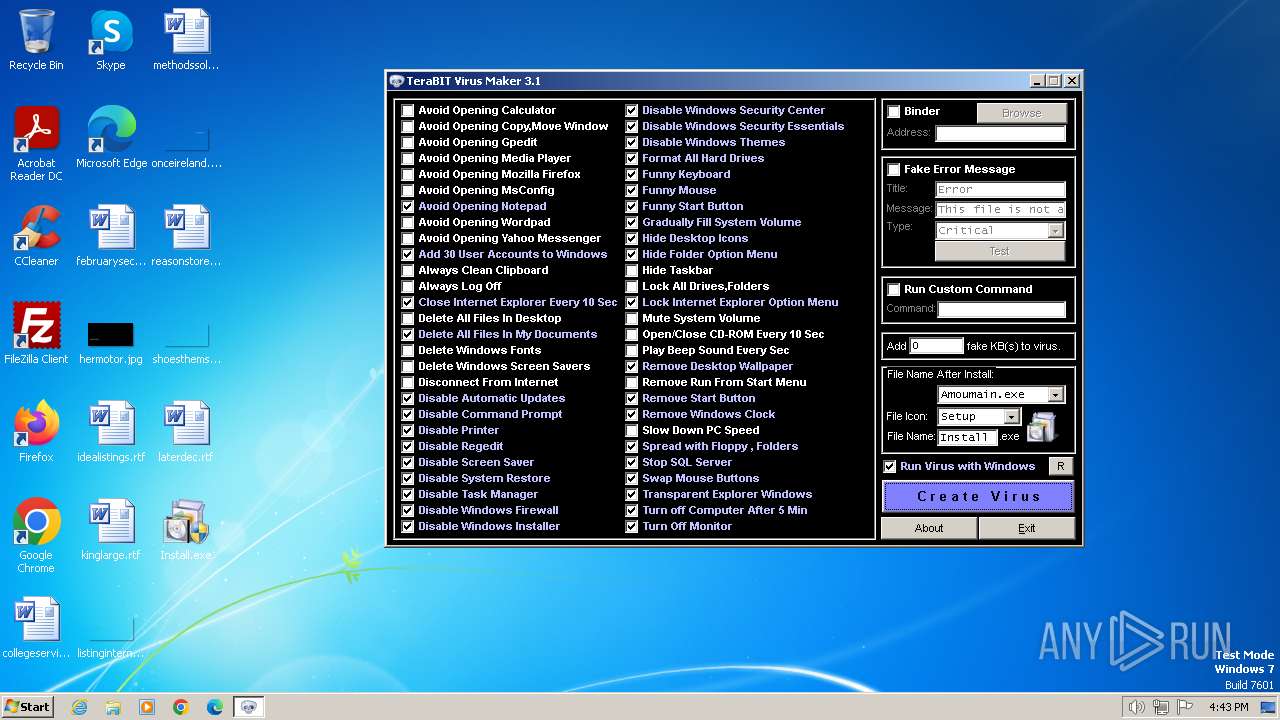
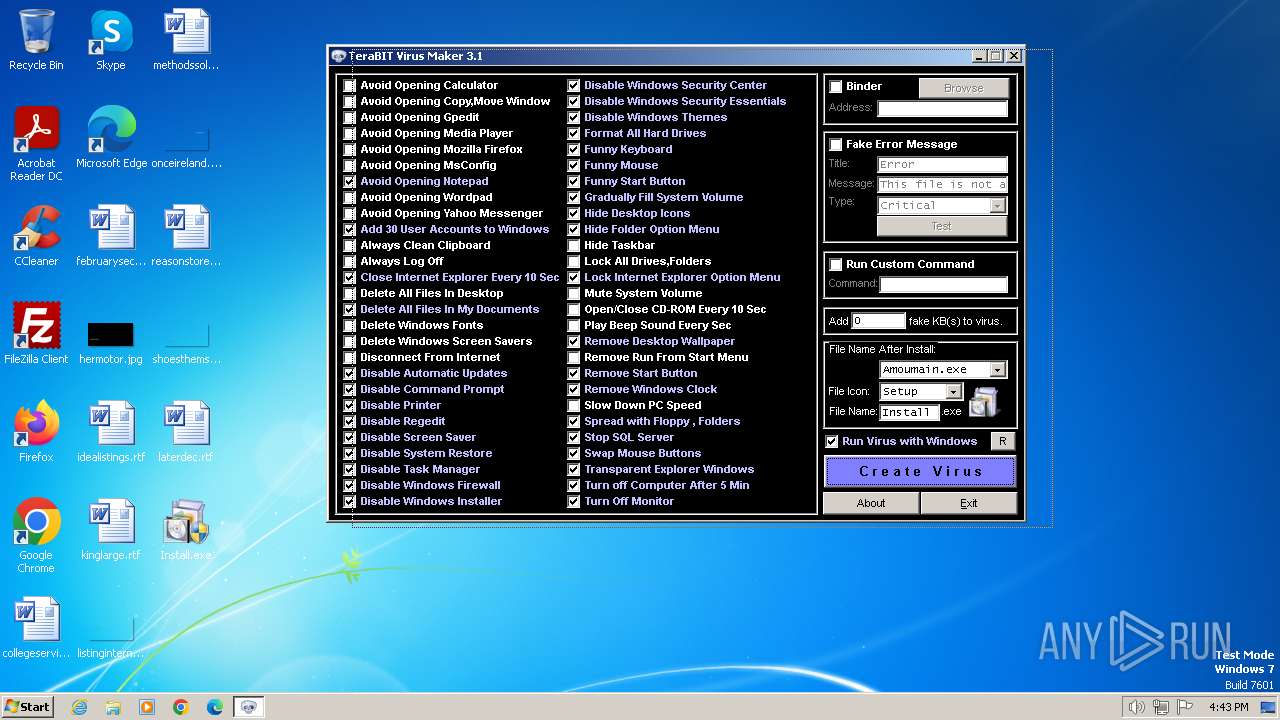
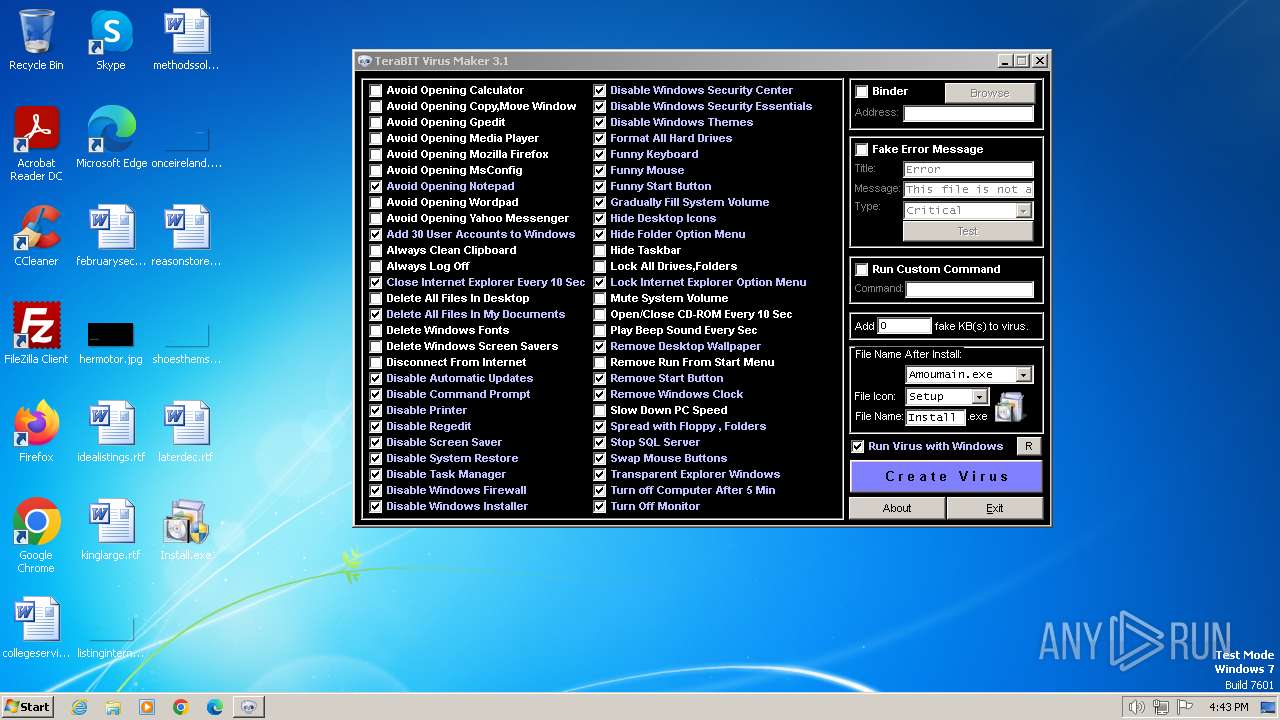
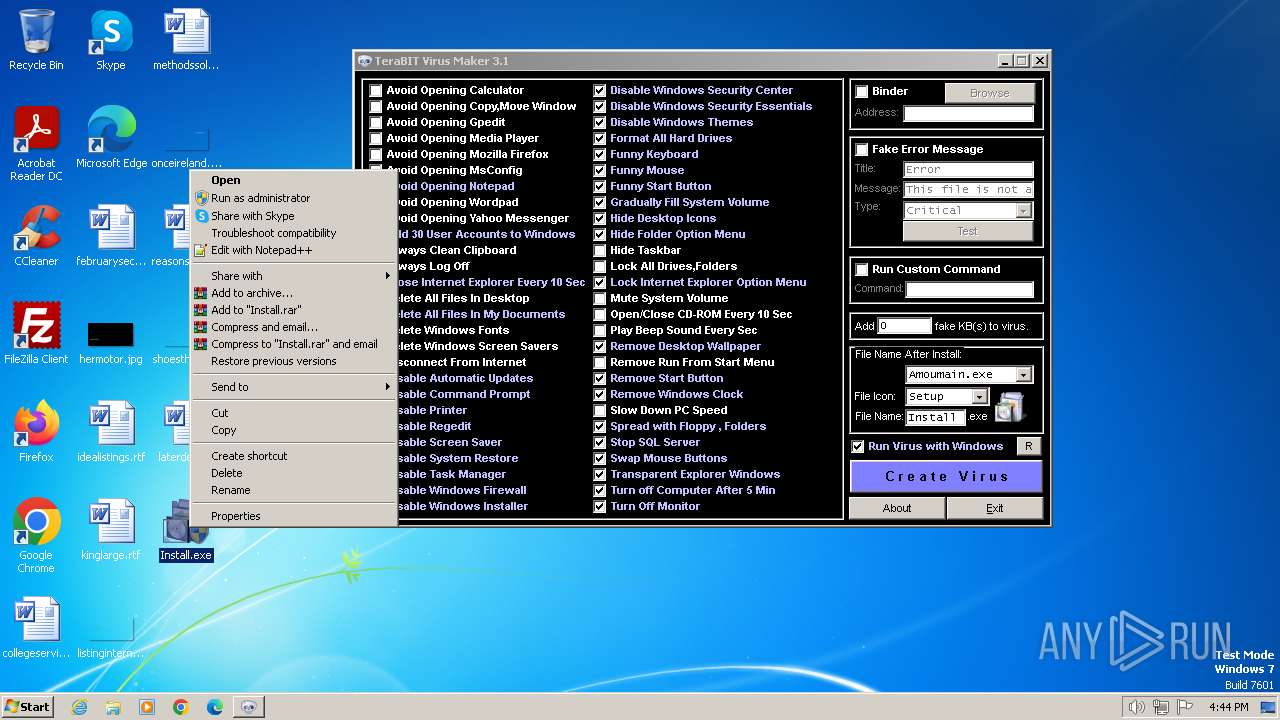
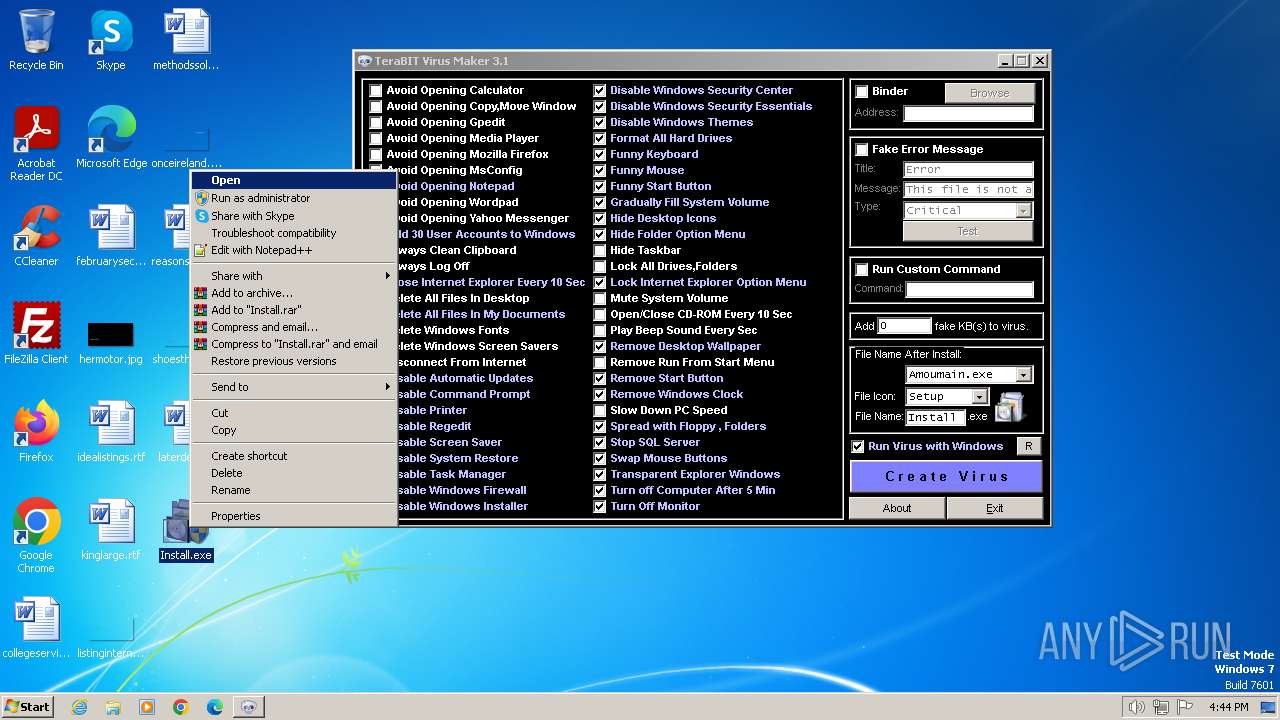
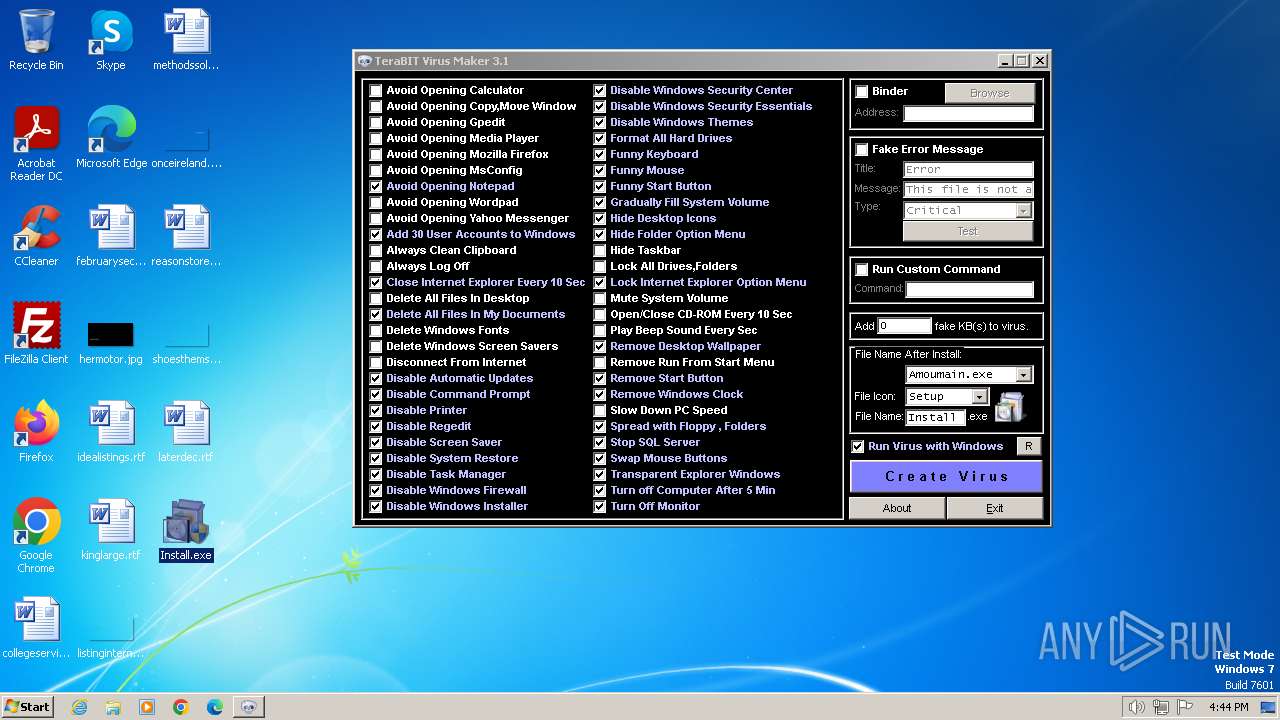
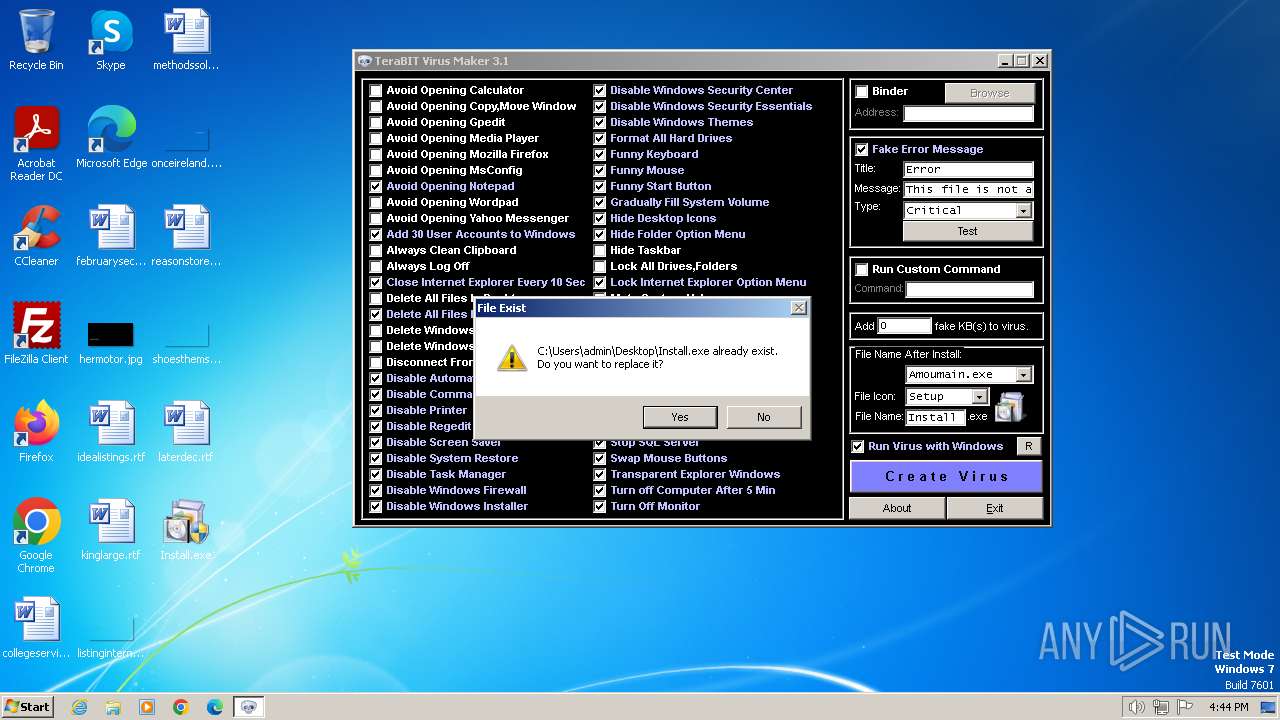
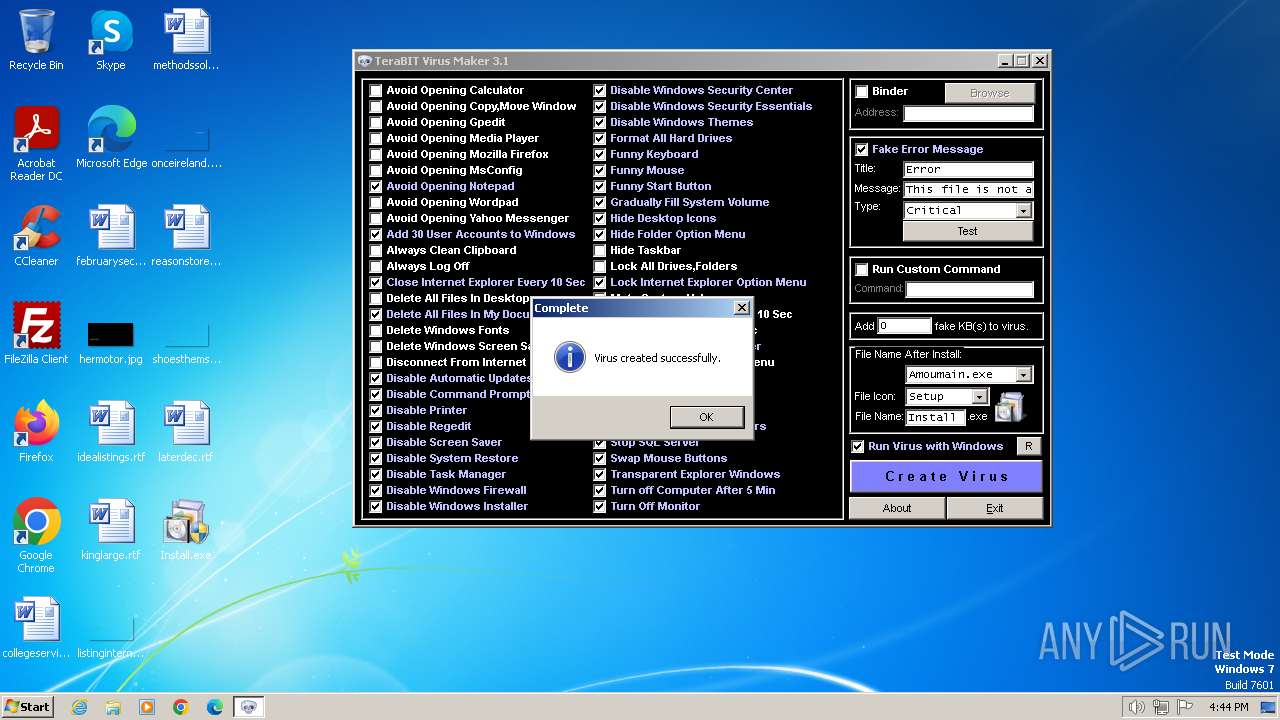
| File name: | tVirusMaker.exe |
| Full analysis: | https://app.any.run/tasks/5a5b9ac1-cff3-4c95-a173-748ac4cda7f9 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2024, 16:42:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5B7CBFC8D8BC22798EE4FC4AA4B03E3B |
| SHA1: | 76F643B3F67F76F4182EF18E43E298E2E8570044 |
| SHA256: | 35BCBAE8DD3191CF58C48618D0CC43FB8FEE8493E7C872D7742B4D499C383AF9 |
| SSDEEP: | 24576:Enu3UN6V2C2G2y2m2rG7GYGCGqG7WGWxW0WwWaw6ESwJcIczdrhrw:EnAUN6V2C2G2y2m2rG7GYGCGqG7WGWxY |
MALICIOUS
Drops the executable file immediately after the start
- tVirusMaker.exe (PID: 2120)
- CCleaner.exe (PID: 3764)
Steals credentials from Web Browsers
- taskhost.exe (PID: 1368)
- CCleaner.exe (PID: 3764)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 3764)
SUSPICIOUS
Creates file in the systems drive root
- tVirusMaker.exe (PID: 2120)
Executable content was dropped or overwritten
- tVirusMaker.exe (PID: 2120)
- CCleaner.exe (PID: 3764)
The process executes via Task Scheduler
- CCleaner.exe (PID: 3764)
Reads Internet Explorer settings
- CCleaner.exe (PID: 3764)
Searches for installed software
- CCleaner.exe (PID: 3764)
Checks Windows Trust Settings
- CCleaner.exe (PID: 3764)
Reads the date of Windows installation
- CCleaner.exe (PID: 3764)
Reads settings of System Certificates
- CCleaner.exe (PID: 3764)
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 3764)
Reads the Internet Settings
- CCleaner.exe (PID: 3764)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 3764)
The process verifies whether the antivirus software is installed
- CCleaner.exe (PID: 3764)
Executes as Windows Service
- taskhost.exe (PID: 1368)
- taskhost.exe (PID: 3984)
Non-standard symbols in registry
- CCleaner.exe (PID: 3764)
Reads browser cookies
- CCleaner.exe (PID: 3764)
Starts application from unusual location
- CCleaner.exe (PID: 3764)
Process drops legitimate windows executable
- CCleaner.exe (PID: 3764)
INFO
Reads the computer name
- tVirusMaker.exe (PID: 2120)
- CCleaner.exe (PID: 3764)
- CCleaner.exe (PID: 2444)
Manual execution by a user
- Install.exe (PID: 2372)
- Install.exe (PID: 1368)
- Install.exe (PID: 116)
- Install.exe (PID: 680)
- Install.exe (PID: 1112)
- Install.exe (PID: 2364)
- Install.exe (PID: 2244)
- Install.exe (PID: 3680)
- Install.exe (PID: 1808)
- Install.exe (PID: 1336)
- Install.exe (PID: 2112)
- Install.exe (PID: 2468)
- Install.exe (PID: 844)
- Install.exe (PID: 3520)
- Install.exe (PID: 2128)
- Install.exe (PID: 2052)
- Install.exe (PID: 1404)
- Install.exe (PID: 2828)
- Install.exe (PID: 712)
- Install.exe (PID: 3088)
- Install.exe (PID: 1652)
- msedge.exe (PID: 3468)
- Install.exe (PID: 2028)
- CCleaner.exe (PID: 2444)
Checks supported languages
- Install.exe (PID: 1368)
- Install.exe (PID: 1112)
- Install.exe (PID: 2364)
- tVirusMaker.exe (PID: 2120)
- Install.exe (PID: 2244)
- Install.exe (PID: 844)
- Install.exe (PID: 2128)
- Install.exe (PID: 3520)
- Install.exe (PID: 2052)
- Install.exe (PID: 3680)
- Install.exe (PID: 712)
- Install.exe (PID: 2028)
- CCleaner.exe (PID: 2444)
- CCleaner.exe (PID: 3764)
- Install.exe (PID: 2828)
Reads the machine GUID from the registry
- tVirusMaker.exe (PID: 2120)
- CCleaner.exe (PID: 3764)
Application launched itself
- msedge.exe (PID: 3468)
Reads Environment values
- CCleaner.exe (PID: 2444)
- CCleaner.exe (PID: 3764)
Reads CPU info
- CCleaner.exe (PID: 3764)
Reads product name
- CCleaner.exe (PID: 3764)
Creates files in the program directory
- CCleaner.exe (PID: 3764)
Reads the software policy settings
- CCleaner.exe (PID: 3764)
Checks proxy server information
- CCleaner.exe (PID: 3764)
Creates files or folders in the user directory
- CCleaner.exe (PID: 3764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (48.5) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (18.4) |
| .exe | | | Win64 Executable (generic) (16.3) |
| .scr | | | Windows screen saver (7.7) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:01:15 09:00:54+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 206336 |
| InitializedDataSize: | 488960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x23ec |
| OSVersion: | 5 |
| ImageVersion: | 3.1 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.0.0 |
| ProductVersionNumber: | 3.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | TeraBIT |
| LegalCopyright: | Copyright © 2006-2009 TeraBIT. |
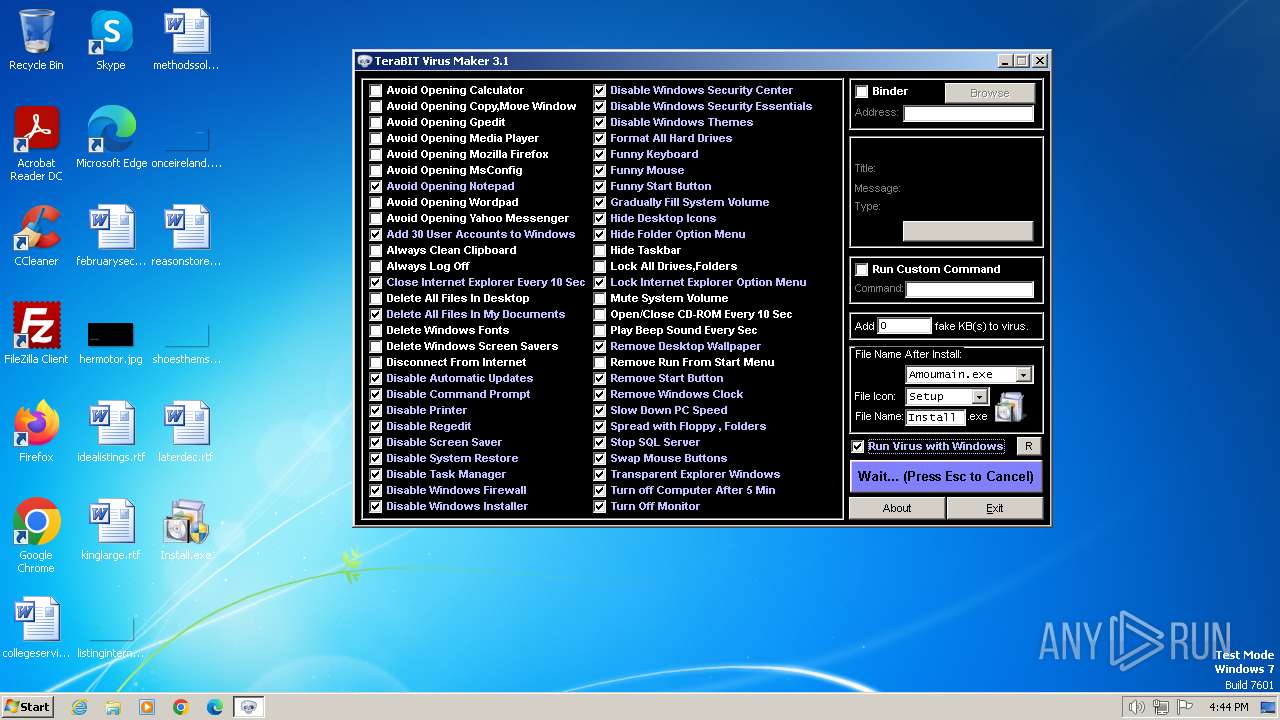
| ProductName: | TeraBIT Virus Maker |
| FileVersion: | 3.01 |
| ProductVersion: | 3.01 |
| InternalName: | tVirusMaker |
| OriginalFileName: | tVirusMaker.exe |
Total processes
96
Monitored processes
35
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | — | explorer.exe | |||||||||||
User: admin Company: None Integrity Level: MEDIUM Exit code: 3221226540 Version: 3.01 Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | — | explorer.exe | |||||||||||
User: admin Company: None Integrity Level: MEDIUM Exit code: 3221226540 Version: 3.01 Modules
| |||||||||||||||
| 712 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | explorer.exe | ||||||||||||
User: admin Company: None Integrity Level: HIGH Exit code: 0 Version: 3.01 Modules
| |||||||||||||||
| 844 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | explorer.exe | ||||||||||||
User: admin Company: None Integrity Level: HIGH Exit code: 0 Version: 3.01 Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | explorer.exe | ||||||||||||
User: admin Company: None Integrity Level: HIGH Exit code: 0 Version: 3.01 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1548 --field-trial-handle=1356,i,4661717187805476074,11254164354440486195,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6bc4f598,0x6bc4f5a8,0x6bc4f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1336 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | — | explorer.exe | |||||||||||
User: admin Company: None Integrity Level: MEDIUM Exit code: 3221226540 Version: 3.01 Modules
| |||||||||||||||
| 1368 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | explorer.exe | ||||||||||||
User: admin Company: None Integrity Level: HIGH Exit code: 0 Version: 3.01 Modules
| |||||||||||||||
| 1368 | "taskhost.exe" | C:\Windows\System32\taskhost.exe | services.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
35 420
Read events
35 058
Write events
281
Delete events
81
Modification events
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\18C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\18C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\18C\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Common Files\system\wab32res.dll,-10100 |
Value: Contacts | |||
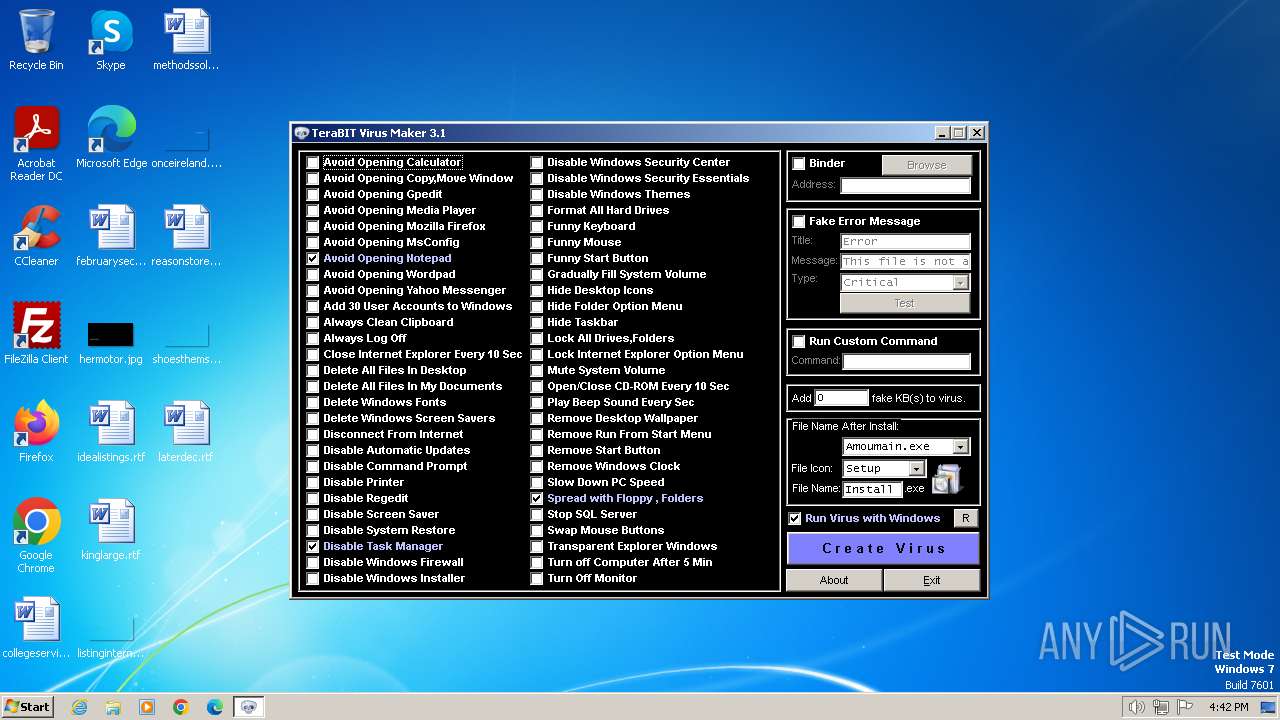
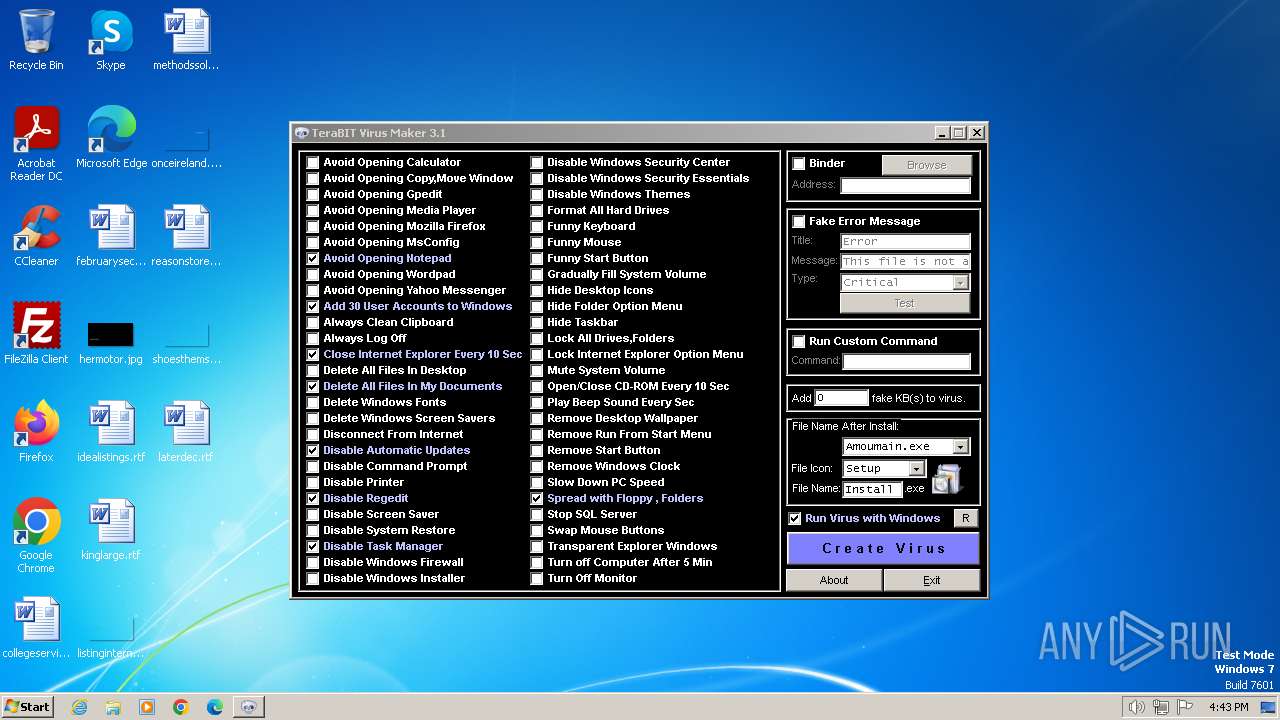
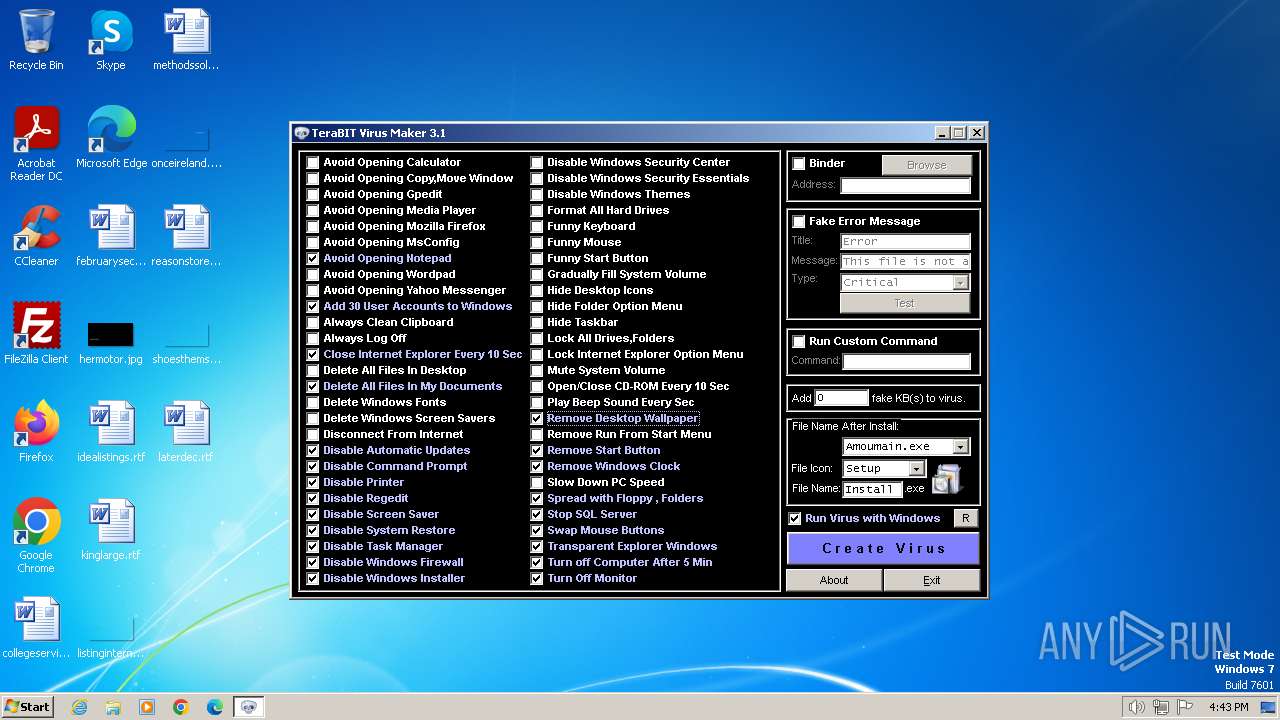
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CURRENT_USER\Software\TeraBIT Virus Maker\3.1 |
| Operation: | write | Name: | Options |
Value: 0000001001001010001111111111111111111001000101111111111 | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CURRENT_USER\Software\TeraBIT Virus Maker\3.1 |
| Operation: | write | Name: | BinderEnabled |
Value: 0 | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CURRENT_USER\Software\TeraBIT Virus Maker\3.1 |
| Operation: | write | Name: | BinderAddress |
Value: | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CURRENT_USER\Software\TeraBIT Virus Maker\3.1 |
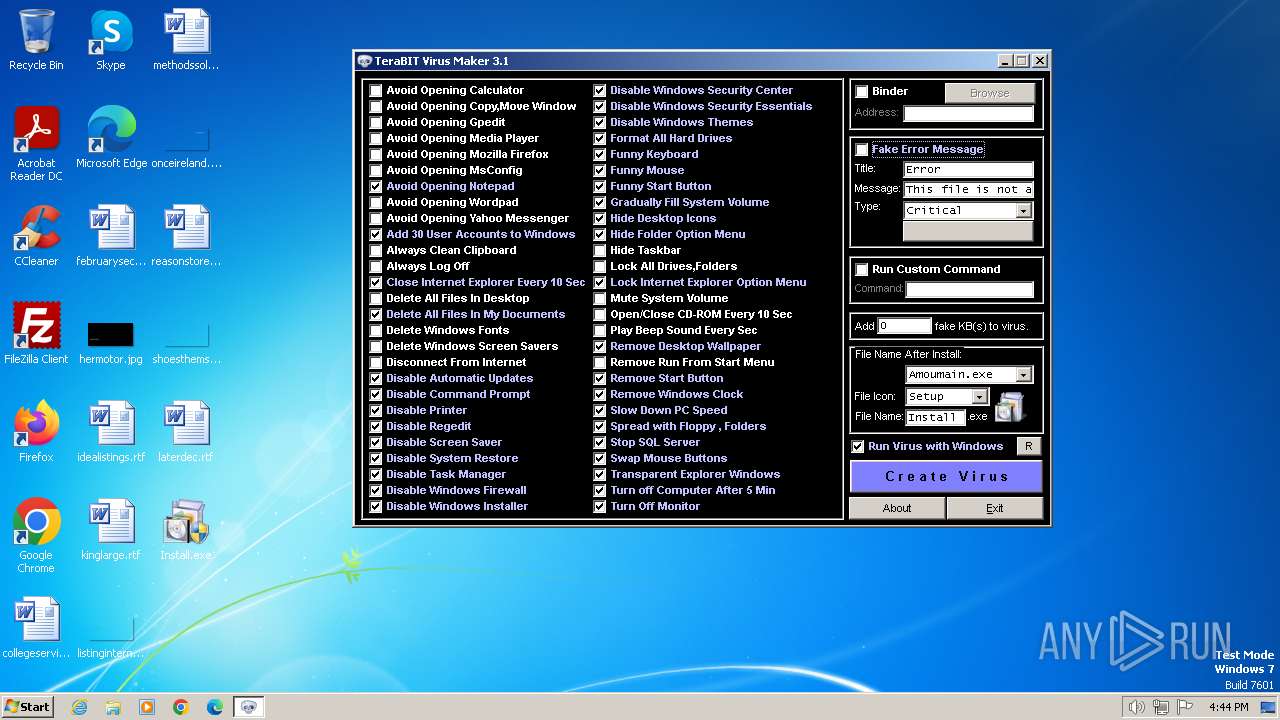
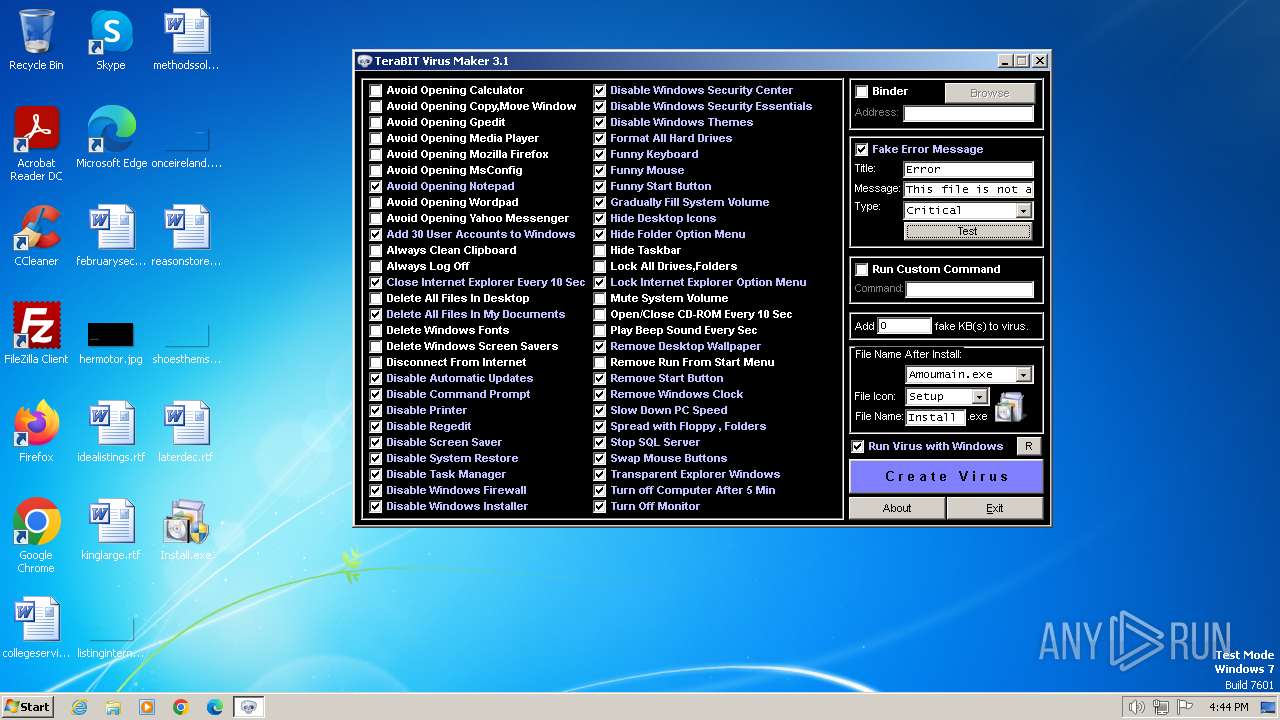
| Operation: | write | Name: | FakeErrorEnabled |
Value: 1 | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CURRENT_USER\Software\TeraBIT Virus Maker\3.1 |
| Operation: | write | Name: | FakeErrorTitle |
Value: Error | |||
| (PID) Process: | (2120) tVirusMaker.exe | Key: | HKEY_CURRENT_USER\Software\TeraBIT Virus Maker\3.1 |
| Operation: | write | Name: | FakeErrorMessage |
Value: This file is not a valid Win32 application. | |||
Executable files
18
Suspicious files
145
Text files
101
Unknown types
55
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3468 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF19c8e4.TMP | — | |
MD5:— | SHA256:— | |||
| 3468 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3468 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF19c922.TMP | — | |
MD5:— | SHA256:— | |||
| 3468 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3468 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF19c980.TMP | — | |
MD5:— | SHA256:— | |||
| 3468 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1316 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3468 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF19c867.TMP | text | |
MD5:2E4F5B4F652DAFFD9C80C58770313C9C | SHA256:21BC9F7B1F0EC2B6DF8435AC271D31602B57FBE030AFAB94761F399CF3D9076E | |||
| 2120 | tVirusMaker.exe | C:\Users\admin\Desktop\RCXF8D2.tmp | executable | |
MD5:53550C8017F50F7A42EF4F1D516398C1 | SHA256:CBE60AD3D81CBE47A5D9BD1BC06873FEDB0EE8CA79BC6314B1A5BE81FCAF93BC | |||
| 2120 | tVirusMaker.exe | C:\Users\admin\Desktop\RCX9C19.tmp | executable | |
MD5:53550C8017F50F7A42EF4F1D516398C1 | SHA256:CBE60AD3D81CBE47A5D9BD1BC06873FEDB0EE8CA79BC6314B1A5BE81FCAF93BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
49
DNS requests
72
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3764 | CCleaner.exe | GET | 304 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b0854c7d12bbbc12 | unknown | — | — | unknown |
3764 | CCleaner.exe | GET | 200 | 23.50.131.31:80 | http://ncc.avast.com/ncc.txt | unknown | text | 26 b | unknown |
3764 | CCleaner.exe | GET | 304 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f2de55c7f8a18d73 | unknown | — | — | unknown |
3764 | CCleaner.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3764 | CCleaner.exe | GET | 304 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ea61611344efb70f | unknown | — | — | unknown |
3764 | CCleaner.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/s/gts1d4/gnsqRwyByMM/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQDjr%2FaO77sJZwqcOJfYDI%2Fi | unknown | binary | 472 b | unknown |
3764 | CCleaner.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD6BeWhIbleexId20FpK0af | unknown | binary | 472 b | unknown |
3764 | CCleaner.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/s/gts1d4/cNag_9NZQXw/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQCDWDmf4XmFvBJNZm86rLoj | unknown | binary | 472 b | unknown |
488 | lsass.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
3764 | CCleaner.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3468 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
2496 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2496 | msedge.exe | 204.79.197.203:443 | api.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2496 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2496 | msedge.exe | 23.53.42.177:443 | assets.msn.com | Akamai International B.V. | DE | unknown |
2496 | msedge.exe | 18.244.18.32:443 | sb.scorecardresearch.com | — | US | unknown |
2496 | msedge.exe | 2.21.20.136:443 | img-s-msn-com.akamaized.net | Akamai International B.V. | DE | unknown |
2496 | msedge.exe | 92.122.215.60:443 | th.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
assets.msn.com |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
th.bing.com |
| whitelisted |
api.msn.com |
| whitelisted |
c.bing.com |
| whitelisted |
c.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
3764 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner.exe | [2024-03-22 16:44:41.442] [error ] [settings ] [ 3764: 2124] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | [2024-03-22 16:44:42.489] [error ] [settings ] [ 3764: 2532] [9434E9: 359] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2024-03-22 16:44:42.536] [error ] [Burger ] [ 3764: 2532] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | [2024-03-22 16:44:42.536] [error ] [Burger ] [ 3764: 2532] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | startCheckingLicense()
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|