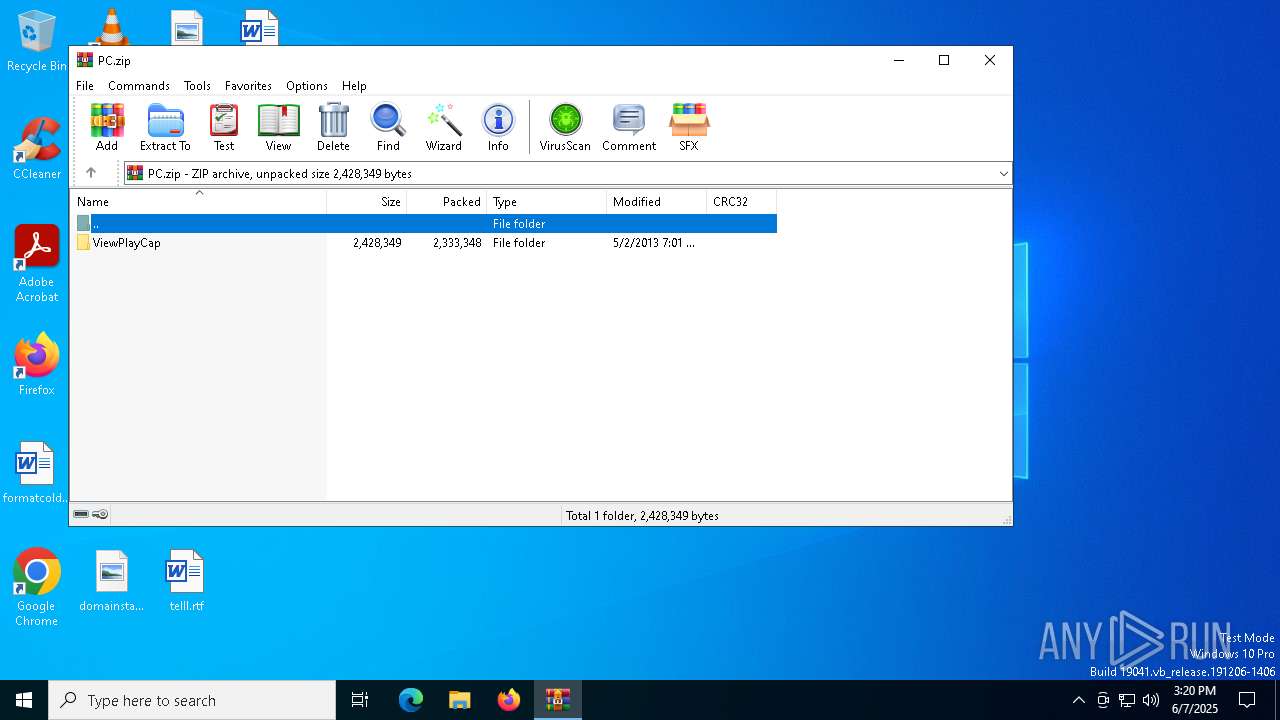
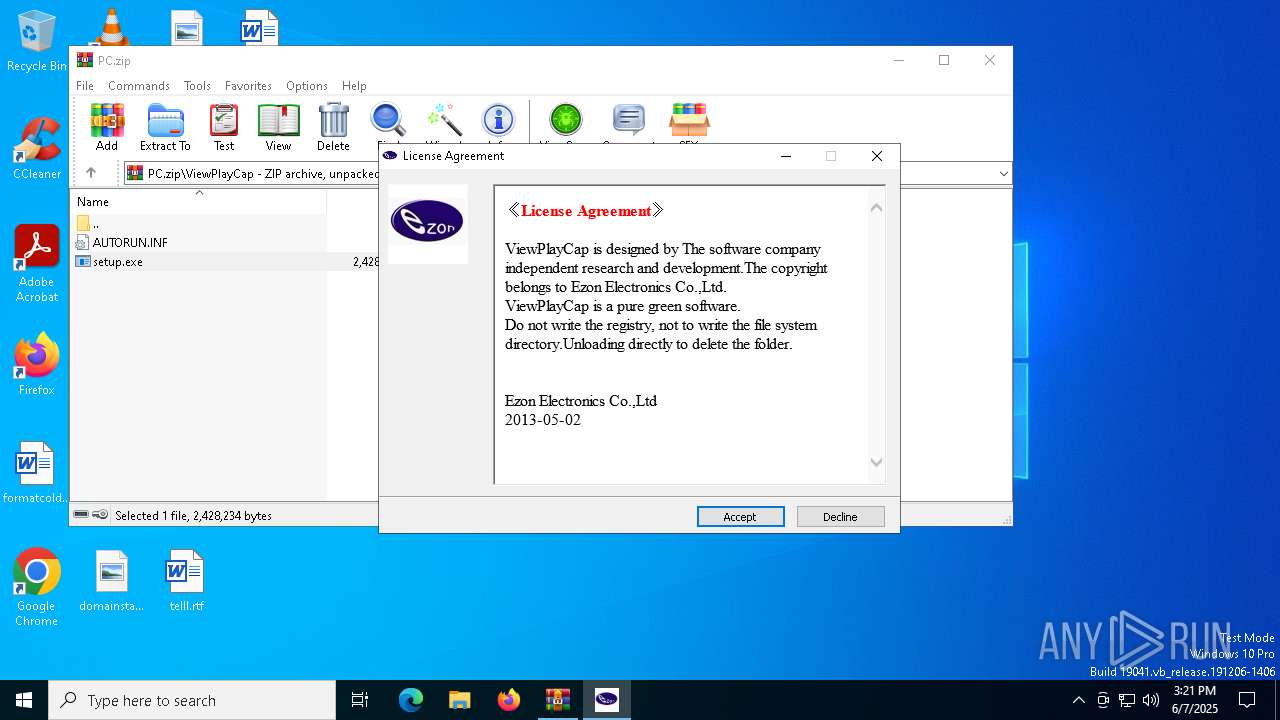
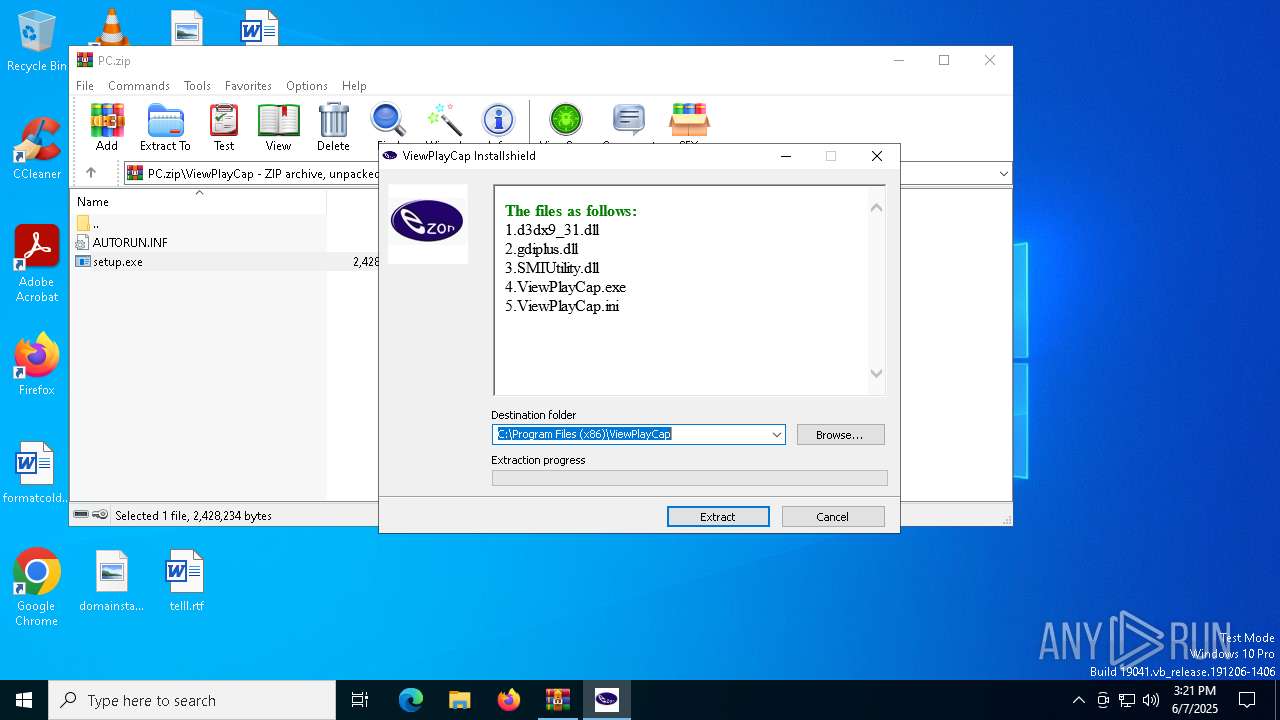
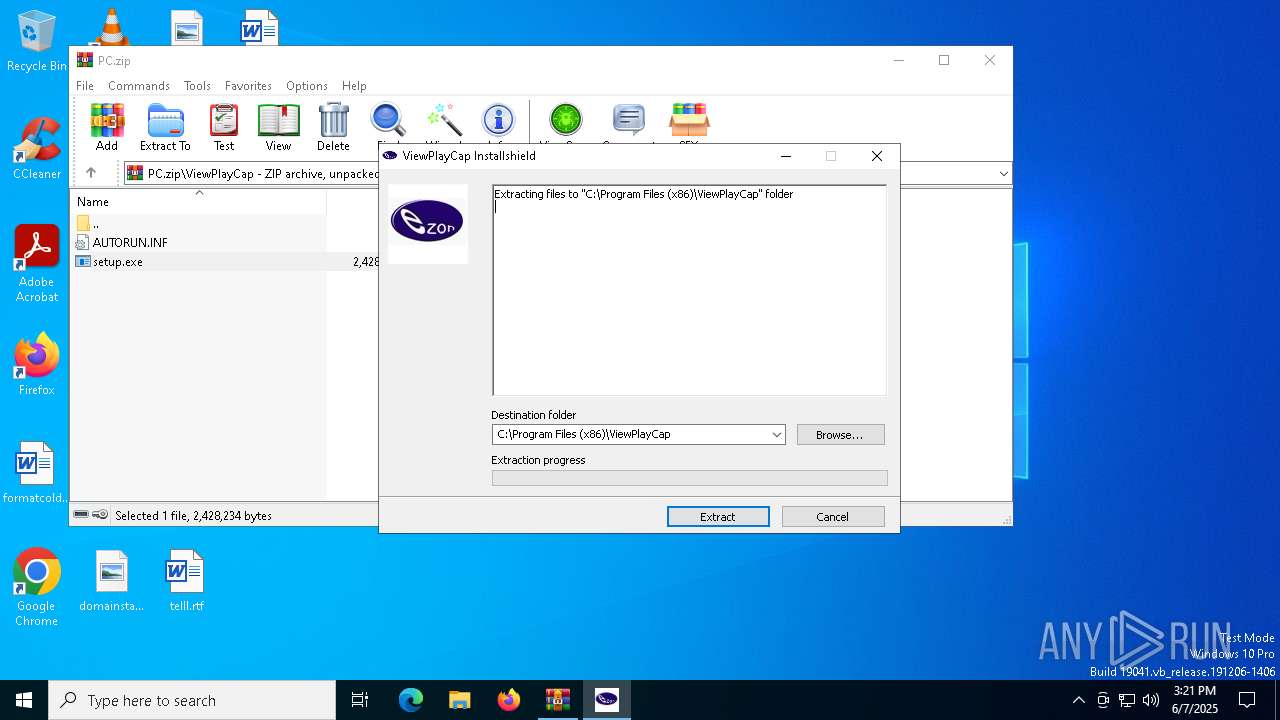
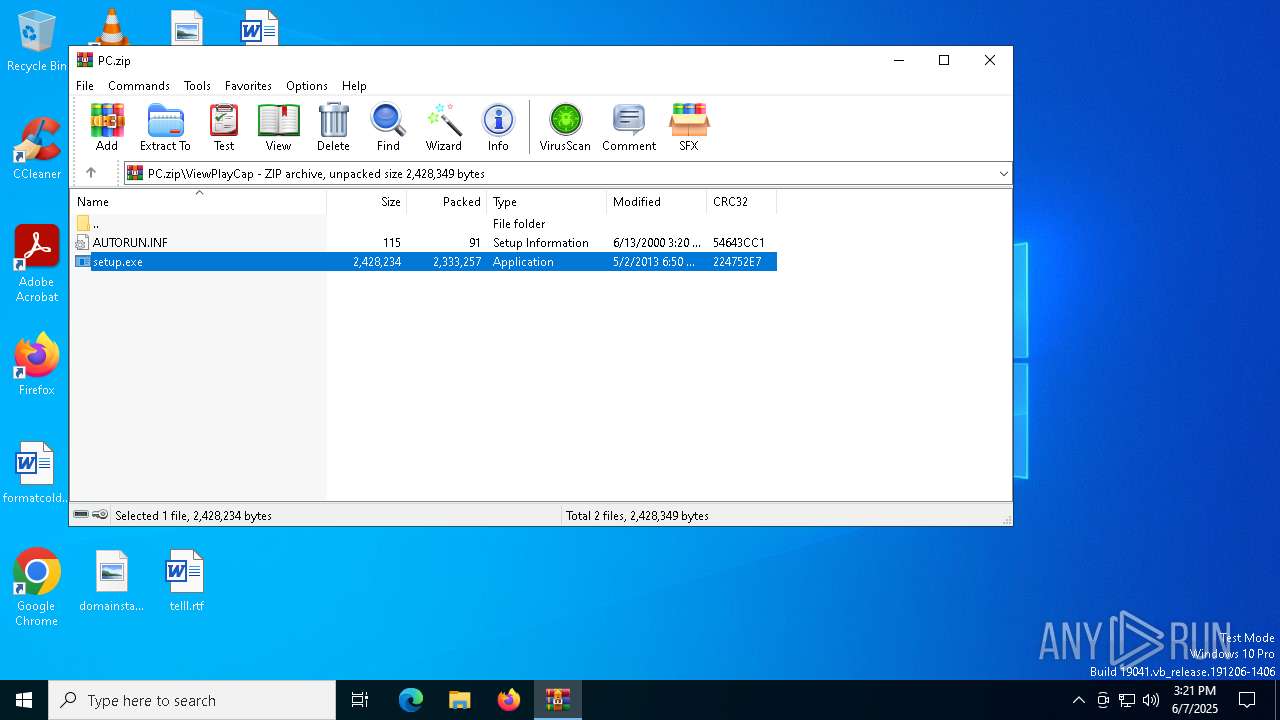
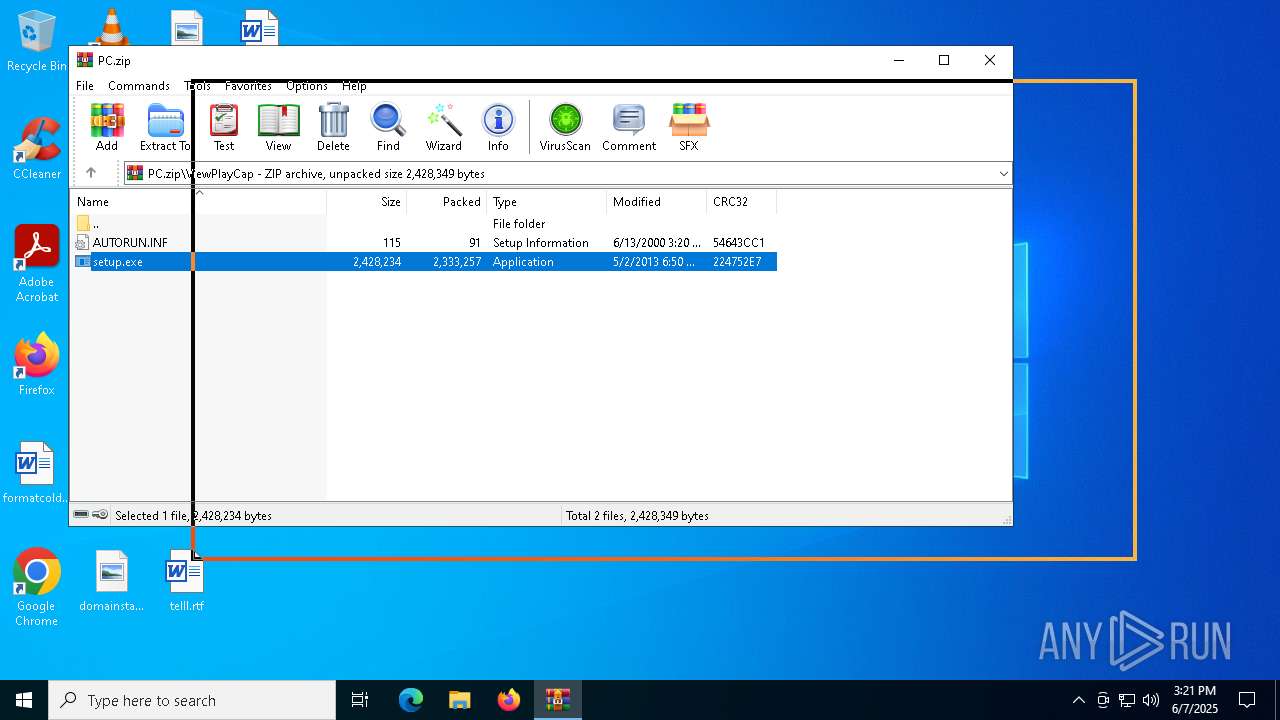
| File name: | PC.zip |
| Full analysis: | https://app.any.run/tasks/63e8fa4f-688b-43f2-a8c8-986f3a9c4478 |
| Verdict: | Malicious activity |
| Analysis date: | June 07, 2025, 15:20:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
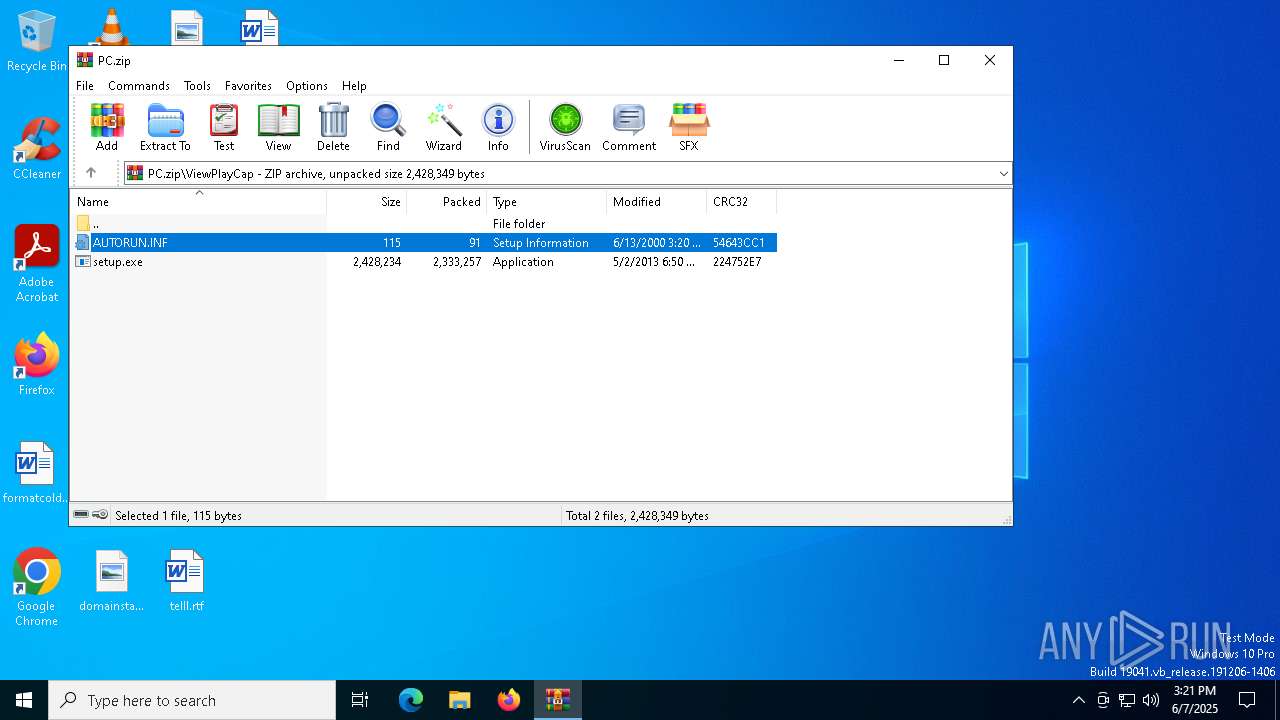
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E3AFE4148D6161D9EE76D71558B7A79C |
| SHA1: | A625B81B01132D1735505A1CA735AB984937B6B2 |
| SHA256: | 35F836F50B8CE76161BE6AE39D035074A8ECDE9D42107D230A86831B7200E65F |
| SSDEEP: | 98304:1taV9zH0J+kc2X3evv408CdShbHPaWhaFuqsQeGnZxUqXENTw4b+pqlNi7LgLy0Z:65papgs |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7448)
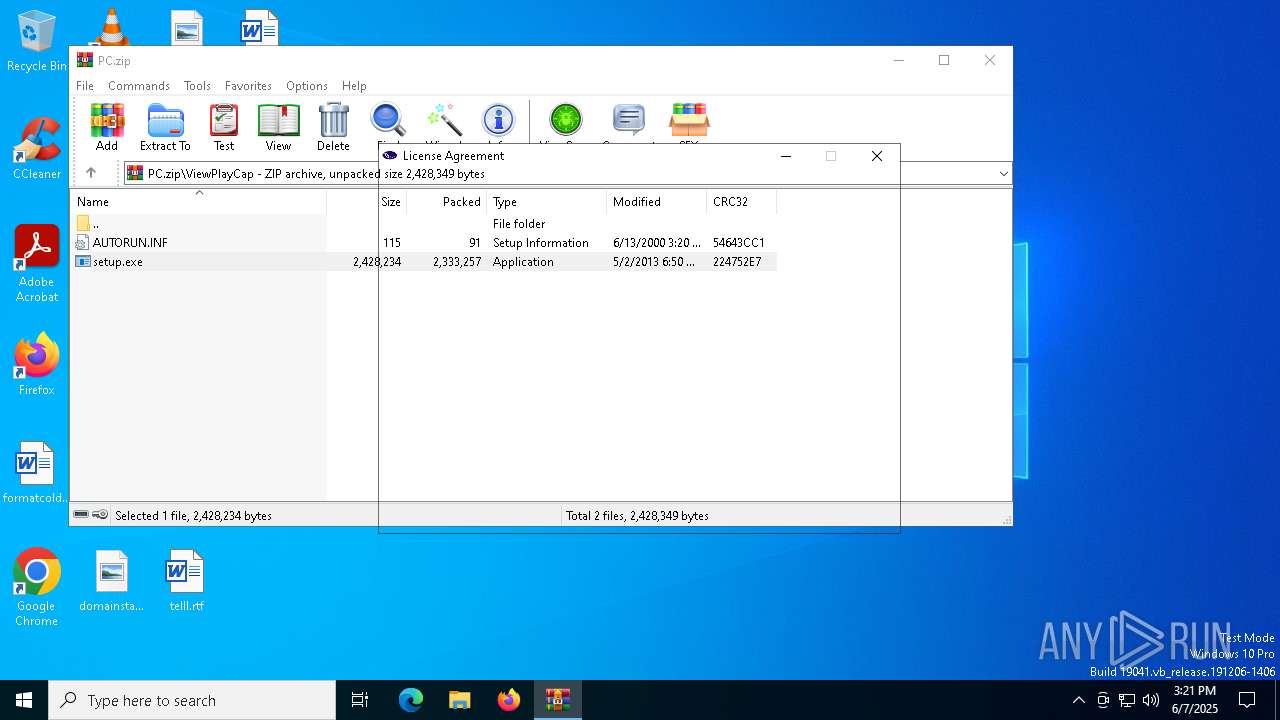
SFX dropper has been detected
- setup.exe (PID: 6920)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7448)
- setup.exe (PID: 6920)
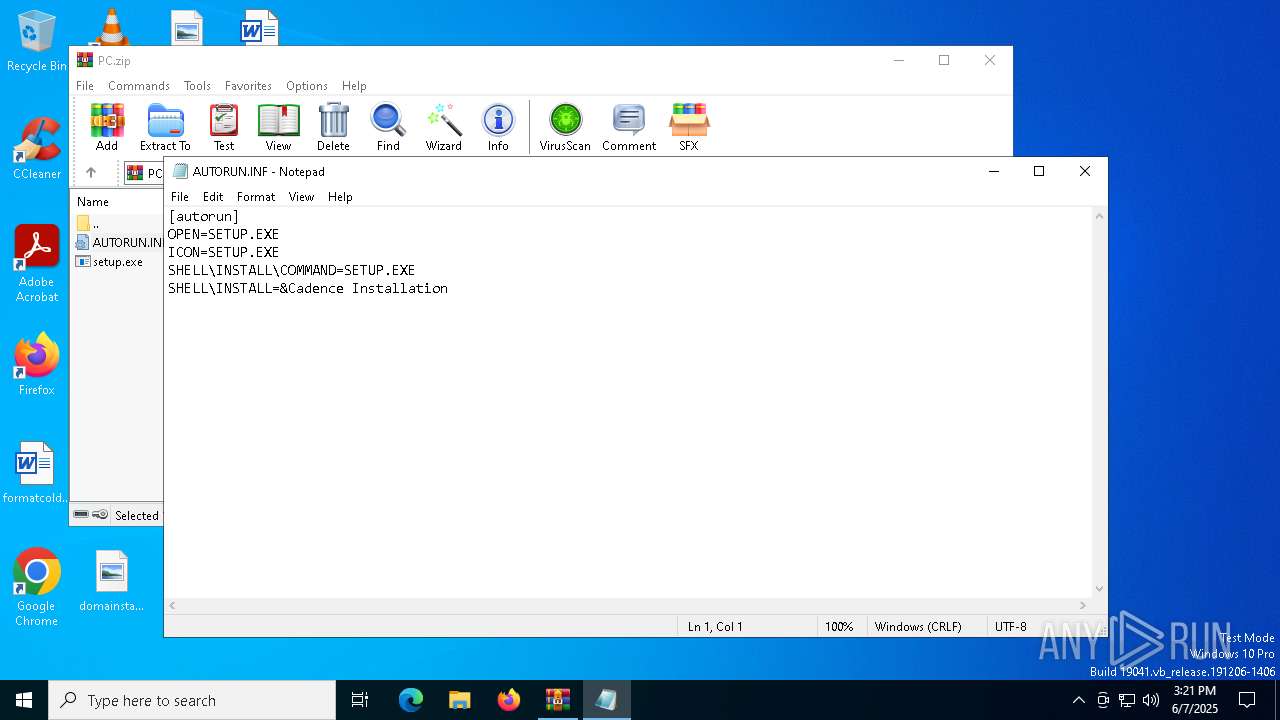
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 7448)
Reads Microsoft Outlook installation path
- setup.exe (PID: 6920)
Reads Internet Explorer settings
- setup.exe (PID: 6920)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 6920)
Application launched itself
- setup.exe (PID: 6920)
Process drops legitimate windows executable
- setup.exe (PID: 6572)
Executable content was dropped or overwritten
- setup.exe (PID: 6572)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 5552)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7448)
Checks supported languages
- setup.exe (PID: 6920)
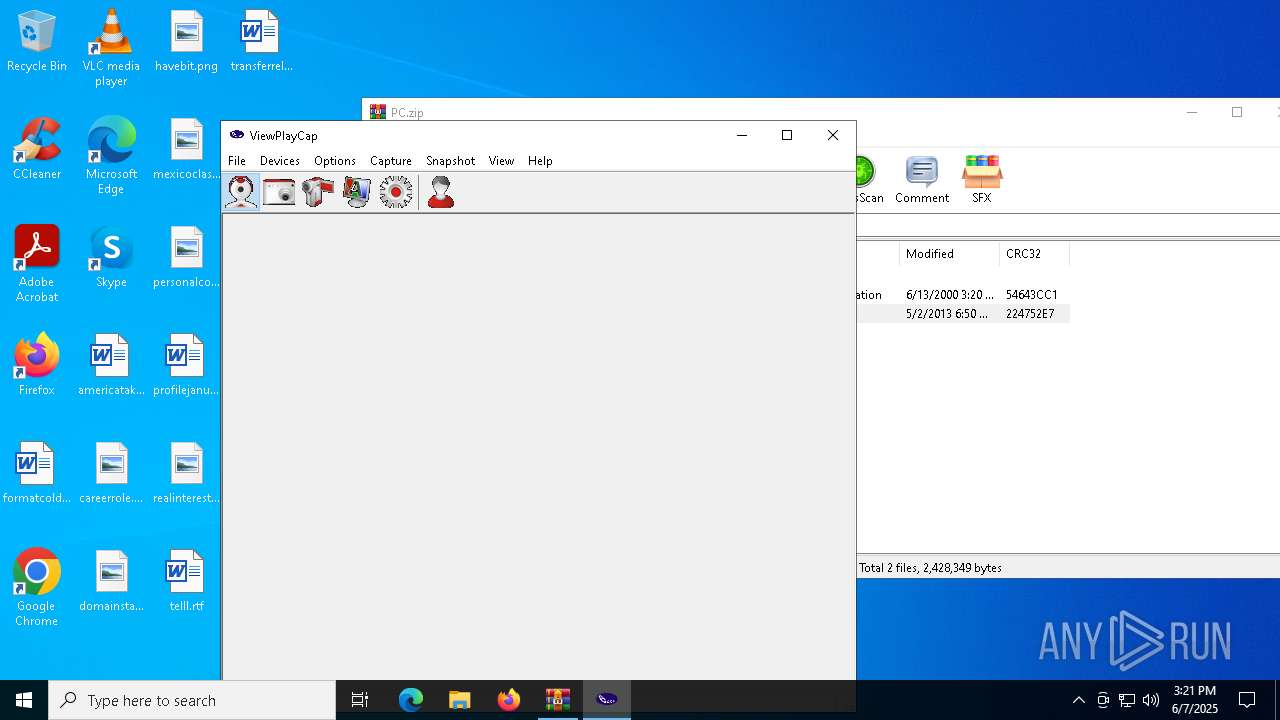
- ViewPlayCap.exe (PID: 7728)
- setup.exe (PID: 6572)
Reads the computer name
- setup.exe (PID: 6920)
- ViewPlayCap.exe (PID: 7728)
- setup.exe (PID: 6572)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7448)
Process checks computer location settings
- setup.exe (PID: 6920)
Manual execution by a user
- ViewPlayCap.exe (PID: 7728)
Creates files or folders in the user directory
- setup.exe (PID: 6572)
The sample compiled with chinese language support
- setup.exe (PID: 6572)
Reads the software policy settings
- slui.exe (PID: 7720)
Checks proxy server information
- setup.exe (PID: 6920)
Creates files in the program directory
- setup.exe (PID: 6572)
The sample compiled with english language support
- setup.exe (PID: 6572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2000:06:13 11:20:40 |
| ZipCRC: | 0x54643cc1 |
| ZipCompressedSize: | 91 |
| ZipUncompressedSize: | 115 |
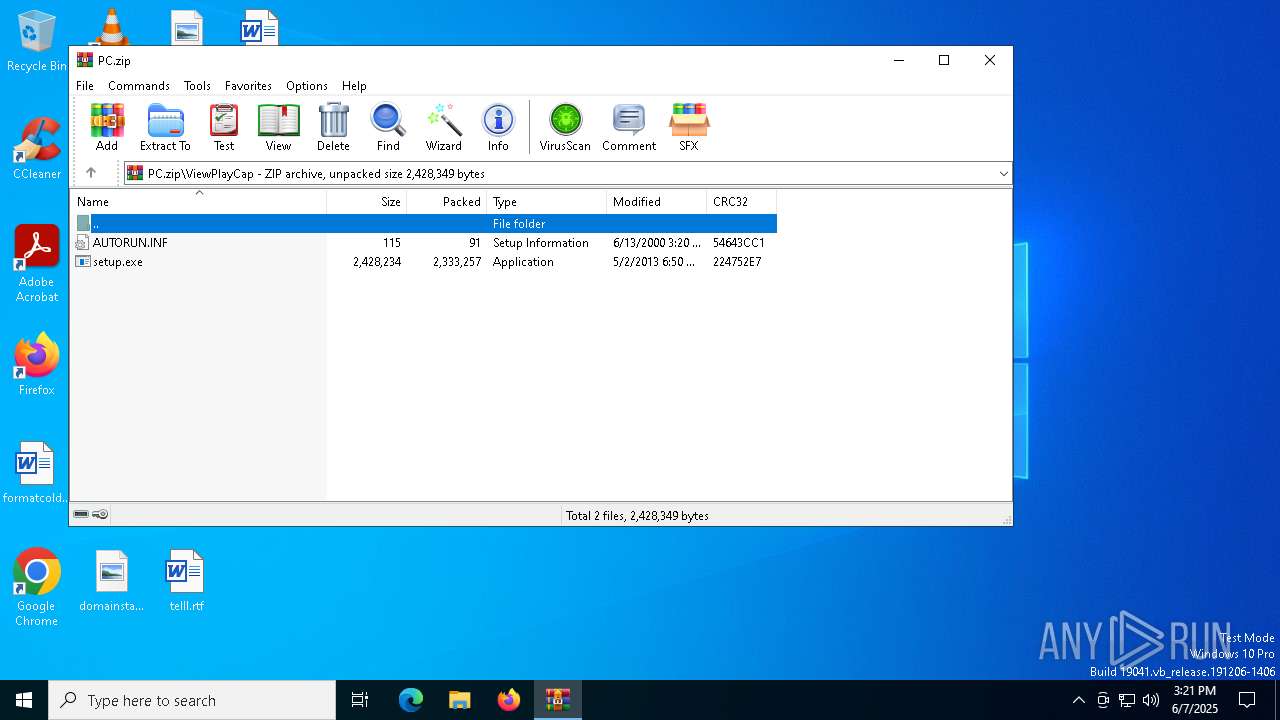
| ZipFileName: | ViewPlayCap/AUTORUN.INF |
Total processes
133
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2236 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5552 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa7448.47546\AUTORUN.INF | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6572 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7448.49493\ViewPlayCap\setup.exe" -el -s2 "-dC:\Program Files (x86)\ViewPlayCap" "-p" "-sp" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7448.49493\ViewPlayCap\setup.exe | setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6920 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7448.49493\ViewPlayCap\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7448.49493\ViewPlayCap\setup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7448 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\PC.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7720 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7728 | "C:\Program Files (x86)\ViewPlayCap\ViewPlayCap.exe" | C:\Program Files (x86)\ViewPlayCap\ViewPlayCap.exe | — | explorer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: ViewPlayCap Version: 3, 0, 0, 0 Modules
| |||||||||||||||
Total events
6 615
Read events
6 588
Write events
27
Delete events
0
Modification events
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PC.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
6
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6572 | setup.exe | C:\Program Files (x86)\ViewPlayCap\d3dx9_31.dll | executable | |
MD5:797E24743937D67D69F28F2CF5052EE8 | SHA256:E2065619FE6EB0034833B1DC0369DEB4A6EDC3110E38A1132EEAFCF430C578A5 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7448.49493\ViewPlayCap\setup.exe | executable | |
MD5:BCDD8DA242AC5BE6D2A7D86A13BE812F | SHA256:85309B4A5739A95743A0DB87A17A9458F14D84AB2CCE2EE46FFD0C63C6E1DE7F | |||
| 6572 | setup.exe | C:\Program Files (x86)\ViewPlayCap\SMIUtility.dll | executable | |
MD5:AEA0D6ACC43D8915A7887D91F690813B | SHA256:1EE6C041276CD5B1A3E14B2A833982DC6F9197694E0F1CD3F55453655427AD40 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7448.47546\AUTORUN.INF | binary | |
MD5:1D7796788CC7F6B21CC62F071D999739 | SHA256:F5AE400AA77AFA5CF40C51036FE860EE3F1247103BB26E1F9647CC95F247B66C | |||
| 6572 | setup.exe | C:\Program Files (x86)\ViewPlayCap\gdiplus.dll | executable | |
MD5:4D328694BB516E46D2D184950D94433F | SHA256:8199452AF9E5289C126D0FF9D99F2302C52861EC49008702B7F95D64D316383C | |||
| 6572 | setup.exe | C:\Program Files (x86)\ViewPlayCap\ViewPlayCap.ini | text | |
MD5:C31F2FC37B7BDC4C252A501E56761047 | SHA256:CCCD7EA56F0FDBE1FA3F25F760F959E098548F0F81662FE67B8AF39815372313 | |||
| 6572 | setup.exe | C:\Users\admin\Desktop\ViewPlayCap.lnk | binary | |
MD5:ED456173A2408225EE0A80C4E06B3D74 | SHA256:BD02F1C0261BF23B1B5C185158B398C29E79A4F0CC723FC59C7095F1DF540173 | |||
| 6572 | setup.exe | C:\Program Files (x86)\ViewPlayCap\ViewPlayCap.exe | executable | |
MD5:969EFC4F3304909E5DD6173432B1F5C5 | SHA256:24D7D197FE1BBE7584DA4EB488213647147DAE3EC7E313ECB59B8B2F1E419C81 | |||
| 6572 | setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\ViewPlayCap.lnk | binary | |
MD5:827FFCB6DF0152E21F45B99B64E6EC50 | SHA256:A622EEF92930734666EDD608BFACE8FBBF212DFECA3AB442A7B0377B556982D3 | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7448.49493\ViewPlayCap\AUTORUN.INF | binary | |
MD5:1D7796788CC7F6B21CC62F071D999739 | SHA256:F5AE400AA77AFA5CF40C51036FE860EE3F1247103BB26E1F9647CC95F247B66C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5592 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5592 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4164 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7328 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4164 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |