| URL: | https://player.nu6i-bg-net.com |
| Full analysis: | https://app.any.run/tasks/e7694b88-29fc-4df8-866c-e948e9db1ff8 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2024, 08:36:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8F5C1D7CABF374833504DBB85E05DCC9 |
| SHA1: | 84D8850A738B64127A5C31C88A45141DF5CBECB7 |
| SHA256: | 368BED9C3B209C2B6049309930839726660CAD229535AA585936E2D71F3C6B7D |
| SSDEEP: | 3:N8N1YktfgIn:2bYo1n |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3240)
The process uses the downloaded file
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2060 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
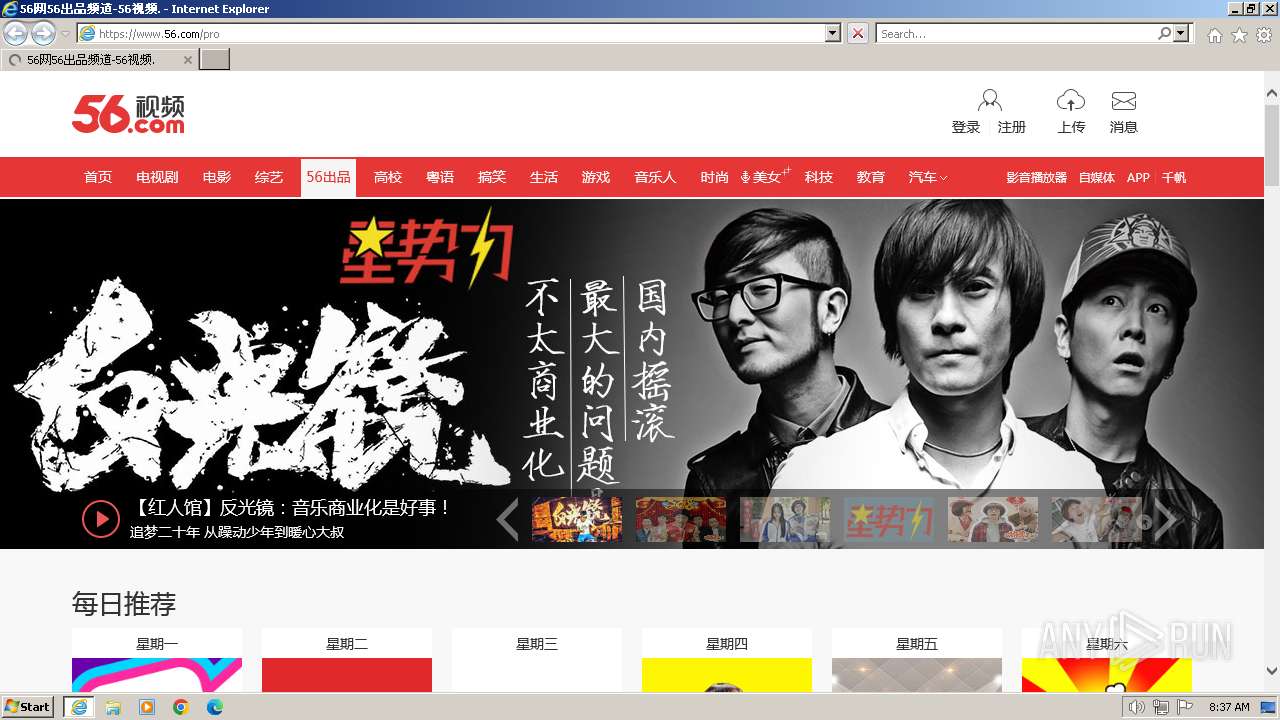
| 3240 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://player.nu6i-bg-net.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3916 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3240 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
35 441
Read events
35 296
Write events
109
Delete events
36
Modification events
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31089221 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31089221 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
155
Text files
537
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:47B0B663FA06E84BA4DC4D76572884D7 | SHA256:F01E94BA91FDB50457BFAF5B51BF00AF959E23837EA4872342A7984FEE946DBA | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:33BBF2BCB694E3F62961F592B038487F | SHA256:1502144E82C63233201F62A19545989E2F3151DE1B75C1D470B9D32D70CD5A5E | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:1BF5D9B826943174A24065275EA2B958 | SHA256:FAB2D3451D2ADB8305C1F11AE4B30291C173A2D5E5716D988ECF90A70E521A5F | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:88F054A45C3A59A06A3C449F7570F83A | SHA256:5CB556E7A050855E2628870B695903213C8C8F7AAB1F6EB631EE7A5BAF4307DC | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8F8712BCE78D28F9C5E3E950CD93EADA_88AC4858D0564F7F097CDB0BBCC4E4A9 | der | |
MD5:97AF9CD7BD92194F3609CC32E8EA61F0 | SHA256:CCC48CB559D27B7CBF888C12C1B5C11177ED2C4129A9E21872112E8F19C019DA | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | der | |
MD5:3EEF56FE4270CDADF054CF3E1A6CD087 | SHA256:EF83F8B3937DBC7AD005F3D20063EE07D2D90D2E45F95C6D4302066474B536E8 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\MTAwMTE0XzE3MDQxMDEyNDI0ODY=[1].jpg | image | |
MD5:B45A09A63B8AD1CFFFBD042D5214B600 | SHA256:562489C401889446A70FF87D74098B71E39201B99AFFBE47CD2C9194F4103FA7 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8F8712BCE78D28F9C5E3E950CD93EADA_0BA2D7600D4338A6D46D0C3E7872B449 | binary | |
MD5:AD928440FDA94F9D1E62E64479951C5F | SHA256:DE7D7566BD72A1F7D7B8C0E622D0FA48781B11E26CF22EB966F462266F8C4314 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8F8712BCE78D28F9C5E3E950CD93EADA_0BA2D7600D4338A6D46D0C3E7872B449 | binary | |
MD5:25DB844B2327EFEAA2F7344279762F3B | SHA256:2A138A62A1E1C5FAC33709B165CD8B34C2200EFFFC01713E2DDBC82C7A570EA3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
112
TCP/UDP connections
253
DNS requests
60
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3916 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c70275e956f241e7 | unknown | — | — | unknown |
3916 | iexplore.exe | GET | 200 | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoEcNCWvIoSyJCm34Ju7Es%3D | unknown | binary | 471 b | unknown |
3916 | iexplore.exe | GET | 200 | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJ%2BYV%2FN5W2THg4NuR8pUi8%3D | unknown | binary | 471 b | unknown |
3916 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3916 | iexplore.exe | GET | 200 | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJ%2BYV%2FN5W2THg4NuR8pUi8%3D | unknown | binary | 471 b | unknown |
3916 | iexplore.exe | GET | 200 | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEA%2FTTmkOYBcvKv8sd6BrFuM%3D | unknown | binary | 471 b | unknown |
3916 | iexplore.exe | GET | 200 | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJ%2BYV%2FN5W2THg4NuR8pUi8%3D | unknown | binary | 471 b | unknown |
3916 | iexplore.exe | GET | — | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJ%2BYV%2FN5W2THg4NuR8pUi8%3D | unknown | — | — | unknown |
3916 | iexplore.exe | GET | 200 | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJ%2BYV%2FN5W2THg4NuR8pUi8%3D | unknown | binary | 471 b | unknown |
3916 | iexplore.exe | GET | 200 | 163.181.56.216:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJl1NKJ3DkPgrdygk1U8cE%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | iexplore.exe | 104.26.11.98:443 | player.nu6i-bg-net.com | CLOUDFLARENET | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3916 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3916 | iexplore.exe | 142.250.186.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 192.168.100.2:53 | — | — | — | whitelisted |
3916 | iexplore.exe | 52.175.9.163:443 | tv.sohu.com | MICROSOFT-CORP-MSN-AS-BLOCK | HK | unknown |
3916 | iexplore.exe | 163.181.56.216:80 | ocsp.dcocsp.cn | Zhejiang Taobao Network Co.,Ltd | DE | unknown |
3916 | iexplore.exe | 163.171.130.132:443 | s2.56img.com | QUANTILNETWORKS | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
player.nu6i-bg-net.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.56.com |
| unknown |
ocsp.dcocsp.cn |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
s2.56img.com |
| whitelisted |
css.tv.itc.cn |
| whitelisted |
js.tv.itc.cn |
| unknown |