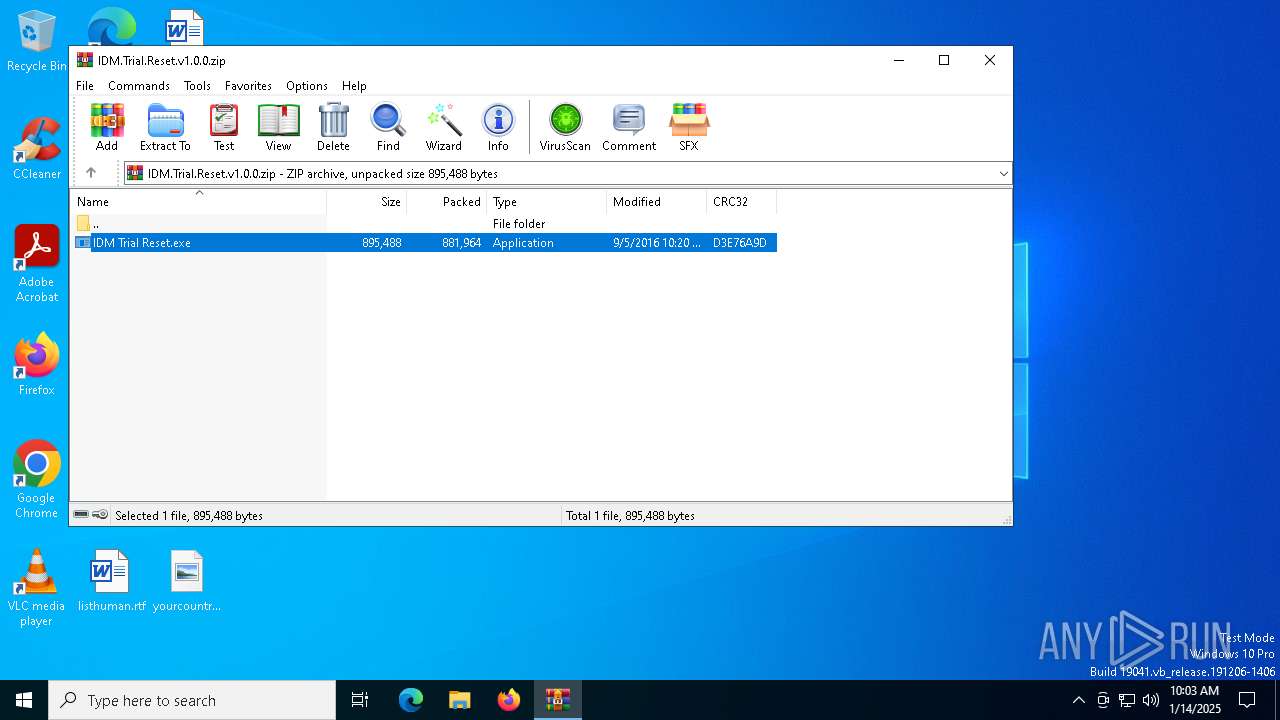
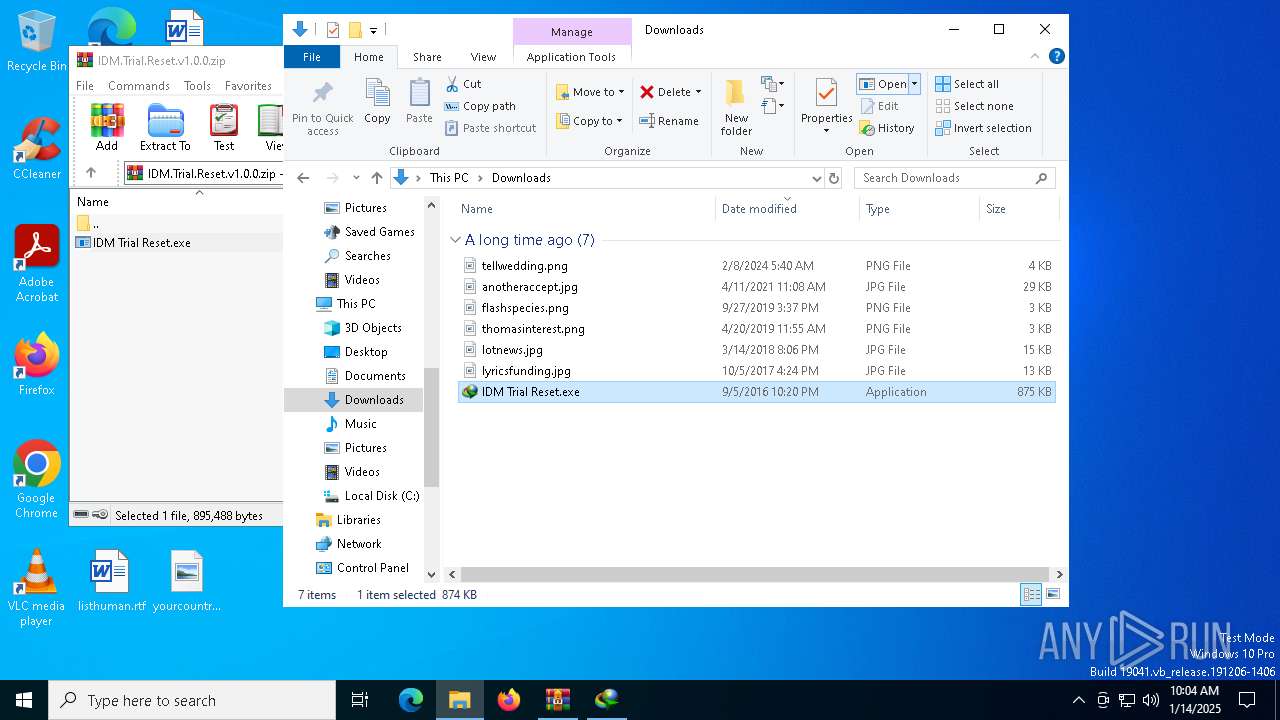
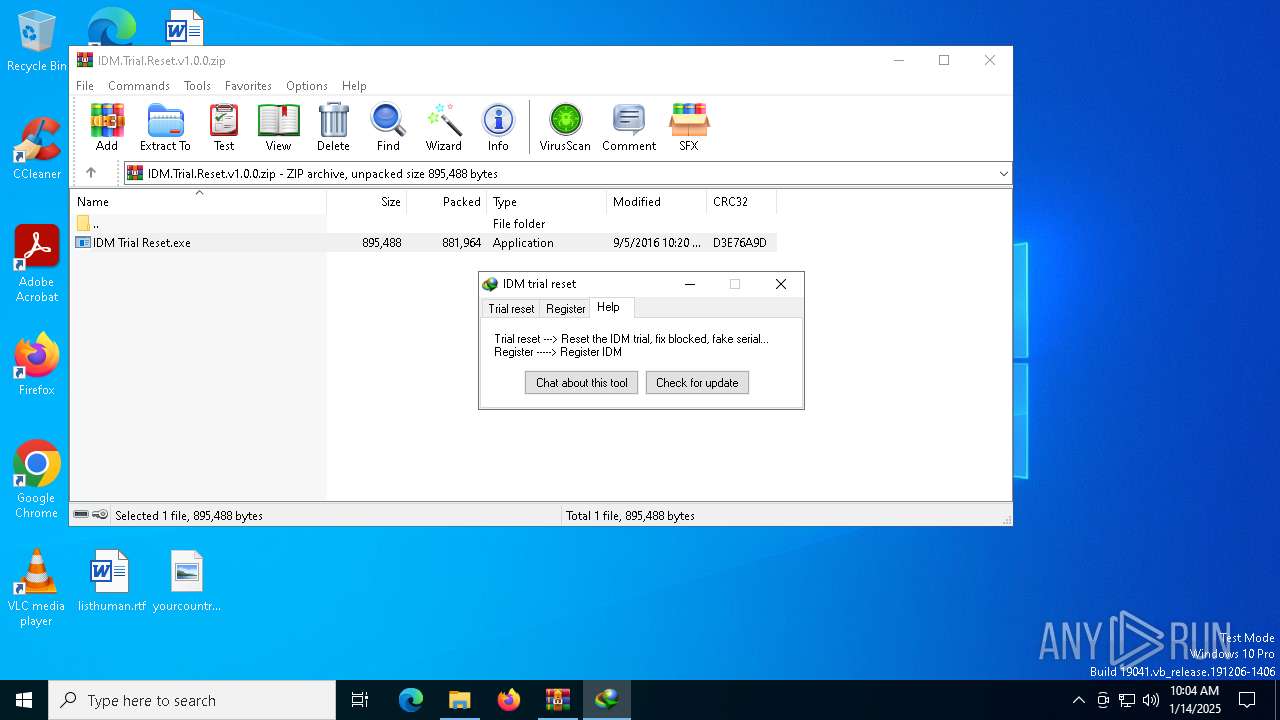
| File name: | IDM.Trial.Reset.v1.0.0.zip |
| Full analysis: | https://app.any.run/tasks/636b0a37-894e-45ef-bd72-24e66b56a241 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2025, 10:03:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 016866100C1BEFF73C59F5E02323BE46 |
| SHA1: | 60AA90998FDE73E03FFBE42BF899793B32E2EE65 |
| SHA256: | 372DC10FBE87C1744D2852877E0D36D37E034B5507F868DE61C8BA6A46D0E012 |
| SSDEEP: | 12288:F3EHTdr/G+70+d5oVe+TghBAcRlbqm9Ks3wjNind3y4/VA/Sznml3gUdfFUWgsD5:BN+g6oVe+TgrVWAAjadF/XAVha2D7l |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6528)
Antivirus name has been found in the command line (generic signature)
- IDM Trial Reset.exe (PID: 6172)
- IDM Trial Reset.exe (PID: 3208)
- IDM Trial Reset.exe (PID: 4264)
- IDM Trial Reset.exe (PID: 5460)
SUSPICIOUS
Executable content was dropped or overwritten
- IDM Trial Reset.exe (PID: 6172)
Starts CMD.EXE for commands execution
- IDM Trial Reset.exe (PID: 6172)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 540)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6528)
The sample compiled with english language support
- WinRAR.exe (PID: 6528)
- IDM Trial Reset.exe (PID: 6172)
Reads mouse settings
- IDM Trial Reset.exe (PID: 6172)
- IDM Trial Reset.exe (PID: 3208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6528)
Manual execution by a user
- IDM Trial Reset.exe (PID: 6172)
- IDM Trial Reset.exe (PID: 3208)
- IDM Trial Reset.exe (PID: 4264)
- IDM Trial Reset.exe (PID: 5460)
Checks supported languages
- IDM Trial Reset.exe (PID: 6172)
Create files in a temporary directory
- IDM Trial Reset.exe (PID: 6172)
- IDM Trial Reset.exe (PID: 4264)
- IDM Trial Reset.exe (PID: 3208)
- IDM Trial Reset.exe (PID: 5460)
The process uses AutoIt
- IDM Trial Reset.exe (PID: 6172)
UPX packer has been detected
- IDM Trial Reset.exe (PID: 6172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:09:06 05:20:26 |
| ZipCRC: | 0xd3e76a9d |
| ZipCompressedSize: | 881964 |
| ZipUncompressedSize: | 895488 |
| ZipFileName: | IDM Trial Reset.exe |
Total processes
137
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | C:\WINDOWS\system32\cmd.exe /c reg query hkcr\clsid /s > C:\Users\admin\AppData\Local\Temp\reg_query.tmp | C:\Windows\SysWOW64\cmd.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | reg query hkcr\clsid /s | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | "C:\Users\admin\Downloads\IDM Trial Reset.exe" | C:\Users\admin\Downloads\IDM Trial Reset.exe | explorer.exe | ||||||||||||
User: admin Company: J2TeaM Integrity Level: HIGH Description: Use IDM forever without cracking Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4264 | "C:\Users\admin\Downloads\IDM Trial Reset.exe" | C:\Users\admin\Downloads\IDM Trial Reset.exe | explorer.exe | ||||||||||||
User: admin Company: J2TeaM Integrity Level: HIGH Description: Use IDM forever without cracking Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4504 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5460 | "C:\Users\admin\Downloads\IDM Trial Reset.exe" | C:\Users\admin\Downloads\IDM Trial Reset.exe | — | explorer.exe | |||||||||||
User: admin Company: J2TeaM Integrity Level: MEDIUM Description: Use IDM forever without cracking Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5748 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6172 | "C:\Users\admin\Downloads\IDM Trial Reset.exe" | C:\Users\admin\Downloads\IDM Trial Reset.exe | explorer.exe | ||||||||||||
User: admin Company: J2TeaM Integrity Level: MEDIUM Description: Use IDM forever without cracking Version: 1.0.0.0 Modules
| |||||||||||||||
| 6528 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\IDM.Trial.Reset.v1.0.0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
17 411
Read events
17 387
Write events
11
Delete events
13
Modification events
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IDM.Trial.Reset.v1.0.0.zip | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
3
Suspicious files
20
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_reset.reg | text | |
MD5:17EBF21FCCAC9756EAB46EB64BA6C029 | SHA256:290A3F67BBBDBD5C1101E90921475C2B95E97DC69A3141412FBAC79FCADD3EE8 | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | executable | |
MD5:451AE03D3C92777F09840CA56F08AB62 | SHA256:D5E779D151772504662E8226EB4107330FFA7A51209EEE42B6D5883D99100BA9 | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autED71.tmp | binary | |
MD5:E68C65421712C99C0FA515EB087B412B | SHA256:2CE685037E366A0FD2FF1827C20F1866BCBE23D646DFCE30A459B8FF3C1B4F2E | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_trial.reg | text | |
MD5:237962E36948F3D0C9EC42EFA289AC52 | SHA256:40AD93CF424EEE41A0877B11ACB92F7F12D58AB3AA6FA6D64D92CFBBE11695A2 | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | executable | |
MD5:3E350EB5DF15C06DEC400A39DD1C6F29 | SHA256:427FF43693CB3CA2812C4754F607F107A6B2D3F5A8B313ADDEE57D89982DF419 | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_reg.reg | text | |
MD5:3DEDFE7770A57CA2BCB76D01D1756EE6 | SHA256:832134EB65B2A91BE5B6584B48AB69B4B7CE9B6228EA4738F6D1B7A8A0E1915E | |||
| 6528 | WinRAR.exe | C:\Users\admin\Downloads\IDM Trial Reset.exe | executable | |
MD5:064F82094AE6A6E22C28A6F1EF868A26 | SHA256:A2D2B22CD0D5628976EB5996A8B20F3B5AC468907910DBC3F826F1069D435587 | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autED83.tmp | binary | |
MD5:2EBB8A2070729BC3CAE5B5E1CC27C963 | SHA256:B951A1F1EC92F71EEF08E59988267CC19BF35286B90A2CBE50C4B1062C2FD0AC | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autEDB3.tmp | binary | |
MD5:715EC543E4A386475E2105954DAD0929 | SHA256:C28E0CB287457A5B00BF34983D00256E263C00231B5CBB0F8BEF4233C47F7D55 | |||
| 6172 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\autED70.tmp | binary | |
MD5:D71743C02DF05822F49FF9E232DE76F0 | SHA256:62AAECFD2ECA11B635DDC0AC246F9EFC991A56CAE43E009EABA9367BB287AD89 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
31
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 304 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3732 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6748 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3732 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.59:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |