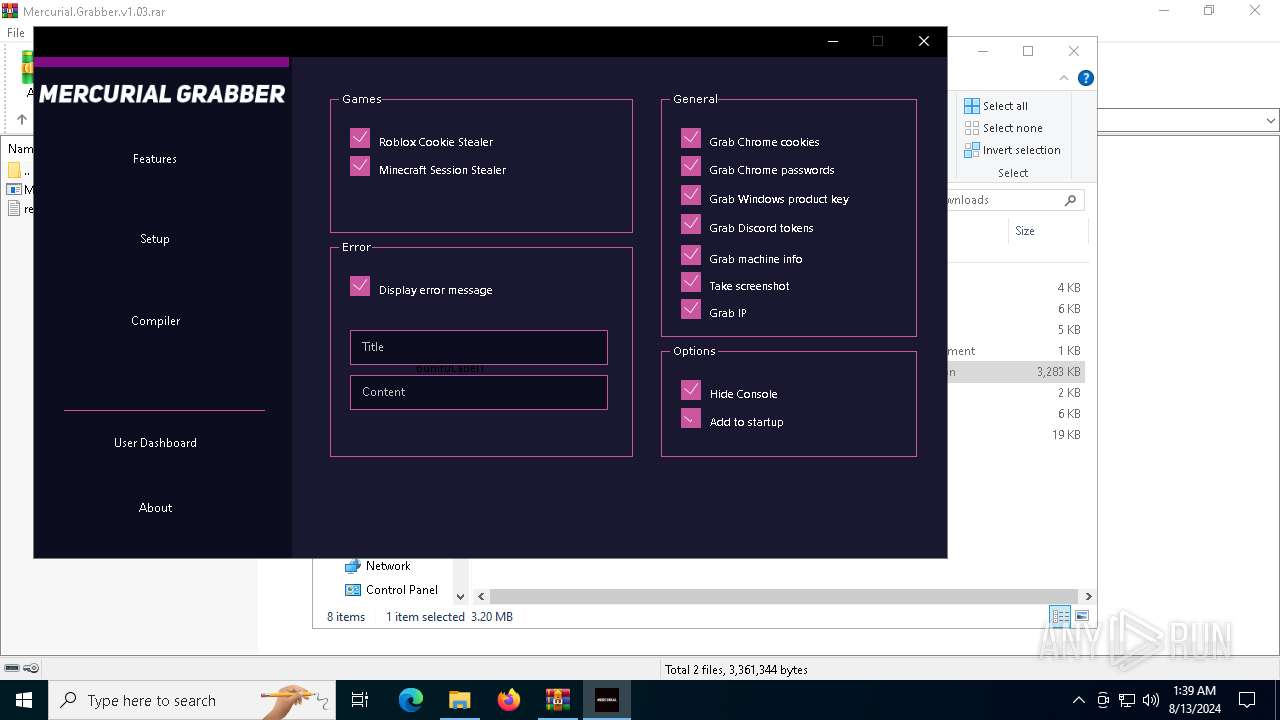
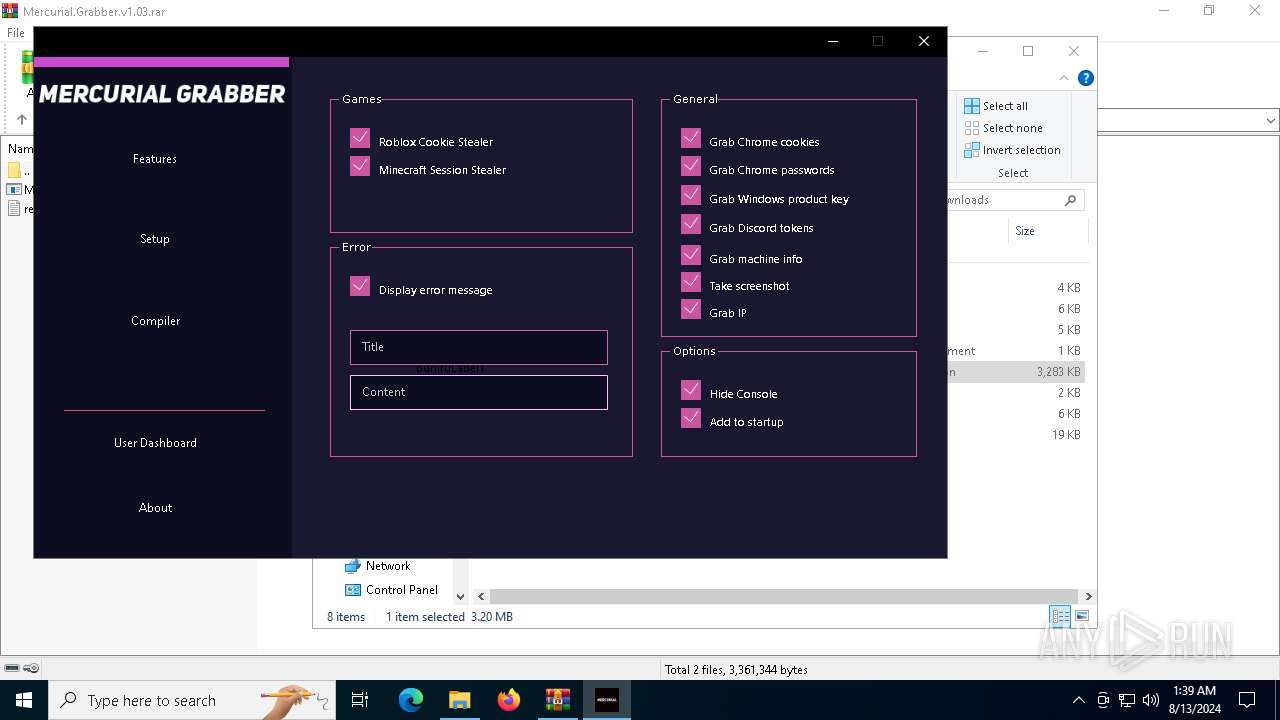
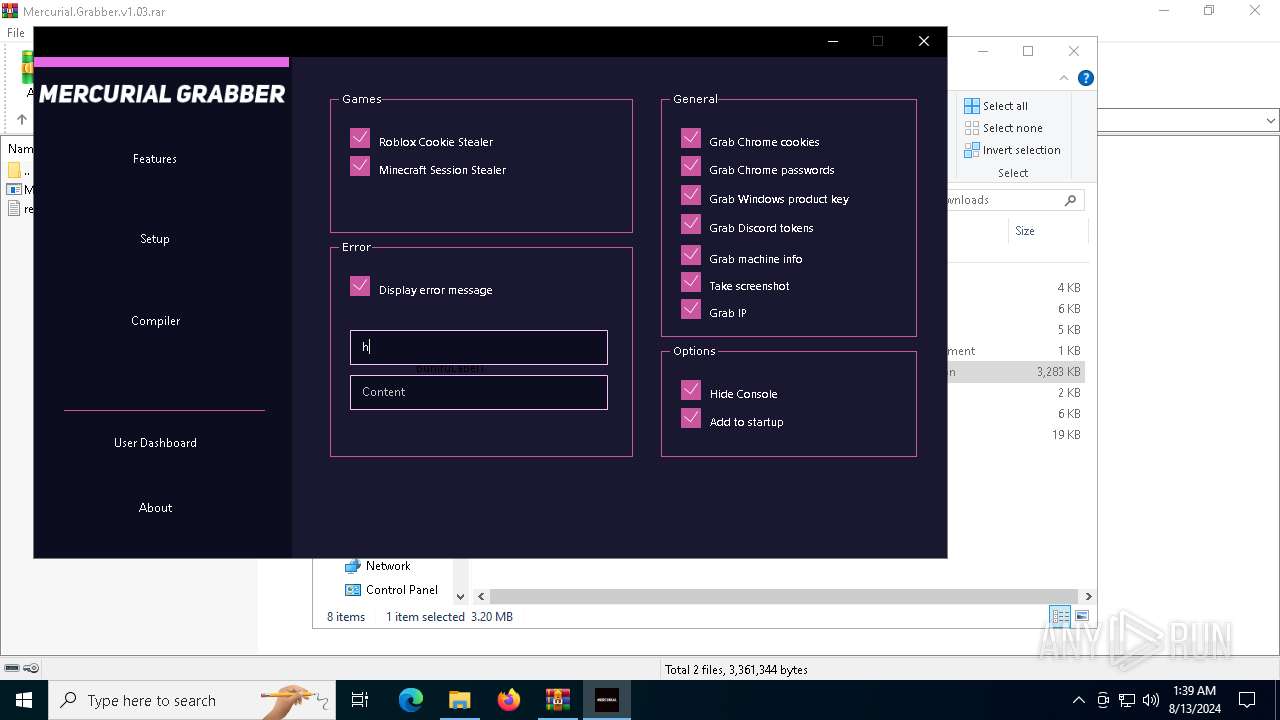
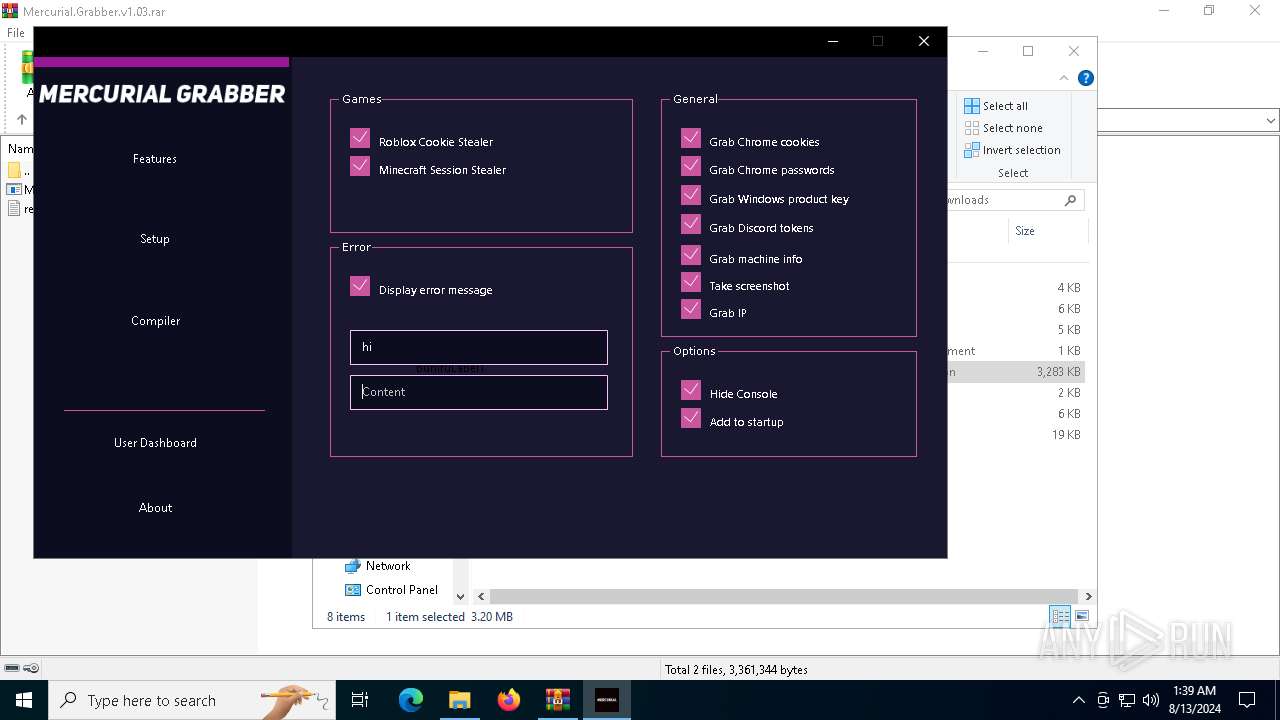
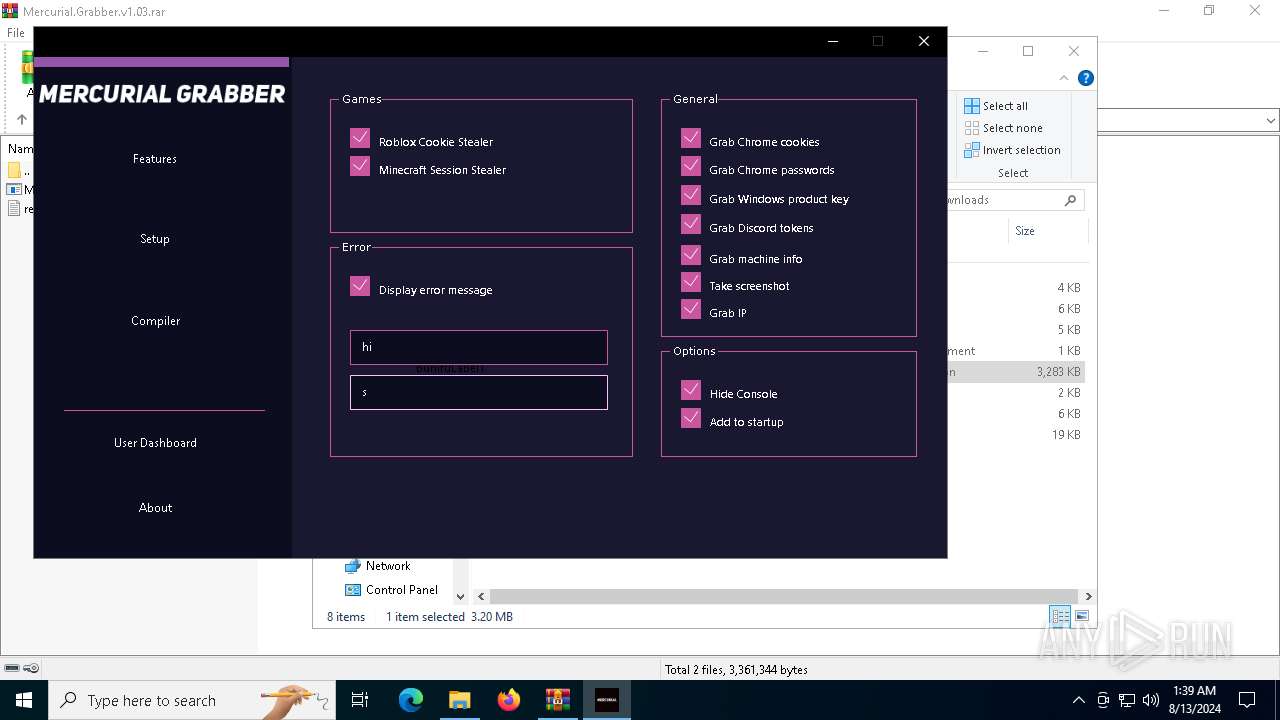
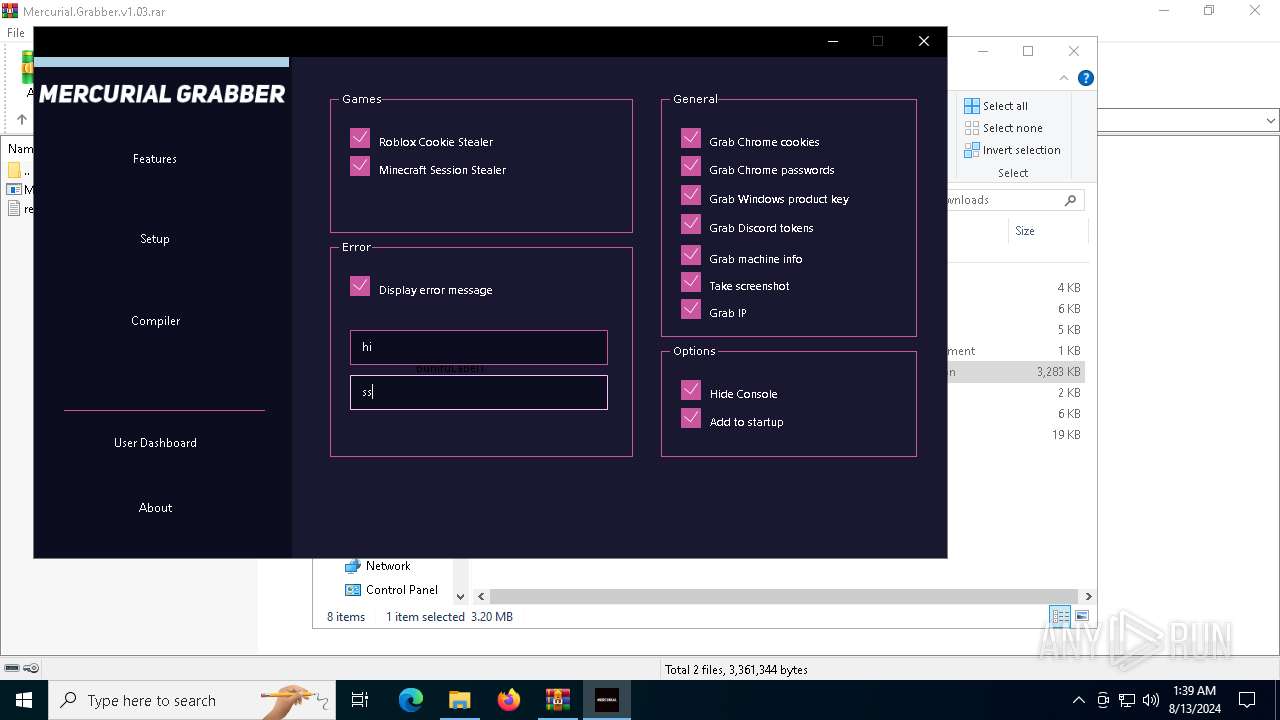
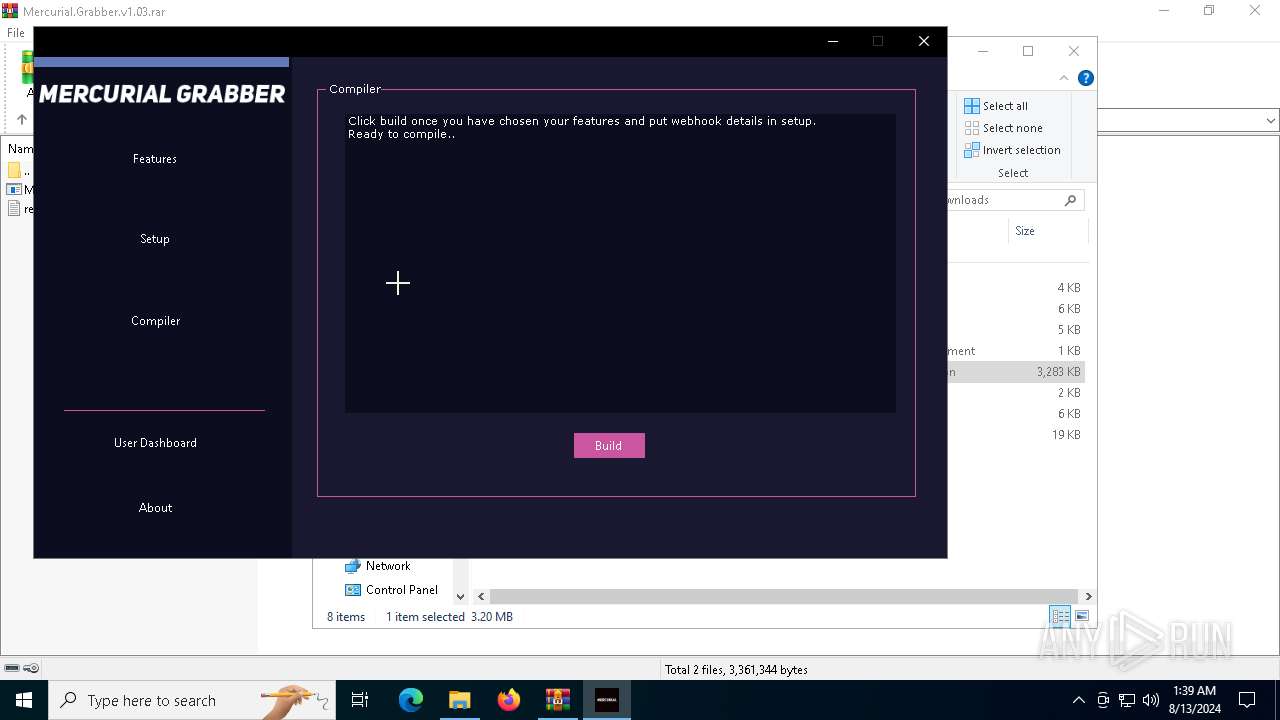
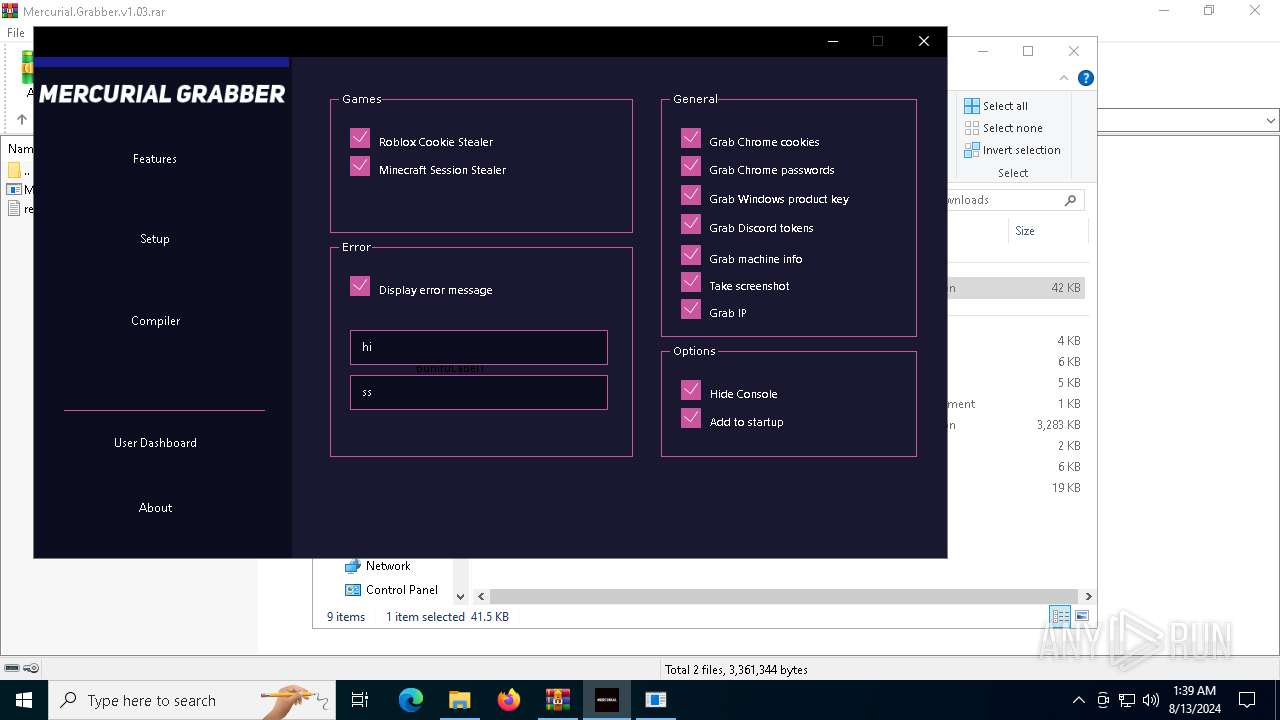
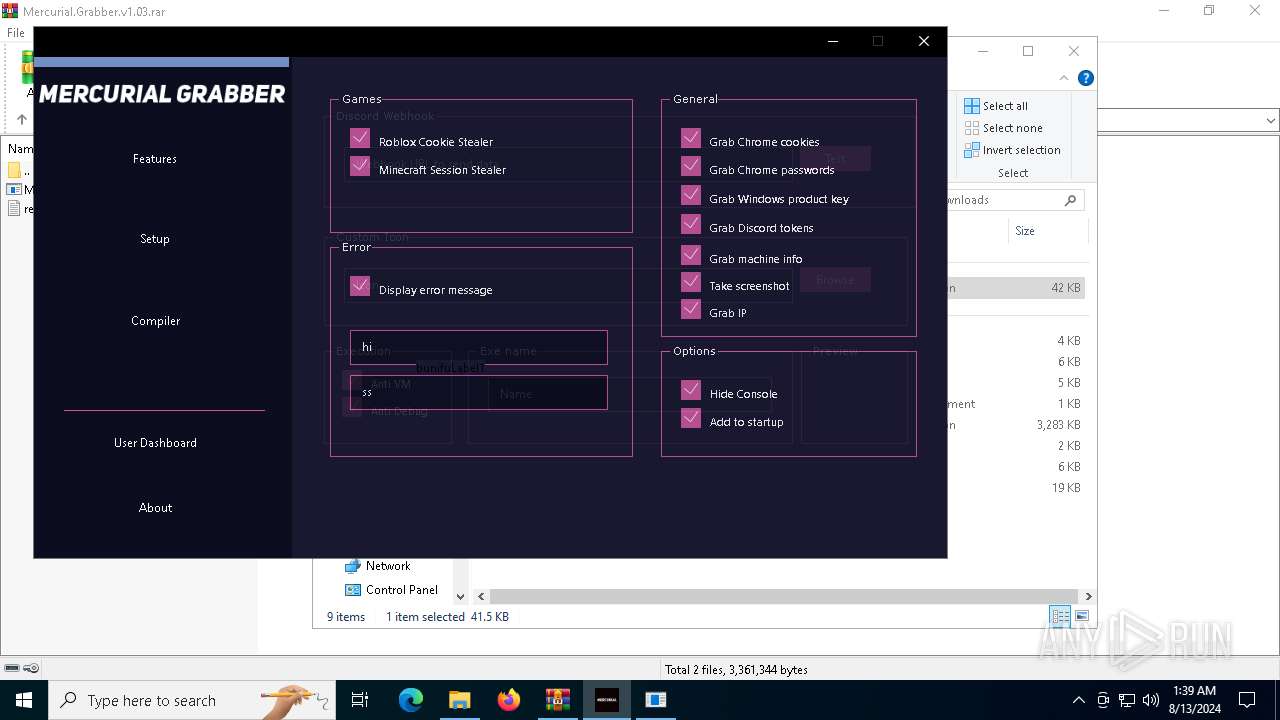
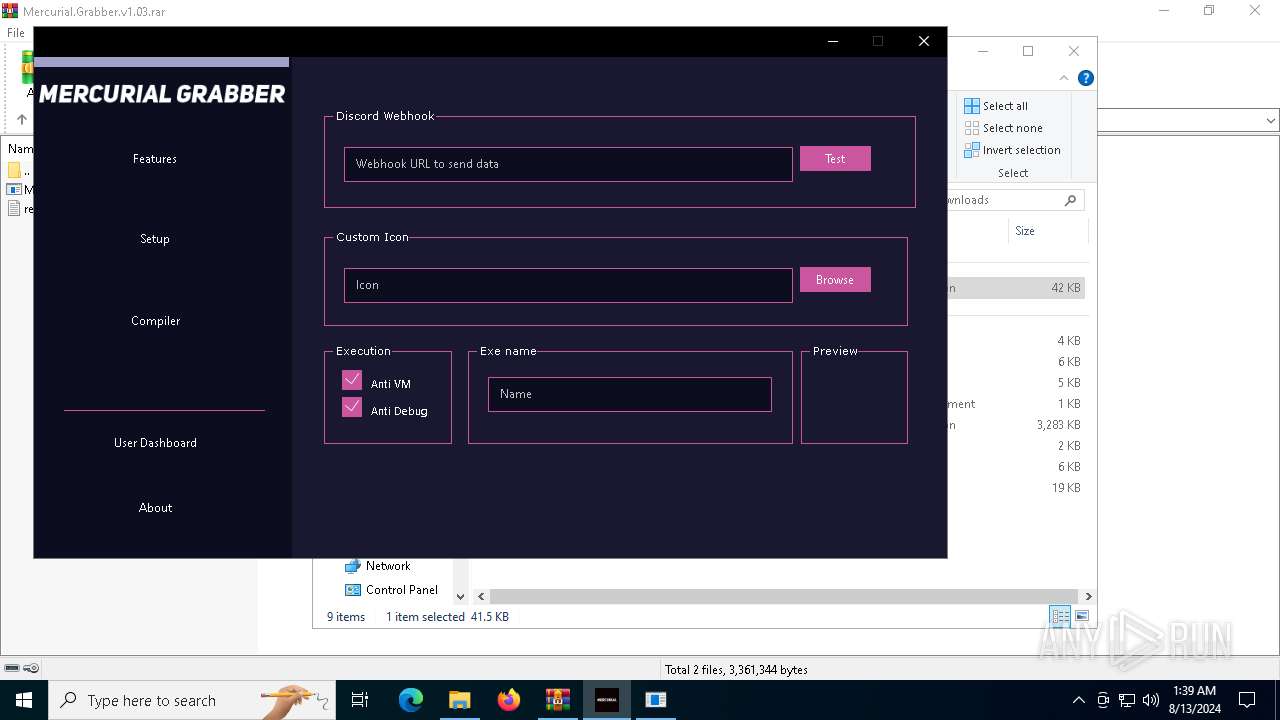
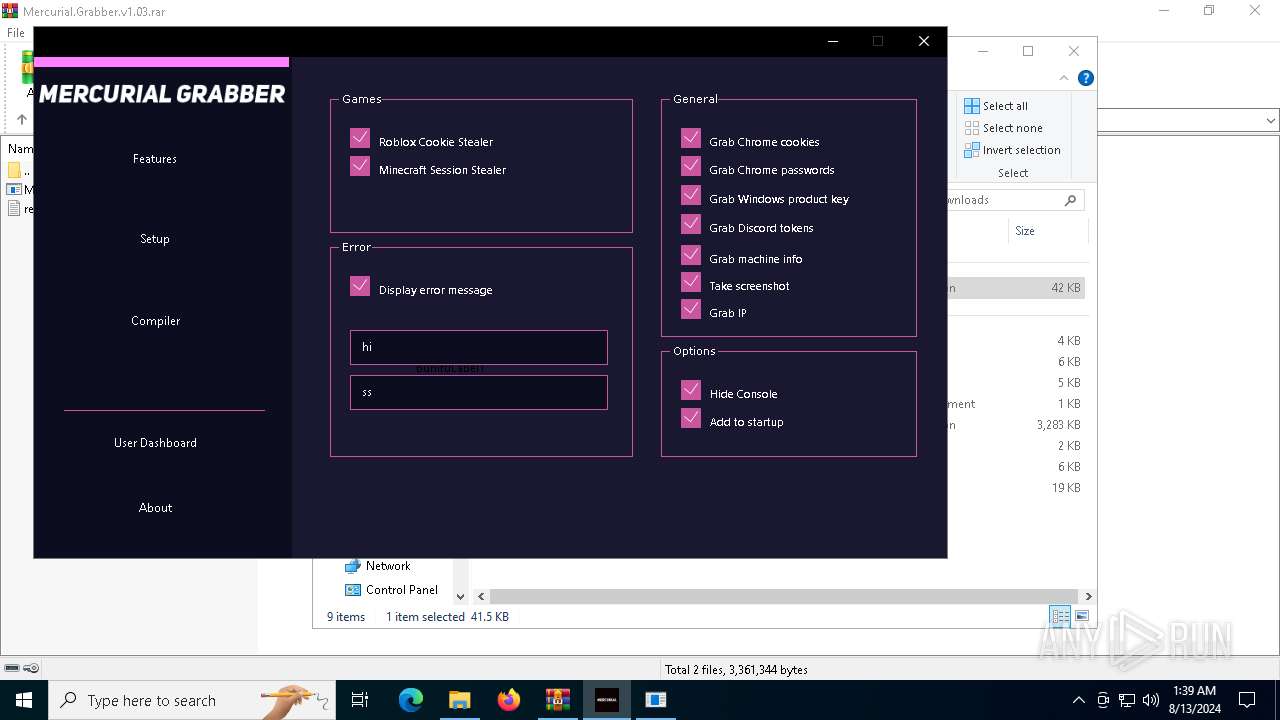
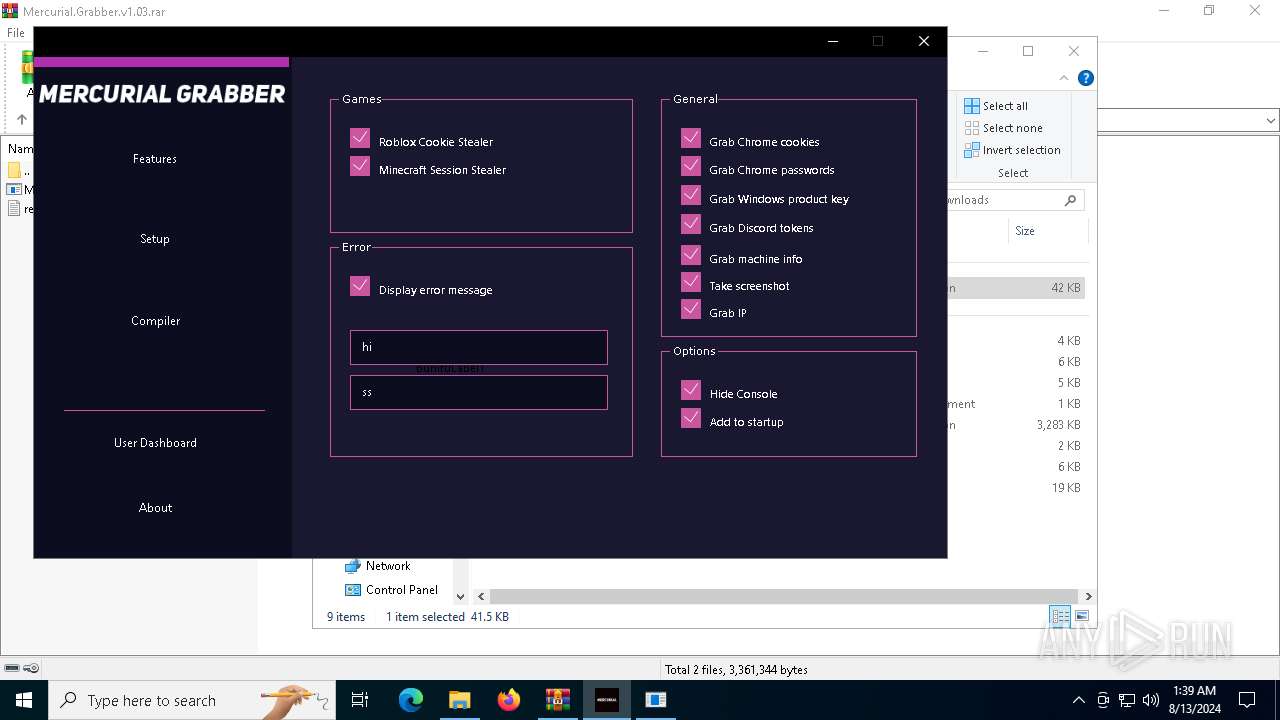
| File name: | Mercurial.Grabber.v1.03.rar |
| Full analysis: | https://app.any.run/tasks/945d5269-7d27-4e0e-87dd-33cc2f8526d6 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2024, 01:38:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
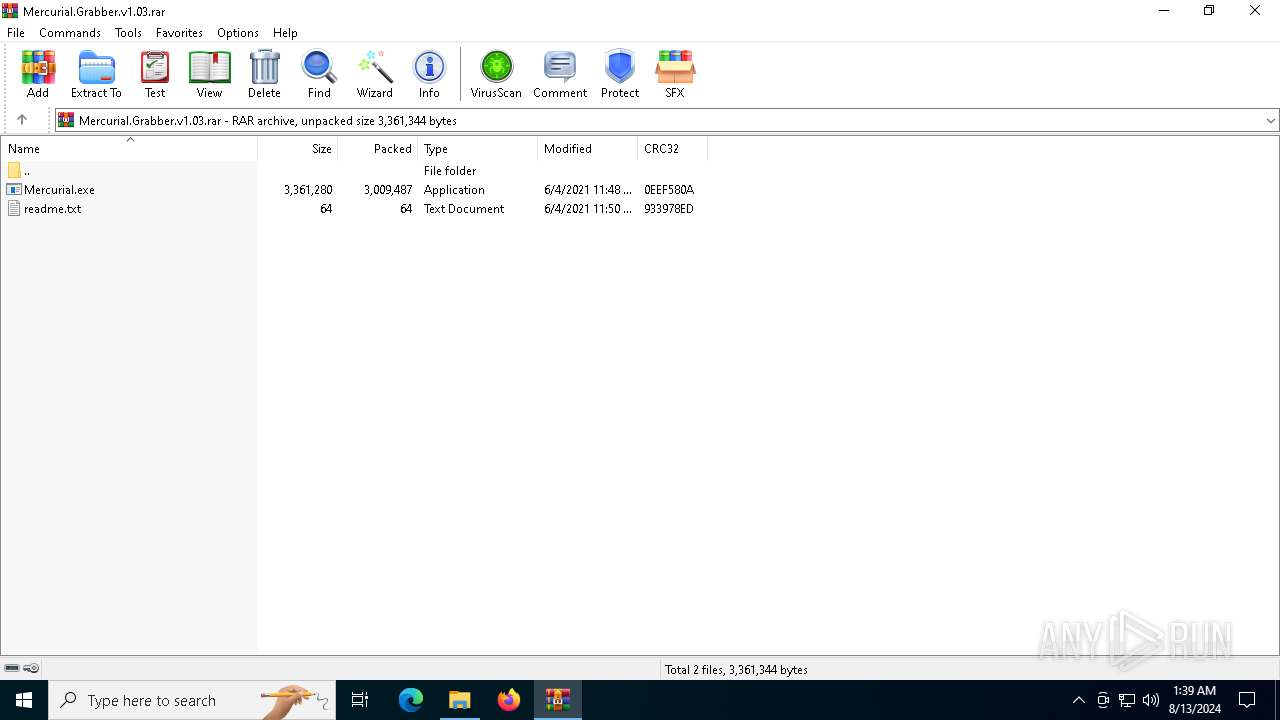
| File info: | RAR archive data, v5 |
| MD5: | 635903BAD1ADA856D701F34D3070CCD9 |
| SHA1: | 3FF98D91B9A3A47BF9F64BDF161EFB9C5AC99FB0 |
| SHA256: | 3759744039346620E9613F40F90E8F318E5F54AD49C070E2BD23B667F7E65BF6 |
| SSDEEP: | 49152:lYtbFd+FwSjhWaqv7yBSw9i4b1g8lDZxu0TR9TlqdqjxaNOH:qkwSVef4NDW8qEfH |
MALICIOUS
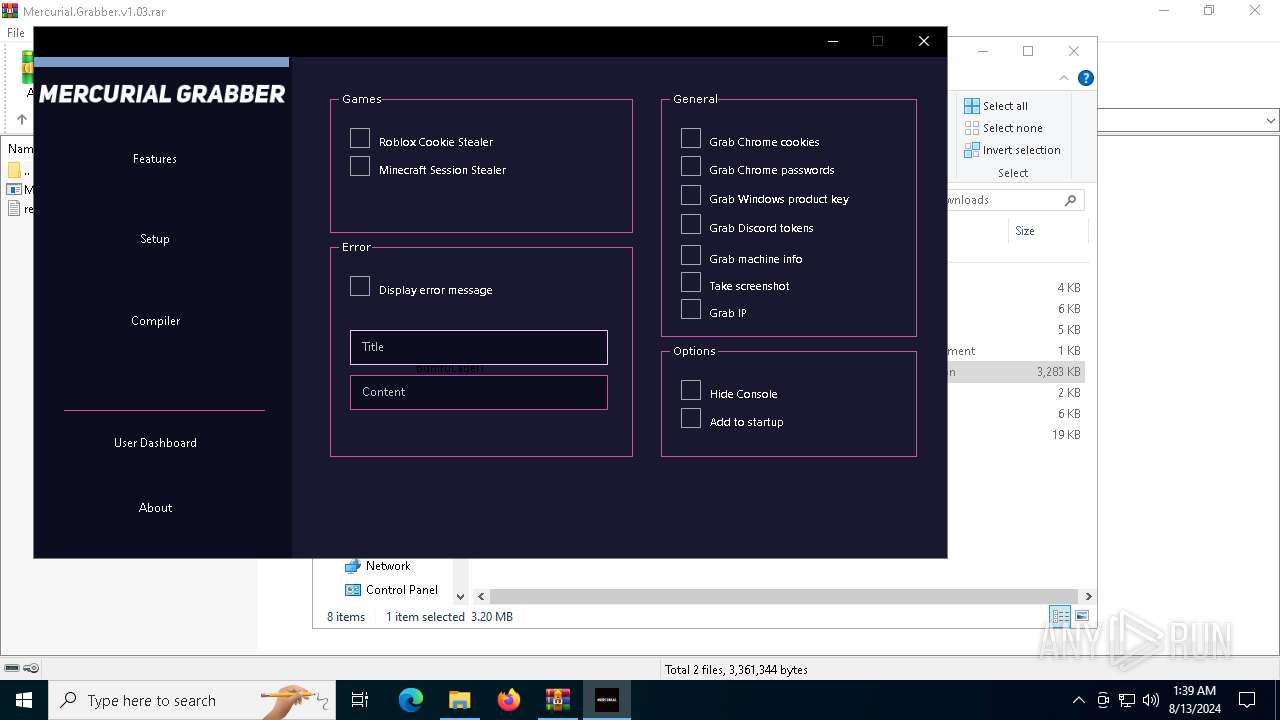
Starts Visual C# compiler
- Mercurial.exe (PID: 3844)
MERCURIALGRABBER has been detected (YARA)
- output.exe (PID: 1048)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6808)
- csc.exe (PID: 3324)
There is functionality for VM detection (VMWare)
- Mercurial.exe (PID: 3844)
There is functionality for taking screenshot (YARA)
- Mercurial.exe (PID: 3844)
There is functionality for VM detection (VirtualBox)
- Mercurial.exe (PID: 3844)
Uses .NET C# to load dll
- Mercurial.exe (PID: 3844)
Executable content was dropped or overwritten
- csc.exe (PID: 3324)
Reads the BIOS version
- output.exe (PID: 1048)
- output.exe (PID: 4208)
Read disk information to detect sandboxing environments
- output.exe (PID: 1048)
- output.exe (PID: 4208)
INFO
Checks supported languages
- Mercurial.exe (PID: 3844)
- TextInputHost.exe (PID: 6536)
- csc.exe (PID: 3324)
- cvtres.exe (PID: 4088)
- output.exe (PID: 1048)
- output.exe (PID: 4208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6808)
Reads the computer name
- Mercurial.exe (PID: 3844)
- TextInputHost.exe (PID: 6536)
- output.exe (PID: 1048)
- output.exe (PID: 4208)
Manual execution by a user
- Mercurial.exe (PID: 3844)
- output.exe (PID: 1048)
- output.exe (PID: 4208)
Reads the machine GUID from the registry
- Mercurial.exe (PID: 3844)
- csc.exe (PID: 3324)
- output.exe (PID: 1048)
- output.exe (PID: 4208)
Create files in a temporary directory
- Mercurial.exe (PID: 3844)
- cvtres.exe (PID: 4088)
Reads Environment values
- output.exe (PID: 1048)
- output.exe (PID: 4208)
Disables trace logs
- output.exe (PID: 4208)
- output.exe (PID: 1048)
Checks proxy server information
- output.exe (PID: 1048)
- output.exe (PID: 4208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
138
Monitored processes
11
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\Users\admin\Downloads\output.exe" | C:\Users\admin\Downloads\output.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3324 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\kudz35n5.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | Mercurial.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3844 | "C:\Users\admin\Downloads\Mercurial.exe" | C:\Users\admin\Downloads\Mercurial.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Mercurial Version: 1.0.0.0 Modules
| |||||||||||||||
| 4088 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESFFA9.tmp" "c:\Users\admin\Downloads\CSCC52ECB602A464B54BAB75D6DD4F99EF3.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 4208 | "C:\Users\admin\Downloads\output.exe" | C:\Users\admin\Downloads\output.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 4692 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | output.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | output.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6536 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6712 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 123
Read events
10 084
Write events
25
Delete events
14
Modification events
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
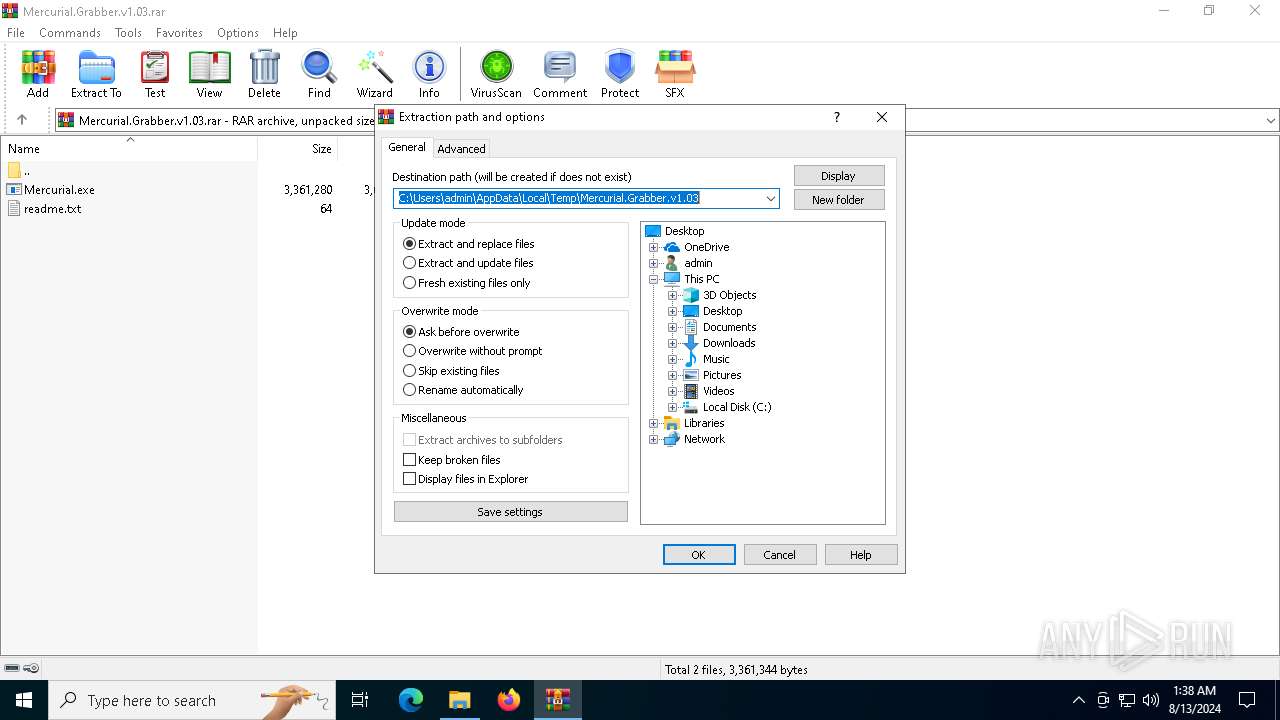
Value: C:\Users\admin\AppData\Local\Temp\Mercurial.Grabber.v1.03.rar | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
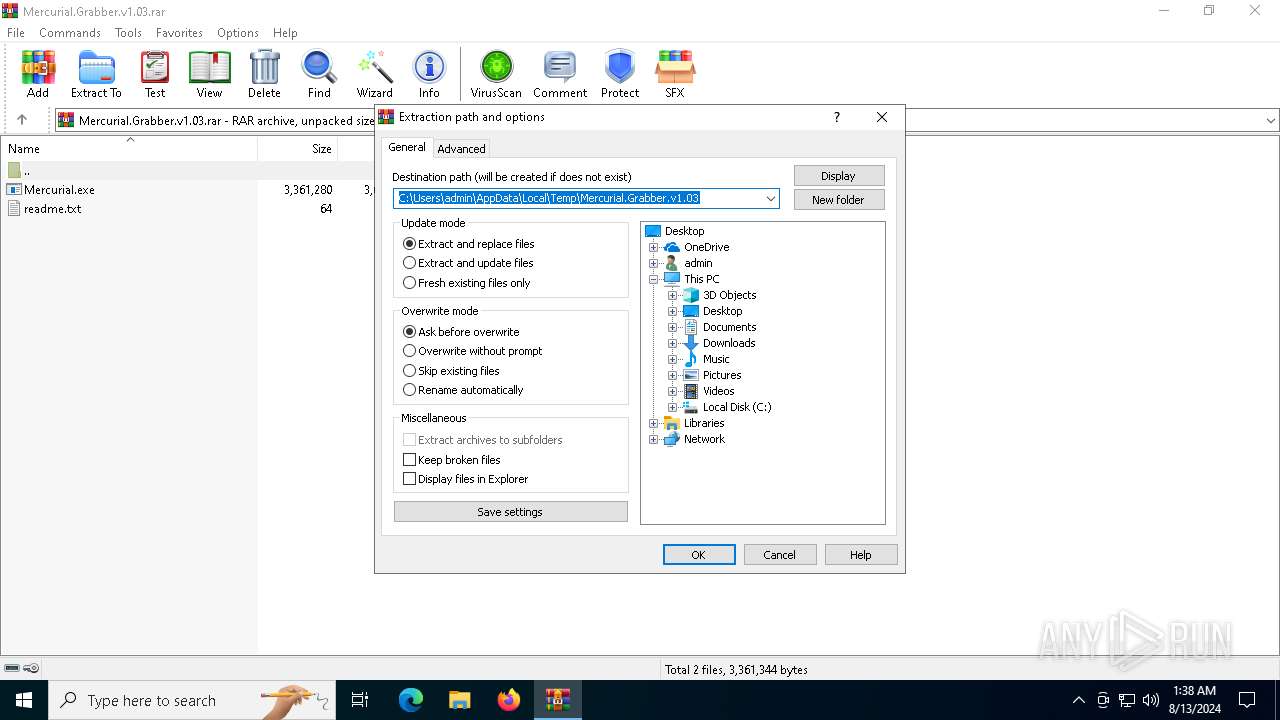
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Mercurial.Grabber.v1.03 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
Executable files
3
Suspicious files
2
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3844 | Mercurial.exe | C:\Users\admin\AppData\Local\Temp\kudz35n5.5.cs | text | |
MD5:42F157AD8E79E06A142791D6E98E0365 | SHA256:E30402CD45589982489719678ADF59B016674FAA6F7A9AF074601E978CC9A0ED | |||
| 6808 | WinRAR.exe | C:\Users\admin\Downloads\Mercurial.exe | executable | |
MD5:A9477B3E21018B96FC5D2264D4016E65 | SHA256:890FD59AF3370E2CE12E0D11916D1AD4EE9B9C267C434347DBED11E9572E8645 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Mercurial.Grabber.v1.03\readme.txt | text | |
MD5:77976AB4F7B14569DD64F212CE6EE64E | SHA256:044B863E9895E669D45D97D44A4F80F2B9AC5F941635EF3C1E9F39AD12747ECF | |||
| 3844 | Mercurial.exe | C:\Users\admin\AppData\Local\Temp\kudz35n5.4.cs | text | |
MD5:FAE5458A5B3CEE952E25D44D6EB9DB85 | SHA256:240478BB9C522341906A0EF376E0188CE6106856A26A3AE0F7B58AF07A377A06 | |||
| 3844 | Mercurial.exe | C:\Users\admin\AppData\Local\Temp\kudz35n5.6.cs | text | |
MD5:8EC0F0E49FFE092345673AB4D9F45641 | SHA256:93B9F783B5FAED3ECFAFBE20DFCF1BEE3CE33F66909879CD39AE88C36ACBDFAC | |||
| 6808 | WinRAR.exe | C:\Users\admin\Downloads\readme.txt | text | |
MD5:77976AB4F7B14569DD64F212CE6EE64E | SHA256:044B863E9895E669D45D97D44A4F80F2B9AC5F941635EF3C1E9F39AD12747ECF | |||
| 3844 | Mercurial.exe | C:\Users\admin\AppData\Local\Temp\kudz35n5.0.cs | text | |
MD5:F3ED6F312DEBBD5AF986C762050D9542 | SHA256:3559CA033CBF3B6B63E0B40EF2191EF0BA8E334D3C6085BE24406A4908D6C6B1 | |||
| 3844 | Mercurial.exe | C:\Users\admin\AppData\Local\Temp\kudz35n5.3.cs | text | |
MD5:6BA707982EE7E5F0AE55CE3FA5CCAD17 | SHA256:19AF9BEA270F830354AF8250CD82DB32FDCAB6327D139E2720713FB7D43A5797 | |||
| 3844 | Mercurial.exe | C:\Users\admin\AppData\Local\Temp\kudz35n5.2.cs | text | |
MD5:6FDAE9AFC1F8E77E882F1BA6B5859A4E | SHA256:A365264DD2D3388ACC38B2F5C8F3C267BBF83CA463F70FBF6C8459123A7CC33D | |||
| 3844 | Mercurial.exe | C:\Users\admin\AppData\Local\Temp\kudz35n5.1.cs | text | |
MD5:8AAB1997664A604ACA551B20202BFD14 | SHA256:029F57FA483BBCEE0DD5464E0D4D89BD03032161424D0FFD1DA2B3D5DB15977F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
39
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6456 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6508 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4016 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5240 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1360 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |