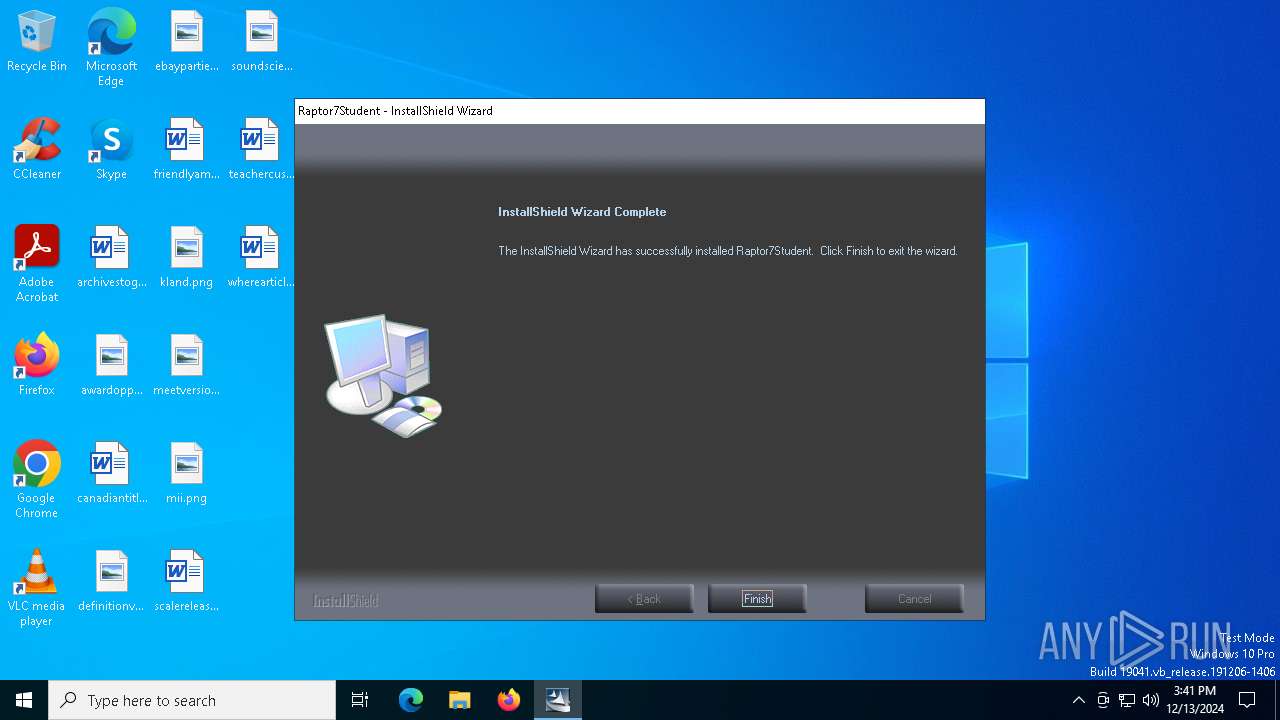
| File name: | Raptor7StudentSetup.exe |
| Full analysis: | https://app.any.run/tasks/972a0fa8-9b8e-4737-bf2d-3e3186bb424b |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 15:40:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 18D775D15AA7CF705CD4B6133EAD65B5 |
| SHA1: | 96DA4C9D30C8AF64D0B9CC6E94E6A1093869103C |
| SHA256: | 36D8E1861DBD3CB74E5431BAE28BB35F15C8E69B606F8942B485AD9BF19079F0 |
| SSDEEP: | 98304:RPhCJdBBbfHPhi2VVSOqXg/jmCjAHBSOauNR0zQ9M9qxzBgsprOyHEYCLf3ZK6mT:/gFYjQ4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Raptor7StudentSetup.exe (PID: 6820)
Application launched itself
- Raptor7StudentSetup.exe (PID: 6796)
Creates a software uninstall entry
- Raptor7StudentSetup.exe (PID: 6820)
Executes as Windows Service
- VSSVC.exe (PID: 6012)
Creates/Modifies COM task schedule object
- Raptor7StudentSetup.exe (PID: 6820)
INFO
The sample compiled with english language support
- Raptor7StudentSetup.exe (PID: 6796)
- Raptor7StudentSetup.exe (PID: 6820)
Checks supported languages
- Raptor7StudentSetup.exe (PID: 6796)
- Raptor7StudentSetup.exe (PID: 6820)
- Raptor7Student.exe (PID: 880)
Reads the computer name
- Raptor7StudentSetup.exe (PID: 6820)
- Raptor7Student.exe (PID: 880)
Create files in a temporary directory
- Raptor7StudentSetup.exe (PID: 6820)
Reads the machine GUID from the registry
- Raptor7StudentSetup.exe (PID: 6820)
Creates files in the program directory
- Raptor7StudentSetup.exe (PID: 6820)
Manages system restore points
- SrTasks.exe (PID: 1916)
Manual execution by a user
- Raptor7Student.exe (PID: 880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (33) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (23.9) |
| .exe | | | Win64 Executable (generic) (21.2) |
| .scr | | | Windows screen saver (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2003:11:10 23:16:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 67072 |
| InitializedDataSize: | 44544 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcc61 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.1.0.429 |
| ProductVersionNumber: | 9.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | InstallShield Software Corporation |
| FileDescription: | Setup.exe |
| FileVersion: | 9.01.429 |
| InternalName: | Setup |
| OriginalFileName: | Setup.exe |
| LegalCopyright: | Copyright (C) 2003 InstallShield Software Corp. |
| ProductName: | InstallShield (R) |
| ProductVersion: | 9.01 |
| OLESelfRegister: | - |
Total processes
142
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | "C:\Program Files (x86)\Raptor7Student\Raptor7Student.exe" | C:\Program Files (x86)\Raptor7Student\Raptor7Student.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1916 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2940 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6012 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6712 | "C:\Users\admin\AppData\Local\Temp\Raptor7StudentSetup.exe" | C:\Users\admin\AppData\Local\Temp\Raptor7StudentSetup.exe | — | explorer.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: MEDIUM Description: Setup.exe Exit code: 3221226540 Version: 9.01.429 Modules
| |||||||||||||||
| 6796 | "C:\Users\admin\AppData\Local\Temp\Raptor7StudentSetup.exe" | C:\Users\admin\AppData\Local\Temp\Raptor7StudentSetup.exe | explorer.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 9.01.429 Modules
| |||||||||||||||
| 6820 | -deleter | C:\Users\admin\AppData\Local\Temp\Raptor7StudentSetup.exe | Raptor7StudentSetup.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 9.01.429 Modules
| |||||||||||||||
Total events
2 747
Read events
2 255
Write events
474
Delete events
18
Modification events
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{AA7E2068-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{AA7E2068-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{AA7E2066-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{AA7E2066-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{CC096170-E2CB-11D2-80C8-00104B1F6CEA}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{CC096170-E2CB-11D2-80C8-00104B1F6CEA}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{8C3C1B11-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B11-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{8C3C1B13-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (6820) Raptor7StudentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B16-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
Executable files
51
Suspicious files
44
Text files
150
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\ISPackFiles.ini | text | |
MD5:AACF8E1D306F0549D91A4A7ABFF22C58 | SHA256:BFB8AE43F0E3A2E1D635ECDA919DA2F2584FF6C9E0DA153F67B6B934435DD6D7 | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\bye8001.tmp\Disk1\data1.cab | compressed | |
MD5:05AB0B0B5F3B0999DFB7DC3611BCEA8E | SHA256:C7F6D16F0BFA0B0AA45AA31DC6197ED51696BD3DD54444AAE6F7ABD1C4F9AB9C | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\bye8001.tmp\Disk1\layout.bin | binary | |
MD5:389A1A2C036B6A0BB304EF16430BF8E2 | SHA256:687E0A59783F815FA271CB82332891A6084A956DC1E6A851DA6A4DB3F1AE581A | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\bye8001.tmp\Disk1\setup.exe | executable | |
MD5:CAFB55AA463C6DF8802122838D50D2BB | SHA256:C500187AB0BAFE03622C8FC4754915ED4CD36F643E691BAF21C172C233660CC8 | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\bye8001.tmp\Disk1\Setup.bmp | binary | |
MD5:81A8E1B9D7F46B4F93FD7D2AB5564AA4 | SHA256:67A66AA65AC238A59AA7B28D22948012088D6CA57080223DC6F45DF2F878E361 | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\bye8001.tmp\Disk1\engine32.cab | compressed | |
MD5:DE89C44F15D1BFBCCA26778AF838F720 | SHA256:FE5DC5947F277B459CB55877439E74E9BB2FB891CB42B72ABC42322A51E8423D | |||
| 6820 | Raptor7StudentSetup.exe | C:\Program Files (x86)\Common Files\InstallShield\Professional\RunTime\09\01\Intel32\isp8601.tmp\temp.000 | executable | |
MD5:298C79AC2F609736788CC7CACDEEEF32 | SHA256:63671696AA87C0862E6381BC759116CD377C5331AB50AE6D05BA7CD29CF02580 | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\iss838C.tmp\setup.ini | ini | |
MD5:EFD756ED8169A36DECDFC8DAADD858C8 | SHA256:5CC1A9C470334672A3AA8236D37988586CBA943FEF55D1A8A2062F6A37302ABE | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\bye8001.tmp\Disk1\setup.ini | ini | |
MD5:EFD756ED8169A36DECDFC8DAADD858C8 | SHA256:5CC1A9C470334672A3AA8236D37988586CBA943FEF55D1A8A2062F6A37302ABE | |||
| 6820 | Raptor7StudentSetup.exe | C:\Users\admin\AppData\Local\Temp\bye8001.tmp\Disk1\setup.ibt | binary | |
MD5:4A12F8954369C34EF142D1AE412FA4A7 | SHA256:51E720521F043690479805B072837F44E6A3D3741AF6E91F180D37C757E3D539 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
47
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1412 | svchost.exe | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1412 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6768 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6452 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6768 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6452 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.17:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1412 | svchost.exe | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1412 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |