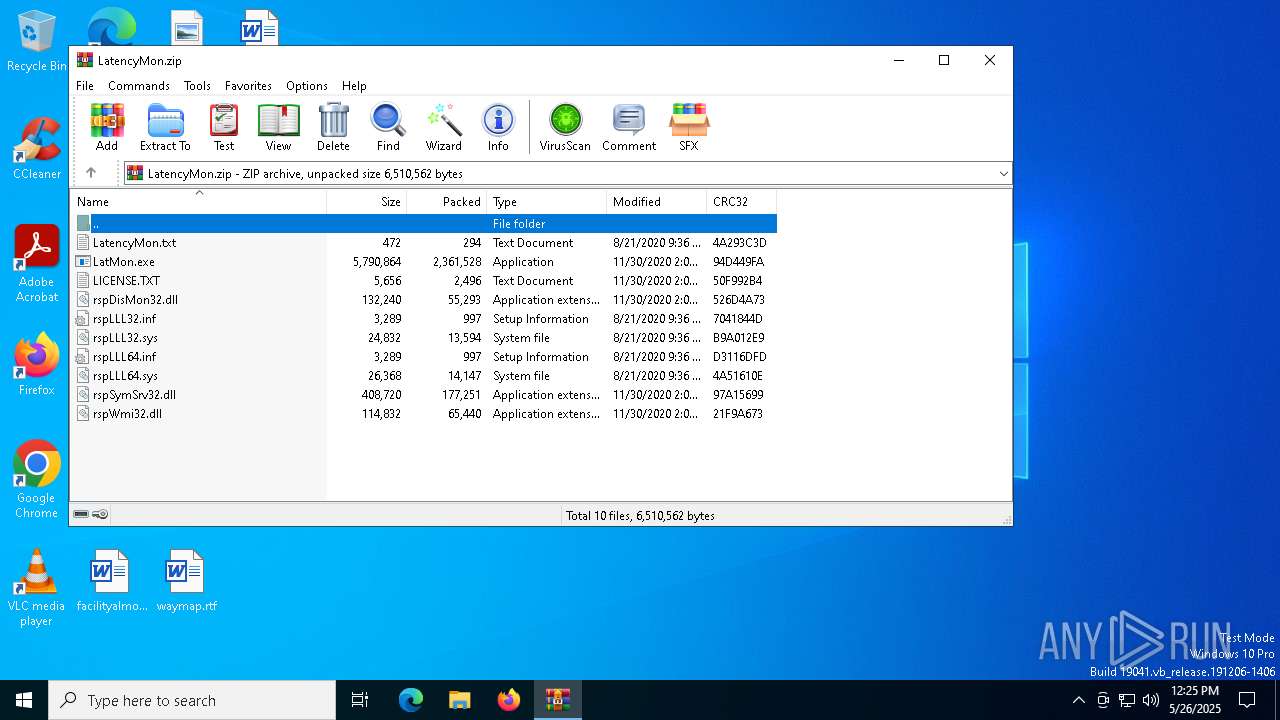
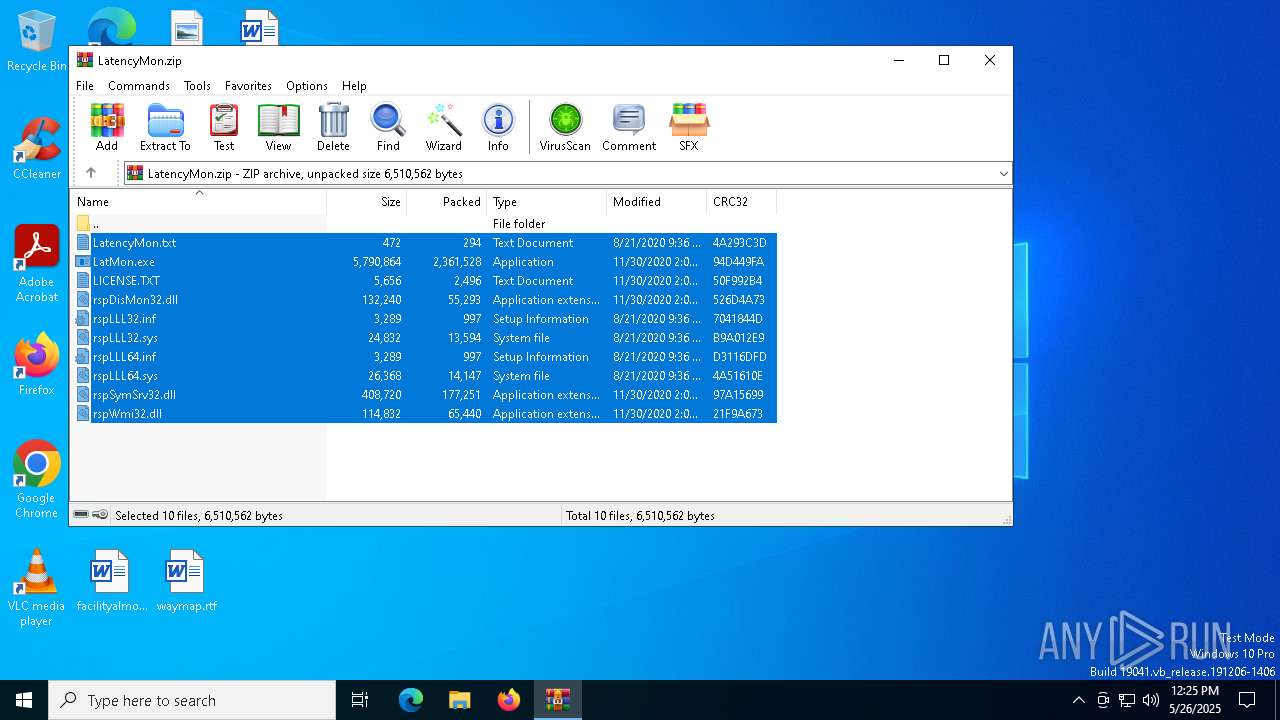
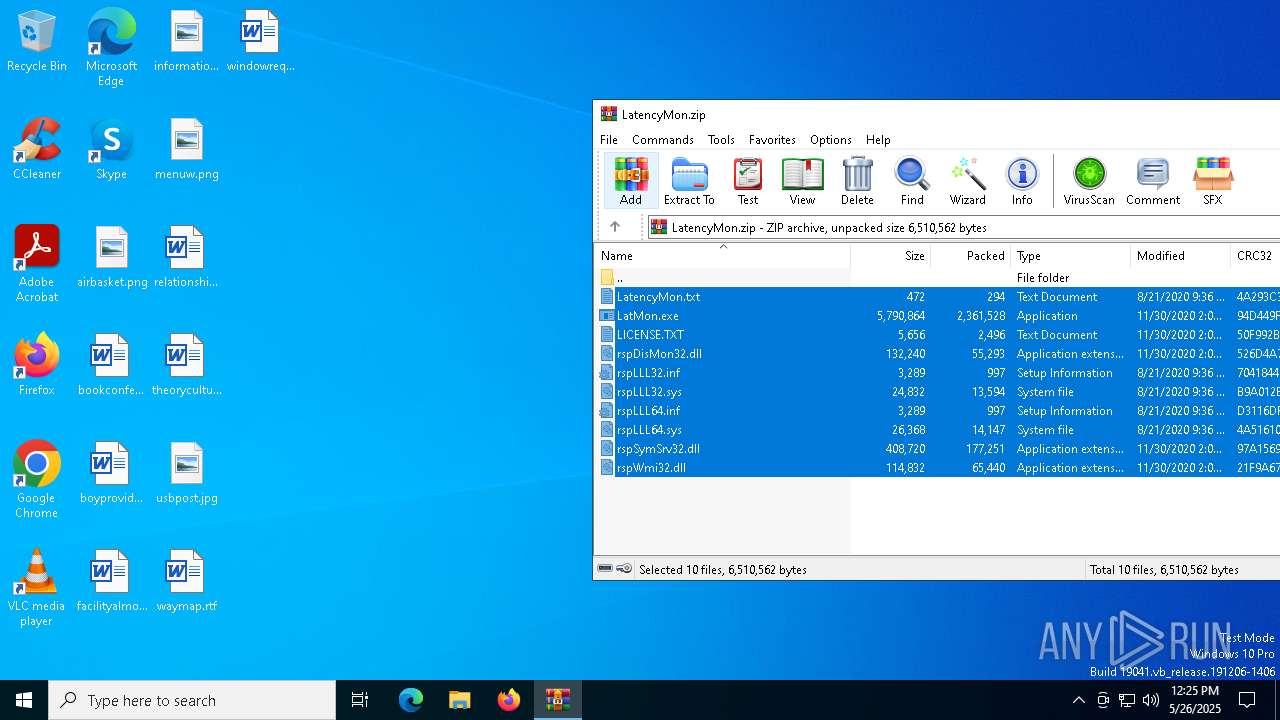
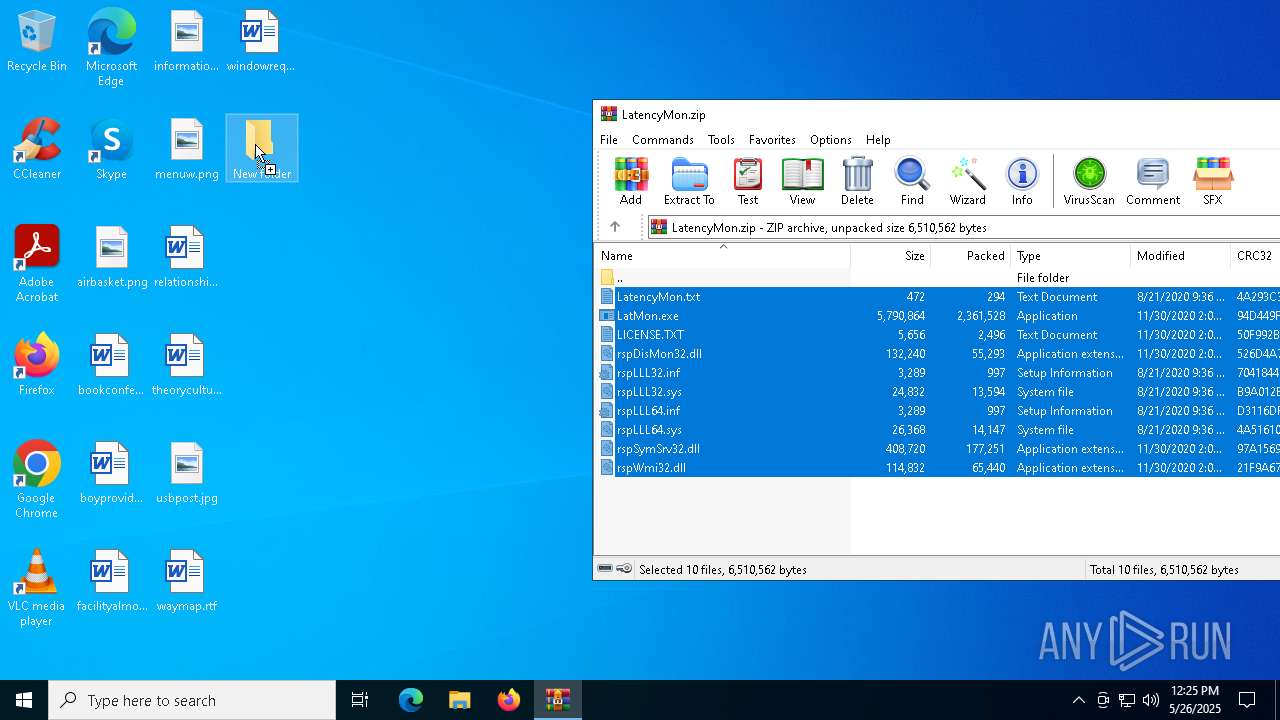
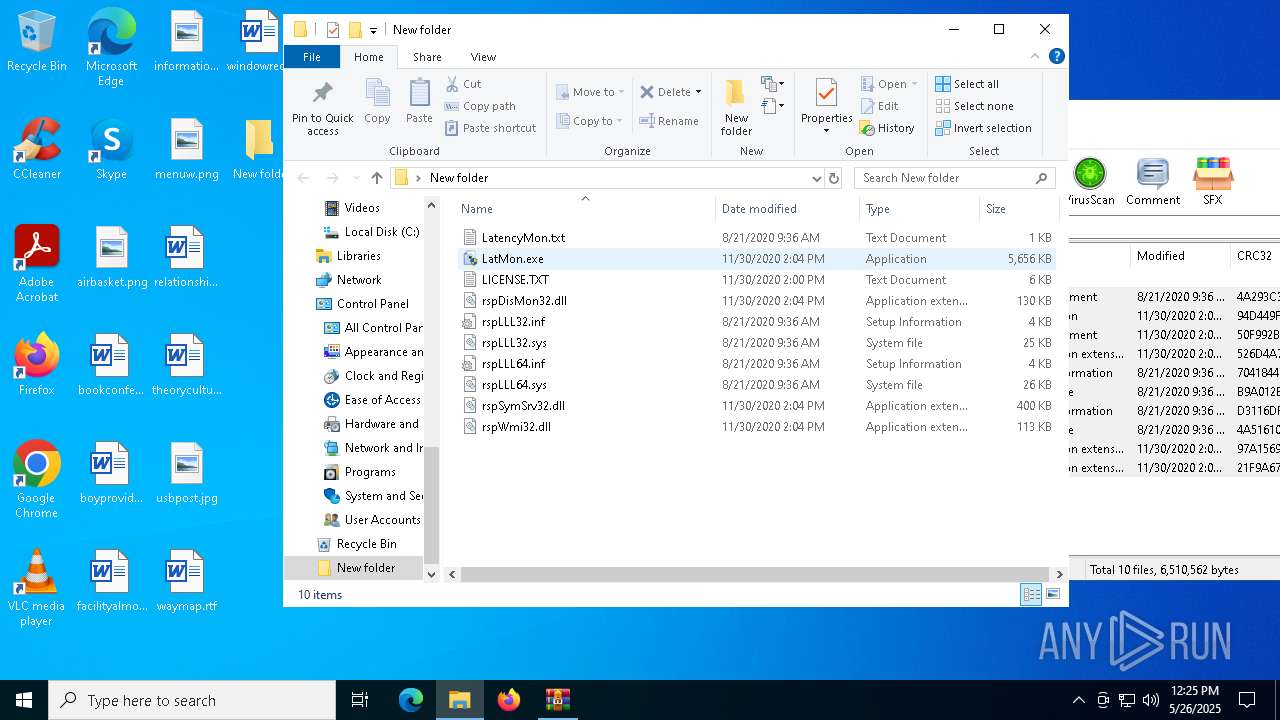
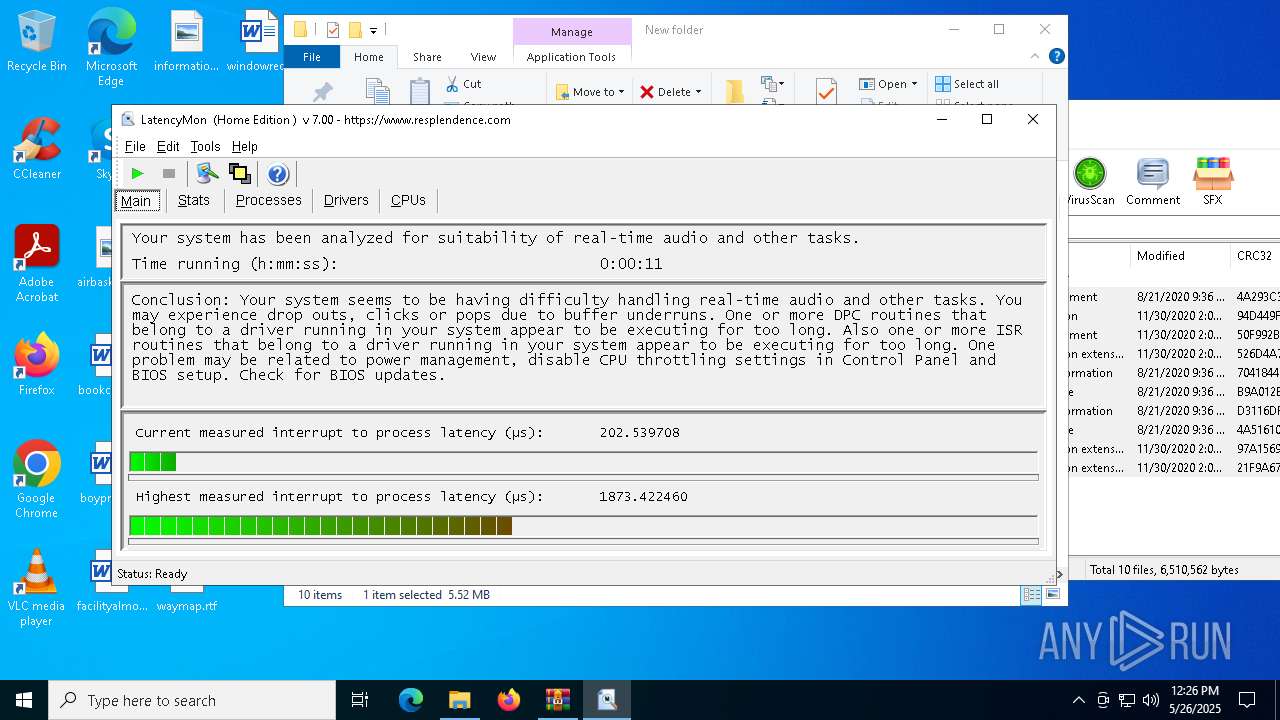
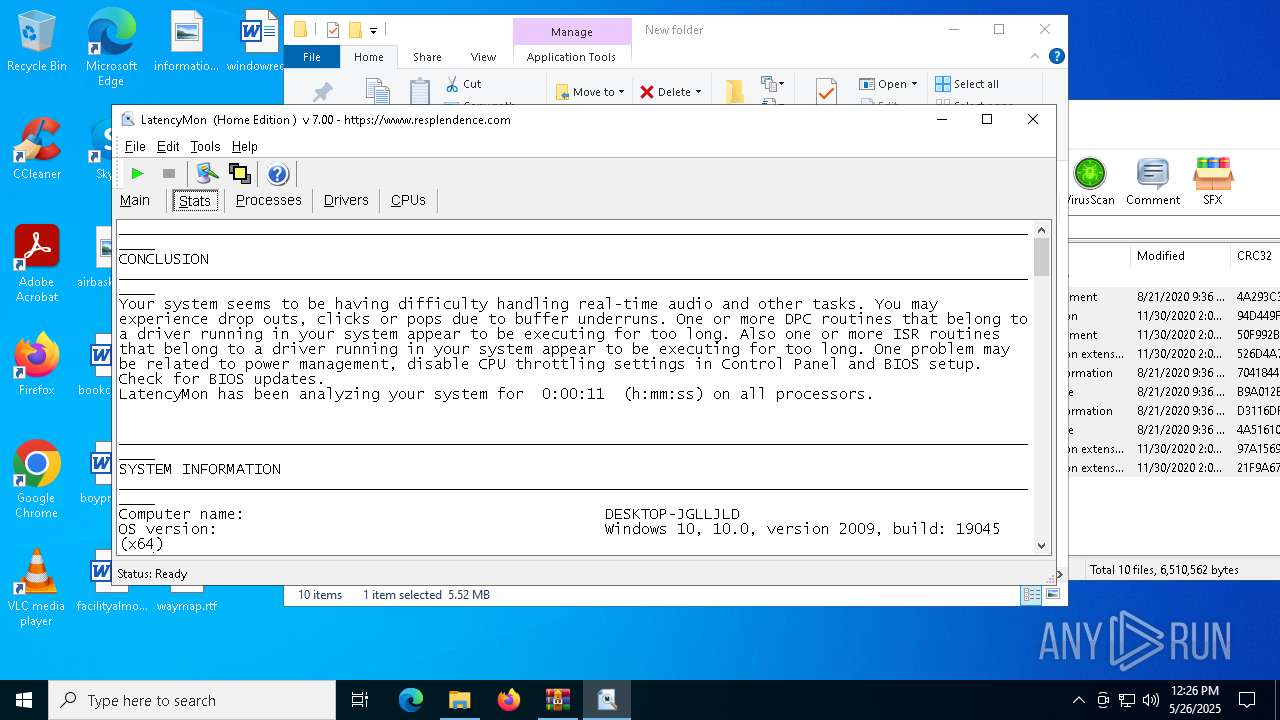
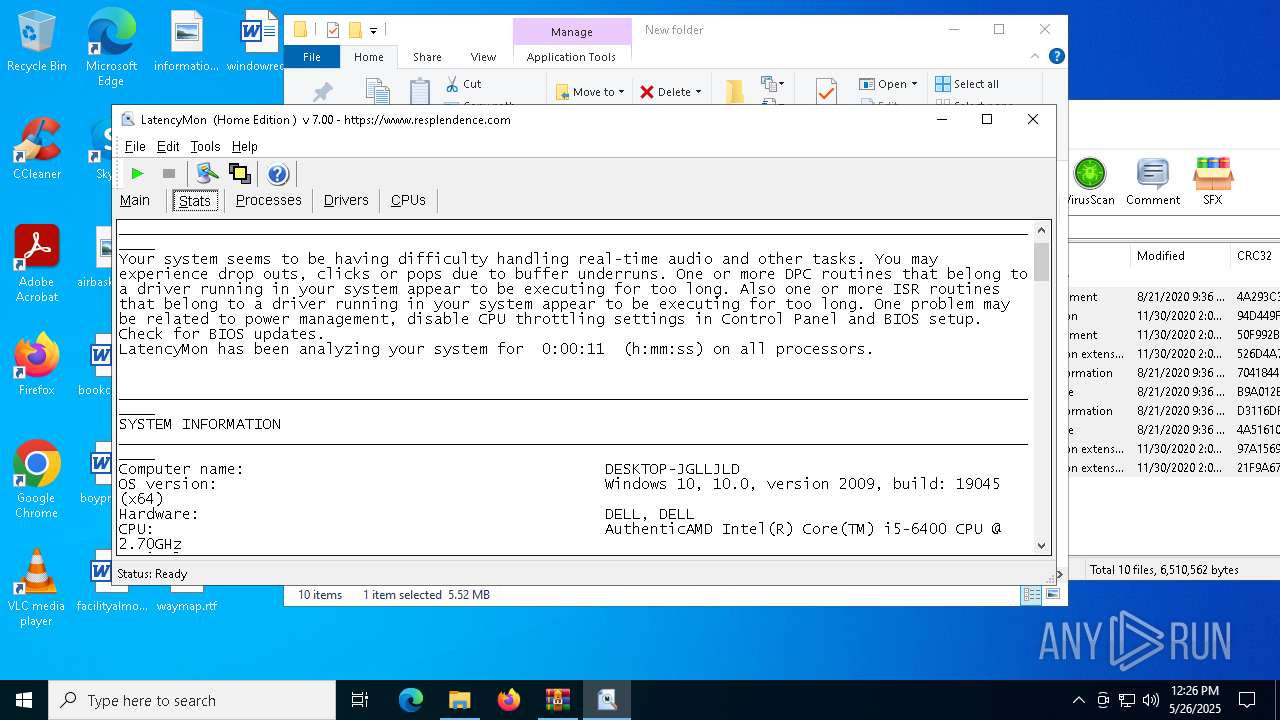
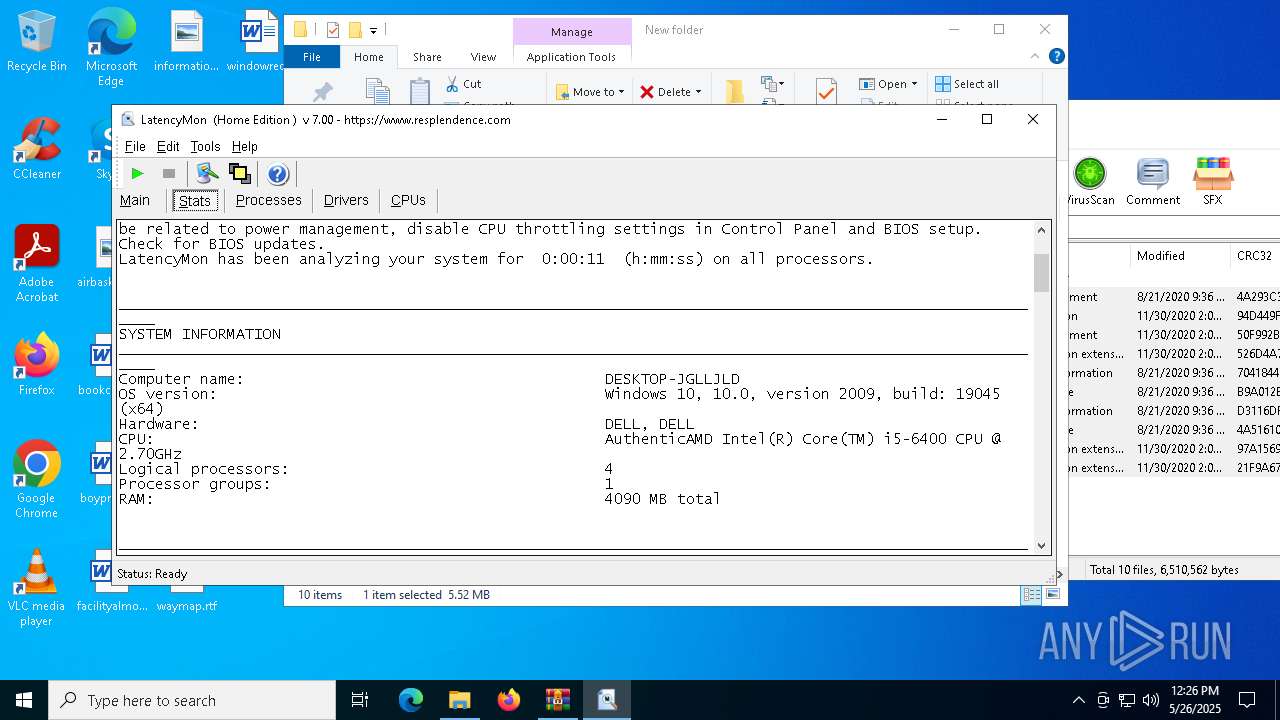
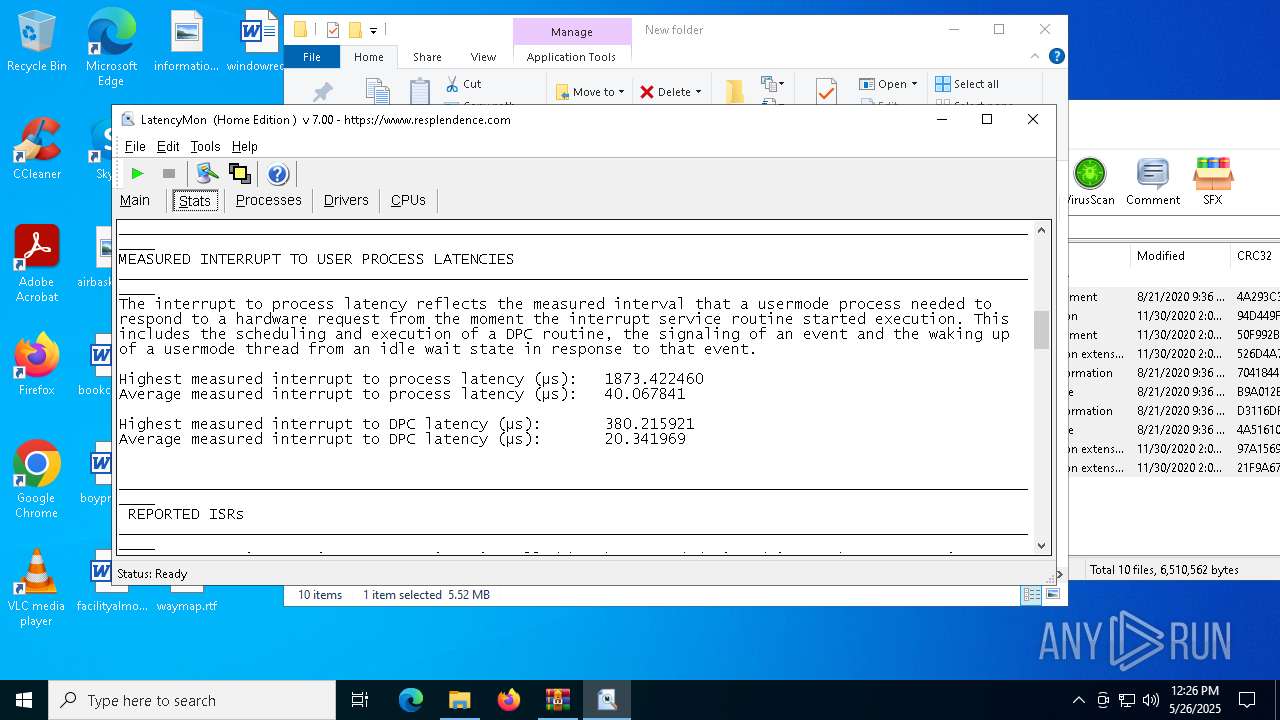
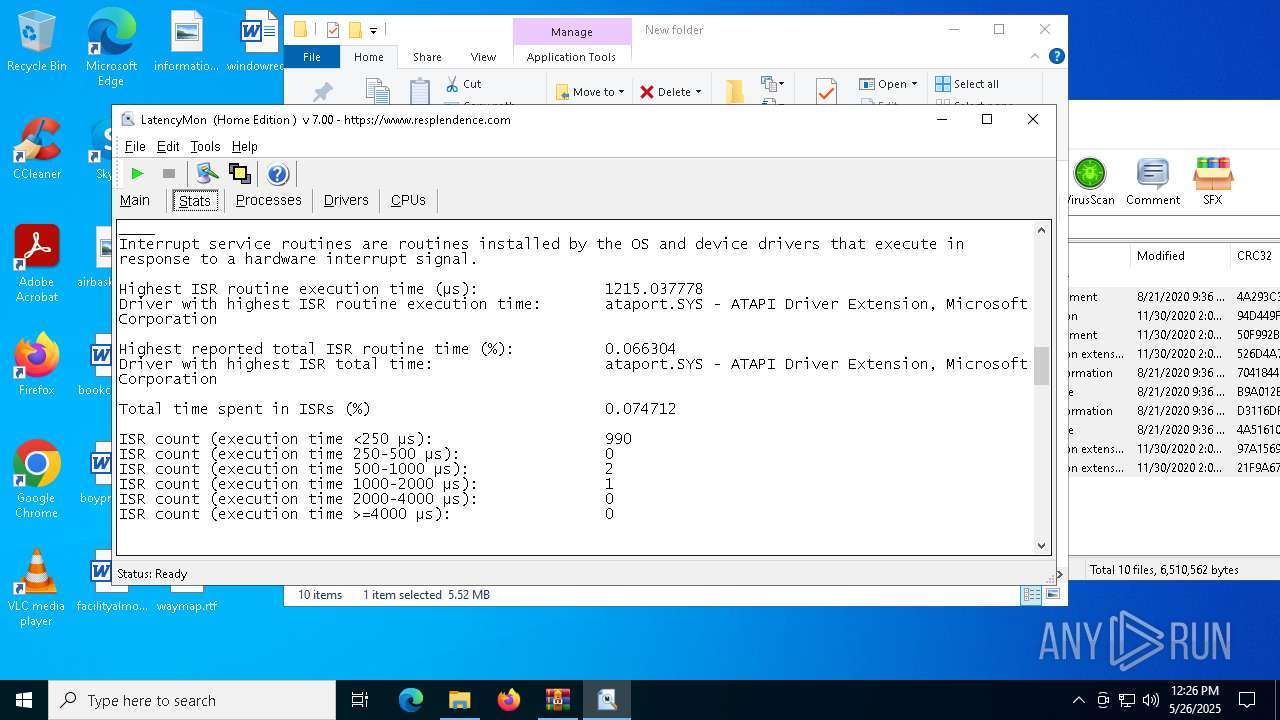
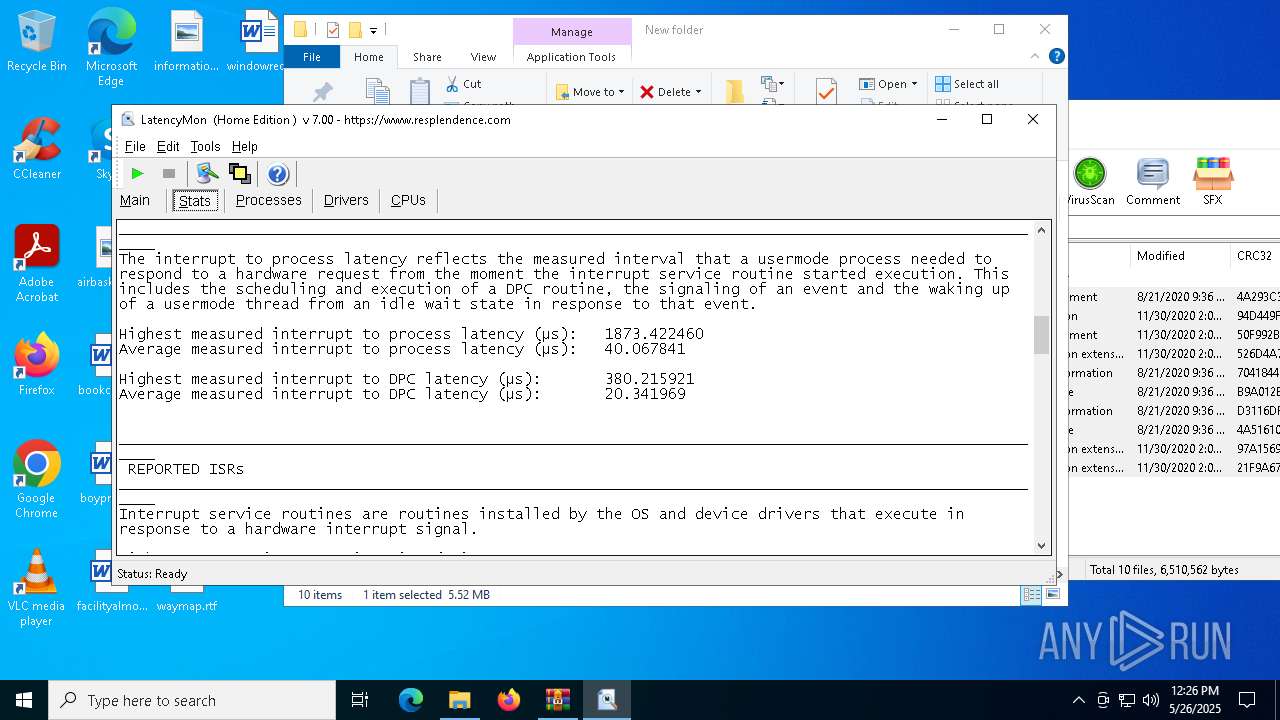
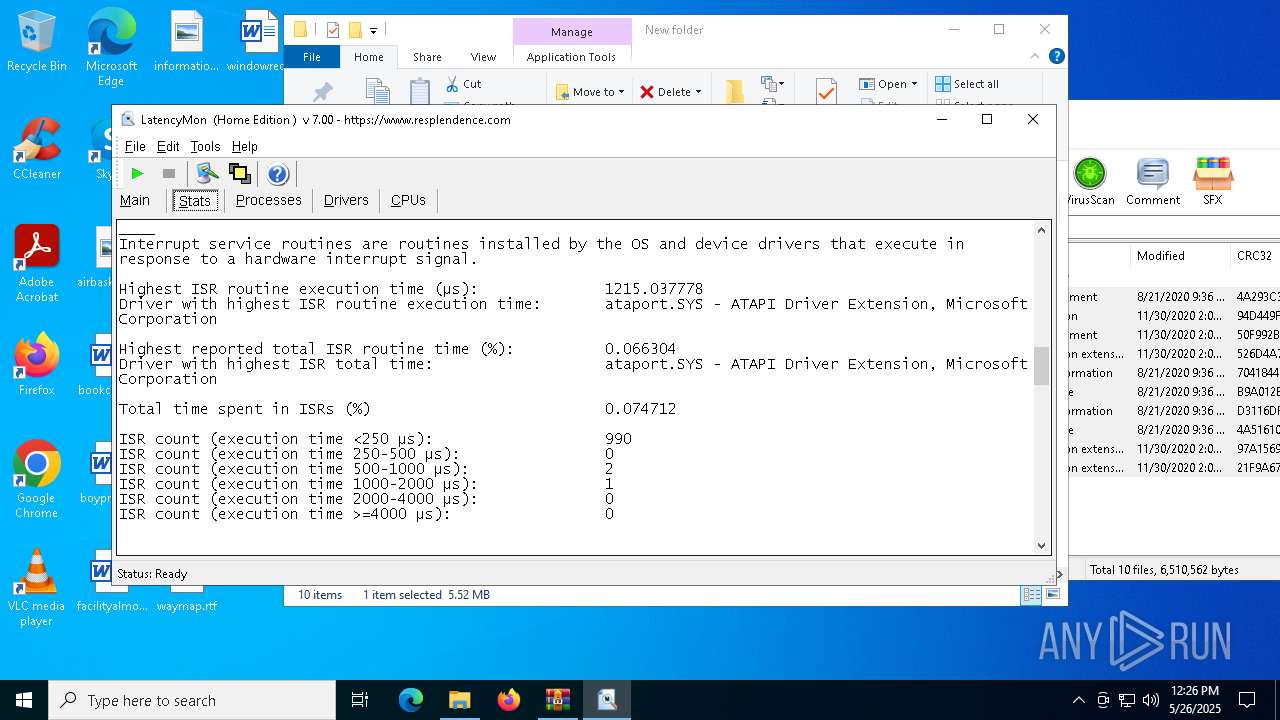
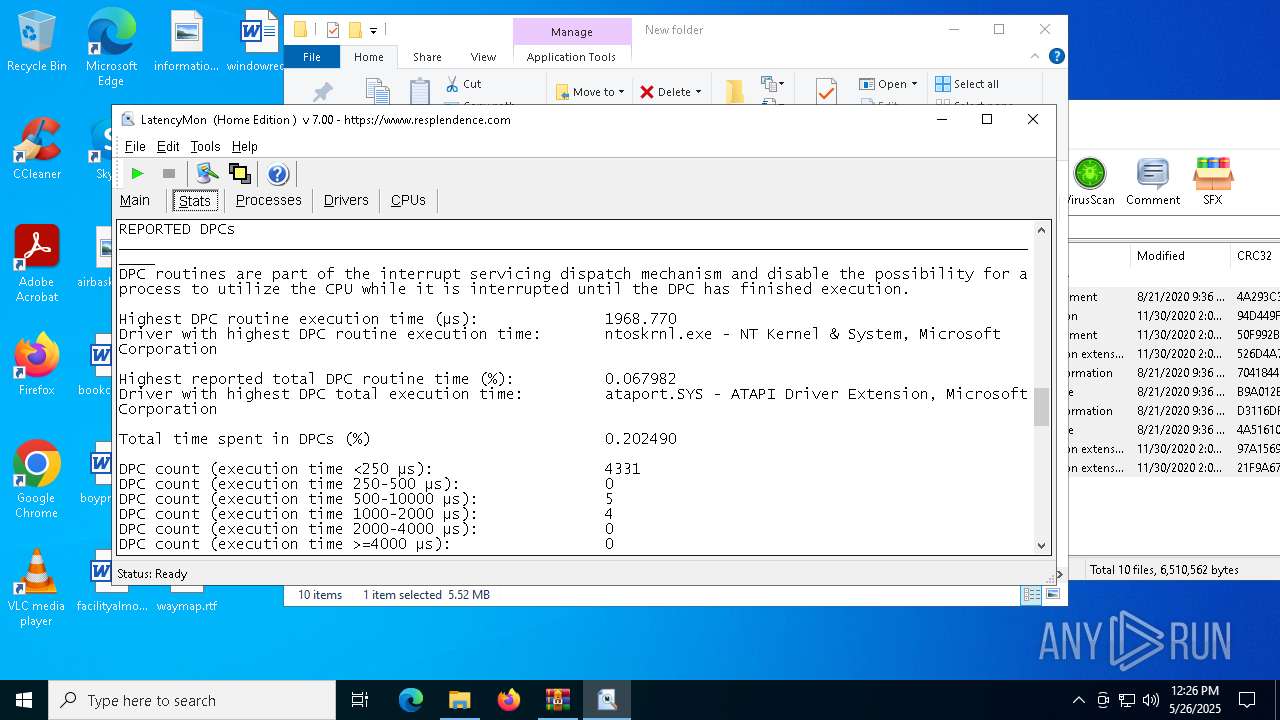
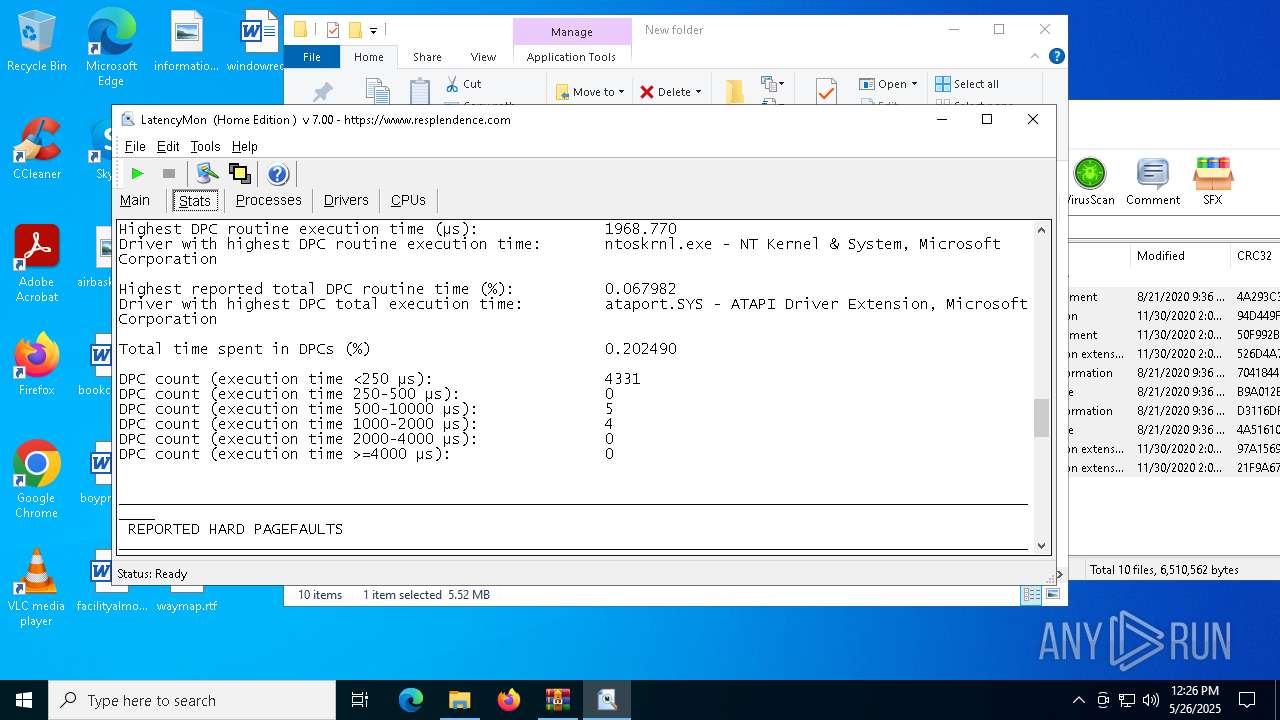
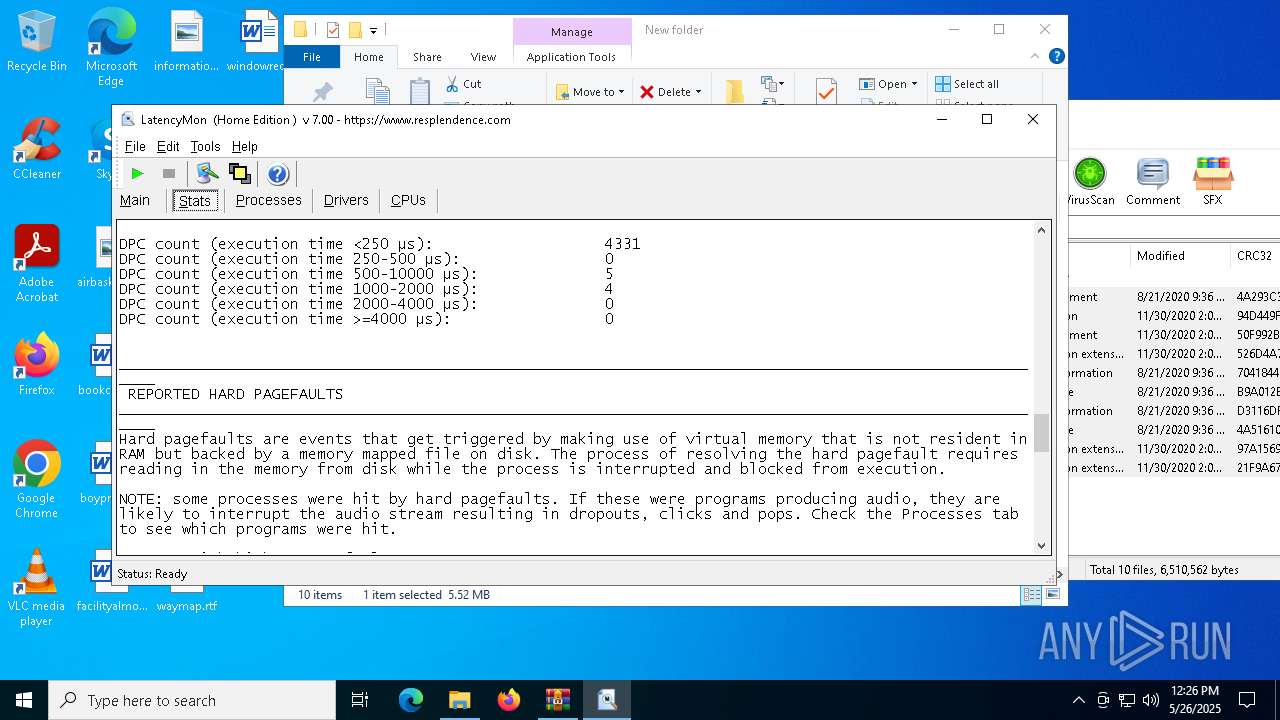
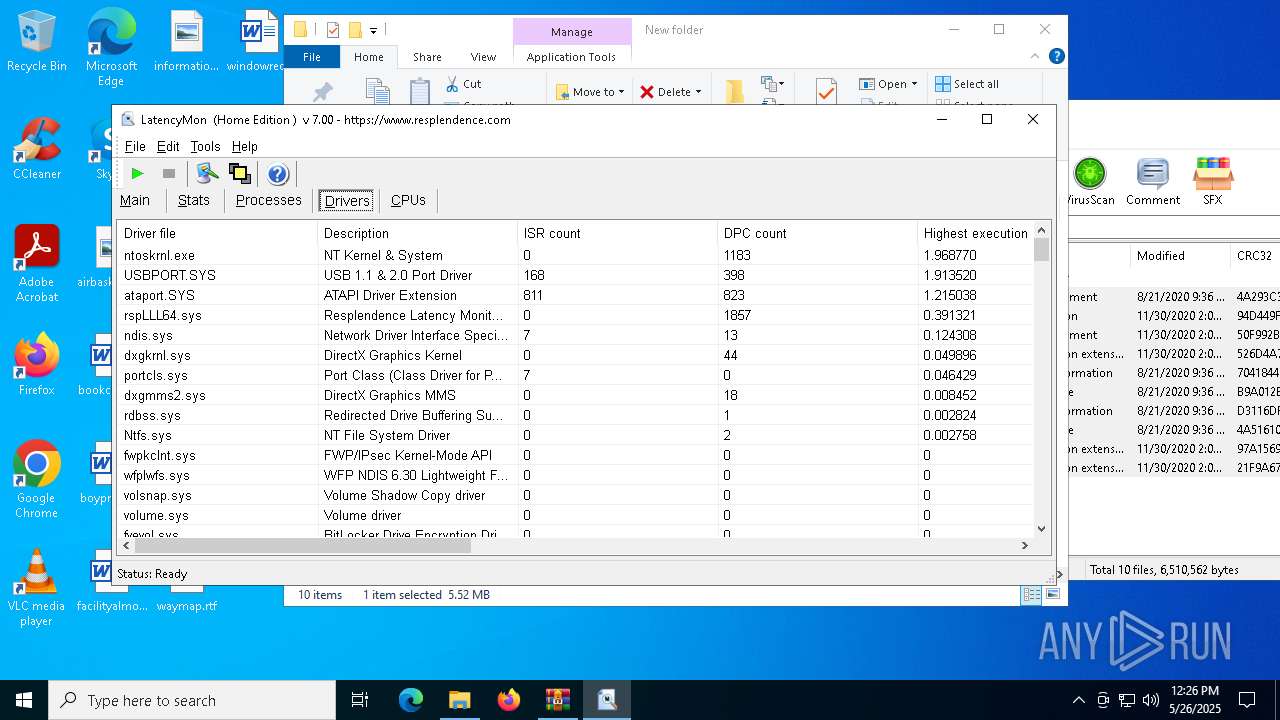
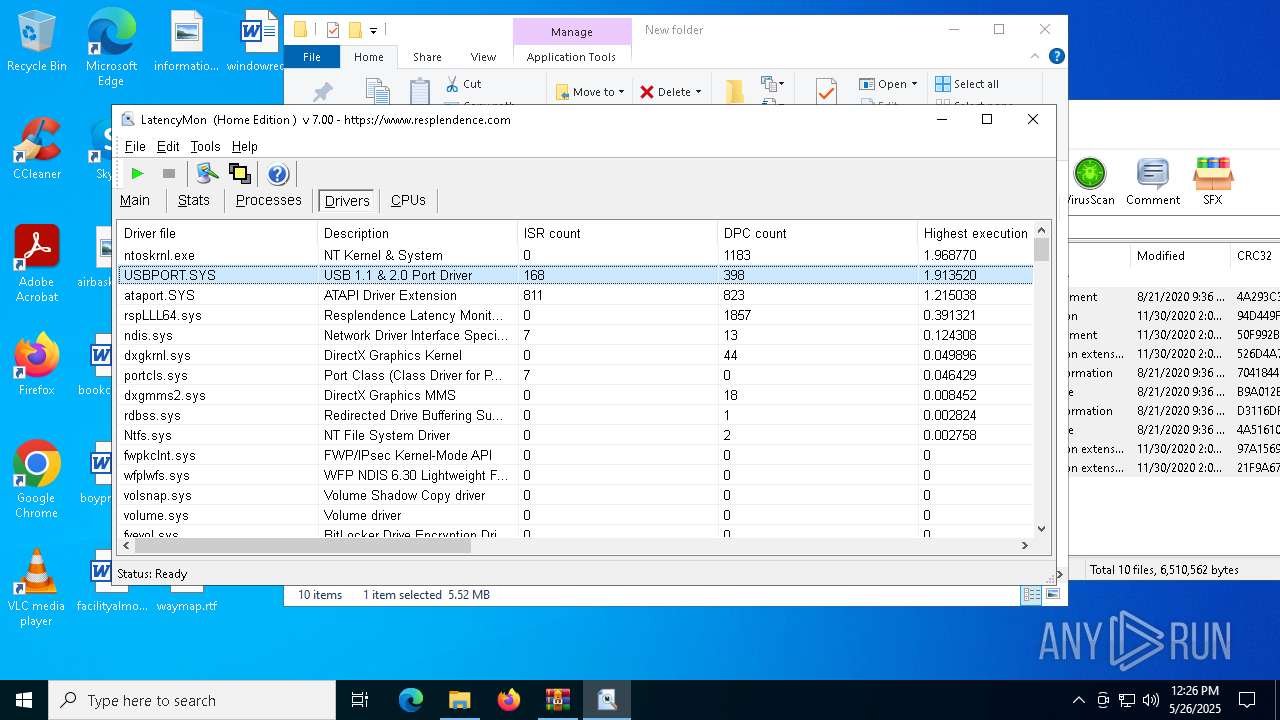
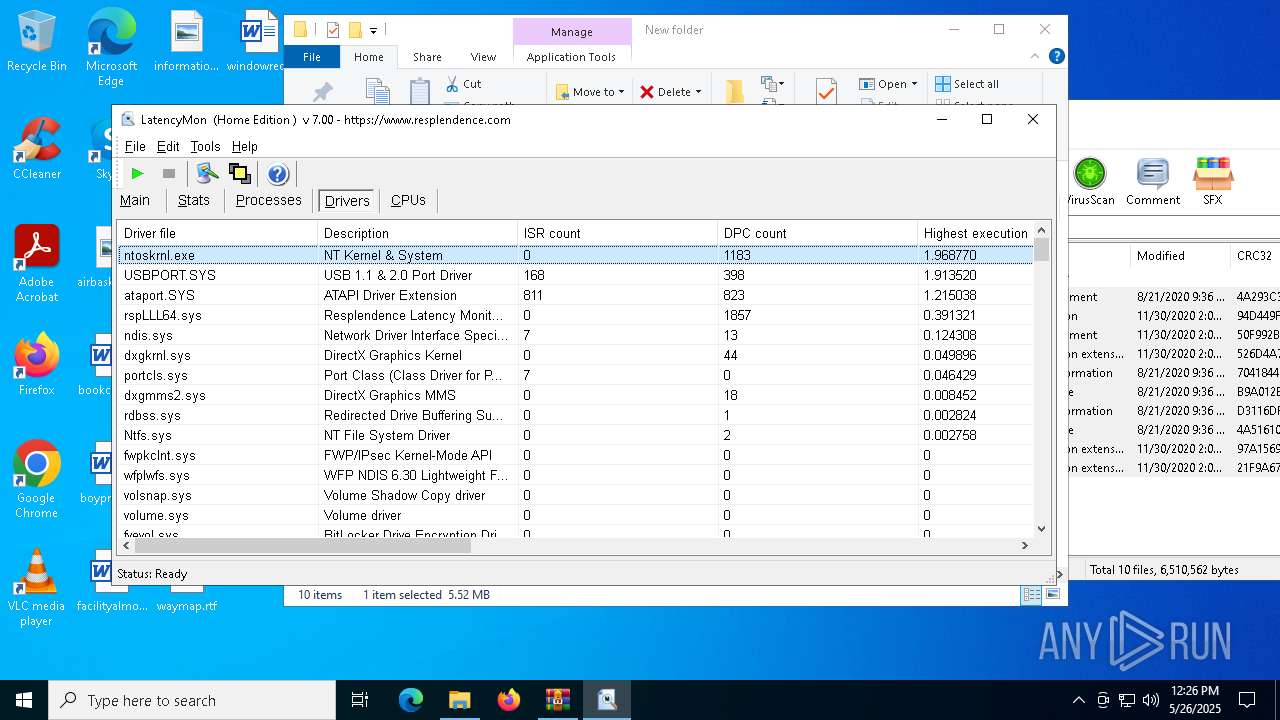
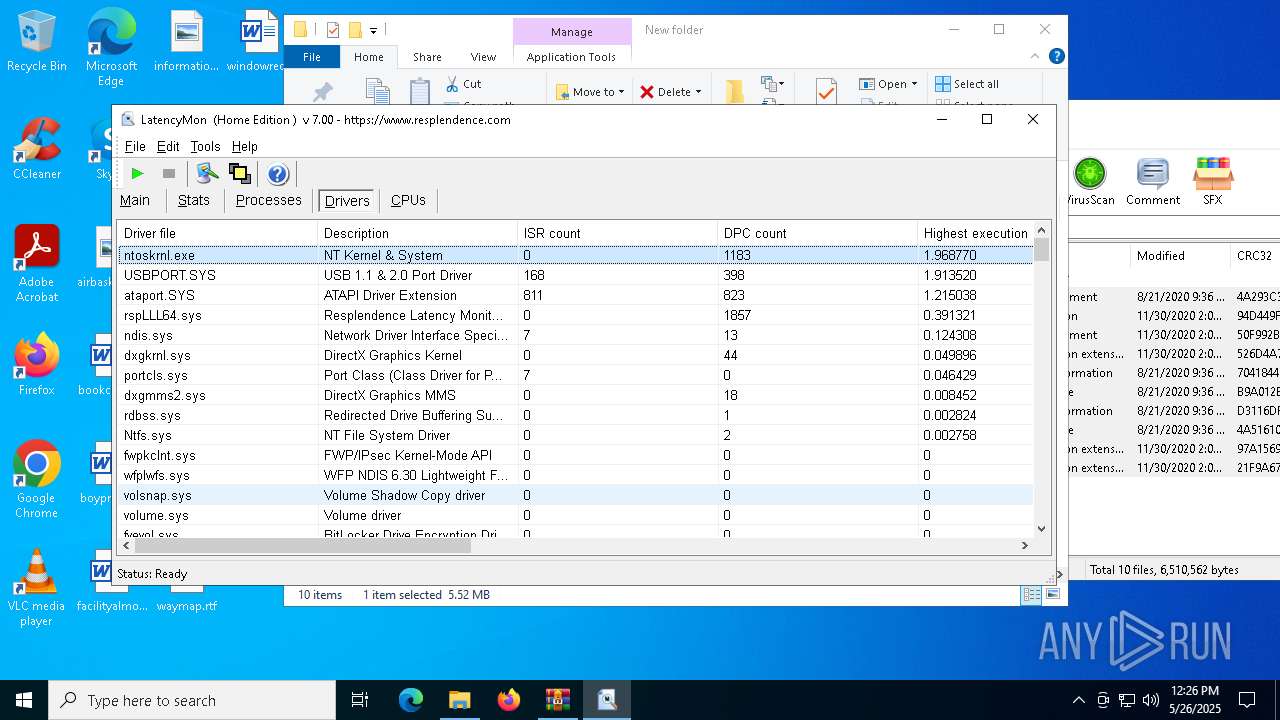
| File name: | LatencyMon.zip |
| Full analysis: | https://app.any.run/tasks/8b92d3c9-fca3-482c-8cd6-801bb3fd24af |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 12:25:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7F7B1AFB982830679AA53D5F2EA286B7 |
| SHA1: | 861B389CDB5B450EA4E4FCE6262E14B1B53BBBF1 |
| SHA256: | 35C558BEAE1FE32D0E8F856C0EF62EBEF0F83BFDC4CEBE55120DC32F8D4526EA |
| SSDEEP: | 98304:FAbRA9lFe2gliJtqugC/smuzS7FHqYigx8RWUOuMwtoXbHVxlOLGkLpxBuX4qVdl:GI |
MALICIOUS
Changes the autorun value in the registry
- rundll32.exe (PID: 5968)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7560)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 7560)
- rundll32.exe (PID: 5968)
Reads the Windows owner or organization settings
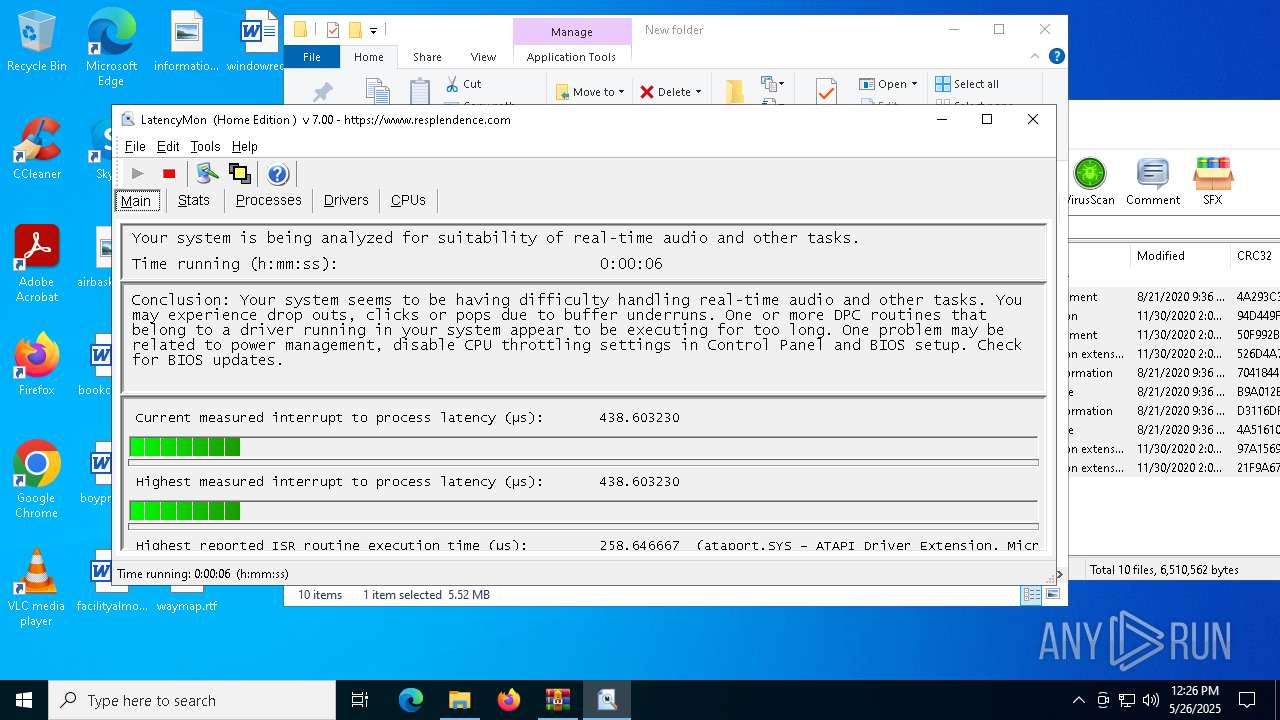
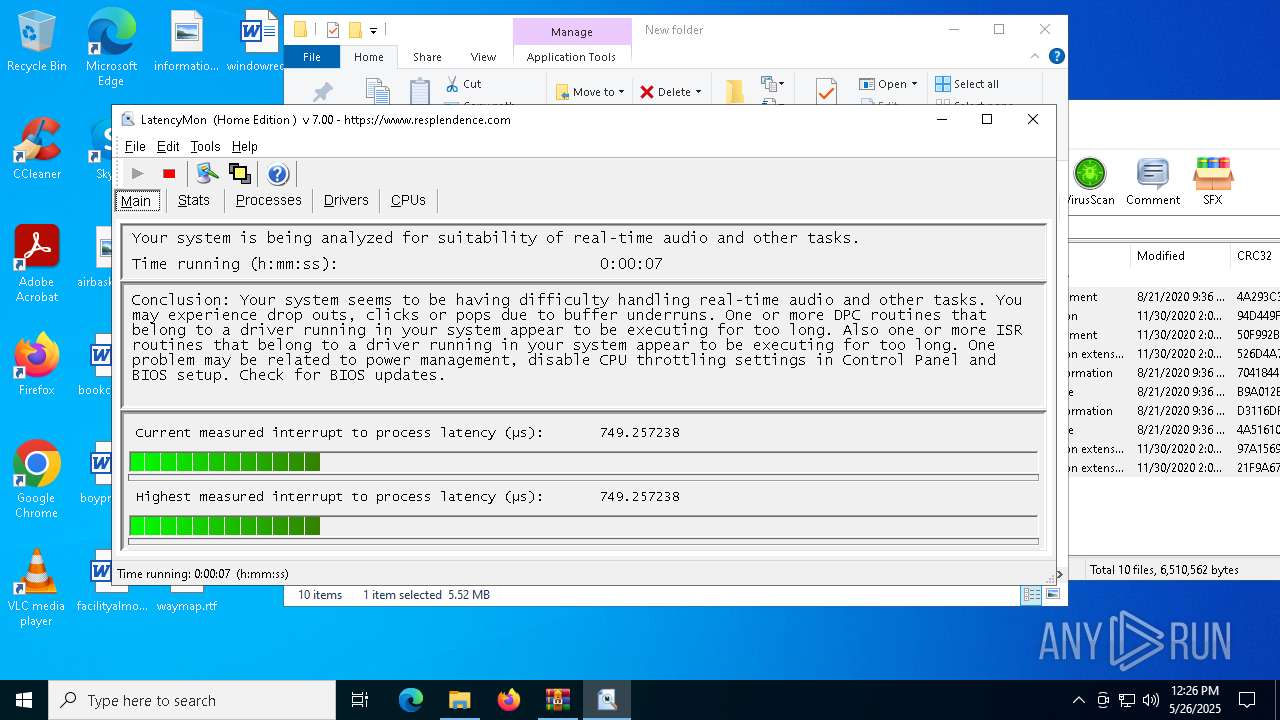
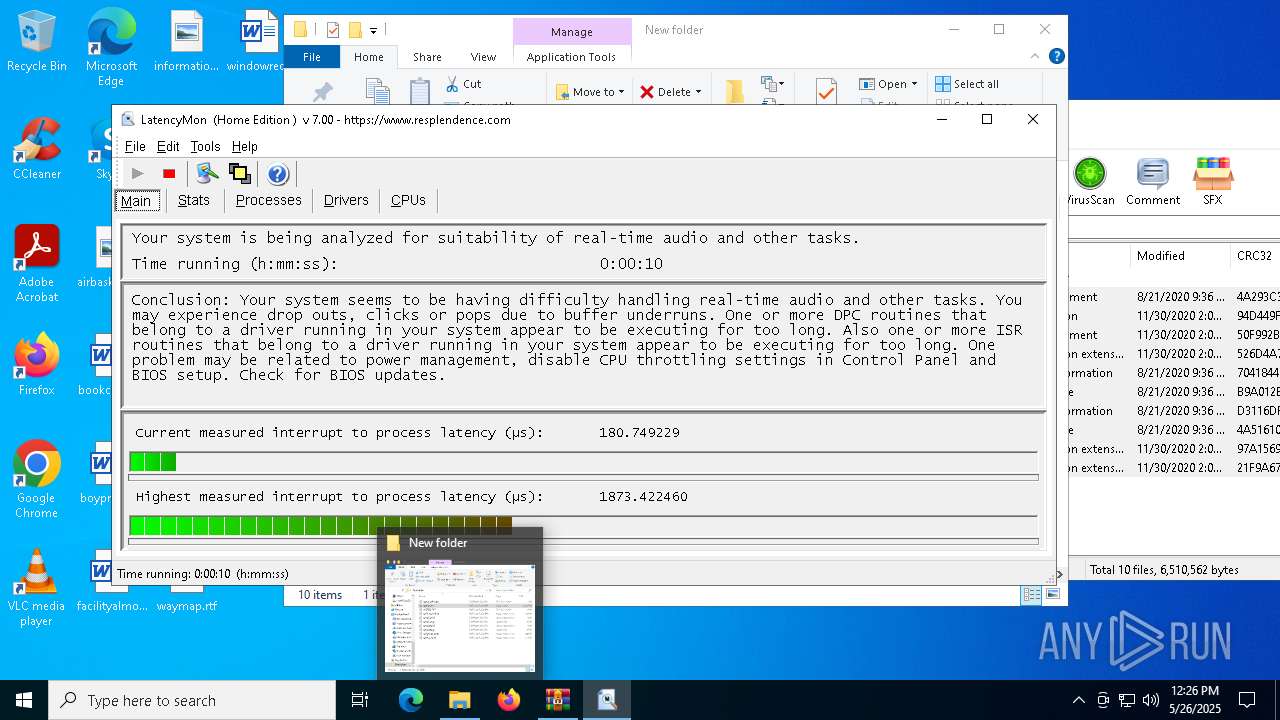
- LatMon.exe (PID: 7392)
Reads security settings of Internet Explorer
- LatMon.exe (PID: 7392)
Uses RUNDLL32.EXE to load library
- LatMon.exe (PID: 7392)
Executable content was dropped or overwritten
- rundll32.exe (PID: 5968)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7560)
The sample compiled with english language support
- WinRAR.exe (PID: 7560)
- rundll32.exe (PID: 5968)
Manual execution by a user
- LatMon.exe (PID: 7364)
- LatMon.exe (PID: 7392)
Reads the computer name
- LatMon.exe (PID: 7392)
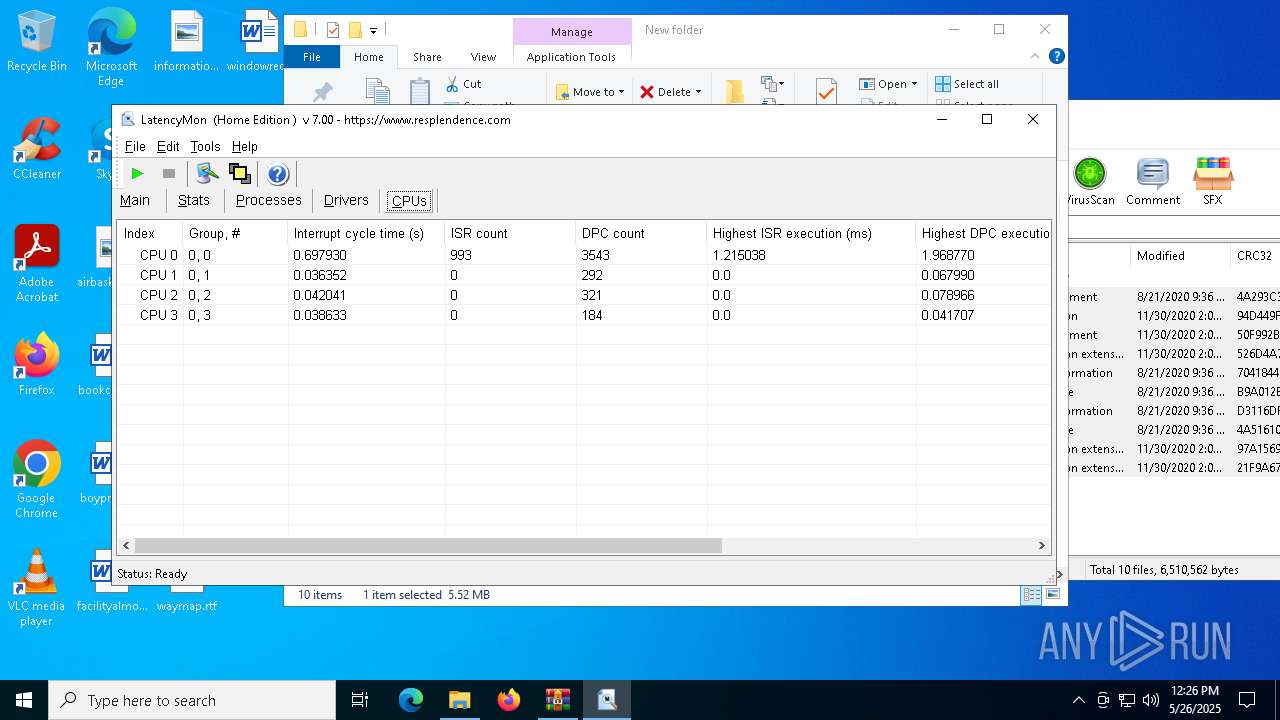
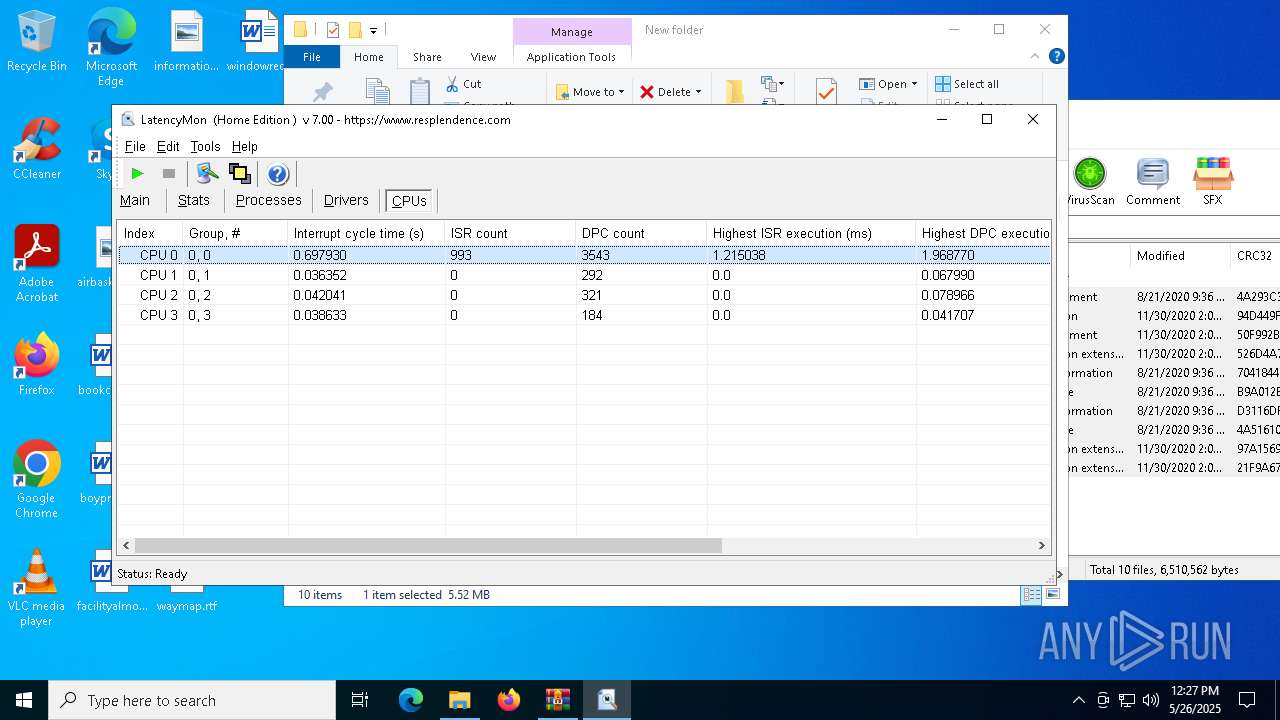
Reads CPU info
- LatMon.exe (PID: 7392)
Checks supported languages
- LatMon.exe (PID: 7392)
Process checks computer location settings
- LatMon.exe (PID: 7392)
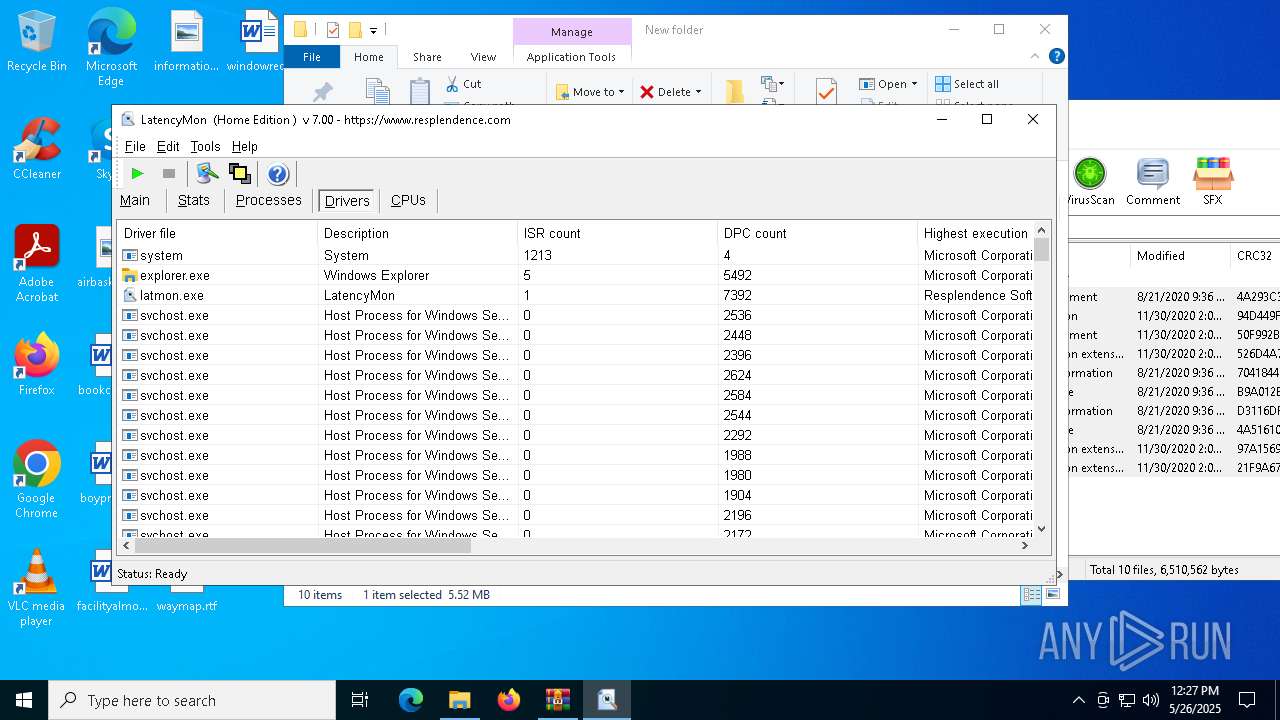
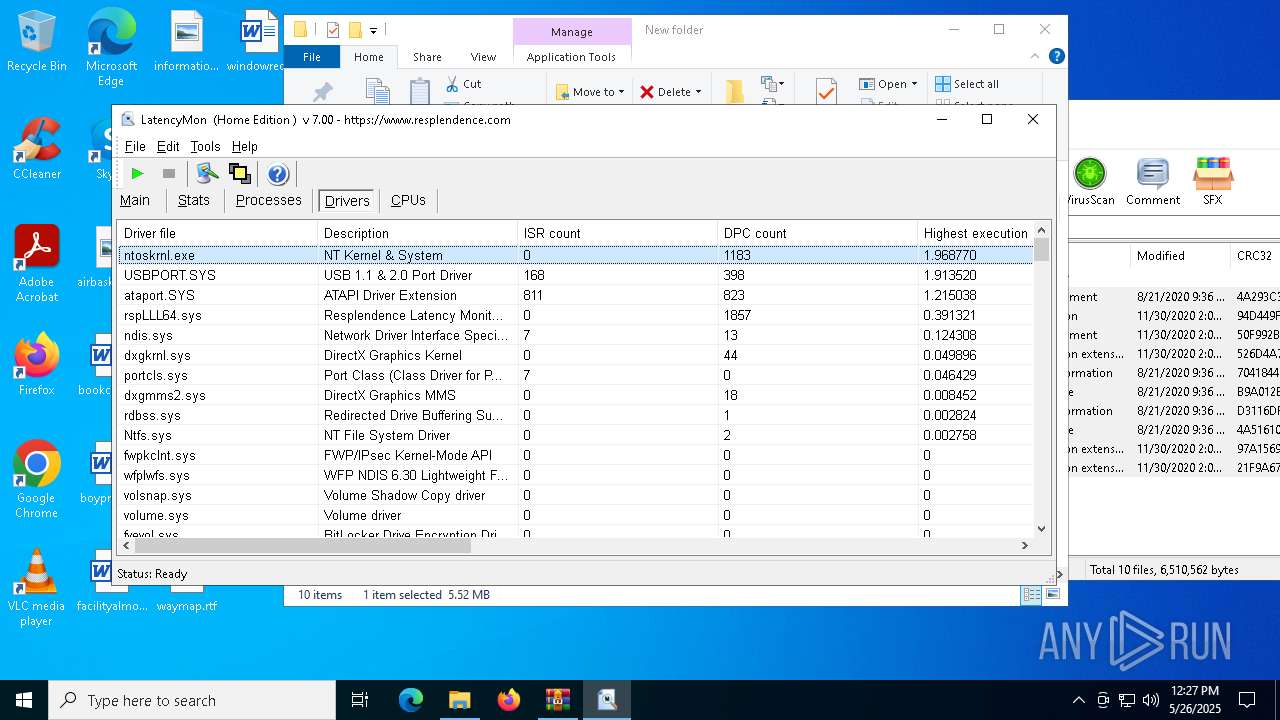
Creates files in the driver directory
- rundll32.exe (PID: 5968)
Launch of the file from Registry key
- rundll32.exe (PID: 5968)
Reads the time zone
- runonce.exe (PID: 1512)
Reads security settings of Internet Explorer
- runonce.exe (PID: 1512)
Create files in a temporary directory
- LatMon.exe (PID: 7392)
Compiled with Borland Delphi (YARA)
- LatMon.exe (PID: 7392)
Checks proxy server information
- slui.exe (PID: 1324)
Reads the software policy settings
- slui.exe (PID: 1324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:11:30 14:00:10 |
| ZipCRC: | 0x50f992b4 |
| ZipCompressedSize: | 2496 |
| ZipUncompressedSize: | 5656 |
| ZipFileName: | LICENSE.TXT |
Total processes
142
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | "C:\WINDOWS\system32\rundll32.exe" SETUPAPI.Dll,InstallHinfSection DefaultInstall 132 C:\Users\admin\Desktop\New folder\rspLLL64.inf | C:\Windows\System32\rundll32.exe | LatMon.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7364 | "C:\Users\admin\Desktop\New folder\LatMon.exe" | C:\Users\admin\Desktop\New folder\LatMon.exe | — | explorer.exe | |||||||||||
User: admin Company: Resplendence Software Projects Sp. Integrity Level: MEDIUM Description: LatencyMon Exit code: 3221226540 Version: 7.0.0.0 Modules
| |||||||||||||||
| 7392 | "C:\Users\admin\Desktop\New folder\LatMon.exe" | C:\Users\admin\Desktop\New folder\LatMon.exe | explorer.exe | ||||||||||||
User: admin Company: Resplendence Software Projects Sp. Integrity Level: HIGH Description: LatencyMon Version: 7.0.0.0 Modules
| |||||||||||||||
| 7560 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\LatencyMon.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 8112 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 118
Read events
4 076
Write events
28
Delete events
14
Modification events
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\LatencyMon.zip | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (7560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
14
Suspicious files
11
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\LatencyMon\rspLLL32.sys | executable | |
MD5:EF35273267D6A3FFE452FE66B7086184 | SHA256:7177177A69629BC2A8A7B1554AAA093001F2DE19950AD30897DBFE650F0FCE83 | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\LatencyMon\rspLLL32.inf | binary | |
MD5:7861A7C64115A43EBB2794E85C14B30C | SHA256:1CA9EB617AA37F5BEDD455A20C75ECE82FE88E2ECA9AA9CBDA154BBE4B25C0BB | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\LatencyMon\LICENSE.TXT | text | |
MD5:05F764ADD8A7665E4FD768A459A4B572 | SHA256:9D47979909A1796EC51F447BA224016B3D2054EFD3AEF8EB8C0195264F5ADEC2 | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7560.16636\rspLLL32.sys | executable | |
MD5:EF35273267D6A3FFE452FE66B7086184 | SHA256:7177177A69629BC2A8A7B1554AAA093001F2DE19950AD30897DBFE650F0FCE83 | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\LatencyMon\rspSymSrv32.dll | executable | |
MD5:966B66E93427B4670953C5C55BC996F2 | SHA256:85D10A09E57F56B7576D3AD7E98716D9A0A92C00FE8AAE70FF1B3B0C94E30353 | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\LatencyMon\LatencyMon.txt | text | |
MD5:312F63970E1C5A3251227345C2BC0E27 | SHA256:3E8EA16D47F40DAA82C2121F8072CFBDC72D143A0E20DDB31A0CC985F4BC1293 | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7560.16636\rspLLL32.inf | binary | |
MD5:7861A7C64115A43EBB2794E85C14B30C | SHA256:1CA9EB617AA37F5BEDD455A20C75ECE82FE88E2ECA9AA9CBDA154BBE4B25C0BB | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\LatencyMon\LatMon.exe | executable | |
MD5:B4936C6125FD8336034CA8077452800A | SHA256:BDE387A7F7519614B9408723019A35F84C0294DFA0C802CF1AA37DDB890BC051 | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7560.16636\rspDisMon32.dll | executable | |
MD5:CD74828FBF465ECA3F1F34342331D075 | SHA256:6860781A468B810D42E7CA7F0F153402284696338486B5A820DEBFEBF1F7570E | |||
| 7560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7560.16636\LICENSE.TXT | text | |
MD5:05F764ADD8A7665E4FD768A459A4B572 | SHA256:9D47979909A1796EC51F447BA224016B3D2054EFD3AEF8EB8C0195264F5ADEC2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7248 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7248 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7248 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7248 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |