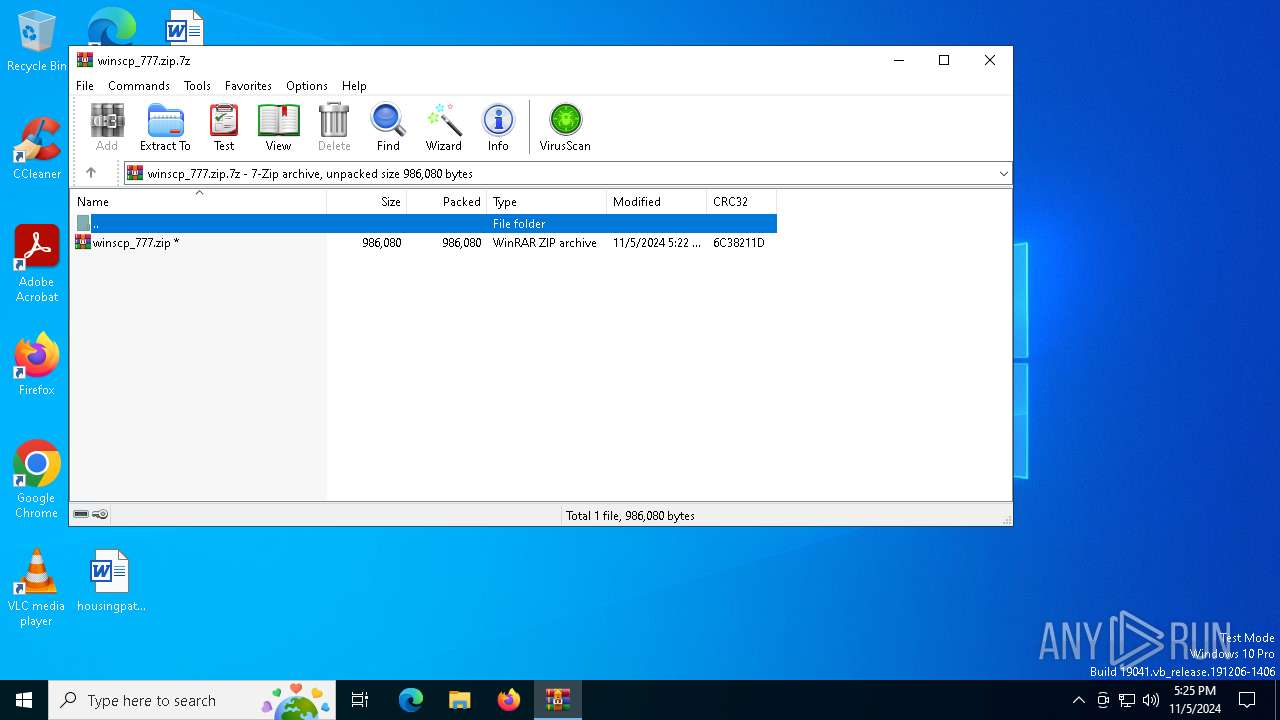
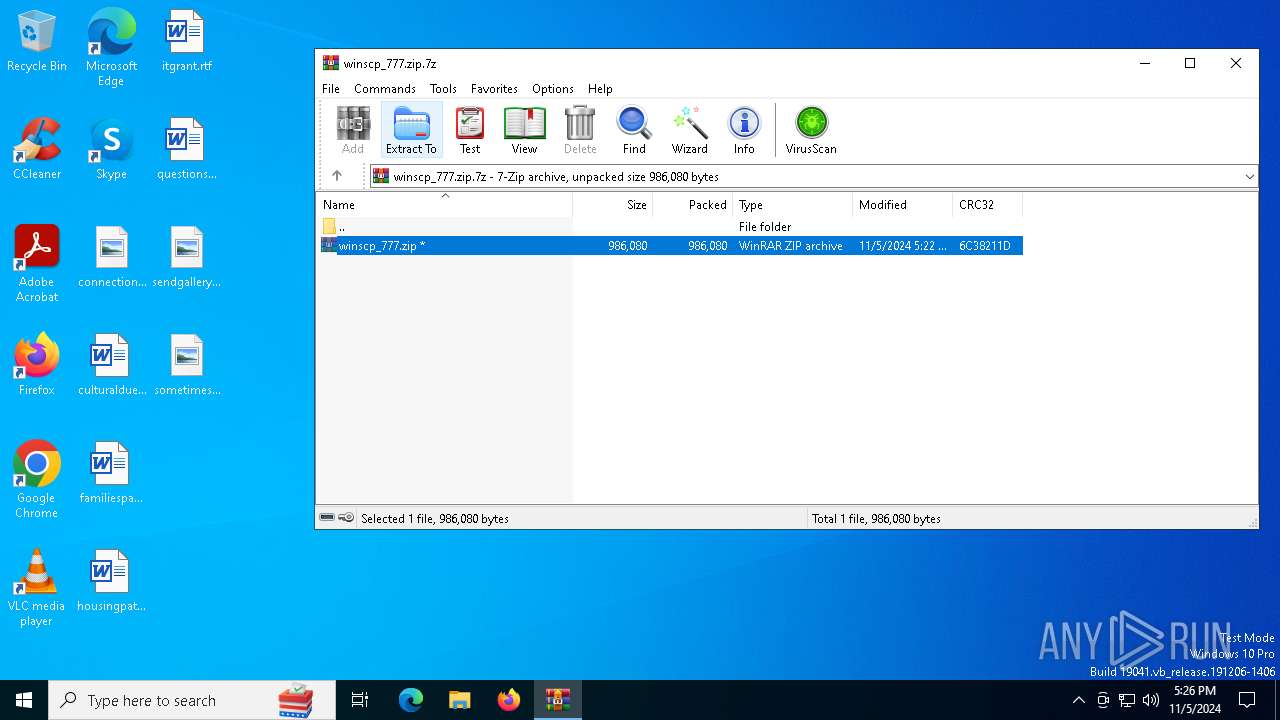
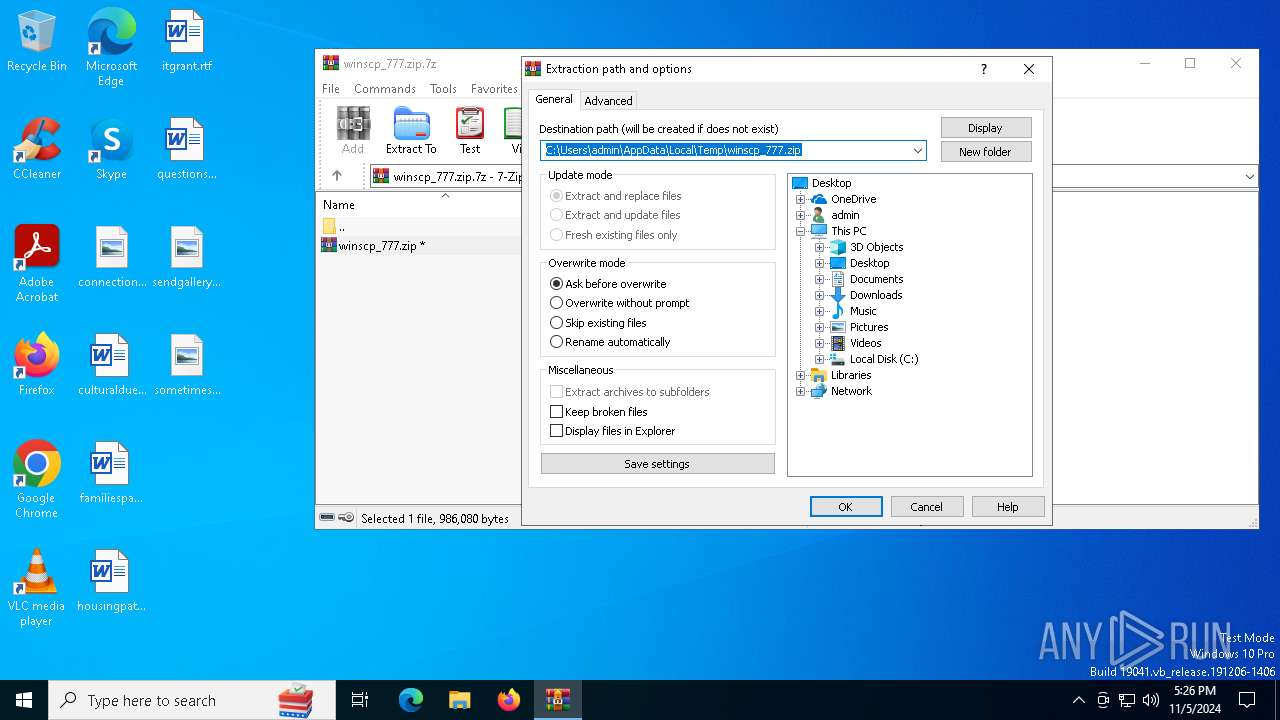
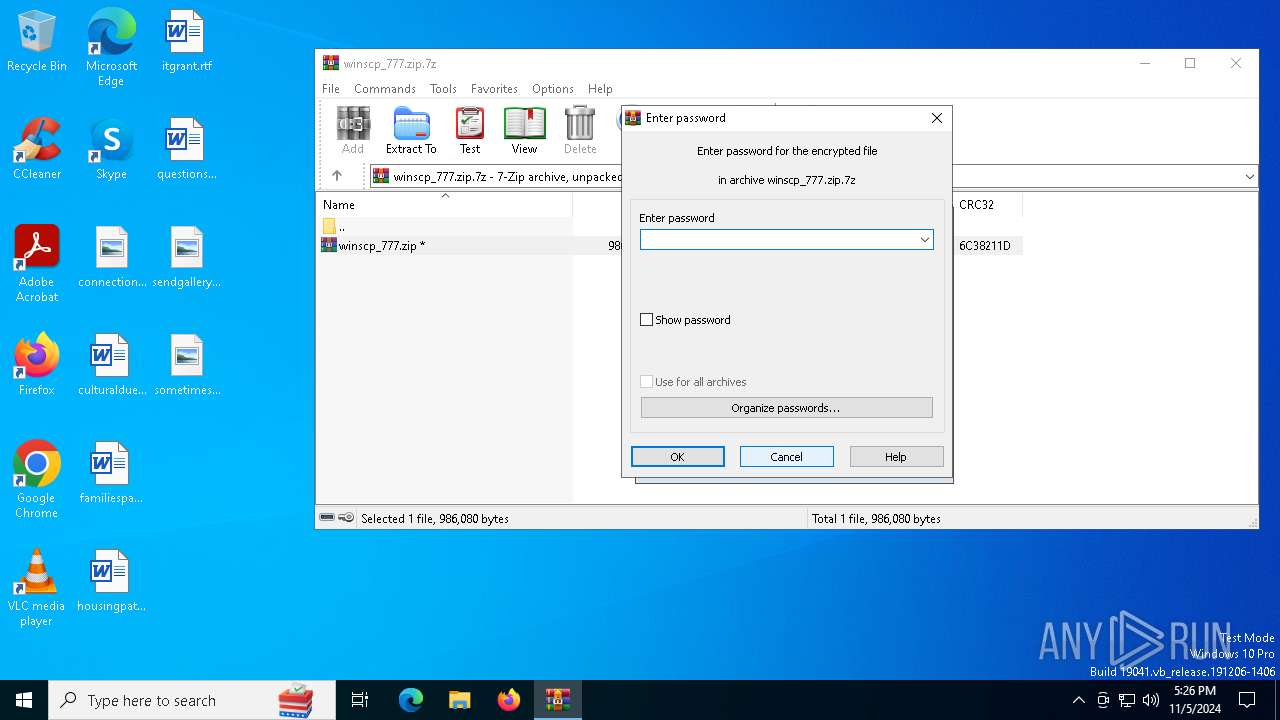
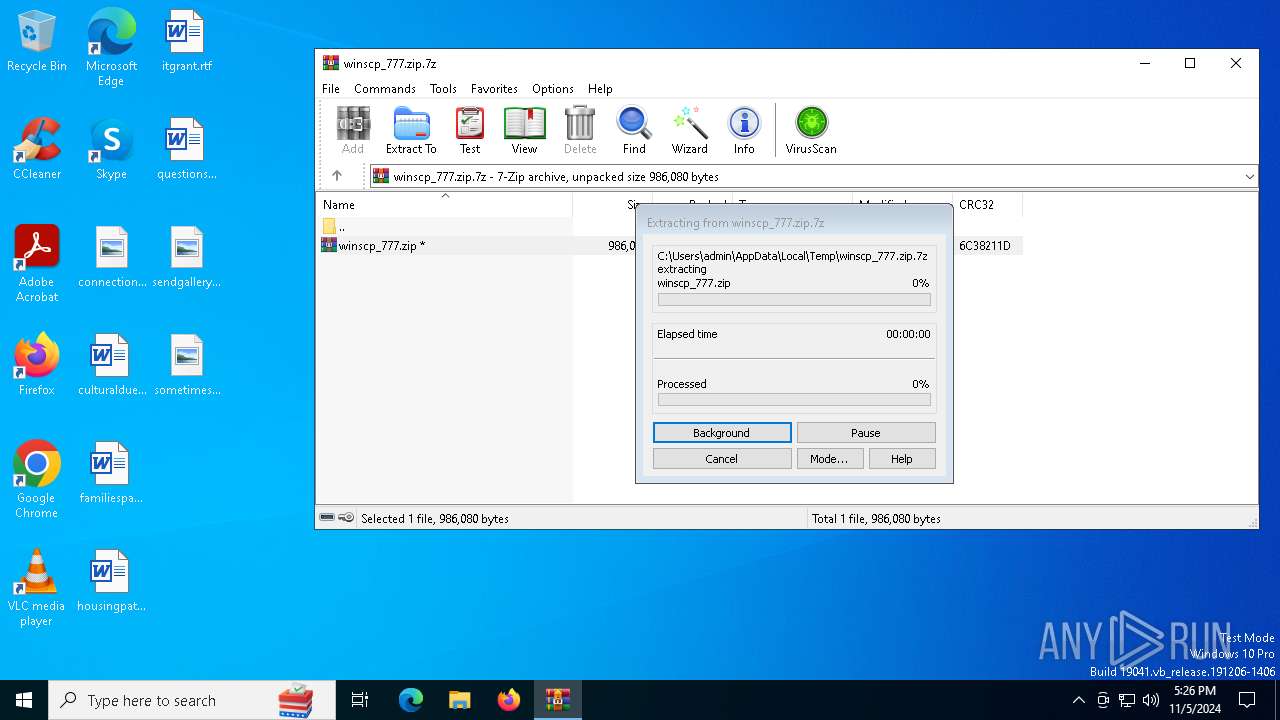
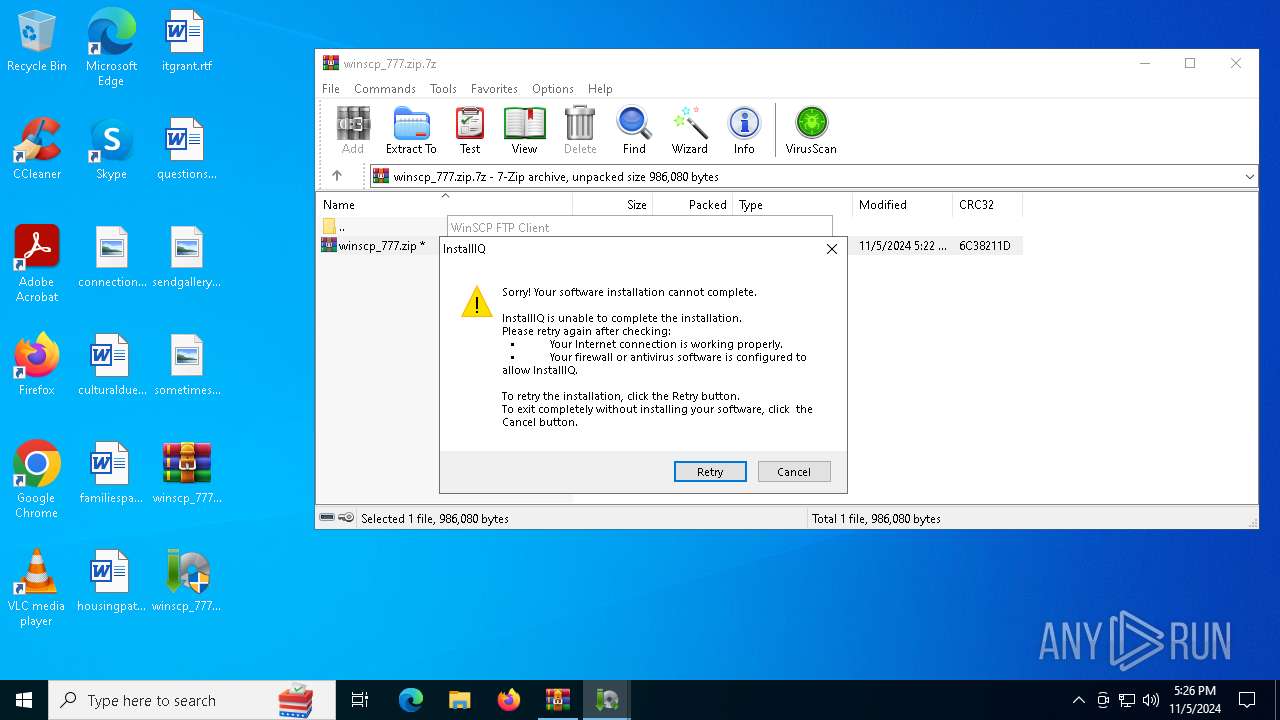
| File name: | winscp_777.zip.7z |
| Full analysis: | https://app.any.run/tasks/a954aca4-a598-48f8-8a79-68c73e2fc48d |
| Verdict: | Malicious activity |
| Analysis date: | November 05, 2024, 17:25:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 80569555360EFDA6EA557929066F1703 |
| SHA1: | 050D724FD43C3437A4AAEBFEC6E984A73797CF30 |
| SHA256: | 36EF2E99513BF6790EB8F7CDA198DBD9FD58D992F747CB3DDDFEE8B986A595CF |
| SSDEEP: | 49152:dTjGEichdHPjoAgY7xAwdI423qxMgP/MDUxcgQKaMsiHABnjjWrjIxNvqEHx+we8:dTjG3SPgQWh423qx9pIMs+ABnPWWvqEs |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6364)
SUSPICIOUS
Application launched itself
- winscp_777.exe (PID: 3620)
- winscp_777.exe (PID: 700)
Potential Corporate Privacy Violation
- winscp_777.exe (PID: 6916)
INFO
Manual execution by a user
- WinRAR.exe (PID: 1248)
- winscp_777.exe (PID: 5264)
- winscp_777.exe (PID: 3620)
- WinRAR.exe (PID: 6660)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1248)
- WinRAR.exe (PID: 6660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:11:05 17:22:38+00:00 |
| ArchivedFileName: | winscp_777.zip |
Total processes
147
Monitored processes
12
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6660.41296\winscp_777.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6660.41296\winscp_777.exe | WinRAR.exe | ||||||||||||
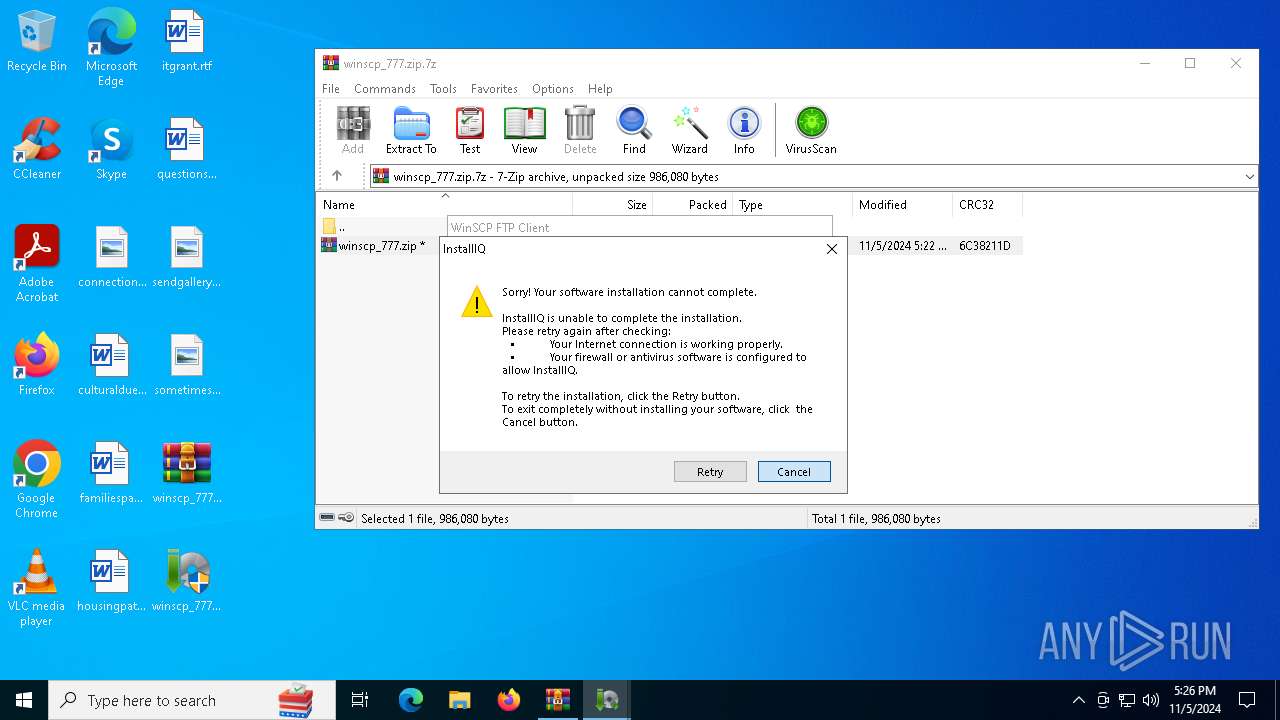
User: admin Company: W3i, LLC Integrity Level: HIGH Description: InstallIQ Installation Utility Version: 2.105.0.0 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\winscp_777.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\Desktop\winscp_777.exe" | C:\Users\admin\Desktop\winscp_777.exe | explorer.exe | ||||||||||||
User: admin Company: W3i, LLC Integrity Level: HIGH Description: InstallIQ Installation Utility Version: 2.105.0.0 Modules
| |||||||||||||||
| 4448 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6660.41296\winscp_777.exe" /wrapper /dir="C:\Users\admin\AppData\Local\Temp\pkg_111a2cf60" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6660.41296\winscp_777.exe | — | winscp_777.exe | |||||||||||
User: admin Company: W3i, LLC Integrity Level: HIGH Description: InstallIQ Installation Utility Version: 2.105.0.0 Modules
| |||||||||||||||
| 4676 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6660.41296\winscp_777.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6660.41296\winscp_777.exe | — | WinRAR.exe | |||||||||||
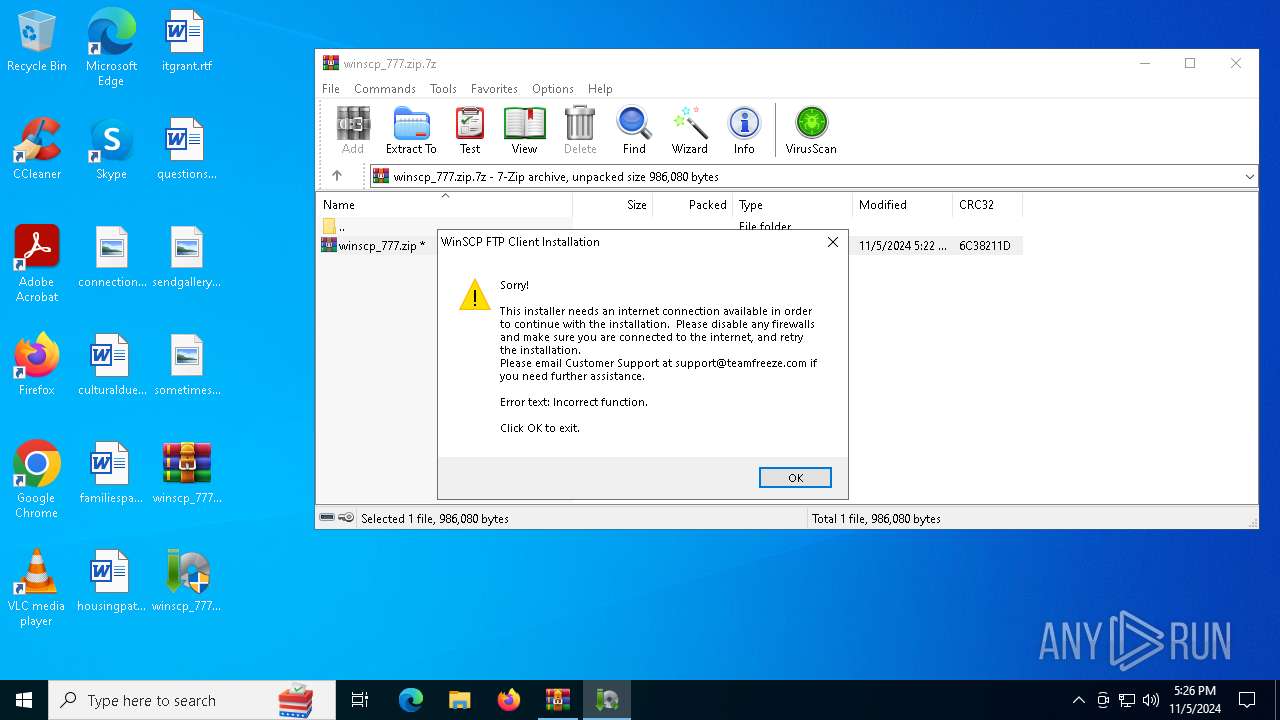
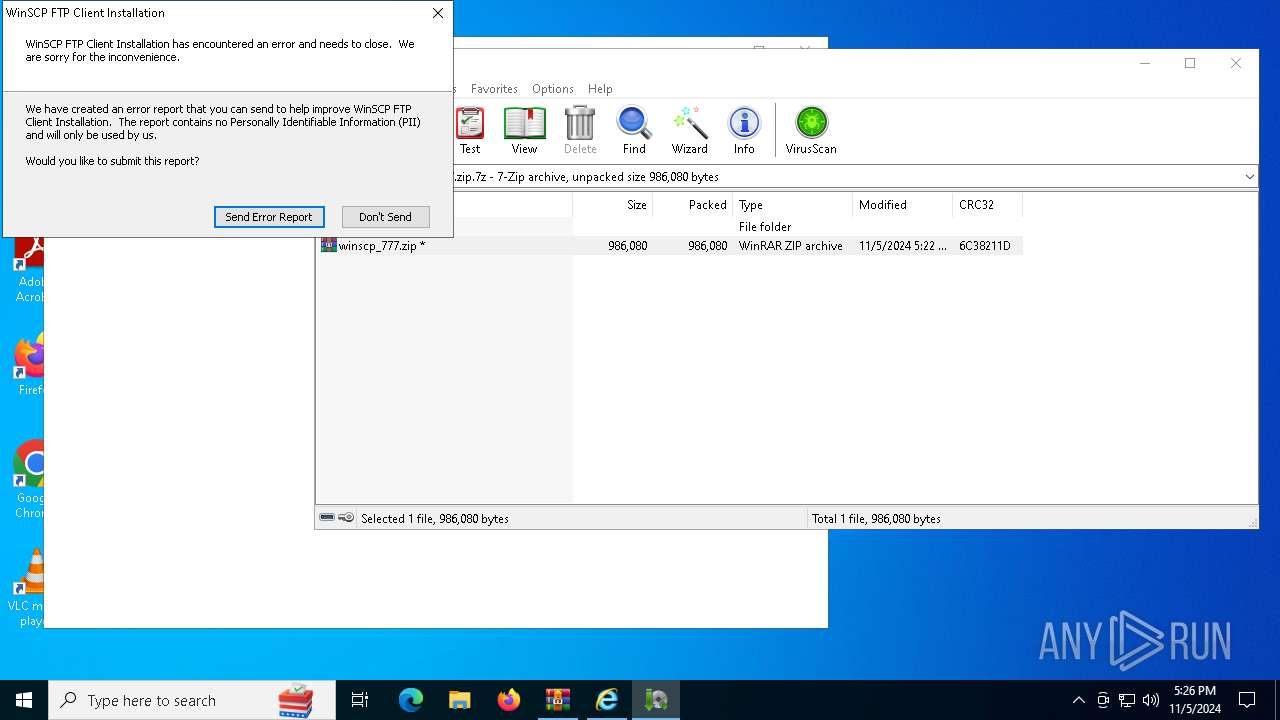
User: admin Company: W3i, LLC Integrity Level: MEDIUM Description: InstallIQ Installation Utility Exit code: 3221226540 Version: 2.105.0.0 Modules
| |||||||||||||||
| 5264 | "C:\Users\admin\Desktop\winscp_777.exe" | C:\Users\admin\Desktop\winscp_777.exe | — | explorer.exe | |||||||||||
User: admin Company: W3i, LLC Integrity Level: MEDIUM Description: InstallIQ Installation Utility Exit code: 3221226540 Version: 2.105.0.0 Modules
| |||||||||||||||
| 6332 | "C:\Program Files\Internet Explorer\IEXPLORE.EXE" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6364 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\winscp_777.zip.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6660 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\winscp_777.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6680 | "C:\Program Files (x86)\Internet Explorer\ielowutil.exe" -CLSID:{0002DF01-0000-0000-C000-000000000046} -Embedding | C:\Program Files (x86)\Internet Explorer\ielowutil.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Low-Mic Utility Tool Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 938
Read events
7 839
Write events
67
Delete events
32
Modification events
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\winscp_777.zip.7z | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (6364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
3
Suspicious files
11
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3620 | winscp_777.exe | C:\Users\admin\AppData\Local\Temp\pkg_111a1a2fa0\wrapper.xml | text | |
MD5:7DF4B6DB3FBBD712D68509779B2ED8FB | SHA256:357DA15A7E543CF183942D2E0E125D8814DD2BDB225AC5FE7D1FAE0601B4473B | |||
| 1248 | WinRAR.exe | C:\Users\admin\Desktop\winscp_777.exe | executable | |
MD5:14917E98FAD49B52419271A2F00958D8 | SHA256:268E54968B35D028C28FD0B3349A49887CC37CDF033B0E1831521CBF74B69A59 | |||
| 6364 | WinRAR.exe | C:\Users\admin\Desktop\winscp_777.zip | compressed | |
MD5:393F51503F849531B85B02A8E920D1B2 | SHA256:CA4F7A3D99A0A1805B01234F44848840ADAF90C33DB28E3673FEFCA632DAFBCC | |||
| 6364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\winscp_777.zip\winscp_777.zip | compressed | |
MD5:393F51503F849531B85B02A8E920D1B2 | SHA256:CA4F7A3D99A0A1805B01234F44848840ADAF90C33DB28E3673FEFCA632DAFBCC | |||
| 6916 | winscp_777.exe | C:\Users\admin\AppData\Local\Temp\pkg_111a1a2fa0\detectionrules.dat | html | |
MD5:76A01A9BBF428AC976967805476583E0 | SHA256:2D49F0F0CD2C767153AA5DE42728E0F5B51796B78650B6D2283EF9CCC1F93B02 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6660.41296\winscp_777.exe | executable | |
MD5:14917E98FAD49B52419271A2F00958D8 | SHA256:268E54968B35D028C28FD0B3349A49887CC37CDF033B0E1831521CBF74B69A59 | |||
| 3620 | winscp_777.exe | C:\Users\admin\AppData\Local\Temp\pkg_111a1a2fa0\stub.log | text | |
MD5:F789C6444B87207B0198F7D0F05BFDF3 | SHA256:08AAB9CEA231F932F34151450AA7EEB152482BE76FECCD0CE85AF65F5BA8C99B | |||
| 3620 | winscp_777.exe | C:\Users\admin\AppData\Local\Temp\pkg_111a1a2fa0\autorun.txt | ini | |
MD5:021A3564273D893F018F4A0772D010EB | SHA256:221296ADB0916E5021BADF2753C90134CE8A68F3A0C45A94C9DD937CB9E6E7D2 | |||
| 3620 | winscp_777.exe | C:\Users\admin\AppData\Local\Temp\pkg_111a1a2fa0\timings.txt | text | |
MD5:98D975E000DF976711F3485697B6933B | SHA256:5BCE77B1515424F93176AE7198B437E0F0231D3E6A3AF6C12EEEEBB0105E95F3 | |||
| 7080 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:C0EF978F645BBBD2D756CDBD7B33F8F1 | SHA256:7900093A0B4CAD3B1837C7D3F485D6AA8DA596447BACA8397AC6A140B59924AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
58
DNS requests
33
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4904 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7080 | iexplore.exe | GET | 200 | 199.59.243.227:80 | http://survey-smiles.com/ | unknown | — | — | whitelisted |
7080 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSzT%2FzqwcqNvhP9i4c4sCPz2JbzrAQU%2FglxQFUFEETYpIF1uJ4a6UoGiMgCEzMA8nzFbypE4tpMp9EAAADyfMU%3D | unknown | — | — | whitelisted |
7080 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6332 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6332 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4904 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.43:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7036 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4904 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
6944 | svchost.exe | 2.16.164.43:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.160:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6916 | winscp_777.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |
6916 | winscp_777.exe | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |
— | — | Potential Corporate Privacy Violation | ET POLICY InstallIQ Updater Software request |