| File name: | KeyboardSplitter.exe |
| Full analysis: | https://app.any.run/tasks/14323b62-d4f0-491f-85a4-6605a84c7c5e |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2023, 21:22:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 81E89981CEBF899BD3EE985A88A63D53 |
| SHA1: | 67C2733322E10475A91C9AD4805FE478662A7B0B |
| SHA256: | 36656BC7DF1C724AFECEA974A85533D83D1BCA3675DC541E42CD2592AF00EE77 |
| SSDEEP: | 98304:o1tpy43QTufo7h3XFvfXMWMmyHoeRzCueFrq3bOBqygpCtyawall0XtkPp1DQvQL:o8bhLytkgZqeUJi |
MALICIOUS
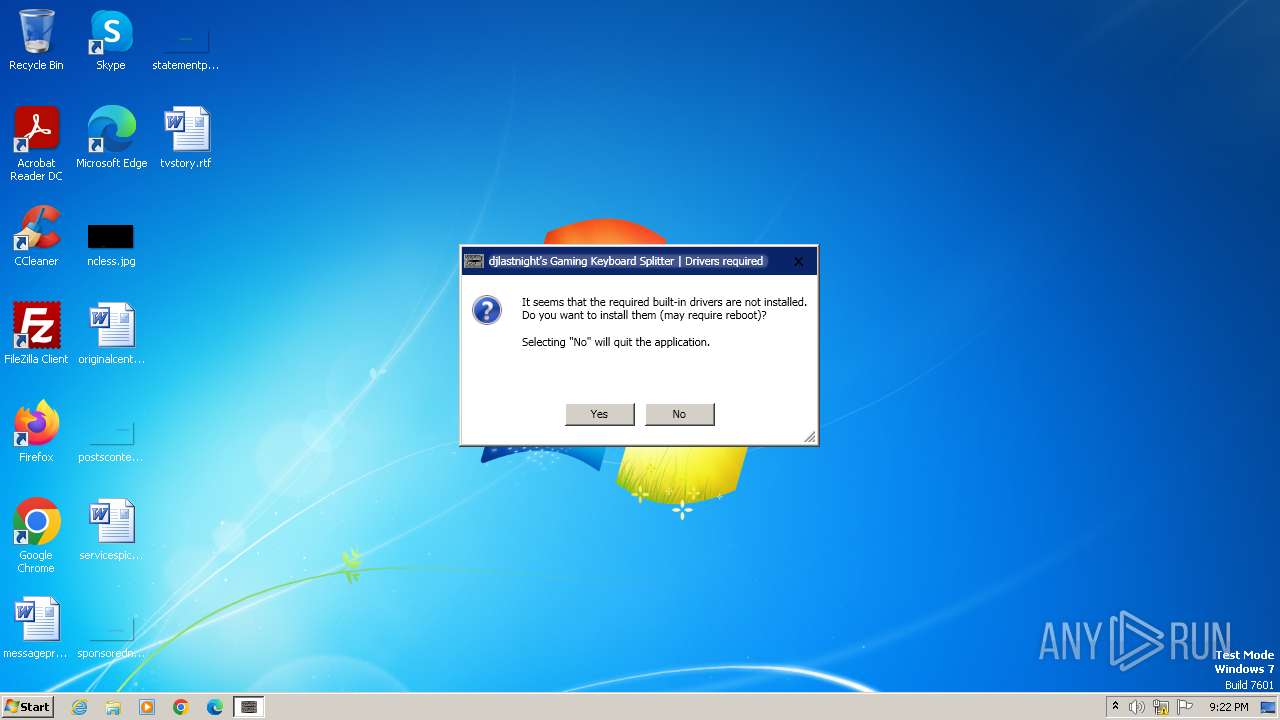
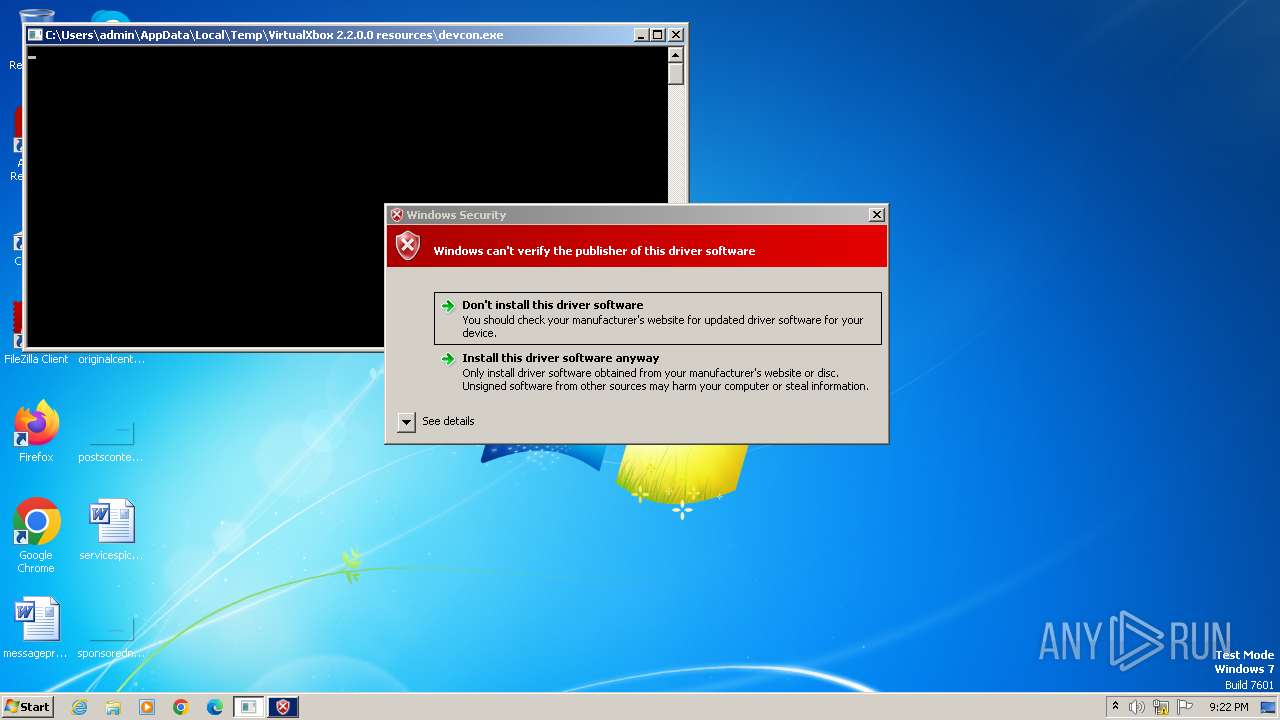
Drops the executable file immediately after the start
- KeyboardSplitter.exe (PID: 2476)
- devcon.exe (PID: 292)
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
- keyboard_driver.exe (PID: 1072)
Creates a writable file in the system directory
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
- keyboard_driver.exe (PID: 1072)
SUSPICIOUS
Reads the Internet Settings
- KeyboardSplitter.exe (PID: 2476)
- sipnotify.exe (PID: 1496)
Checks Windows Trust Settings
- devcon.exe (PID: 292)
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
Reads settings of System Certificates
- devcon.exe (PID: 292)
- sipnotify.exe (PID: 1496)
Reads security settings of Internet Explorer
- devcon.exe (PID: 292)
Process drops legitimate windows executable
- devcon.exe (PID: 292)
- KeyboardSplitter.exe (PID: 2476)
- drvinst.exe (PID: 3160)
Drops a system driver (possible attempt to evade defenses)
- devcon.exe (PID: 292)
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
- keyboard_driver.exe (PID: 1072)
- KeyboardSplitter.exe (PID: 2476)
Creates files in the driver directory
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
- keyboard_driver.exe (PID: 1072)
Executes as Windows Service
- VSSVC.exe (PID: 1028)
The system shut down or reboot
- KeyboardSplitter.exe (PID: 2476)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1692)
- sipnotify.exe (PID: 1496)
INFO
Checks supported languages
- KeyboardSplitter.exe (PID: 2476)
- keyboard_driver.exe (PID: 1072)
- devcon.exe (PID: 292)
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
- IMEKLMG.EXE (PID: 1076)
- IMEKLMG.EXE (PID: 1708)
- wmpnscfg.exe (PID: 2252)
- wmpnscfg.exe (PID: 2344)
- wmpnscfg.exe (PID: 2460)
Reads the computer name
- KeyboardSplitter.exe (PID: 2476)
- devcon.exe (PID: 292)
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
- IMEKLMG.EXE (PID: 1076)
- IMEKLMG.EXE (PID: 1708)
- wmpnscfg.exe (PID: 2252)
- wmpnscfg.exe (PID: 2344)
- wmpnscfg.exe (PID: 2460)
Reads the machine GUID from the registry
- KeyboardSplitter.exe (PID: 2476)
- devcon.exe (PID: 292)
- drvinst.exe (PID: 3160)
- drvinst.exe (PID: 3480)
- wmpnscfg.exe (PID: 2252)
- wmpnscfg.exe (PID: 2344)
- wmpnscfg.exe (PID: 2460)
Create files in a temporary directory
- KeyboardSplitter.exe (PID: 2476)
- devcon.exe (PID: 292)
Manual execution by a user
- IMEKLMG.EXE (PID: 1076)
- IMEKLMG.EXE (PID: 1708)
- wmpnscfg.exe (PID: 2344)
- wmpnscfg.exe (PID: 2252)
- wmpnscfg.exe (PID: 2460)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 1708)
- IMEKLMG.EXE (PID: 1076)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (45.4) |
|---|---|---|
| .exe | | | InstallShield setup (26.7) |
| .exe | | | Win64 Executable (generic) (17.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (4) |
| .exe | | | Win32 Executable (generic) (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:28 14:31:47+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 6309888 |
| InitializedDataSize: | 374784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6067de |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.3.0.0 |
| ProductVersionNumber: | 2.3.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Keyboard Splitter (Creates up to 4 virtual xbox 360 contollers and feeds them using keyboards and/or mice) |
| CompanyName: | djlastnight |
| FileDescription: | Keyboard Splitter |
| FileVersion: | 2.3.0.0 |
| InternalName: | KeyboardSplitter.exe |
| LegalCopyright: | Copyright © 2023 |
| OriginalFileName: | KeyboardSplitter.exe |
| ProductName: | djlastnight's Gaming Keyboard Splitter |
| ProductVersion: | 2.3.0.0 |
| AssemblyVersion: | 2.3.0.0 |
Total processes
105
Monitored processes
16
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
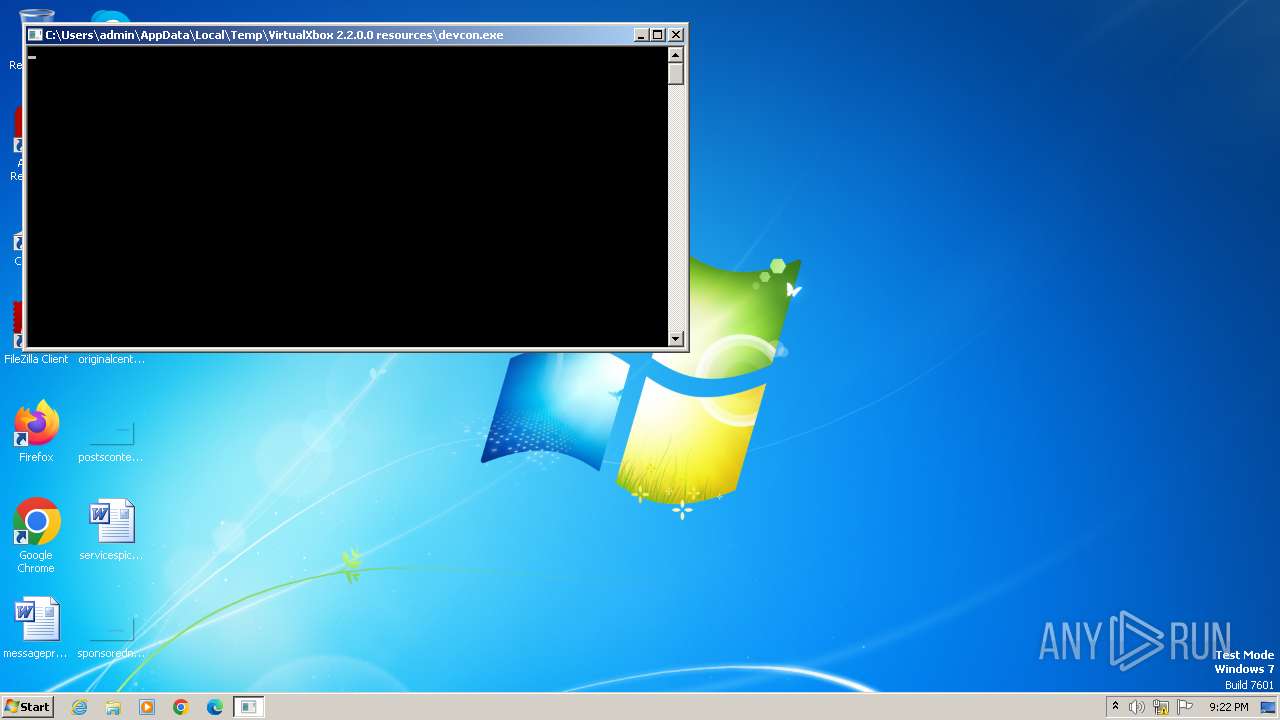
| 292 | "C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\devcon.exe" install ScpVBus.inf Root\ScpVBus | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\devcon.exe | — | KeyboardSplitter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.10586.0 (th2_release.151029-1700) Modules
| |||||||||||||||
| 1028 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\KeyboardSplitter 2.3.0.0 resources\keyboard_driver.exe" /install | C:\Users\admin\AppData\Local\Temp\KeyboardSplitter 2.3.0.0 resources\keyboard_driver.exe | — | KeyboardSplitter.exe | |||||||||||
User: admin Company: Francisco Lopes Integrity Level: HIGH Description: Interception command line installation tool Exit code: 0 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 1076 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 1496 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1692 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1708 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2460 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 250
Read events
13 160
Write events
77
Delete events
13
Modification events
| (PID) Process: | (2476) KeyboardSplitter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1072) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E96B-E325-11CE-BFC1-08002BE10318} |
| Operation: | write | Name: | UpperFilters |
Value: kbdclass | |||
| (PID) Process: | (1072) keyboard_driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E96F-E325-11CE-BFC1-08002BE10318} |
| Operation: | write | Name: | UpperFilters |
Value: mouclass | |||
| (PID) Process: | (292) devcon.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3160) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3160) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3160) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3160) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (3160) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3160) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
20
Suspicious files
26
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2476 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\djlastnight's Gaming Keyboard Splitter v2.3.0.0\interception.dll | executable | |
MD5:C53B817577411AE5776A1EF0F22D1818 | SHA256:53650570A3841949C85F7CF1BEEA968ED50893E5C8EAE00263247ED78FE9F06F | |||
| 2476 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\splitter_log.txt | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 1072 | keyboard_driver.exe | C:\Windows\system32\drivers\keyboard.sys | executable | |
MD5:08D1211820889F97D8A8796584D38EB9 | SHA256:979F790B75860FC713C159740F00ED4A11E7BC785E417B3442F765FFEC4DDC36 | |||
| 2476 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\djlastnight's Gaming Keyboard Splitter v2.3.0.0\VirtualXboxNative.dll | executable | |
MD5:AC4FF97B7CD229177E710EAA02663063 | SHA256:9E670480ABC2676670840B708CF1E3CC8E101167AE419913AE8DA8A8A7754C17 | |||
| 2476 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\KeyboardSplitter 2.3.0.0 resources\keyboard_driver.exe | executable | |
MD5:0485D7466D93B687FA90E1644B2AACBB | SHA256:41362F9A019E55A63E4EFE5761F703FFDCB06CA185BF2E36092F8E1BF5A264FF | |||
| 2476 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\ScpVBus.sys | executable | |
MD5:E8C68162860C9865CD366163CE74ECC7 | SHA256:558BF1E430631F6DE64763B5B87265CBD6238BF583A4459B67B84EB4EF9A1C04 | |||
| 292 | devcon.exe | C:\Windows\INF\setupapi.app.log | text | |
MD5:2F7F2A9DA878A78313439B160D8226F0 | SHA256:4953C60C19D90870F9BA856F7934F3C4ECA3F83BC88A433DE2731F601AEBB589 | |||
| 2476 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\devcon.exe | executable | |
MD5:B14F9FFBEAAAB08167E6223CAC933B22 | SHA256:21DCF559210ECD2ED8DD8DF704A9248D52E9EABE33059F448E0E044B0153CE73 | |||
| 2476 | KeyboardSplitter.exe | C:\Users\admin\AppData\Local\Temp\VirtualXbox 2.2.0.0 resources\ScpVBus.inf | binary | |
MD5:D0A8B29B7BFD6AD6B024BEA51AE96BFA | SHA256:0470B305E9C9E98A016F80A72181BAA9F350CCAC0455A7B7870CAA2EDF595205 | |||
| 292 | devcon.exe | C:\Users\admin\AppData\Local\Temp\{25a5d65c-dc86-1093-3727-d96f32076c1b}\WdfCoInstaller01009.dll | executable | |
MD5:A9970042BE512C7981B36E689C5F3F9F | SHA256:7A6BF1F950684381205C717A51AF2D9C81B203CB1F3DB0006A4602E2DF675C77 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1496 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133458529732960000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1496 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
2528 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
drvinst.exe | WdfCoInstaller: [11/30/2023 21:22.30.893] DIF_INSTALLDEVICE: Pre-Processing
|
drvinst.exe | WdfCoInstaller: [11/30/2023 21:22.30.908] ReadComponents: WdfSection for Driver Service ScpVBus using KMDF lib version Major 0x1, minor 0x9
|
drvinst.exe | WdfCoInstaller: [11/30/2023 21:22.33.987] DIF_INSTALLDEVICE: Post-Processing
|