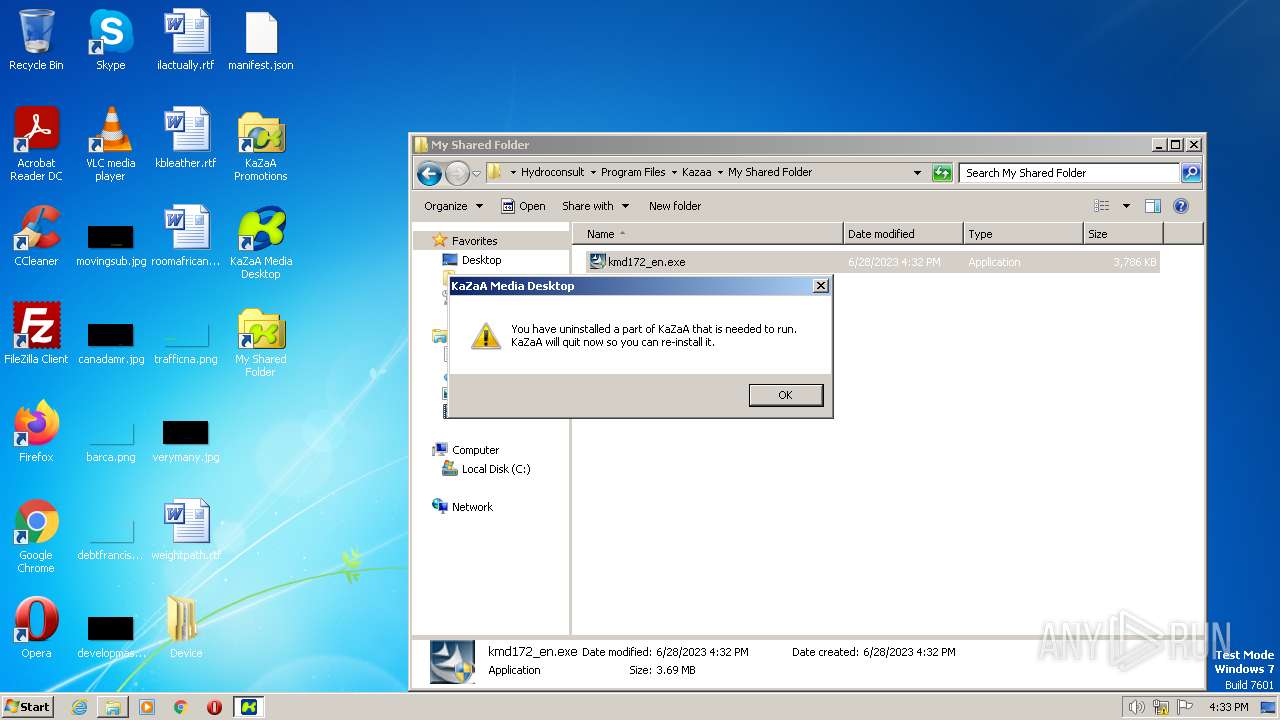
| File name: | MSICALFILE7_2023-06-28_09_02_20.zip |
| Full analysis: | https://app.any.run/tasks/09dad8c1-8d20-43f0-b143-247adb602723 |
| Verdict: | Malicious activity |
| Analysis date: | June 28, 2023, 15:31:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract |
| MD5: | 66F1A88E1202569B7FBC5800816F2D14 |
| SHA1: | A311752E99E6F7274DB13BC21FD0C75CF561BDBB |
| SHA256: | 3634C77138B64D454D3550040BA008901235736AD009174026F51E7954787547 |
| SSDEEP: | 49152:f7LWz6kXJ8Fu6b2qmD8MmOnN8Oxayfb6waW+yK71Ad0sfwfPiQGAtVLFVneFmmFT:fWzRqurD8MbOiV+L80eUP+u+FmmFWa3 |
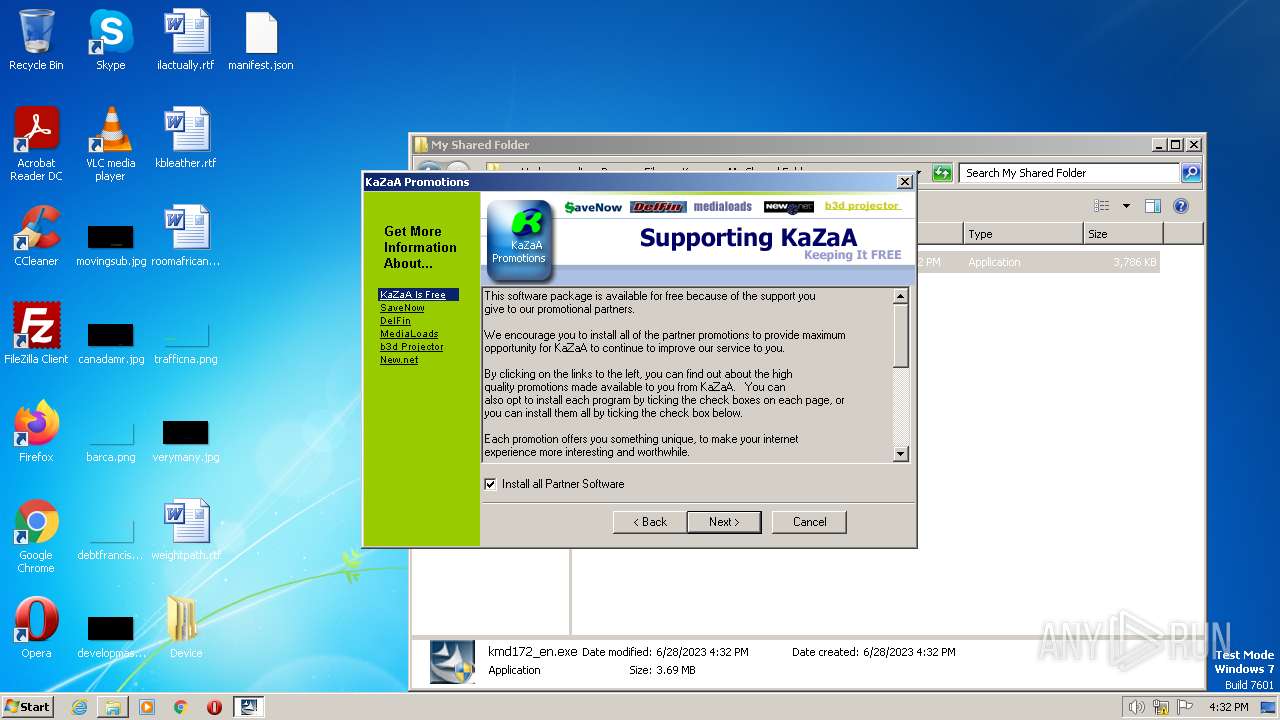
MALICIOUS
Application was dropped or rewritten from another process
- kmd172_en.exe (PID: 2116)
- kmd172_en.exe (PID: 2496)
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 3400)
- IKernel.exe (PID: 3280)
- IKernel.exe (PID: 4048)
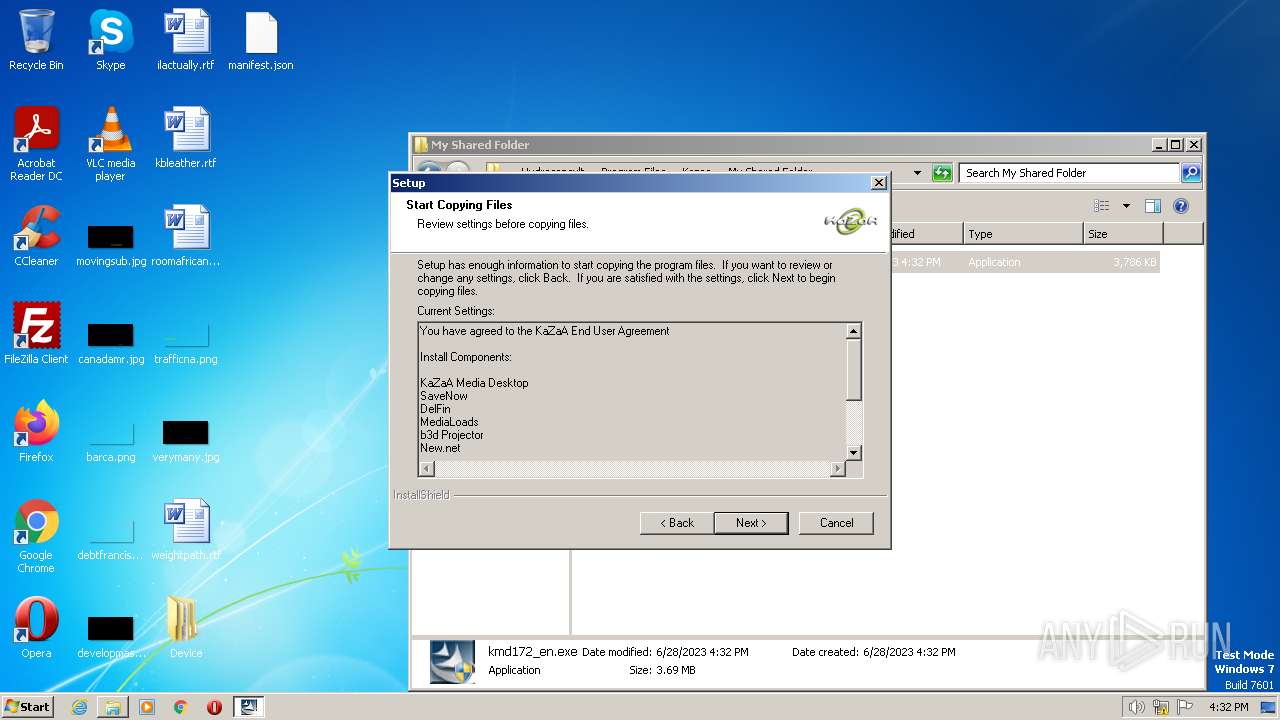
Loads dropped or rewritten executable
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 4048)
SUSPICIOUS
Executable content was dropped or overwritten
- kmd172_en.exe (PID: 2496)
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 4048)
- cd_install_291.exe (PID: 3952)
- SaveNowInst.exe (PID: 2140)
- setup.exe (PID: 4044)
- kazaa_336.exe (PID: 2408)
- DelFinMediaViewer29j.exe (PID: 3040)
Executes as Windows Service
- VSSVC.exe (PID: 2472)
Application launched itself
- IKernel.exe (PID: 4048)
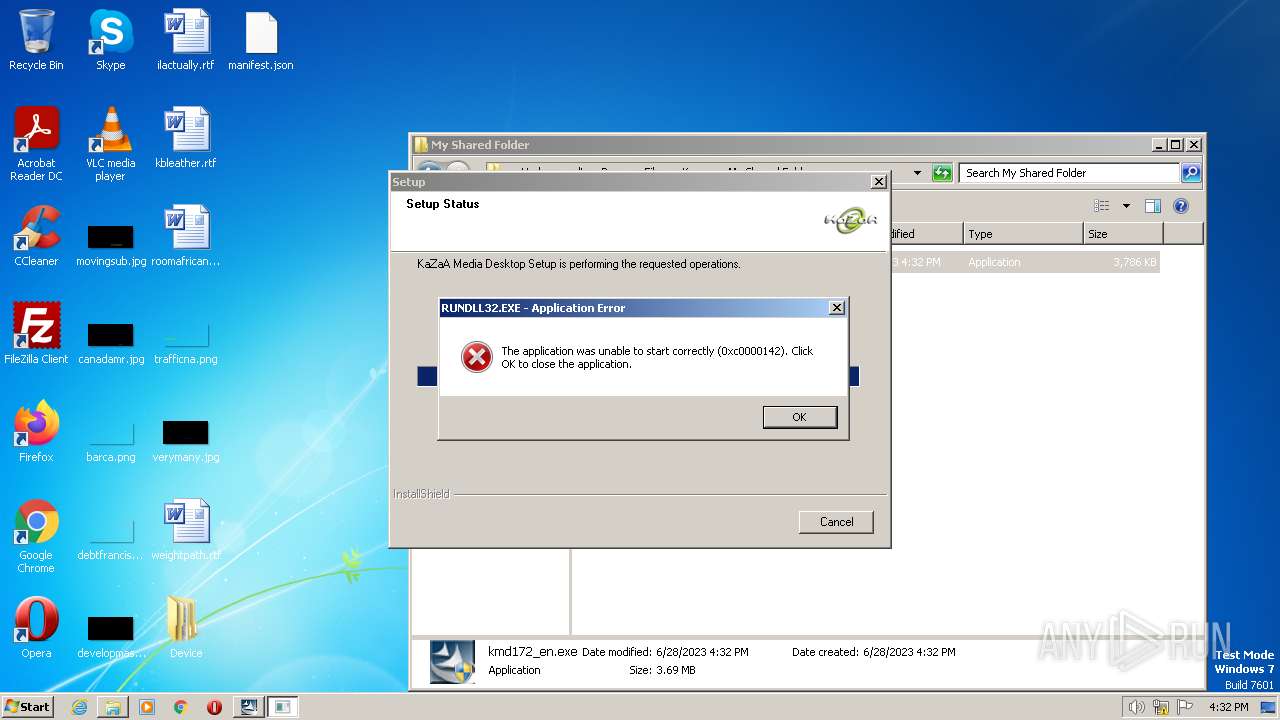
Uses RUNDLL32.EXE to load library
- kazaa_336.exe (PID: 2408)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3076)
The process checks LSA protection
- dllhost.exe (PID: 3712)
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 4048)
Manual execution by a user
- kmd172_en.exe (PID: 2116)
- kmd172_en.exe (PID: 2496)
Create files in a temporary directory
- kmd172_en.exe (PID: 2496)
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 4048)
Creates files in the program directory
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 4048)
Checks supported languages
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 4048)
- IKernel.exe (PID: 3400)
- kmd172_en.exe (PID: 2496)
- IKernel.exe (PID: 3280)
Reads the computer name
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 3400)
- IKernel.exe (PID: 4048)
- IKernel.exe (PID: 3280)
Reads the machine GUID from the registry
- Setup.exe (PID: 3284)
- IKernel.exe (PID: 4048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
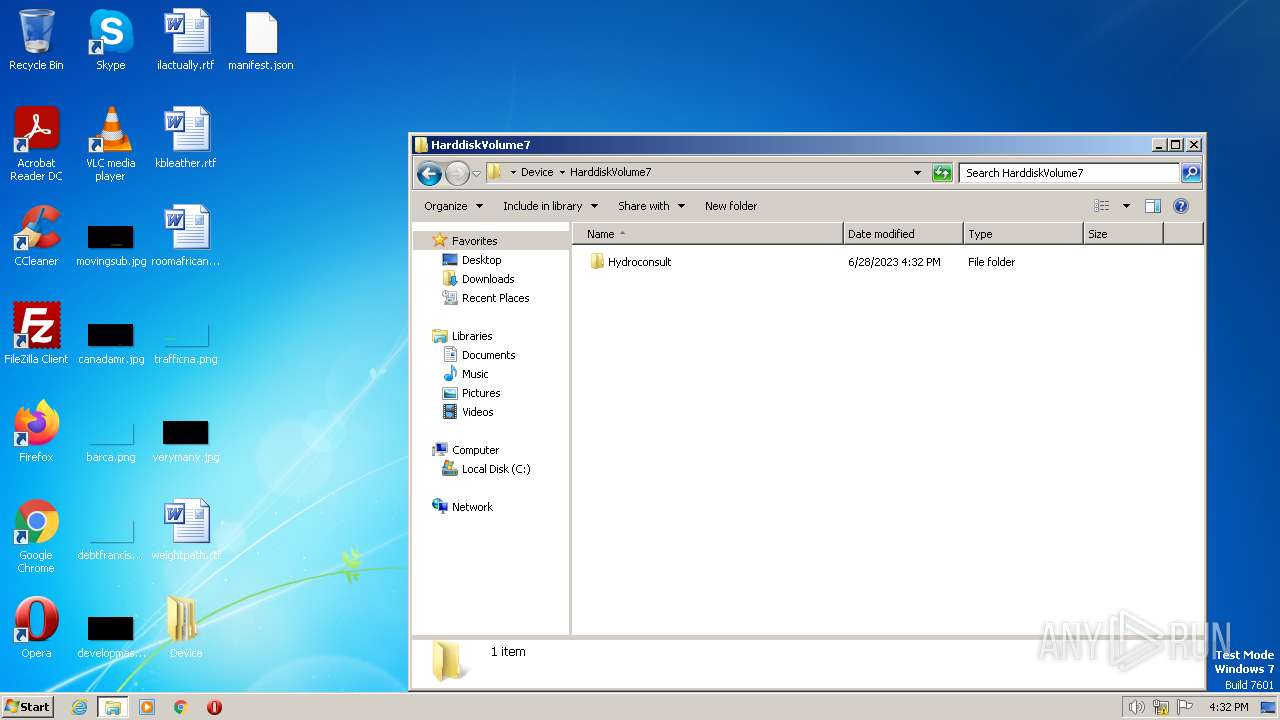
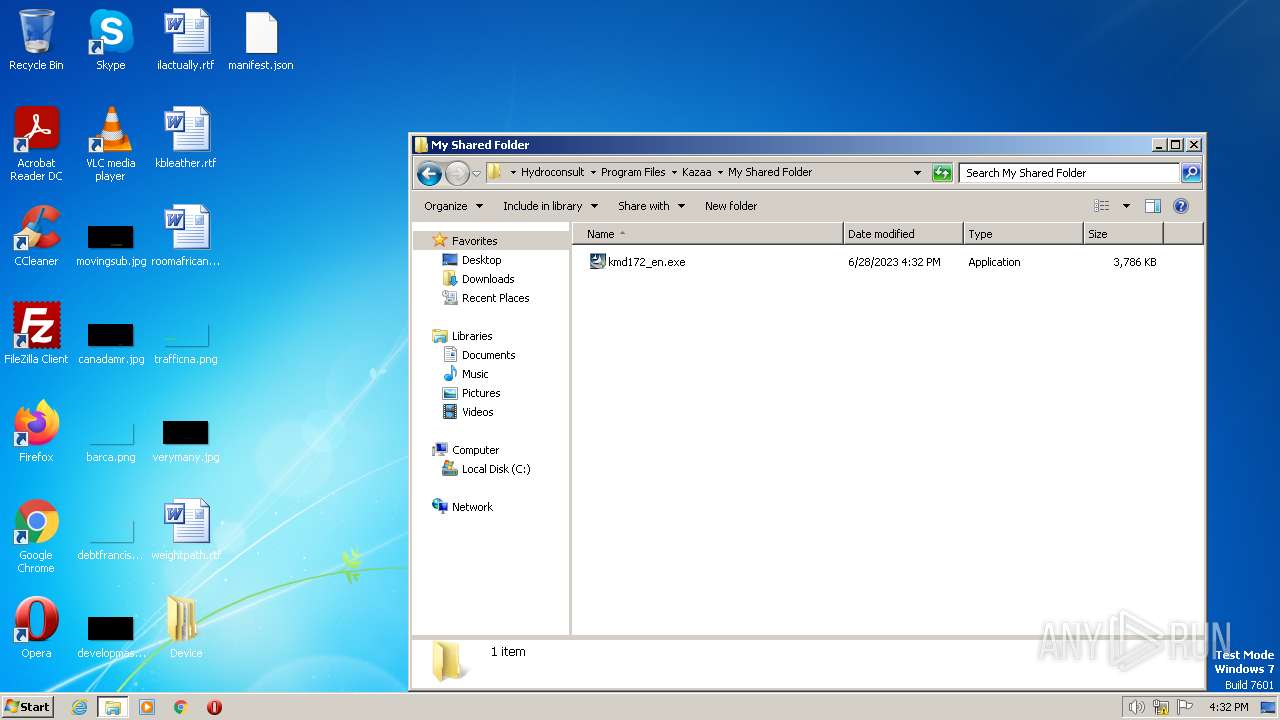
| ZipFileName: | Device/HarddiskVolume7/Hydroconsult/Program Files/Kazaa/My Shared Folder/kmd172_en.exe |
|---|---|
| ZipUncompressedSize: | 3876511 |
| ZipCompressedSize: | 3684379 |
| ZipCRC: | 0xb10d16dd |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0801 |
| ZipRequiredVersion: | 45 |
Total processes
66
Monitored processes
25
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Users\admin\AppData\Local\Temp\QWa03948\cduninst.exe" 253 | C:\Users\admin\AppData\Local\Temp\QWa03948\cduninst.exe | — | cd_install_291.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 1068 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | "C:\Program Files\SaveNow\SaveNow.exe" | C:\Program Files\SaveNow\SaveNow.exe | — | SaveNowInst.exe | |||||||||||
User: admin Company: WhenU.com, Inc. Integrity Level: HIGH Description: SaveNow Exit code: 0 Version: 1, 6, 0, 1 | |||||||||||||||
| 1612 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1824 | C:\Windows\\Temp\Adware\WebInstall.exe /i | C:\Windows\Temp\Adware\WebInstall.exe | — | IKernel.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Web Install Exit code: 0 Version: 1.0.0.41 | |||||||||||||||
| 1908 | rundll32.exe C:\Users\admin\AppData\Local\Temp\QWa03948\cd_clint.dll,ServiceRunDll q_253 | C:\Users\admin\AppData\Local\Temp\QWa03948\RUNDLL32.EXE | — | cduninst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run a DLL as an App Exit code: 3221225794 Version: 4.10.1998 | |||||||||||||||
| 2116 | "C:\Users\admin\Desktop\Device\HarddiskVolume7\Hydroconsult\Program Files\Kazaa\My Shared Folder\kmd172_en.exe" | C:\Users\admin\Desktop\Device\HarddiskVolume7\Hydroconsult\Program Files\Kazaa\My Shared Folder\kmd172_en.exe | — | explorer.exe | |||||||||||
User: admin Company: Sharman Networks Ltd Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 1.7.2 Modules
| |||||||||||||||
| 2140 | C:\Windows\\Temp\Adware\SaveNowInst.exe http://app.whenu.com/Offers?url=ZNST0102 | C:\Windows\Temp\Adware\SaveNowInst.exe | IKernel.exe | ||||||||||||
User: admin Company: WhenU.com, Inc. Integrity Level: HIGH Description: SaveNow Setup Exit code: 0 Version: 1, 6, 0, 2 | |||||||||||||||
| 2408 | C:\Windows\\Temp\Adware\kazaa_336.exe | C:\Windows\Temp\Adware\kazaa_336.exe | IKernel.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 2472 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
Total events
5 058
Read events
4 864
Write events
194
Delete events
0
Modification events
| (PID) Process: | (1068) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000003D77C3133A5D7248BA6D7744BB9A3E16000000000200000000001066000000010000200000004A9CAAC251DD88A0E7E33FFB23F636A225CB7CC4485369C7C9B03862A811D096000000000E8000000002000020000000659B7585C71088AEEB1875008044DFB4B07623A0B20C3E867A78A9695191E29230000000F9C4E47AAD7D214C673E4CDC8385C59DDC5AE0E28396FCF21F9D028C590E79749BDDC16862F8E26B3D4F8E8966EEF17C4000000006EE6EDF8BC2D3544F7C9D682CF07277A50A34FA9DF6D8FB7B39CA5834F62523E20C12EF252EC87A75BE0FA4A5D7BD80B713248892E659363C3419474A1FEA18 | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1068) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
109
Suspicious files
91
Text files
89
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2496 | kmd172_en.exe | C:\Users\admin\AppData\Local\Temp\pft313C.tmp\Disk1\Copy of Setup.exe | executable | |
MD5:1AEB989E361AF85F5099DE3DA25457F4 | SHA256:AB9E0291A763EFC32E84E7117F9A0FBC99B681C96DF0BB27A66433A726667E5C | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\Device\HarddiskVolume7\Hydroconsult\Program Files\Kazaa\My Shared Folder\kmd172_en.exe | executable | |
MD5:57280C91136E4D9213DBEA2DF76BE252 | SHA256:D30AFDECF03C5672803636D3EAC36C3136916051BDE36B2F63DACDEE42C86C2D | |||
| 2496 | kmd172_en.exe | C:\Users\admin\AppData\Local\Temp\pft313C.tmp\pftw1.pkg | compressed | |
MD5:1FB635809DA280DBE19E21243A16811F | SHA256:48BD184C657A53D4F8EEC8B77E0FC7DE934A9C17ABAB09E1E0EC6D3B48D4E179 | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\manifest.json | text | |
MD5:75F6F4985EC0F6A54CFAB94EB9DC49B3 | SHA256:55CA6A74DAAF9C7970BC396CC86EBD0F3CF154433F10167ABDAC1B057F193B14 | |||
| 2496 | kmd172_en.exe | C:\Users\admin\AppData\Local\Temp\ext310C.tmp | text | |
MD5:9EFCC61A0BAA38A6D7C67A05A97C7B87 | SHA256:7CCB3A50CA08C66A220E4DA614CBABA1D05157359EDD174223C788B86D929EDF | |||
| 2496 | kmd172_en.exe | C:\Users\admin\AppData\Local\Temp\pft313C.tmp\Disk1\data1.cab | compressed | |
MD5:78DED6D9928A1809A432D1434ED06BE0 | SHA256:03ADB3317BEAB07601100720E32D037BDA5776EBAB76572347FE7FD84D0F1D4C | |||
| 2496 | kmd172_en.exe | C:\Users\admin\AppData\Local\Temp\pft313C.tmp\Disk1\data2.cab | compressed | |
MD5:07857DB0D0D9D67C5C08E179A11BAE06 | SHA256:7819A91667E4557427424B8DB71A45A17B470B53FDFB9164266C17D3F63CFC0F | |||
| 2496 | kmd172_en.exe | C:\Users\admin\AppData\Local\Temp\pft313C.tmp\Disk1\data1.hdr | binary | |
MD5:5D1FA87C2C4027EE6D72BA82199D027F | SHA256:177DE914B92E520099D23B1F017D791E5A317E2F48579BEEEF3EB70306BC7F88 | |||
| 4048 | IKernel.exe | C:\Program Files\Common Files\InstallShield\Engine\6\Intel 32\corecomp.ini | text | |
MD5:62D5F9827D867EB3E4AB9E6B338348A1 | SHA256:5214789C08EE573E904990DCD29E9E03AAF5CF12E86FAE368005FD8F4E371BD5 | |||
| 2496 | kmd172_en.exe | C:\Users\admin\AppData\Local\Temp\pft313C.tmp\Disk1\layout.bin | binary | |
MD5:52AC2910EFFDBFC1DCB24566621B0DD1 | SHA256:2F6C3E9AEEF07BE318D5347600F4D36C27C359B6C09DA056EC89D7A2BF7EA37C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
9
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 18.205.187.81:80 | http://18.205.187.81:80/ | US | — | — | unknown |
— | — | HEAD | 400 | 23.56.201.214:80 | http://23.56.201.214:80/ | GB | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 18.205.187.81:80 | www.brilliantdigital.com | AMAZON-AES | US | unknown |
820 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 23.56.201.214:80 | www.intel.com | AKAMAI-AS | GB | suspicious |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
adserv.internetfuel.com |
| unknown |
ad2.brilliantdigital.com |
| unknown |
www.brilliantdigital.com |
| unknown |
www.intel.com |
| whitelisted |
upgrade.new.tech |
| unknown |
upgrade.newdotnet.net |
| malicious |