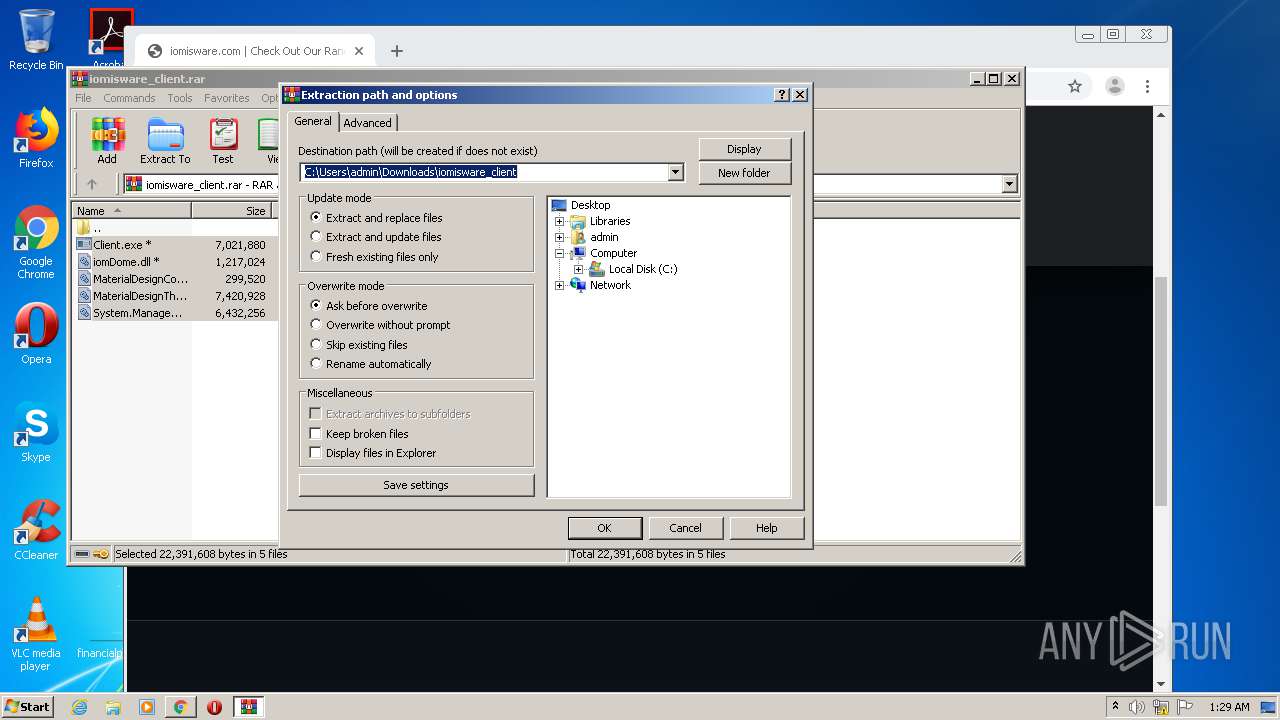
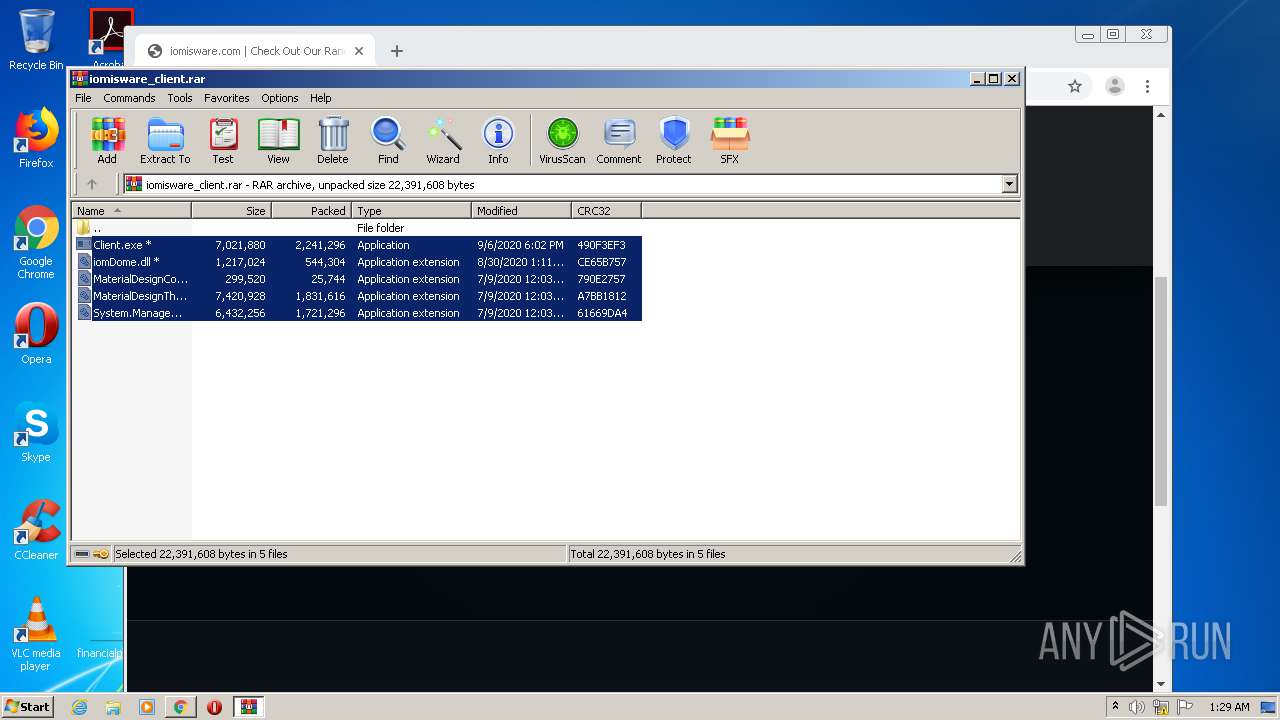
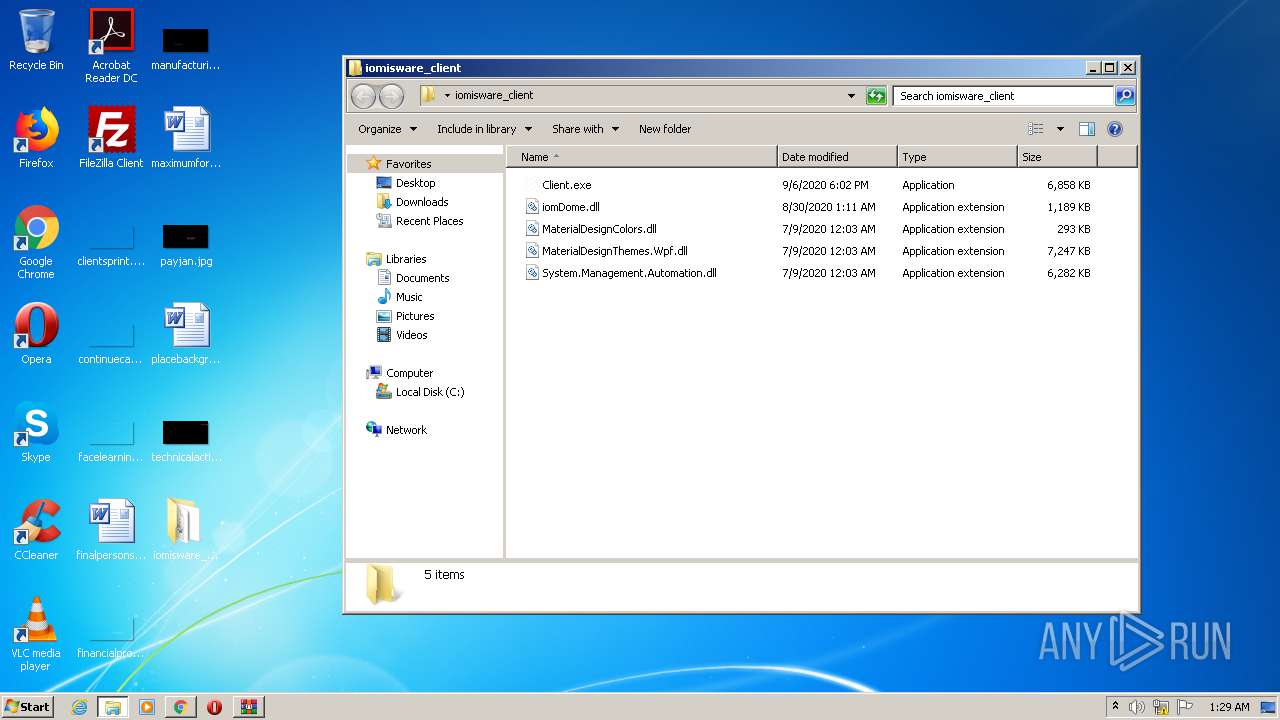
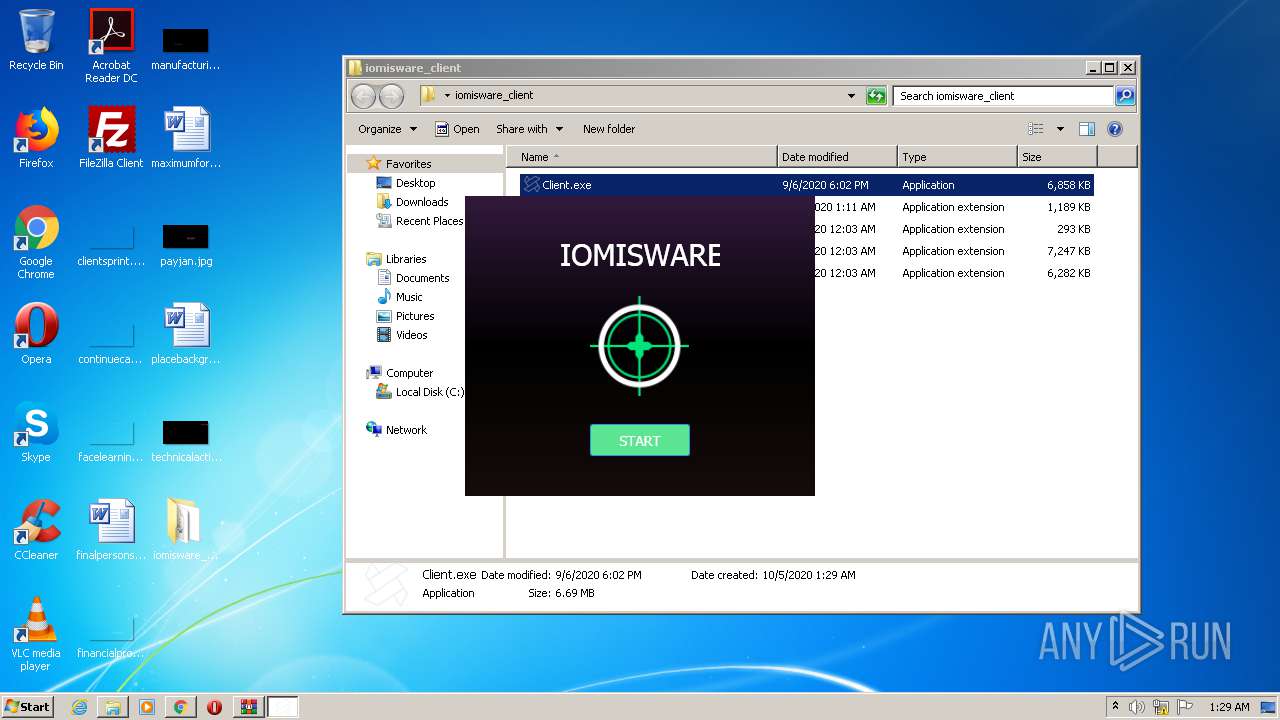
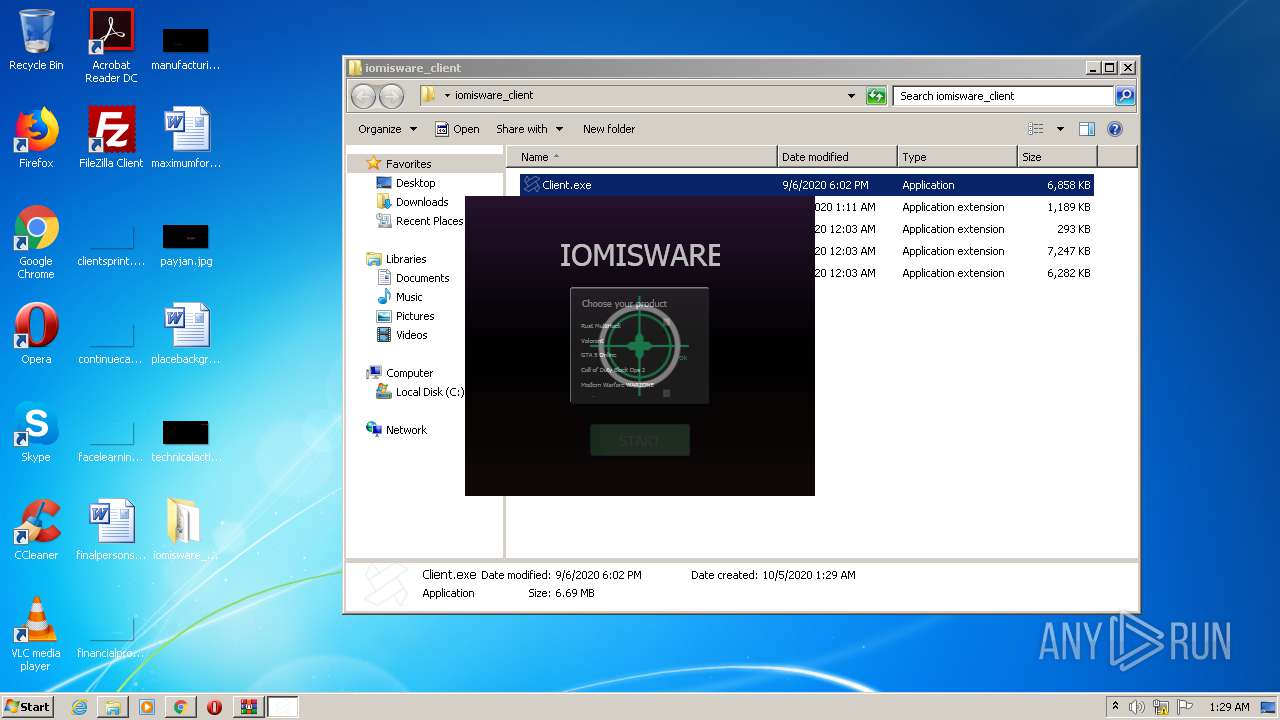
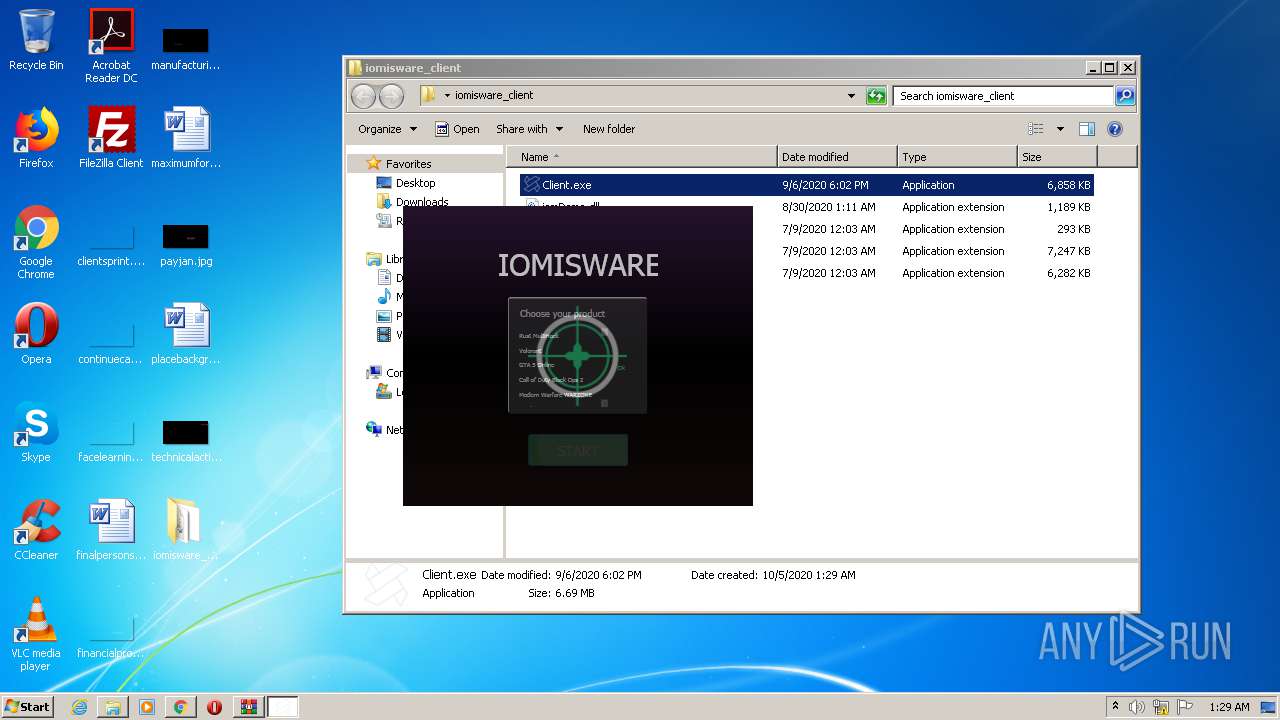
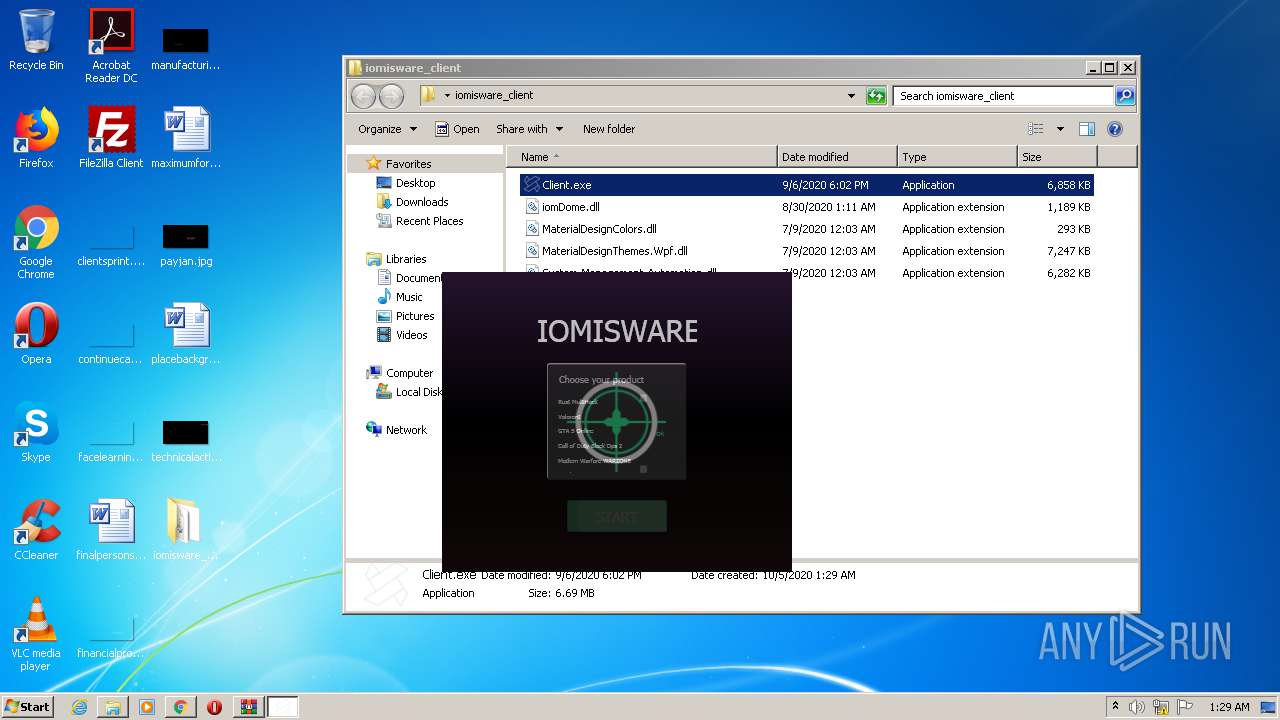
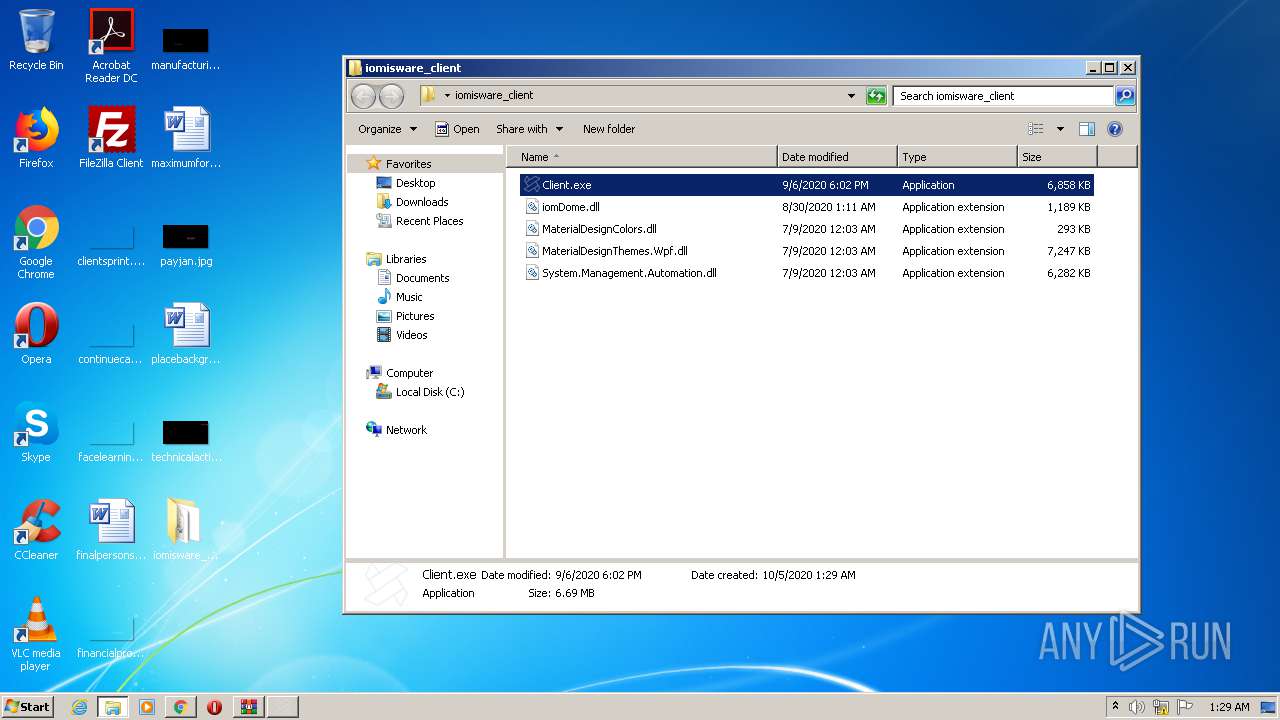
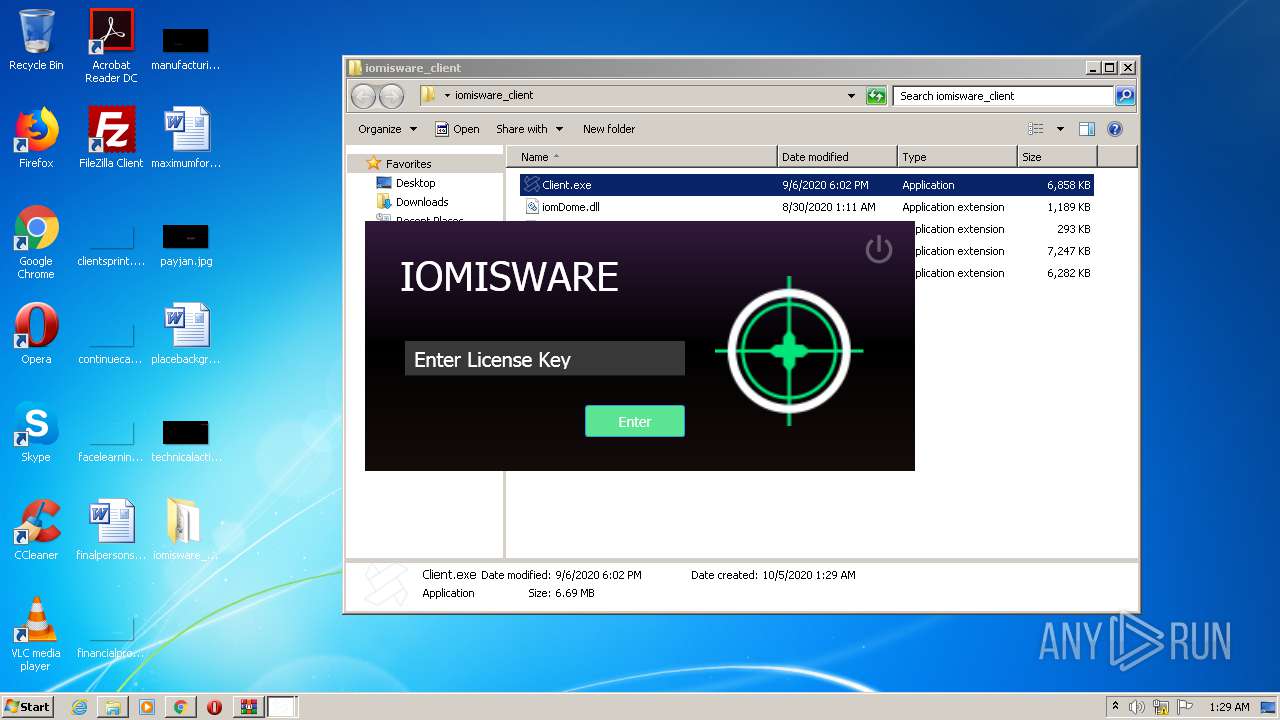
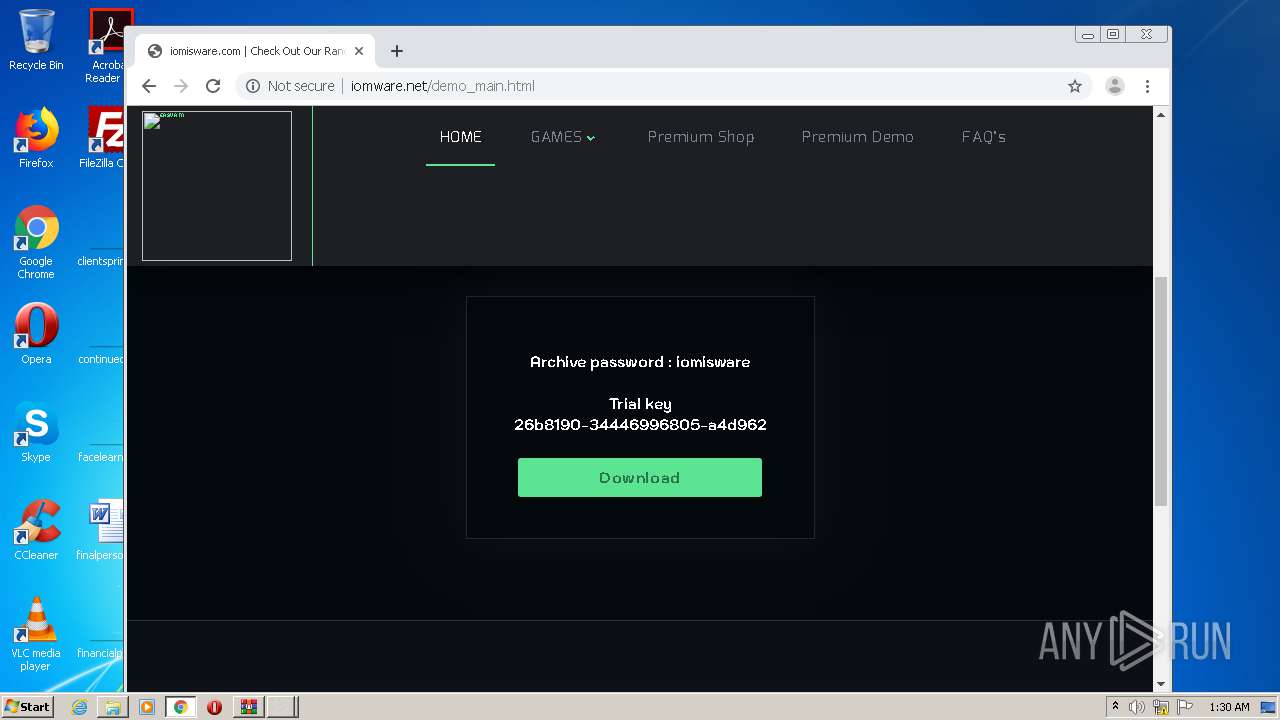
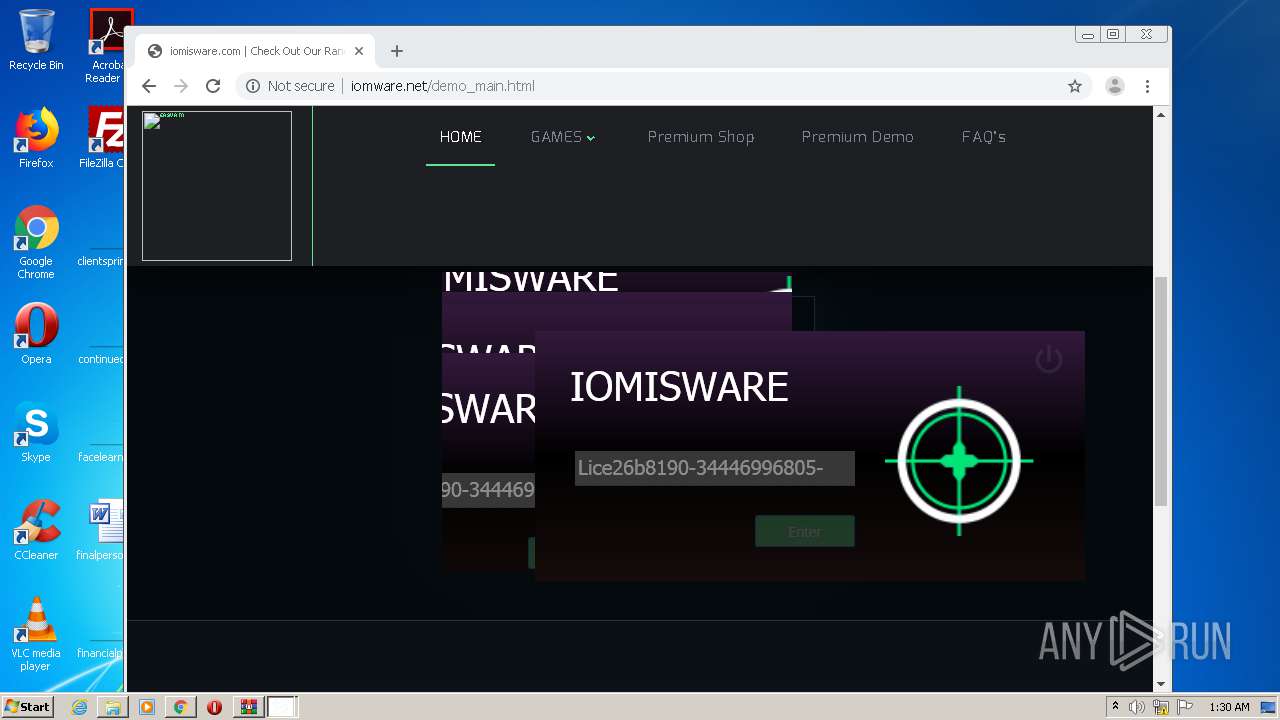
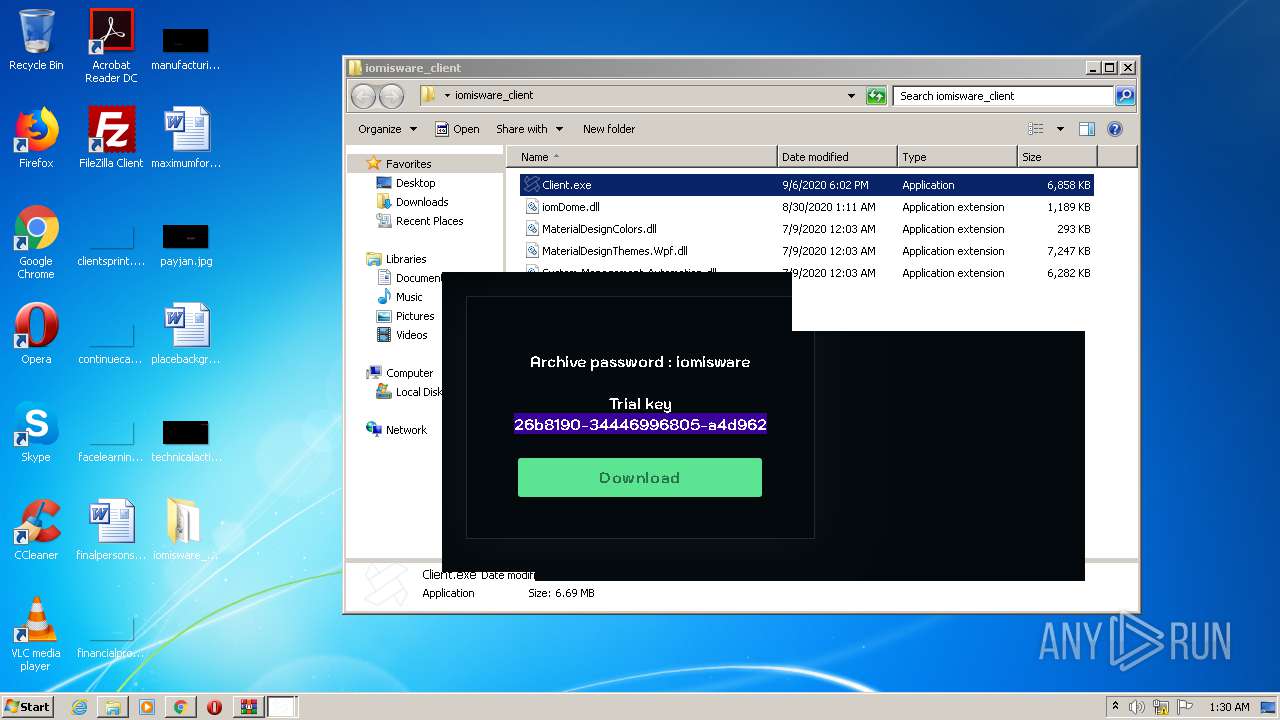
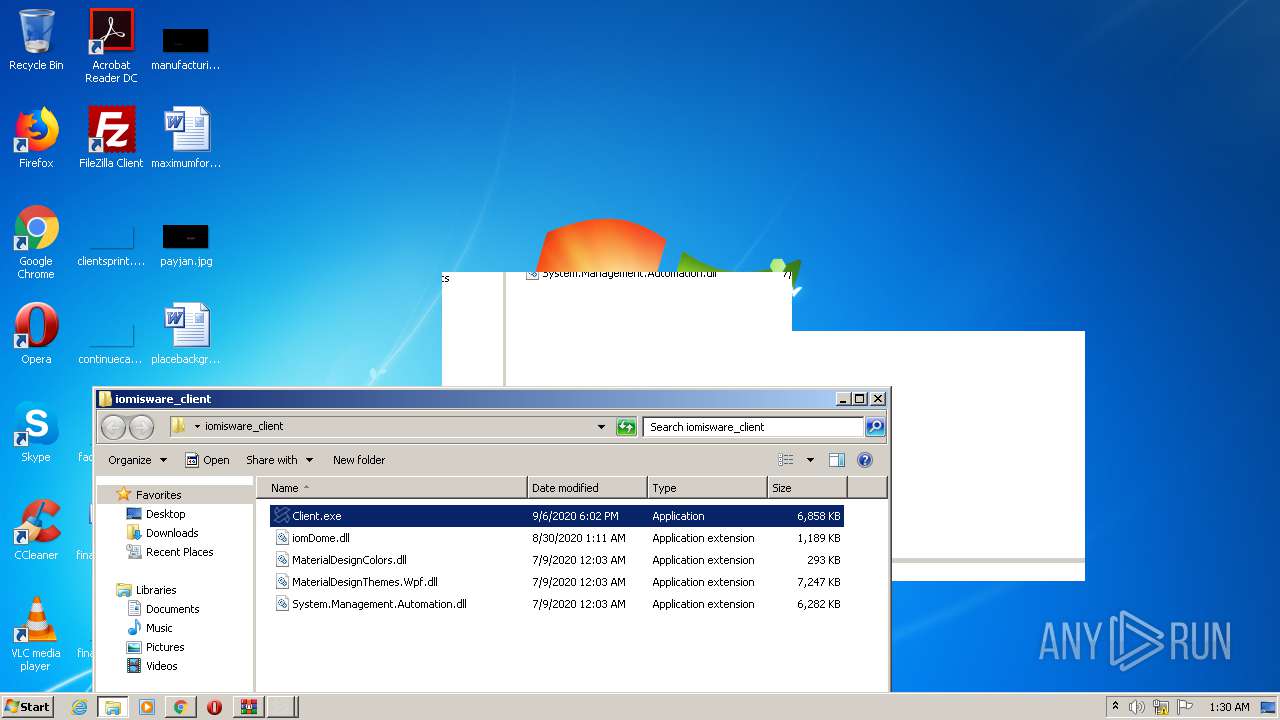
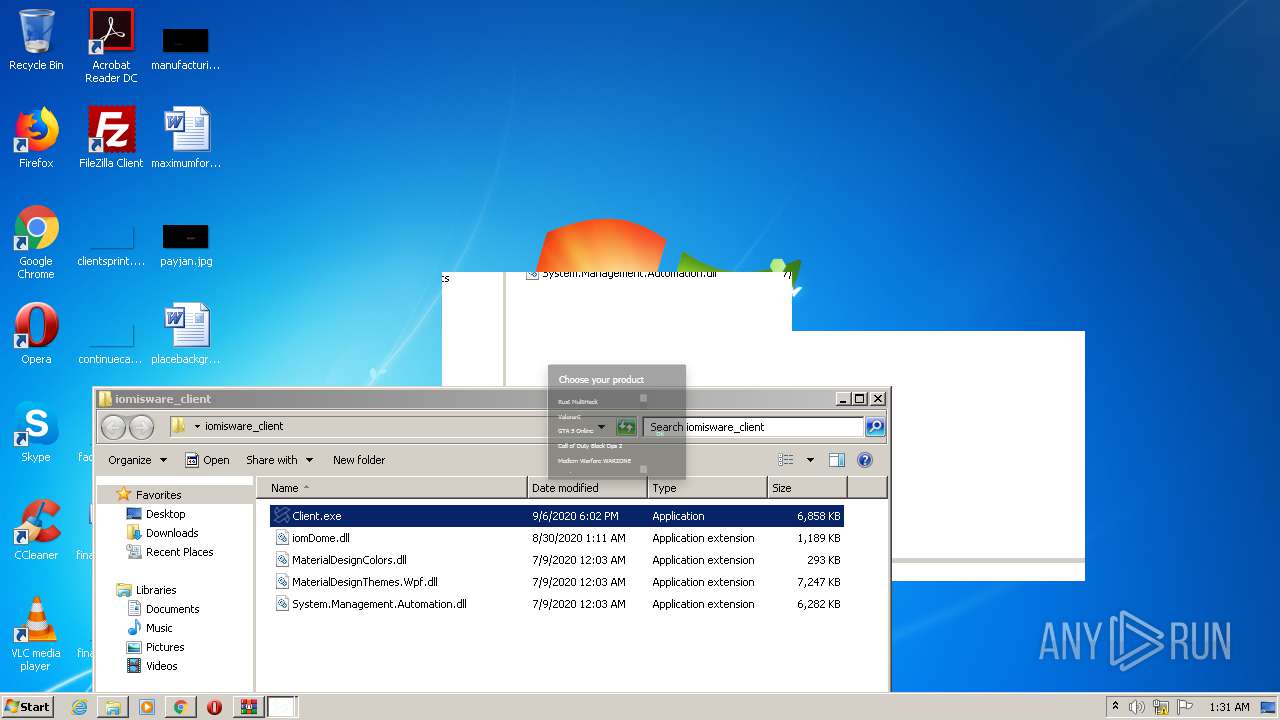
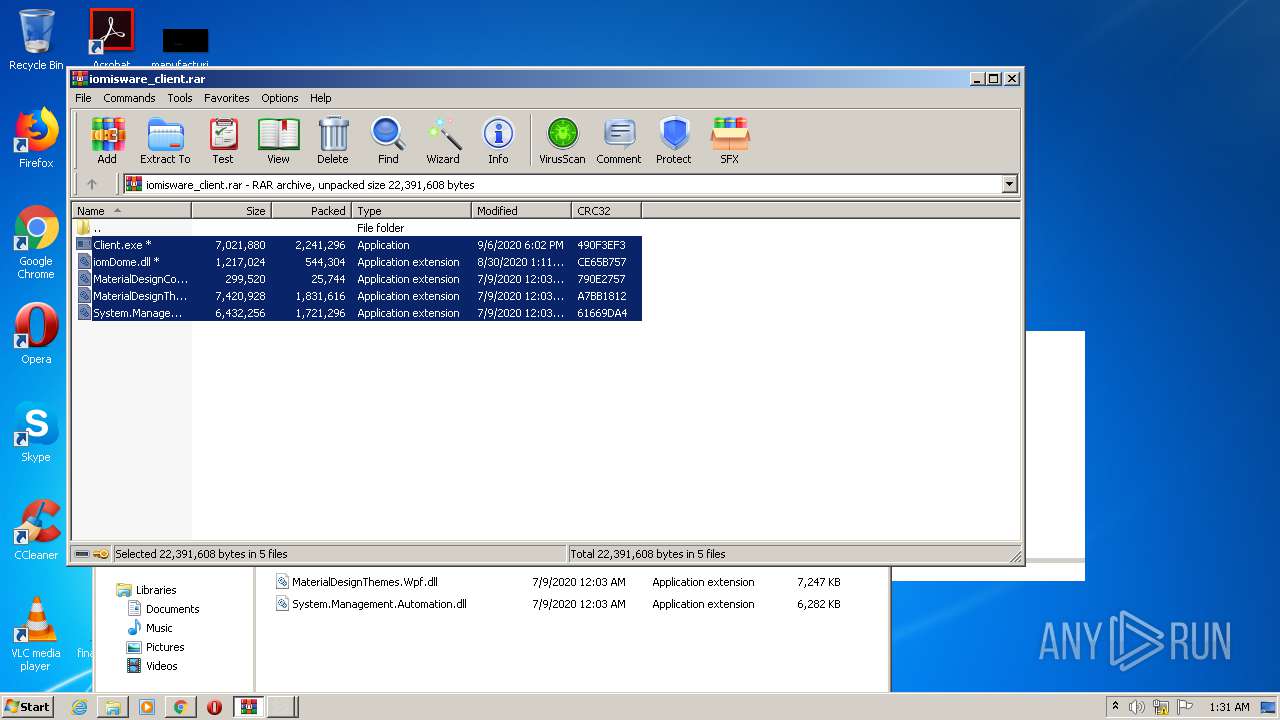
| File name: | Client.exe |
| Full analysis: | https://app.any.run/tasks/b66b76a7-2ea8-43c3-a2b0-59bdb2cb23bb |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2020, 00:28:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | AFA62DC8568BF0A34B3D586CFB0F0E87 |
| SHA1: | 83B00F1629170A3BCD5D1065D5B0B4A5903C7053 |
| SHA256: | 35F51FD7DBE66C1C840289ADF516373FB717AF0D80F632CDEBC3ED24F97E6D6A |
| SSDEEP: | 49152:Y815KBAZYGcT0nJ4E3dAig3hasIuareG8rXtZ8yn8oCun0K7rXCDp9OQJXH002Qv:k0J2asarexj0V |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3832)
- explorer.exe (PID: 328)
- Client.exe (PID: 1680)
- Client.exe (PID: 372)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1852)
Reads Environment values
- Client.exe (PID: 1680)
INFO
Application launched itself
- chrome.exe (PID: 2528)
Manual execution by user
- chrome.exe (PID: 2528)
- Client.exe (PID: 1680)
Reads the hosts file
- chrome.exe (PID: 2528)
- chrome.exe (PID: 2116)
Reads settings of System Certificates
- chrome.exe (PID: 2116)
Reads Internet Cache Settings
- chrome.exe (PID: 2528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2094:05:28 10:27:18+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 6896640 |
| InitializedDataSize: | 116736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x695a6e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.5.3.4 |
| ProductVersionNumber: | 0.5.3.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
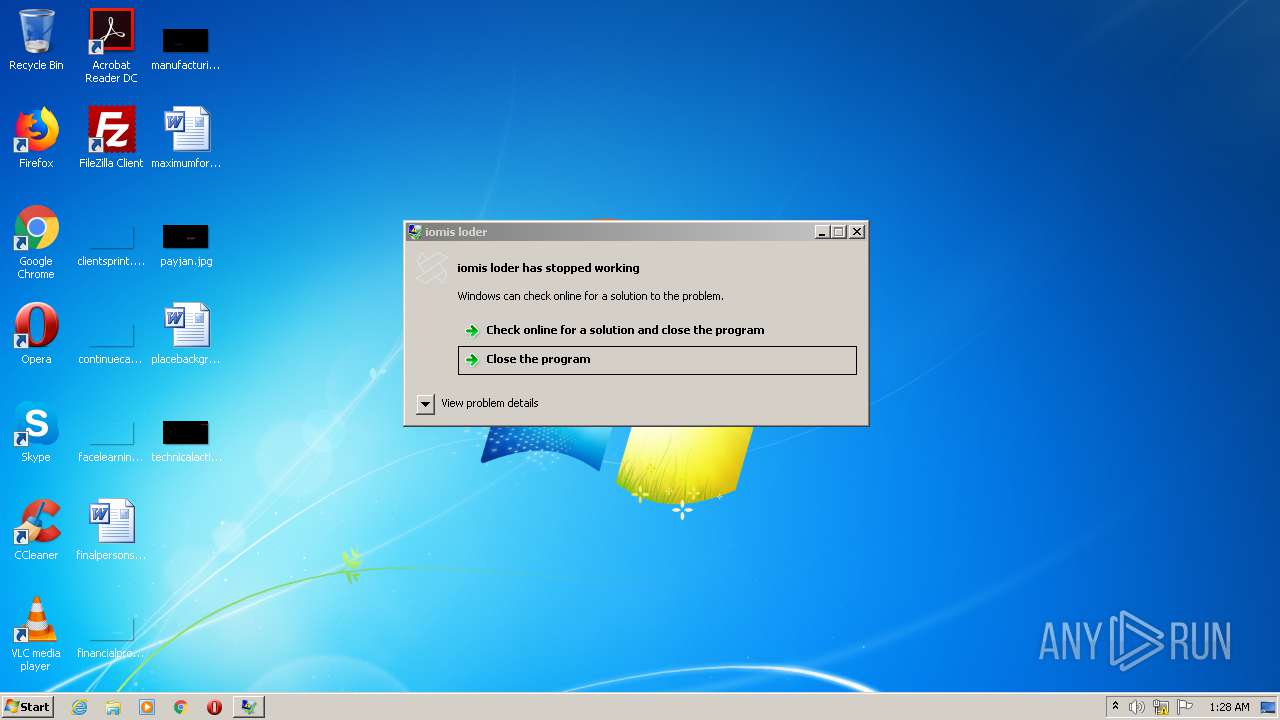
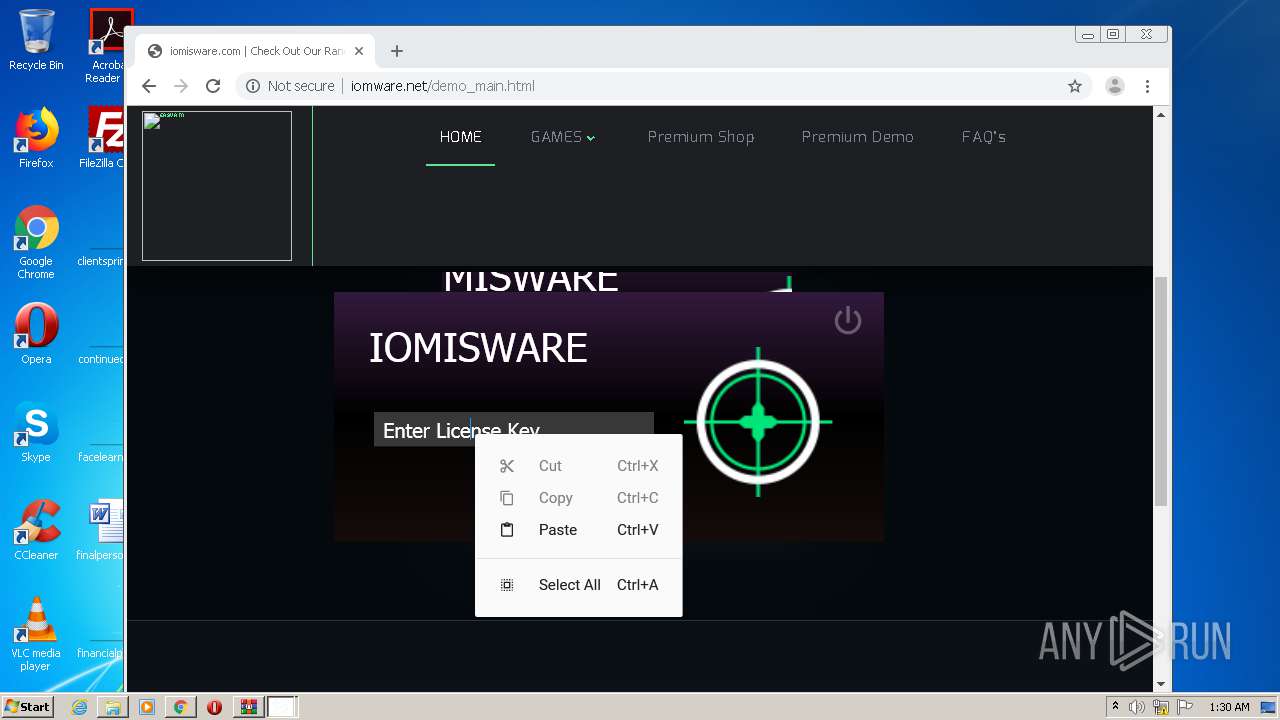
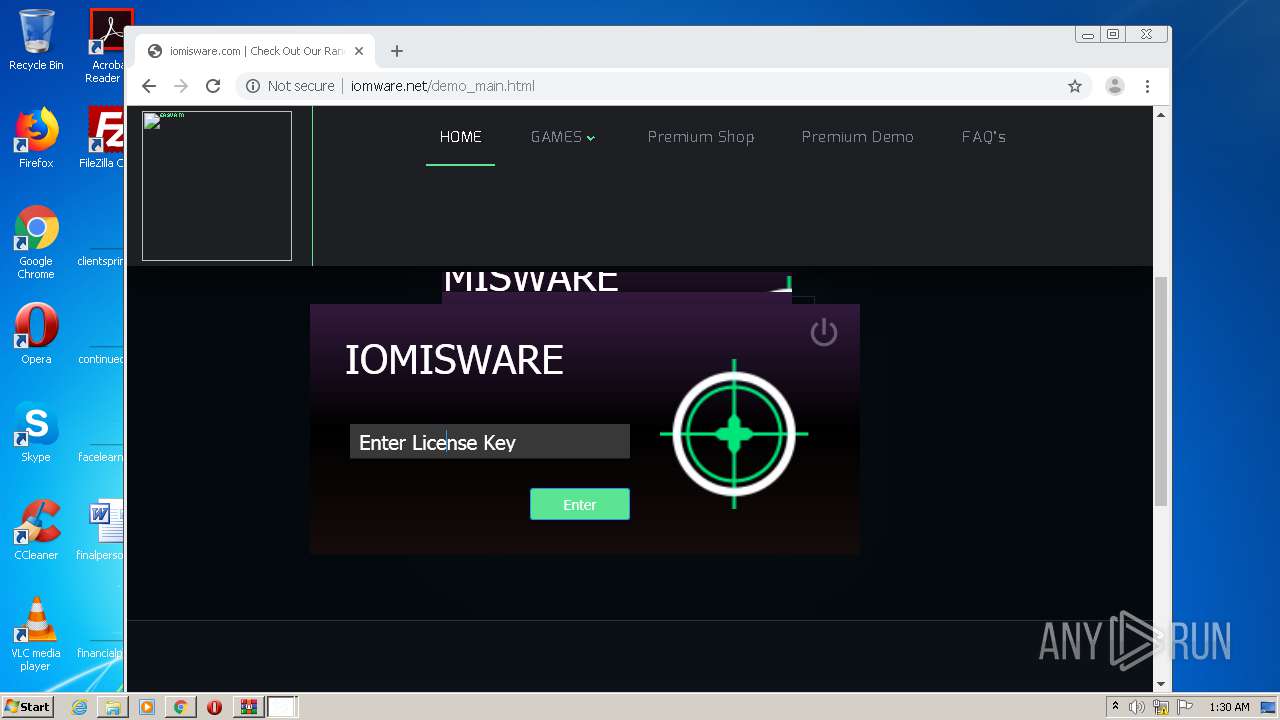
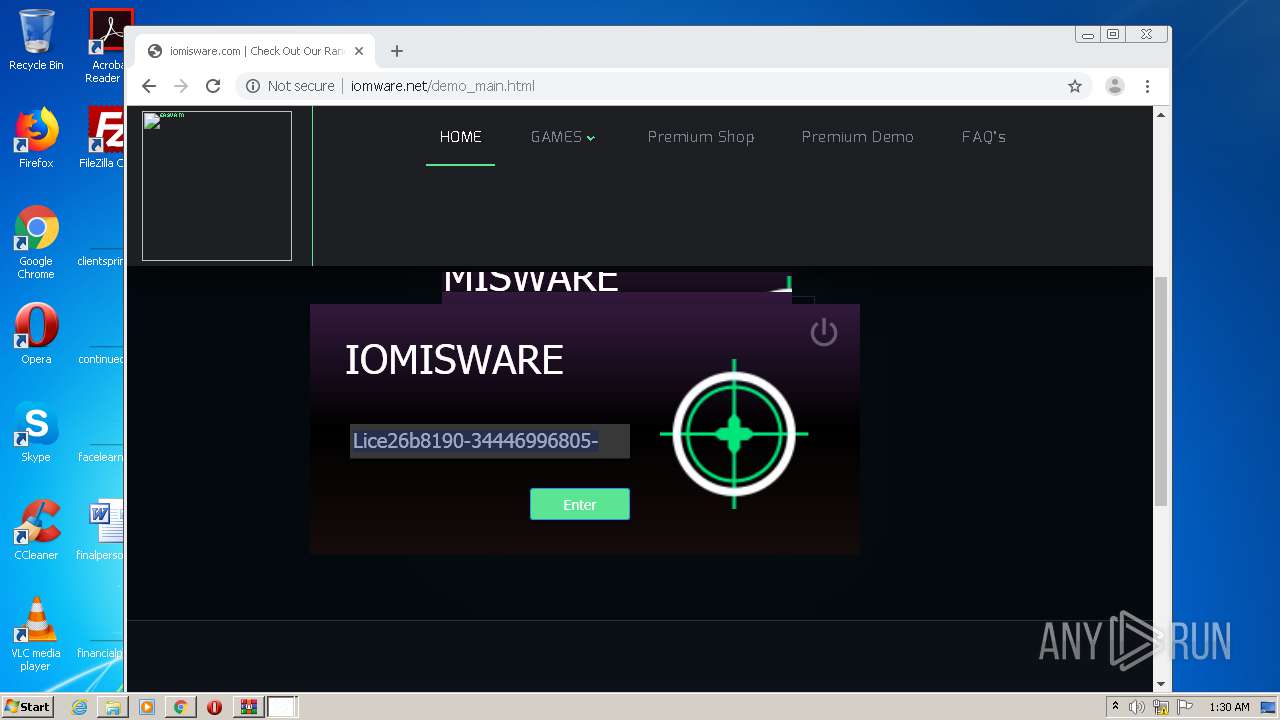
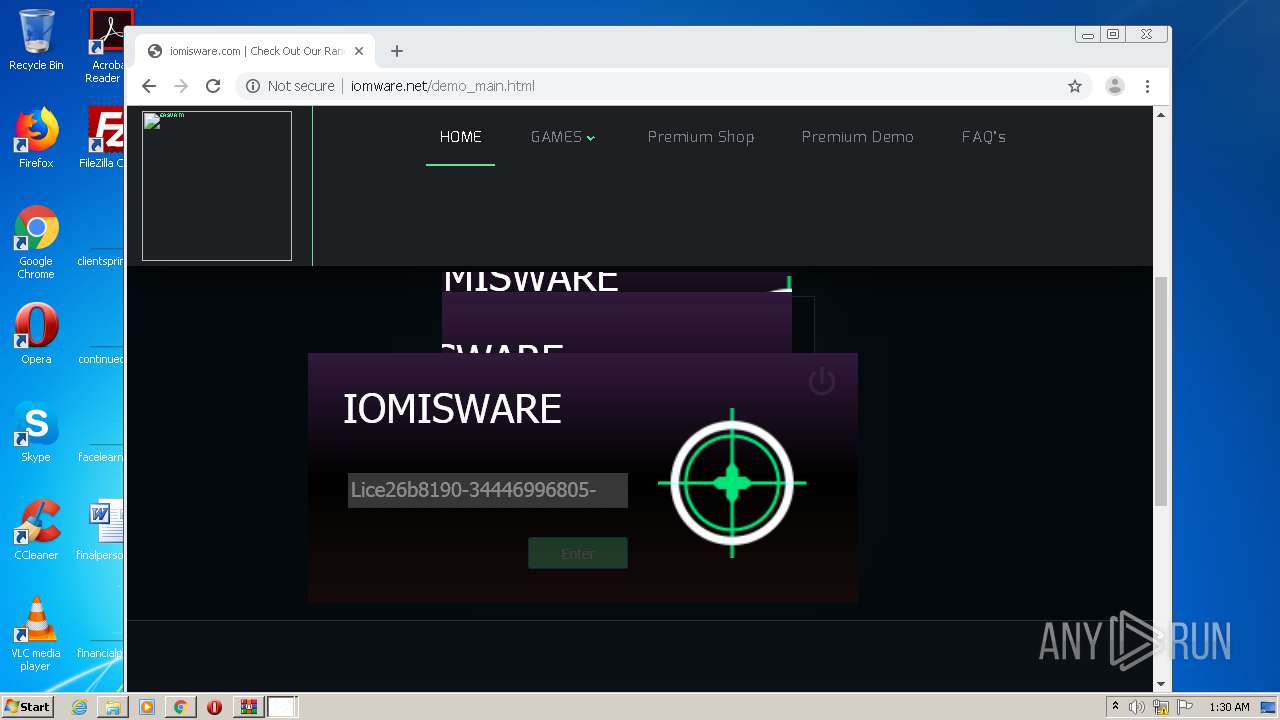
| FileDescription: | iomis loder |
| FileVersion: | 0.5.3.4 |
| InternalName: | iomis loder.exe |
| LegalCopyright: | Copyright © 2020 |
| LegalTrademarks: | - |
| OriginalFileName: | iomis loder.exe |
| ProductName: | iomis loder |
| ProductVersion: | 0.5.3.4 |
| AssemblyVersion: | 8.6.4.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 22-Apr-1958 01:59:02 |
| Debug artifacts: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | iomis loder |
| FileVersion: | 0.5.3.4 |
| InternalName: | iomis loder.exe |
| LegalCopyright: | Copyright © 2020 |
| LegalTrademarks: | - |
| OriginalFilename: | iomis loder.exe |
| ProductName: | iomis loder |
| ProductVersion: | 0.5.3.4 |
| Assembly Version: | 8.6.4.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 22-Apr-1958 01:59:02 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00693A74 | 0x00693C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.1387 |
.rsrc | 0x00696000 | 0x0001C588 | 0x0001C600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.96545 |
.reloc | 0x006B4000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 3.35901 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 3.35078 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 3.20084 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 2.59673 | 96752 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.85546 | 76 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
69
Monitored processes
28
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
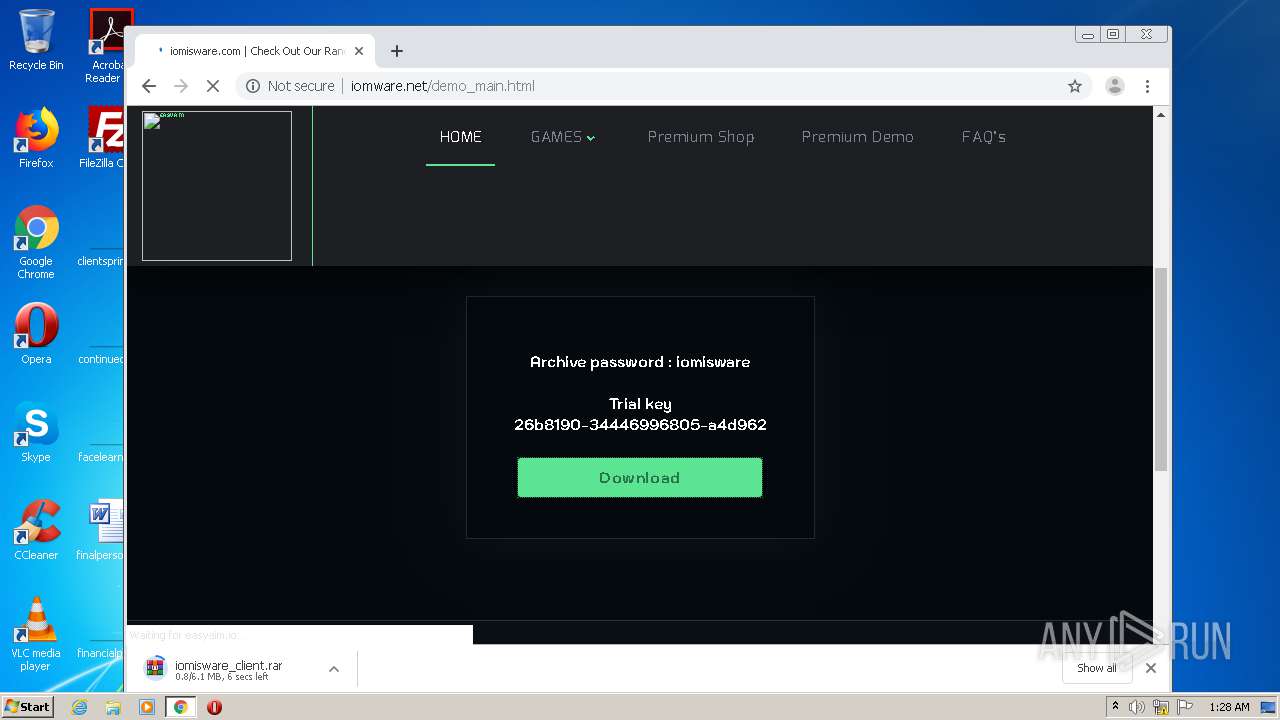
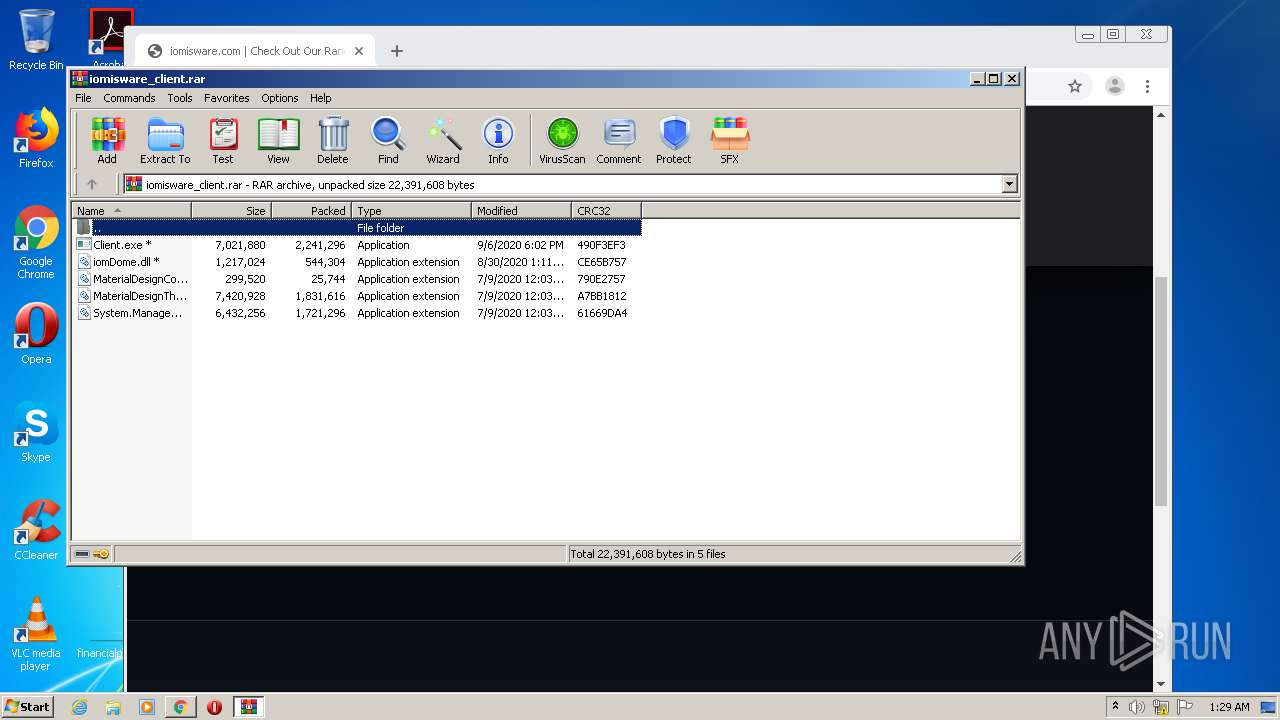
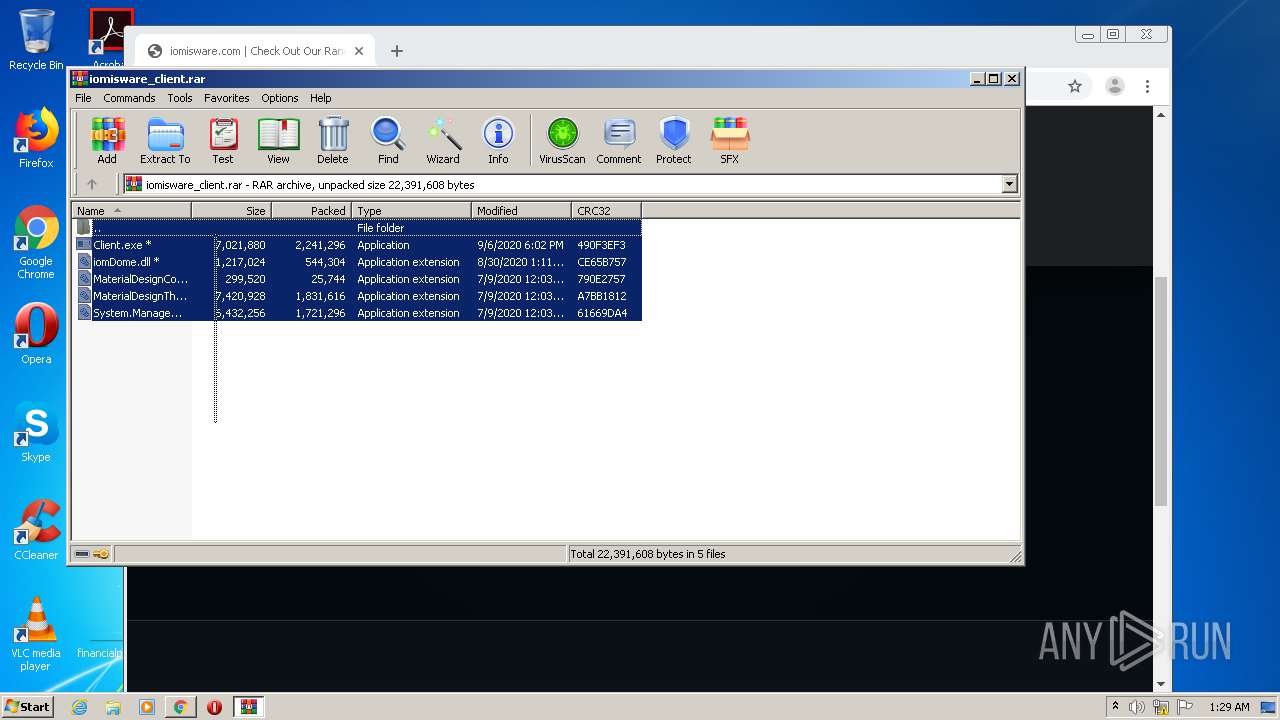
| 372 | "C:\Users\admin\Desktop\iomisware_client\Client.exe" | C:\Users\admin\Desktop\iomisware_client\Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: iomis loder Exit code: 0 Version: 0.5.3.4 Modules
| |||||||||||||||
| 556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,173544494382028713,622811413750000895,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=7963182305495491744 --mojo-platform-channel-handle=3564 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,173544494382028713,622811413750000895,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11103772678486502453 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2268 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,173544494382028713,622811413750000895,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=14330378699691305545 --mojo-platform-channel-handle=1232 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1680 | "C:\Users\admin\Desktop\iomisware_client\Client.exe" | C:\Users\admin\Desktop\iomisware_client\Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: iomis loder Exit code: 0 Version: 0.5.3.4 Modules
| |||||||||||||||
| 1716 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,173544494382028713,622811413750000895,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2848726617866139850 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3184 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
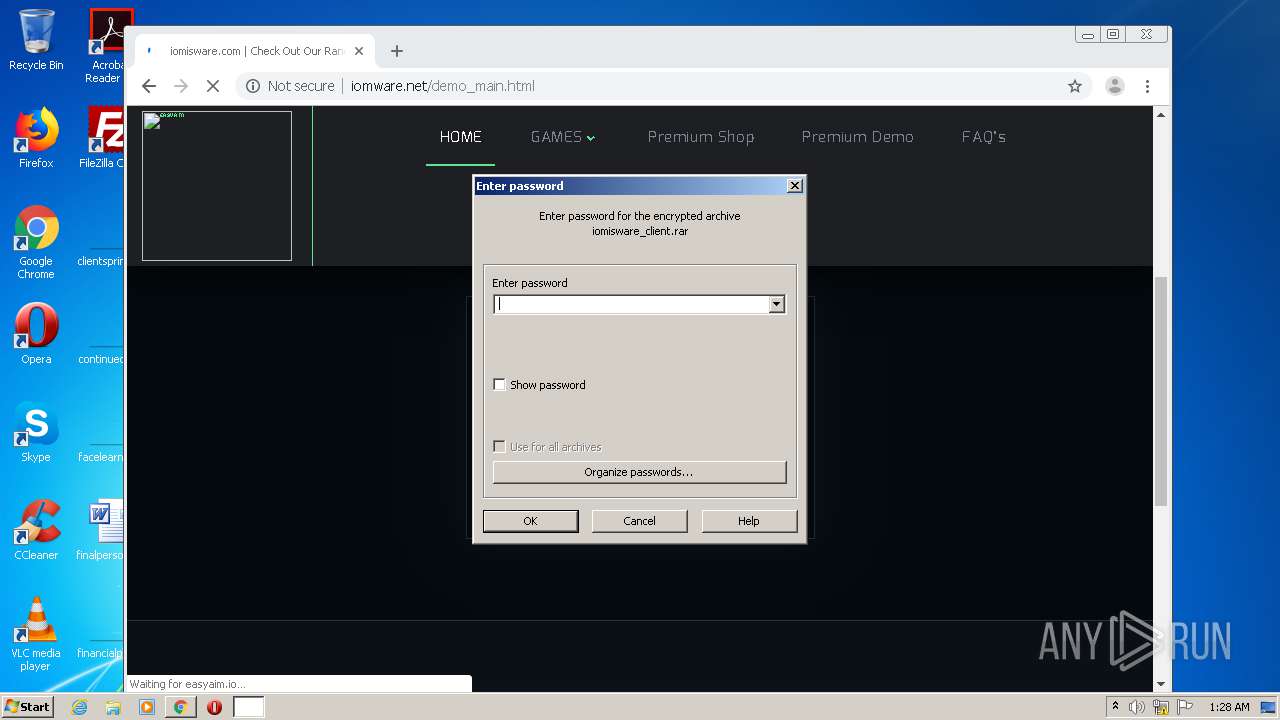
| 1852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\iomisware_client.rar" | C:\Program Files\WinRAR\WinRAR.exe | chrome.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,173544494382028713,622811413750000895,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=2822441231218825149 --mojo-platform-channel-handle=1196 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6699a9d0,0x6699a9e0,0x6699a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
4 361
Read events
4 030
Write events
325
Delete events
6
Modification events
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | Puebzr |
Value: 000000000D0000001B000000E54F1000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF6008B070AE9AD60100000000 | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000650000009500000070B740000F00000031000000FA9415007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E00650078006500000065007000610064002B002B002E00650078006500000065000000880115E1597752793800FEFFFFFFD31C5E774F345E7700C00500B8467E0164E8880174E88801E05ADF760000000068EA880168D55C770100000000000000C0687E0188E888015BB95A7701007E01D00000000000000000000000B5145E77B6E888010000000054155E7700000800000000007F155E770000000000000000F6E9880108E988010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000E72F5D773281ED760000000011000000483D4300403D4300000000000300D100DE07330080E9000091228F1334E988018291287680E988011CDC0000BD228F1348E98801B69C287620DC25034C06000060E9880190D725036CE9880111000000483D4300403D430060E98801B0D72503D0E90000E5228F1380E9880182912876D0E9880184E9880127952876000000001CDC2503ACE98801CD9428761CDC250358EA880190D72503E19428760000000090D7250358EA8801B4E988010F00000031000000FA9415007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E00650078006500000065007000610064002B002B002E00650078006500000065000000880115E1597752793800FEFFFFFFD31C5E774F345E7700C00500B8467E0164E8880174E88801E05ADF760000000068EA880168D55C770100000000000000C0687E0188E888015BB95A7701007E01D00000000000000000000000B5145E77B6E888010000000054155E7700000800000000007F155E770000000000000000F6E9880108E988010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000E72F5D773281ED760000000011000000483D4300403D4300000000000300D100DE07330080E9000091228F1334E988018291287680E988011CDC0000BD228F1348E98801B69C287620DC25034C06000060E9880190D725036CE9880111000000483D4300403D430060E98801B0D72503D0E90000E5228F1380E9880182912876D0E9880184E9880127952876000000001CDC2503ACE98801CD9428761CDC250358EA880190D72503E19428760000000090D7250358EA8801B4E988010F00000031000000FA9415007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E00650078006500000065007000610064002B002B002E00650078006500000065000000880115E1597752793800FEFFFFFFD31C5E774F345E7700C00500B8467E0164E8880174E88801E05ADF760000000068EA880168D55C770100000000000000C0687E0188E888015BB95A7701007E01D00000000000000000000000B5145E77B6E888010000000054155E7700000800000000007F155E770000000000000000F6E9880108E988010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000E72F5D773281ED760000000011000000483D4300403D4300000000000300D100DE07330080E9000091228F1334E988018291287680E988011CDC0000BD228F1348E98801B69C287620DC25034C06000060E9880190D725036CE9880111000000483D4300403D430060E98801B0D72503D0E90000E5228F1380E9880182912876D0E9880184E9880127952876000000001CDC2503ACE98801CD9428761CDC250358EA880190D72503E19428760000000090D7250358EA8801B4E98801 | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Tbbtyr Puebzr.yax |
Value: 00000000080000000000000007000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF5052B270AE9AD60100000000 | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000003100000000000000300000000F000000000000000F0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000004D35D03399CBC75D066440300030000000000000D000000D0694403AF020000D066440334D35D03431928767F694403186727035E000000D066440358A02F03AF020000B8F9277660891C0260891C0244D35D036419287658A02F0318672703DCD75D03BF43287658A02F030000000000000000FFFFFFFF0000000000000000000000001867270330672703186727035A6727030000000000000000000000000000287618B03C03C06A270328D85D03BF43287618B03C030000000000000000FFFFFFFF000000000000000000000000C06A2703D86A2703C06A2703026B2703DA1A000086EC2701E8D35D0333AB5D7786E8FCAF0A0C00001027000017000000995602001CD45D03F8AA5D779956020086EC27013CD45D0378E62503BCD45D0300000000A40100007CD40000991F5A112CD45D03829128767CD45D0330D45D03279528760000000004EB250358D45D03CD94287604EB250304D55D0378E62503E19428760000000078E6250304D55D0360D45D030F000000000000000F0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000004D35D03399CBC75D066440300030000000000000D000000D0694403AF020000D066440334D35D03431928767F694403186727035E000000D066440358A02F03AF020000B8F9277660891C0260891C0244D35D036419287658A02F0318672703DCD75D03BF43287658A02F030000000000000000FFFFFFFF0000000000000000000000001867270330672703186727035A6727030000000000000000000000000000287618B03C03C06A270328D85D03BF43287618B03C030000000000000000FFFFFFFF000000000000000000000000C06A2703D86A2703C06A2703026B2703DA1A000086EC2701E8D35D0333AB5D7786E8FCAF0A0C00001027000017000000995602001CD45D03F8AA5D779956020086EC27013CD45D0378E62503BCD45D0300000000A40100007CD40000991F5A112CD45D03829128767CD45D0330D45D03279528760000000004EB250358D45D03CD94287604EB250304D55D0378E62503E19428760000000078E6250304D55D0360D45D030F000000000000000F0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000004D35D03399CBC75D066440300030000000000000D000000D0694403AF020000D066440334D35D03431928767F694403186727035E000000D066440358A02F03AF020000B8F9277660891C0260891C0244D35D036419287658A02F0318672703DCD75D03BF43287658A02F030000000000000000FFFFFFFF0000000000000000000000001867270330672703186727035A6727030000000000000000000000000000287618B03C03C06A270328D85D03BF43287618B03C030000000000000000FFFFFFFF000000000000000000000000C06A2703D86A2703C06A2703026B2703DA1A000086EC2701E8D35D0333AB5D7786E8FCAF0A0C00001027000017000000995602001CD45D03F8AA5D779956020086EC27013CD45D0378E62503BCD45D0300000000A40100007CD40000991F5A112CD45D03829128767CD45D0330D45D03279528760000000004EB250358D45D03CD94287604EB250304D55D0378E62503E19428760000000078E6250304D55D0360D45D03 | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Tbbtyr Puebzr.yax |
Value: 00000000080000000000000008000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF5052B270AE9AD60100000000 | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000003100000000000000310000000F000000000000000F0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000004D35D03399CBC75D066440300030000000000000D000000D0694403AF020000D066440334D35D03431928767F694403186727035E000000D066440358A02F03AF020000B8F9277660891C0260891C0244D35D036419287658A02F0318672703DCD75D03BF43287658A02F030000000000000000FFFFFFFF0000000000000000000000001867270330672703186727035A6727030000000000000000000000000000287618B03C03C06A270328D85D03BF43287618B03C030000000000000000FFFFFFFF000000000000000000000000C06A2703D86A2703C06A2703026B2703DA1A000086EC2701E8D35D0333AB5D7786E8FCAF0A0C00001027000017000000995602001CD45D03F8AA5D779956020086EC27013CD45D0378E62503BCD45D0300000000A40100007CD40000991F5A112CD45D03829128767CD45D0330D45D03279528760000000004EB250358D45D03CD94287604EB250304D55D0378E62503E19428760000000078E6250304D55D0360D45D030F000000000000000F0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000004D35D03399CBC75D066440300030000000000000D000000D0694403AF020000D066440334D35D03431928767F694403186727035E000000D066440358A02F03AF020000B8F9277660891C0260891C0244D35D036419287658A02F0318672703DCD75D03BF43287658A02F030000000000000000FFFFFFFF0000000000000000000000001867270330672703186727035A6727030000000000000000000000000000287618B03C03C06A270328D85D03BF43287618B03C030000000000000000FFFFFFFF000000000000000000000000C06A2703D86A2703C06A2703026B2703DA1A000086EC2701E8D35D0333AB5D7786E8FCAF0A0C00001027000017000000995602001CD45D03F8AA5D779956020086EC27013CD45D0378E62503BCD45D0300000000A40100007CD40000991F5A112CD45D03829128767CD45D0330D45D03279528760000000004EB250358D45D03CD94287604EB250304D55D0378E62503E19428760000000078E6250304D55D0360D45D030F000000000000000F0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000004D35D03399CBC75D066440300030000000000000D000000D0694403AF020000D066440334D35D03431928767F694403186727035E000000D066440358A02F03AF020000B8F9277660891C0260891C0244D35D036419287658A02F0318672703DCD75D03BF43287658A02F030000000000000000FFFFFFFF0000000000000000000000001867270330672703186727035A6727030000000000000000000000000000287618B03C03C06A270328D85D03BF43287618B03C030000000000000000FFFFFFFF000000000000000000000000C06A2703D86A2703C06A2703026B2703DA1A000086EC2701E8D35D0333AB5D7786E8FCAF0A0C00001027000017000000995602001CD45D03F8AA5D779956020086EC27013CD45D0378E62503BCD45D0300000000A40100007CD40000991F5A112CD45D03829128767CD45D0330D45D03279528760000000004EB250358D45D03CD94287604EB250304D55D0378E62503E19428760000000078E6250304D55D0360D45D03 | |||
| (PID) Process: | (2528) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2528) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2528) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2528) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
Executable files
5
Suspicious files
42
Text files
98
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F7A68AA-9E0.pma | — | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\8747058f-5443-41de-a14f-922a59cc7f7b.tmp | — | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000046.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1abfc7.TMP | text | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF1ac034.TMP | text | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1abfc7.TMP | text | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1abff6.TMP | text | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF1ac053.TMP | text | |
MD5:— | SHA256:— | |||
| 2528 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
52
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
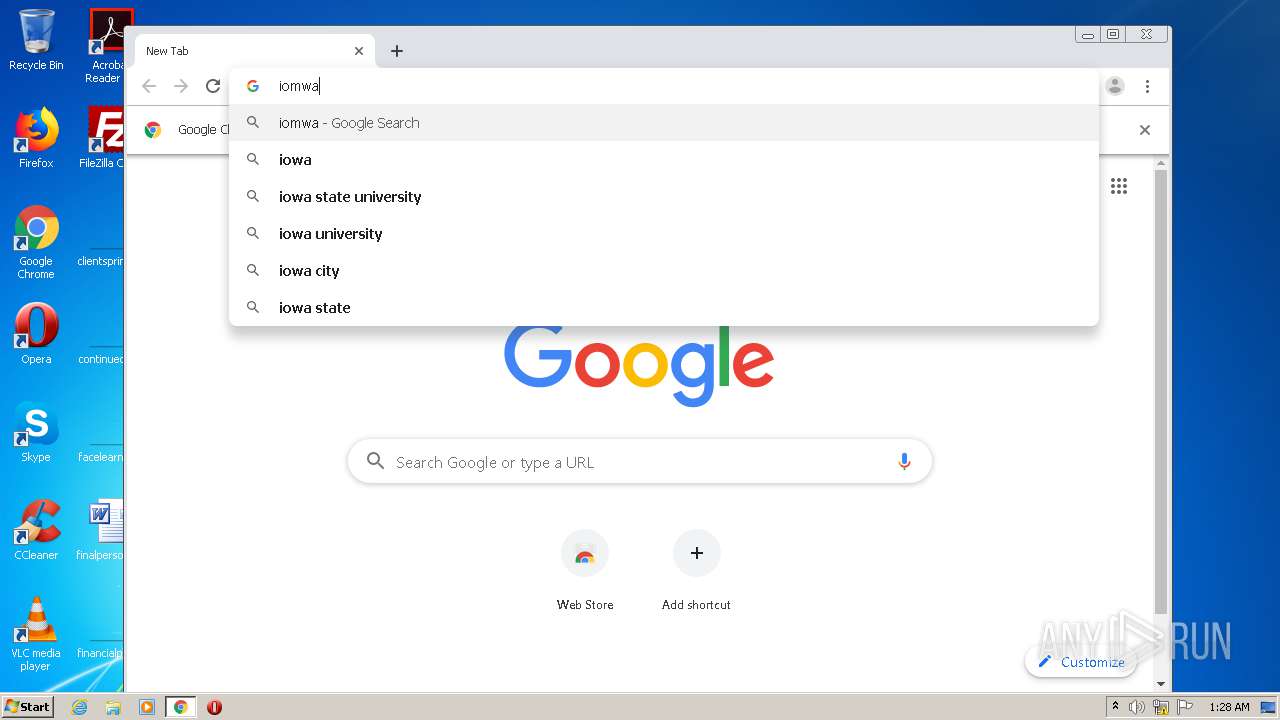
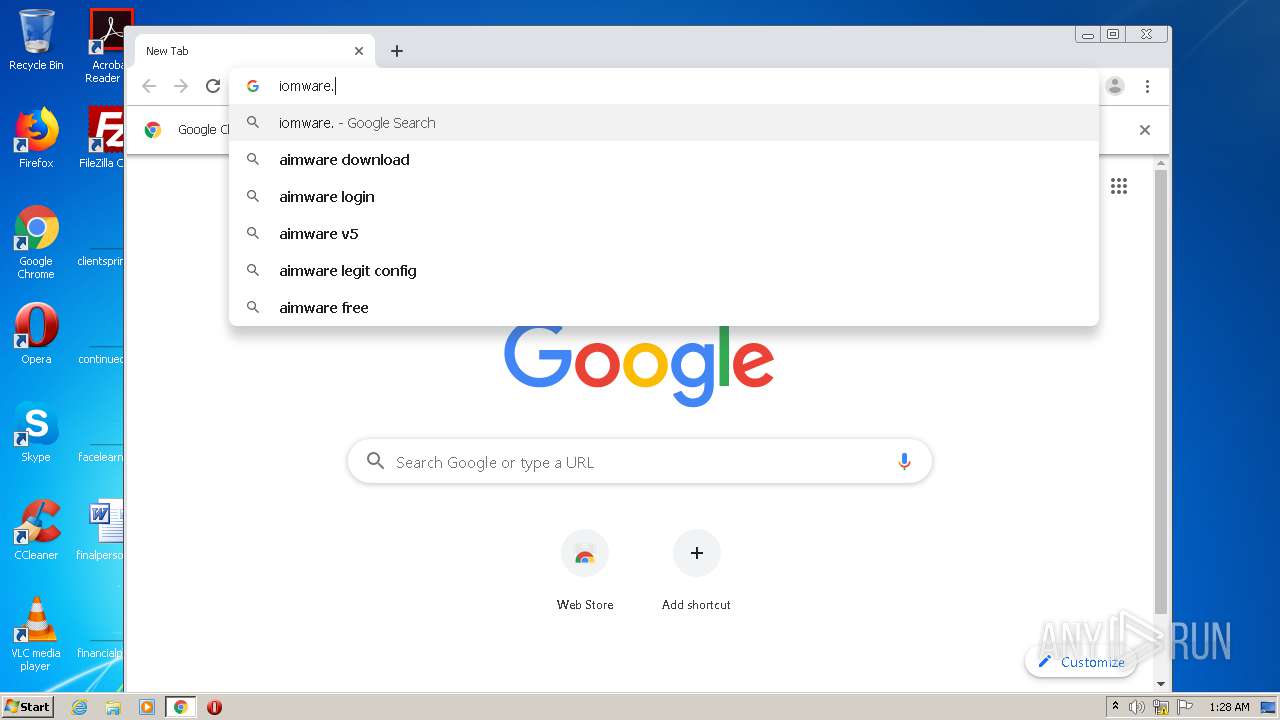
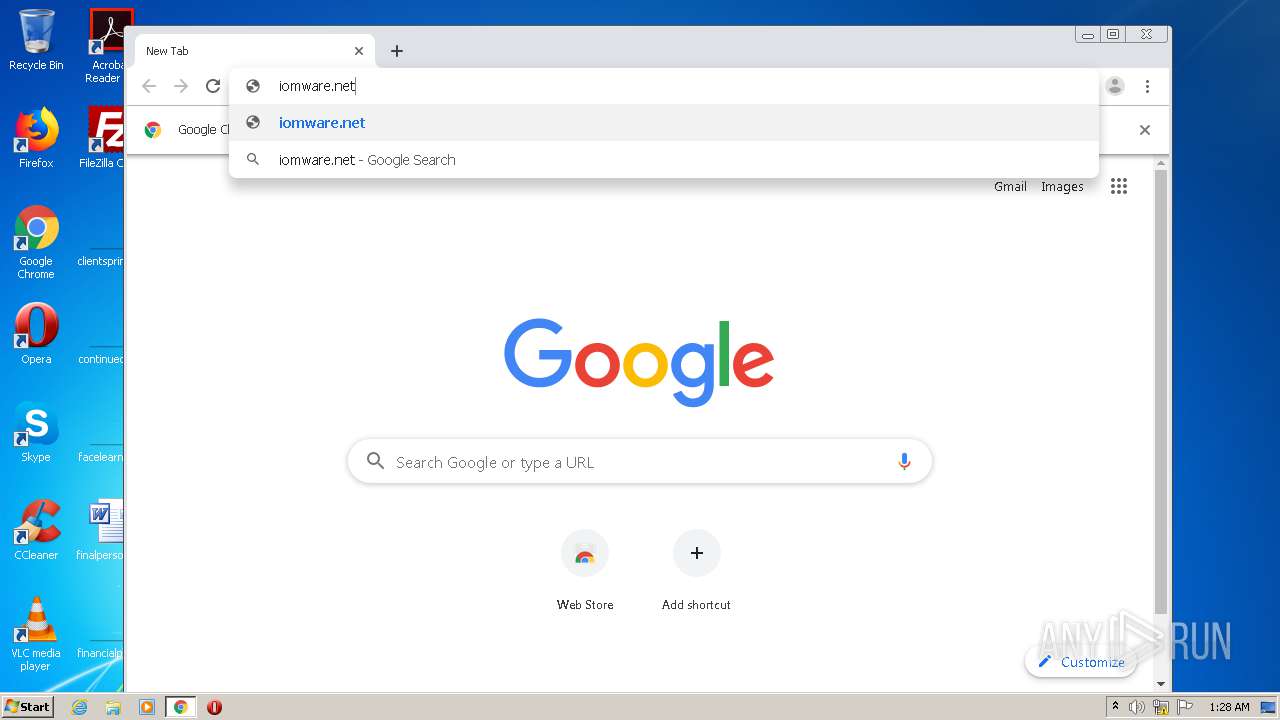
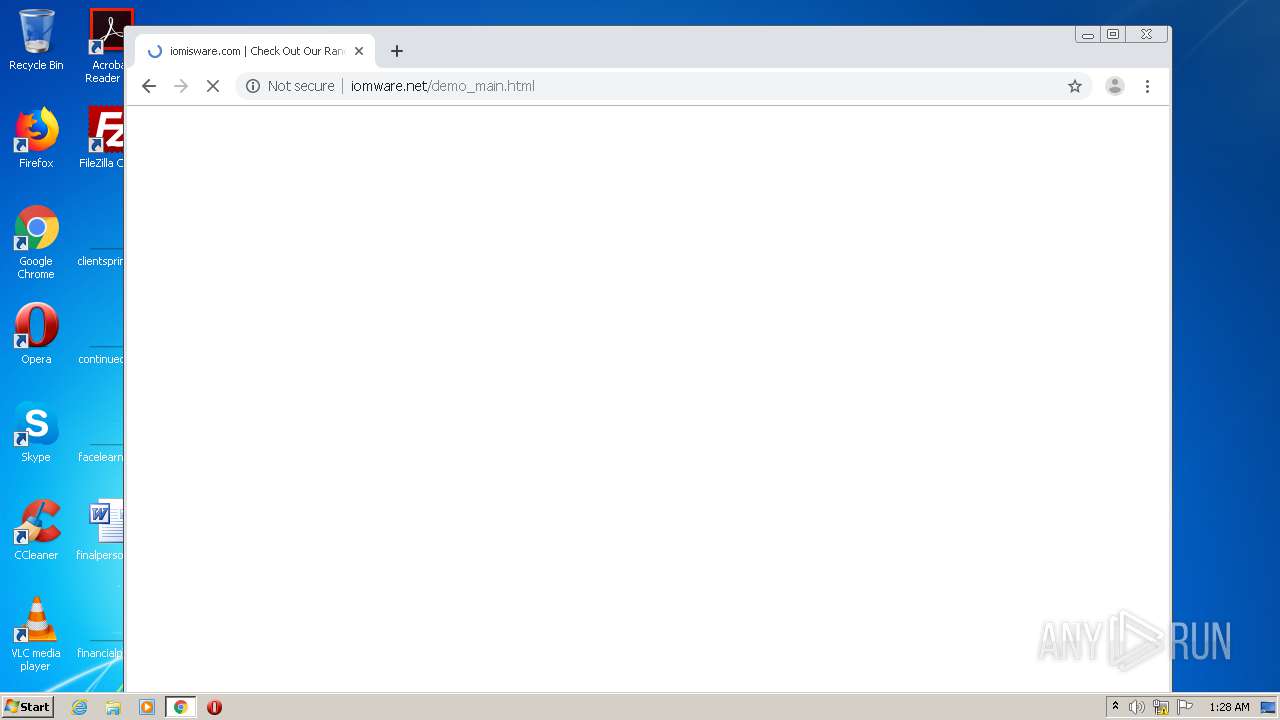
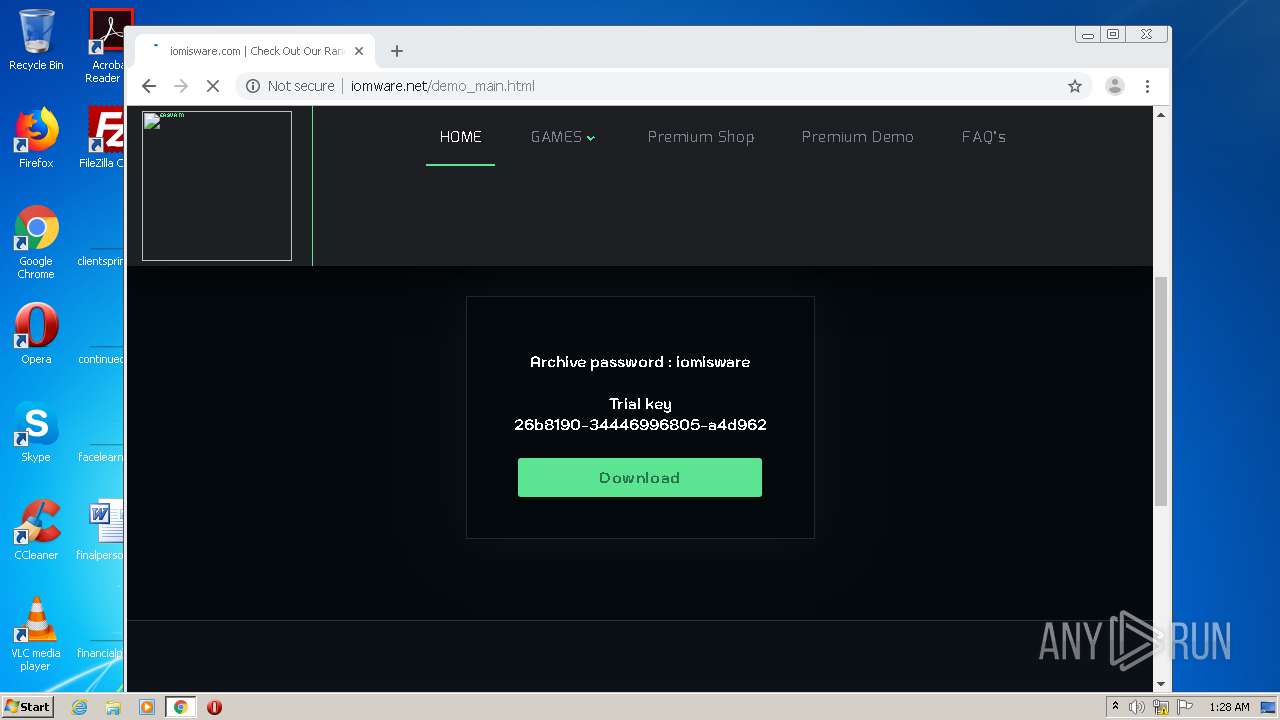
2116 | chrome.exe | GET | — | 164.132.77.139:80 | http://iomware.net/wp-content/cache/minify/5e3a8.js | FR | — | — | malicious |
2116 | chrome.exe | GET | 200 | 79.137.96.21:80 | http://iomisware.com/wp-content/uploads/2020/03/easyaim-Green-logo.png.webp | IE | html | 1.22 Kb | suspicious |
2116 | chrome.exe | GET | 200 | 164.132.77.139:80 | http://iomware.net/wp-content/uploads/2020/03/page-title-default-3.jpg | FR | image | 105 Kb | malicious |
2116 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJ9L2KGL92BpjF3kAtaDtxauTmhgQUPdNQpdagre7zSmAKZdMh1Pj41g8CEAqN7HPiQ2%2F4c3rdXE3uHG8%3D | US | der | 471 b | whitelisted |
2116 | chrome.exe | GET | 200 | 164.132.77.139:80 | http://iomware.net/wp-content/uploads/2020/03/easyaim-Green-logo.png.webp | FR | image | 4.12 Kb | malicious |
1680 | Client.exe | GET | 200 | 195.2.92.143:80 | http://195.2.92.143/select_games.php | RU | text | 476 b | malicious |
1052 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA7yTSbUNi7CXXtef0luXqk%3D | US | der | 279 b | whitelisted |
2116 | chrome.exe | GET | 404 | 164.132.77.139:80 | http://iomware.net/wp-content/cache/minify/5e3a8.js | FR | html | 144 Kb | malicious |
2116 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
1680 | Client.exe | GET | 200 | 195.2.92.143:80 | http://195.2.92.143/init.php?from_=WarThunder | RU | text | 15 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2116 | chrome.exe | 216.58.206.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
2116 | chrome.exe | 216.58.210.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2116 | chrome.exe | 164.132.77.139:80 | iomware.net | OVH SAS | FR | malicious |
2116 | chrome.exe | 151.101.2.133:443 | fast.a.klaviyo.com | Fastly | US | malicious |
2116 | chrome.exe | 147.75.32.125:443 | script.hotjar.com | Packet Host, Inc. | US | unknown |
2116 | chrome.exe | 172.217.21.226:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
2116 | chrome.exe | 172.217.22.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2116 | chrome.exe | 142.250.74.206:443 | ogs.google.com | Google Inc. | US | whitelisted |
2116 | chrome.exe | 172.217.22.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
2116 | chrome.exe | 172.67.199.33:443 | easyaim.io | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ogs.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
iomware.net |
| malicious |