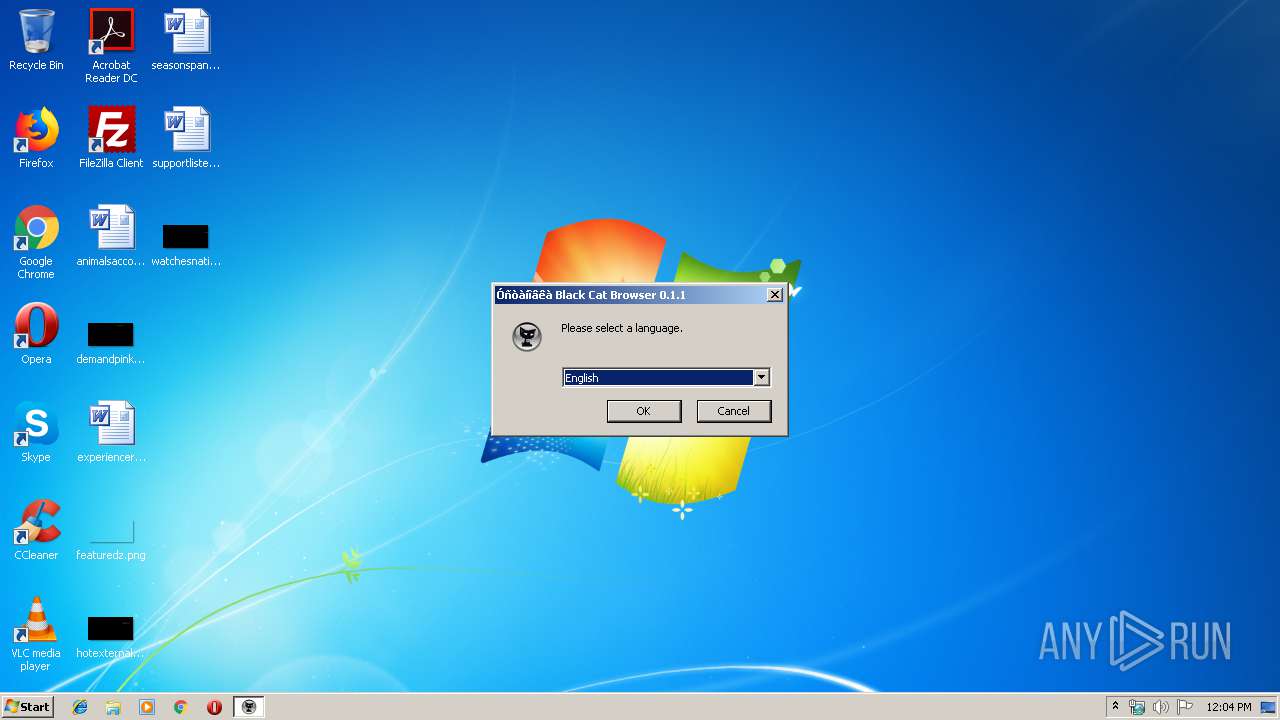
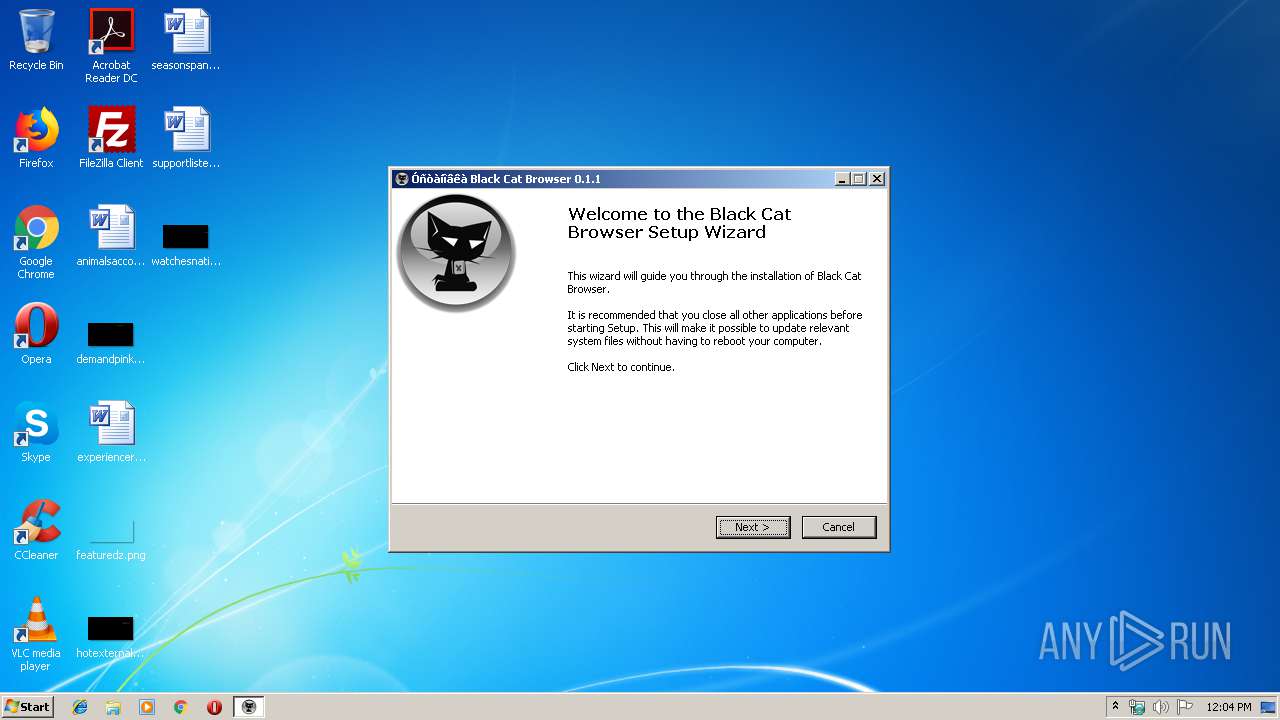
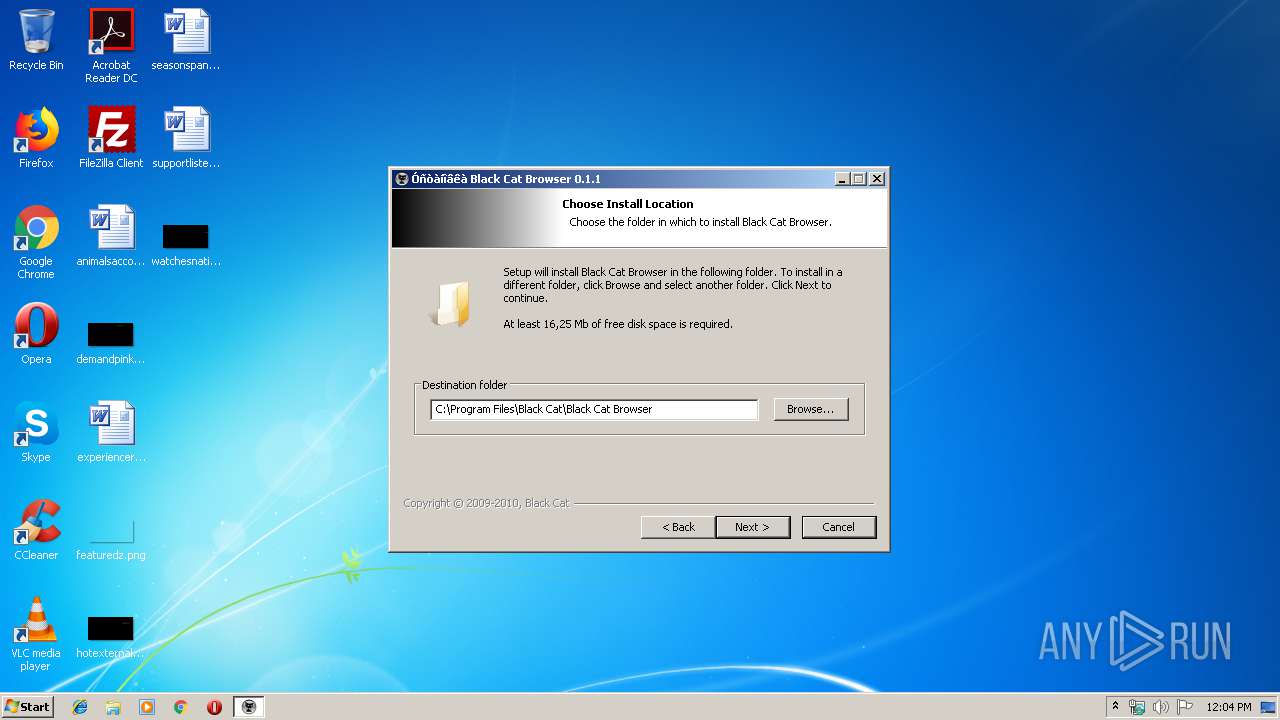
| File name: | blackcat_setup.exe |
| Full analysis: | https://app.any.run/tasks/16b64c5e-f3e7-4237-a354-d5fb9c752145 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2019, 12:03:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B1A2E07BDF3AFC88B04E7E375234FECC |
| SHA1: | 1BDB8344F8EDF956C32F7C4A9720D81D18BCE327 |
| SHA256: | 369807A030F340D5DF314ACD8246FBBA633BE189D2F31AC4C19CDCAC17C687A9 |
| SSDEEP: | 98304:BAI+BGAvjy5Qqbedf/iFMtoDZijGpOBP95tuD3cq2F7MHcOiViMzv2rG9ivG:KtBGcjyjbofadD4GpO1ujMzOiV9eS9gG |
MALICIOUS
Application was dropped or rewritten from another process
- Black Cat.exe (PID: 1576)
SUSPICIOUS
Creates files in the program directory
- blackcat_setup.exe (PID: 2584)
Creates a software uninstall entry
- blackcat_setup.exe (PID: 2584)
Creates files in the user directory
- blackcat_setup.exe (PID: 2584)
Executable content was dropped or overwritten
- blackcat_setup.exe (PID: 2584)
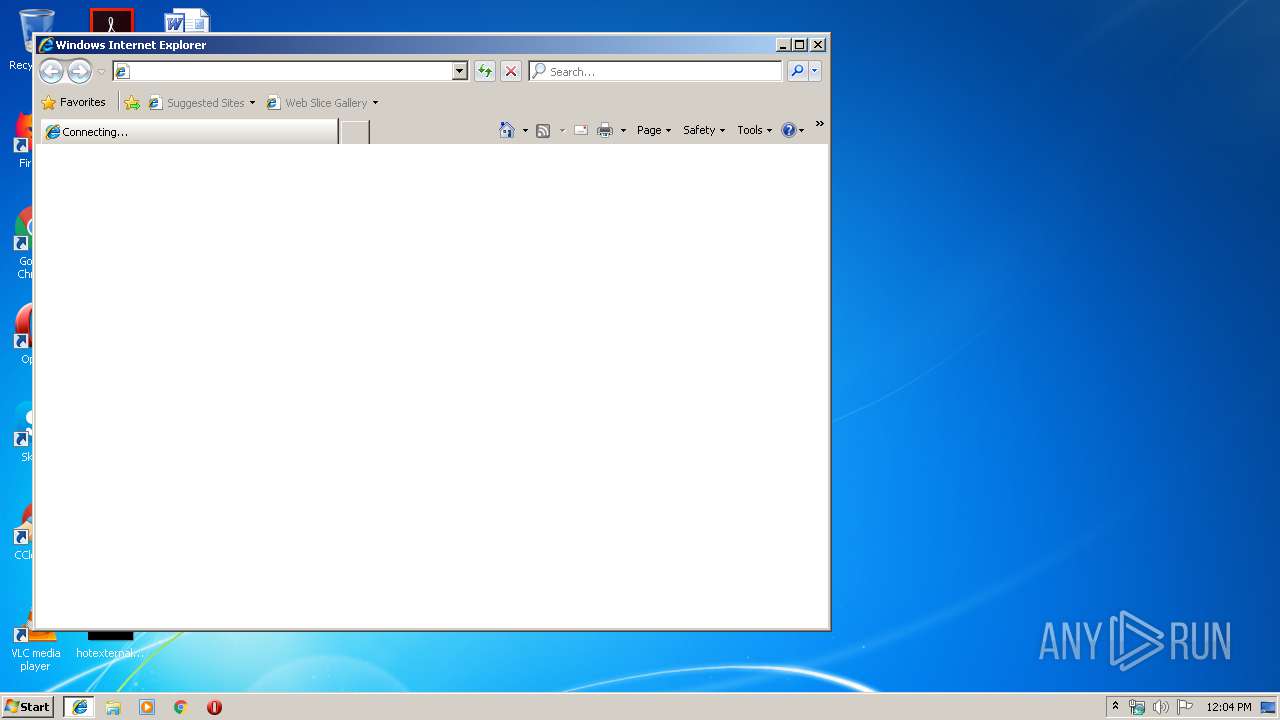
Starts Internet Explorer
- blackcat_setup.exe (PID: 2584)
INFO
Application launched itself
- iexplore.exe (PID: 320)
Changes internet zones settings
- iexplore.exe (PID: 320)
Reads internet explorer settings
- iexplore.exe (PID: 2596)
Creates files in the user directory
- iexplore.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (31.9) |
|---|---|---|
| .scr | | | Windows screen saver (29.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 148992 |
| InitializedDataSize: | 78336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25468 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.1.1.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
| CompanyName: | Black Cat |
| FileDescription: | Black Cat Browser 0.1.1 Installation |
| FileVersion: | 0.1.1 |
| LegalCopyright: | Black Cat |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | Black Cat |
| FileDescription: | Black Cat Browser 0.1.1 Installation |
| FileVersion: | 0.1.1 |
| LegalCopyright: | Black Cat |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x000244CC | 0x00024600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59443 |
DATA | 0x00026000 | 0x00002894 | 0x00002A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.79376 |
BSS | 0x00029000 | 0x000010F5 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0002B000 | 0x00001798 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.88555 |
.tls | 0x0002D000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0002E000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x0002F000 | 0x00001884 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.58665 |
.rsrc | 0x00031000 | 0x0000D360 | 0x0000D400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.80011 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.93923 | 886 | UNKNOWN | Russian - Russia | RT_MANIFEST |
50 | 3.05842 | 744 | UNKNOWN | UNKNOWN | RT_ICON |
51 | 3.11256 | 296 | UNKNOWN | UNKNOWN | RT_ICON |
52 | 4.75161 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
53 | 4.95214 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
54 | 4.82457 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
55 | 7.9376 | 25127 | UNKNOWN | UNKNOWN | RT_ICON |
56 | 4.83183 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
57 | 4.92722 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
58 | 5.08731 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
Imports
advapi32.dll |
cabinet.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
winmm.dll |
Total processes
42
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | blackcat_setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1284 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Black Cat\Black Cat Browser\Black Cat.exe" | C:\Program Files\Black Cat\Black Cat Browser\Black Cat.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\AppData\Local\Temp\blackcat_setup.exe" | C:\Users\admin\AppData\Local\Temp\blackcat_setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Black Cat Integrity Level: MEDIUM Description: Black Cat Browser 0.1.1 Installation Exit code: 3221226540 Version: 0.1.1 Modules
| |||||||||||||||
| 2584 | "C:\Users\admin\AppData\Local\Temp\blackcat_setup.exe" | C:\Users\admin\AppData\Local\Temp\blackcat_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Black Cat Integrity Level: HIGH Description: Black Cat Browser 0.1.1 Installation Exit code: 0 Version: 0.1.1 Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:320 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
421
Read events
333
Write events
87
Delete events
1
Modification events
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | DisplayName |
Value: Black Cat Browser 0.1.1 | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | DisplayVersion |
Value: 0.1.1 | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | VersionMajor |
Value: 0 | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | VersionMinor |
Value: 1 | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | Publisher |
Value: Black Cat | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Black Cat\Black Cat Browser\Uninstall.exe | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Black Cat\Black Cat Browser\Uninstall.exe | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.blackcat.bz/ | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | HelpLink |
Value: mailto:support@blackcat.bz | |||
| (PID) Process: | (2584) blackcat_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Black Cat Browser 0.1.1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Black Cat\Black Cat Browser\ | |||
Executable files
3
Suspicious files
8
Text files
24
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2584 | blackcat_setup.exe | C:\Users\admin\AppData\Local\Temp\$inst\temp_0.tmp | — | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2584 | blackcat_setup.exe | C:\Program Files\Black Cat\Black Cat Browser\Uninstall.exe | executable | |
MD5:— | SHA256:— | |||
| 2584 | blackcat_setup.exe | C:\Users\admin\AppData\Local\Temp\$inst\5.tmp | image | |
MD5:E5DE207BC2B5FDE14CA9578B4ED1D767 | SHA256:440CC7851CEE9BE206E6C25AF74D60F8B92DC33D51E159EC95240A05458E2985 | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF2E31A32B62D40A1F.TMP | — | |
MD5:— | SHA256:— | |||
| 2584 | blackcat_setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\IETldCache\index.dat | dat | |
MD5:D7A950FEFD60DBAA01DF2D85FEFB3862 | SHA256:75D0B1743F61B76A35B1FEDD32378837805DE58D79FA950CB6E8164BFA72073A | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF7204EDA81C0E3441.TMP | — | |
MD5:— | SHA256:— | |||
| 2596 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\noConnect[1] | image | |
MD5:3CB8FACCD5DE434D415AB75C17E8FD86 | SHA256:6976C426E3AC66D66303C114B22B2B41109A7DE648BA55FFC3E5A53BD0DB09E7 | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF5933AEDFCFA3A5BB.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
10
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1576 | Black Cat.exe | GET | — | 140.211.166.81:80 | http://adblockplus.mozdev.org/easylist/easylist.txt | US | — | — | suspicious |
1576 | Black Cat.exe | GET | 204 | 216.58.205.227:80 | http://clients1.google.ru/generate_204 | US | — | — | whitelisted |
1576 | Black Cat.exe | GET | 204 | 172.217.16.195:80 | http://www.google.ru/client_204?&atyp=i&biw=853&bih=370&ei=b8-UXJD9OIXStAWR7LzQCA | US | — | — | whitelisted |
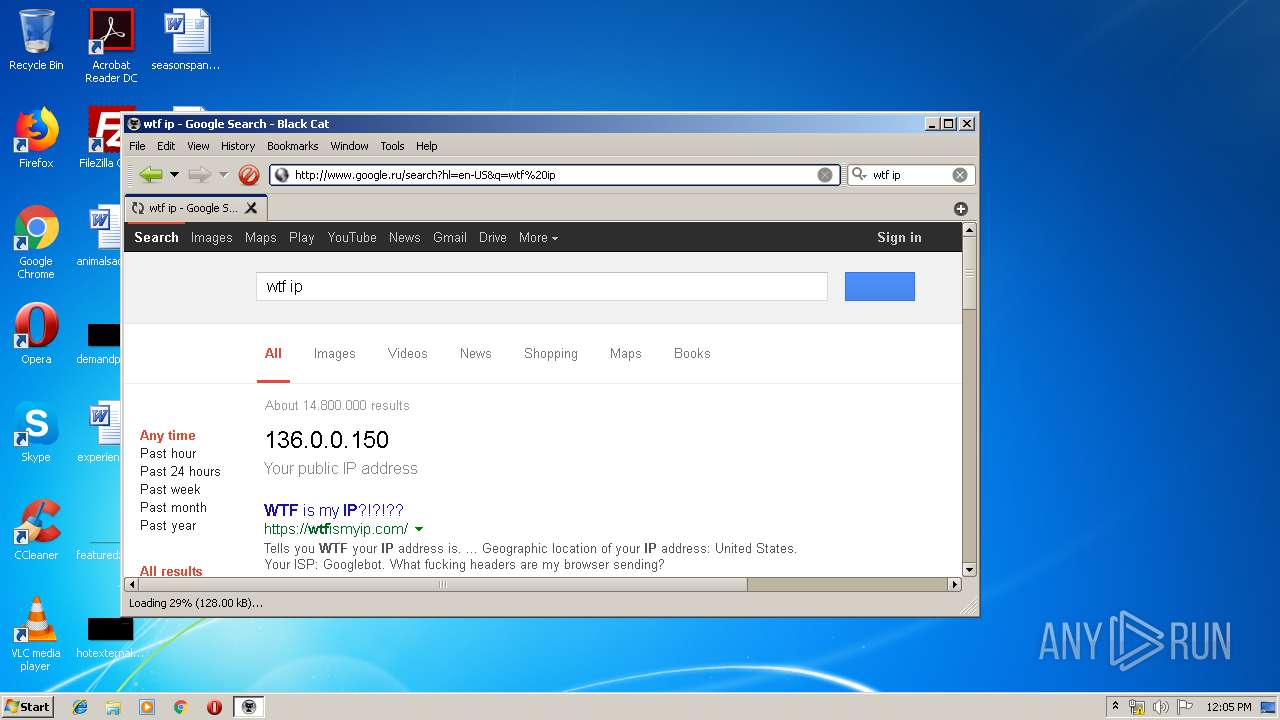
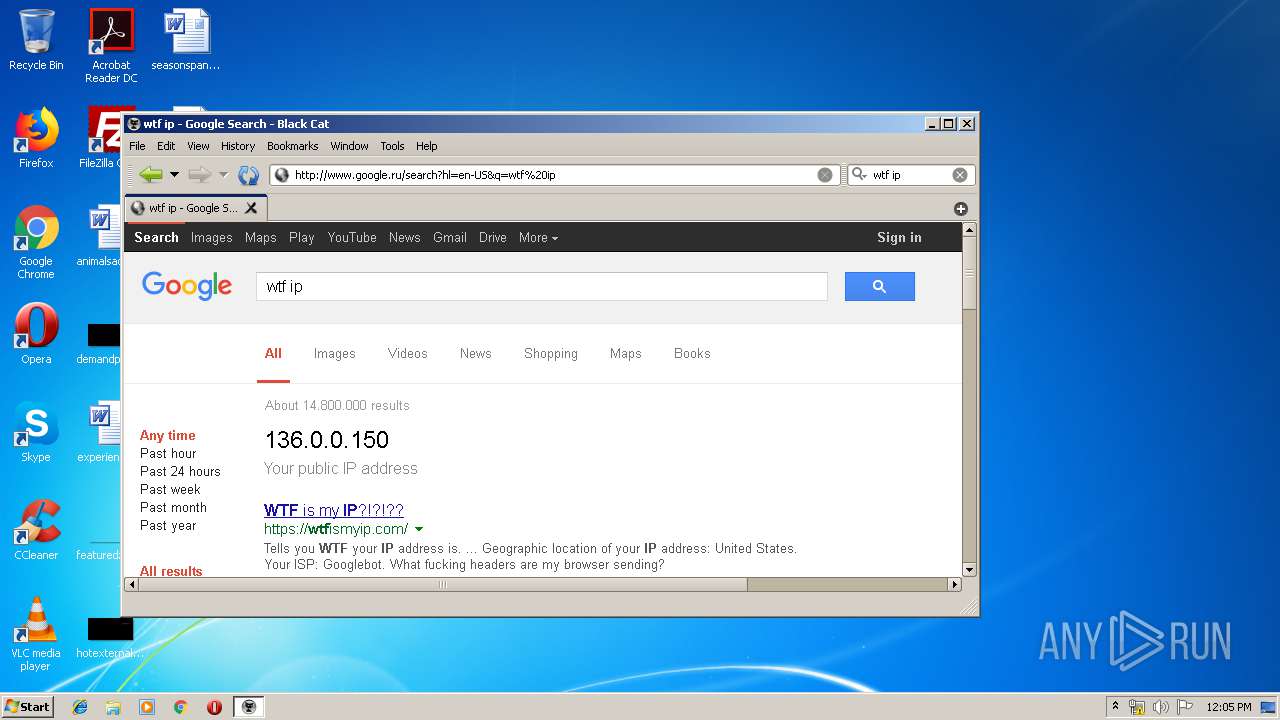
1576 | Black Cat.exe | GET | 200 | 172.217.16.195:80 | http://www.google.ru/search?hl=en-US&q=wtf%20ip | US | html | 21.5 Kb | whitelisted |
1576 | Black Cat.exe | GET | 200 | 172.217.16.195:80 | http://www.google.ru/xjs/_/js/k=xjs.hp.en.un0kSKBuyvA.O/m=sb_he,d/rt=j/d=1/rs=ACT90oEdNPbSegkZ0CsNKEb_5PK1su-XSA | US | text | 49.3 Kb | whitelisted |
1576 | Black Cat.exe | GET | 302 | 172.217.16.195:80 | http://www.google.ru/url?q=https://wtfismyip.com/&sa=U&ved=0ahUKEwjQ8PbR2pXhAhUFKa0KHRE2D4oQFggVMAE&usg=AOvVaw2rqTQLpwlLc8zRaijsTgg2 | US | html | 219 b | whitelisted |
320 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
1576 | Black Cat.exe | GET | 200 | 172.217.16.195:80 | http://www.google.ru/images/nav_logo229.png | US | image | 11.9 Kb | whitelisted |
1576 | Black Cat.exe | GET | 200 | 216.58.207.67:80 | http://ssl.gstatic.com/gb/js/sem_5d0e9a88d640580d12b41844f0901e23.js | US | text | 20.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
320 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1576 | Black Cat.exe | 140.211.166.81:80 | adblockplus.mozdev.org | Network for Education and Research in Oregon (NERO) | US | suspicious |
1576 | Black Cat.exe | 172.217.16.195:80 | www.google.ru | Google Inc. | US | whitelisted |
1576 | Black Cat.exe | 216.58.205.227:80 | clients1.google.ru | Google Inc. | US | whitelisted |
1576 | Black Cat.exe | 216.58.207.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1576 | Black Cat.exe | 198.27.74.146:443 | wtfismyip.com | OVH SAS | CA | suspicious |
1576 | Black Cat.exe | 216.58.207.67:80 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
blackcat.bz |
| unknown |
www.bing.com |
| whitelisted |
adblockplus.mozdev.org |
| suspicious |
suggestqueries.google.ru |
| unknown |
www.google.ru |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients1.google.ru |
| whitelisted |
wtfismyip.com |
| shared |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
Black Cat.exe | QGradient::setColorAt: Color position must be specified in the range 0 to 1
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
Black Cat.exe | QSslSocket: cannot call unresolved function SSLv3_client_method
|