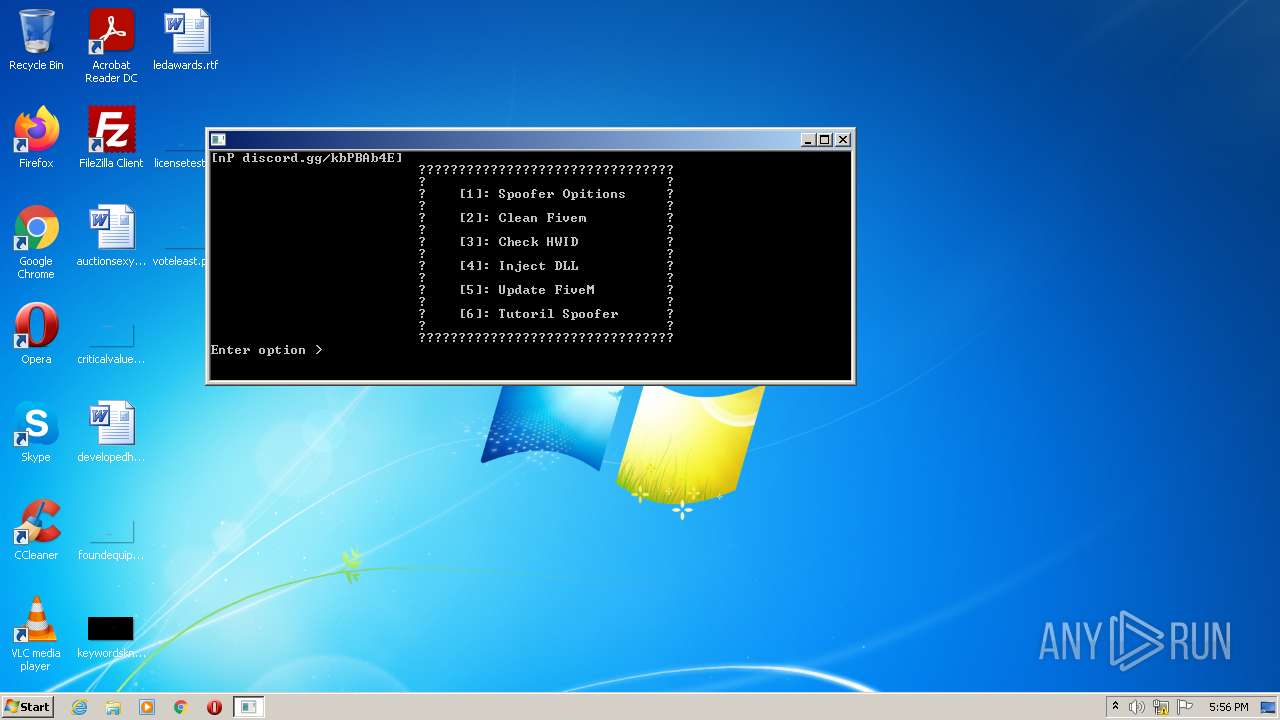
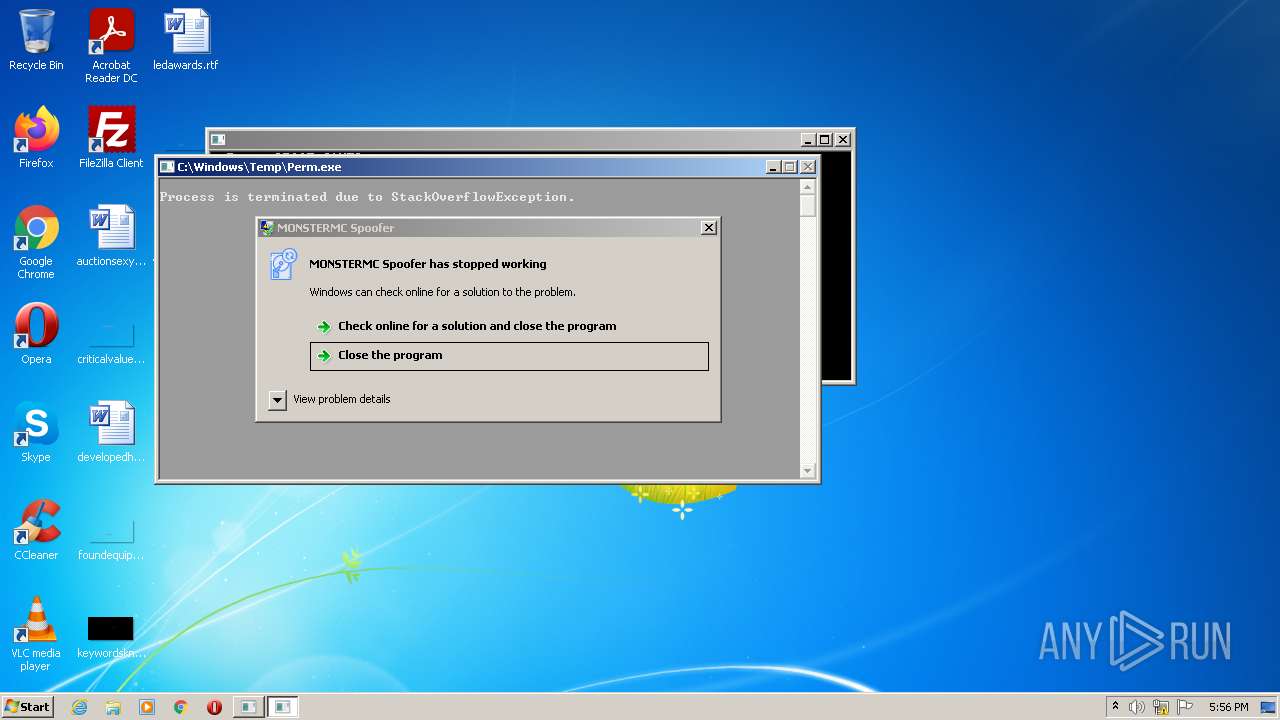
| File name: | nProjectV4.exe |
| Full analysis: | https://app.any.run/tasks/cdbcea0c-5551-41a6-92a5-e7b1eeee75de |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 17:54:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | A453E063EC259B6429FD73ED70308D8E |
| SHA1: | 6BBC2317CF7F6E08BA14BC12370E27D6BBD6F786 |
| SHA256: | 3632C73738F73C6623543B6F97FE1C80B929D3C63FB15FB8CB3EABB0BC7D4736 |
| SSDEEP: | 98304:IzIgQfwnF+pbZlkLkxMc7Hk71xdnkomKi:IzIfIn8pbPz2xxkoG |
MALICIOUS
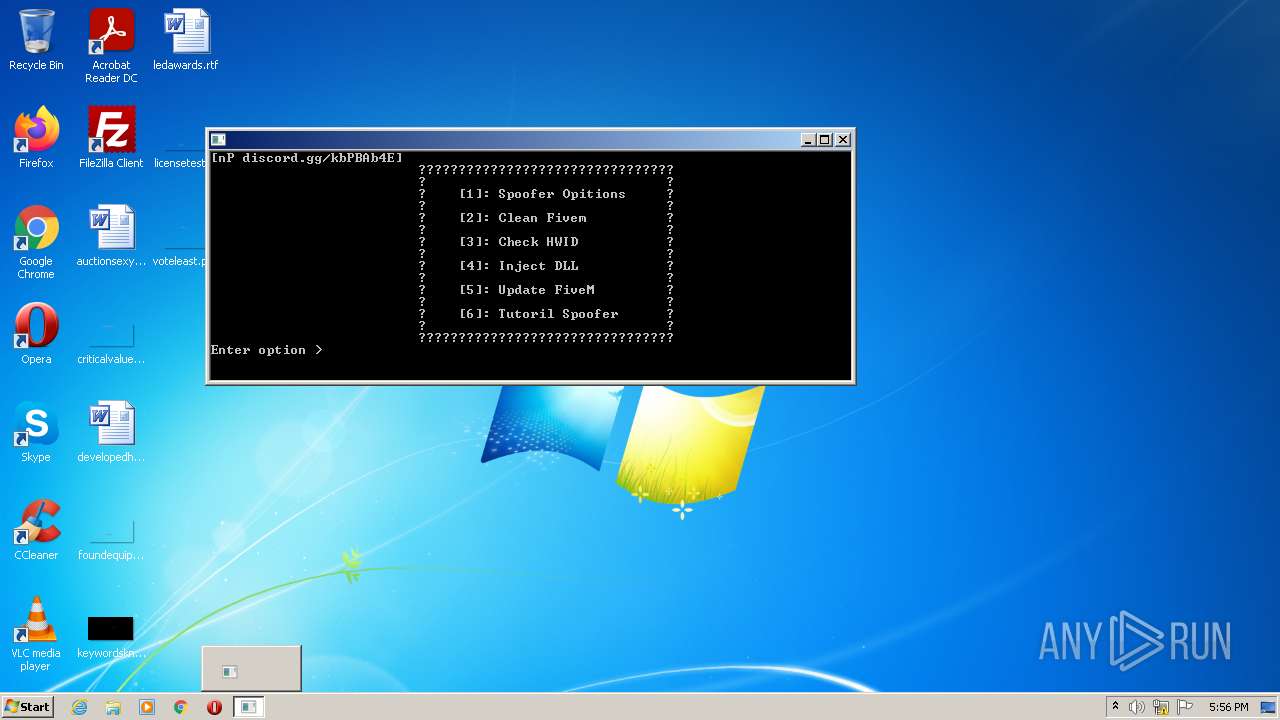
Drops the executable file immediately after the start
- nProjectV4.exe (PID: 4016)
Application was dropped or rewritten from another process
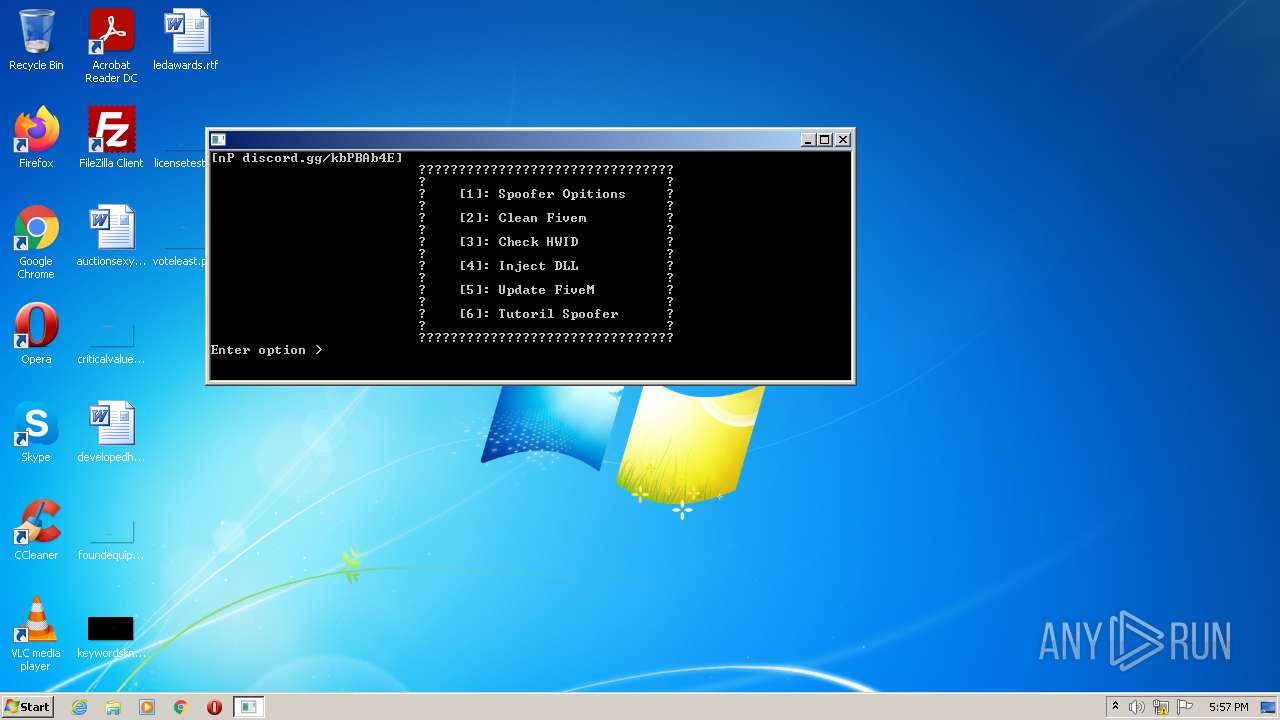
- FiveM_Cleaner.exe (PID: 3400)
- Perm.exe (PID: 3240)
Writes to the hosts file
- cmd.exe (PID: 4024)
SUSPICIOUS
Starts CMD.EXE for commands execution
- nProjectV4.exe (PID: 4016)
- FiveM_Cleaner.exe (PID: 3400)
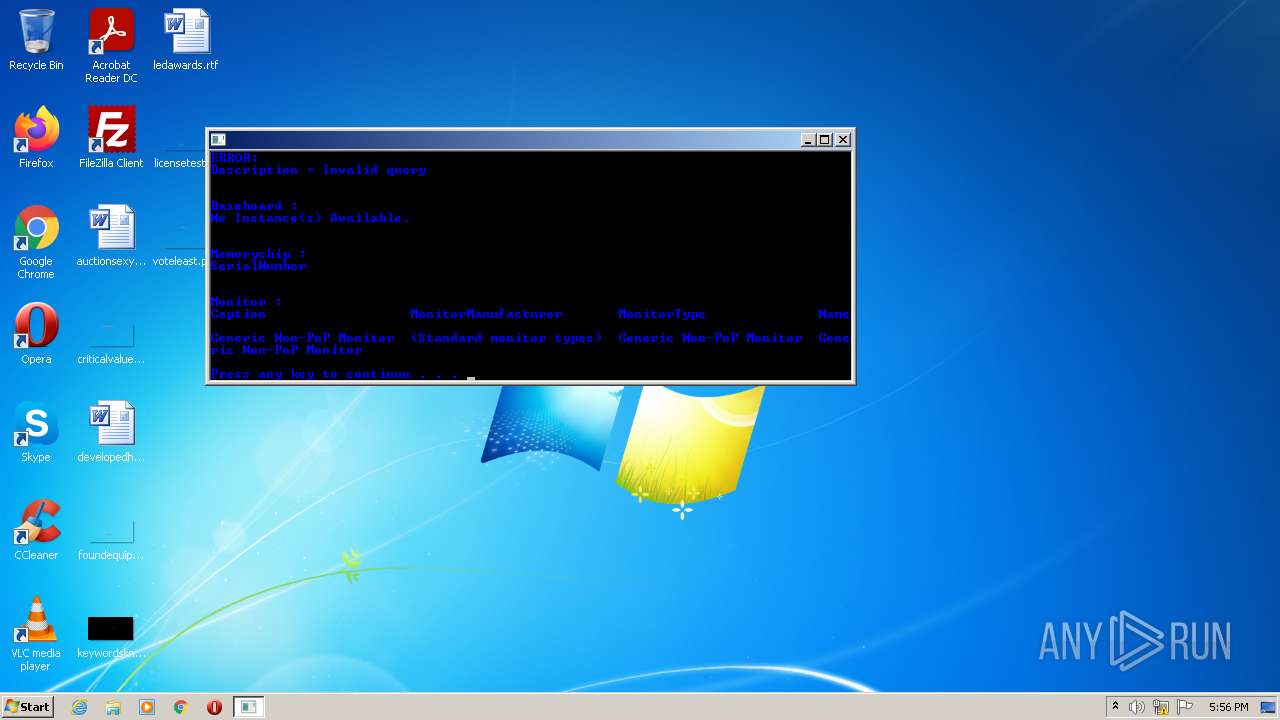
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 3060)
Reads the BIOS version
- nProjectV4.exe (PID: 4016)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 3960)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 1704)
Uses WMIC.EXE to obtain memory chip information
- cmd.exe (PID: 1344)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 420)
Reads settings of System Certificates
- nProjectV4.exe (PID: 4016)
Uses WMIC.EXE to obtain desktop monitor information
- cmd.exe (PID: 768)
Reads the Internet Settings
- nProjectV4.exe (PID: 4016)
Checks Windows Trust Settings
- nProjectV4.exe (PID: 4016)
Reads security settings of Internet Explorer
- nProjectV4.exe (PID: 4016)
Executable content was dropped or overwritten
- nProjectV4.exe (PID: 4016)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4024)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 2224)
Uses TASKKILL.EXE to terminate process
- cmd.exe (PID: 4024)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 2224)
- cmd.exe (PID: 2324)
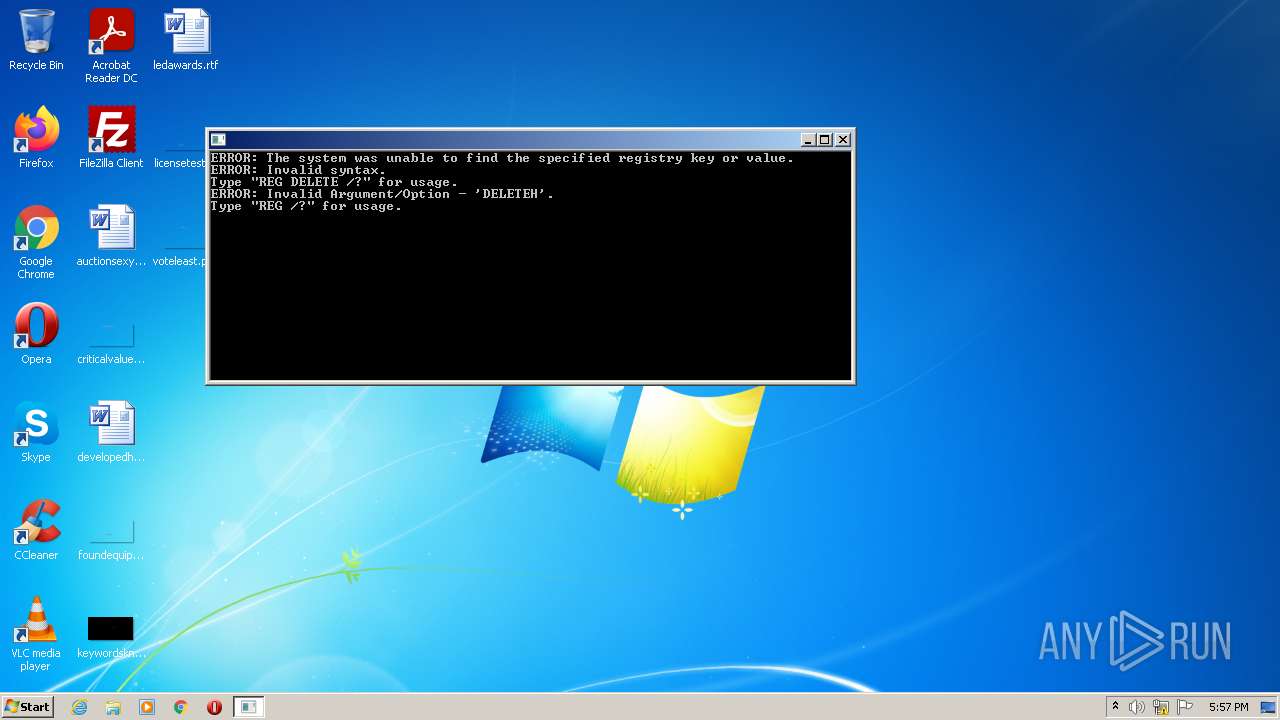
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 4024)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 2224)
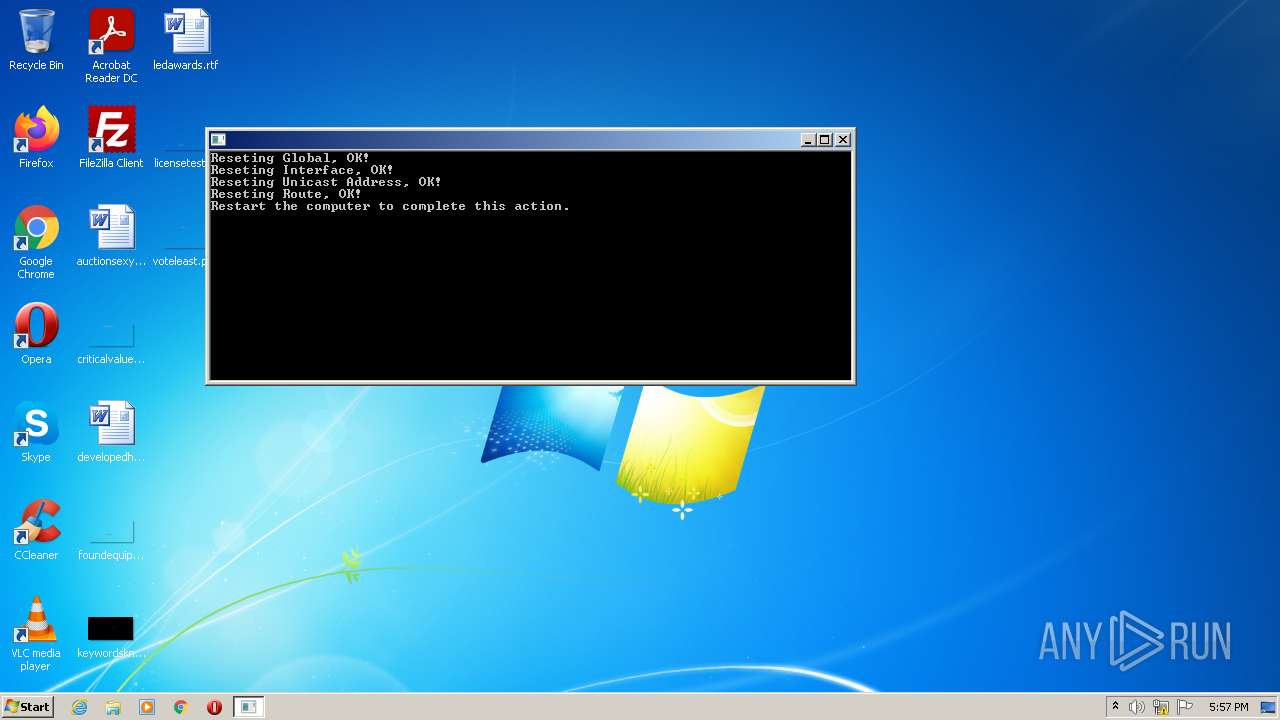
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3216)
INFO
Checks supported languages
- mode.com (PID: 3356)
- nProjectV4.exe (PID: 4016)
- mode.com (PID: 2100)
- FiveM_Cleaner.exe (PID: 3400)
- mode.com (PID: 2676)
- Perm.exe (PID: 3240)
- mode.com (PID: 3044)
Reads the computer name
- nProjectV4.exe (PID: 4016)
- FiveM_Cleaner.exe (PID: 3400)
- Perm.exe (PID: 3240)
Checks proxy server information
- nProjectV4.exe (PID: 4016)
Creates files in the program directory
- nProjectV4.exe (PID: 4016)
Process checks are UAC notifies on
- nProjectV4.exe (PID: 4016)
Drops a file that was compiled in debug mode
- nProjectV4.exe (PID: 4016)
Reads the hosts file
- cmd.exe (PID: 4024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 2022-Oct-25 19:07:56 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 280 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 12 |
| TimeDateStamp: | 2022-Oct-25 19:07:56 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
4096 | 1808350 | 946417 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.98788 | |
(#2) | 1814528 | 513806 | 247674 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.97055 |
(#3) | 2330624 | 44460 | 5898 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.84924 |
(#4) | 2375680 | 488 | 275 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.25982 |
(#5) | 2379776 | 79092 | 48287 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 7.97533 |
.imports | 2461696 | 4096 | 1536 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.43151 |
.tls | 2465792 | 4096 | 512 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.181202 |
.rsrc | 2469888 | 4096 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.77204 |
.themida | 2473984 | 4300800 | 0 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.boot | 6774784 | 2683904 | 2683904 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.9478 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.89623 | 392 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
CRYPT32.dll |
MSVCP140.dll |
RPCRT4.dll |
SHELL32.dll |
USER32.dll |
USERENV.dll |
VCRUNTIME140.dll |
WS2_32.dll |
api-ms-win-crt-convert-l1-1-0.dll |
Total processes
197
Monitored processes
155
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | REG DELETE HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache / f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 124 | REG DELETE HKEY_CURRENT_USER\Software\WinRAR\ArcHistory /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | C:\Windows\system32\cmd.exe /c echo CPU : | C:\Windows\system32\cmd.exe | — | nProjectV4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 312 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\system32\cmd.exe | — | nProjectV4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 312 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\system32\cmd.exe | — | nProjectV4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 344 | "C:\Users\admin\AppData\Local\Temp\nProjectV4.exe" | C:\Users\admin\AppData\Local\Temp\nProjectV4.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 352 | REG DELETE HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 420 | C:\Windows\system32\cmd.exe /c wmic baseboard get serialnumber | C:\Windows\system32\cmd.exe | — | nProjectV4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 436 | REG DELETE HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppSwitched /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | REG DELETE HKEY_CURRENT_USER\Software\WinRAR\ArcHistory /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
60 532
Read events
42 623
Write events
17 906
Delete events
3
Modification events
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4016) nProjectV4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{362E934C-743B-4588-8259-D2482DB771A8} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
Executable files
8
Suspicious files
4
Text files
14
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_5524823BD00A413DFC52CF245D9BF052 | der | |
MD5:— | SHA256:— | |||
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\CLOSE_.EXE[1].exe | executable | |
MD5:— | SHA256:— | |||
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9FF67FB3141440EED32363089565AE60_5524823BD00A413DFC52CF245D9BF052 | binary | |
MD5:— | SHA256:— | |||
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 4016 | nProjectV4.exe | C:\Windows\Temp\Perm.exe | executable | |
MD5:— | SHA256:— | |||
| 4016 | nProjectV4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\CLEANER_PERM[1].exe | executable | |
MD5:E45983720608F1B55AEB6479E2B5EDFB | SHA256:26974120AB54B19A10B99F4BB120E3FAE07EFDE4C40C847FBE4CA96387205134 | |||
| 4016 | nProjectV4.exe | C:\ProgramData\FiveM_Cleaner.exe | executable | |
MD5:C4C27642B041BC79E25FE5E644036FBA | SHA256:7286678F12AEB16D2EFA0D2131012C0395425C997DEBCB4528C67A1AEC3FD9CD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
5
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4016 | nProjectV4.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
4016 | nProjectV4.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA4ZFS%2FPJgg7ME3dUpREkGs%3D | US | der | 279 b | whitelisted |
4016 | nProjectV4.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d02a935be103eb44 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4016 | nProjectV4.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
4016 | nProjectV4.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
4016 | nProjectV4.exe | 188.114.97.3:443 | keyauth.win | CLOUDFLARENET | NL | malicious |
4016 | nProjectV4.exe | 162.159.129.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
keyauth.win |
| malicious |
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
4016 | nProjectV4.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
4016 | nProjectV4.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
4016 | nProjectV4.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |