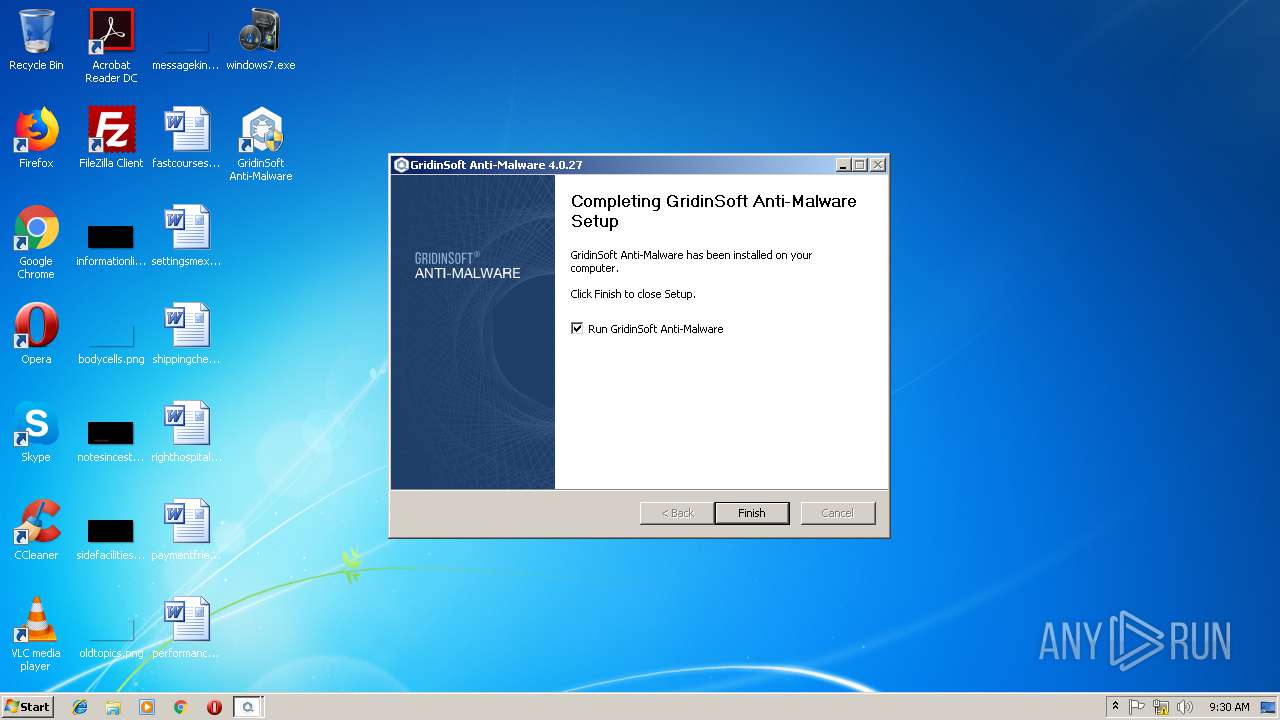
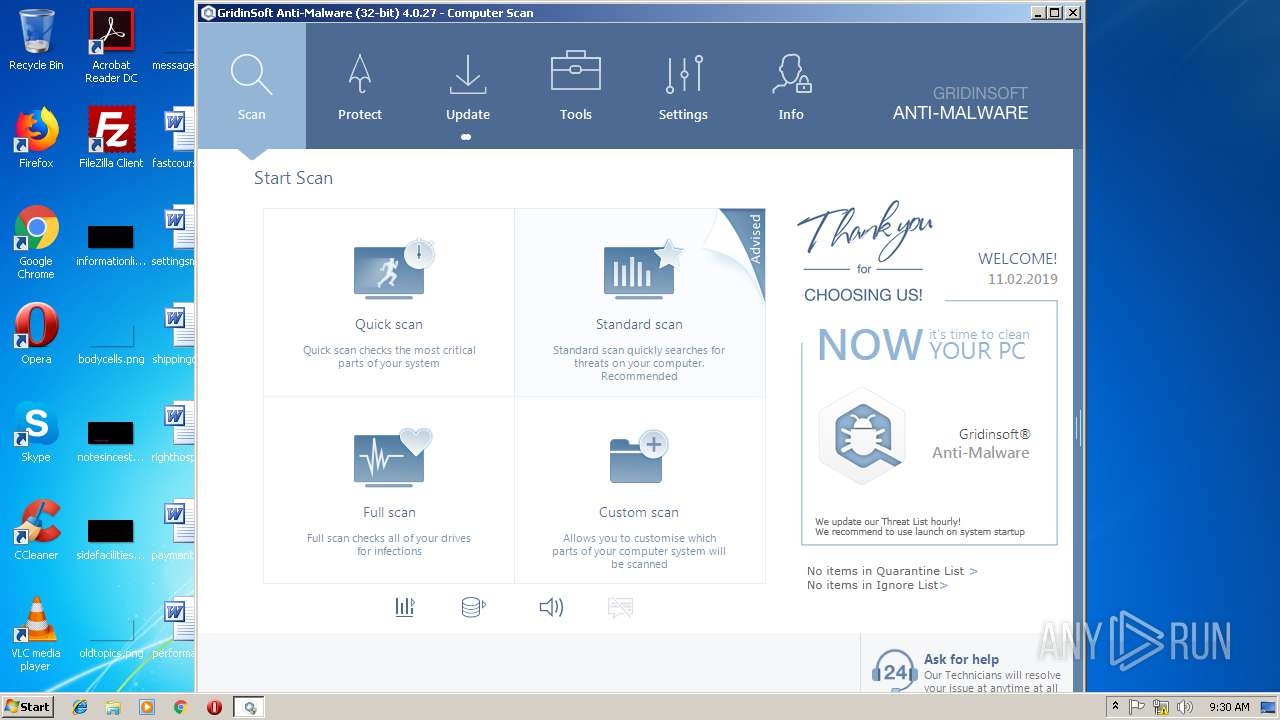
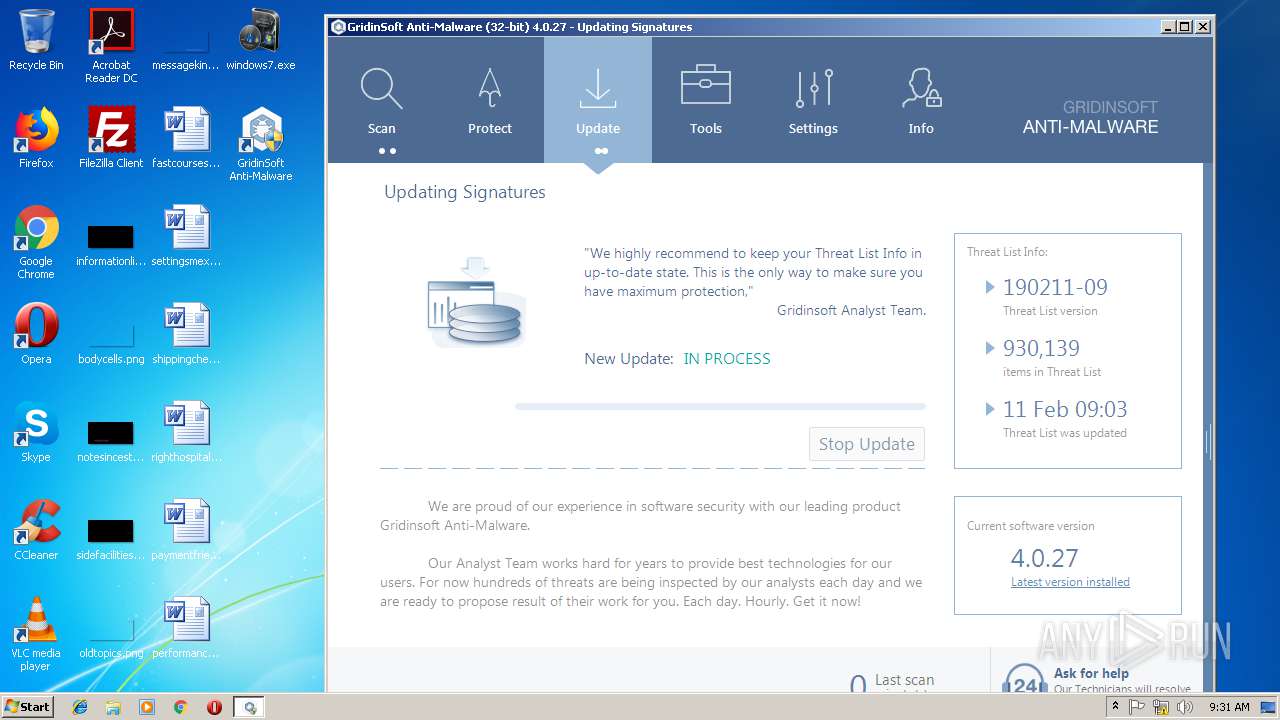
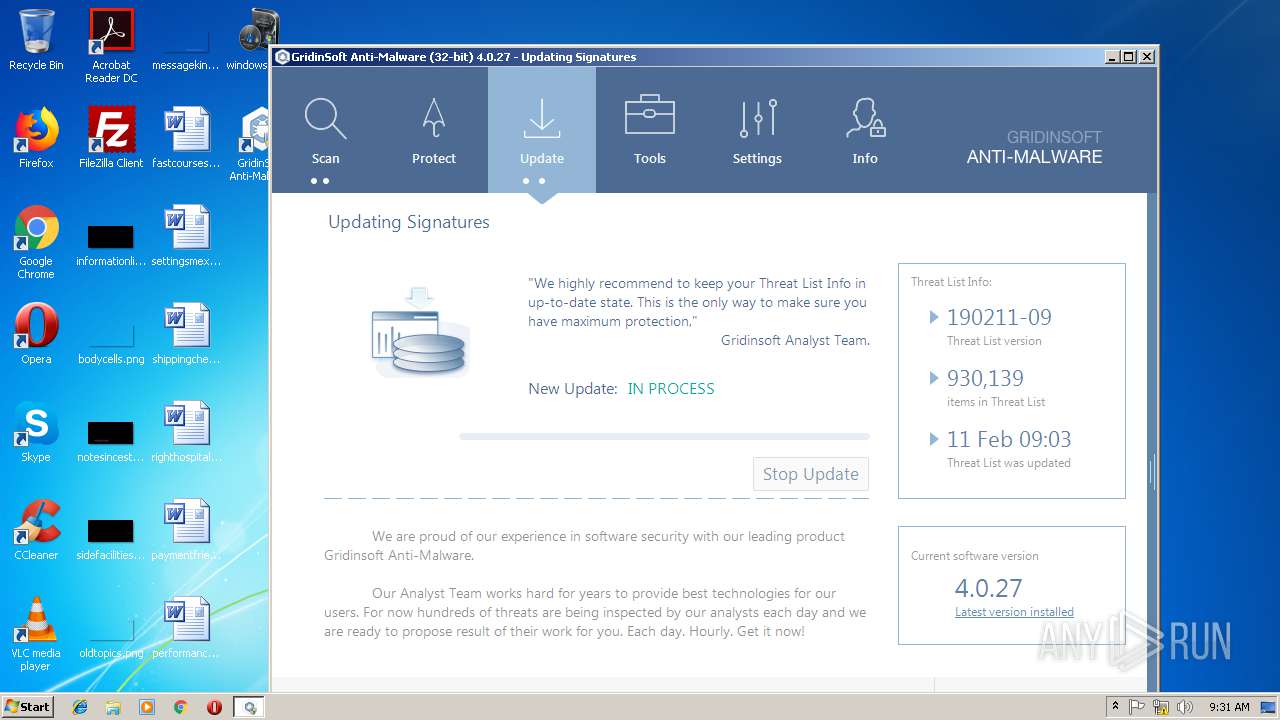
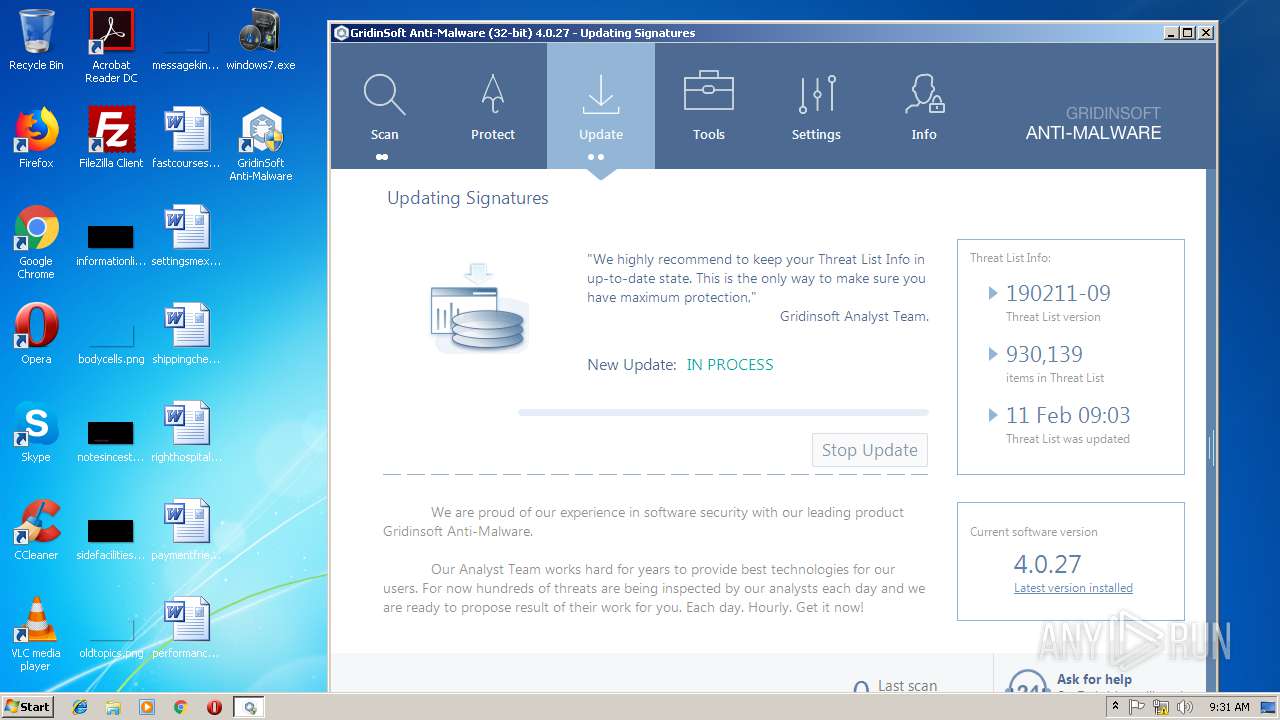
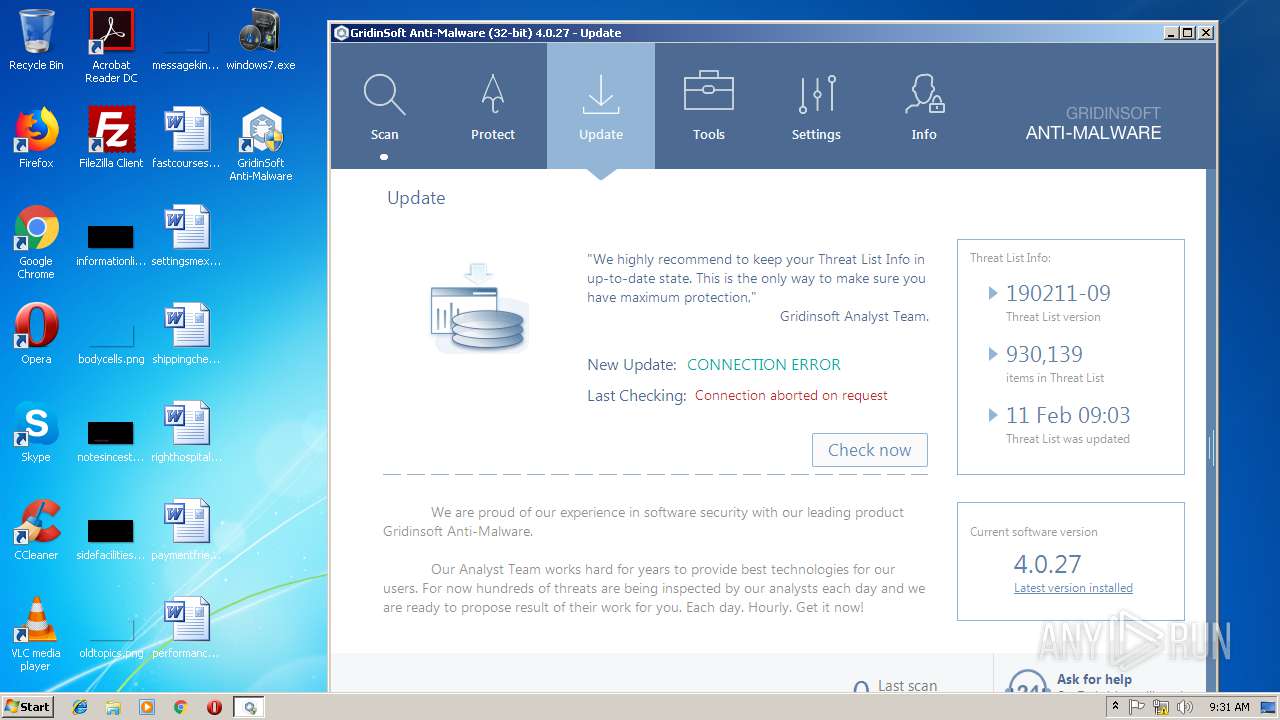
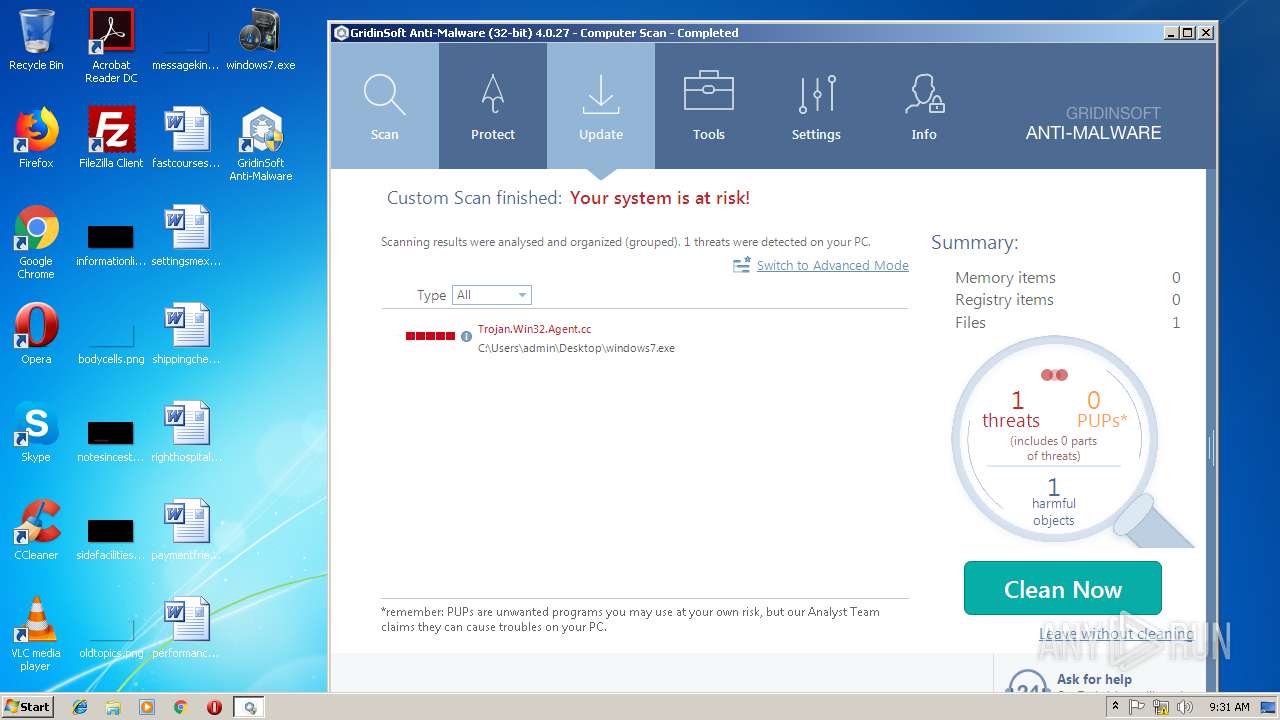
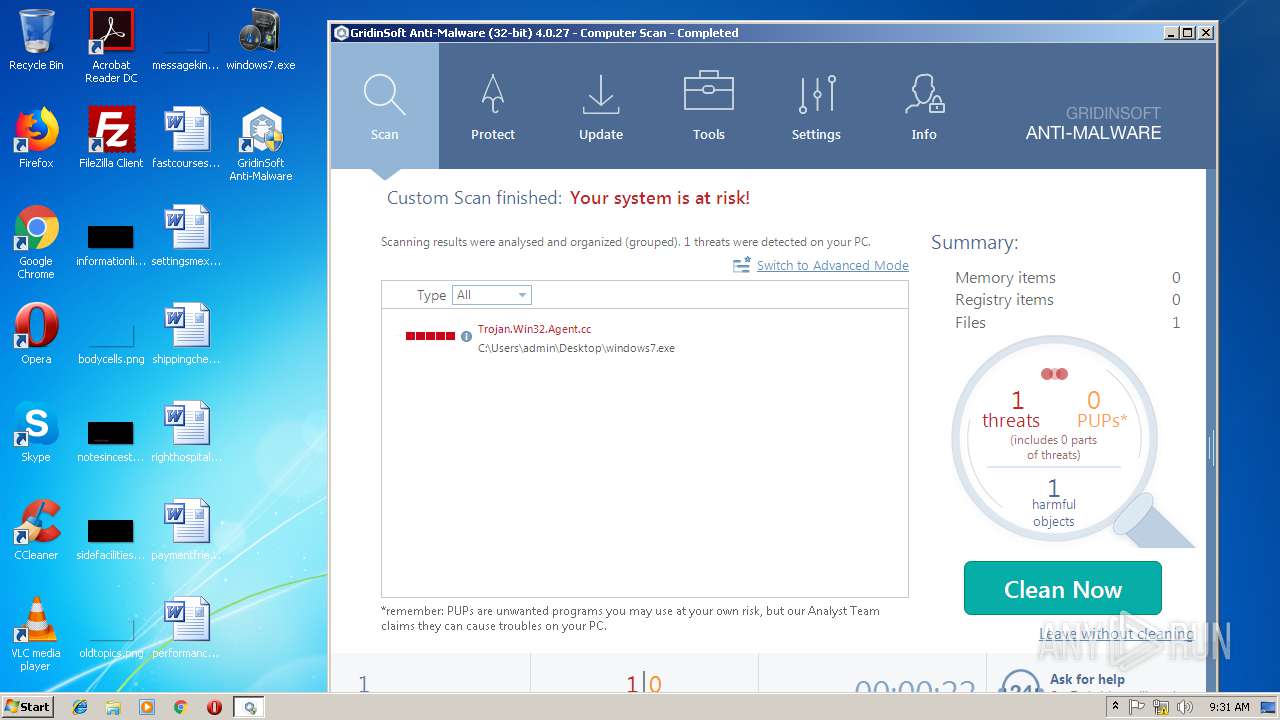
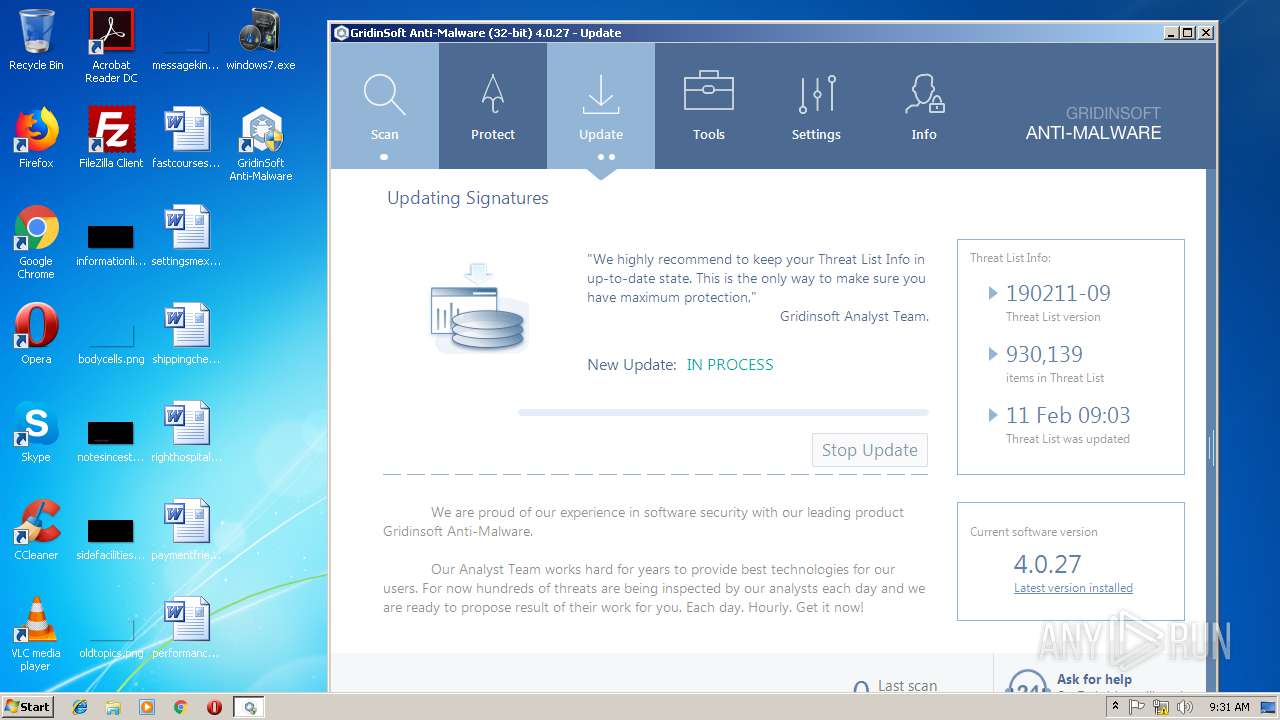
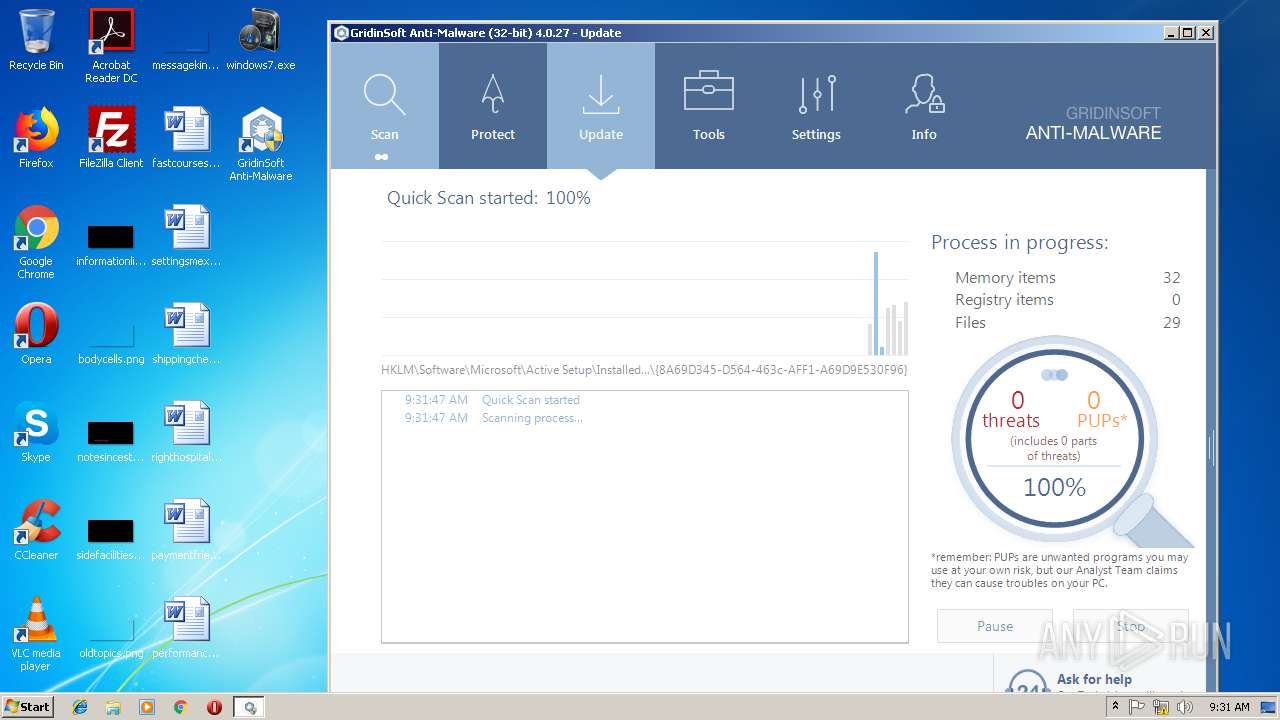
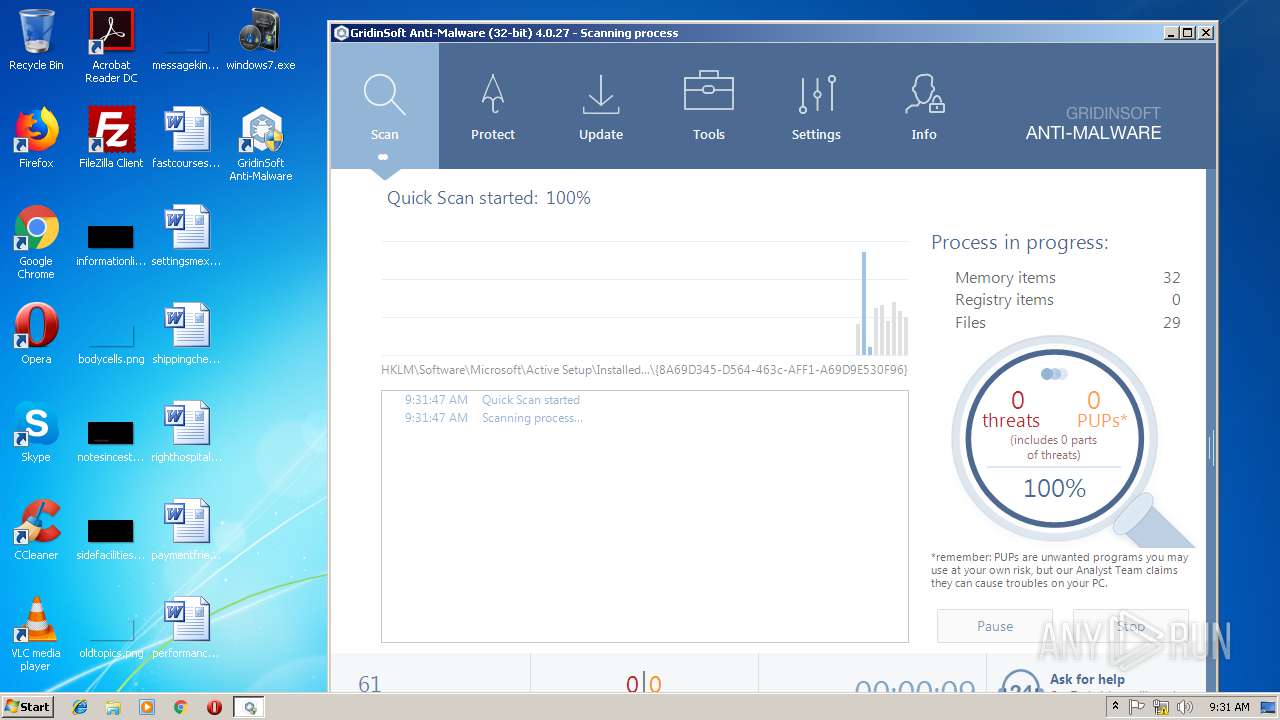
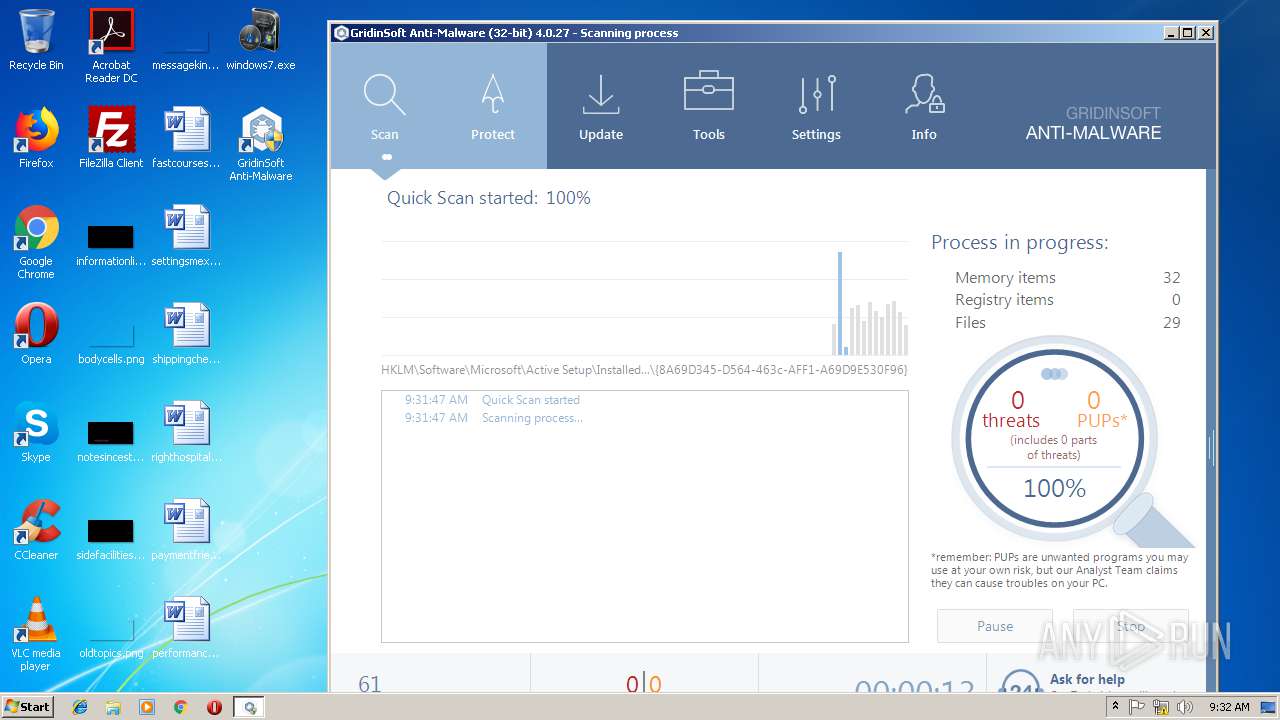
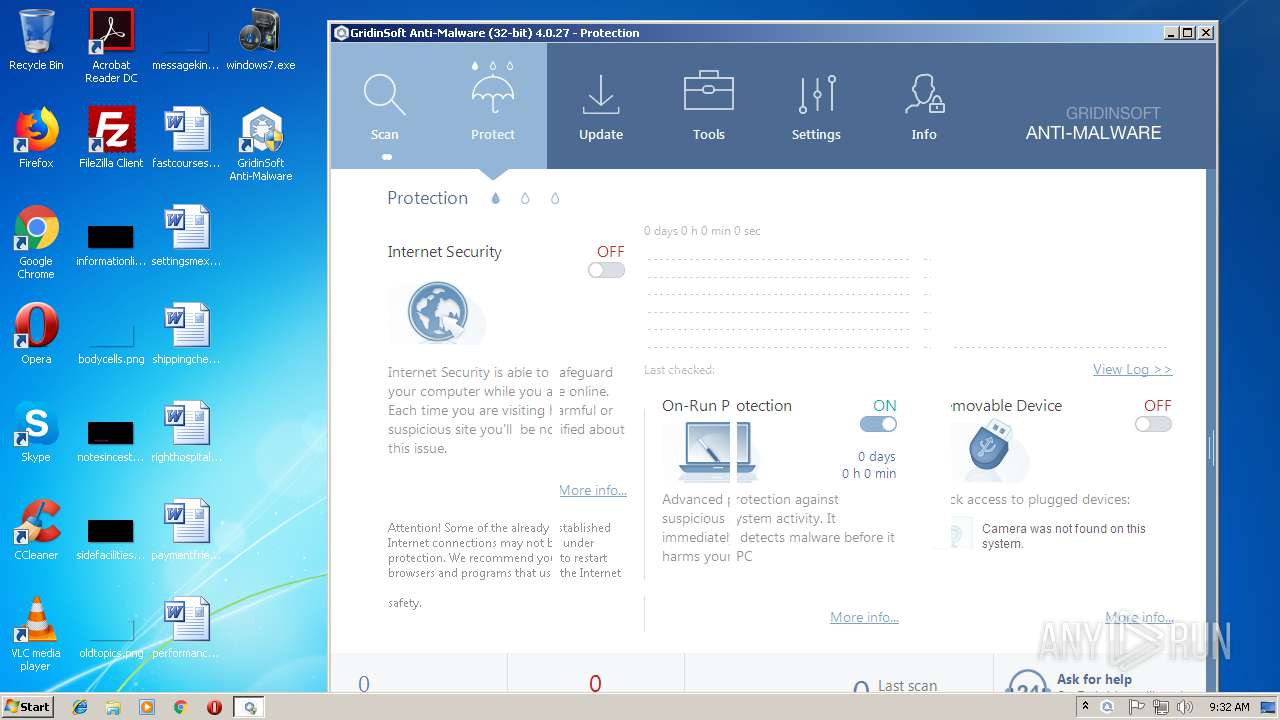
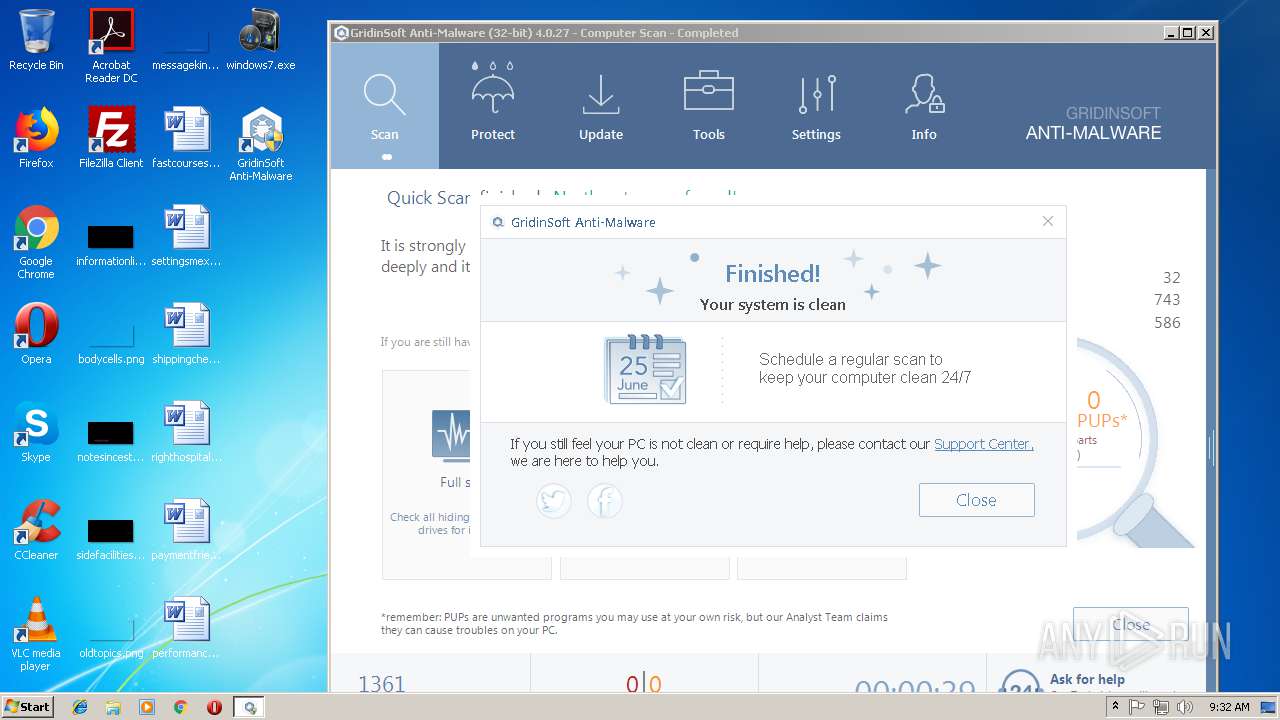
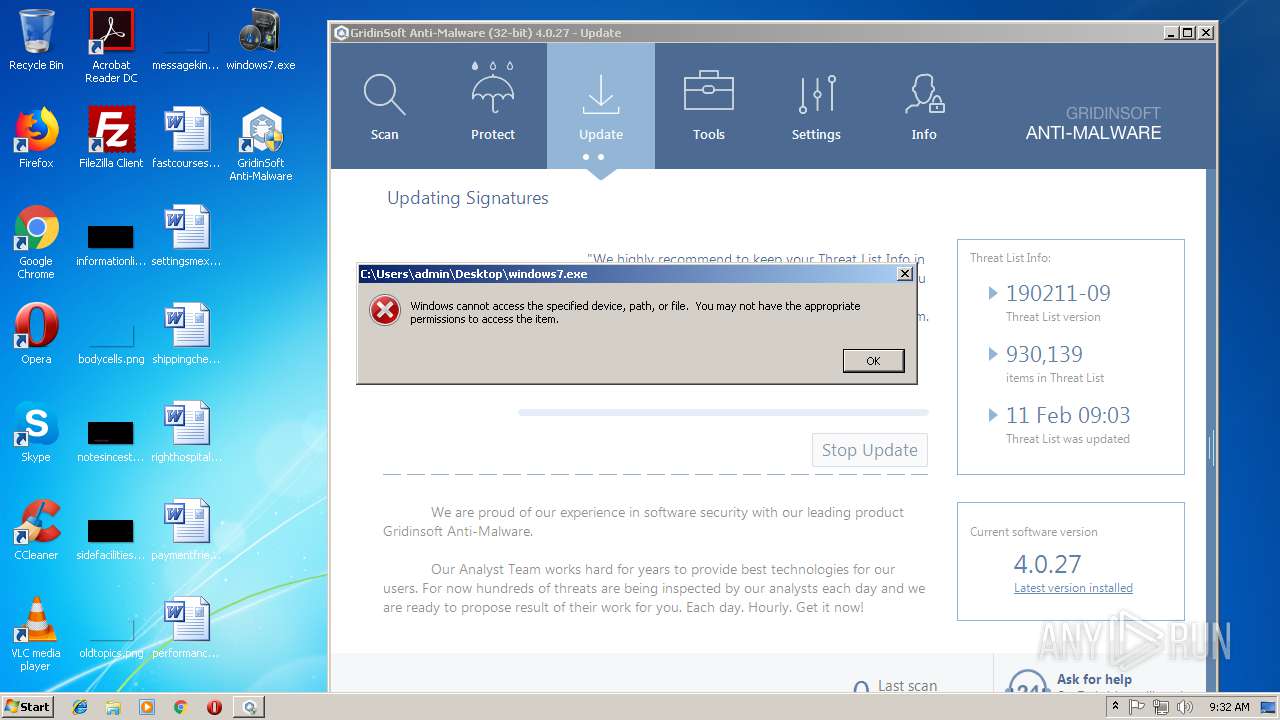
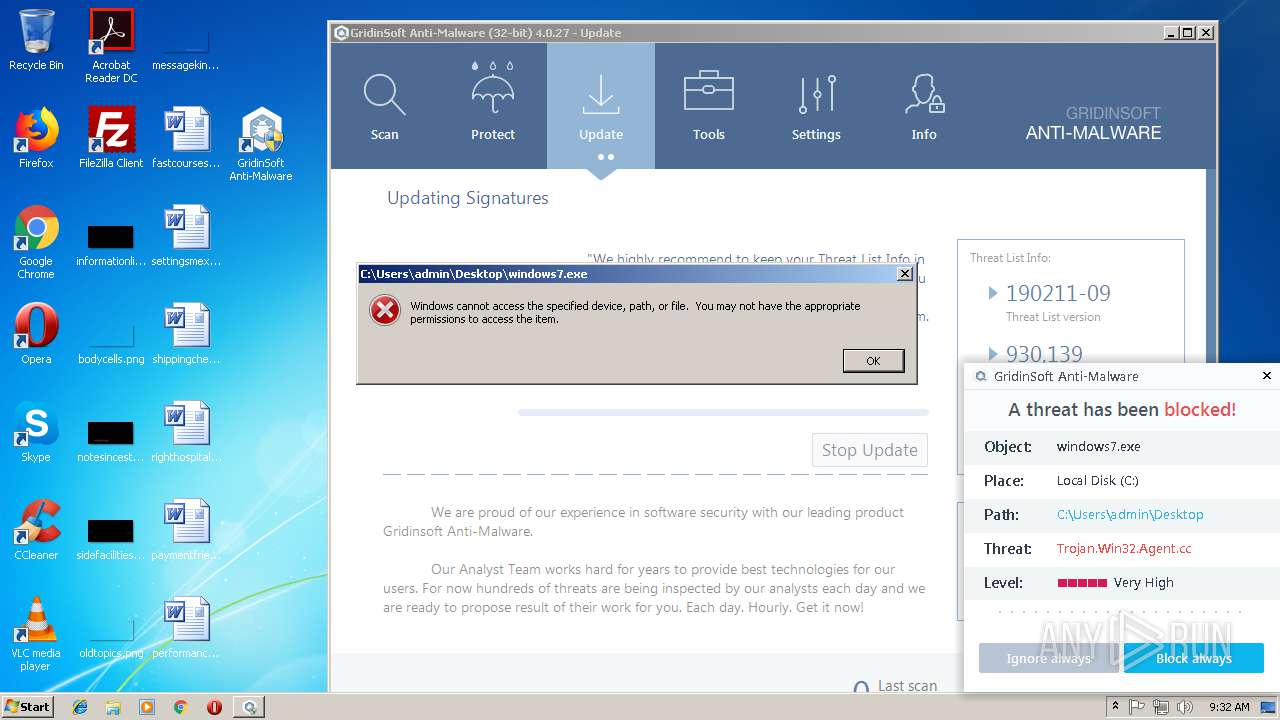
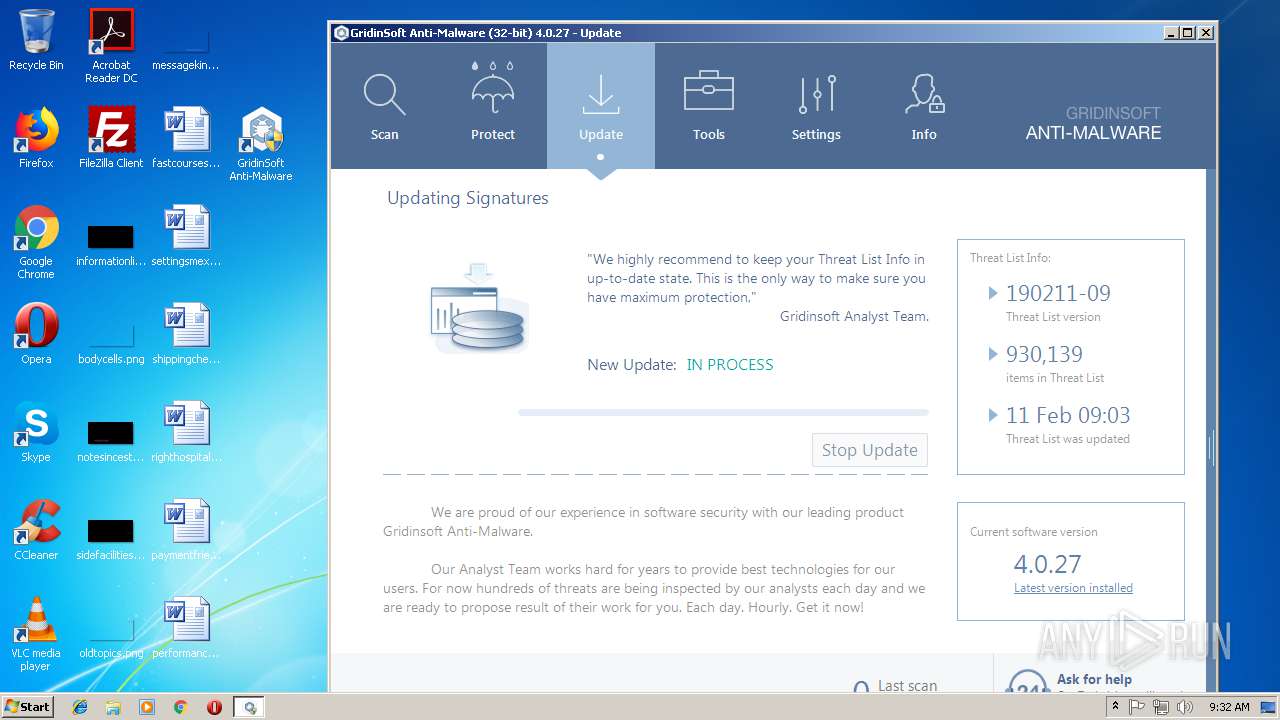
| File name: | windows7.exe |
| Full analysis: | https://app.any.run/tasks/06fb5ee6-6da5-4f5b-95ba-566d2402ff6a |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 09:28:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5281A955DE6A0087BBD186742FB34D50 |
| SHA1: | ADAF9D9A4C8D0205FA650E8E17506016C188D669 |
| SHA256: | 367C8DB9F475EF0A82611BC683C1EE10D500DB71BA044A287B953FDB7B9E5234 |
| SSDEEP: | 24576:utb20pkaCqT5TBWgNQ7ad04blfmD+A6A:bVg5tQ7aOyADP5 |
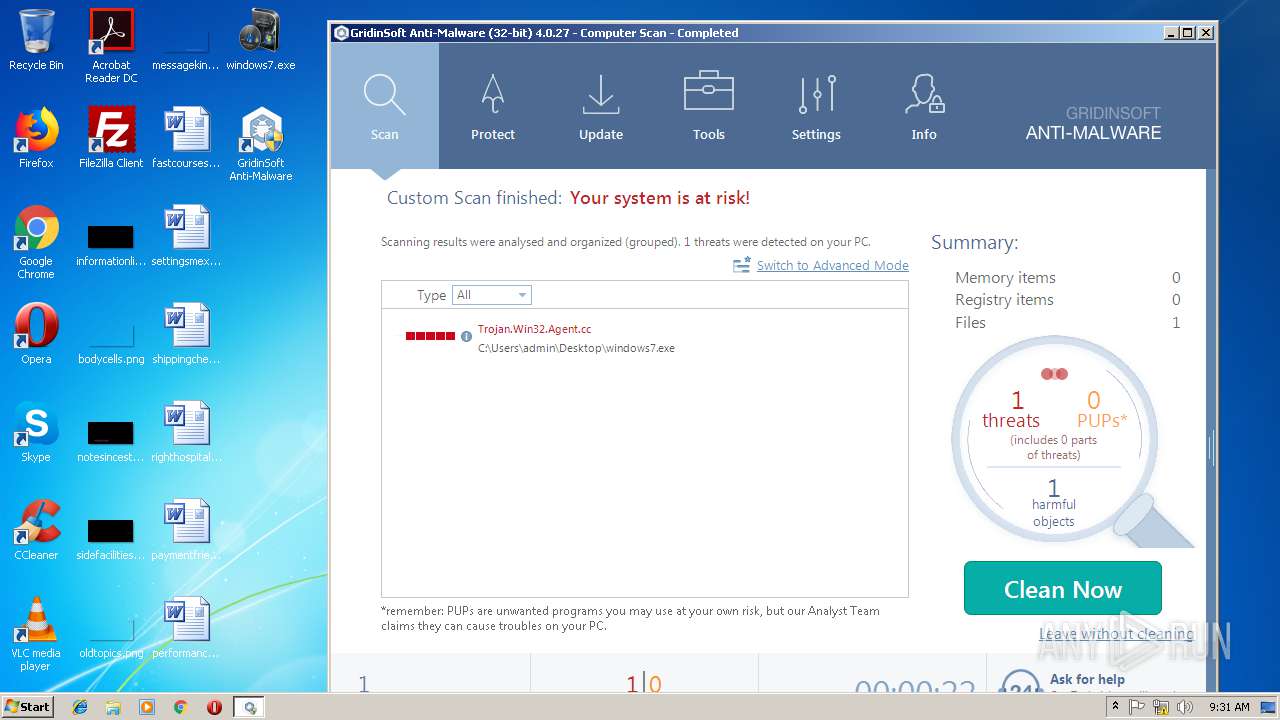
MALICIOUS
Application was dropped or rewritten from another process
- gsam-4.0.27-setup.exe (PID: 3892)
- gsam-4.0.27-setup.exe (PID: 2188)
- gsam-4.0.27-setup.exe (PID: 3976)
- gsam-4.0.27-setup.exe (PID: 3964)
- gsam.exe (PID: 2744)
- devcon32.exe (PID: 3876)
- devcon32.exe (PID: 1328)
- devcon32.exe (PID: 3228)
- gsam.exe (PID: 2160)
- gsam.exe (PID: 3248)
- devcon32.exe (PID: 3460)
- devcon32.exe (PID: 3248)
- devcon32.exe (PID: 3012)
- devcon32.exe (PID: 2480)
- devcon32.exe (PID: 2576)
- devcon32.exe (PID: 2352)
- devcon32.exe (PID: 2528)
Loads dropped or rewritten executable
- gsam-4.0.27-setup.exe (PID: 3976)
- gsam-4.0.27-setup.exe (PID: 3964)
- regsvr32.exe (PID: 3372)
- gsam.exe (PID: 2744)
- gsam.exe (PID: 3248)
- explorer.exe (PID: 284)
Registers / Runs the DLL via REGSVR32.EXE
- gsam-4.0.27-setup.exe (PID: 3964)
Changes the autorun value in the registry
- RUNDLL32.EXE (PID: 2716)
- RUNDLL32.EXE (PID: 3488)
- RUNDLL32.EXE (PID: 2332)
Loads the Task Scheduler COM API
- gsam.exe (PID: 2744)
Loads the Task Scheduler DLL interface
- gsam.exe (PID: 2744)
Actions looks like stealing of personal data
- gsam.exe (PID: 2744)
Changes settings of System certificates
- gsam.exe (PID: 2744)
SUSPICIOUS
Executable content was dropped or overwritten
- gsam-4.0.27-setup.exe (PID: 3976)
- chrome.exe (PID: 3896)
- gsam-4.0.27-setup.exe (PID: 3964)
- RUNDLL32.EXE (PID: 3488)
- RUNDLL32.EXE (PID: 2332)
Creates files in the program directory
- gsam-4.0.27-setup.exe (PID: 3964)
- gsam.exe (PID: 2744)
- cmd.exe (PID: 1528)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 3228)
- cmd.exe (PID: 348)
- cmd.exe (PID: 1340)
- cmd.exe (PID: 2884)
- cmd.exe (PID: 3592)
- cmd.exe (PID: 2484)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 1240)
Creates a software uninstall entry
- gsam-4.0.27-setup.exe (PID: 3964)
Uses RUNDLL32.EXE to load library
- gsam-4.0.27-setup.exe (PID: 3964)
Creates files in the driver directory
- RUNDLL32.EXE (PID: 3488)
- RUNDLL32.EXE (PID: 2332)
Removes files from Windows directory
- RUNDLL32.EXE (PID: 3488)
- RUNDLL32.EXE (PID: 2332)
Creates files in the Windows directory
- RUNDLL32.EXE (PID: 3488)
- RUNDLL32.EXE (PID: 2332)
Reads CPU info
- gsam.exe (PID: 2744)
- gsam.exe (PID: 3248)
Creates COM task schedule object
- regsvr32.exe (PID: 3372)
Starts CMD.EXE for commands execution
- gsam.exe (PID: 2744)
Reads Internet Cache Settings
- gsam.exe (PID: 2744)
Reads Environment values
- gsam.exe (PID: 3248)
- gsam.exe (PID: 2744)
Searches for installed software
- gsam.exe (PID: 2744)
Reads Microsoft Outlook installation path
- gsam.exe (PID: 2744)
Adds / modifies Windows certificates
- gsam.exe (PID: 2744)
INFO
Application launched itself
- chrome.exe (PID: 3896)
Reads Internet Cache Settings
- chrome.exe (PID: 3896)
Reads settings of System Certificates
- gsam.exe (PID: 2744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:11:16 04:20:28+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 570880 |
| InitializedDataSize: | 496640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25f74 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 16-Nov-2014 03:20:28 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 16-Nov-2014 03:20:28 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0008B54F | 0x0008B600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.68041 |
.rdata | 0x0008D000 | 0x0002CC42 | 0x0002CE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.77019 |
.data | 0x000BA000 | 0x00009D54 | 0x00006200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.00269 |
.rsrc | 0x000C4000 | 0x0003BC68 | 0x0003BE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.16417 |
.reloc | 0x00100000 | 0x0000A474 | 0x0000A600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.24543 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.38312 | 944 | Latin 1 / Western European | English - United Kingdom | RT_MANIFEST |
2 | 2.05883 | 296 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
3 | 2.25499 | 296 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
4 | 7.98643 | 69804 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
5 | 4.82778 | 67624 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
6 | 5.0776 | 38056 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
7 | 3.34702 | 1428 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
8 | 3.2817 | 1674 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
9 | 3.28849 | 1168 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
10 | 3.28373 | 1532 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
MPR.dll |
OLEAUT32.dll |
PSAPI.DLL |
SHELL32.dll |
Total processes
104
Monitored processes
51
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | cmd.exe /c "C:\Program Files\GridinSoft Anti-Malware\devcon32.exe" find =image >devconout2231562 | C:\Windows\system32\cmd.exe | — | gsam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1240 | cmd.exe /c "C:\Program Files\GridinSoft Anti-Malware\devcon32.exe" find =image >devconout2349187 | C:\Windows\system32\cmd.exe | — | gsam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=904,5524988714595490015,3537961272117865834,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=345441D26E216D0356DB4A2DBB6816C1 --mojo-platform-channel-handle=4000 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\GridinSoft Anti-Malware\devcon32.exe" find =camera | C:\Program Files\GridinSoft Anti-Malware\devcon32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.17134.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1340 | cmd.exe /c "C:\Program Files\GridinSoft Anti-Malware\devcon32.exe" find =camera >devconout2263921 | C:\Windows\system32\cmd.exe | — | gsam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1528 | cmd.exe /c "C:\Program Files\GridinSoft Anti-Malware\devcon32.exe" find =camera >devconout2231296 | C:\Windows\system32\cmd.exe | — | gsam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2160 | "C:\PROGRA~1\GRIDIN~1\gsam.exe" "C:\Users\admin\Desktop\windows7.exe" | C:\PROGRA~1\GRIDIN~1\gsam.exe | — | explorer.exe | |||||||||||
User: admin Company: GridinSoft LLC Integrity Level: MEDIUM Description: GridinSoft Anti-Malware Exit code: 3221226540 Version: 4.0.27.252 Modules
| |||||||||||||||
| 2188 | "C:\Users\admin\Downloads\gsam-4.0.27-setup.exe" | C:\Users\admin\Downloads\gsam-4.0.27-setup.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2208 | "C:\Windows\system32\runonce.exe" -r | C:\Windows\system32\runonce.exe | — | RUNDLL32.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 487
Read events
8 146
Write events
331
Delete events
10
Modification events
| (PID) Process: | (3896) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3896) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3896) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | Puebzr |
Value: 000000000400000001000000F5470000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFE0203144ECC1D40100000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002F0000003D00000085431500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000E0000005DEC04007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000003702000008023CE23702350100C082BAD075B048D4750200000001000000A048D4750100000068E23702C5B8D075A848D47501000000C81008000000000090E237026BB9D07500000000350100C001000000B0E23702973CB8779C3CB877F58CF77501000000350100C00000000088E23702FFFFFFFFF8E23702EDE0B47745727800FEFFFFFFC0E237020D6BD075A0E737028CE8370200000000F8E23702973CB8779C3CB877BD8CF775000000008CE83702A0E73702D0E237020100000070E73702EDE0B47745727800FEFFFFFF08E337020D6BD0757E0000008CE8370280E73702F36BD075E186D0752794C6128CE8370210000000570104003E0040008CE83702A0E73702000000000000000000000000000008025CE537020000080254E33702350100C000000000D8E637023200000018000000000000000000000088E3370211000000B8450B00B0450B0032000000D8E63702F0E300009B1EC112A0E3370282919576F0E33702A4E3370227959576000000006C155002CCE33702CD9495766C15500278E43702E0105002E194957600000000E010500278E43702D4E33702090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | P:\Hfref\Choyvp\Qrfxgbc\Tbbtyr Puebzr.yax |
Value: 00000000040000000000000003000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFE0203144ECC1D40100000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 0000000026000000000000002500000009000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000001D020000000085F990758C52F402BCD51D0294D51D028852F402C8D51D02546F9D76BC66AC760000000068DA1D026C31917568DA1D02553E9175337AD50628DD1D0200000000813E917590DA1D0294DA1D028852F402CD78D50656DD1D0200000000337AD506740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000091768106A77681069176810600000000000000000000000000000000000000000000000000000000000000009D240000C0ED9D0388D61D0233AB4777C019F5EFFC0B00001027000008000000ED530200BCD61D02F8AA4777ED530200C0ED9D03DCD61D02E8DED4035CD71D0200000000A20100001CD700001360DF7ACCD61D02829191751CD71D02D0D61D02279591750000000074E3D403F8D61D02CD94917574E3D403A4D71D02E8DED403E194917500000000E8DED403A4D71D0200D71D0209000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000001D020000000085F990758C52F402BCD51D0294D51D028852F402C8D51D02546F9D76BC66AC760000000068DA1D026C31917568DA1D02553E9175337AD50628DD1D0200000000813E917590DA1D0294DA1D028852F402CD78D50656DD1D0200000000337AD506740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000091768106A77681069176810600000000000000000000000000000000000000000000000000000000000000009D240000C0ED9D0388D61D0233AB4777C019F5EFFC0B00001027000008000000ED530200BCD61D02F8AA4777ED530200C0ED9D03DCD61D02E8DED4035CD71D0200000000A20100001CD700001360DF7ACCD61D02829191751CD71D02D0D61D02279591750000000074E3D403F8D61D02CD94917574E3D403A4D71D02E8DED403E194917500000000E8DED403A4D71D0200D71D0209000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000001D020000000085F990758C52F402BCD51D0294D51D028852F402C8D51D02546F9D76BC66AC760000000068DA1D026C31917568DA1D02553E9175337AD50628DD1D0200000000813E917590DA1D0294DA1D028852F402CD78D50656DD1D0200000000337AD506740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000091768106A77681069176810600000000000000000000000000000000000000000000000000000000000000009D240000C0ED9D0388D61D0233AB4777C019F5EFFC0B00001027000008000000ED530200BCD61D02F8AA4777ED530200C0ED9D03DCD61D02E8DED4035CD71D0200000000A20100001CD700001360DF7ACCD61D02829191751CD71D02D0D61D02279591750000000074E3D403F8D61D02CD94917574E3D403A4D71D02E8DED403E194917500000000E8DED403A4D71D0200D71D02 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | P:\Hfref\Choyvp\Qrfxgbc\Tbbtyr Puebzr.yax |
Value: 00000000040000000000000004000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFE0203144ECC1D40100000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 0000000026000000000000002600000009000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000001D020000000085F990758C52F402BCD51D0294D51D028852F402C8D51D02546F9D76BC66AC760000000068DA1D026C31917568DA1D02553E9175337AD50628DD1D0200000000813E917590DA1D0294DA1D028852F402CD78D50656DD1D0200000000337AD506740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000091768106A77681069176810600000000000000000000000000000000000000000000000000000000000000009D240000C0ED9D0388D61D0233AB4777C019F5EFFC0B00001027000008000000ED530200BCD61D02F8AA4777ED530200C0ED9D03DCD61D02E8DED4035CD71D0200000000A20100001CD700001360DF7ACCD61D02829191751CD71D02D0D61D02279591750000000074E3D403F8D61D02CD94917574E3D403A4D71D02E8DED403E194917500000000E8DED403A4D71D0200D71D0209000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000001D020000000085F990758C52F402BCD51D0294D51D028852F402C8D51D02546F9D76BC66AC760000000068DA1D026C31917568DA1D02553E9175337AD50628DD1D0200000000813E917590DA1D0294DA1D028852F402CD78D50656DD1D0200000000337AD506740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000091768106A77681069176810600000000000000000000000000000000000000000000000000000000000000009D240000C0ED9D0388D61D0233AB4777C019F5EFFC0B00001027000008000000ED530200BCD61D02F8AA4777ED530200C0ED9D03DCD61D02E8DED4035CD71D0200000000A20100001CD700001360DF7ACCD61D02829191751CD71D02D0D61D02279591750000000074E3D403F8D61D02CD94917574E3D403A4D71D02E8DED403E194917500000000E8DED403A4D71D0200D71D0209000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C004100630072006F0062006100740020005200650061006400650072002000440043002E006C006E006B0000006C006E006B000000630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000001D020000000085F990758C52F402BCD51D0294D51D028852F402C8D51D02546F9D76BC66AC760000000068DA1D026C31917568DA1D02553E9175337AD50628DD1D0200000000813E917590DA1D0294DA1D028852F402CD78D50656DD1D0200000000337AD506740A91750000000000000000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000091768106A77681069176810600000000000000000000000000000000000000000000000000000000000000009D240000C0ED9D0388D61D0233AB4777C019F5EFFC0B00001027000008000000ED530200BCD61D02F8AA4777ED530200C0ED9D03DCD61D02E8DED4035CD71D0200000000A20100001CD700001360DF7ACCD61D02829191751CD71D02D0D61D02279591750000000074E3D403F8D61D02CD94917574E3D403A4D71D02E8DED403E194917500000000E8DED403A4D71D0200D71D02 | |||
| (PID) Process: | (3912) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3896-13194350960048000 |
Value: 259 | |||
Executable files
45
Suspicious files
113
Text files
149
Unknown types
81
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ed0f2747-561e-4d6e-9dcb-e0123c97650f.tmp | — | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\0bcae05a-0bce-43c9-844b-493bbf7849b5.tmp | — | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF210bd6.TMP | text | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF210c05.TMP | text | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3896 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
20
DNS requests
14
Threats
80
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
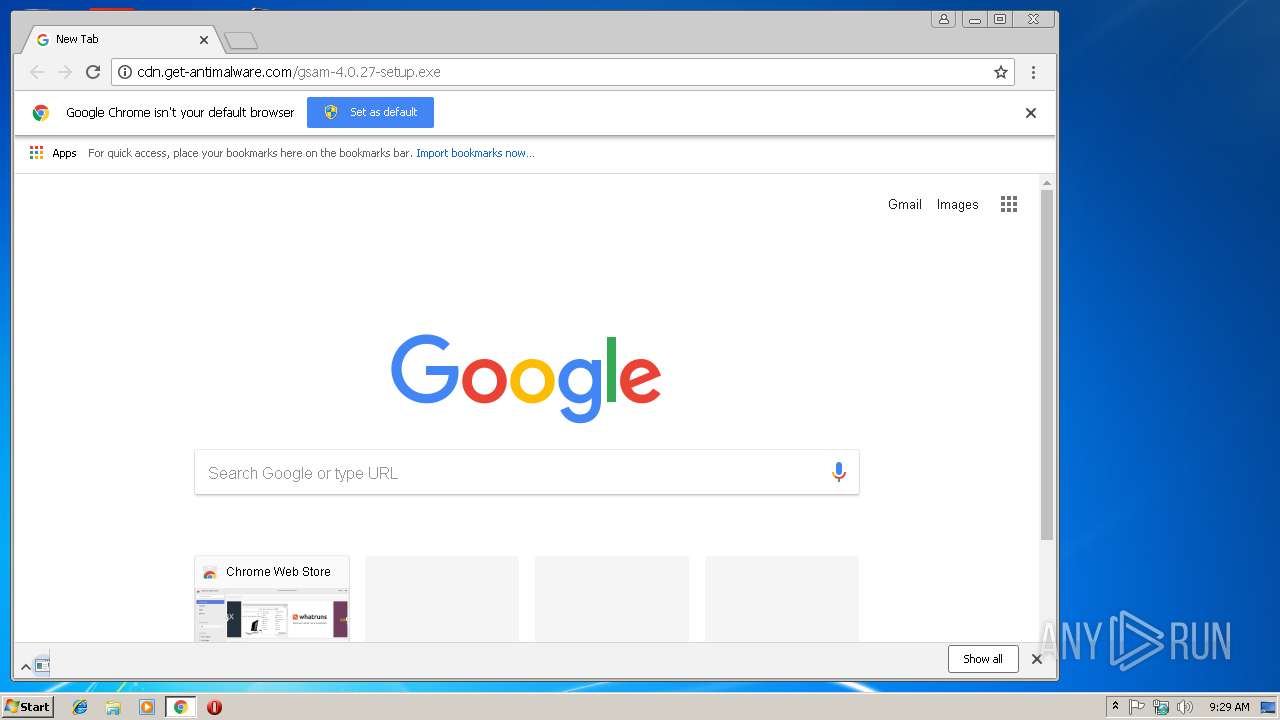
3896 | chrome.exe | GET | — | 2.20.143.8:80 | http://cdn.get-antimalware.com/gsam-4.0.27-setup.exe | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3896 | chrome.exe | 216.58.205.227:443 | www.google.de | Google Inc. | US | whitelisted |
3896 | chrome.exe | 172.217.21.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 172.217.22.106:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 216.58.207.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 172.217.22.110:443 | apis.google.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 74.125.206.106:443 | www.google.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 216.58.208.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 172.217.22.78:443 | ogs.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
cdn.get-antimalware.com |
| whitelisted |
www.google.com |
| malicious |
www.google.co.uk |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3896 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
2744 | gsam.exe | A Network Trojan was detected | ET INFO Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
Process | Message |
|---|---|
gsam.exe | unknown property 'align-items' at ((31))
|
gsam.exe | unknown property 'align-items' at ((31))
|
gsam.exe | unknown property 'align-items' at ((31))
|
gsam.exe | unknown property 'align-items' at ((31))
|
gsam.exe | unknown property 'align-items' at ((31))
|
gsam.exe | unknown property 'align-items' at ((73))
|
gsam.exe | unknown property 'align-items' at ((73))
|
gsam.exe | unknown property 'align-items' at ((63))
|
gsam.exe | unknown property 'align-items' at ((31))
|
gsam.exe | unknown property 'align-items' at ((31))
|