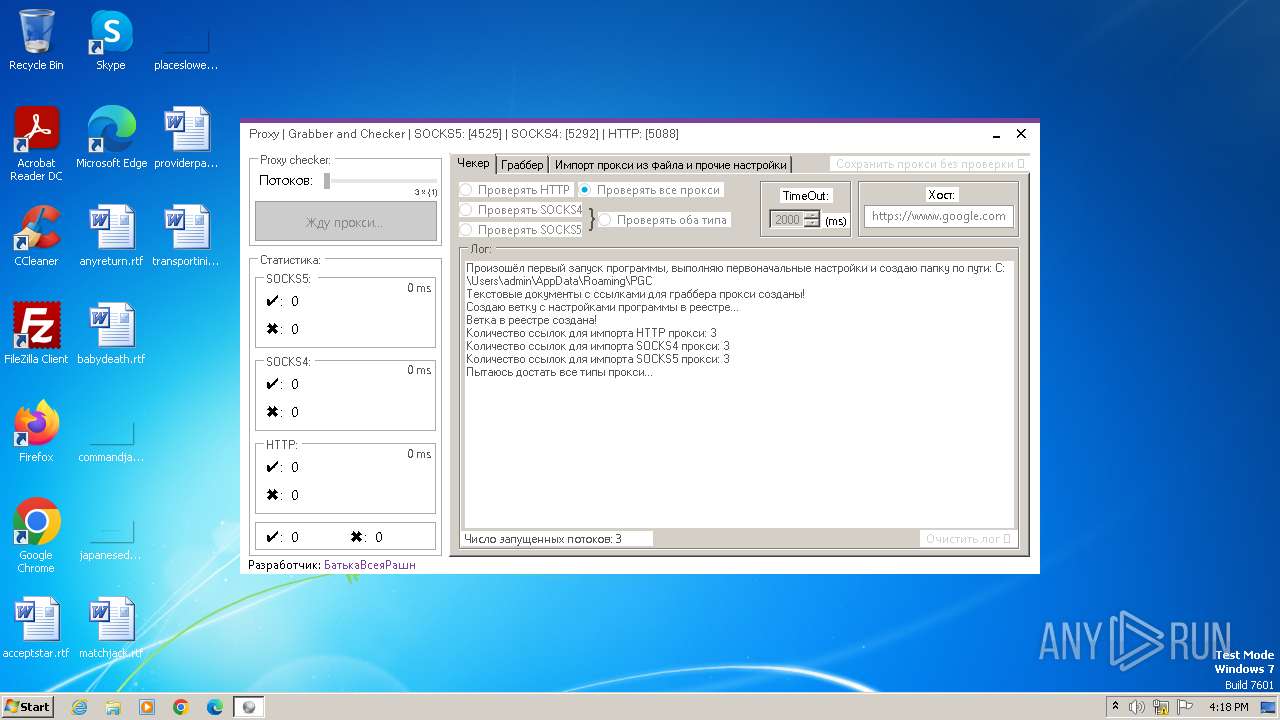
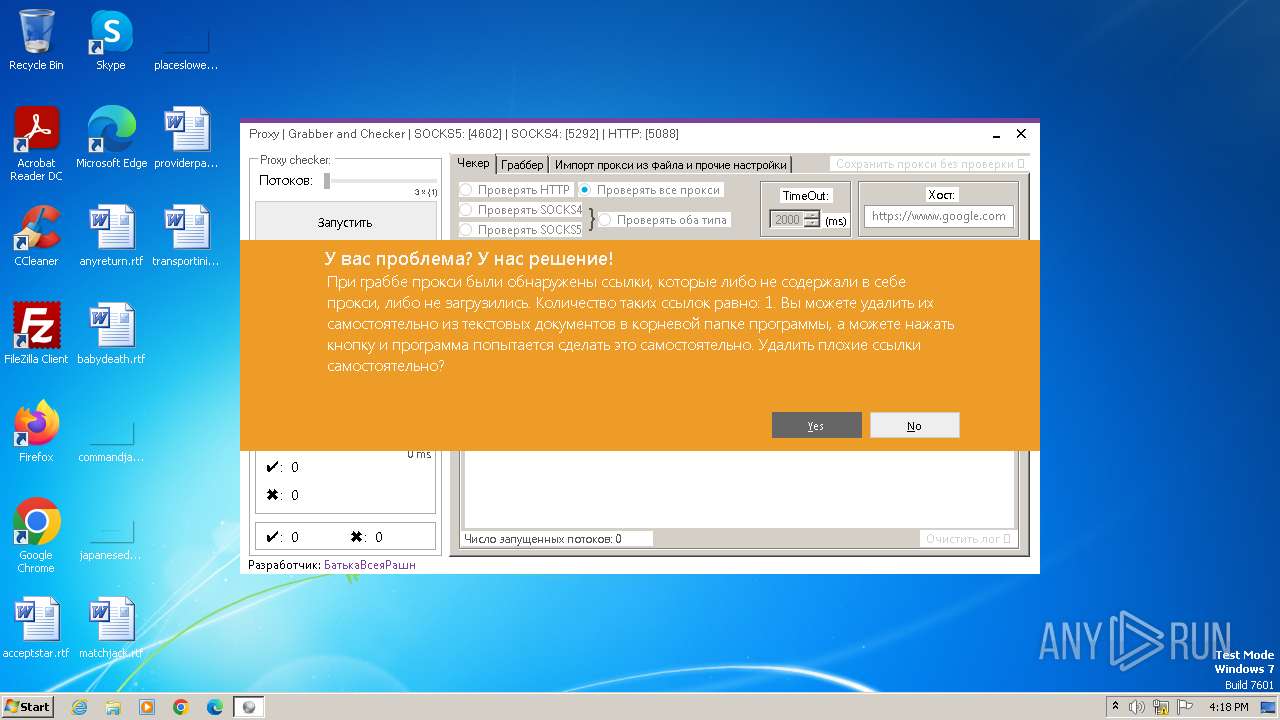
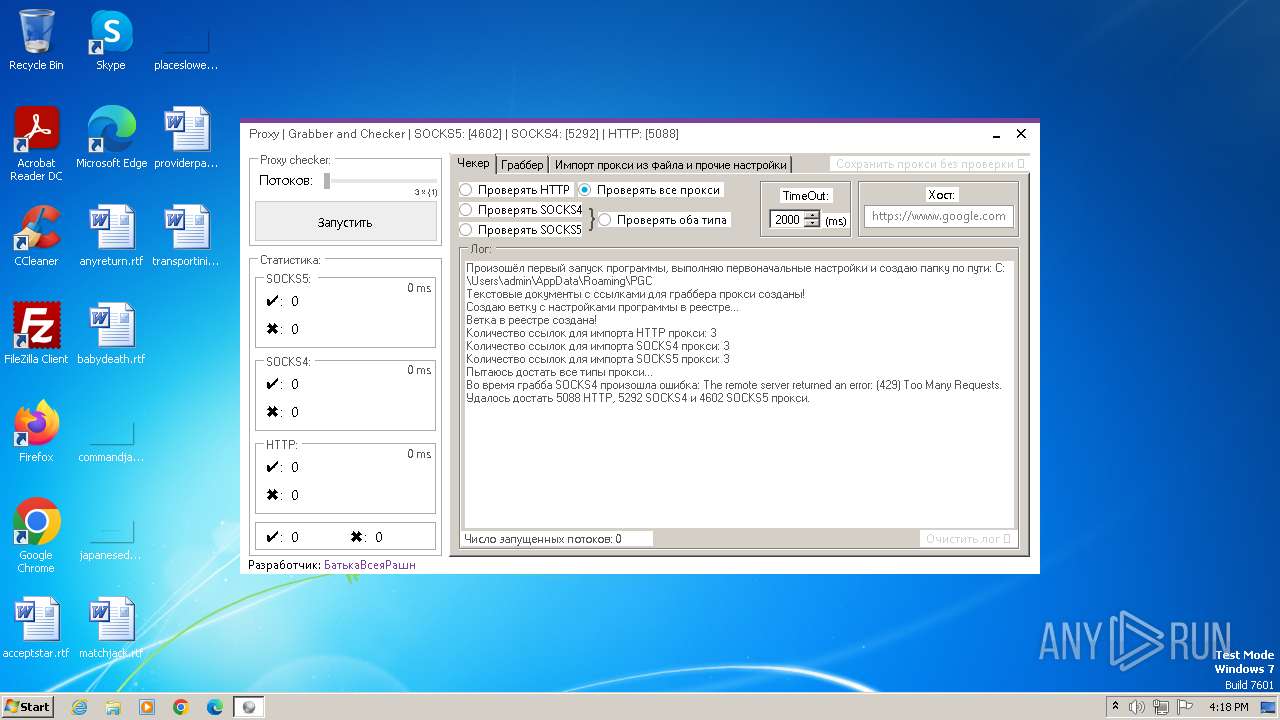
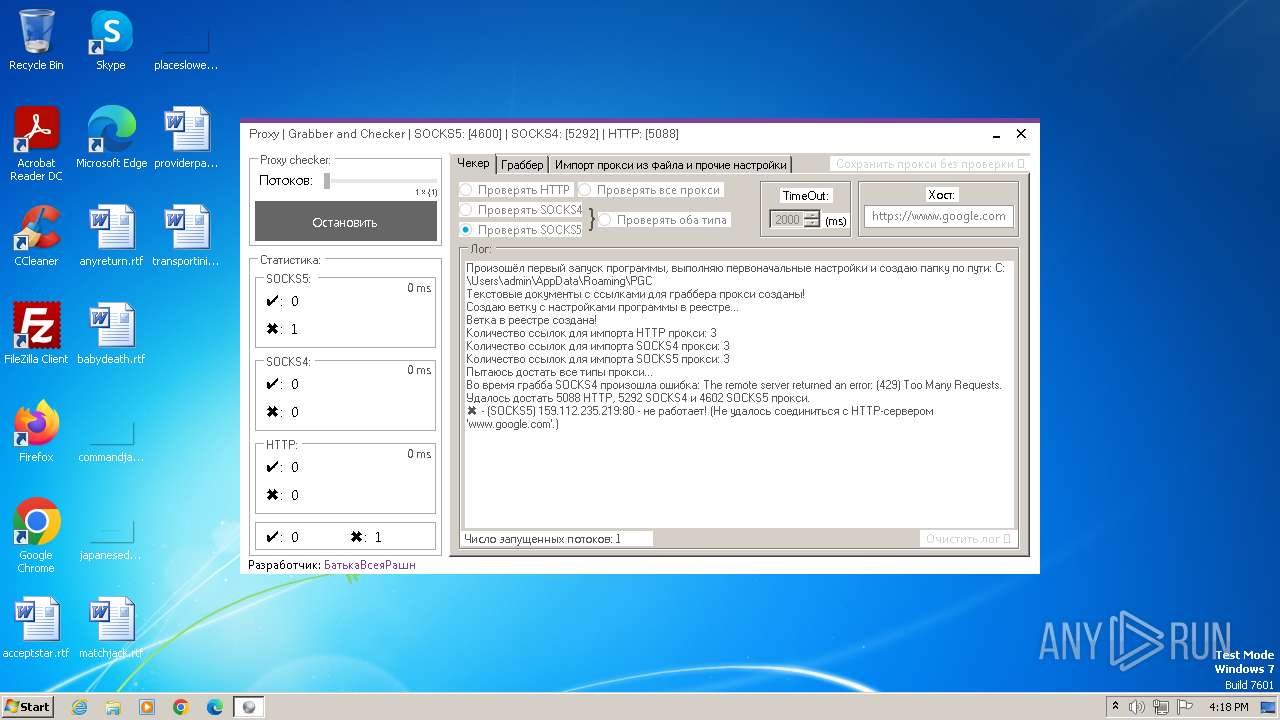
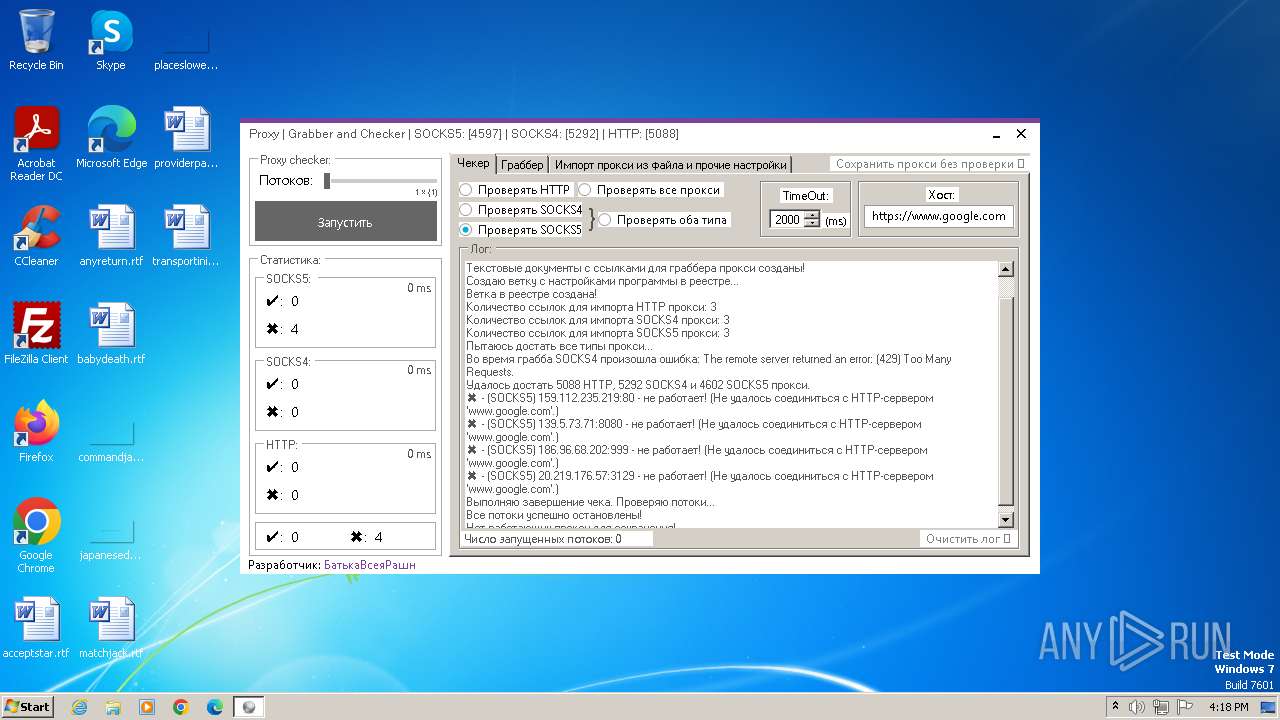
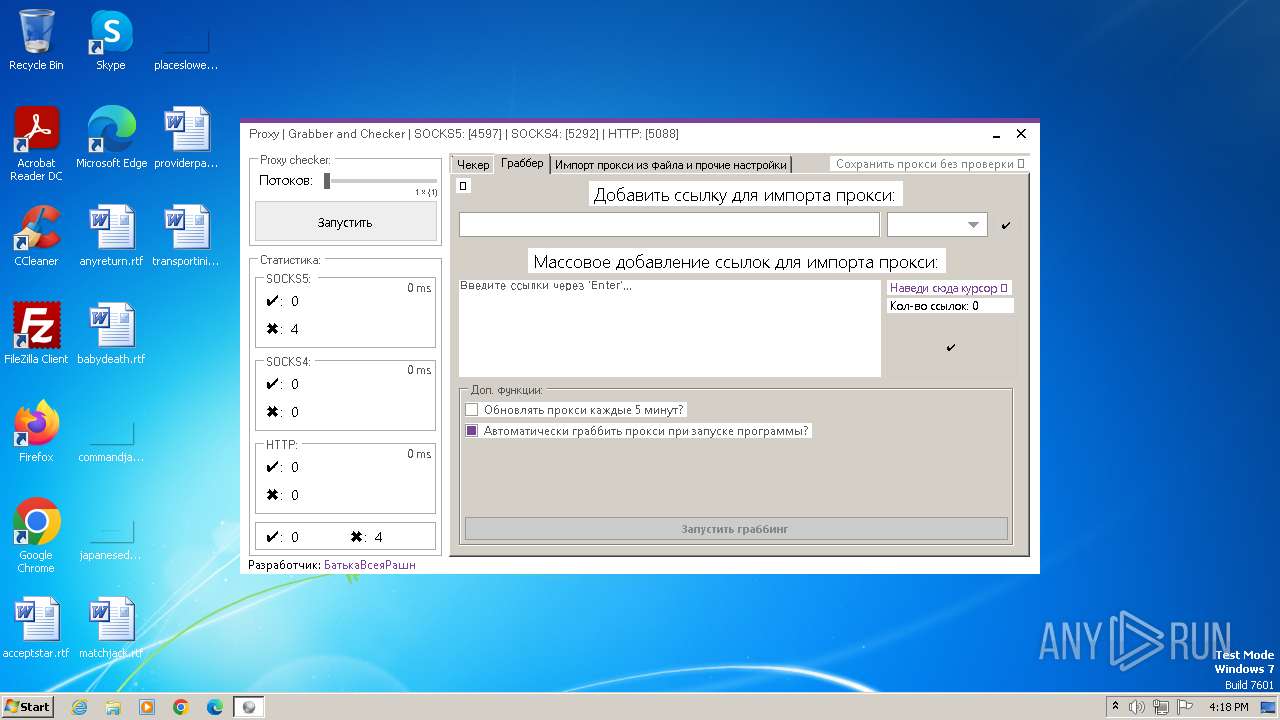
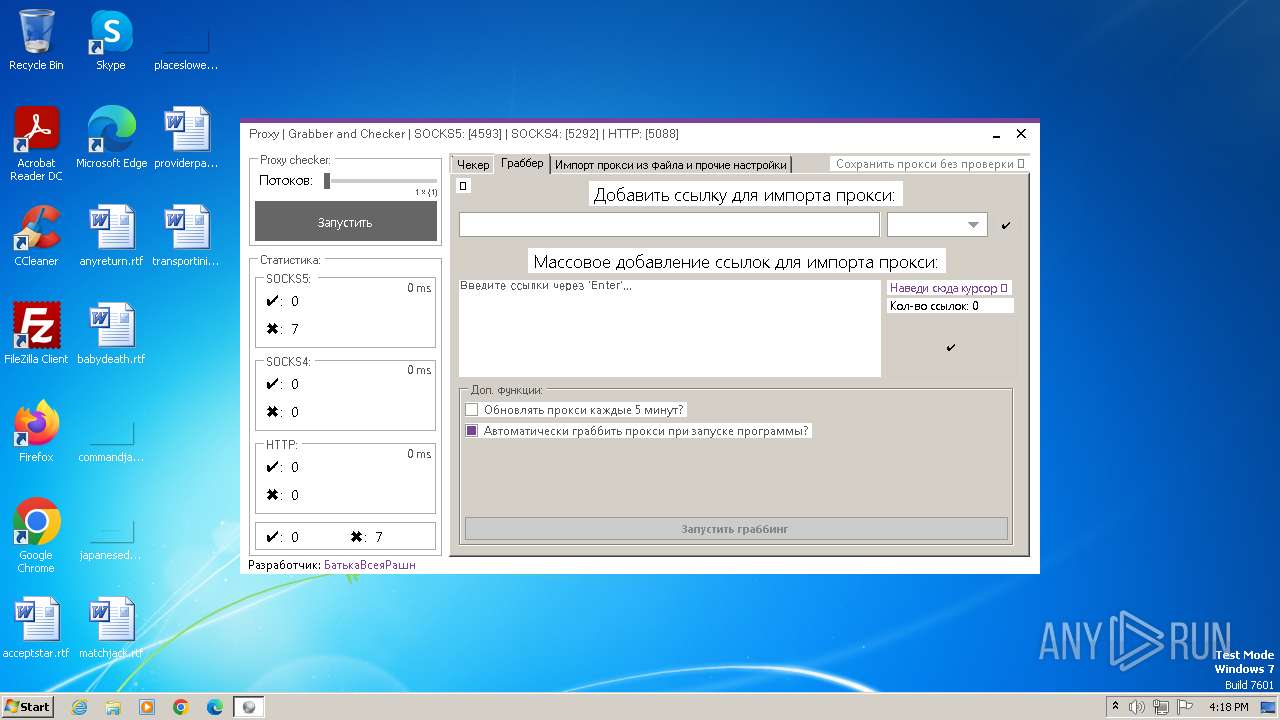
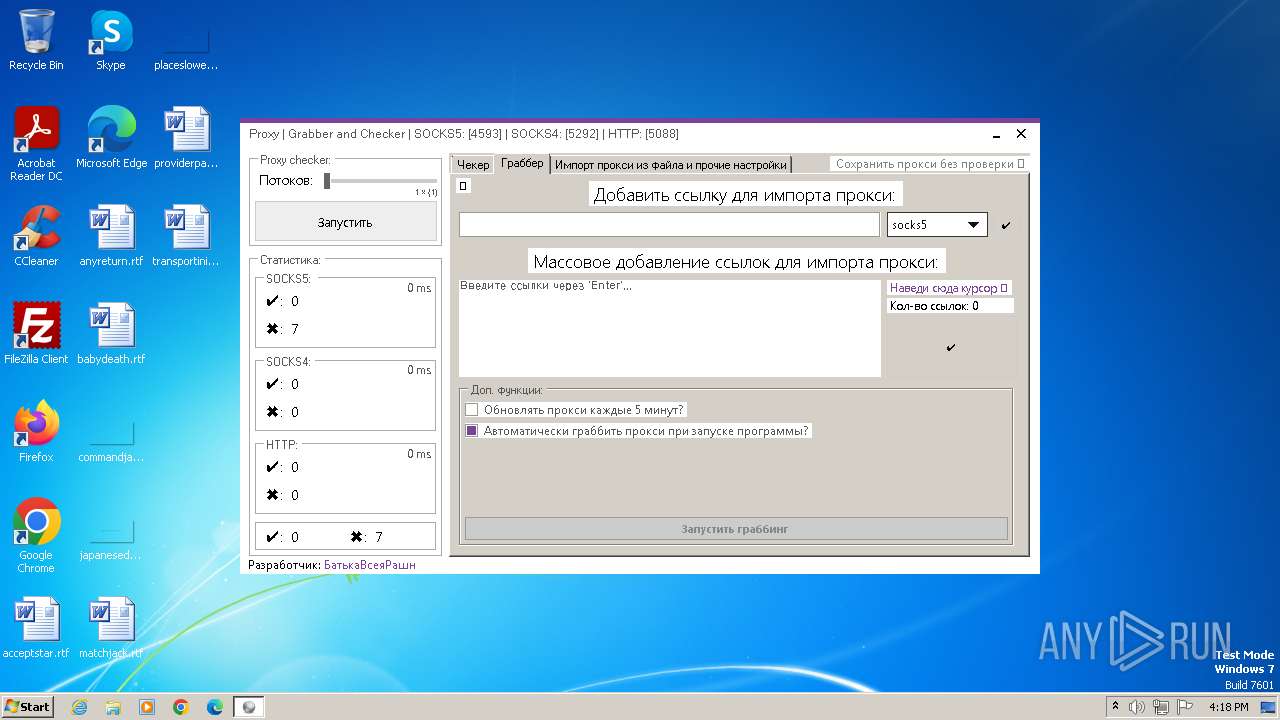
| File name: | Proxy.Grabber.and.Checker.exe |
| Full analysis: | https://app.any.run/tasks/9c26cd66-3446-41fb-82a6-15ac934ab20f |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2023, 16:17:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | A6EFCD6A68716471CCF82A6370D68182 |
| SHA1: | DEAC40EAC148FF5132A05B9005B196ED8EB22908 |
| SHA256: | 3743F014B4EEFCA85496DAA65A32AB21F84DCEBB7C45158750275C40BE7FF143 |
| SSDEEP: | 49152:e0Dqzp0GnH+GXV18sP1RJTdvjhpbgfRXX53LTH9shst:e0DqzqyeGXHPfJTxjbbgfR53LBiQ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads settings of System Certificates
- Proxy.Grabber.and.Checker.exe (PID: 3460)
Reads the Internet Settings
- Proxy.Grabber.and.Checker.exe (PID: 3460)
Connects to unusual port
- Proxy.Grabber.and.Checker.exe (PID: 3460)
INFO
Reads the machine GUID from the registry
- Proxy.Grabber.and.Checker.exe (PID: 3460)
- wmpnscfg.exe (PID: 3512)
Reads the computer name
- Proxy.Grabber.and.Checker.exe (PID: 3460)
- wmpnscfg.exe (PID: 3512)
Checks supported languages
- Proxy.Grabber.and.Checker.exe (PID: 3460)
- wmpnscfg.exe (PID: 3512)
Create files in a temporary directory
- Proxy.Grabber.and.Checker.exe (PID: 3460)
Creates files or folders in the user directory
- Proxy.Grabber.and.Checker.exe (PID: 3460)
Reads Environment values
- Proxy.Grabber.and.Checker.exe (PID: 3460)
Manual execution by a user
- wmpnscfg.exe (PID: 3512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2081:03:18 22:20:22+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 842752 |
| InitializedDataSize: | 70144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcfbce |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.6.1 |
| ProductVersionNumber: | 5.0.6.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Proxy Grabber and Checker by wDude |
| CompanyName: | wDude |
| FileDescription: | Proxy Grabber and Checker by wDude |
| FileVersion: | 5.0.6.1 |
| InternalName: | Proxy Grabber and Checker.exe |
| LegalCopyright: | БатькаВсеяРашн © 2020 |
| LegalTrademarks: | wDude (LZT: БатькаВсеяРашн) |
| OriginalFileName: | Proxy Grabber and Checker.exe |
| ProductName: | PGC |
| ProductVersion: | 5.0.6.1 |
| AssemblyVersion: | 5.0.6.1 |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3460 | "C:\Users\admin\AppData\Local\Temp\Proxy.Grabber.and.Checker.exe" | C:\Users\admin\AppData\Local\Temp\Proxy.Grabber.and.Checker.exe | explorer.exe | ||||||||||||
User: admin Company: wDude Integrity Level: MEDIUM Description: Proxy Grabber and Checker by wDude Exit code: 0 Version: 5.0.6.1 Modules
| |||||||||||||||
| 3512 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 159
Read events
13 144
Write events
12
Delete events
3
Modification events
| (PID) Process: | (3460) Proxy.Grabber.and.Checker.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3512) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{254D42F1-A5A8-4619-885B-FEB84238BD71}\{66D32667-6CA6-4C3F-90FC-6DE9AFF64E37} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3512) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{254D42F1-A5A8-4619-885B-FEB84238BD71} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3512) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{D5A4089A-263F-474E-97B5-7CEB90A5F883} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
6
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\Local\Temp\Cab74B9.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\Local\Temp\Tar74A9.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:6CCBDF91F81B406AE494535B2ABF8CB2 | SHA256:33DEEDBFCD72CCCA8D802ABE75A9D85039261EC6AC655FCE4B3F36EF45ED0E48 | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\Roaming\PGC\urlsHTTP.txt | text | |
MD5:977DAC55DAAB50E52D1BF957F3339665 | SHA256:8E279274A0226D3120473A47F7238EF5CBE24EBDEAB48B9F3AE8BCB3AA46E962 | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\Roaming\PGC\urlsSOCKS4.txt | text | |
MD5:2F9B0356AE5E008C2EF3F042E03BB68E | SHA256:1AADFAB2A6B3382AC1146098779326596AB6C918AA69437C463F0017681D1F2F | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\Local\Temp\Cab74A8.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\Local\Temp\Tar74BA.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 3460 | Proxy.Grabber.and.Checker.exe | C:\Users\admin\AppData\Roaming\PGC\urlsSOCKS5.txt | text | |
MD5:A782A0FDAFEC670F77F0EBC94E9F151D | SHA256:216C945CD5A00DC06177D37E9050D7D9EC4E2C094A63AB0B8939043126270142 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
24
DNS requests
12
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3460 | Proxy.Grabber.and.Checker.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?07bb945927422fab | unknown | compressed | 61.6 Kb | unknown |
3460 | Proxy.Grabber.and.Checker.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c7e50a7e320509f2 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3460 | Proxy.Grabber.and.Checker.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3460 | Proxy.Grabber.and.Checker.exe | 188.114.96.3:443 | www.proxy-list.download | CLOUDFLARENET | NL | unknown |
3460 | Proxy.Grabber.and.Checker.exe | 104.18.11.5:443 | api.proxyscrape.com | CLOUDFLARENET | — | unknown |
3460 | Proxy.Grabber.and.Checker.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3460 | Proxy.Grabber.and.Checker.exe | 159.112.235.219:80 | — | Cloudflare London, LLC | US | unknown |
3460 | Proxy.Grabber.and.Checker.exe | 139.5.73.71:8080 | — | WorldLink Communications Pvt Ltd | NP | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.proxyscrape.com |
| unknown |
www.proxy-list.download |
| unknown |
raw.githubusercontent.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Public Proxy Service Domain in DNS Lookup (api .proxyscrape .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Public Proxy Service Domain in DNS Lookup (api .proxyscrape .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Public Proxy Service Domain in DNS Lookup (api .proxyscrape .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Public Proxy Service Domain in DNS Lookup (api .proxyscrape .com) |
3460 | Proxy.Grabber.and.Checker.exe | Potentially Bad Traffic | ET INFO Observed Public Proxy Service Domain (api .proxyscrape .com in TLS SNI) |
3460 | Proxy.Grabber.and.Checker.exe | Potentially Bad Traffic | ET INFO Observed Public Proxy Service Domain (api .proxyscrape .com in TLS SNI) |