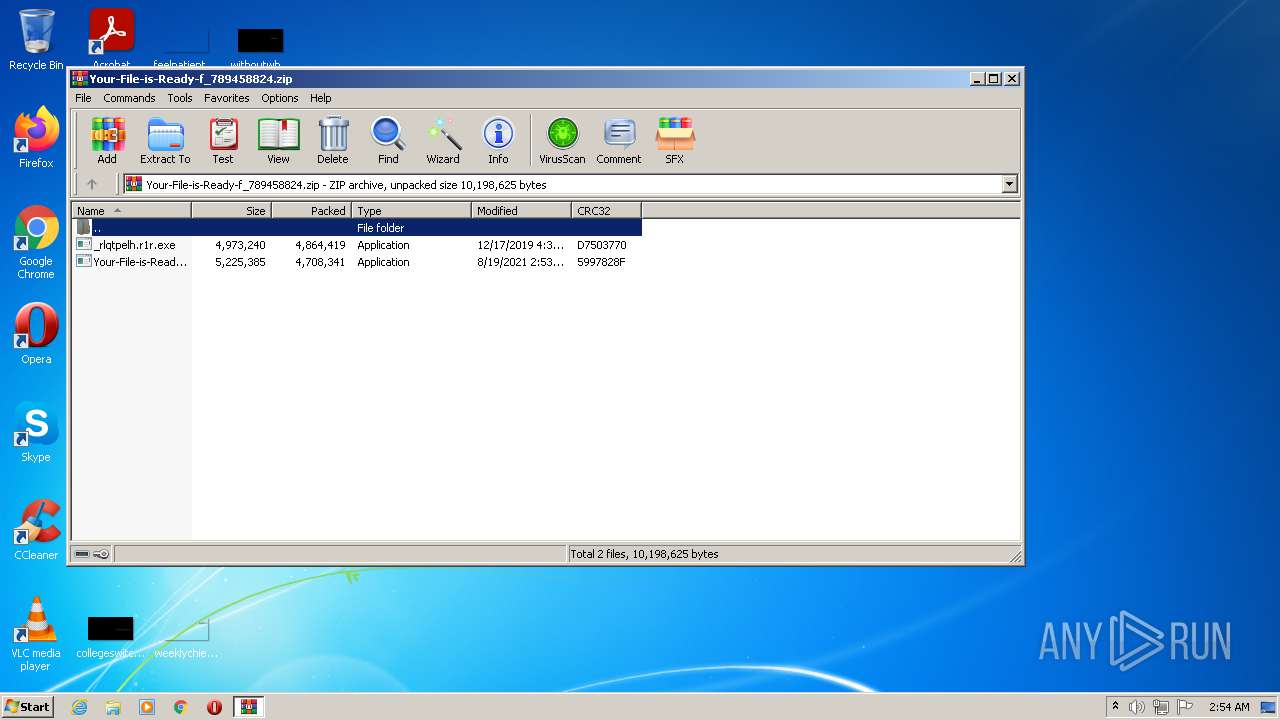
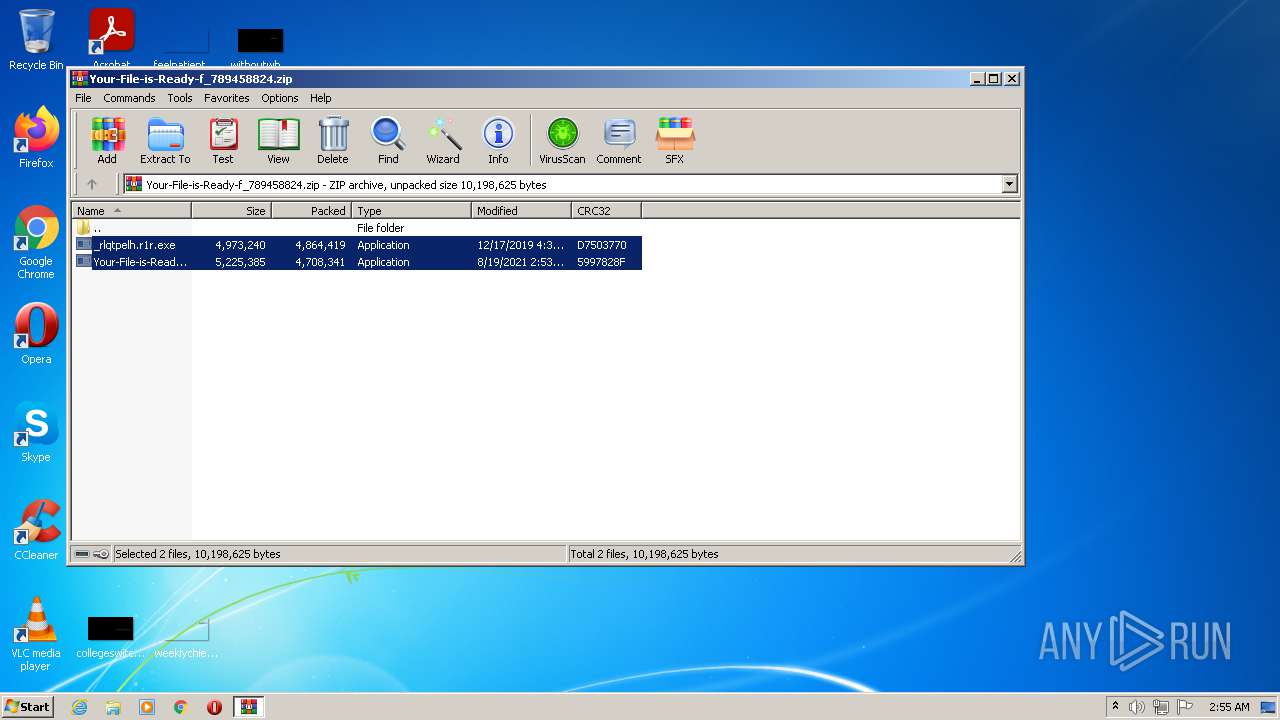
| File name: | Your-File-is-Ready-f_789458824.zip |
| Full analysis: | https://app.any.run/tasks/158cd675-5e53-463f-868e-9e5a607a549a |
| Verdict: | Malicious activity |
| Analysis date: | August 19, 2021, 01:54:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 59C7B5B14798A740BD7947A93852D5A9 |
| SHA1: | F15118D679EA36C2CF841D50B5FCE2DDE1D3852E |
| SHA256: | 36C2700AF2687239545E01E26D71F7664594F73D314E89C5860787715F62EB52 |
| SSDEEP: | 196608:k7iha/qgW4JmrqVgHUWUu1zmhASQPgj8GBLIE0YFiRnp0CaPvALGk3C:yqeWkRgHZX1zmhVQPgwG9inpMPP |
MALICIOUS
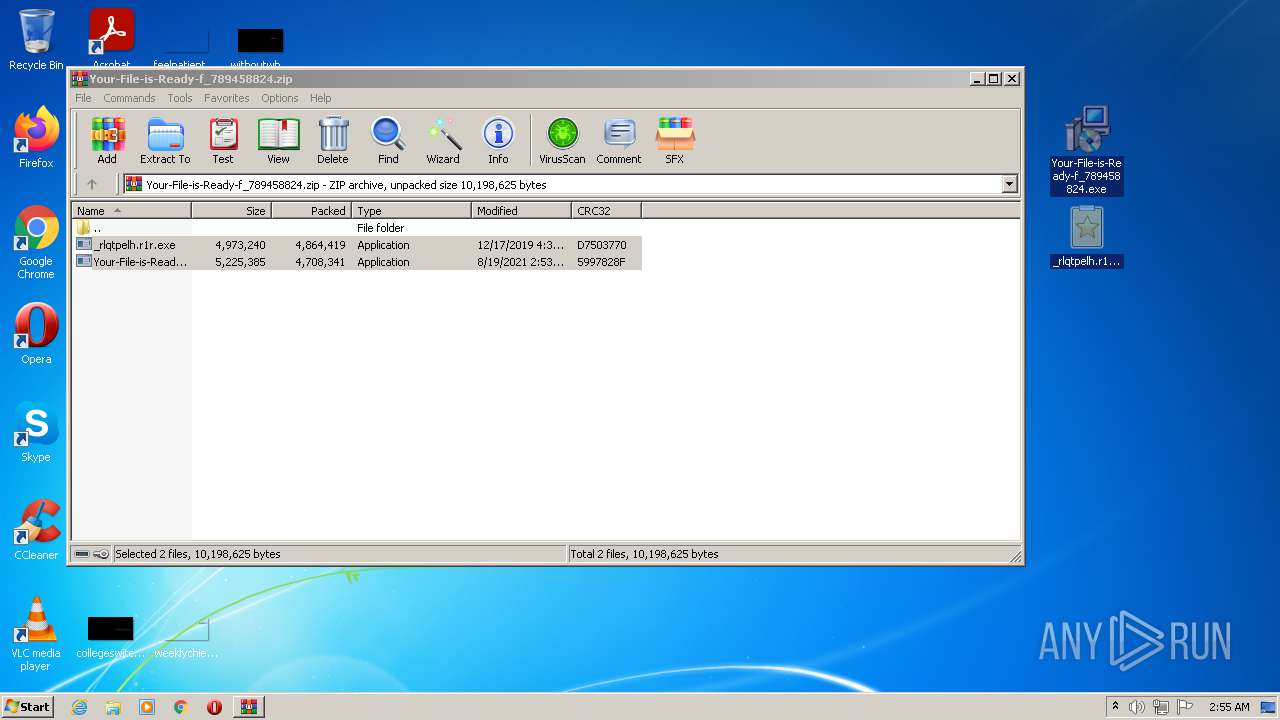
Drops executable file immediately after starts
- Explorer.EXE (PID: 1724)
- _rlqtpelh.r1r.exe (PID: 3908)
- _rlqtpelh.r1r.exe (PID: 3348)
- Your-File-is-Ready-f_789458824.exe (PID: 1956)
- Your-File-is-Ready-f_789458824.exe (PID: 3340)
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
- _rlqtpelh.r1r.exe (PID: 3704)
- _rlqtpelh.r1r.exe (PID: 3520)
Application was dropped or rewritten from another process
- _rlqtpelh.r1r.exe (PID: 3908)
- _rlqtpelh.r1r.exe (PID: 3348)
- Your-File-is-Ready-f_789458824.exe (PID: 1956)
- Your-File-is-Ready-f_789458824.exe (PID: 3340)
- _rlqtpelh.r1r.exe (PID: 3704)
- _rlqtpelh.r1r.exe (PID: 3520)
- CClipboard.exe (PID: 1276)
- CClipboardCm.exe (PID: 2072)
- CClipboard.exe (PID: 3300)
- CClipboardCm.exe (PID: 4072)
- COptions.exe (PID: 2480)
Registers / Runs the DLL via REGSVR32.EXE
- _rlqtpelh.r1r.tmp (PID: 1552)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 3748)
- CClipboard.exe (PID: 3300)
- Explorer.EXE (PID: 1724)
- CClipboardCm.exe (PID: 4072)
- DllHost.exe (PID: 2288)
- svchost.exe (PID: 1772)
- DllHost.exe (PID: 520)
- ctfmon.exe (PID: 1488)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3176)
- _rlqtpelh.r1r.tmp (PID: 3876)
- _rlqtpelh.r1r.exe (PID: 3908)
- _rlqtpelh.r1r.exe (PID: 3348)
- _rlqtpelh.r1r.tmp (PID: 1552)
- Your-File-is-Ready-f_789458824.tmp (PID: 1284)
- Your-File-is-Ready-f_789458824.exe (PID: 1956)
- Your-File-is-Ready-f_789458824.exe (PID: 3340)
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
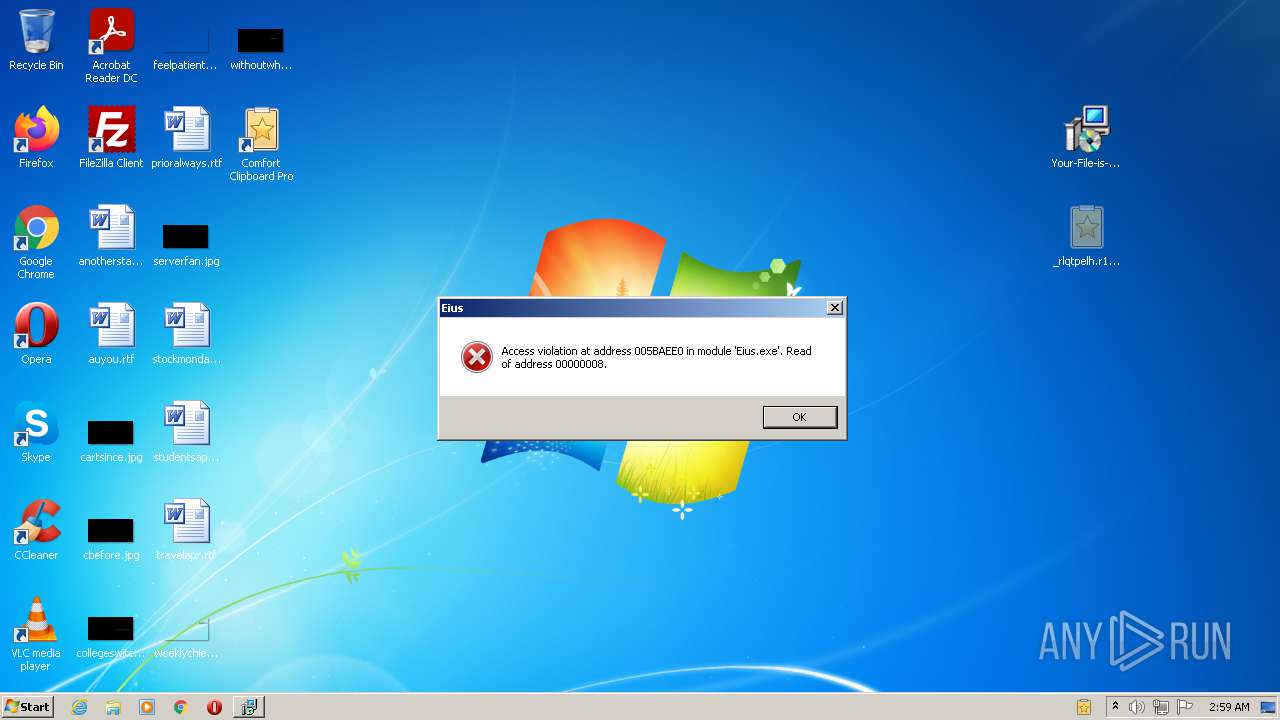
- Eius.exe (PID: 460)
- _rlqtpelh.r1r.exe (PID: 3704)
- _rlqtpelh.r1r.tmp (PID: 2908)
- _rlqtpelh.r1r.exe (PID: 3520)
- CClipboard.exe (PID: 3300)
- CClipboardCm.exe (PID: 4072)
- COptions.exe (PID: 2480)
- _rlqtpelh.r1r.tmp (PID: 3556)
Reads the computer name
- WinRAR.exe (PID: 3176)
- _rlqtpelh.r1r.tmp (PID: 3876)
- Your-File-is-Ready-f_789458824.tmp (PID: 1284)
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
- _rlqtpelh.r1r.tmp (PID: 1552)
- Eius.exe (PID: 460)
- _rlqtpelh.r1r.tmp (PID: 2908)
- CClipboard.exe (PID: 3300)
Executable content was dropped or overwritten
- _rlqtpelh.r1r.exe (PID: 3908)
- WinRAR.exe (PID: 3176)
- _rlqtpelh.r1r.exe (PID: 3348)
- Your-File-is-Ready-f_789458824.exe (PID: 1956)
- Your-File-is-Ready-f_789458824.exe (PID: 3340)
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
- _rlqtpelh.r1r.exe (PID: 3520)
- _rlqtpelh.r1r.exe (PID: 3704)
- _rlqtpelh.r1r.tmp (PID: 1552)
Reads the date of Windows installation
- _rlqtpelh.r1r.tmp (PID: 3876)
- _rlqtpelh.r1r.tmp (PID: 2908)
Drops a file with a compile date too recent
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
Reads the Windows organization settings
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
- _rlqtpelh.r1r.tmp (PID: 1552)
Reads Windows owner or organization settings
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
- _rlqtpelh.r1r.tmp (PID: 1552)
Reads Microsoft Outlook installation path
- Eius.exe (PID: 460)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 3748)
Creates files in the user directory
- CClipboard.exe (PID: 3300)
Creates a directory in Program Files
- CClipboard.exe (PID: 3300)
- _rlqtpelh.r1r.tmp (PID: 1552)
Creates files in the program directory
- CClipboard.exe (PID: 3300)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1724)
INFO
Manual execution by user
- _rlqtpelh.r1r.exe (PID: 3908)
- Your-File-is-Ready-f_789458824.exe (PID: 1956)
- _rlqtpelh.r1r.exe (PID: 3704)
Application was dropped or rewritten from another process
- _rlqtpelh.r1r.tmp (PID: 1552)
- _rlqtpelh.r1r.tmp (PID: 3876)
- Your-File-is-Ready-f_789458824.tmp (PID: 1284)
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
- Eius.exe (PID: 460)
- _rlqtpelh.r1r.tmp (PID: 2908)
- _rlqtpelh.r1r.tmp (PID: 3556)
Creates a software uninstall entry
- _rlqtpelh.r1r.tmp (PID: 1552)
Checks supported languages
- regsvr32.exe (PID: 3748)
- DllHost.exe (PID: 520)
- regsvr32.exe (PID: 3568)
- DllHost.exe (PID: 2288)
Reads the computer name
- DllHost.exe (PID: 520)
- DllHost.exe (PID: 2288)
Loads dropped or rewritten executable
- _rlqtpelh.r1r.tmp (PID: 3876)
- Your-File-is-Ready-f_789458824.tmp (PID: 3112)
- _rlqtpelh.r1r.tmp (PID: 3556)
- Eius.exe (PID: 460)
- _rlqtpelh.r1r.tmp (PID: 2908)
Checks Windows Trust Settings
- CClipboard.exe (PID: 3300)
Reads settings of System Certificates
- CClipboard.exe (PID: 3300)
Creates files in the program directory
- _rlqtpelh.r1r.tmp (PID: 1552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | _rlqtpelh.r1r.exe |
|---|---|
| ZipUncompressedSize: | 4973240 |
| ZipCompressedSize: | 4864419 |
| ZipCRC: | 0xd7503770 |
| ZipModifyDate: | 2019:12:17 19:30:18 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
71
Monitored processes
26
Malicious processes
12
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Users\admin\AppData\Local\Temp\is-MUA6F.tmp\Eius.exe" 6cb7add20650a0a6289d2deb5605b187 | C:\Users\admin\AppData\Local\Temp\is-MUA6F.tmp\Eius.exe | Your-File-is-Ready-f_789458824.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 520 | C:\Windows\system32\DllHost.exe /Processid:{AB8902B4-09CA-4BB6-B78D-A8F59079A8D5} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1276 | "C:\Program Files\ComfortClipboard\CClipboard.exe" | C:\Program Files\ComfortClipboard\CClipboard.exe | — | _rlqtpelh.r1r.tmp | |||||||||||
User: admin Company: Comfort Software Group Integrity Level: MEDIUM Description: Comfort Clipboard Pro 9 Exit code: 3221226540 Version: 9.1.1.0 Modules
| |||||||||||||||
| 1284 | "C:\Users\admin\AppData\Local\Temp\is-UGFMP.tmp\Your-File-is-Ready-f_789458824.tmp" /SL5="$D01A0,4418666,780800,C:\Users\admin\Desktop\Your-File-is-Ready-f_789458824.exe" | C:\Users\admin\AppData\Local\Temp\is-UGFMP.tmp\Your-File-is-Ready-f_789458824.tmp | — | Your-File-is-Ready-f_789458824.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1488 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1552 | "C:\Users\admin\AppData\Local\Temp\is-QIGJ0.tmp\_rlqtpelh.r1r.tmp" /SL5="$110176,4409556,180736,C:\Users\admin\Desktop\_rlqtpelh.r1r.exe" /SPAWNWND=$120144 /NOTIFYWND=$C0192 | C:\Users\admin\AppData\Local\Temp\is-QIGJ0.tmp\_rlqtpelh.r1r.tmp | _rlqtpelh.r1r.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1724 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1956 | "C:\Users\admin\Desktop\Your-File-is-Ready-f_789458824.exe" | C:\Users\admin\Desktop\Your-File-is-Ready-f_789458824.exe | Explorer.EXE | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Dolores Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2072 | "C:\Program Files\ComfortClipboard\CClipboardCm.exe" | C:\Program Files\ComfortClipboard\CClipboardCm.exe | — | CClipboard.exe | |||||||||||
User: admin Company: Comfort Software Group Integrity Level: MEDIUM Description: Comfort Clipboard Service Exit code: 3221226540 Version: 7.4.0.0 Modules
| |||||||||||||||
Total events
12 752
Read events
12 220
Write events
528
Delete events
4
Modification events
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\171\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Your-File-is-Ready-f_789458824.zip | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1724) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
29
Suspicious files
6
Text files
128
Unknown types
105
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1724 | Explorer.EXE | C:\Users\admin\Desktop\Your-File-is-Ready-f_789458824.exe | executable | |
MD5:— | SHA256:— | |||
| 3176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3176.26465\Your-File-is-Ready-f_789458824.exe | executable | |
MD5:— | SHA256:— | |||
| 1956 | Your-File-is-Ready-f_789458824.exe | C:\Users\admin\AppData\Local\Temp\is-UGFMP.tmp\Your-File-is-Ready-f_789458824.tmp | executable | |
MD5:— | SHA256:— | |||
| 1724 | Explorer.EXE | C:\Users\admin\Desktop\_rlqtpelh.r1r.exe | executable | |
MD5:— | SHA256:— | |||
| 1552 | _rlqtpelh.r1r.tmp | C:\Program Files\ComfortClipboard\is-1CSMH.tmp | executable | |
MD5:— | SHA256:— | |||
| 3704 | _rlqtpelh.r1r.exe | C:\Users\admin\AppData\Local\Temp\is-R5LLJ.tmp\_rlqtpelh.r1r.tmp | executable | |
MD5:— | SHA256:— | |||
| 3348 | _rlqtpelh.r1r.exe | C:\Users\admin\AppData\Local\Temp\is-QIGJ0.tmp\_rlqtpelh.r1r.tmp | executable | |
MD5:— | SHA256:— | |||
| 1552 | _rlqtpelh.r1r.tmp | C:\Program Files\ComfortClipboard\Lang\be.txt | text | |
MD5:— | SHA256:— | |||
| 1552 | _rlqtpelh.r1r.tmp | C:\Program Files\ComfortClipboard\Lang\is-1AMTD.tmp | text | |
MD5:— | SHA256:— | |||
| 3520 | _rlqtpelh.r1r.exe | C:\Users\admin\AppData\Local\Temp\is-T0E7L.tmp\_rlqtpelh.r1r.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
7
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1672 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0968e9df1e2aec06 | US | — | — | whitelisted |
1672 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?65aa4131f7afa66c | US | — | — | whitelisted |
460 | Eius.exe | POST | — | 172.67.177.45:80 | http://jorjifornk.live/v3/api | US | — | — | malicious |
460 | Eius.exe | POST | — | 172.67.177.45:80 | http://jorjifornk.live/v3/api | US | — | — | malicious |
3300 | CClipboard.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3300 | CClipboard.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83c7148e1baea2e5 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.67.177.45:80 | jorjifornk.live | — | US | malicious |
460 | Eius.exe | 172.67.177.45:80 | jorjifornk.live | — | US | malicious |
3300 | CClipboard.exe | 104.21.24.80:443 | www.comfort-software.com | Cloudflare Inc | US | malicious |
3300 | CClipboard.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1672 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3300 | CClipboard.exe | 104.21.57.22:443 | www.comfortsoftware.com | Cloudflare Inc | US | unknown |
3300 | CClipboard.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jorjifornk.live |
| unknown |
www.comfort-software.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.comfortsoftware.com |
| malicious |