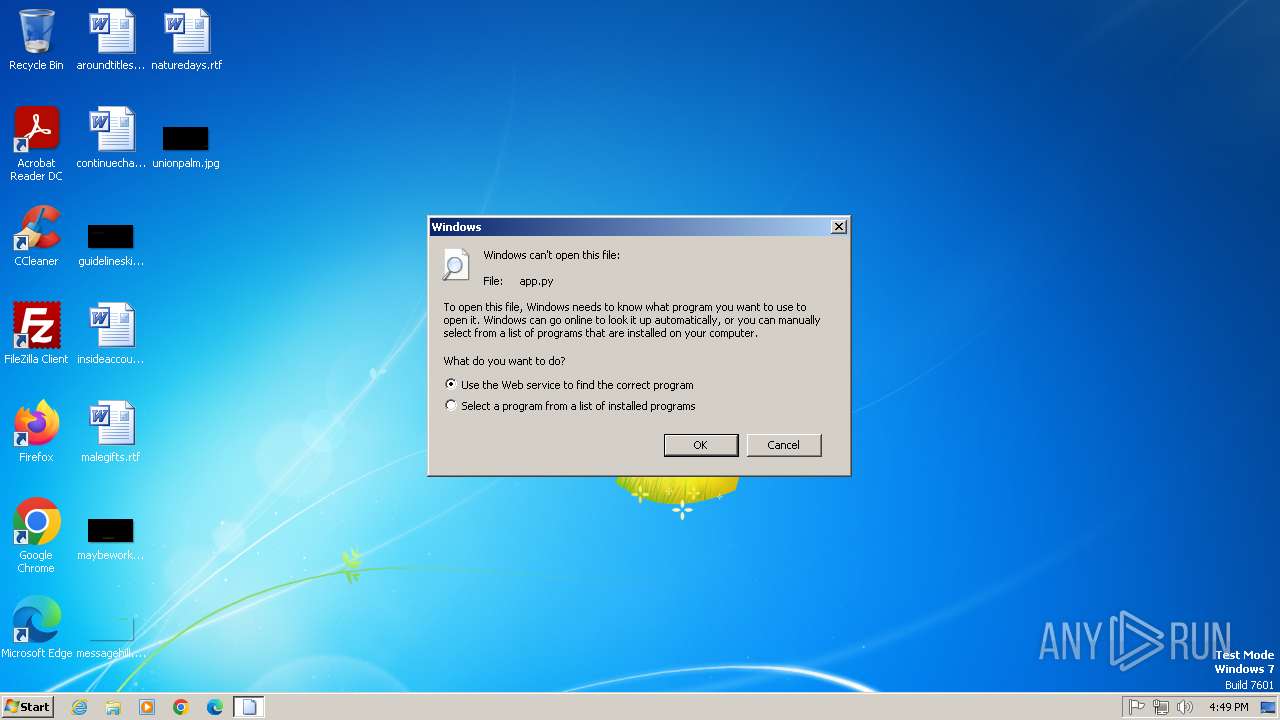
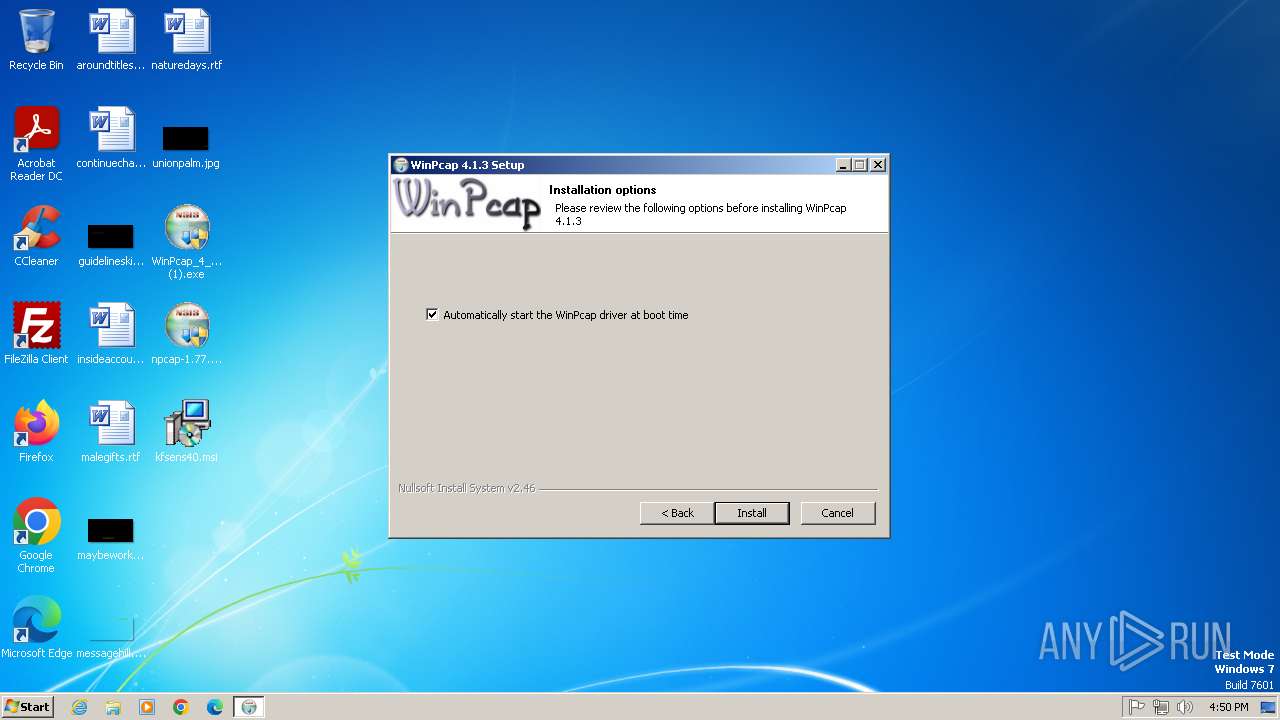
| File name: | app.py |
| Full analysis: | https://app.any.run/tasks/d3a68476-752e-4b54-b0e9-83c7654453cd |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2025, 15:49:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-script.python |
| File info: | Python script, ASCII text executable, with CRLF line terminators |
| MD5: | 97D2E53A9D0486B6231D96E93AAD4870 |
| SHA1: | A17FDAE9A1AFB3CF57110876D925B05C48BB4DD2 |
| SHA256: | 36EF8A035886ADC14F67A321078A5BEDBB7506DEDC41EE9699F15D991DC8734D |
| SSDEEP: | 24:WYt13LoRmjRxrCn3u1FIM+a38n5TFuc+GFSIH+TykjryFan:Pr3LJREn3Q7ITFAG0IeTykHyFan |
MALICIOUS
Starts NET.EXE for service management
- WinPcap_4_1_3 (1).exe (PID: 2944)
- net.exe (PID: 2812)
Run PowerShell with an invisible window
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1240)
- powershell.exe (PID: 1596)
- powershell.exe (PID: 2924)
- powershell.exe (PID: 2832)
Uses Task Scheduler to run other applications
- ns9BBE.tmp (PID: 2992)
Changes the autorun value in the registry
- msiexec.exe (PID: 3168)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
Creates files in the driver directory
- WinPcap_4_1_3 (1).exe (PID: 2944)
- drvinst.exe (PID: 2708)
- NPFInstall.exe (PID: 3920)
The process creates files with name similar to system file names
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
Executable content was dropped or overwritten
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
- NPFInstall.exe (PID: 3920)
- drvinst.exe (PID: 2708)
Creates or modifies Windows services
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
Creates a software uninstall entry
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
Drops a system driver (possible attempt to evade defenses)
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
- NPFInstall.exe (PID: 3920)
- drvinst.exe (PID: 2708)
Starts CMD.EXE for commands execution
- nsE9A4.tmp (PID: 2620)
- nsEA13.tmp (PID: 3952)
- ns7F50.tmp (PID: 4012)
Stops a currently running service
- sc.exe (PID: 3172)
- sc.exe (PID: 4052)
Starts SC.EXE for service management
- cmd.exe (PID: 1800)
- cmd.exe (PID: 3260)
Windows service management via SC.EXE
- sc.exe (PID: 3252)
- sc.exe (PID: 1736)
Uses WMIC.EXE to obtain quick Fix Engineering (patches) data
- cmd.exe (PID: 3388)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3388)
Starts application with an unusual extension
- npcap-1.77.exe (PID: 1948)
Reads the Internet Settings
- WMIC.exe (PID: 4092)
- msiexec.exe (PID: 1576)
The process hide an interactive prompt from the user
- nsF1A6.tmp (PID: 2680)
- nsEC08.tmp (PID: 2312)
- nsF747.tmp (PID: 2608)
- nsFCE5.tmp (PID: 2920)
- ns941B.tmp (PID: 3744)
Starts POWERSHELL.EXE for commands execution
- nsEC08.tmp (PID: 2312)
- nsF1A6.tmp (PID: 2680)
- nsF747.tmp (PID: 2608)
- nsFCE5.tmp (PID: 2920)
- ns941B.tmp (PID: 3744)
The process bypasses the loading of PowerShell profile settings
- nsEC08.tmp (PID: 2312)
- nsFCE5.tmp (PID: 2920)
- nsF747.tmp (PID: 2608)
- nsF1A6.tmp (PID: 2680)
- ns941B.tmp (PID: 3744)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 2924)
- powershell.exe (PID: 1240)
- powershell.exe (PID: 1596)
Removes files via Powershell
- powershell.exe (PID: 2924)
- powershell.exe (PID: 1596)
Adds/modifies Windows certificates
- certutil.exe (PID: 2744)
Executes as Windows Service
- VSSVC.exe (PID: 1116)
- kfmond.exe (PID: 2380)
- kfsnserv.exe (PID: 1624)
Reads settings of System Certificates
- rundll32.exe (PID: 3596)
- NPFInstall.exe (PID: 3920)
Reads security settings of Internet Explorer
- NPFInstall.exe (PID: 3920)
- msiexec.exe (PID: 1576)
Application launched itself
- msiexec.exe (PID: 3168)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3168)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 2772)
INFO
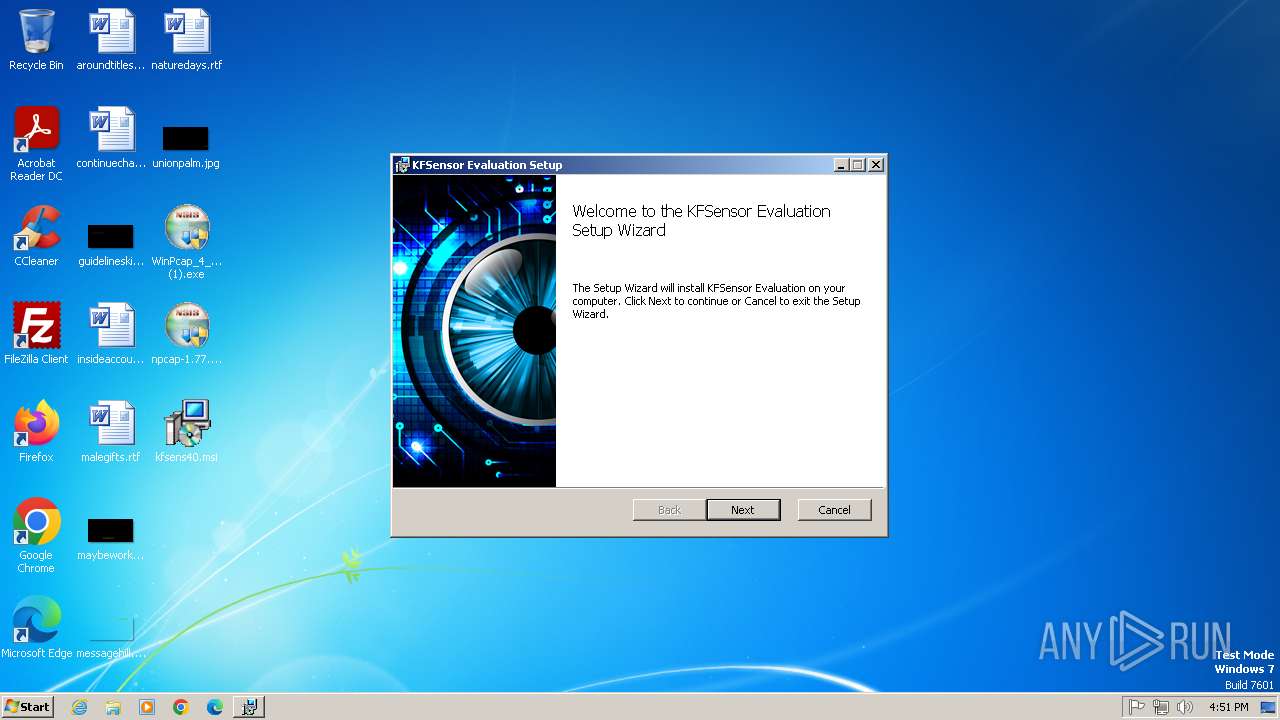
Manual execution by a user
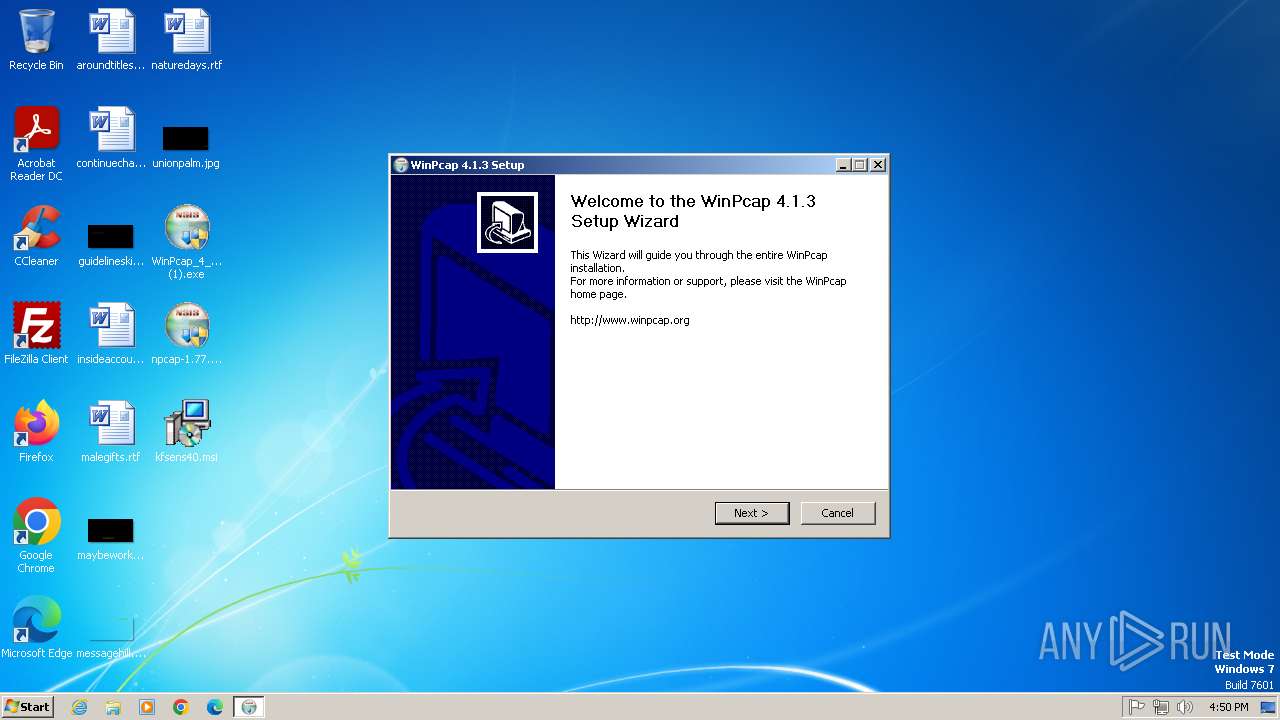
- WinPcap_4_1_3 (1).exe (PID: 2944)
- WinPcap_4_1_3 (1).exe (PID: 3308)
- npcap-1.77.exe (PID: 3436)
- npcap-1.77.exe (PID: 1948)
- msiexec.exe (PID: 1500)
- cmd.exe (PID: 2772)
Reads the computer name
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
- NPFInstall.exe (PID: 2784)
- NPFInstall.exe (PID: 3796)
- NPFInstall.exe (PID: 3920)
- drvinst.exe (PID: 2708)
- msiexec.exe (PID: 3168)
- kfsnserv.exe (PID: 1624)
- msiexec.exe (PID: 1576)
- kfsensmonitor.exe (PID: 2408)
- kfmond.exe (PID: 2380)
Reads Environment values
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
Checks supported languages
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
- NPFInstall.exe (PID: 2784)
- nsE9A4.tmp (PID: 2620)
- nsEA13.tmp (PID: 3952)
- ns7F50.tmp (PID: 4012)
- nsE83C.tmp (PID: 2416)
- nsEC08.tmp (PID: 2312)
- nsF1A6.tmp (PID: 2680)
- nsF65A.tmp (PID: 2596)
- nsF6D8.tmp (PID: 3944)
- nsF747.tmp (PID: 2608)
- nsFCE5.tmp (PID: 2920)
- ns12C.tmp (PID: 3644)
- NPFInstall.exe (PID: 3380)
- ns296.tmp (PID: 148)
- ns382.tmp (PID: 1120)
- ns40F.tmp (PID: 3872)
- NPFInstall.exe (PID: 3796)
- NPFInstall.exe (PID: 3920)
- drvinst.exe (PID: 2708)
- ns1AA.tmp (PID: 268)
- ns218.tmp (PID: 3600)
- ns9BBE.tmp (PID: 2992)
- ns941B.tmp (PID: 3744)
- msiexec.exe (PID: 3168)
- kfmond.exe (PID: 2380)
- kfsnserv.exe (PID: 1624)
- msiexec.exe (PID: 1576)
- kfsensmonitor.exe (PID: 2408)
Creates files in the program directory
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
- NPFInstall.exe (PID: 2784)
Create files in a temporary directory
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
- NPFInstall.exe (PID: 3920)
- msiexec.exe (PID: 3168)
The sample compiled with english language support
- WinPcap_4_1_3 (1).exe (PID: 2944)
- npcap-1.77.exe (PID: 1948)
- msiexec.exe (PID: 1500)
- msiexec.exe (PID: 3168)
Reads the machine GUID from the registry
- NPFInstall.exe (PID: 3920)
- drvinst.exe (PID: 2708)
- msiexec.exe (PID: 3168)
- msiexec.exe (PID: 1576)
Reads the software policy settings
- drvinst.exe (PID: 2708)
- rundll32.exe (PID: 3596)
- NPFInstall.exe (PID: 3920)
- msiexec.exe (PID: 1500)
- msiexec.exe (PID: 3168)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3596)
- msiexec.exe (PID: 1500)
Adds/modifies Windows certificates
- drvinst.exe (PID: 2708)
Launching a file from Task Scheduler
- ns9BBE.tmp (PID: 2992)
Creates a software uninstall entry
- msiexec.exe (PID: 3168)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1500)
- msiexec.exe (PID: 3168)
Launching a file from a Registry key
- msiexec.exe (PID: 3168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
133
Monitored processes
63
Malicious processes
6
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Users\admin\AppData\Local\Temp\nsk7F20.tmp\ns296.tmp" "C:\Program Files\Npcap\NPFInstall.exe" -n -c | C:\Users\admin\AppData\Local\Temp\nsk7F20.tmp\ns296.tmp | — | npcap-1.77.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 268 | "C:\Users\admin\AppData\Local\Temp\nsk7F20.tmp\ns1AA.tmp" certutil.exe -addstore -f "Root" "C:\Users\admin\AppData\Local\Temp\nsk7F20.tmp\5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25.sst" | C:\Users\admin\AppData\Local\Temp\nsk7F20.tmp\ns1AA.tmp | — | npcap-1.77.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 2148086027 Modules
| |||||||||||||||
| 656 | SCHTASKS.EXE /Create /F /RU SYSTEM /SC ONSTART /TN npcapwatchdog /TR "'C:\Program Files\Npcap\CheckStatus.bat'" /NP | C:\Windows\System32\schtasks.exe | — | ns9BBE.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1116 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1120 | "C:\Users\admin\AppData\Local\Temp\nsk7F20.tmp\ns382.tmp" "C:\Program Files\Npcap\NPFInstall.exe" -n -iw | C:\Users\admin\AppData\Local\Temp\nsk7F20.tmp\ns382.tmp | — | npcap-1.77.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1240 | powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "Get-ChildItem Cert:\LocalMachine\Root | Where-Object {$_.Thumbprint -eq '5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25'} | Sort-Object -Descending -Property FriendlyName | Select-Object -Skip 1 | Remove-Item" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | nsF747.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1500 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\kfsens40.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | C:\Windows\System32\findstr.exe "^KB4474419" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | C:\Windows\system32\MsiExec.exe -Embedding C917914919B2511B4718D4247243A4BB C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "If (Get-ChildItem Cert:\LocalMachine\Root\5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25){certutil.exe -verifystore 'Root' '5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25';If($LASTEXITCODE -ne 0){Remove-Item Cert:\LocalMachine\Root\5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25}}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | nsFCE5.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
45 037
Read events
44 017
Write events
988
Delete events
32
Modification events
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\NPF |
| Operation: | write | Name: | Start |
Value: 2 | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | DisplayName |
Value: WinPcap 4.1.3 | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\WinPcap\uninstall.exe | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | Publisher |
Value: Riverbed Technology, Inc. | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.riverbed.com/ | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | URLUpdateInfo |
Value: http://www.winpcap.org | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | VersionMajor |
Value: 4 | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | VersionMinor |
Value: 1 | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | DisplayVersion |
Value: 4.1.0.2980 | |||
| (PID) Process: | (2944) WinPcap_4_1_3 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WinPcapInst |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\WinPcap\uninstall.exe | |||
Executable files
64
Suspicious files
41
Text files
226
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | WinPcap_4_1_3 (1).exe | C:\Users\admin\AppData\Local\Temp\nse6379.tmp\ioSpecial.ini | ini | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Users\admin\AppData\Local\Temp\nse6379.tmp\modern-header.bmp | image | |
MD5:D8F59A707B2A5000C7903595EDDC3D48 | SHA256:C0E284FDE834FE8A6F90504DBA7ABFF25B1E7DD4611483341203FD3EFC5DE8A6 | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Program Files\WinPcap\WinPcapInstall.dll | executable | |
MD5:E78291558CB803DFD091AD8FB56FEECC | SHA256:D9F4CD9F0E1BC9A138FB4DA6F83C92C3E86EB3DE4F988D5943D75C9B1DC6BB9D | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Program Files\WinPcap\install.log | text | |
MD5:6A69C0B7A263CDC8D261F73C406DB6BB | SHA256:30DD77859CDD3854DD387CBA3D1419F68B8D21C046D00A0F4D2619627CD90C73 | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Windows\System32\pthreadVC.dll | executable | |
MD5:F04A90F917BA10AE2DCBE859870F4DEA | SHA256:99C61ABF41C3AEC38CAB3ED6270ADBCA9A247BBF5F9AA9D29ECB0659A5527F48 | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Users\admin\AppData\Local\Temp\nse6379.tmp\bootOptions.ini | binary | |
MD5:9F64B7E590B32B5BA414F4301FB8B3D5 | SHA256:F6F2E247226AB06E9B56AE2D10CCD02D9298ABCCAC85C56ABFA19E5587446D54 | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Windows\System32\drivers\npf.sys | executable | |
MD5:25401B0C9576C8456B3E0BBD74FF0771 | SHA256:BB569C99360A631850537DC2EDA0BF85D091CC30BD98B3FD2AC9DABDFB7741DA | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Users\admin\AppData\Local\Temp\nse6379.tmp\ExecDos.dll | executable | |
MD5:A7CD6206240484C8436C66AFB12BDFBF | SHA256:69AC56D2FDF3C71B766D3CC49B33B36F1287CC2503310811017467DFCB455926 | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Windows\System32\Packet.dll | executable | |
MD5:86316BE34481C1ED5B792169312673FD | SHA256:49656C178B17198470AD6906E9EE0865F16F01C1DBBF11C613B55A07246A7918 | |||
| 2944 | WinPcap_4_1_3 (1).exe | C:\Users\admin\AppData\Local\Temp\nse6379.tmp\System.dll | executable | |
MD5:C17103AE9072A06DA581DEC998343FC1 | SHA256:DC58D8AD81CACB0C1ED72E33BFF8F23EA40B5252B5BB55D393A0903E6819AE2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |