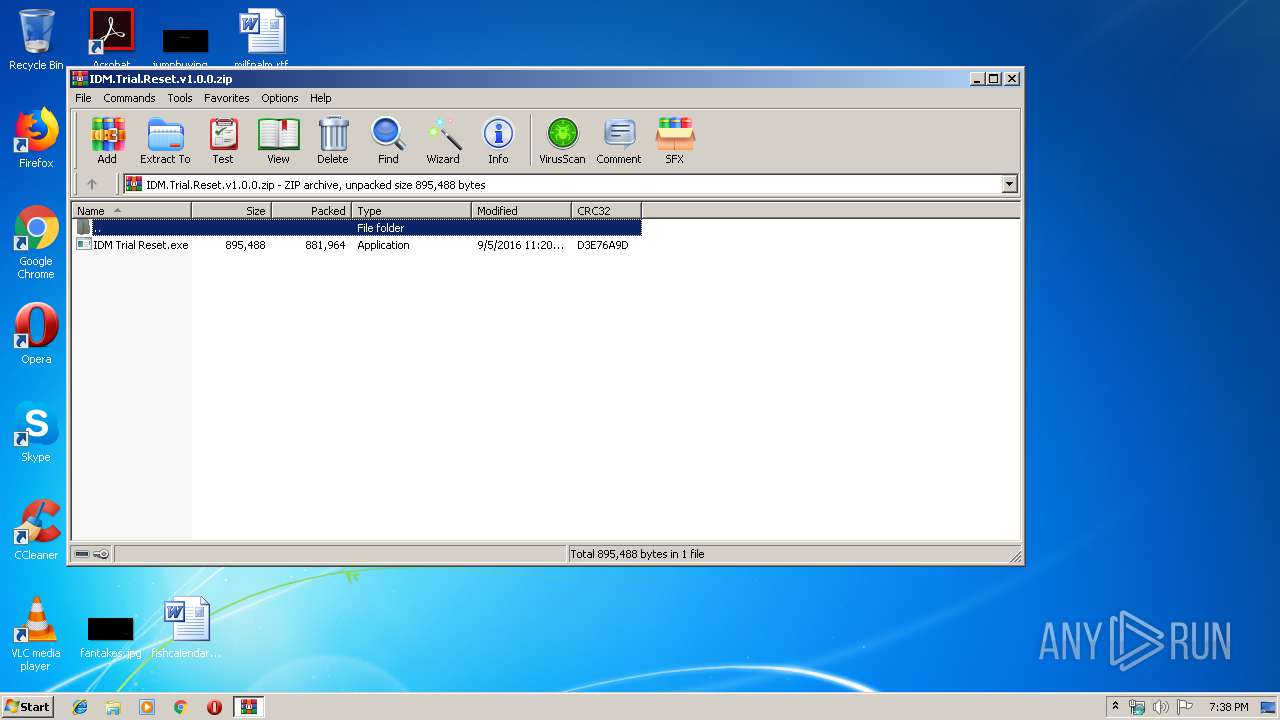
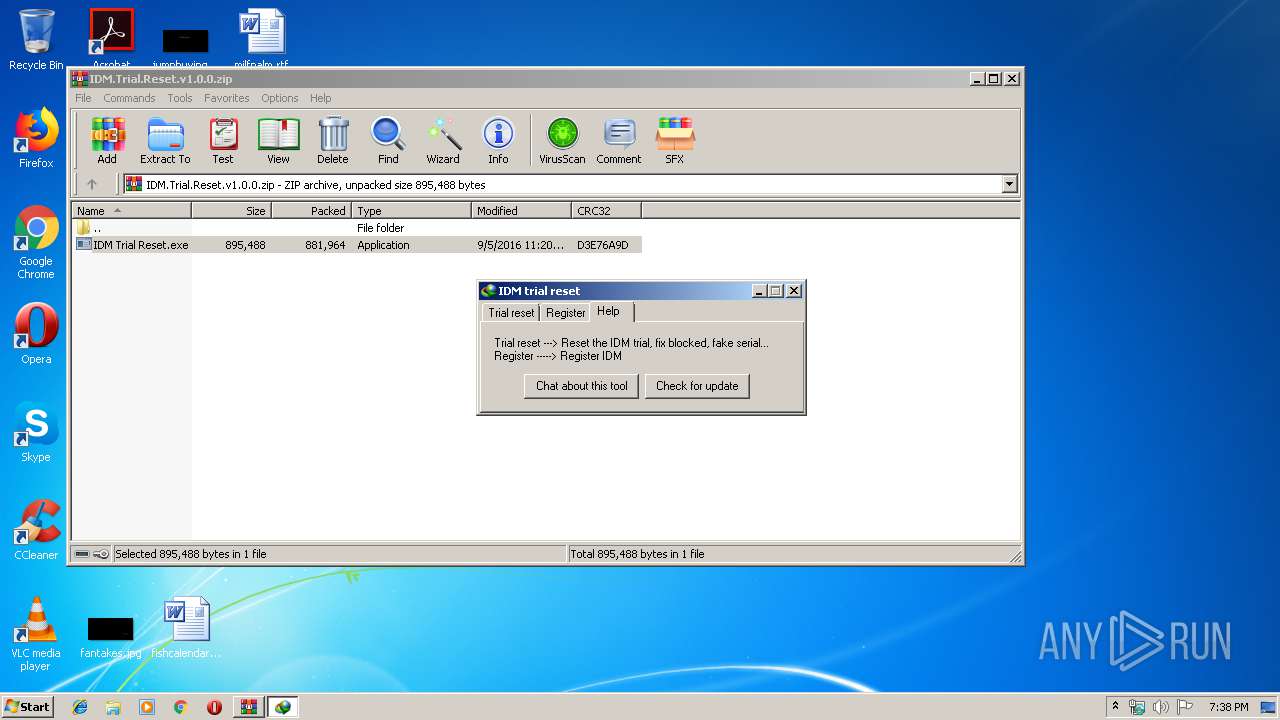
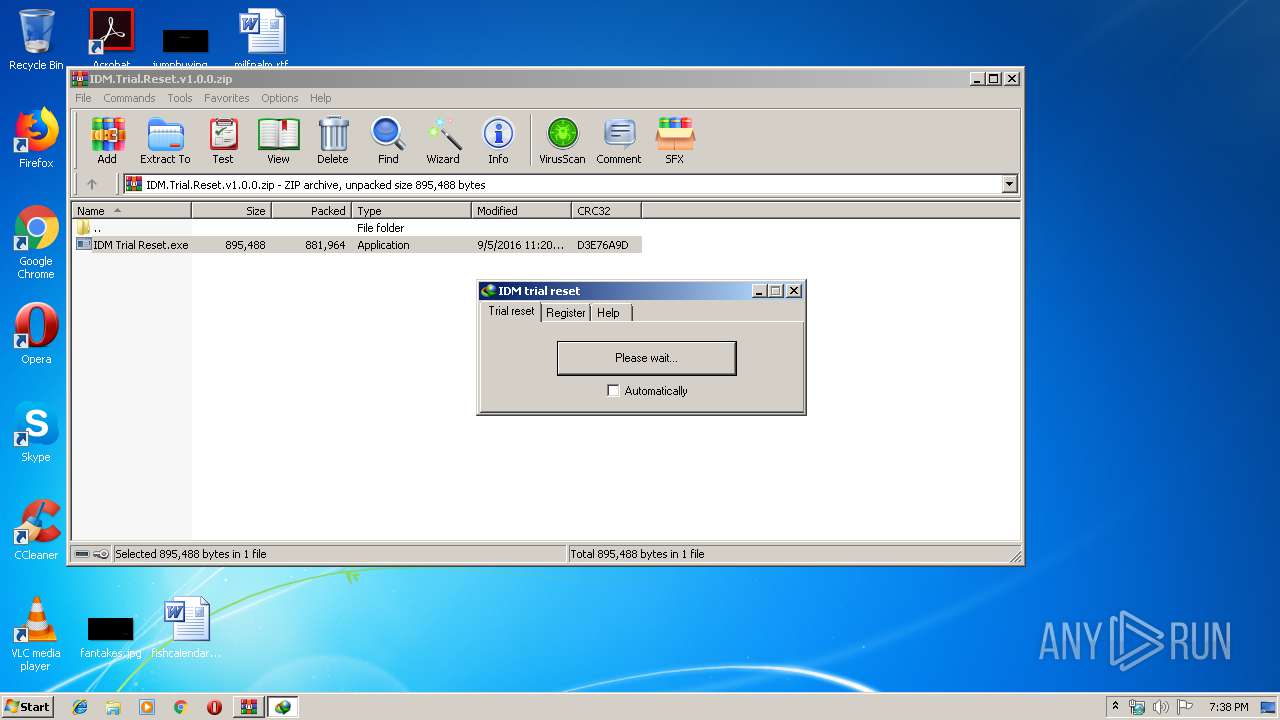
| File name: | IDM.Trial.Reset.v1.0.0.zip |
| Full analysis: | https://app.any.run/tasks/af164cd0-810a-4551-8931-e8fb6e26c185 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2019, 19:37:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 016866100C1BEFF73C59F5E02323BE46 |
| SHA1: | 60AA90998FDE73E03FFBE42BF899793B32E2EE65 |
| SHA256: | 372DC10FBE87C1744D2852877E0D36D37E034B5507F868DE61C8BA6A46D0E012 |
| SSDEEP: | 12288:F3EHTdr/G+70+d5oVe+TghBAcRlbqm9Ks3wjNind3y4/VA/Sznml3gUdfFUWgsD5:BN+g6oVe+TgrVWAAjadF/XAVha2D7l |
MALICIOUS
Application was dropped or rewritten from another process
- SetACLx32.exe (PID: 2800)
- SetACLx32.exe (PID: 932)
- IDM Trial Reset.exe (PID: 2060)
- SetACLx32.exe (PID: 2392)
- SetACLx32.exe (PID: 3184)
- SetACLx32.exe (PID: 2668)
- SetACLx32.exe (PID: 4024)
- SetACLx32.exe (PID: 3096)
- SetACLx32.exe (PID: 1848)
- SetACLx32.exe (PID: 2884)
- SetACLx32.exe (PID: 3852)
- SetACLx32.exe (PID: 716)
- SetACLx32.exe (PID: 3792)
- SetACLx32.exe (PID: 1216)
- SetACLx32.exe (PID: 964)
- SetACLx32.exe (PID: 2356)
- SetACLx32.exe (PID: 3040)
- SetACLx32.exe (PID: 2104)
- SetACLx32.exe (PID: 1024)
- SetACLx32.exe (PID: 2856)
- SetACLx32.exe (PID: 3176)
- SetACLx32.exe (PID: 2876)
- SetACLx32.exe (PID: 2156)
- SetACLx32.exe (PID: 3048)
- SetACLx32.exe (PID: 2468)
- SetACLx32.exe (PID: 3848)
- SetACLx32.exe (PID: 1932)
- SetACLx32.exe (PID: 1316)
- SetACLx32.exe (PID: 2876)
- SetACLx32.exe (PID: 1956)
- SetACLx32.exe (PID: 3396)
- SetACLx32.exe (PID: 284)
- SetACLx32.exe (PID: 3868)
- SetACLx32.exe (PID: 4016)
- SetACLx32.exe (PID: 3460)
- SetACLx32.exe (PID: 2144)
- SetACLx32.exe (PID: 3048)
- SetACLx32.exe (PID: 2844)
- SetACLx32.exe (PID: 2356)
- SetACLx32.exe (PID: 1904)
- SetACLx32.exe (PID: 3968)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1484)
- IDM Trial Reset.exe (PID: 2060)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3088)
Starts CMD.EXE for commands execution
- IDM Trial Reset.exe (PID: 2060)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:09:06 05:20:13 |
| ZipCRC: | 0xd3e76a9d |
| ZipCompressedSize: | 881964 |
| ZipUncompressedSize: | 895488 |
| ZipFileName: | IDM Trial Reset.exe |
Total processes
133
Monitored processes
53
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Users\admin\AppData\Local\Temp\SetACLx32.exe" -on HKCU\Software\Classes\Wow6432Node\CLSID\{07999AC3-058B-40BF-984F-69EB1E554CA7} -ot reg -actn ace -ace "n:everyone;p:full" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 716 | "C:\Users\admin\AppData\Local\Temp\SetACLx32.exe" -on HKCU\Software\Classes\CLSID\{6DDF00DB-1234-46EC-8356-27E7B2051192} -ot reg -actn ace -ace "n:everyone;p:full" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 856 | findstr /b -1: | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 932 | "C:\Users\admin\AppData\Local\Temp\SetACLx32.exe" -on HKCU\Software\Classes\CLSID\{6DDF00DB-1234-46EC-8356-27E7B2051192} -ot reg -actn setowner -ownr "n:S-1-1-0" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 5 Version: 3.0.6.0 Modules
| |||||||||||||||
| 964 | "C:\Users\admin\AppData\Local\Temp\SetACLx32.exe" -on HKCU\Software\Classes\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C} -ot reg -actn setowner -ownr "n:S-1-1-0" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 5 Version: 3.0.6.0 Modules
| |||||||||||||||
| 1024 | "C:\Users\admin\AppData\Local\Temp\SetACLx32.exe" -on HKCU\Software\Classes\CLSID\{D5B91409-A8CA-4973-9A0B-59F713D25671} -ot reg -actn ace -ace "n:everyone;p:full" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 1096 | findstr /N . C:\Users\admin\AppData\Local\Temp\reg_query.tmp | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1216 | "C:\Users\admin\AppData\Local\Temp\SetACLx32.exe" -on HKLM\Software\Classes\CLSID\{6DDF00DB-1234-46EC-8356-27E7B2051192} -ot reg -actn ace -ace "n:everyone;p:full" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 1292 | "C:\Windows\system32\cmd.exe" /c findstr /N /I cDTvBFquXk0 C:\Users\admin\AppData\Local\Temp\reg_query.tmp | C:\Windows\system32\cmd.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1316 | "C:\Users\admin\AppData\Local\Temp\SetACLx32.exe" -on HKCU\Software\Classes\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C} -ot reg -actn ace -ace "n:everyone;p:full" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
Total events
19 283
Read events
19 271
Write events
12
Delete events
0
Modification events
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IDM.Trial.Reset.v1.0.0.zip | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autC7EE.tmp | — | |
MD5:— | SHA256:— | |||
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autC7EF.tmp | — | |
MD5:— | SHA256:— | |||
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autC7F0.tmp | — | |
MD5:— | SHA256:— | |||
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autC7F1.tmp | — | |
MD5:— | SHA256:— | |||
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autC821.tmp | — | |
MD5:— | SHA256:— | |||
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_trial.reg | text | |
MD5:237962E36948F3D0C9EC42EFA289AC52 | SHA256:40AD93CF424EEE41A0877B11ACB92F7F12D58AB3AA6FA6D64D92CFBBE11695A2 | |||
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_reset.reg | text | |
MD5:17EBF21FCCAC9756EAB46EB64BA6C029 | SHA256:290A3F67BBBDBD5C1101E90921475C2B95E97DC69A3141412FBAC79FCADD3EE8 | |||
| 3088 | cmd.exe | C:\Users\admin\AppData\Local\Temp\reg_query.tmp | text | |
MD5:— | SHA256:— | |||
| 1484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1484.10474\IDM Trial Reset.exe | executable | |
MD5:064F82094AE6A6E22C28A6F1EF868A26 | SHA256:A2D2B22CD0D5628976EB5996A8B20F3B5AC468907910DBC3F826F1069D435587 | |||
| 2060 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | executable | |
MD5:3E350EB5DF15C06DEC400A39DD1C6F29 | SHA256:427FF43693CB3CA2812C4754F607F107A6B2D3F5A8B313ADDEE57D89982DF419 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report