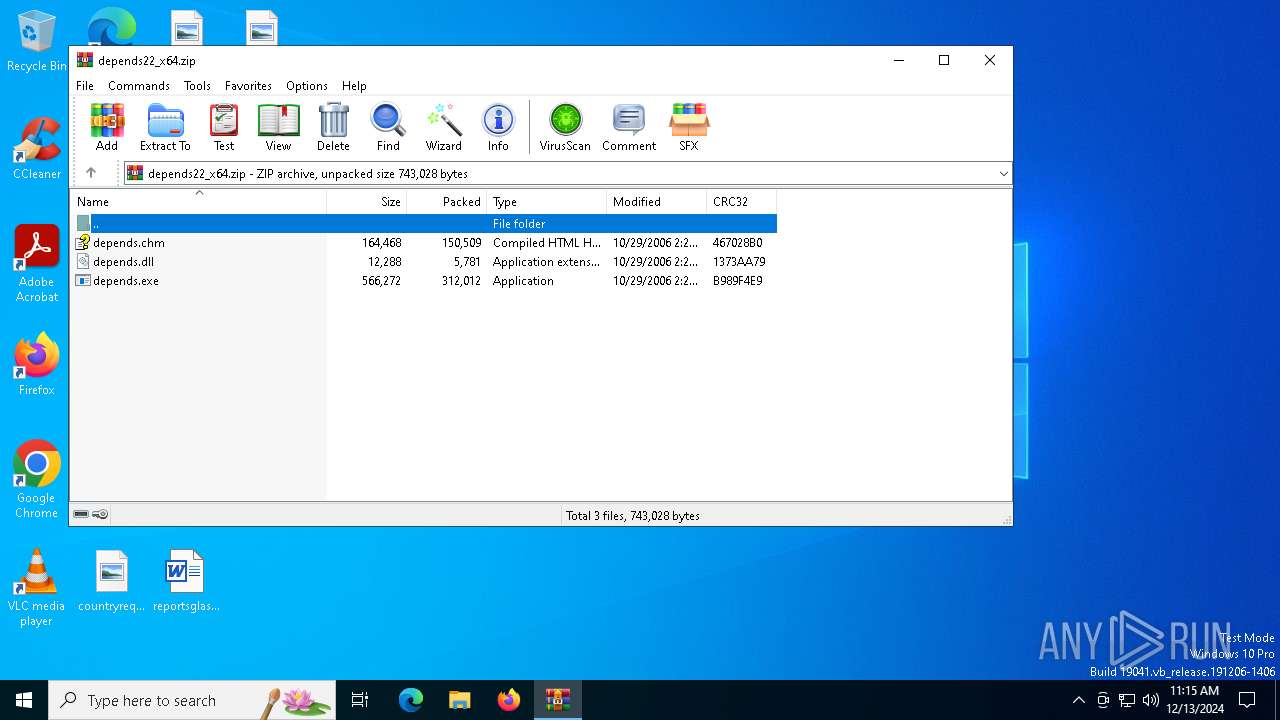
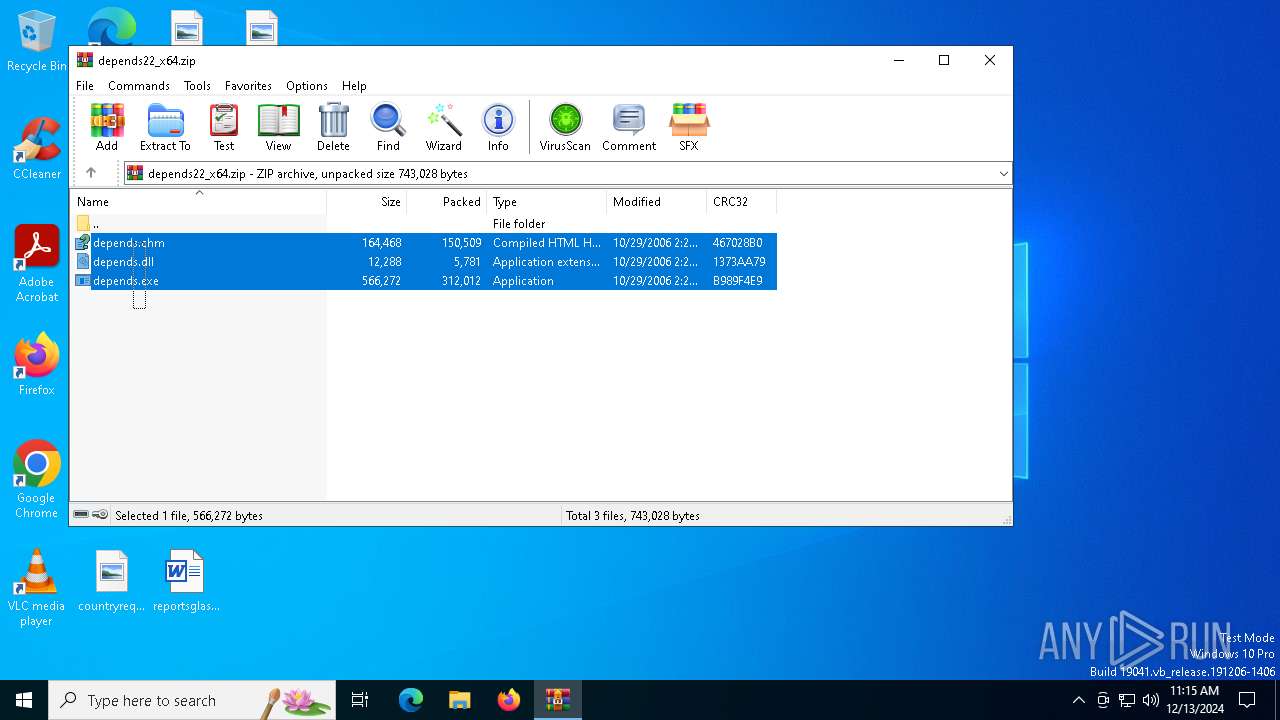
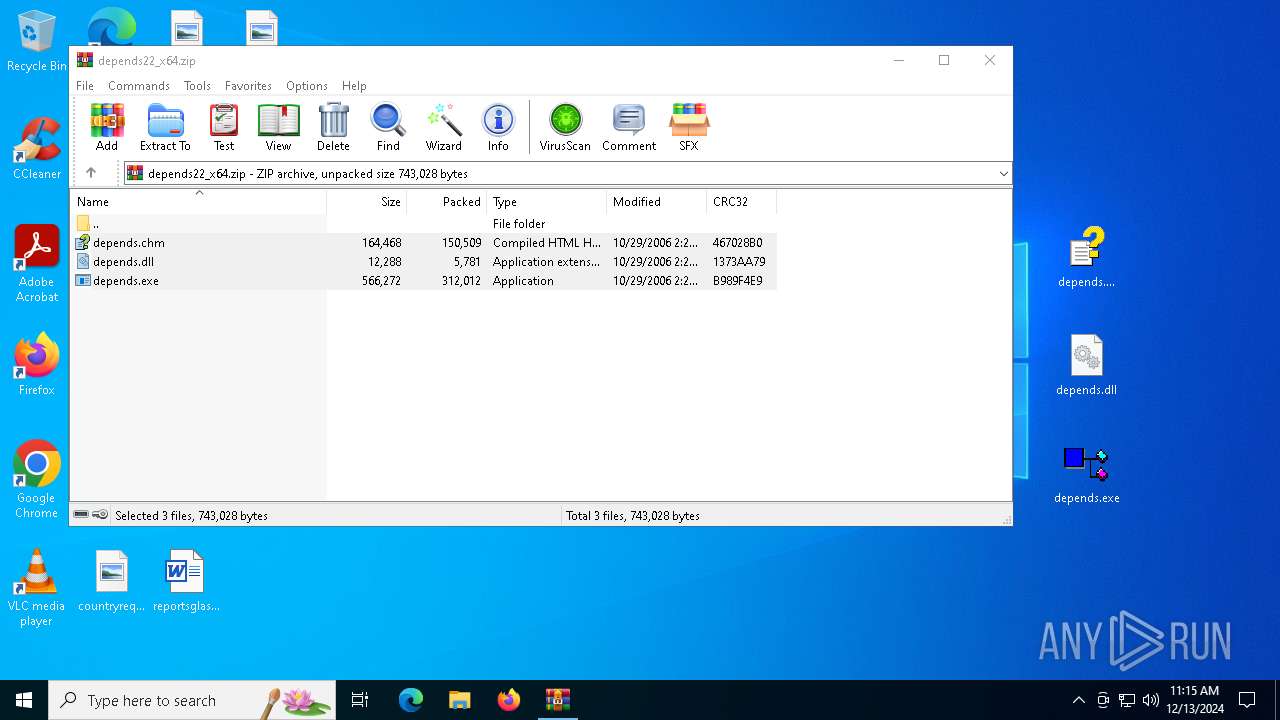
| File name: | depends22_x64.zip |
| Full analysis: | https://app.any.run/tasks/e244dbac-a82c-4b59-9266-88fb9cd8fdc2 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 11:15:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7975054E322794CD332D5F1C00EEEC5F |
| SHA1: | 4831D2A8376D64110FF9CD18799FE6C69509D3EA |
| SHA256: | 35DB68A613874A2E8C1422EB0EA7861F825FC71717D46DABF1F249CE9634B4F1 |
| SSDEEP: | 12288:NdvBbKbWHrH1rYkasCk/Xyid/HhdvBhKCD+UrH1dY:rJwcYQCaXyq/nH5CSY |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6396)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6396)
Starts a Microsoft application from unusual location
- depends.exe (PID: 7128)
- depends.exe (PID: 3152)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6396)
The sample compiled with english language support
- WinRAR.exe (PID: 6396)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6396)
Manual execution by a user
- depends.exe (PID: 7128)
- depends.exe (PID: 3152)
Reads the computer name
- depends.exe (PID: 7128)
Checks supported languages
- depends.exe (PID: 7128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2006:10:29 02:20:00 |
| ZipCRC: | 0x467028b0 |
| ZipCompressedSize: | 150509 |
| ZipUncompressedSize: | 164468 |
| ZipFileName: | depends.chm |
Total processes
127
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3152 | "C:\Users\admin\Desktop\depends.exe" | C:\Users\admin\Desktop\depends.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Dependency Walker for Win64 (x64) Version: 2.2.6000 Modules
| |||||||||||||||
| 6396 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\depends22_x64.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7128 | "C:\Users\admin\Desktop\depends.exe" | C:\Users\admin\Desktop\depends.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Dependency Walker for Win64 (x64) Version: 2.2.6000 Modules
| |||||||||||||||
Total events
1 822
Read events
1 814
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\depends22_x64.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6396.35534\depends.chm | chm | |
MD5:D23E88EB8928034285595FE5D67485A0 | SHA256:E5A4E001FBFE731B5D8B9D2046C57FA1786599364366704A800D59239D0C064D | |||
| 6396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6396.35534\depends.exe | executable | |
MD5:FC9015FC4596D90BFE0547AB96CB21B3 | SHA256:57C483DC985A9757501993E969C2A7043C26517F97FD49A42B33D2D6A4193D8B | |||
| 6396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6396.35534\depends.dll | executable | |
MD5:0D50C42B88C74468D05EC4E228A5DAD3 | SHA256:7A5CAE7605AE5D8C8AEE3E6D8E77E455537B636B395B8F00AEBE17BF8B228770 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6212 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6212 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7012 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2224 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.139:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3976 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |