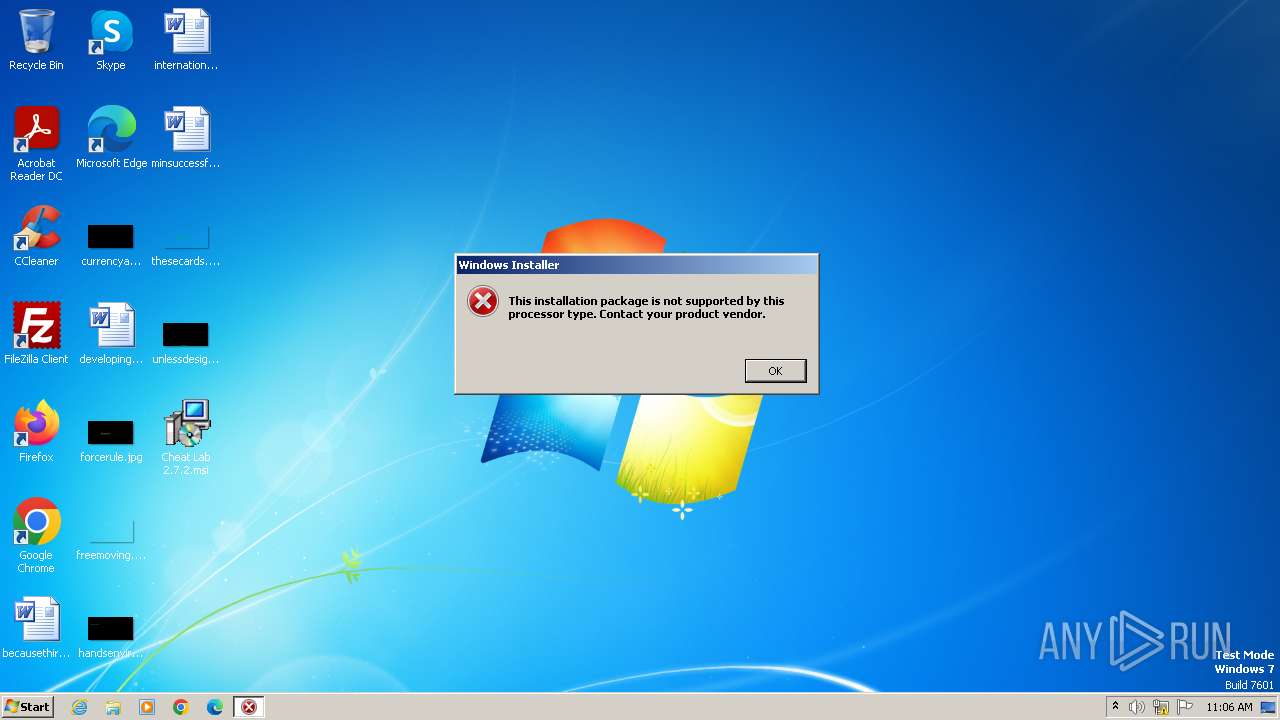
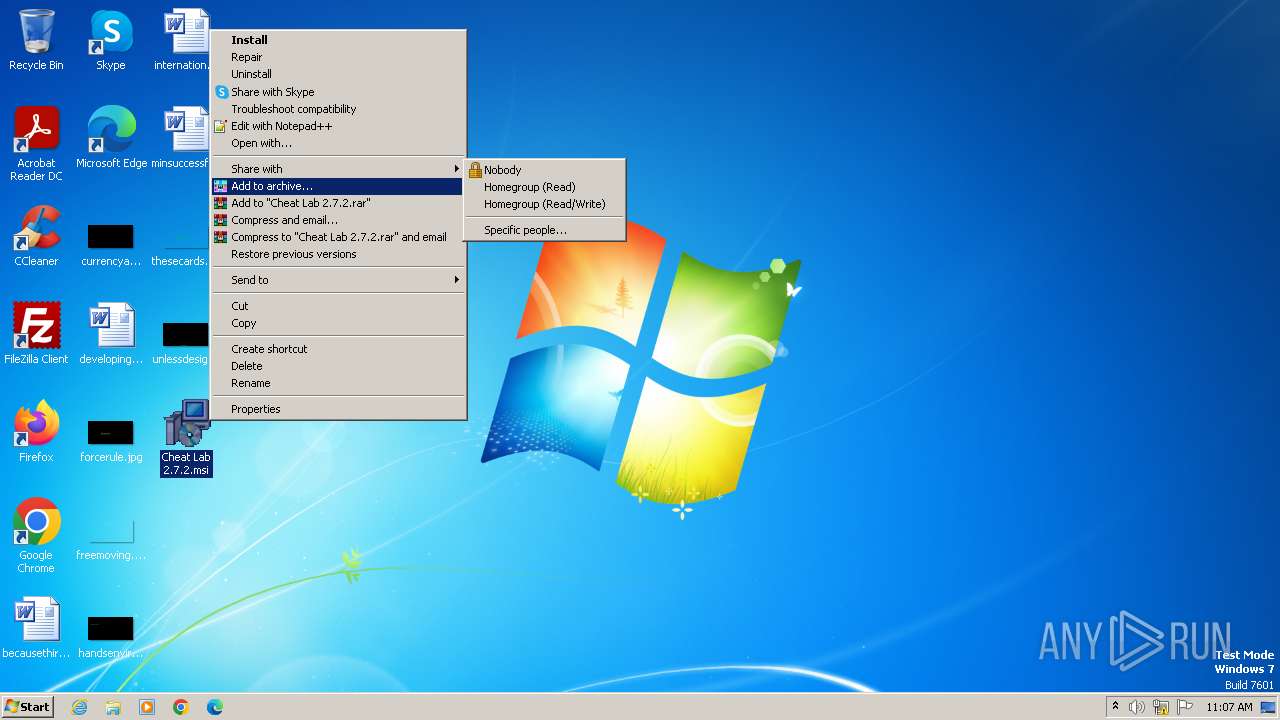
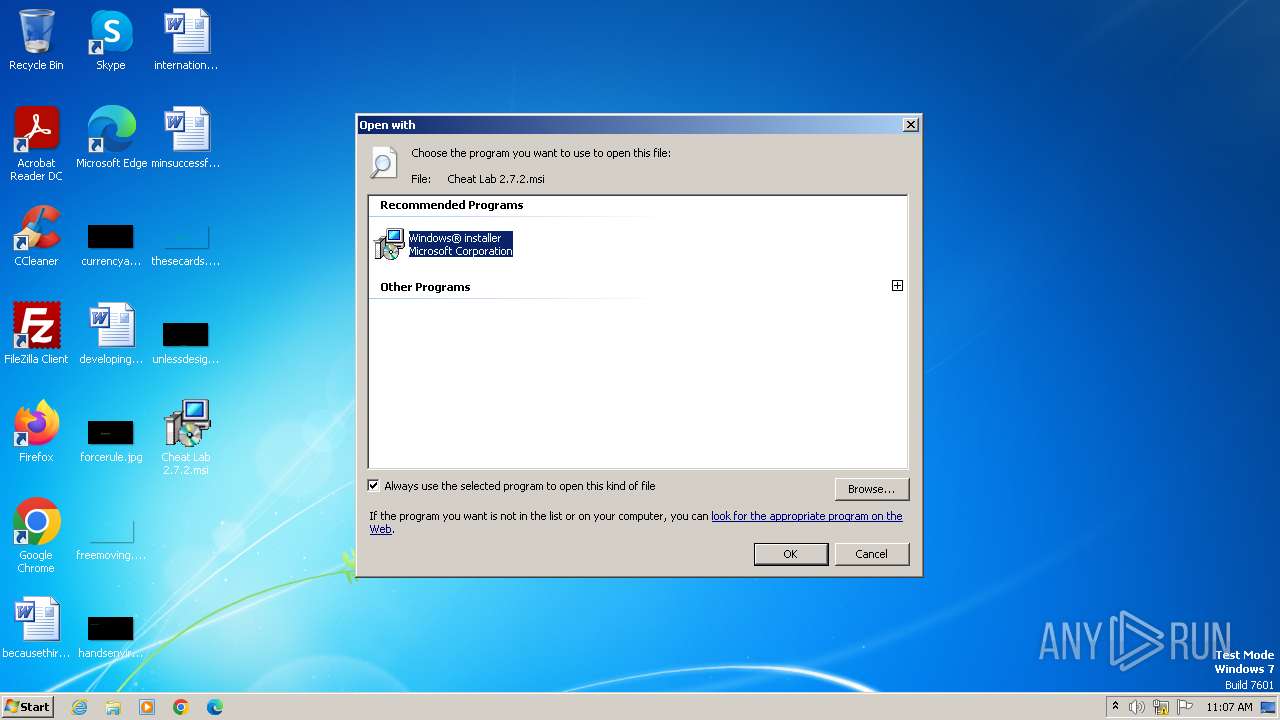
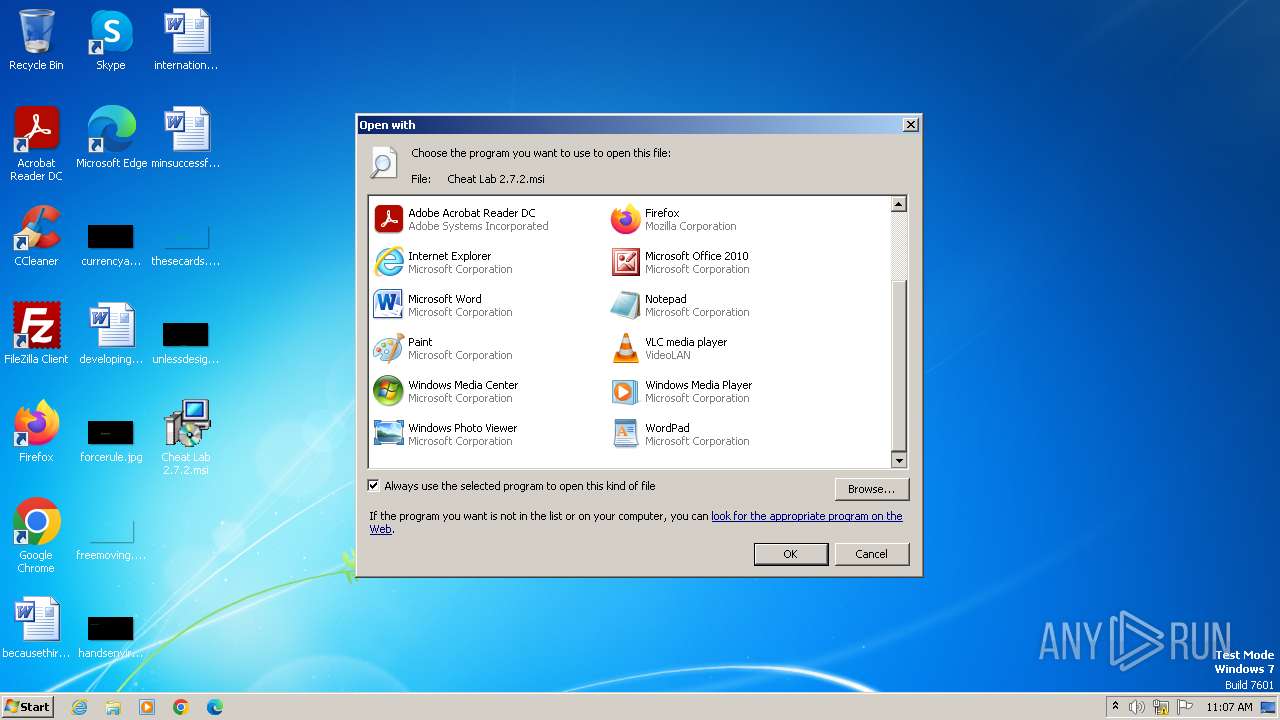
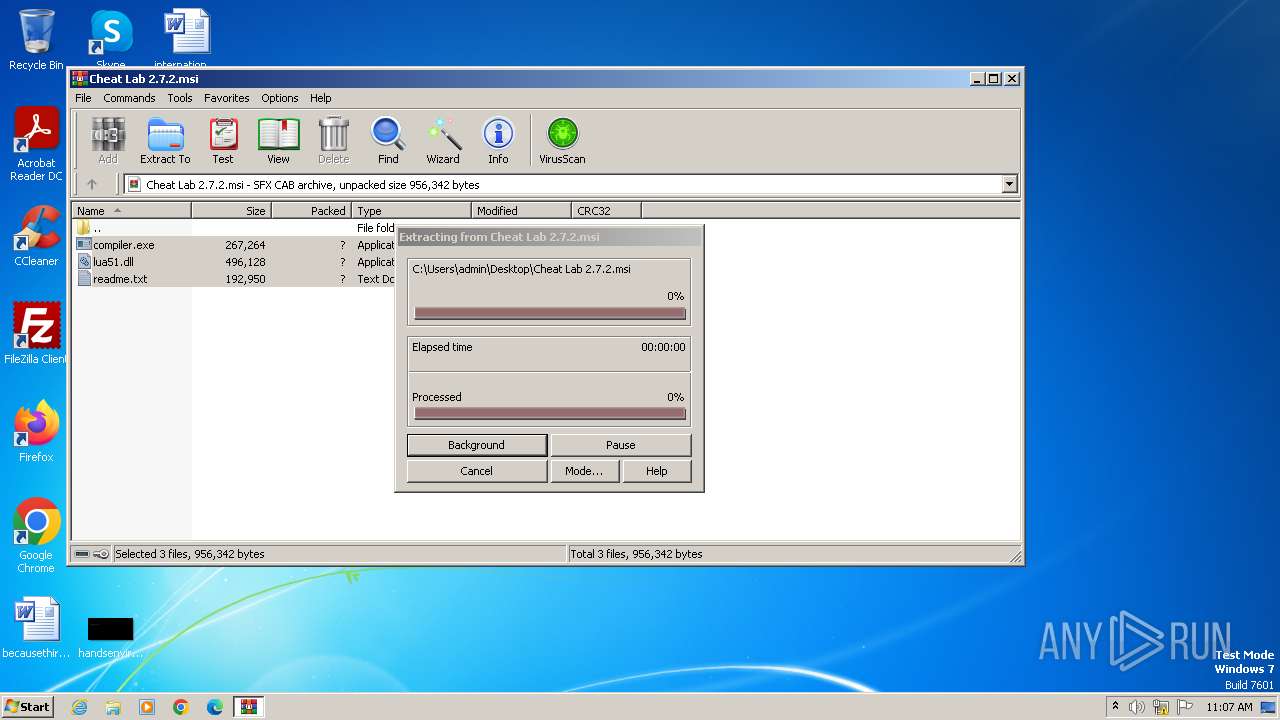
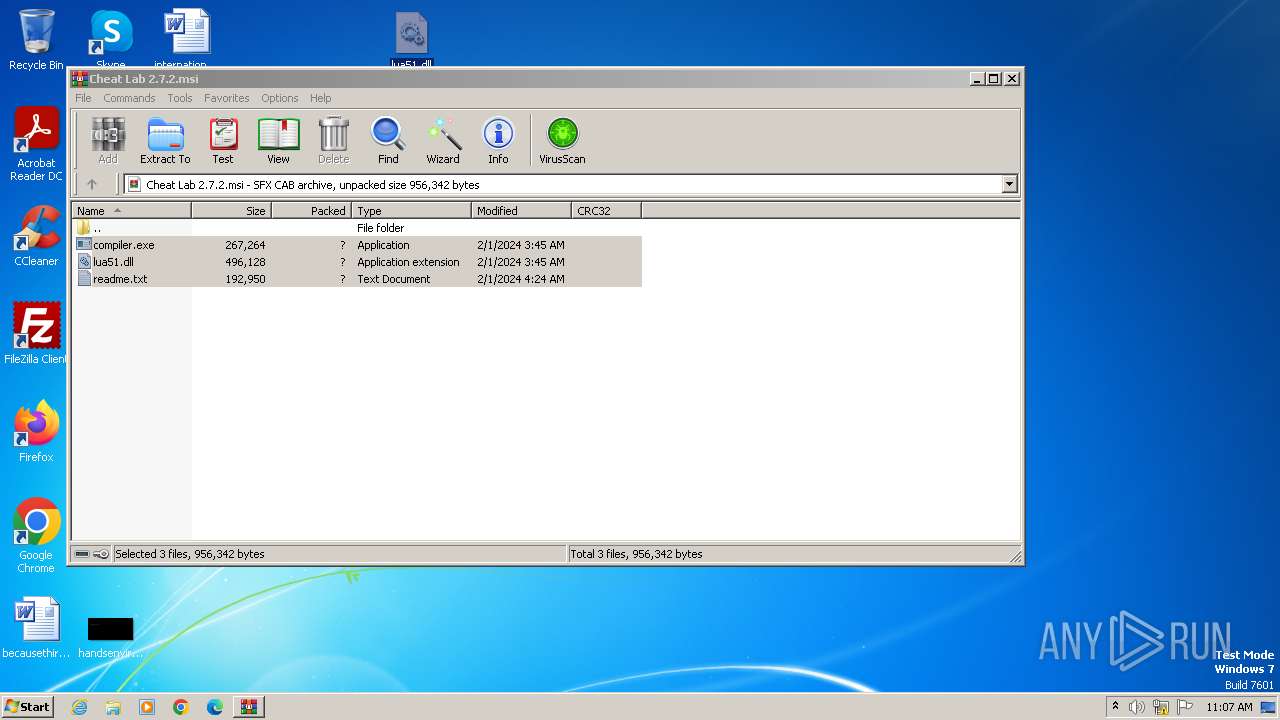
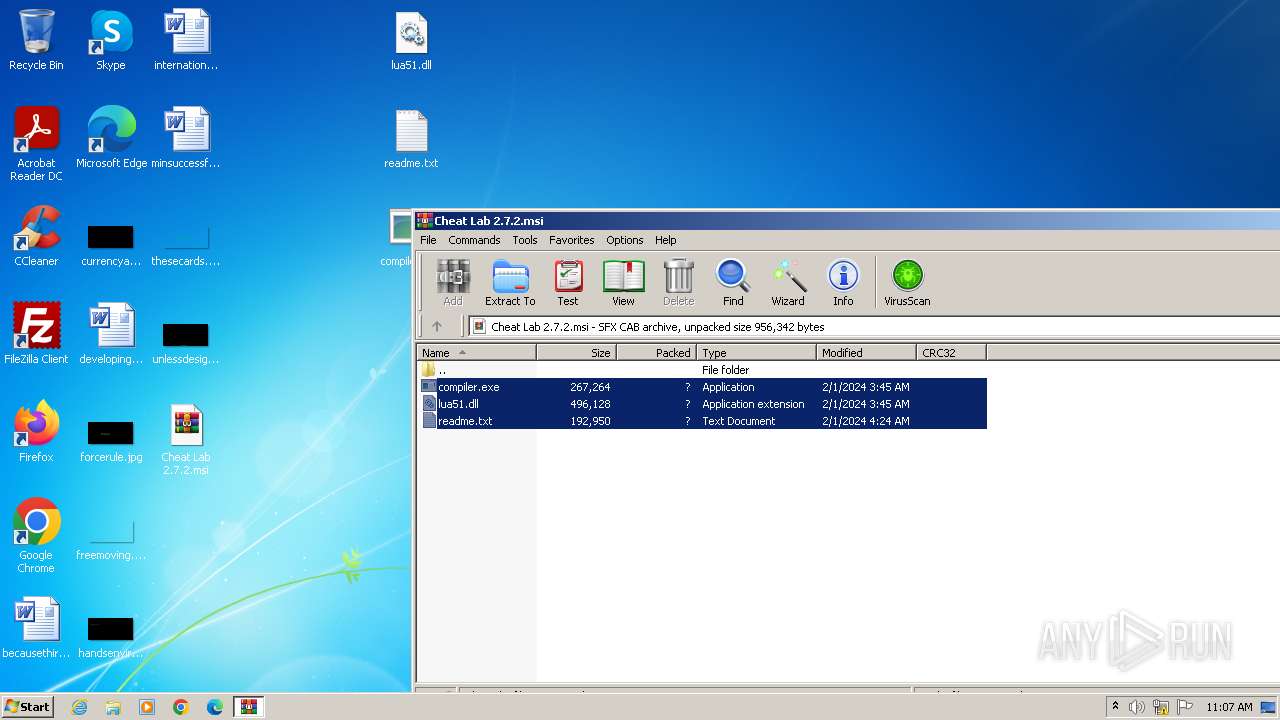
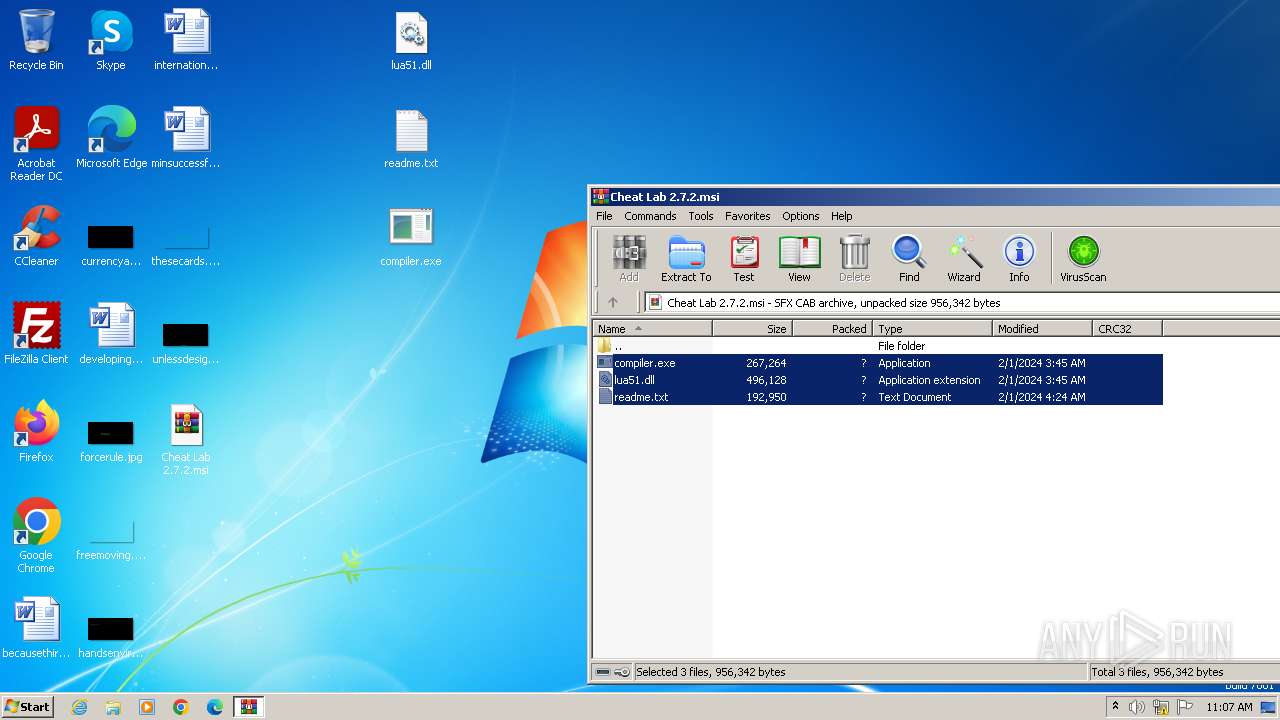
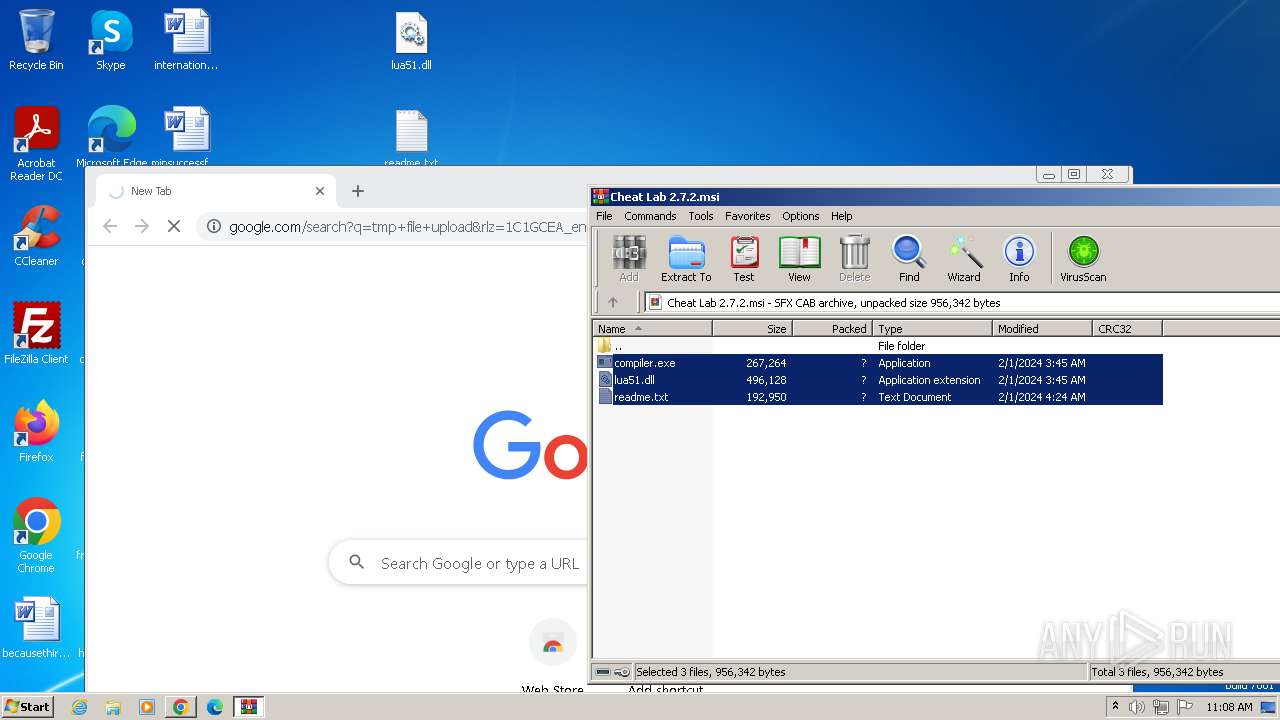
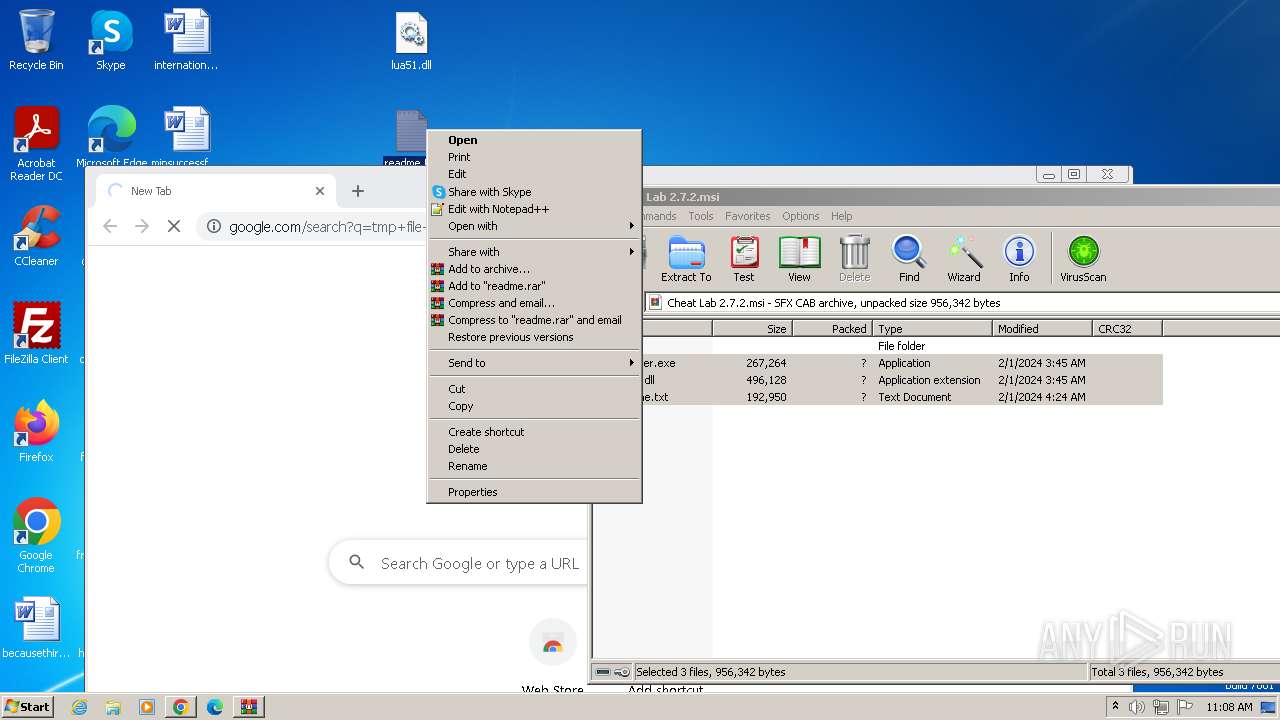
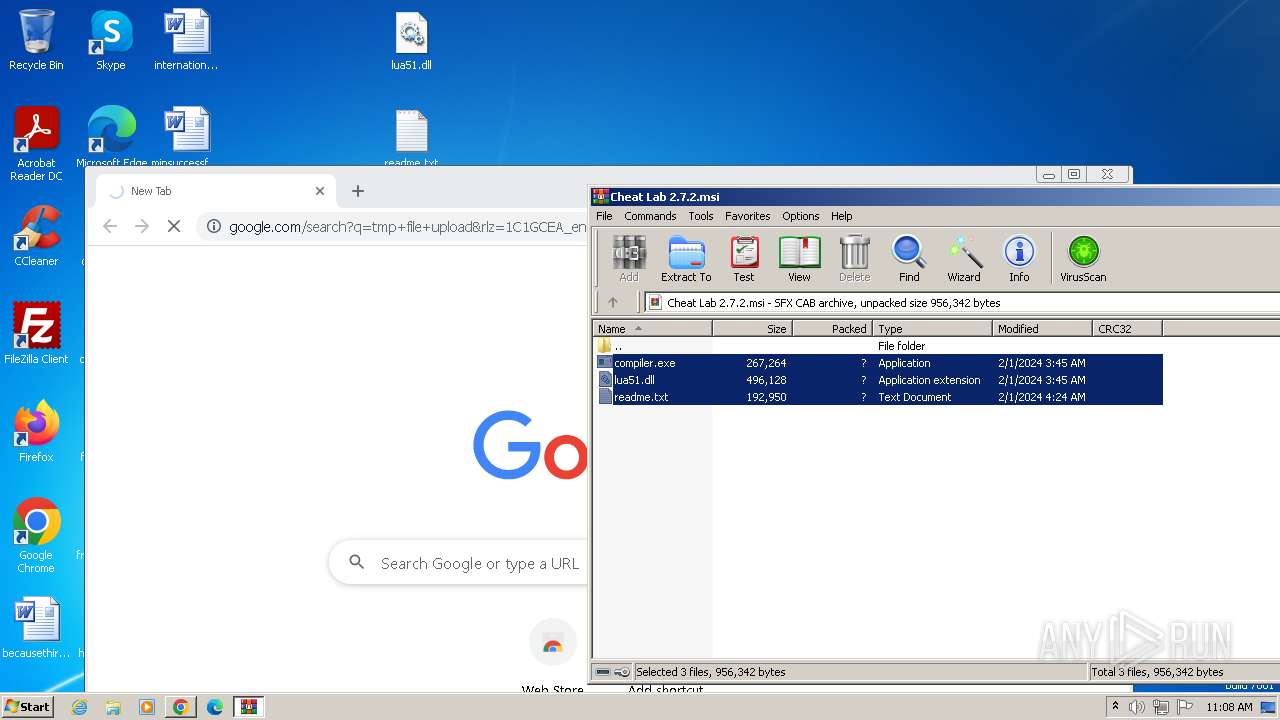
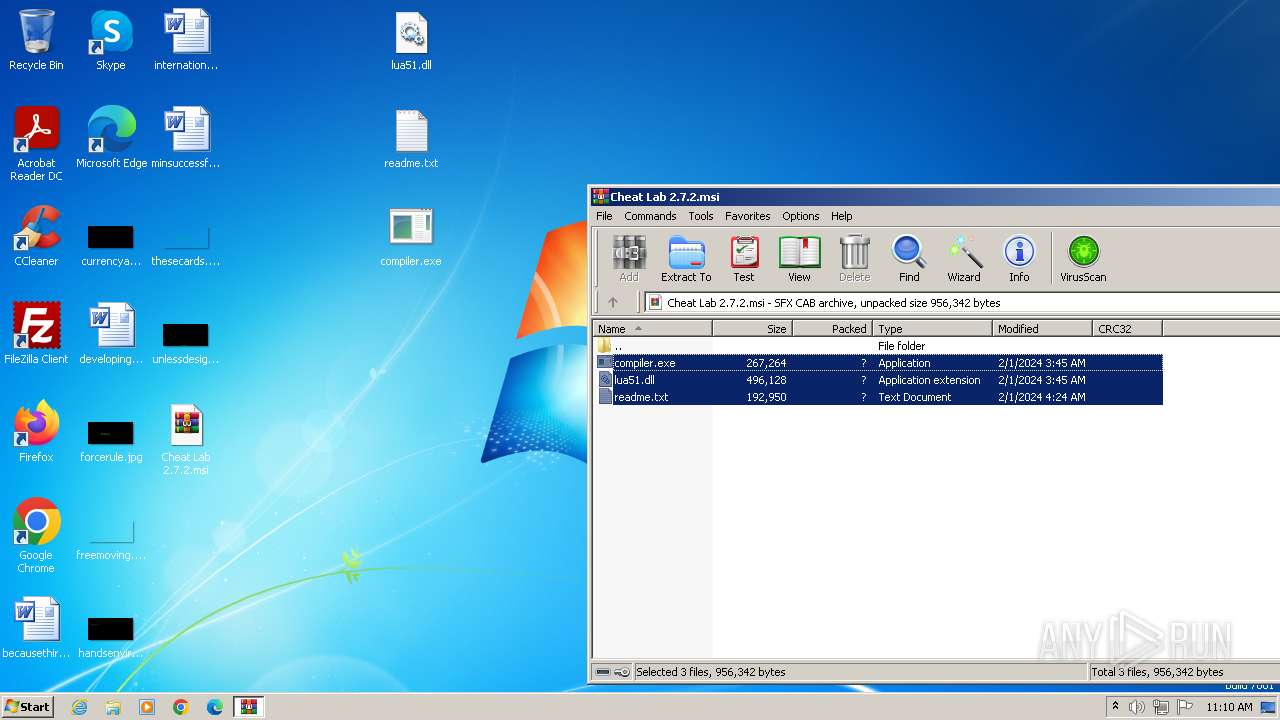
| File name: | Cheat Lab 2.7.2.msi |
| Full analysis: | https://app.any.run/tasks/21174b61-2294-43d6-8384-719a559b7834 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2024, 10:06:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.3, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {00FE08F5-576C-4B89-A91C-6447F4CD4F8A}, Number of Words: 2, Subject: Cheat Lab, Author: Cheat Lab Inc., Name of Creating Application: Cheat Lab, Template: x64;1033, Comments: This installer database contains the logic and data required to install Cheat Lab., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | F97903FAC84172871545926D6E553EB9 |
| SHA1: | E6E027B77DF4823F4FF37656867E8F40D4EBD732 |
| SHA256: | 35CEE7837F460D9E1141E375AF8438E868A9E6B8D923ED2673A980FCADFD4774 |
| SSDEEP: | 98304:Skb8vGY+bTeorFXXiyP4Pr8fW7XoKR/W74n9O4j1w8uw6C:3 |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3972)
SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 928)
INFO
Reads the machine GUID from the registry
- msiexec.exe (PID: 4008)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 928)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1432)
- msedge.exe (PID: 1184)
Manual execution by a user
- chrome.exe (PID: 616)
- rundll32.exe (PID: 928)
- wmpnscfg.exe (PID: 972)
- notepad.exe (PID: 2544)
- msedge.exe (PID: 1184)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1432)
Application launched itself
- chrome.exe (PID: 616)
- msedge.exe (PID: 1184)
Reads the computer name
- wmpnscfg.exe (PID: 972)
- msiexec.exe (PID: 4008)
Checks supported languages
- wmpnscfg.exe (PID: 972)
- msiexec.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {00FE08F5-576C-4B89-A91C-6447F4CD4F8A} |
| Words: | 2 |
| Subject: | Cheat Lab |
| Author: | Cheat Lab Inc. |
| LastModifiedBy: | - |
| Software: | Cheat Lab |
| Template: | x64;1033 |
| Comments: | This installer database contains the logic and data required to install Cheat Lab. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
77
Monitored processes
43
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 928 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Cheat Lab 2.7.2.msi | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2268 --field-trial-handle=1300,i,7100860108467174805,14825327645689261019,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 972 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Cheat Lab 2.7.2.msi" | C:\Program Files\WinRAR\WinRAR.exe | rundll32.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1644 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4016 --field-trial-handle=1300,i,7100860108467174805,14825327645689261019,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1628 --field-trial-handle=1300,i,7100860108467174805,14825327645689261019,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bea8b38,0x6bea8b48,0x6bea8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4040 --field-trial-handle=1300,i,7100860108467174805,14825327645689261019,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
21 853
Read events
21 577
Write events
264
Delete events
12
Modification events
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\msiexec.exe |
Value: Windows® installer | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: Firefox | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (928) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
Executable files
4
Suspicious files
165
Text files
61
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF113b12.TMP | — | |
MD5:— | SHA256:— | |||
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18255\compiler.exe | executable | |
MD5:F33E239A228AD29B22F40A503DB1DD60 | SHA256:DFBF23697CFD9D35F263AF7A455351480920A95BFC642F3254EE8452CE20655A | |||
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18255\lua51.dll | executable | |
MD5:75D539DF595217555D98C59AF85EDAB1 | SHA256:873AA2E88DBC2EFA089E6EFD1C8A5370E04C9F5749D7631F2912BCB640439997 | |||
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF113b31.TMP | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF113e3e.TMP | — | |
MD5:— | SHA256:— | |||
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF113c6a.TMP | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
| 616 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old~RF113cc7.TMP | text | |
MD5:E53573A93829681410D5E7DBB1B61C78 | SHA256:A82D28F2C1E22A2AE0ABC5F5AF0CC8EE7AD913BAB3A0BF84CE6D8D23F67E06A3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
66
DNS requests
65
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | — | — | unknown |
2276 | chrome.exe | GET | — | 142.250.186.35:80 | http://www.gstatic.com/generate_204 | unknown | — | — | unknown |
884 | svchost.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acf5iuk6pnjlc6lnxtqm5ki6eoqq_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win_aclnpjhtsv44pze3qmxsxb7fq66q.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2276 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
616 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2276 | chrome.exe | 142.250.186.68:443 | www.google.com | GOOGLE | US | whitelisted |
2276 | chrome.exe | 142.250.185.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
616 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
2276 | chrome.exe | 142.250.186.163:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| unknown |
encrypted-tbn0.gstatic.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3160 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |