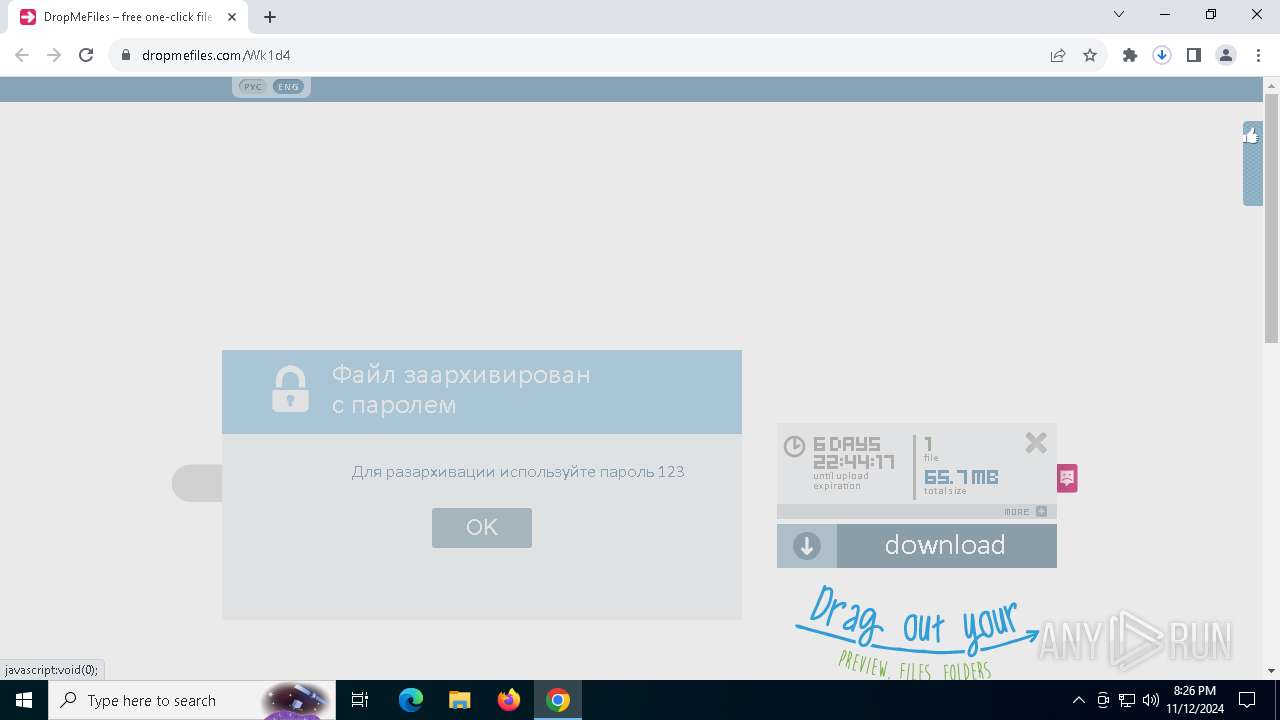
| URL: | https://dropmefiles.com/Wk1d4 |
| Full analysis: | https://app.any.run/tasks/8b492b2d-cd86-4297-937b-585c6325247c |
| Verdict: | Malicious activity |
| Analysis date: | November 12, 2024, 20:25:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 868E89F926FF179FAE753F2766BEB651 |
| SHA1: | 6AB69EEF8C568969C221ADDF5A512DE311A8FA1D |
| SHA256: | 375869255953497FADEEA2B5406509A20C7BBF1B72C3E9298A1E437855A3E2D1 |
| SSDEEP: | 3:N8PKV9DNRn:2oDNR |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 6760)
Bypass execution policy to execute commands
- powershell.exe (PID: 5220)
- powershell.exe (PID: 6380)
SUSPICIOUS
Executable content was dropped or overwritten
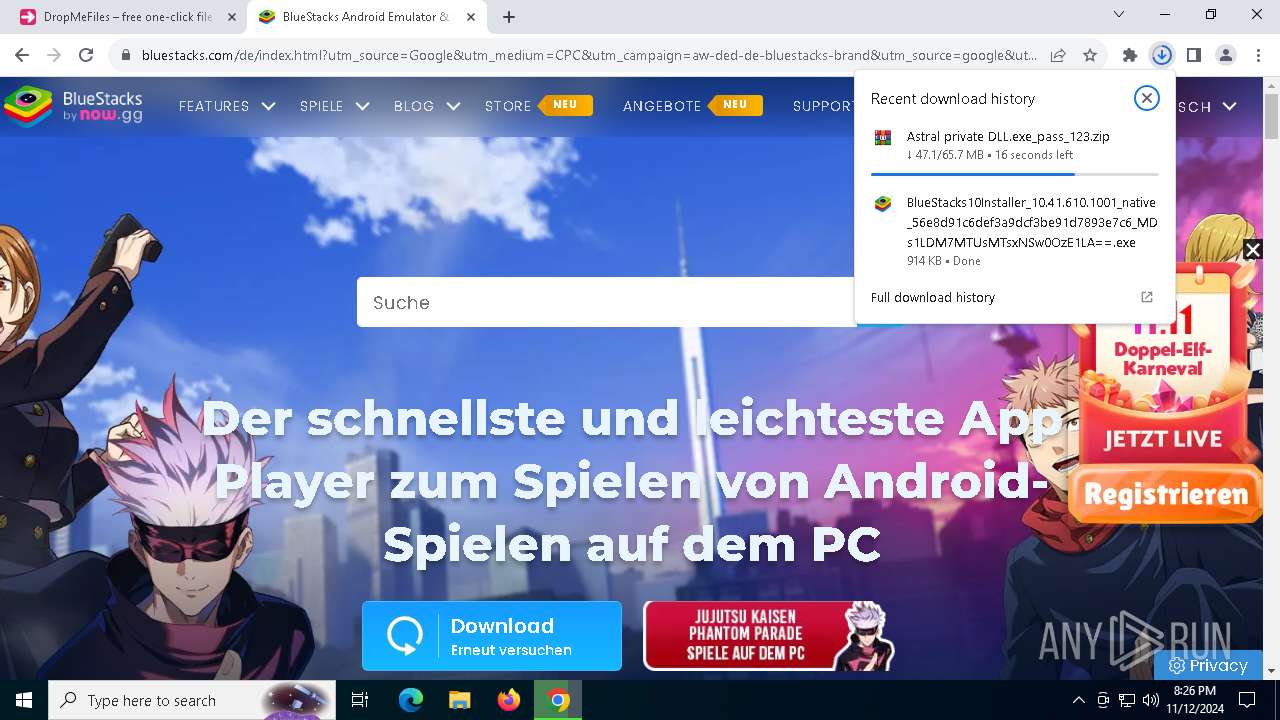
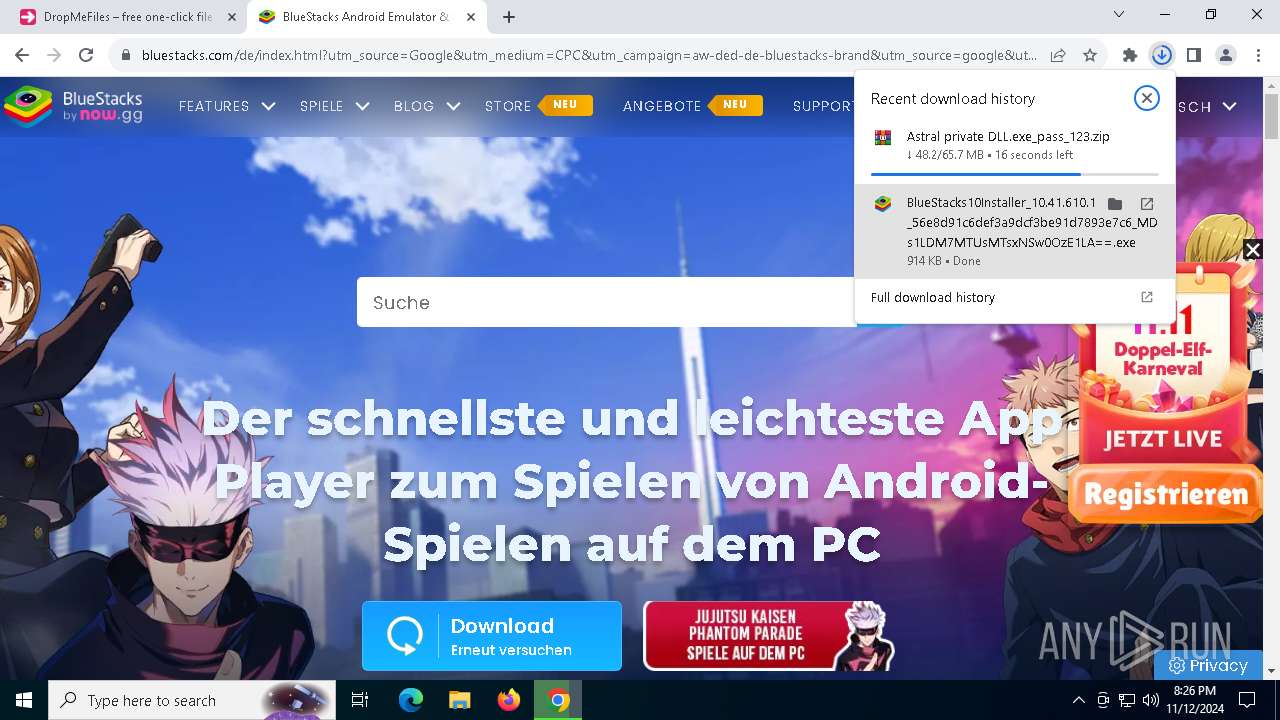
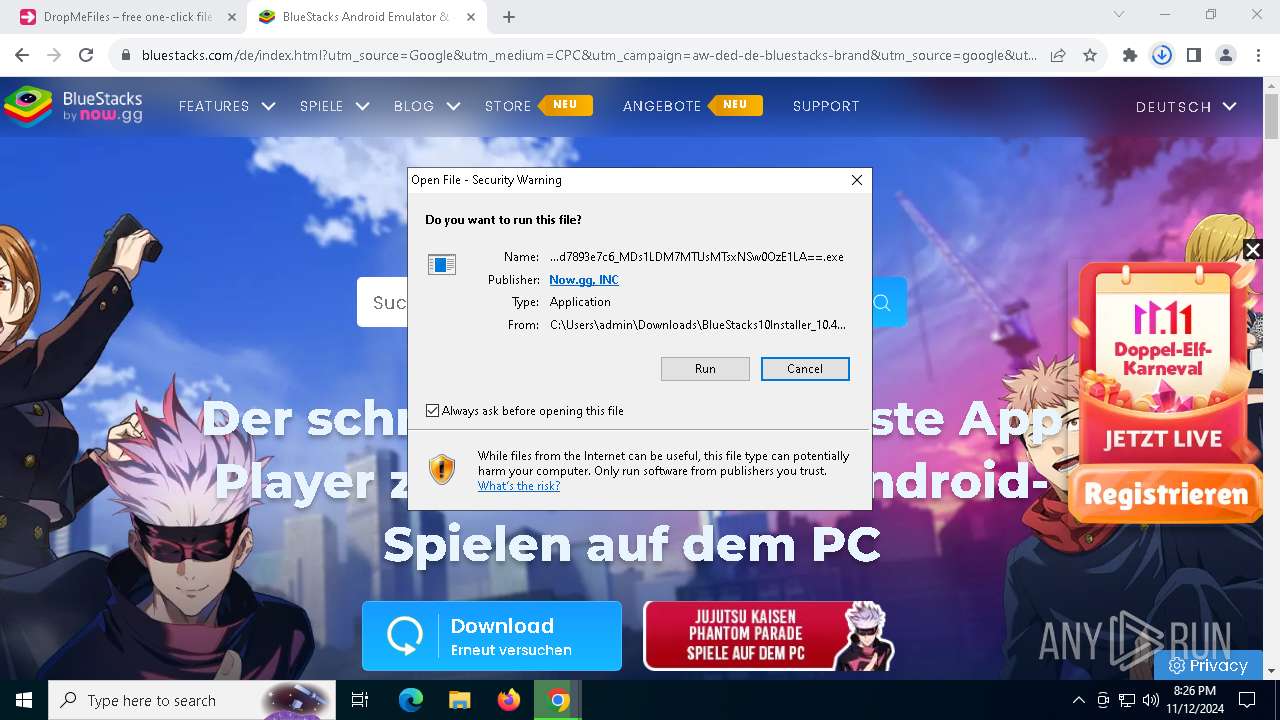
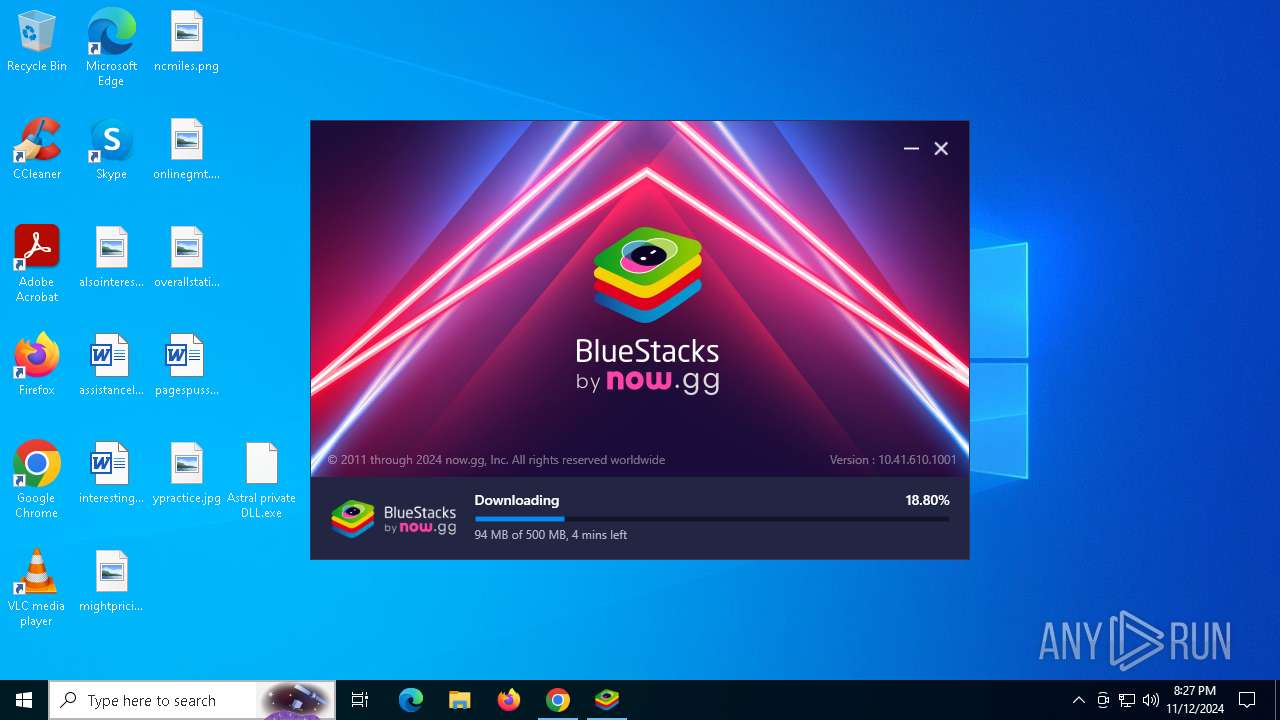
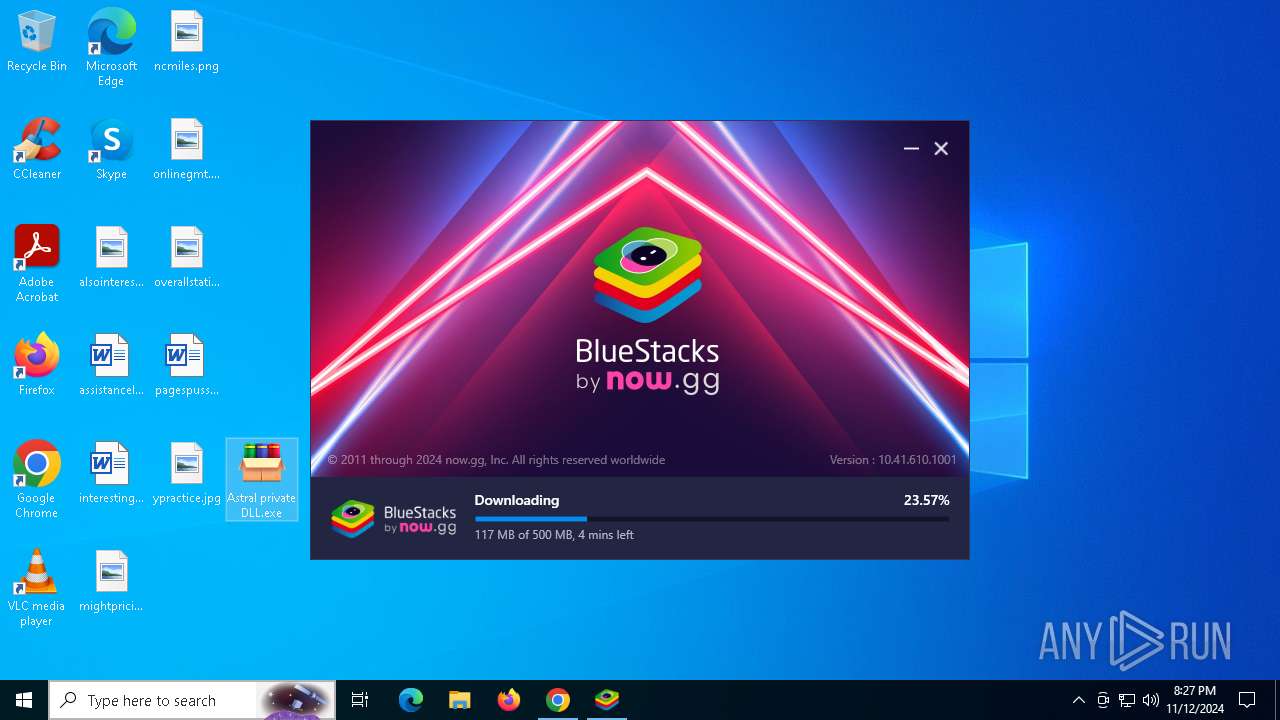
- BlueStacks10Installer_10.41.610.1001_native_56e8d91c6def3a9dcf3be91d7893e7c6_MDs1LDM7MTUsMTsxNSw0OzE1LA==.exe (PID: 7876)
- BSX-Setup-5.21.610.1003_nxt.exe (PID: 8168)
- BlueStacks10Installer_10.41.610.1001_native_56e8d91c6def3a9dcf3be91d7893e7c6_MDs1LDM7MTUsMTsxNSw0OzE1LA==.exe (PID: 6976)
- 7zr.exe (PID: 7800)
- 7zr.exe (PID: 7652)
- 7zr.exe (PID: 4060)
- BlueStacksServicesSetup.exe (PID: 5564)
- BlueStacksInstaller.exe (PID: 1028)
- BlueStacksServices.exe (PID: 3024)
- 7zr.exe (PID: 6852)
Application launched itself
- BlueStacksInstaller.exe (PID: 7888)
- BlueStacksServices.exe (PID: 3024)
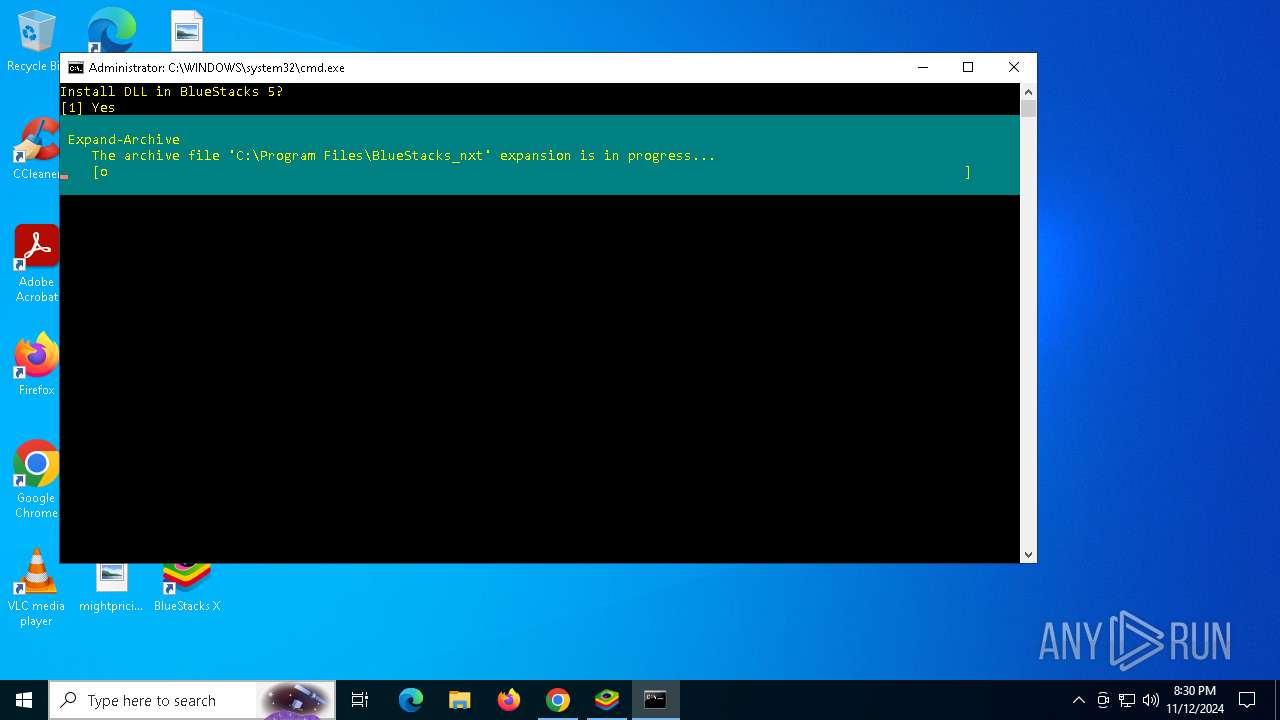
Malware-specific behavior (creating "System.dll" in Temp)
- BSX-Setup-5.21.610.1003_nxt.exe (PID: 8168)
- BlueStacksServicesSetup.exe (PID: 5564)
Drops 7-zip archiver for unpacking
- BSX-Setup-5.21.610.1003_nxt.exe (PID: 8168)
- 7zr.exe (PID: 4060)
- BlueStacks10Installer_10.41.610.1001_native_56e8d91c6def3a9dcf3be91d7893e7c6_MDs1LDM7MTUsMTsxNSw0OzE1LA==.exe (PID: 6976)
- BlueStacksServicesSetup.exe (PID: 5564)
Executing commands from a ".bat" file
- wscript.exe (PID: 8128)
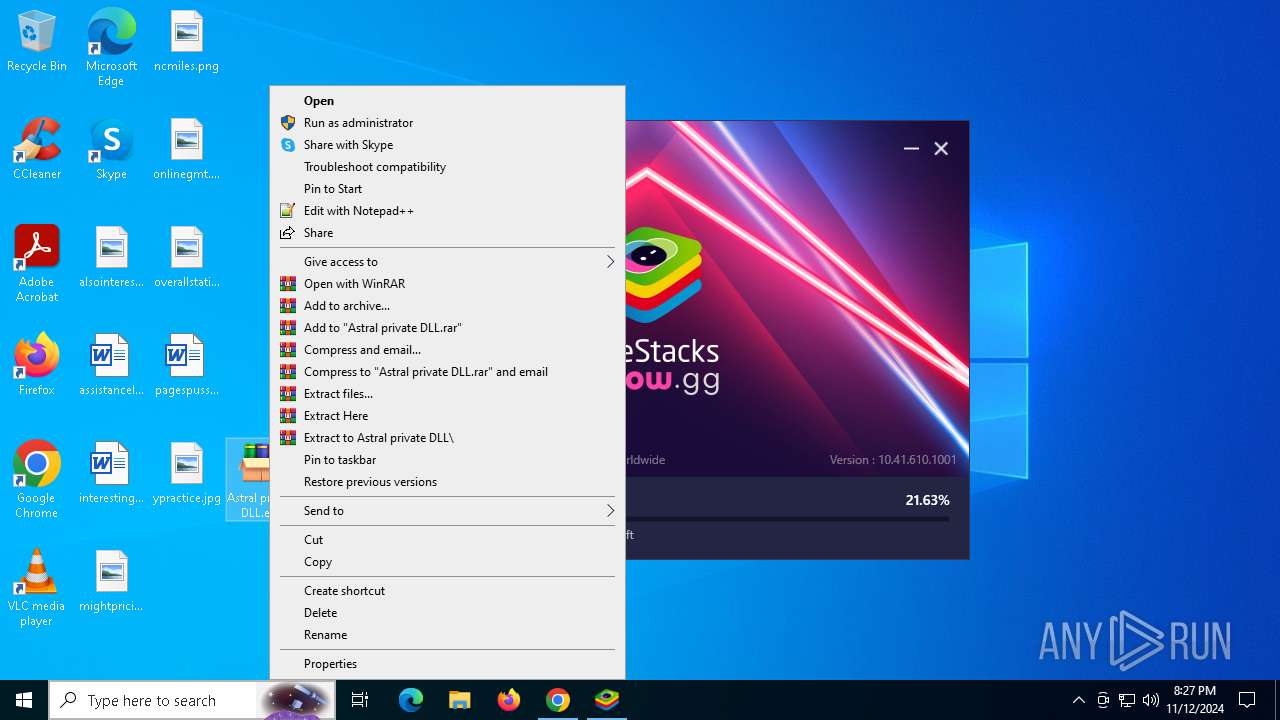
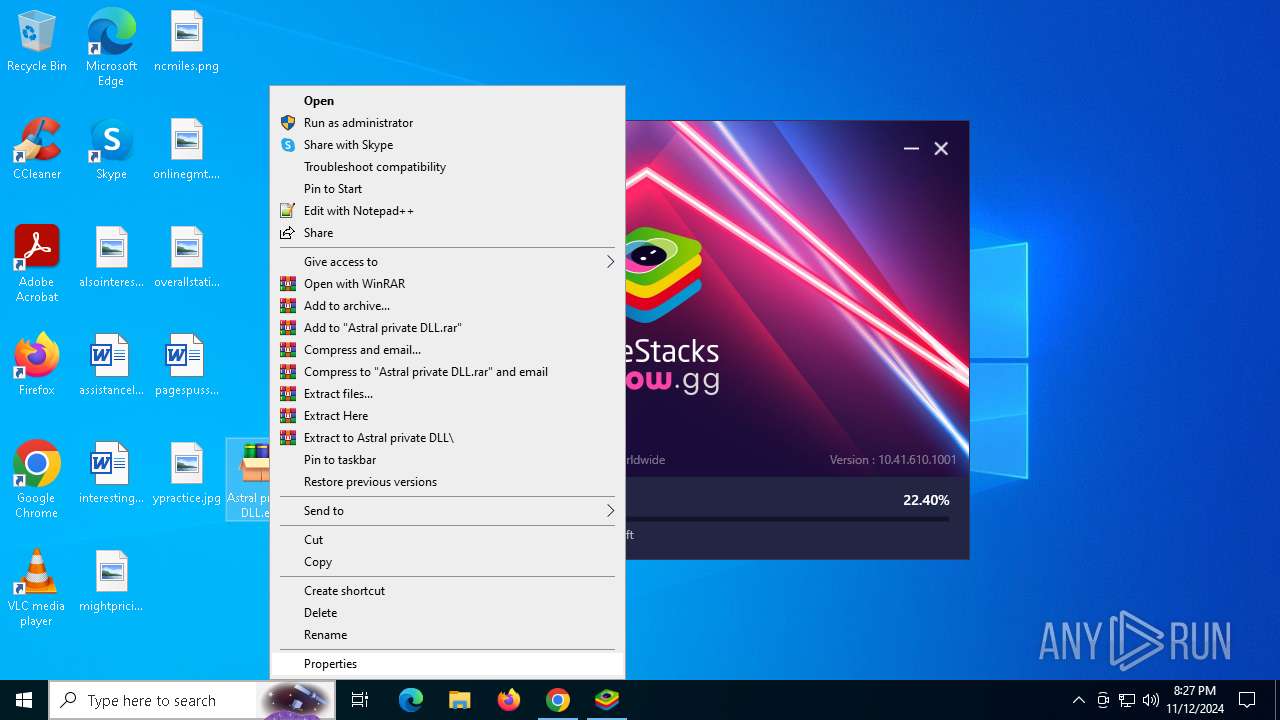
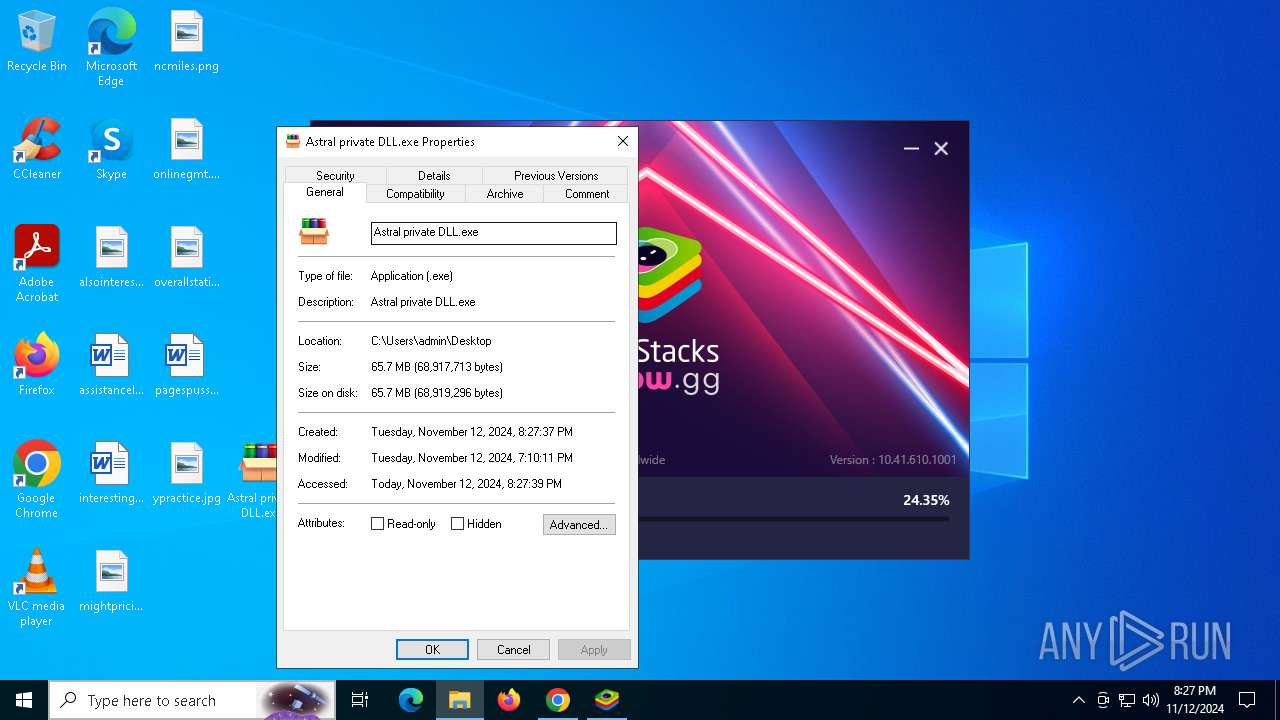
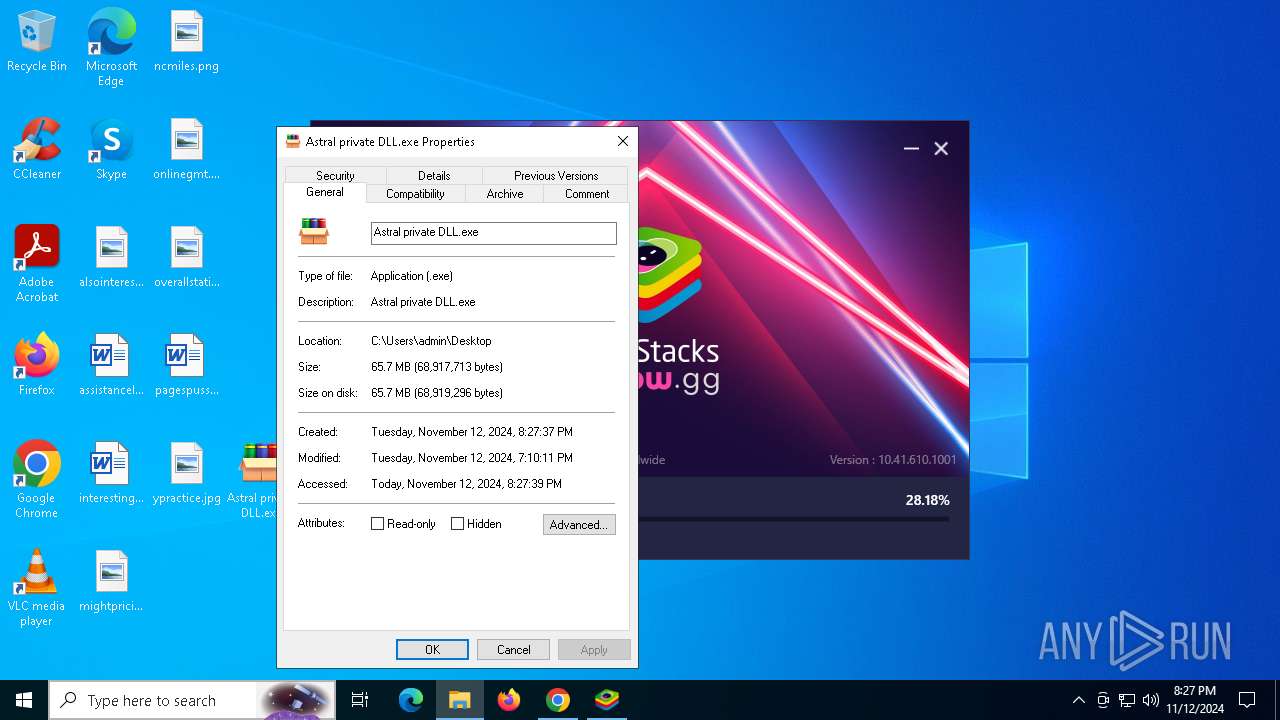
- Astral private DLL.exe (PID: 5372)
- Astral private DLL.exe (PID: 8060)
The process drops C-runtime libraries
- BSX-Setup-5.21.610.1003_nxt.exe (PID: 8168)
- 7zr.exe (PID: 7800)
- 7zr.exe (PID: 4060)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 8128)
- Astral private DLL.exe (PID: 5372)
- BlueStacksServicesSetup.exe (PID: 5564)
- Astral private DLL.exe (PID: 8060)
- BlueStacksServices.exe (PID: 3024)
The process executes VB scripts
- BSX-Setup-5.21.610.1003_nxt.exe (PID: 8168)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8128)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 624)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 624)
Process drops legitimate windows executable
- BSX-Setup-5.21.610.1003_nxt.exe (PID: 8168)
- BlueStacks10Installer_10.41.610.1001_native_56e8d91c6def3a9dcf3be91d7893e7c6_MDs1LDM7MTUsMTsxNSw0OzE1LA==.exe (PID: 6976)
- 7zr.exe (PID: 7800)
- 7zr.exe (PID: 4060)
- BlueStacksServicesSetup.exe (PID: 5564)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7768)
- cmd.exe (PID: 6760)
The process executes Powershell scripts
- cmd.exe (PID: 7768)
- cmd.exe (PID: 6760)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 7768)
- net.exe (PID: 2140)
- cmd.exe (PID: 6760)
- net.exe (PID: 6936)
Get information on the list of running processes
- BlueStacksServicesSetup.exe (PID: 5564)
- cmd.exe (PID: 7340)
- BlueStacksServices.exe (PID: 3024)
- cmd.exe (PID: 7344)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 6772)
- cmd.exe (PID: 2844)
Drops a system driver (possible attempt to evade defenses)
- 7zr.exe (PID: 4060)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6380)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 7708)
- cscript.exe (PID: 6404)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 6696)
- cscript.exe (PID: 7836)
- cscript.exe (PID: 2660)
- cscript.exe (PID: 6260)
- cscript.exe (PID: 7048)
- cscript.exe (PID: 4904)
- cscript.exe (PID: 7816)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7708)
- cscript.exe (PID: 6404)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 6696)
- cscript.exe (PID: 7836)
- cscript.exe (PID: 2660)
- cscript.exe (PID: 6260)
- cscript.exe (PID: 7048)
- cscript.exe (PID: 4904)
- cscript.exe (PID: 7816)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 7708)
- cscript.exe (PID: 6404)
- cscript.exe (PID: 7820)
- cscript.exe (PID: 7836)
- cscript.exe (PID: 2660)
- cscript.exe (PID: 7048)
- cscript.exe (PID: 6696)
- cscript.exe (PID: 6260)
- cscript.exe (PID: 7816)
- cscript.exe (PID: 4904)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 7708)
- cscript.exe (PID: 6404)
- cscript.exe (PID: 6260)
- cscript.exe (PID: 2660)
- cscript.exe (PID: 7836)
- cscript.exe (PID: 7048)
- cscript.exe (PID: 4904)
- cscript.exe (PID: 7816)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 300)
- chrome.exe (PID: 1588)
Sends debugging messages
- BSX-Setup-5.21.610.1003_nxt.exe (PID: 8168)
Application launched itself
- chrome.exe (PID: 6168)
- chrome.exe (PID: 1588)
Manual execution by a user
- chrome.exe (PID: 6168)
- Astral private DLL.exe (PID: 5372)
- BlueStacksServicesSetup.exe (PID: 5564)
- Astral private DLL.exe (PID: 8060)
- BlueStacksServices.exe (PID: 3024)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6380)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
276
Monitored processes
140
Malicious processes
17
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | tasklist /FI "IMAGENAME eq BlueStacks X.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6368 --field-trial-handle=1928,i,5176999518621291801,1380004210323684776,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 612 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffbc12bdc40,0x7ffbc12bdc4c,0x7ffbc12bdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 624 | "C:\Windows\System32\cmd.exe" /c green.bat | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | HD-GLCheck.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 944 | tasklist /FI "USERNAME eq admin" /FI "IMAGENAME eq BlueStacksServices.exe" | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Temp\7zS04BBB4AC\BlueStacksInstaller.exe" -versionMachineID="3580b817-08df-46d5-96fd-a2a1c9bb4272" -machineID="19d72a22-69a3-42b9-a4a9-f7f3fefb91e9" -pddir="C:\ProgramData\BlueStacks_nxt" -defaultImageName="Nougat32" -imageToLaunch="Nougat32" -appToLaunch="bsx" -bsxVersion="10.41.610.1001" -country="DE" -skipBinaryShortcuts -isWalletFeatureEnabled -parentpath="C:\Users\admin\AppData\Local\BlueStacksSetup\BlueStacks10Installer_10.41.610.1001_native_56e8d91c6def3a9dcf3be91d7893e7c6_MDs1LDM7MTUsMTsxNSw0OzE1LA==.exe" -md5=56e8d91c6def3a9dcf3be91d7893e7c6 -app64= | C:\Users\admin\AppData\Local\Temp\7zS04BBB4AC\BlueStacksInstaller.exe | Bootstrapper.exe | ||||||||||||
User: admin Company: now.gg, Inc. Integrity Level: HIGH Description: BlueStacks Installer Version: 5.21.610.1003 Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5672 --field-trial-handle=1928,i,5176999518621291801,1380004210323684776,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1156 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7zr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=5060 --field-trial-handle=1928,i,5176999518621291801,1380004210323684776,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
40 893
Read events
40 756
Write events
108
Delete events
29
Modification events
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1588) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (7676) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000CBA791304135DB01 | |||
| (PID) Process: | (7888) BlueStacksInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\BlueStacksInstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7888) BlueStacksInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\BlueStacksInstaller_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7888) BlueStacksInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\BlueStacksInstaller_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
576
Suspicious files
725
Text files
732
Unknown types
74
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF8f3fe.TMP | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF8f3fe.TMP | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF8f3fe.TMP | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF8f3fe.TMP | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF8f3fe.TMP | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1588 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
165
DNS requests
153
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6908 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5604 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
6312 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6312 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5604 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
1588 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
1588 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
1588 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAT51QpseSyf051HLpg3tf8%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4360 | SearchApp.exe | 2.16.110.147:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4376 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4376 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
780 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dropmefiles.com |
| whitelisted |
accounts.google.com |
| whitelisted |
th.bing.com |
| whitelisted |
imasdk.googleapis.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6044 | chrome.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (dropmefiles .com) |
6044 | chrome.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (dropmefiles .com) |
6044 | chrome.exe | Misc activity | ET INFO Observed File Sharing Service Domain (dropmefiles .com in TLS SNI) |
6044 | chrome.exe | Misc activity | ET INFO Observed File Sharing Service Domain (dropmefiles .com in TLS SNI) |
6044 | chrome.exe | Misc activity | ET INFO Observed File Sharing Service Domain (dropmefiles .com in TLS SNI) |
6044 | chrome.exe | Misc activity | ET INFO Observed File Sharing Service Domain (dropmefiles .com in TLS SNI) |
6044 | chrome.exe | Misc activity | ET INFO Observed File Sharing Service Domain (dropmefiles .com in TLS SNI) |
6044 | chrome.exe | Misc activity | ET INFO Observed File Sharing Service Domain (dropmefiles .com in TLS SNI) |
6044 | chrome.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (dropmefiles .com) |
6044 | chrome.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (dropmefiles .com) |
Process | Message |
|---|---|
BSX-Setup-5.21.610.1003_nxt.exe | C:\Program Files (x86) |
BSX-Setup-5.21.610.1003_nxt.exe | closebtn |
BSX-Setup-5.21.610.1003_nxt.exe | CustomInstall |
BSX-Setup-5.21.610.1003_nxt.exe | btnSelectDir |
BSX-Setup-5.21.610.1003_nxt.exe | DirText |
BSX-Setup-5.21.610.1003_nxt.exe | BtnOneClick |
BSX-Setup-5.21.610.1003_nxt.exe | BtnInstallFinished |
BSX-Setup-5.21.610.1003_nxt.exe | C:\Program Files (x86) |
BSX-Setup-5.21.610.1003_nxt.exe | showInstallPage |
BSX-Setup-5.21.610.1003_nxt.exe | 0% |