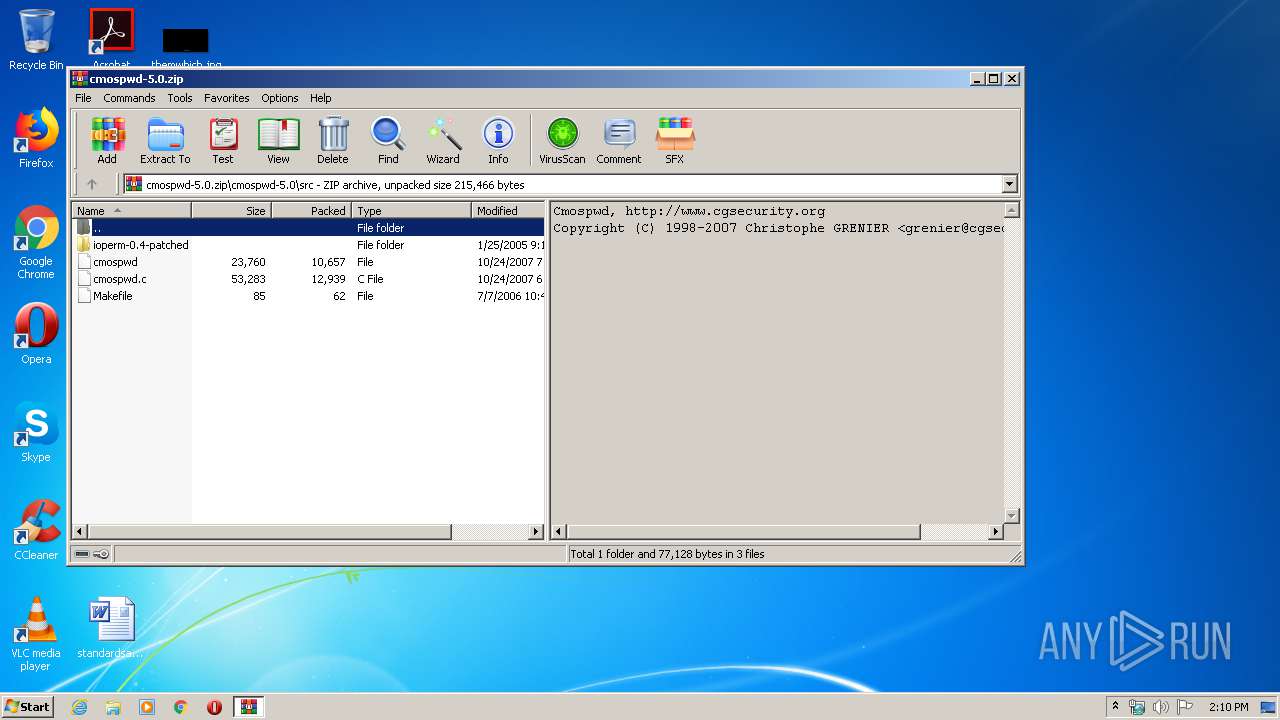
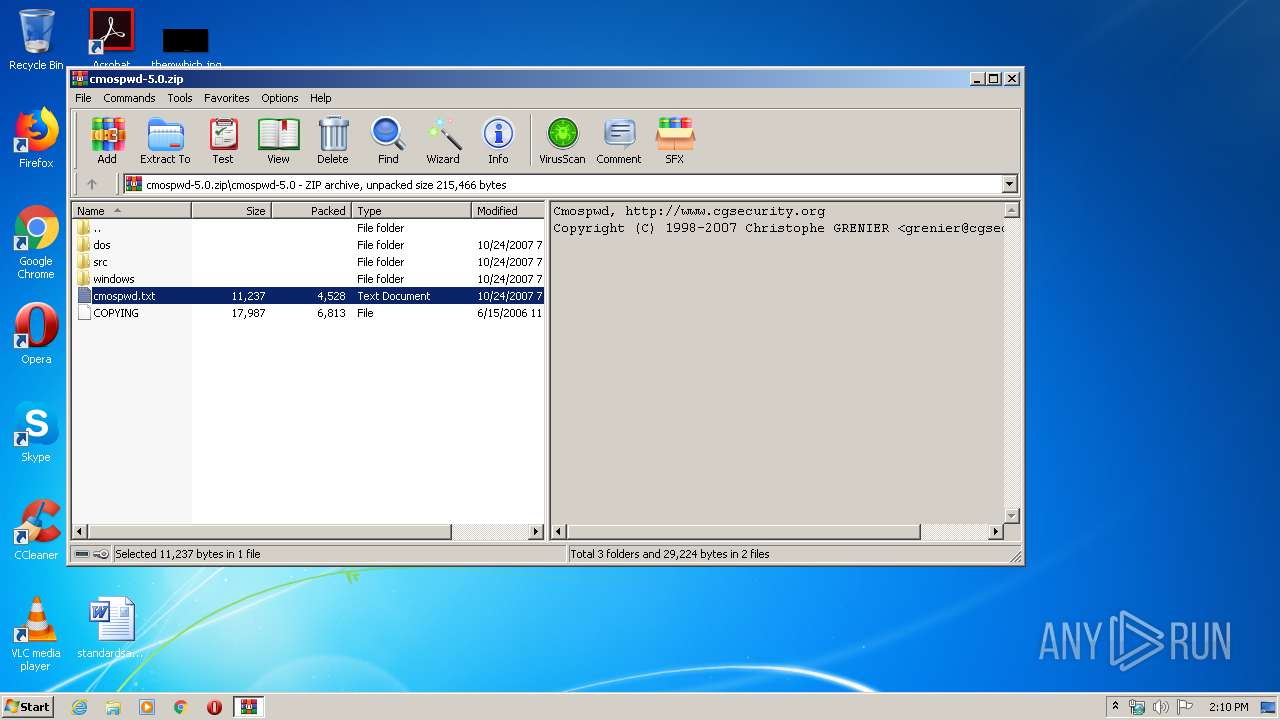
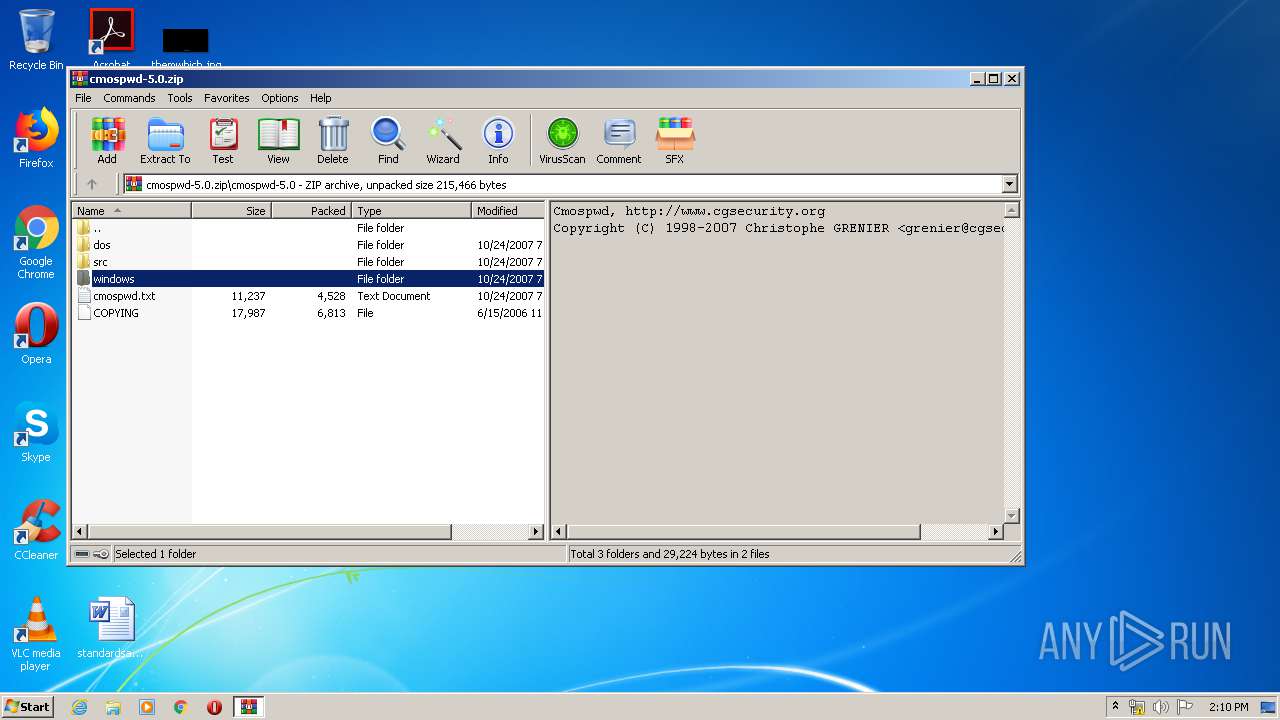
| File name: | cmospwd-5.0.zip |
| Full analysis: | https://app.any.run/tasks/0f6e1fae-26e5-4c1d-9445-0dac1ad48b14 |
| Verdict: | No threats detected |
| Analysis date: | April 11, 2020, 13:09:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | C01A306646E375F1B8D8C7BE75C41D5F |
| SHA1: | 45EEF3F27D709AAC8054E3C24D23D2A2B48018D5 |
| SHA256: | 365AA166DA68F2A982B06E6D69FF32A04034FC08D9500A943942E7E0DD953127 |
| SSDEEP: | 3072:nIfGZSZBH6lNi2jt+DtCGv4J2DImPumVr/:fAZqNiOJdmBr |
MALICIOUS
Application was dropped or rewritten from another process
- cmospwd_win.exe (PID: 3804)
- ioperm.exe (PID: 4004)
- ioperm.exe (PID: 3476)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2812)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2007:10:24 08:07:17 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
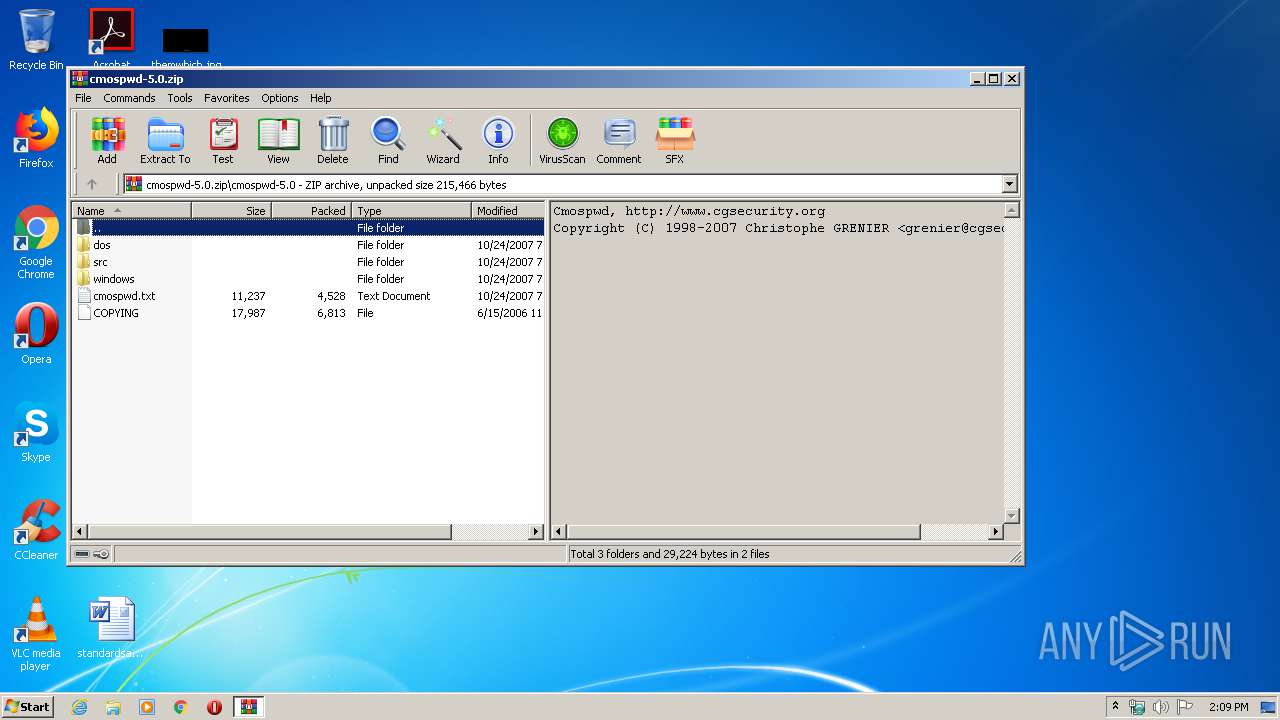
| ZipFileName: | cmospwd-5.0/ |
Total processes
43
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
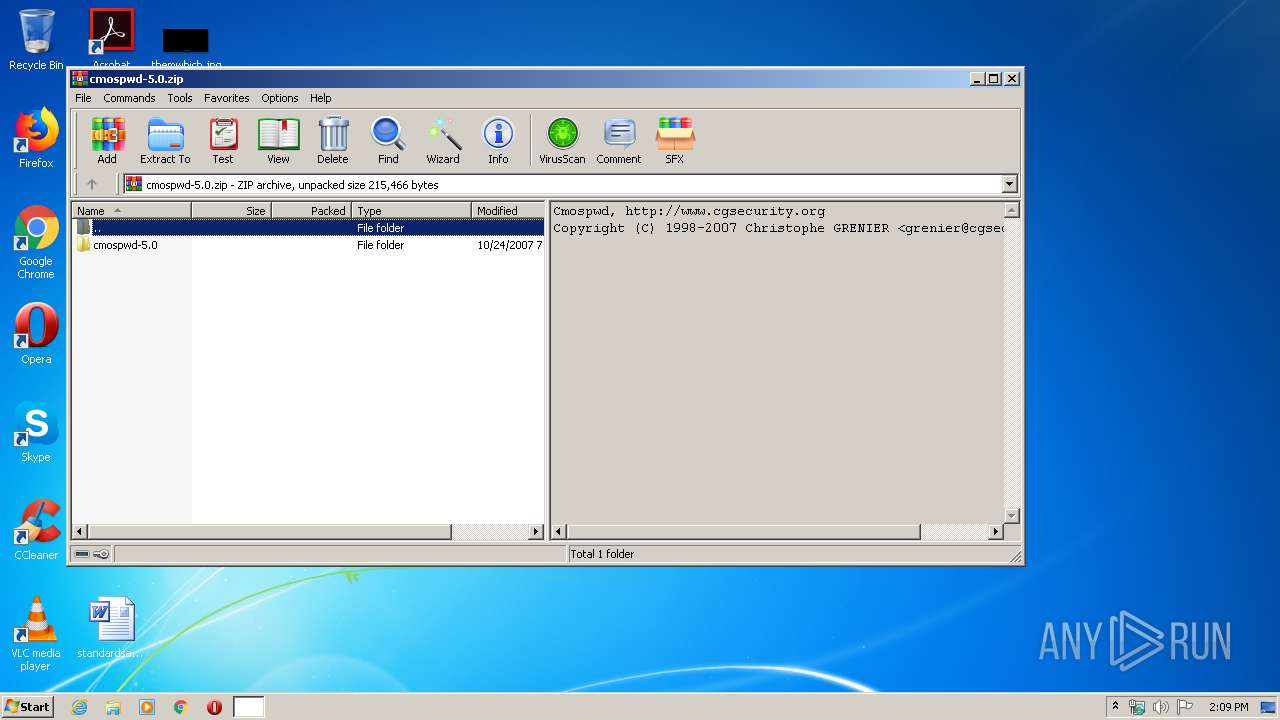
| 2812 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\cmospwd-5.0.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2872 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2812.43943\cmospwd.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
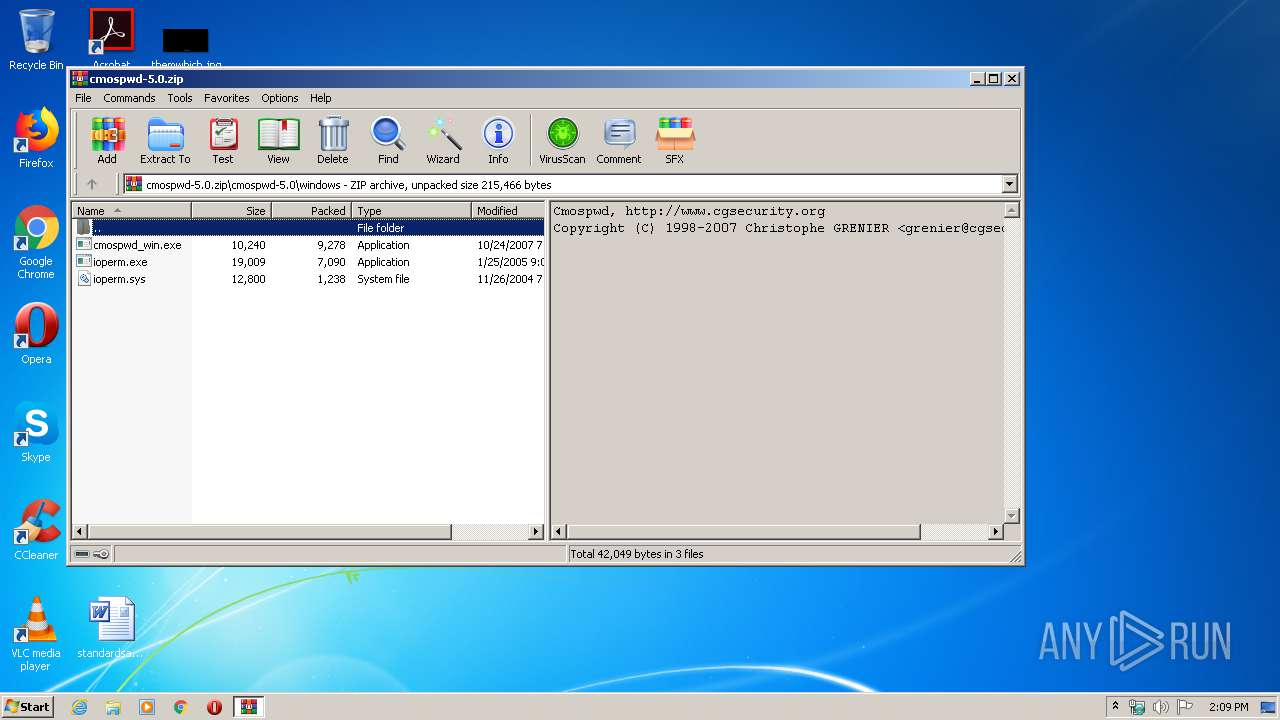
| 3476 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.42404\cmospwd-5.0\windows\ioperm.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.42404\cmospwd-5.0\windows\ioperm.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 3804 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\windows\cmospwd_win.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\windows\cmospwd_win.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3840 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2812.46403\cmospwd.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4004 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.42148\cmospwd-5.0\windows\ioperm.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.42148\cmospwd-5.0\windows\ioperm.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
485
Read events
468
Write events
17
Delete events
0
Modification events
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\cmospwd-5.0.zip | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2812) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
15
Suspicious files
0
Text files
26
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
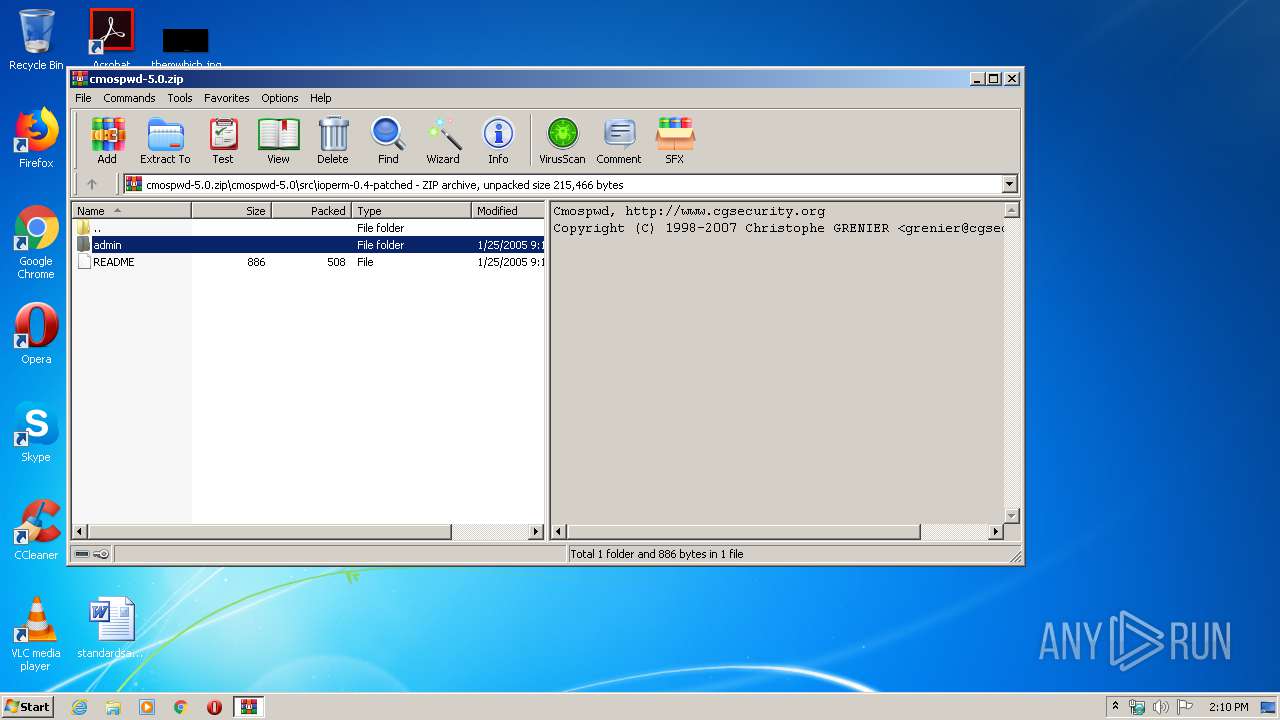
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\src\ioperm-0.4-patched\README | text | |
MD5:96B0880521FA35490A66F5CCCC16237F | SHA256:AE46D3E942CE5B33EC938DFF6D50F3AA51061E547EC43B7F22002C96B5BF6EDD | |||
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\src\ioperm-0.4-patched\admin\uninstall.c | text | |
MD5:56791BC92BA3C589F58EF482DFA6CDAF | SHA256:722013F3447C2870C5C512858E94725D94FA2D026ACAC52859609EC32DB99435 | |||
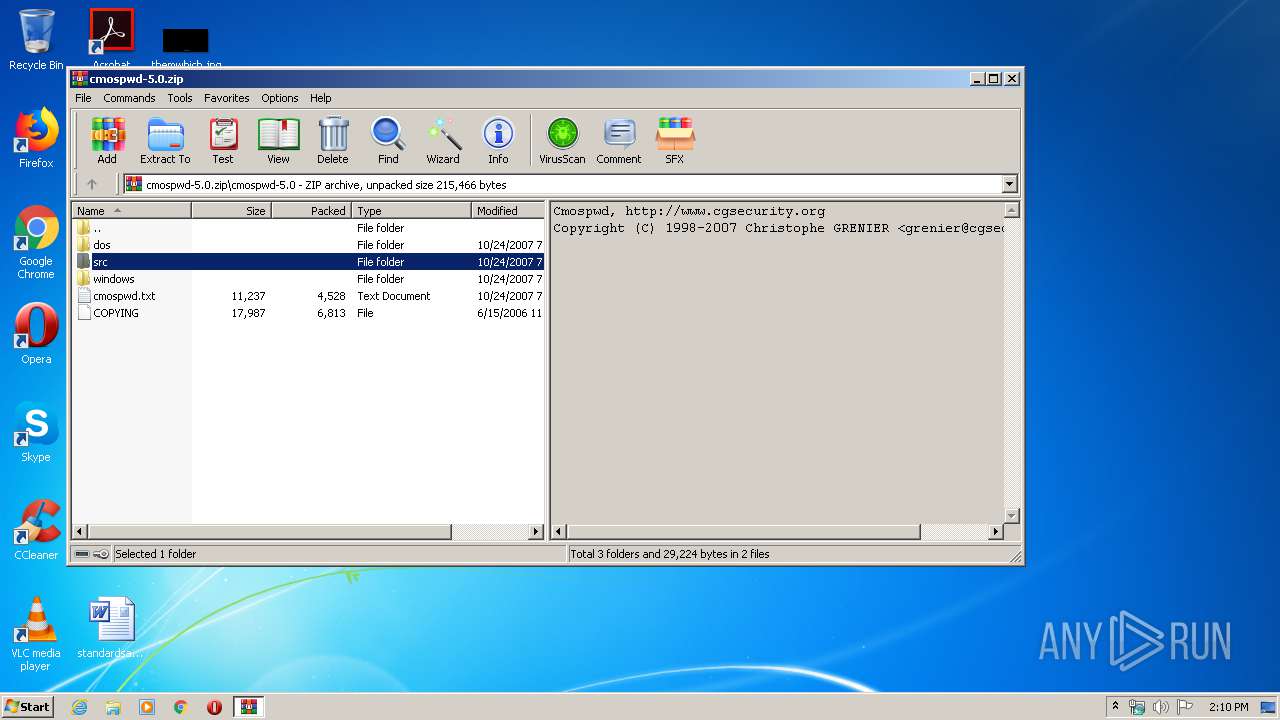
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\src\cmospwd.c | text | |
MD5:33277792A536E707D9641A8F7039816F | SHA256:CA4231162D5A0D29B8E28126318EEE9BE9A1557A933FBD5981397FD64D3A9493 | |||
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\dos\cwsdpmi.exe | executable | |
MD5:A508F105F1126DA8C0AC86EF856F25B2 | SHA256:977ED1DA112B182536D0F0F9ECE9A79E02B2E02CB94A0725758927EC03CA41AD | |||
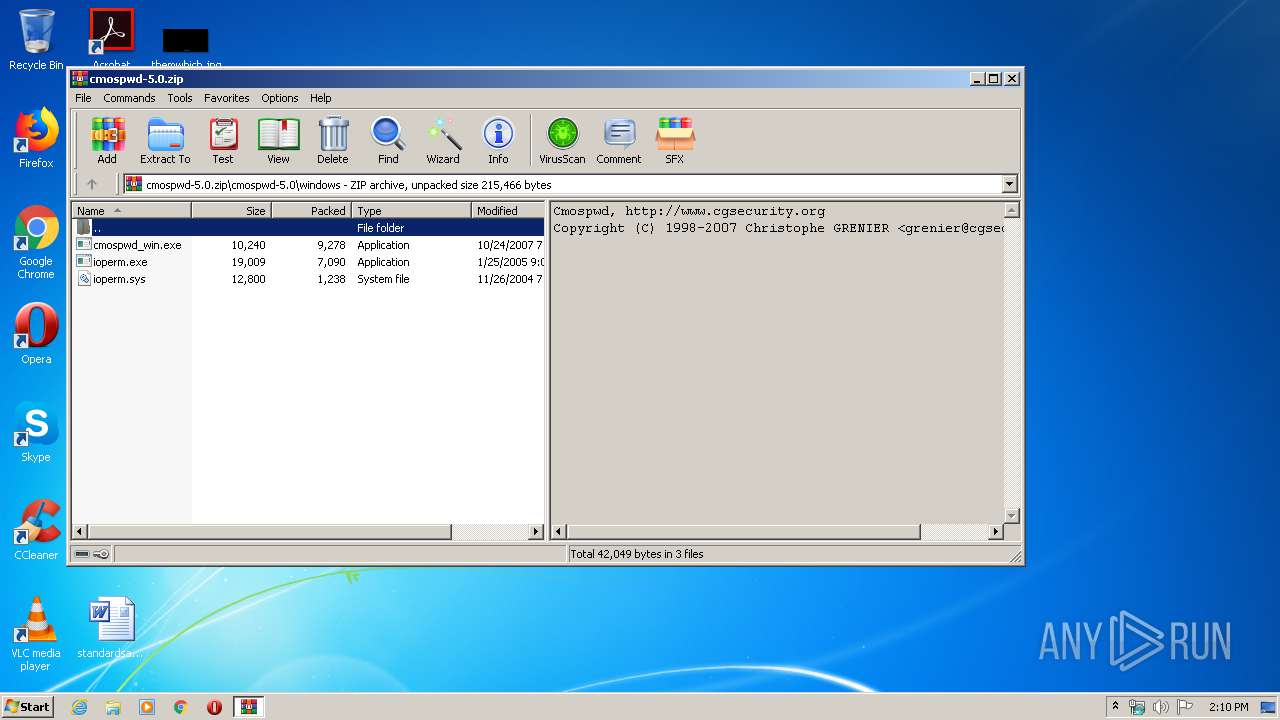
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\windows\ioperm.exe | executable | |
MD5:97A719BDD0F9BDEED48D827107DD3E96 | SHA256:315B5AF8B2051A820BCF096DB2B486E98A48F9BF8FA93BE503600D3193CF29A2 | |||
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\windows\ioperm.sys | executable | |
MD5:7092F08AE018D1EF082C2C31ED80E4EB | SHA256:0F1D13283E4E0A5640BBA99AAB01A637FE04A6721AFB50659FB15A40D029034E | |||
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\windows\cmospwd_win.exe | executable | |
MD5:A2295C92AAF55F5CC03CED3566542F30 | SHA256:11E2F27EA8885188128E285C08DA5D9AB1B707E2051B8434ED3E8B1FBCBAC087 | |||
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.42148\cmospwd-5.0\windows\cmospwd_win.exe | executable | |
MD5:A2295C92AAF55F5CC03CED3566542F30 | SHA256:11E2F27EA8885188128E285C08DA5D9AB1B707E2051B8434ED3E8B1FBCBAC087 | |||
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\src\ioperm-0.4-patched\admin\ioperm.c | text | |
MD5:7DFADB32C8237BA6D3DE82F38C44DFEA | SHA256:3C461C596A591A25F52C8CD64712A714BBEA2EE2ED0733F4597AC16C0AA72B9F | |||
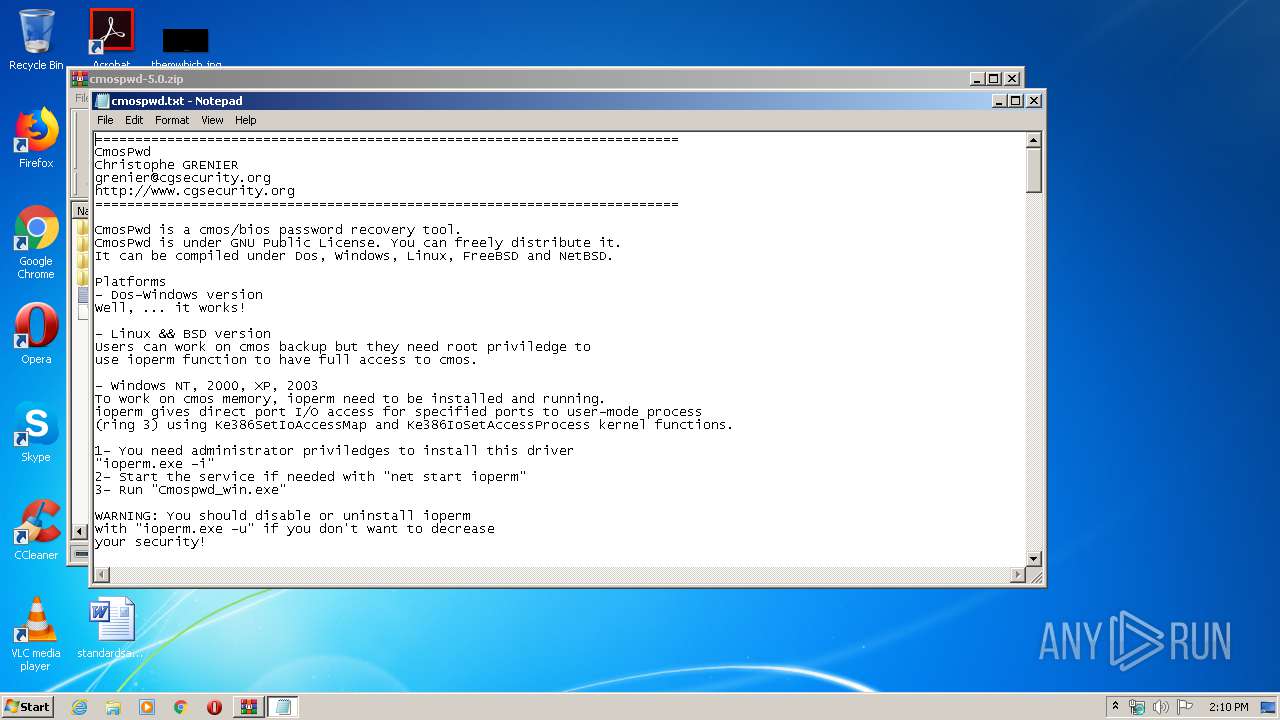
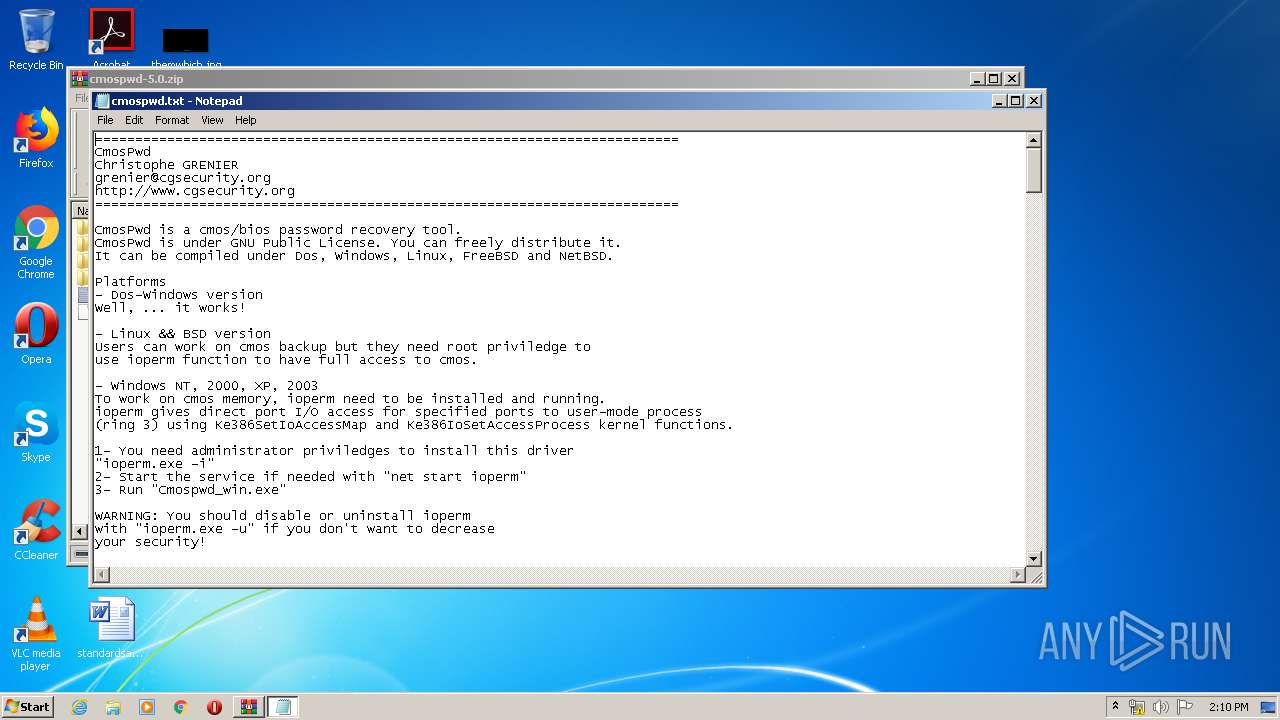
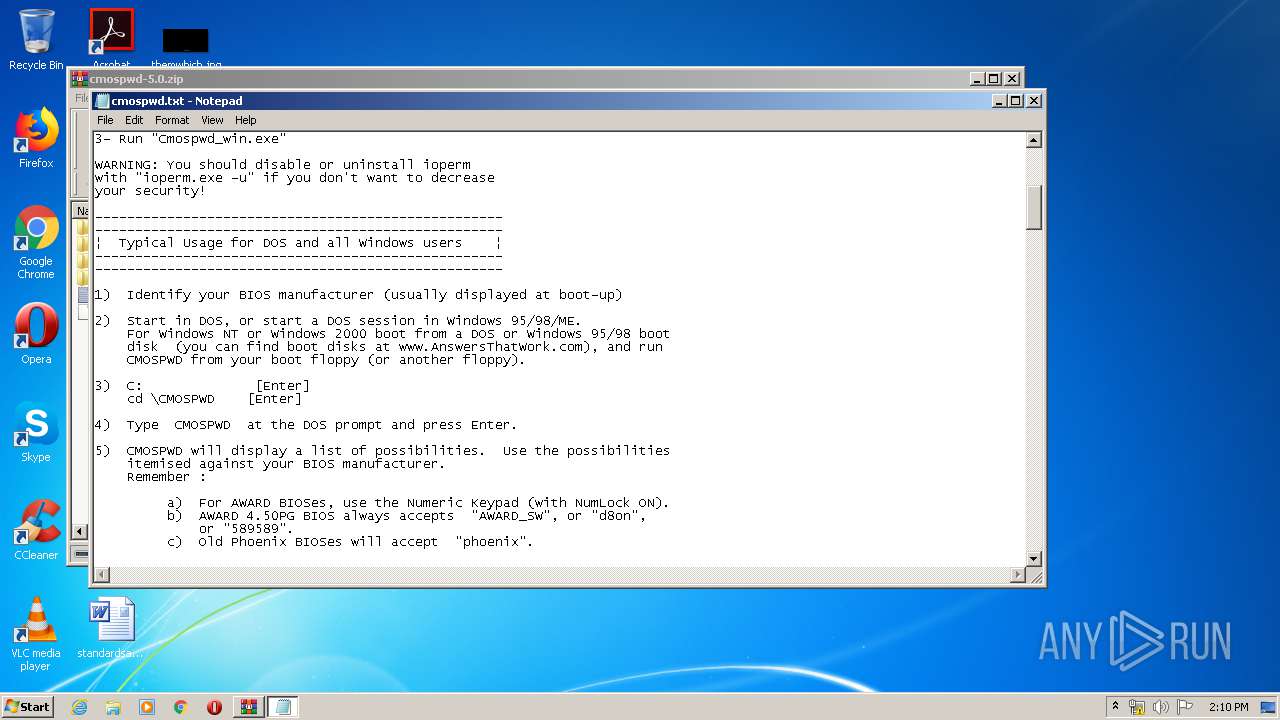
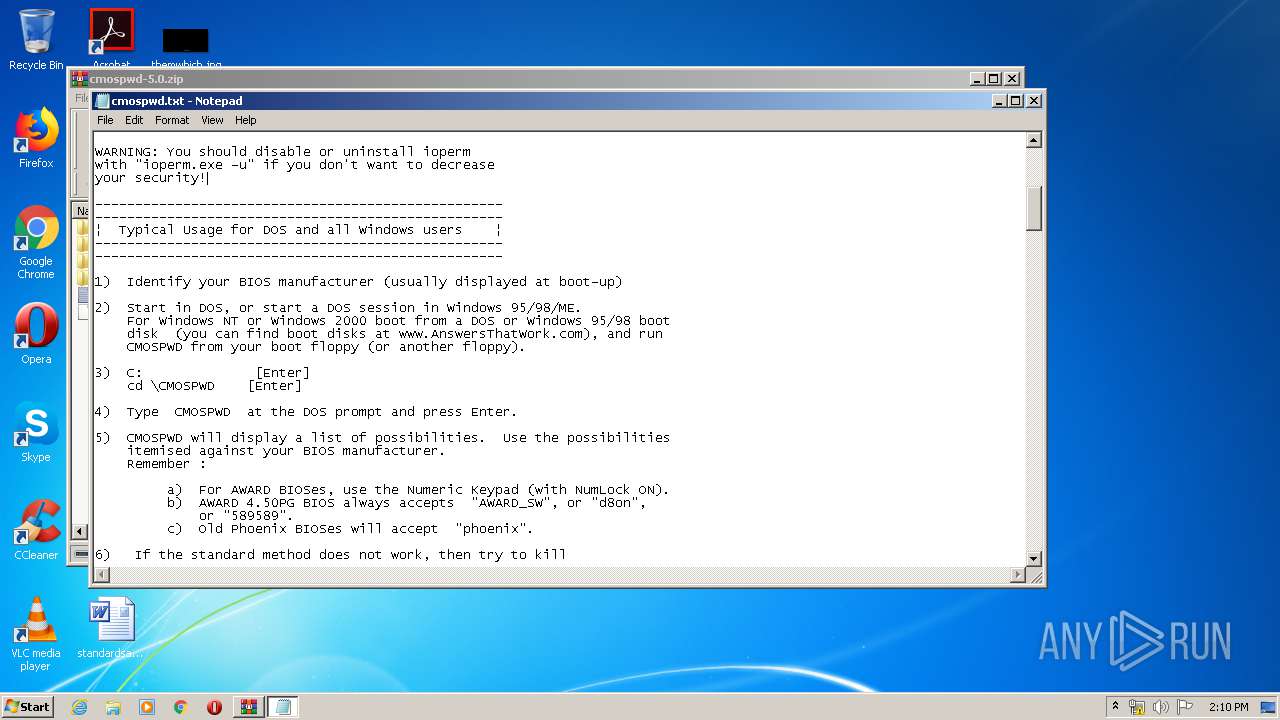
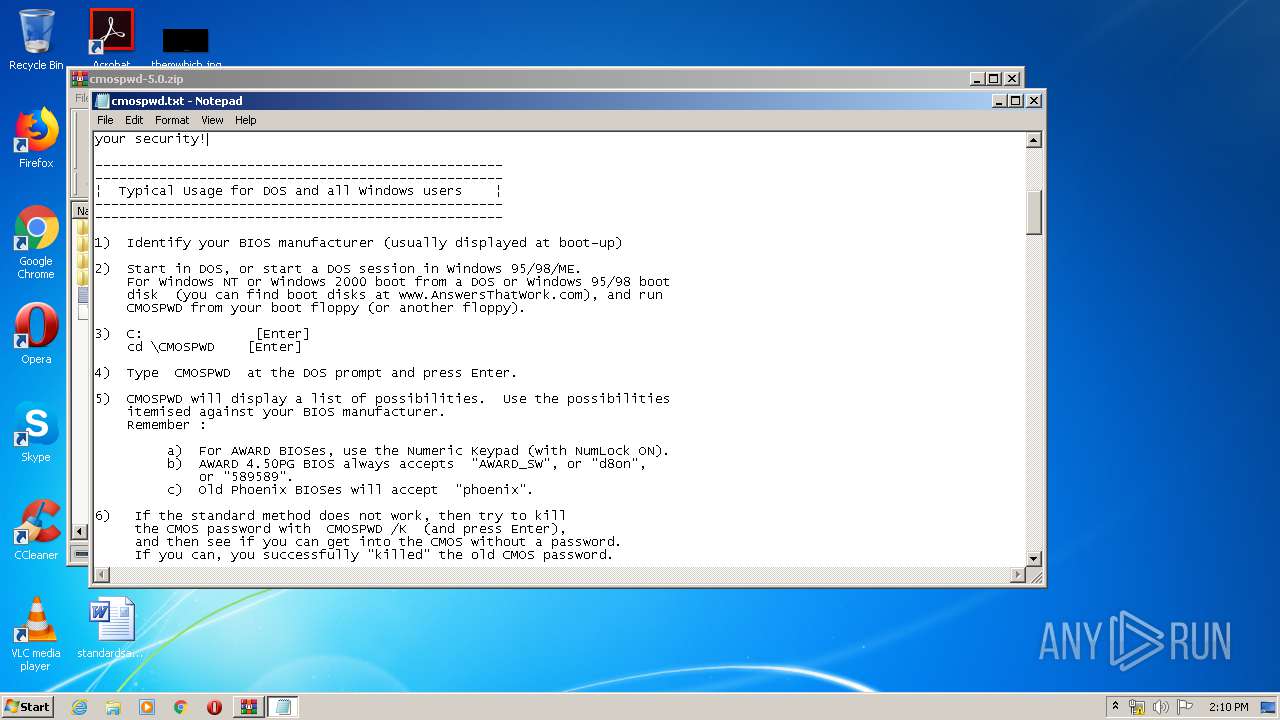
| 2812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2812.41784\cmospwd-5.0\cmospwd.txt | text | |
MD5:5D5CEB32C98F97B91C8BDAC05ED8935A | SHA256:AB067CBE0ADF33A24D4808B6E7FC015A213833FB624092A5EEC8F180CCC6910B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report