| File name: | RAD.exe |
| Full analysis: | https://app.any.run/tasks/aca8fcd9-20c7-4add-ae8f-c28372075875 |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2024, 09:11:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 4C8E78129D660A270DFAE0A950E31ED1 |
| SHA1: | 8F68FB04E4D953361C2AD85D3F94EEA812E3FE39 |
| SHA256: | 36C9D5D4F2A78752219ECC7A4F396E1723962F28DF0A46E810F02262B4689B3D |
| SSDEEP: | 12288:ap4/I4inmuB5KEufiI4tWyaNgKXoQHNUeH3tWh8/DuETn:QPEjoQtfX0h8BTn |
MALICIOUS
Drops the executable file immediately after the start
- RAD.exe (PID: 116)
SUSPICIOUS
Starts itself from another location
- RAD.exe (PID: 116)
Executable content was dropped or overwritten
- RAD.exe (PID: 116)
INFO
Checks supported languages
- Roblox Audio Downloader.exe (PID: 2072)
- RAD.exe (PID: 116)
Reads the computer name
- RAD.exe (PID: 116)
Creates files or folders in the user directory
- RAD.exe (PID: 116)
Dropped object may contain TOR URL's
- RAD.exe (PID: 116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:01:03 19:25:12+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.37 |
| CodeSize: | 374272 |
| InitializedDataSize: | 101888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5acc1 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.2.1.0 |
| ProductVersionNumber: | 0.2.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
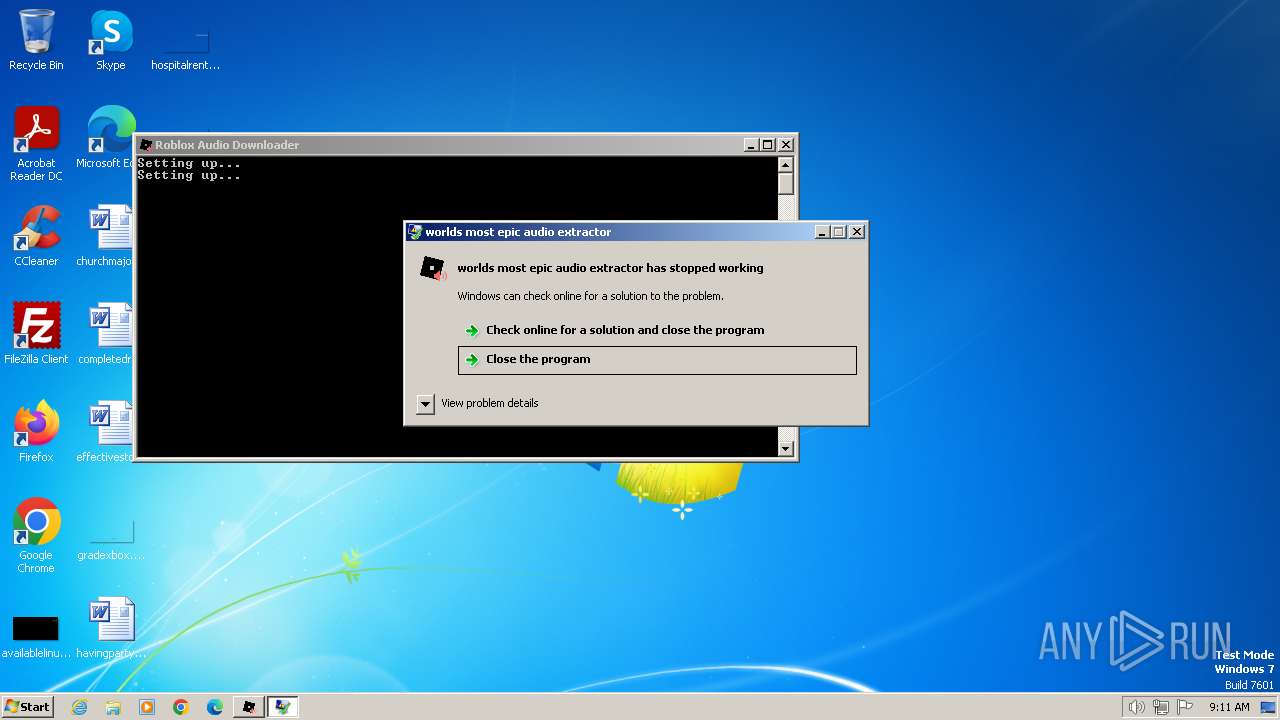
| FileDescription: | worlds most epic audio extractor |
| FileVersion: | 0.2.1.0 |
| InternalName: | RAD.exe |
| LegalCopyright: | Copyright (C) 2023 |
| OriginalFileName: | RAD.exe |
| ProductName: | Roblox Audio Downloader |
| ProductVersion: | 0.2.1.0 |
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\RAD.exe" | C:\Users\admin\AppData\Local\Temp\RAD.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: worlds most epic audio extractor Exit code: 3 Version: 0.2.1.0 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Roblox Audio Downloader\Roblox Audio Downloader.exe" | C:\Users\admin\AppData\Local\Roblox Audio Downloader\Roblox Audio Downloader.exe | RAD.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: worlds most epic audio extractor Exit code: 3 Version: 0.2.1.0 Modules
| |||||||||||||||
Total events
177
Read events
177
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | RAD.exe | C:\Users\admin\AppData\Local\Roblox Audio Downloader\rad.ico | image | |
MD5:1E037237FFE432527C686BC8239E97C4 | SHA256:08307D5C29EB0D810F7CB8AF82F6FA0A6E0A61500DA44402A3BA21A9D9DB95AE | |||
| 116 | RAD.exe | C:\Users\admin\AppData\Local\Roblox Audio Downloader\Roblox Audio Downloader.exe | executable | |
MD5:4C8E78129D660A270DFAE0A950E31ED1 | SHA256:36C9D5D4F2A78752219ECC7A4F396E1723962F28DF0A46E810F02262B4689B3D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
488 | lsass.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fa455765e490287c | unknown | compressed | 4.66 Kb | unknown |
488 | lsass.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
116 | RAD.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
488 | lsass.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
488 | lsass.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |