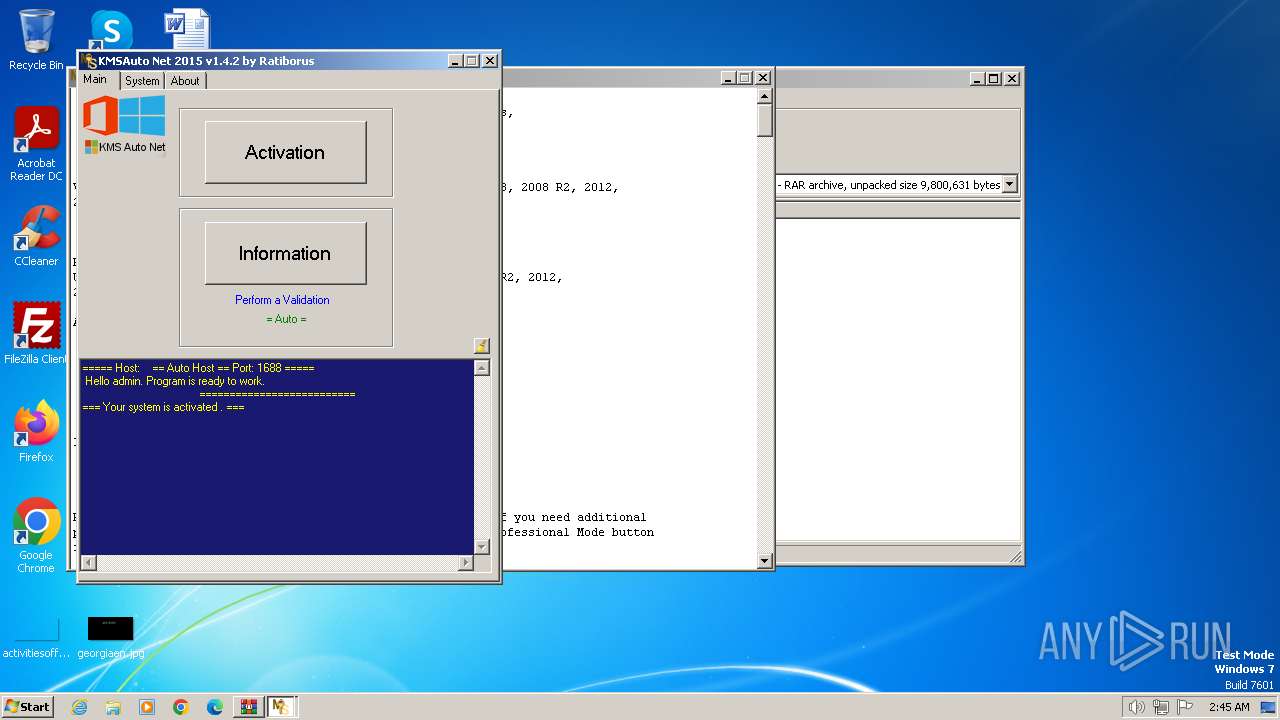
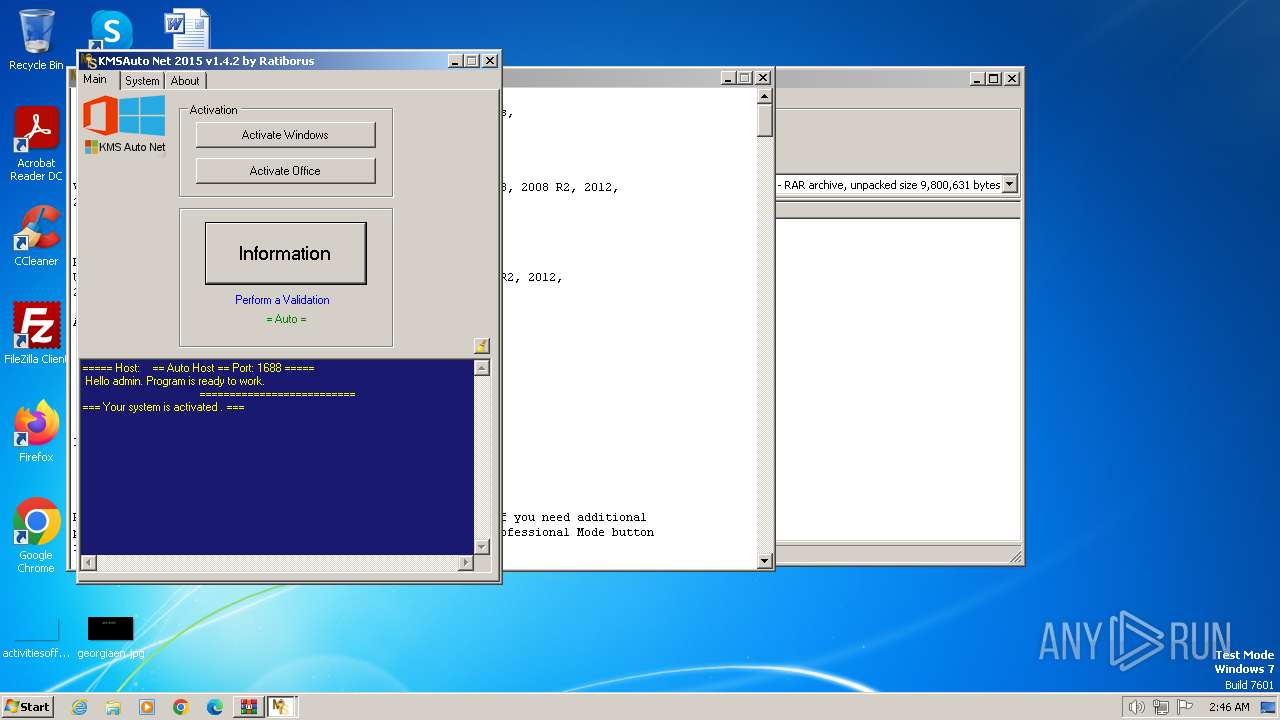
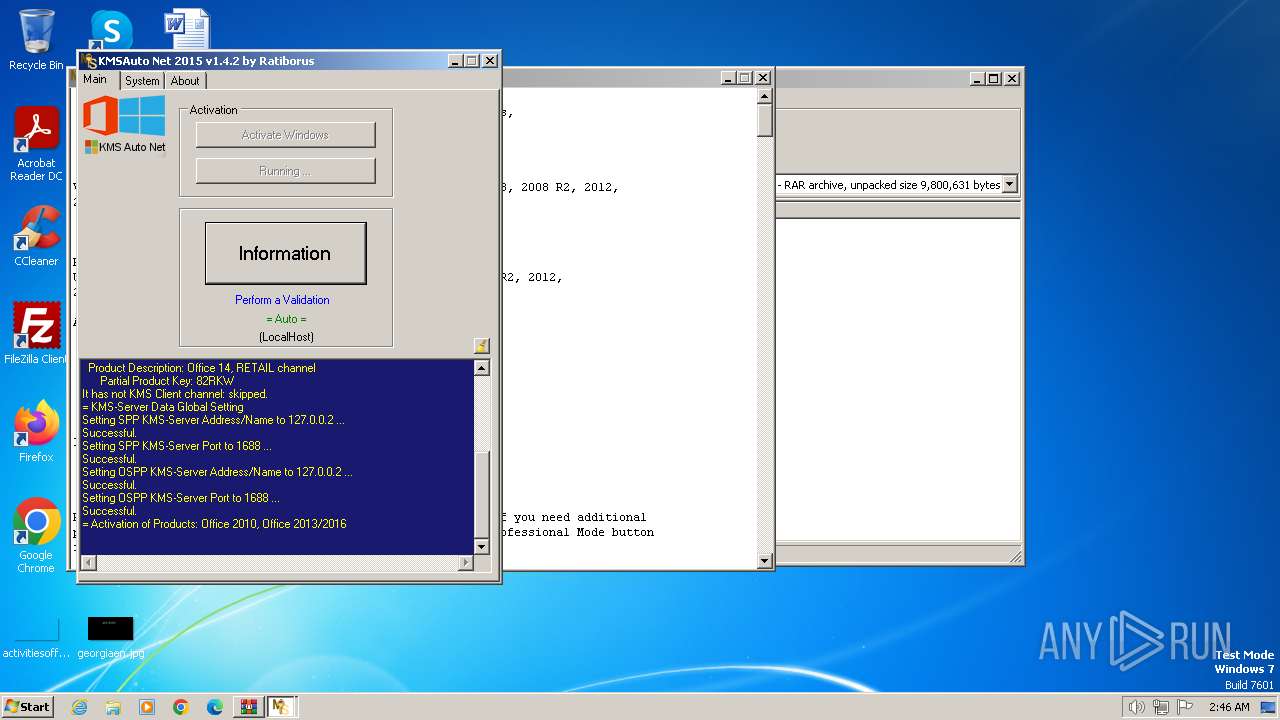
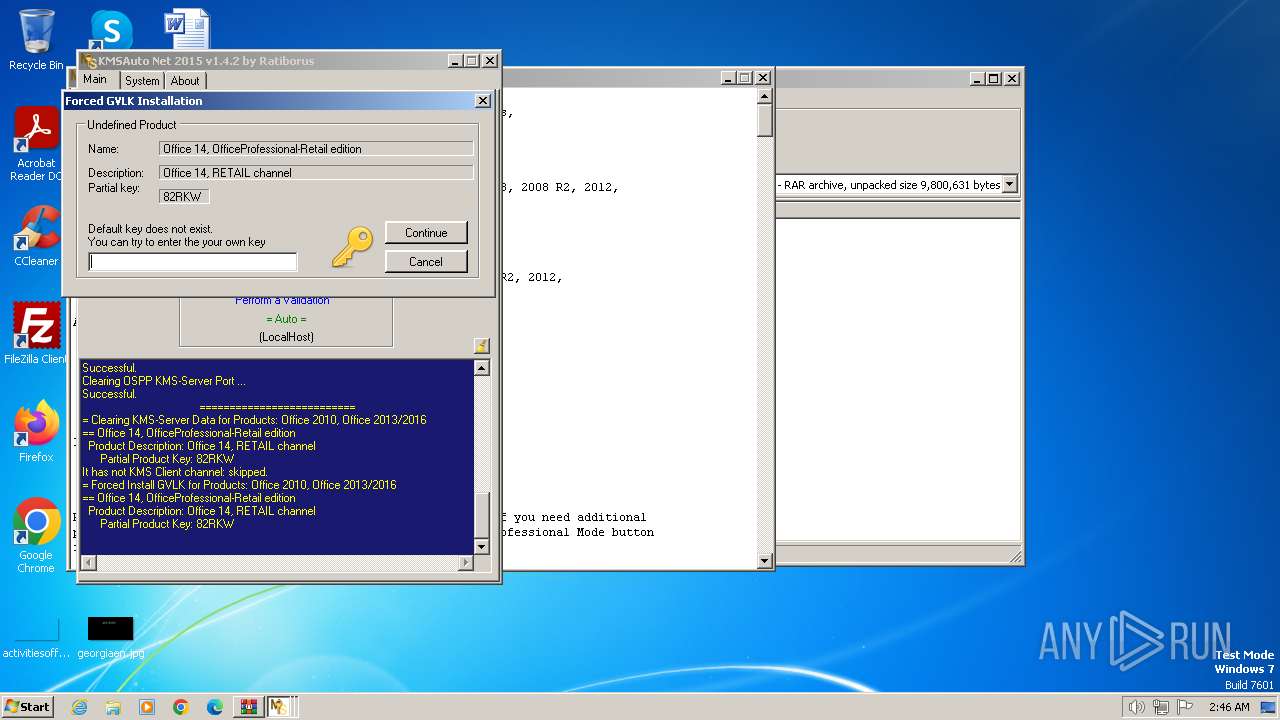
| File name: | KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201.rar |
| Full analysis: | https://app.any.run/tasks/3a97f230-5e4c-4ba5-be5a-7d12c948c463 |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2024, 02:44:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C617B18AA6CEE2693F2EBA7917B103B8 |
| SHA1: | B8F3BB64C2935764A5DA9548B5F2F47AB4D01930 |
| SHA256: | 3641B4B2A5A664BE066AEC4DF2554BD9EA7FF3A95B7F21076C6399EDEF64B542 |
| SSDEEP: | 98304:5odQKiYBhlIEusQAx/ugL9EEnY2sqVWyxdqDh9CecGpqQuPU55YON6n4ZnwPQDb5:Jx5cqUohv |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3956)
- KMSAuto Net.exe (PID: 1656)
- wzt.dat (PID: 2020)
- bin.dat (PID: 3272)
- AESDecoder.exe (PID: 3760)
- bin_x86.dat (PID: 2028)
- wzt.dat (PID: 2432)
- bin.dat (PID: 568)
- AESDecoder.exe (PID: 3984)
- bin_x86.dat (PID: 2128)
- wzt.dat (PID: 2912)
- bin.dat (PID: 2624)
- AESDecoder.exe (PID: 2776)
- bin_x86.dat (PID: 3676)
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 2112)
- drvinst.exe (PID: 3040)
Creates a writable file in the system directory
- drvinst.exe (PID: 2112)
- drvinst.exe (PID: 3040)
Starts NET.EXE for service management
- net.exe (PID: 1288)
- net.exe (PID: 2204)
- KMSAuto Net.exe (PID: 1656)
- net.exe (PID: 2728)
- net.exe (PID: 2096)
Changes the autorun value in the registry
- drvinst.exe (PID: 3040)
- devcon.exe (PID: 3796)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3956)
- devcon.exe (PID: 2176)
- TunMirror.exe (PID: 2652)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 1656)
Executable content was dropped or overwritten
- KMSAuto Net.exe (PID: 1656)
- wzt.dat (PID: 2020)
- bin.dat (PID: 3272)
- AESDecoder.exe (PID: 3760)
- bin_x86.dat (PID: 2028)
- wzt.dat (PID: 2432)
- bin.dat (PID: 568)
- AESDecoder.exe (PID: 3984)
- bin_x86.dat (PID: 2128)
- wzt.dat (PID: 2912)
- bin.dat (PID: 2624)
- AESDecoder.exe (PID: 2776)
- bin_x86.dat (PID: 3676)
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 2112)
- drvinst.exe (PID: 3040)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 1656)
- cmd.exe (PID: 2080)
- cmd.exe (PID: 1936)
- cmd.exe (PID: 2776)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 1656)
Starts application with an unusual extension
- cmd.exe (PID: 1608)
- cmd.exe (PID: 2956)
- cmd.exe (PID: 3792)
- cmd.exe (PID: 2832)
- cmd.exe (PID: 3696)
- cmd.exe (PID: 1484)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 2596)
Adds/modifies Windows certificates
- certmgr.exe (PID: 2376)
- certmgr.exe (PID: 1036)
- certmgr.exe (PID: 3516)
- certmgr.exe (PID: 1900)
- certmgr.exe (PID: 3960)
- certmgr.exe (PID: 1492)
- certutil.exe (PID: 3404)
- devcon.exe (PID: 2176)
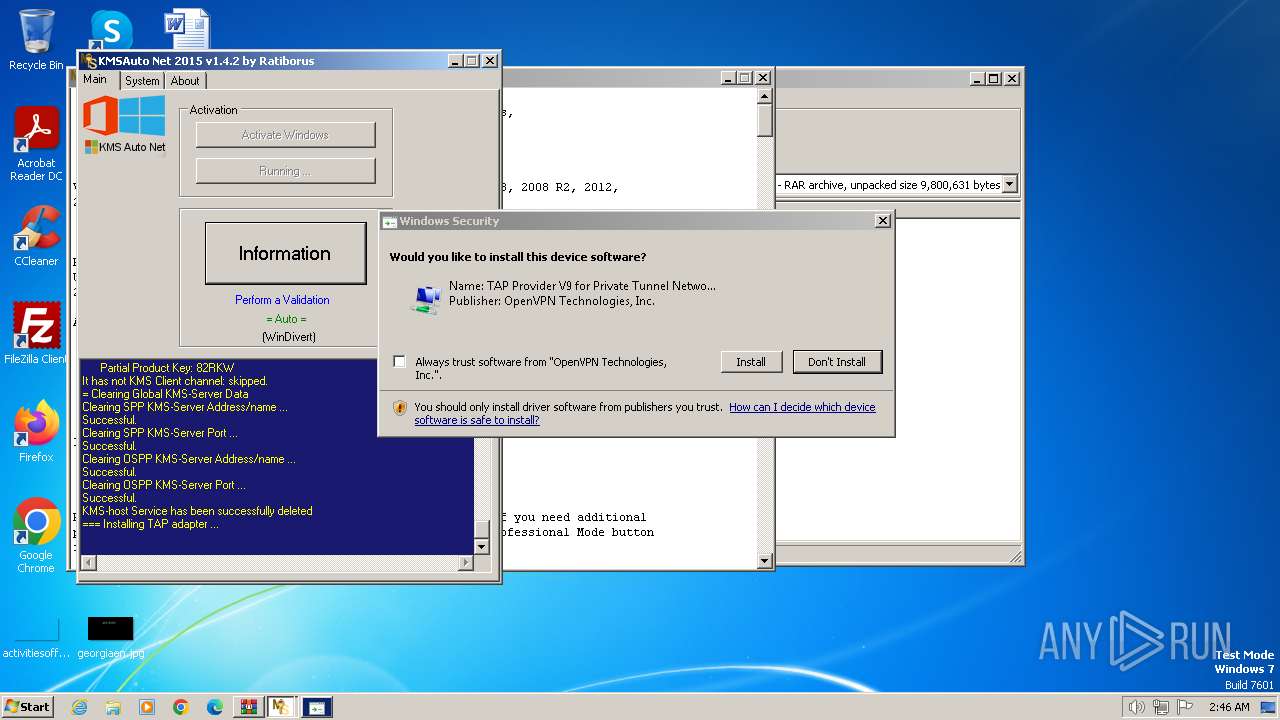
Drops a system driver (possible attempt to evade defenses)
- bin_x86.dat (PID: 2028)
- bin_x86.dat (PID: 2128)
- bin_x86.dat (PID: 3676)
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 2112)
- drvinst.exe (PID: 3040)
Starts SC.EXE for service management
- KMSAuto Net.exe (PID: 1656)
Application launched itself
- cmd.exe (PID: 2080)
- cmd.exe (PID: 1936)
- cmd.exe (PID: 2776)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 1656)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 1656)
Executes as Windows Service
- KMSSS.exe (PID: 3644)
- KMSSS.exe (PID: 3760)
- VSSVC.exe (PID: 2128)
- TunMirror.exe (PID: 3652)
- KMSSS.exe (PID: 796)
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 1656)
Process drops legitimate windows executable
- bin_x86.dat (PID: 2028)
- wzt.dat (PID: 2432)
- bin_x86.dat (PID: 2128)
- wzt.dat (PID: 2912)
- wzt.dat (PID: 2020)
- bin_x86.dat (PID: 3676)
Uses REG/REGEDIT.EXE to modify registry
- KMSAuto Net.exe (PID: 1656)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 3168)
- cmd.exe (PID: 3008)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 1380)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 2032)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3604)
Reads the Internet Settings
- WMIC.exe (PID: 1972)
- WMIC.exe (PID: 2728)
- WMIC.exe (PID: 3600)
- TunMirror.exe (PID: 2652)
- WMIC.exe (PID: 880)
Reads settings of System Certificates
- devcon.exe (PID: 2176)
- rundll32.exe (PID: 1232)
- TunMirror.exe (PID: 2652)
Uses WMIC.EXE
- cmd.exe (PID: 1900)
- cmd.exe (PID: 2388)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 3048)
Checks Windows Trust Settings
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 2112)
- drvinst.exe (PID: 3040)
- TunMirror.exe (PID: 2652)
Creates files in the driver directory
- drvinst.exe (PID: 2112)
- drvinst.exe (PID: 3040)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 3408)
INFO
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 1656)
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 3040)
- drvinst.exe (PID: 2112)
- TunMirror.exe (PID: 2652)
- TunMirror.exe (PID: 3652)
- TunMirror.exe (PID: 1376)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3956)
Checks supported languages
- KMSAuto Net.exe (PID: 1656)
- wzt.dat (PID: 2020)
- certmgr.exe (PID: 2376)
- certmgr.exe (PID: 1036)
- bin.dat (PID: 3272)
- AESDecoder.exe (PID: 3760)
- KMSSS.exe (PID: 3644)
- bin_x86.dat (PID: 2028)
- wzt.dat (PID: 2432)
- certmgr.exe (PID: 3516)
- certmgr.exe (PID: 1900)
- bin.dat (PID: 568)
- AESDecoder.exe (PID: 3984)
- bin_x86.dat (PID: 2128)
- KMSSS.exe (PID: 3760)
- FakeClient.exe (PID: 3808)
- wzt.dat (PID: 2912)
- certmgr.exe (PID: 3960)
- certmgr.exe (PID: 1492)
- bin.dat (PID: 2624)
- AESDecoder.exe (PID: 2776)
- bin_x86.dat (PID: 3676)
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 3040)
- drvinst.exe (PID: 2112)
- TunMirror.exe (PID: 2652)
- TunMirror.exe (PID: 3652)
- wmpnscfg.exe (PID: 4048)
- wmpnscfg.exe (PID: 4044)
- wmpnscfg.exe (PID: 3164)
- KMSSS.exe (PID: 796)
- wmpnscfg.exe (PID: 1168)
- wmpnscfg.exe (PID: 2972)
- TunMirror.exe (PID: 1376)
- devcon.exe (PID: 3796)
- wmpnscfg.exe (PID: 3392)
Reads the computer name
- KMSAuto Net.exe (PID: 1656)
- KMSSS.exe (PID: 3644)
- FakeClient.exe (PID: 3808)
- KMSSS.exe (PID: 3760)
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 3040)
- drvinst.exe (PID: 2112)
- TunMirror.exe (PID: 2652)
- TunMirror.exe (PID: 3652)
- wmpnscfg.exe (PID: 4048)
- wmpnscfg.exe (PID: 3164)
- wmpnscfg.exe (PID: 4044)
- KMSSS.exe (PID: 796)
- wmpnscfg.exe (PID: 1168)
- TunMirror.exe (PID: 1376)
- wmpnscfg.exe (PID: 3392)
- wmpnscfg.exe (PID: 2972)
- devcon.exe (PID: 3796)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 1656)
Reads Environment values
- KMSAuto Net.exe (PID: 1656)
- drvinst.exe (PID: 3040)
Reads product name
- KMSAuto Net.exe (PID: 1656)
Creates files in the program directory
- cmd.exe (PID: 3444)
- KMSAuto Net.exe (PID: 1656)
- wzt.dat (PID: 2020)
- bin.dat (PID: 3272)
- AESDecoder.exe (PID: 3760)
- KMSSS.exe (PID: 3644)
- bin_x86.dat (PID: 2028)
- wzt.dat (PID: 2432)
- bin.dat (PID: 568)
- cmd.exe (PID: 3828)
- AESDecoder.exe (PID: 3984)
- bin_x86.dat (PID: 2128)
- KMSSS.exe (PID: 3760)
- wzt.dat (PID: 2912)
- cmd.exe (PID: 4024)
- bin.dat (PID: 2624)
- AESDecoder.exe (PID: 2776)
- bin_x86.dat (PID: 3676)
- TunMirror.exe (PID: 2652)
- KMSSS.exe (PID: 796)
- TunMirror.exe (PID: 1376)
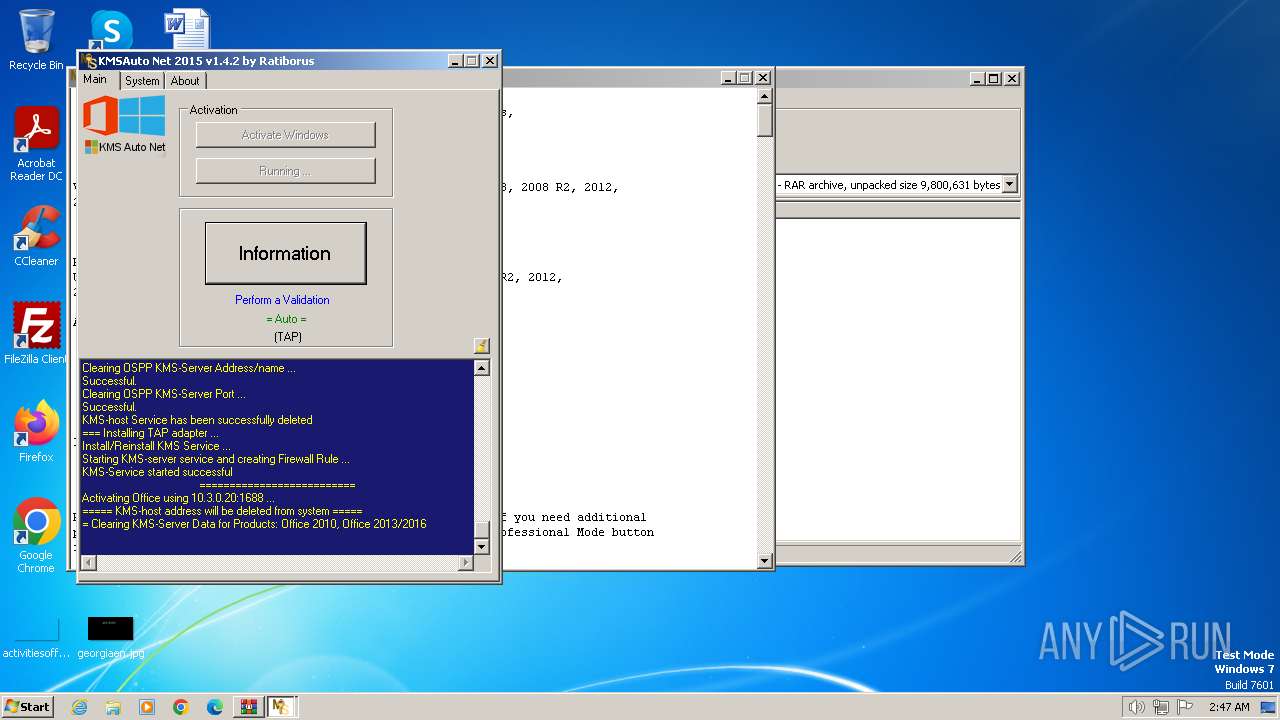
Reads Microsoft Office registry keys
- KMSAuto Net.exe (PID: 1656)
Reads the software policy settings
- devcon.exe (PID: 2176)
- drvinst.exe (PID: 2112)
- rundll32.exe (PID: 1232)
- drvinst.exe (PID: 3040)
- TunMirror.exe (PID: 2652)
Create files in a temporary directory
- devcon.exe (PID: 2176)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1232)
Manual execution by a user
- wmpnscfg.exe (PID: 3164)
- wmpnscfg.exe (PID: 4048)
- wmpnscfg.exe (PID: 4044)
- wmpnscfg.exe (PID: 3392)
- wmpnscfg.exe (PID: 1168)
- wmpnscfg.exe (PID: 2972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
360
Monitored processes
190
Malicious processes
18
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform\0FF1CE15-A989-479D-AF46-F275C6370663" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 452 | C:\Windows\system32\cmd.exe /c netstat -ano | find ":1688 " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 548 | C:\Windows\System32\cmd.exe /D /c FakeClient.exe 100.100.0.10 | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 568 | bin.dat -y -pkmsauto | C:\ProgramData\KMSAuto\bin.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 15.09 beta Modules
| |||||||||||||||
| 680 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55C92734-D682-4D71-983E-D6EC3F16059F" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | "sc.exe" create KMSEmulator binpath= temp.exe type= own start= auto | C:\Windows\System32\sc.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | C:\Windows\System32\cmd.exe /D /c del /F /Q "bin_x86.dat" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 796 | "C:\ProgramData\KMSAuto\bin\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -AI 43200 -RI 43200 KillProcessOnPort -Log -IP | C:\ProgramData\KMSAuto\bin\KMSSS.exe | — | services.exe | |||||||||||
User: SYSTEM Company: MDL Forum, mod by Ratiborus Integrity Level: SYSTEM Description: KMS Server Emulator Service (XP) Exit code: 0 Version: 1.2.1.0 Modules
| |||||||||||||||
| 880 | WMIC Path Win32_NetworkAdapter WHERE ServiceName="ptun0901" get Manufacturer | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | "C:\Windows\System32\cmd.exe" /c rd "C:\ProgramData\KMSAuto\wzt" /S /Q | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
45 336
Read events
43 966
Write events
1 228
Delete events
142
Modification events
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201.rar | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
54
Suspicious files
35
Text files
25
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\KMSAuto Net.exe | executable | |
MD5:311F3BAA9BFA5B2364FEA8B254D15EB9 | SHA256:BEA219F0F08ED083677A0B869E658BA09785F470668EADC659DB2885FA89F3B9 | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\readme\readme_en.txt | text | |
MD5:CC3B6A890378A4543FB955C1CB943106 | SHA256:BA0F59DAACFADF37D1BBE7293DAE505753B0939DDF3444D64D995AED110EB6FA | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\KMSCleaner.exe | executable | |
MD5:13EA767A7BA607744EBEA7409B9F8649 | SHA256:A6E2CDC0E9426D50BD72D866BFC80E0FBA941EFB3AE6D1C564D409F57D1EB117 | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\readme\readme_es.txt | text | |
MD5:669A4A375AF88A440520AD2554ED8D90 | SHA256:A753957192D3E91CA30C2B788B96AE95CD323239BAF4745040C45C3F1BC64024 | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\readme\readme_fr.txt | text | |
MD5:2E51FA6A866F4E60FD00B4873172D5F4 | SHA256:C9BEFA23DD0EA4CA56F4C6CC78DC3078B8AD57E61B586C033BA34FDBFBC1F4A4 | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\readme\readme_ua.txt | text | |
MD5:A0D06F83A66E2C4FED71933450DCBB31 | SHA256:C724416B72DD7D97B851085E947D2A2D2345650D208B3E7FD45E9EA85C1531AF | |||
| 1656 | KMSAuto Net.exe | C:\Users\admin\AppData\Local\MSfree Inc\kmsauto.ini | text | |
MD5:B22721ECC7249380EF3032685ED19A5A | SHA256:2AC517A3388939951E5BC81489A251193C4BCB4620A9968BA0EC8F34594952D8 | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\readme\readme_cn.txt | text | |
MD5:96696900C004588220E720565711EA23 | SHA256:E6B15F6F0E3B2108127B0FE21D52D63159F8414E764740DB6CED08F49CFE556F | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\readme\readme_bg.txt | text | |
MD5:D7CDFA2835E66C336DE3DAEED992FCAC | SHA256:CB91C9E5B54D4311DECE177147BEB50DB0D9E134072A9262EC57EF1D81A2647F | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3956.43285\KMSAuto.Net.2015 (Activador Windows 8, 8.1 y 10 office 2010, 201\readme\readme_vi.txt | text | |
MD5:AC57F63B303ABA3CA0E98FC989C69378 | SHA256:3EB02AE075A08E42837D257DE0589720E5EE7AA22C1966B0A4A16CFB46513A4F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
32
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
FakeClient.exe | WdfCoInstaller: [03/23/2024 02:46.44.013] ReadComponents: WdfSection for Driver Service windivert using KMDF lib version Major 0x1, minor 0x9
|
FakeClient.exe | WdfCoInstaller: [03/23/2024 02:46.44.060] BootApplication: GetStartType error error(87) The parameter is incorrect.
Driver Service name windivert
|
FakeClient.exe | WdfCoInstaller: [03/23/2024 02:46.44.060] BootApplication: could not open service windivert, error error(1060) The specified service does not exist as an installed service.
|