| File name: | KeyboardSplitter.exe |
| Full analysis: | https://app.any.run/tasks/4cc3aecc-a62b-4e9f-bb33-668c0df865d3 |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2024, 13:42:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 81E89981CEBF899BD3EE985A88A63D53 |
| SHA1: | 67C2733322E10475A91C9AD4805FE478662A7B0B |
| SHA256: | 36656BC7DF1C724AFECEA974A85533D83D1BCA3675DC541E42CD2592AF00EE77 |
| SSDEEP: | 98304:o1tpy43QTufo7h3XFvfXMWMmyHoeRzCueFrq3bOBqygpCtyawall0XtkPp1DQvQL:o8bhLytkgZqeUJi |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- KeyboardSplitter.exe (PID: 1156)
- keyboard_driver.exe (PID: 6212)
- devcon.exe (PID: 6280)
- drvinst.exe (PID: 6664)
- drvinst.exe (PID: 6448)
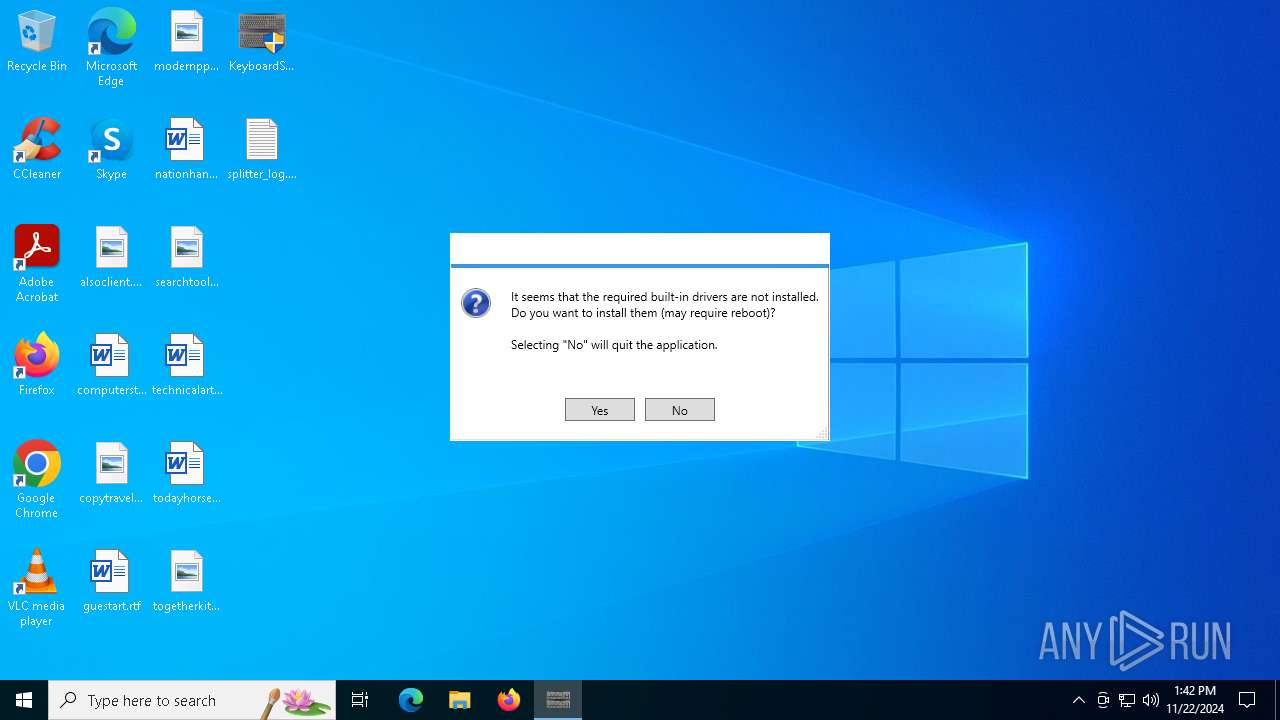
Drops a system driver (possible attempt to evade defenses)
- keyboard_driver.exe (PID: 6212)
- KeyboardSplitter.exe (PID: 1156)
- drvinst.exe (PID: 6448)
- devcon.exe (PID: 6280)
- drvinst.exe (PID: 6664)
Process drops legitimate windows executable
- devcon.exe (PID: 6280)
- KeyboardSplitter.exe (PID: 1156)
- drvinst.exe (PID: 6448)
- drvinst.exe (PID: 6664)
Starts a Microsoft application from unusual location
- devcon.exe (PID: 6280)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (45.4) |
|---|---|---|
| .exe | | | InstallShield setup (26.7) |
| .exe | | | Win64 Executable (generic) (17.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (4) |
| .exe | | | Win32 Executable (generic) (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:28 12:31:47+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 6309888 |
| InitializedDataSize: | 374784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6067de |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.3.0.0 |
| ProductVersionNumber: | 2.3.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Keyboard Splitter (Creates up to 4 virtual xbox 360 contollers and feeds them using keyboards and/or mice) |
| CompanyName: | djlastnight |
| FileDescription: | Keyboard Splitter |
| FileVersion: | 2.3.0.0 |
| InternalName: | KeyboardSplitter.exe |
| LegalCopyright: | Copyright © 2023 |
| OriginalFileName: | KeyboardSplitter.exe |
| ProductName: | djlastnight's Gaming Keyboard Splitter |
| ProductVersion: | 2.3.0.0 |
| AssemblyVersion: | 2.3.0.0 |
Total processes
128
Monitored processes
10
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1156 | "C:\Users\admin\Desktop\KeyboardSplitter.exe" | C:\Users\admin\Desktop\KeyboardSplitter.exe | explorer.exe | ||||||||||||
User: admin Company: djlastnight Integrity Level: HIGH Description: Keyboard Splitter Version: 2.3.0.0 Modules
| |||||||||||||||
| 4420 | "C:\Users\admin\Desktop\KeyboardSplitter.exe" | C:\Users\admin\Desktop\KeyboardSplitter.exe | — | explorer.exe | |||||||||||
User: admin Company: djlastnight Integrity Level: MEDIUM Description: Keyboard Splitter Exit code: 3221226540 Version: 2.3.0.0 Modules
| |||||||||||||||
| 6096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | KeyboardSplitter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6212 | "C:\Users\admin\AppData\Local\Temp\KeyboardSplitter 2.3.0.0 resources\keyboard_driver.exe" /install | C:\Users\admin\AppData\Local\Temp\KeyboardSplitter 2.3.0.0 resources\keyboard_driver.exe | KeyboardSplitter.exe | ||||||||||||
User: admin Company: Francisco Lopes Integrity Level: HIGH Description: Interception command line installation tool Exit code: 0 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 6220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | keyboard_driver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
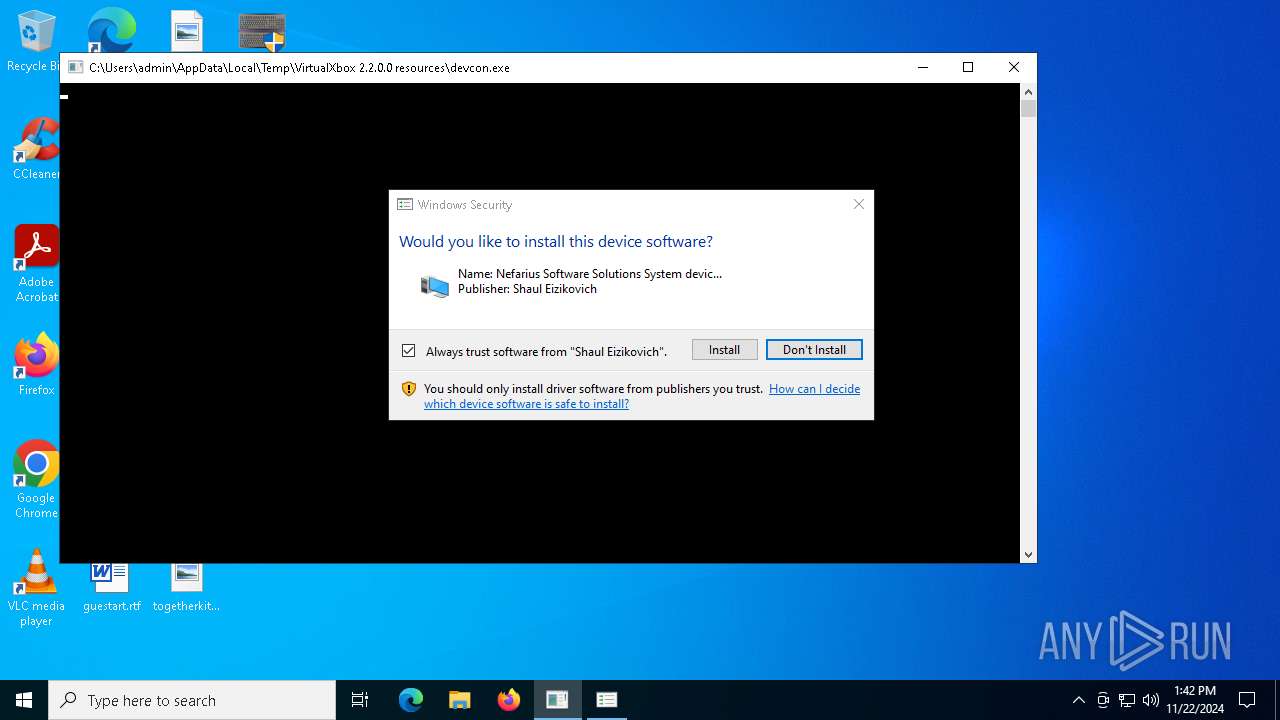
| 6280 | "C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\devcon.exe" install ScpVBus.inf Root\ScpVBus | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\devcon.exe | KeyboardSplitter.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.10240.16399 (th1.150722-1625) Modules
| |||||||||||||||
| 6288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6448 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{cc05fdd0-c885-7643-85f1-464cdced529e}\scpvbus.inf" "9" "4b5cfab93" "00000000000000F0" "WinSta0\Default" "00000000000001D4" "208" "c:\users\admin\appdata\local\temp\virtualxbox 2.2.0.0 resources" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | rundll32.exe C:\WINDOWS\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{b9b4c18e-4e7c-6a42-977b-80d0a757683b} Global\{2d140c59-a01a-4a48-9698-c28b536fdcfd} C:\WINDOWS\System32\DriverStore\Temp\{cbf9f1ba-a0fb-0841-8610-8afc2bbb5c29}\scpvbus.inf C:\WINDOWS\System32\DriverStore\Temp\{cbf9f1ba-a0fb-0841-8610-8afc2bbb5c29}\ScpVBus.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6664 | DrvInst.exe "2" "211" "ROOT\SYSTEM\0001" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:c14ce88487555a35:ScpVBus_Device:22.52.24.182:root\scpvbus," "4b5cfab93" "00000000000000F0" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 254
Read events
11 216
Write events
28
Delete events
10
Modification events
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\keyboard |
| Operation: | write | Name: | DisplayName |
Value: Keyboard Upper Filter Driver | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\keyboard |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\keyboard |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\keyboard |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\mouse |
| Operation: | write | Name: | DisplayName |
Value: Mouse Upper Filter Driver | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\mouse |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\mouse |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\mouse |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4d36e96b-e325-11ce-bfc1-08002be10318} |
| Operation: | write | Name: | UpperFilters |
Value: keyboard | |||
| (PID) Process: | (6212) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4d36e96f-e325-11ce-bfc1-08002be10318} |
| Operation: | write | Name: | UpperFilters |
Value: mouse | |||
Executable files
21
Suspicious files
10
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1156 | KeyboardSplitter.exe | C:\Users\admin\Desktop\splitter_log.txt | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 6212 | keyboard_driver.exe | C:\Windows\System32\drivers\keyboard.sys | executable | |
MD5:9D39232310190DC8C0CB7472DB523A1E | SHA256:2CB5EC142CFAC879BCE4A2F9549258DB972AEBBD24F4551B6B748B464EB7DBA9 | |||
| 1156 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\ScpVBus.sys | executable | |
MD5:6011AB0CA3D08527CF2AF246D792548F | SHA256:2C363A38F474ABE214D947F4E8C5D246A65228F4FF1F56C65EC66253A38F04E8 | |||
| 1156 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\scpvbus.cat | cat | |
MD5:F731EB640512970DA863BB207C911AFB | SHA256:E7CD617710F38C80F0E8700780A92C97C5B2DDC42586DE1D8AFBD2E624225629 | |||
| 1156 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\WdfCoinstaller01009.dll | executable | |
MD5:4DA5DA193E0E4F86F6F8FD43EF25329A | SHA256:18487B4FF94EDCCC98ED59D9FCA662D4A1331C5F1E14DF8DB3093256DD9F1C3E | |||
| 6280 | devcon.exe | C:\Users\admin\AppData\Local\Temp\{cc05fdd0-c885-7643-85f1-464cdced529e}\ScpVBus.cat | cat | |
MD5:F731EB640512970DA863BB207C911AFB | SHA256:E7CD617710F38C80F0E8700780A92C97C5B2DDC42586DE1D8AFBD2E624225629 | |||
| 1156 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\devcon.exe | executable | |
MD5:7920632D06BDA4F19F4815232796FD24 | SHA256:F4225D077A71787E8B98ED2E649AAE8AF1AE5C92E82414B59F71C9DD1784E729 | |||
| 6212 | keyboard_driver.exe | C:\Windows\System32\drivers\mouse.sys | executable | |
MD5:CCF564011EEFA7B44D74915D231B8FD7 | SHA256:0F12D47D01864CA5E1EB663A52B3D2C060521E57B68FF99D70E7F01506E400F9 | |||
| 6280 | devcon.exe | C:\Windows\INF\setupapi.dev.log | text | |
MD5:2145BBA4D0CA069799FE19062EDBAB7D | SHA256:2DDA20A500CE5B34D573ABC52EDB7F196DA69C45D8DB7998BCCEA5FFA31ED001 | |||
| 6280 | devcon.exe | C:\Users\admin\AppData\Local\Temp\{cc05fdd0-c885-7643-85f1-464cdced529e}\SETCA02.tmp | executable | |
MD5:4DA5DA193E0E4F86F6F8FD43EF25329A | SHA256:18487B4FF94EDCCC98ED59D9FCA662D4A1331C5F1E14DF8DB3093256DD9F1C3E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
35
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4300 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.161:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4932 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |