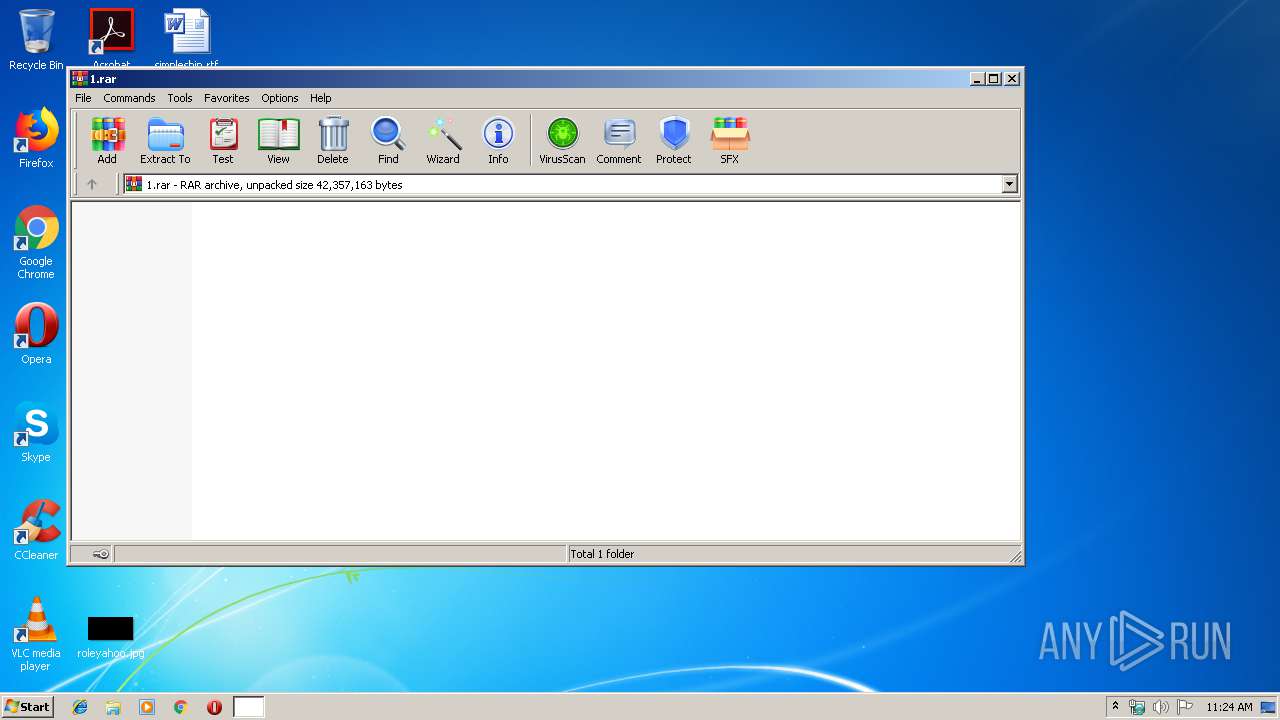
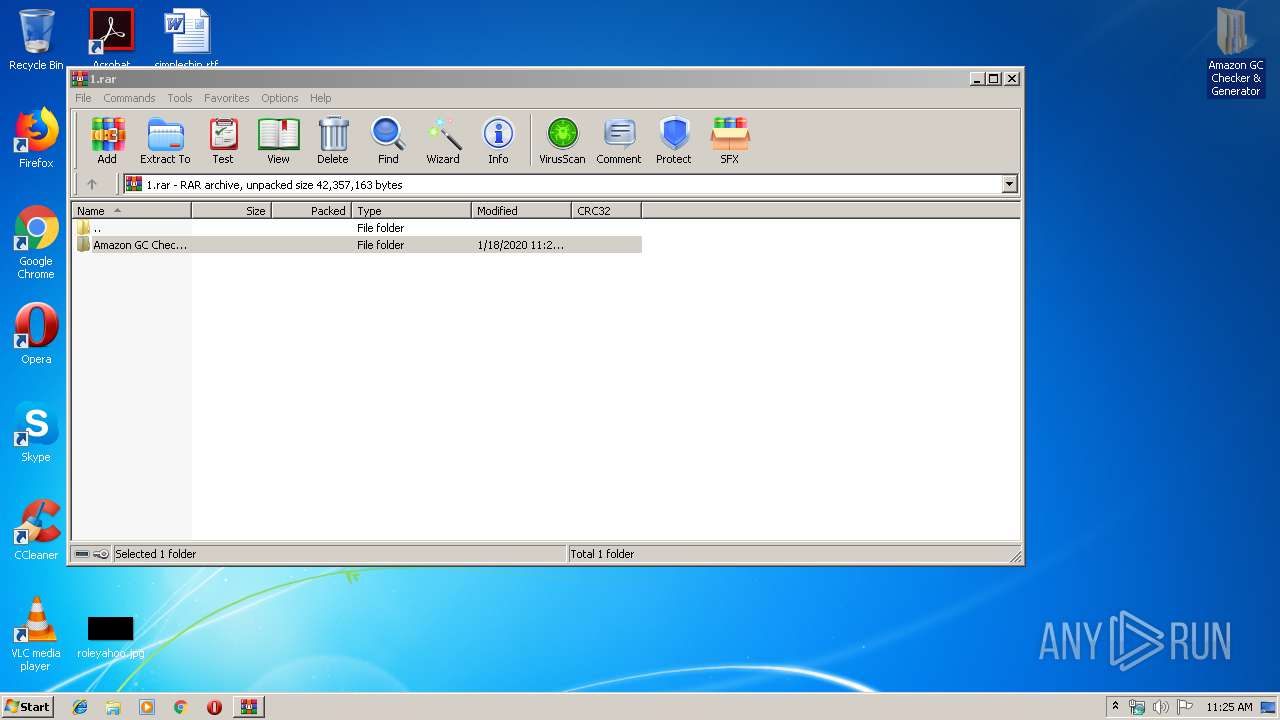
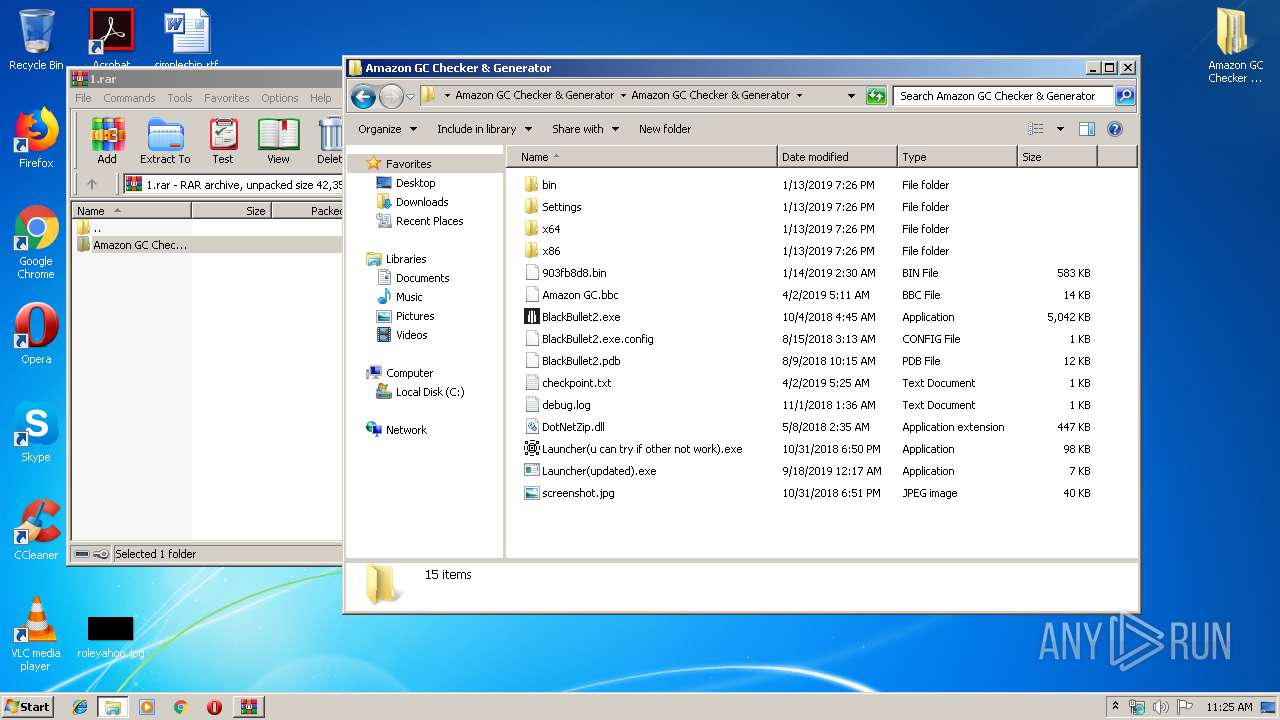
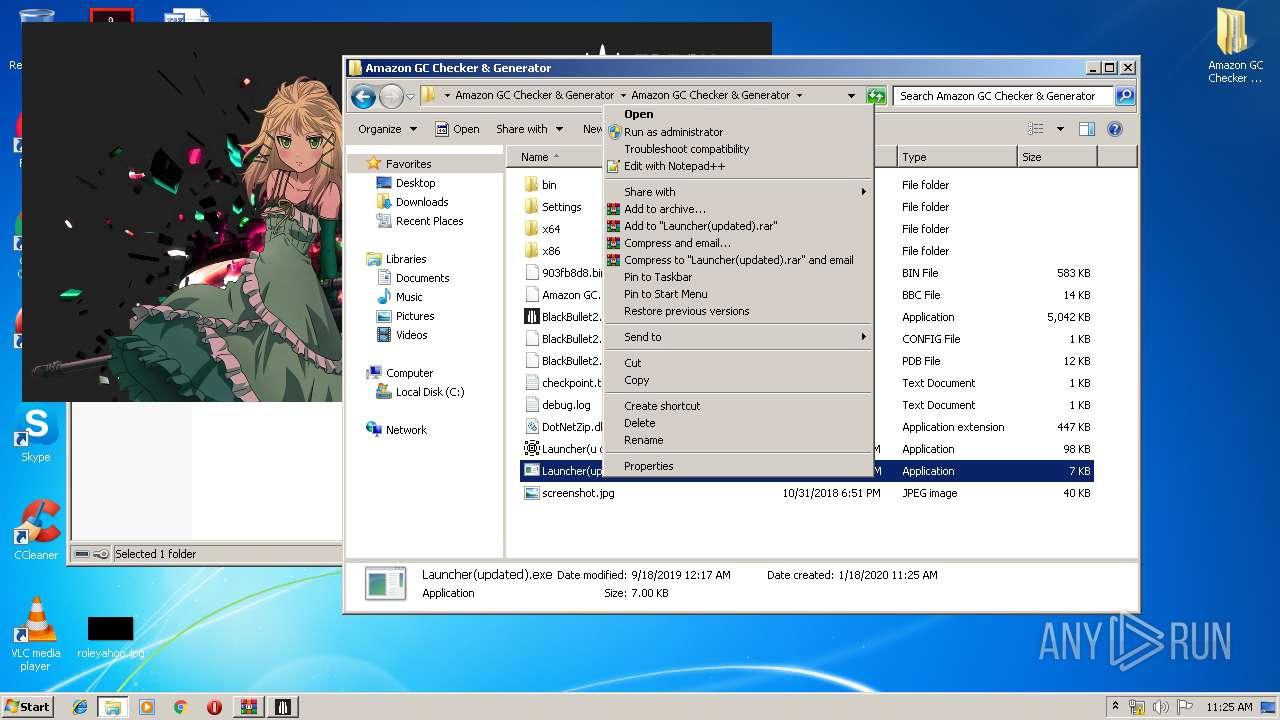
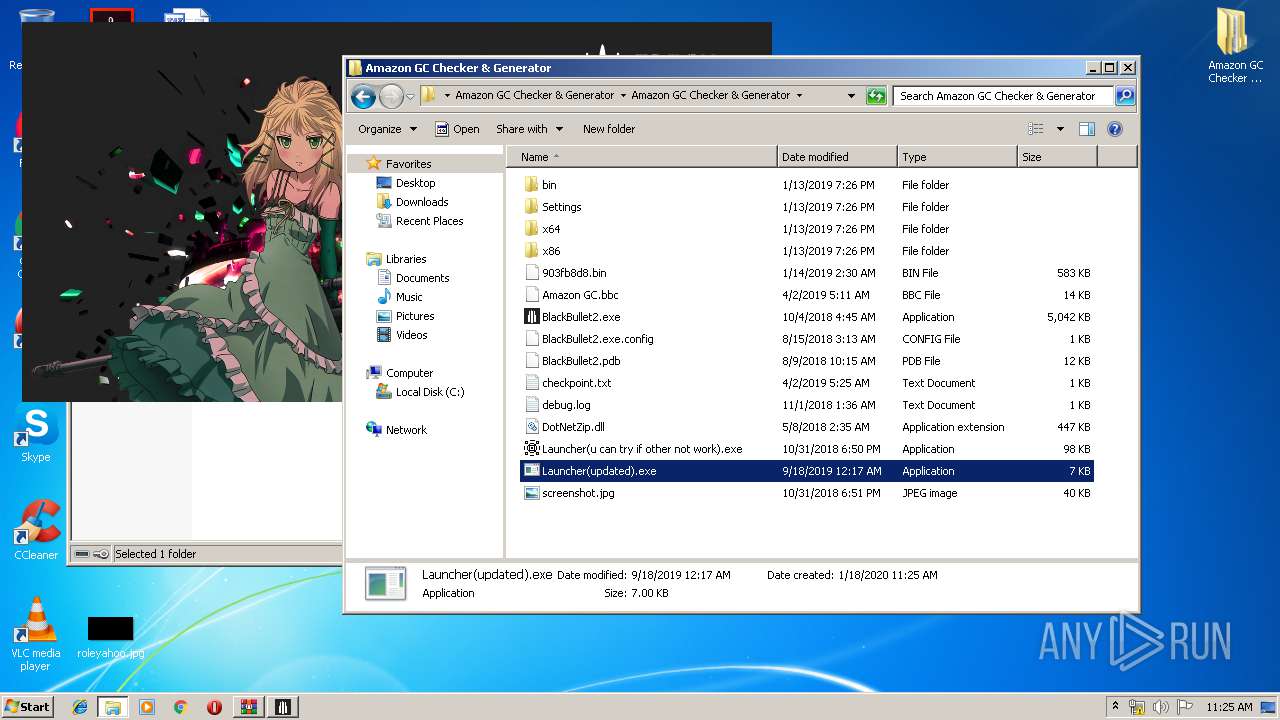
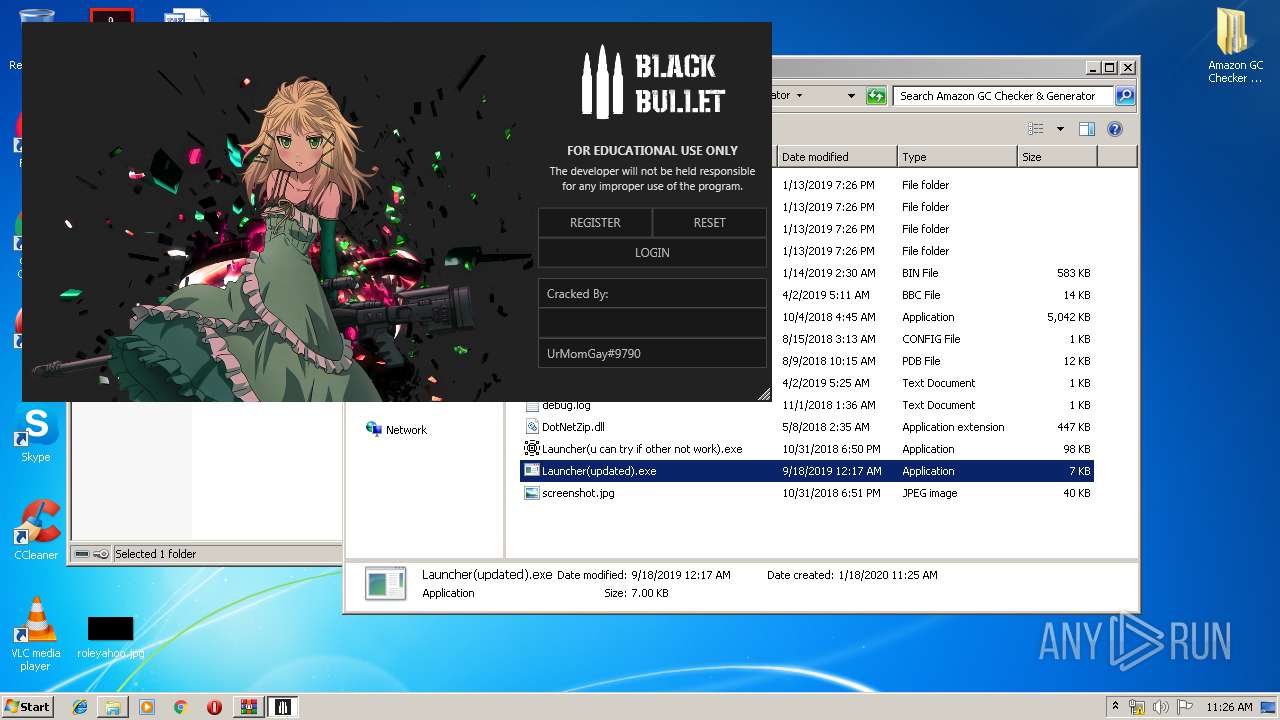
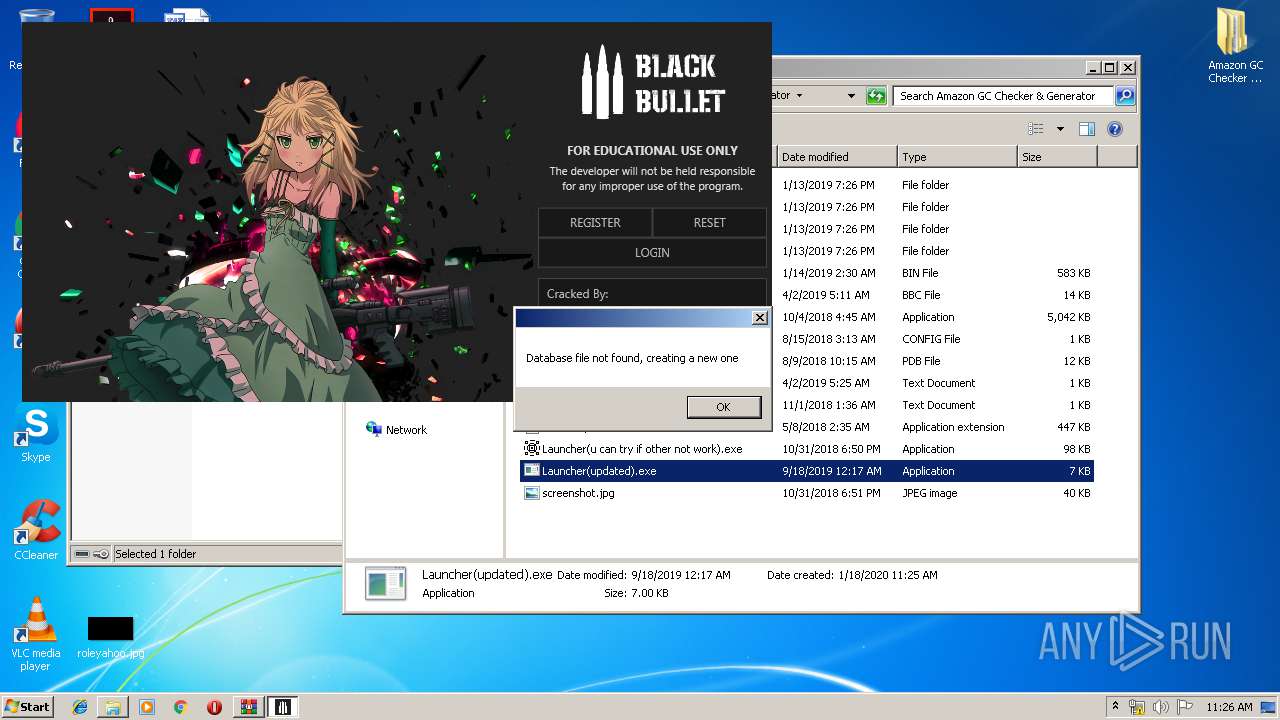
| File name: | 1.rar |
| Full analysis: | https://app.any.run/tasks/34418fc8-8c5b-43e9-a1e3-377c5b262cb0 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2020, 11:24:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 30EDD123DC12367712A5C4EE6CA68635 |
| SHA1: | 75543031C63C5CD1145AD429056726E8E3528C97 |
| SHA256: | 36E345A37B718088538C4C4A84FFF940DBB7A0B94F243D60072666D88356E9F9 |
| SSDEEP: | 393216:lLKjgS3HY3hlZxncawyHXQA9aFYZrW5sjfviS:Jq7XY3rXcqXQA9EOjniS |
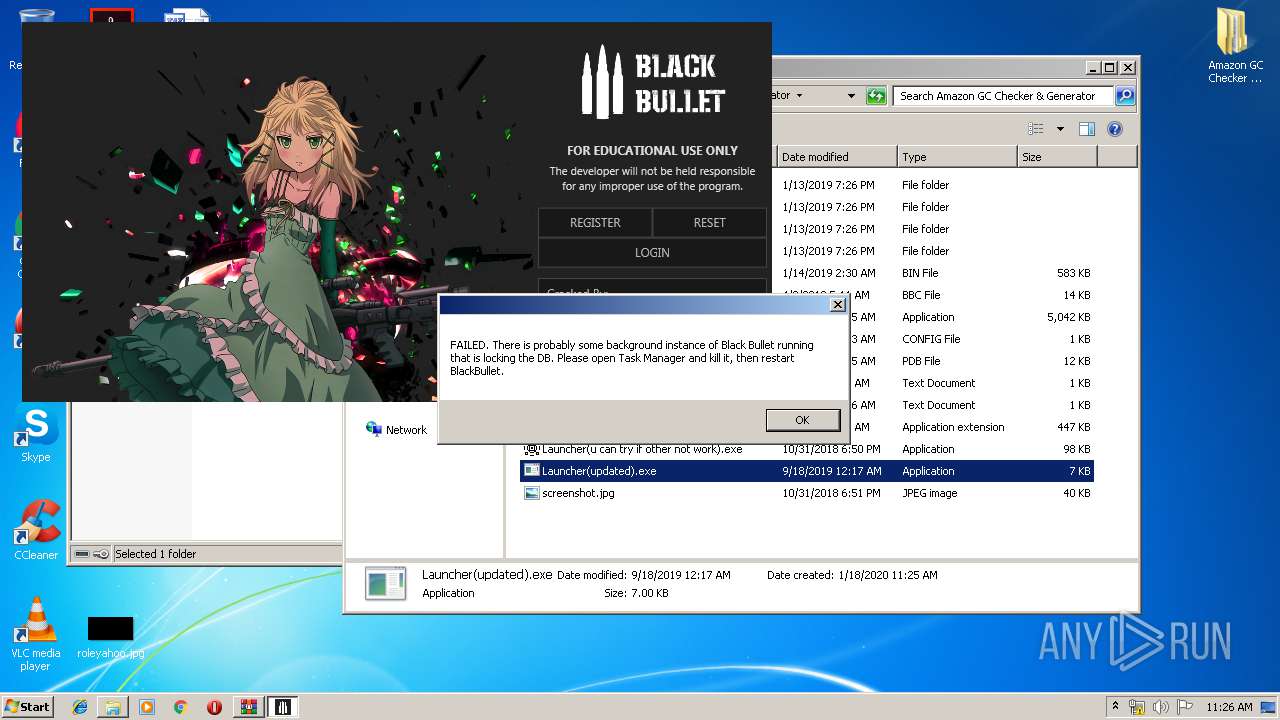
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3544)
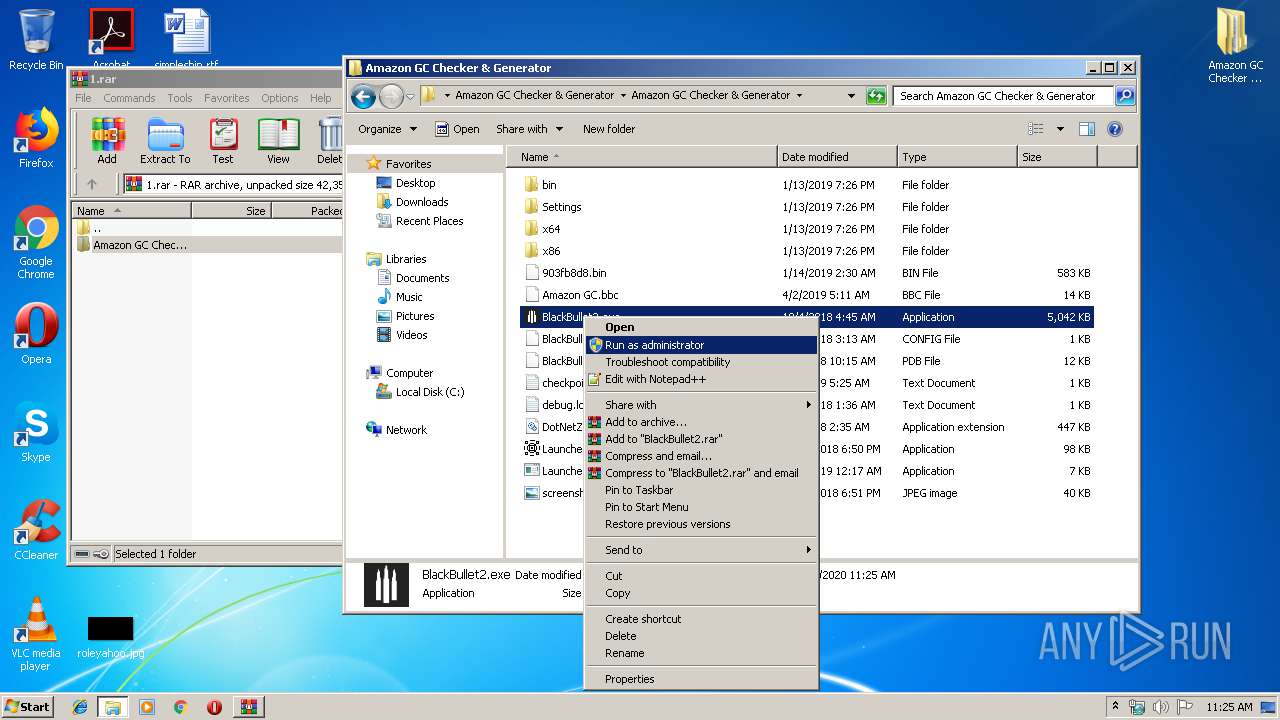
- BlackBullet2.exe (PID: 1096)
- BlackBullet2.exe (PID: 3652)
SUSPICIOUS
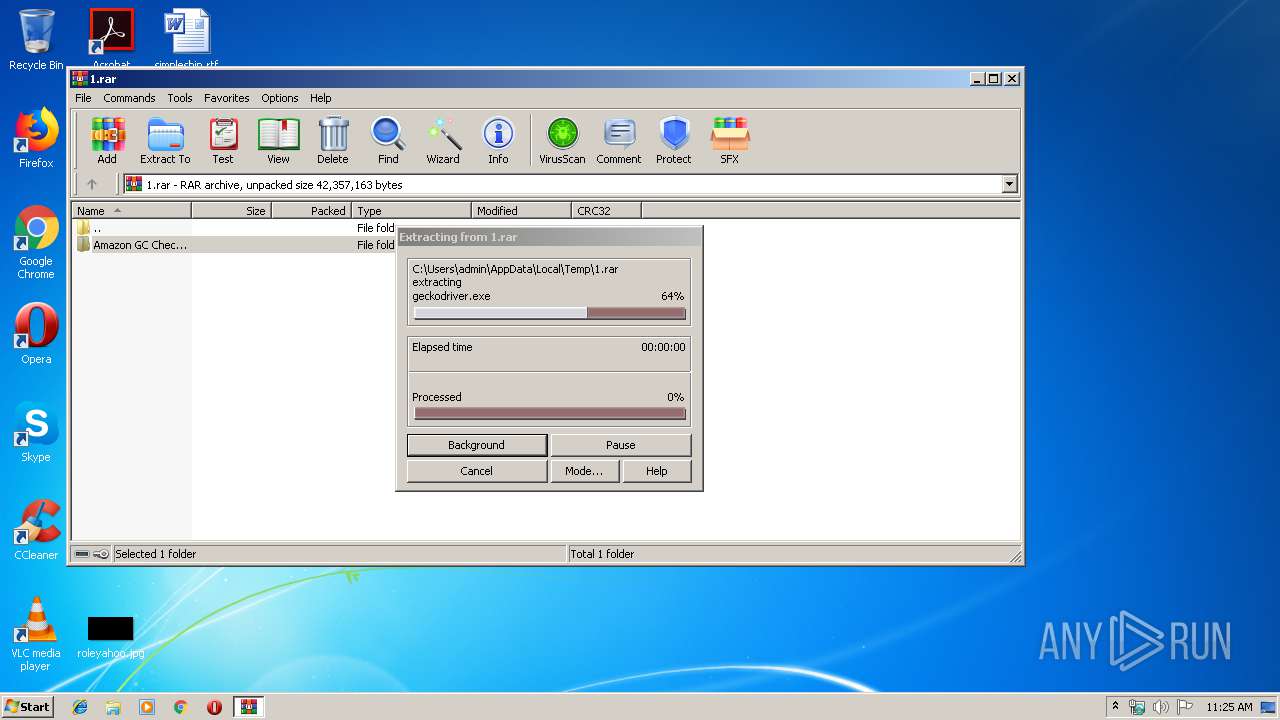
Executable content was dropped or overwritten
- WinRAR.exe (PID: 996)
Starts CMD.EXE for commands execution
- Launcher(u can try if other not work).exe (PID: 2444)
Starts Internet Explorer
- cmd.exe (PID: 1292)
INFO
Manual execution by user
- BlackBullet2.exe (PID: 1096)
- Launcher(u can try if other not work).exe (PID: 2444)
- Launcher(updated).exe (PID: 3772)
- Launcher(updated).exe (PID: 3096)
- Launcher(updated).exe (PID: 3292)
Changes internet zones settings
- iexplore.exe (PID: 4040)
Creates files in the user directory
- iexplore.exe (PID: 2136)
Changes settings of System certificates
- iexplore.exe (PID: 2136)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2136)
Reads internet explorer settings
- iexplore.exe (PID: 2136)
Reads Internet Cache Settings
- iexplore.exe (PID: 2136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
58
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 996 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
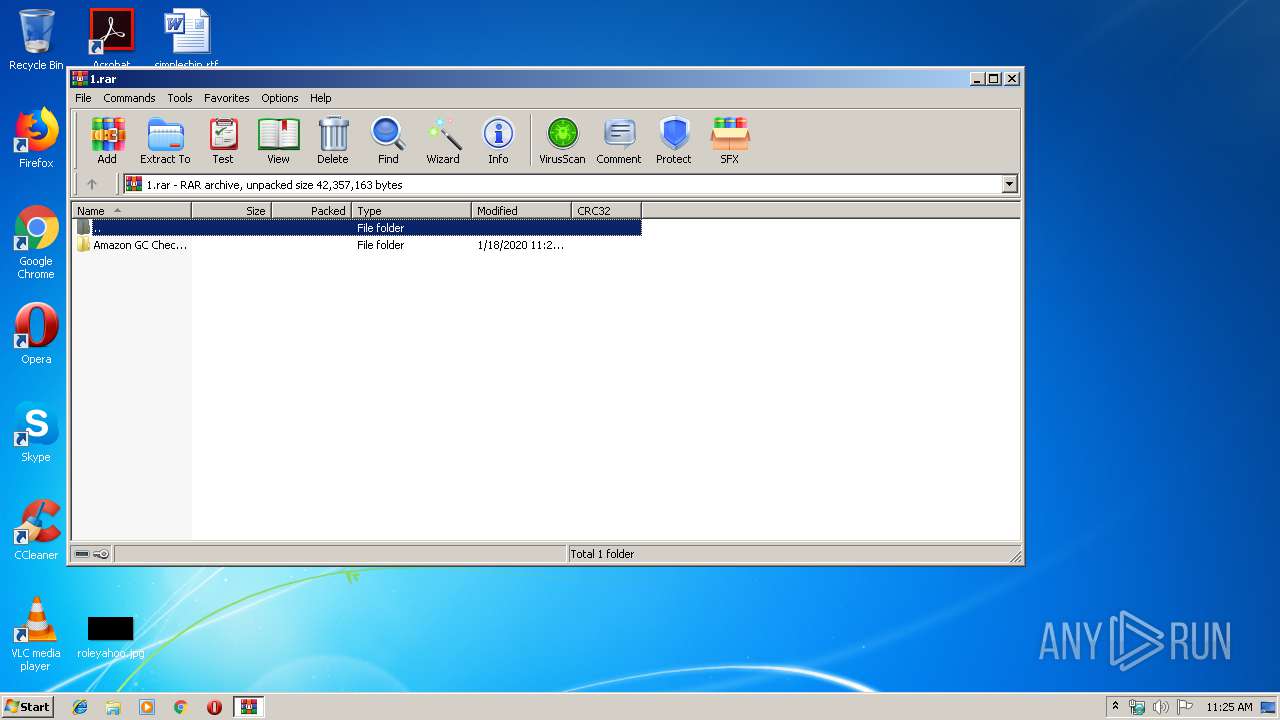
| 1096 | "C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\BlackBullet2.exe" | C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\BlackBullet2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: BlackBullet2 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1292 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\7EF9.tmp\7EFA.tmp\7EFB.bat "C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(u can try if other not work).exe"" | C:\Windows\system32\cmd.exe | — | Launcher(u can try if other not work).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4040 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(u can try if other not work).exe" | C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(u can try if other not work).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3096 | "C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(updated).exe" | C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(updated).exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID Hardware Monitor Integrity Level: MEDIUM Description: CPUID Hardware Monitor Exit code: 0 Version: 1.3.4.0 Modules
| |||||||||||||||
| 3292 | "C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(updated).exe" | C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(updated).exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID Hardware Monitor Integrity Level: MEDIUM Description: CPUID Hardware Monitor Exit code: 0 Version: 1.3.4.0 Modules
| |||||||||||||||
| 3544 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3652 | BlackBullet2.exe FL | C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\BlackBullet2.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: BlackBullet2 Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3772 | "C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(updated).exe" | C:\Users\admin\Desktop\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Launcher(updated).exe | explorer.exe | ||||||||||||
User: admin Company: CPUID Hardware Monitor Integrity Level: HIGH Description: CPUID Hardware Monitor Exit code: 0 Version: 1.3.4.0 Modules
| |||||||||||||||
Total events
1 219
Read events
1 134
Write events
83
Delete events
2
Modification events
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1.rar | |||
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3544) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3544) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msxml3r.dll,-1 |
Value: XML Document | |||
Executable files
32
Suspicious files
2
Text files
110
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\Amazon GC.bbc | text | |
MD5:— | SHA256:— | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\903fb8d8.bin | html | |
MD5:— | SHA256:— | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\AntiCaptchaLibrary.pdb | pdb | |
MD5:D40FCC3B05BD2890790DFAB3D7EB857F | SHA256:A72658B2C43BE5FA61F771149155704C4FC550BE24F9AB1148AB0B0CA45747DF | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\DeathByCaptcha.dll | executable | |
MD5:3495203999B4A2C1A91A6C2E7903E0DB | SHA256:FDD3C336E835F01FA052CF23C1B5A8070D510FFA3C8EE12187C1EA46A08287D1 | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\AngleSharp.dll | executable | |
MD5:EC22828DA8A4053F8B4B23FCB5B3FDE0 | SHA256:7BBF3C452CAAF914CCC56A45E6C3BDB21B4B5BF8A4C2C2633A6EC46C97EA885F | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\DeathByCaptcha.pdb | pdb | |
MD5:1C127B5964FE54CA87E72D4E0F27DDBB | SHA256:B880BF64DCB57E490BB05B13F8CC3C0059C80987EE8B8C9D2E113293669309CF | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\chromedriver.exe | executable | |
MD5:2FBE8348A03B7440EB5B025ABAE7F7D1 | SHA256:C68BB9B97E36B5DAAB3D100F427A7977A535D9B4EA20890FBB755F39D0421E94 | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\AntiCaptchaLibrary.dll | executable | |
MD5:7F1F5E8F97C0E8D6A6C110D7E992D3E7 | SHA256:1A3EF40CFCE664828534E83188B1054F4E8A3BEFDFBE9391E402B4C96181C784 | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\DeCaptcherLibrary.dll | executable | |
MD5:DF02DB790400B829B51F831E5ED451B4 | SHA256:E0F83DAC5ADE8FC434A69DFFE75E90267749EFEEFFDEE80033BBA6BABF03D2E3 | |||
| 996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa996.23199\Amazon GC Checker & Generator\Amazon GC Checker & Generator\bin\DeCaptcherLibrary.pdb | pdb | |
MD5:3504A330E2782EF3E549B438946578BF | SHA256:408C07A85B04949CE0900E4545EE9790D93BF1EFDAA51DE7EBAA37BD03BDB62A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
30
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2136 | iexplore.exe | GET | 301 | 104.27.160.126:80 | http://crackingcentral.com/ | US | — | — | malicious |
4040 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4040 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2136 | iexplore.exe | 172.217.18.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2136 | iexplore.exe | 104.17.64.4:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
2136 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
2136 | iexplore.exe | 151.101.2.109:443 | cdn.jsdelivr.net | Fastly | US | suspicious |
2136 | iexplore.exe | 172.217.22.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2136 | iexplore.exe | 172.217.22.2:443 | www.googleadservices.com | Google Inc. | US | whitelisted |
2136 | iexplore.exe | 216.58.208.46:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2136 | iexplore.exe | 173.194.76.156:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
2136 | iexplore.exe | 172.217.23.100:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crackingcentral.com |
| malicious |
www.bing.com |
| whitelisted |
cracked.to |
| whitelisted |
static.cracked.to |
| suspicious |
fonts.googleapis.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |