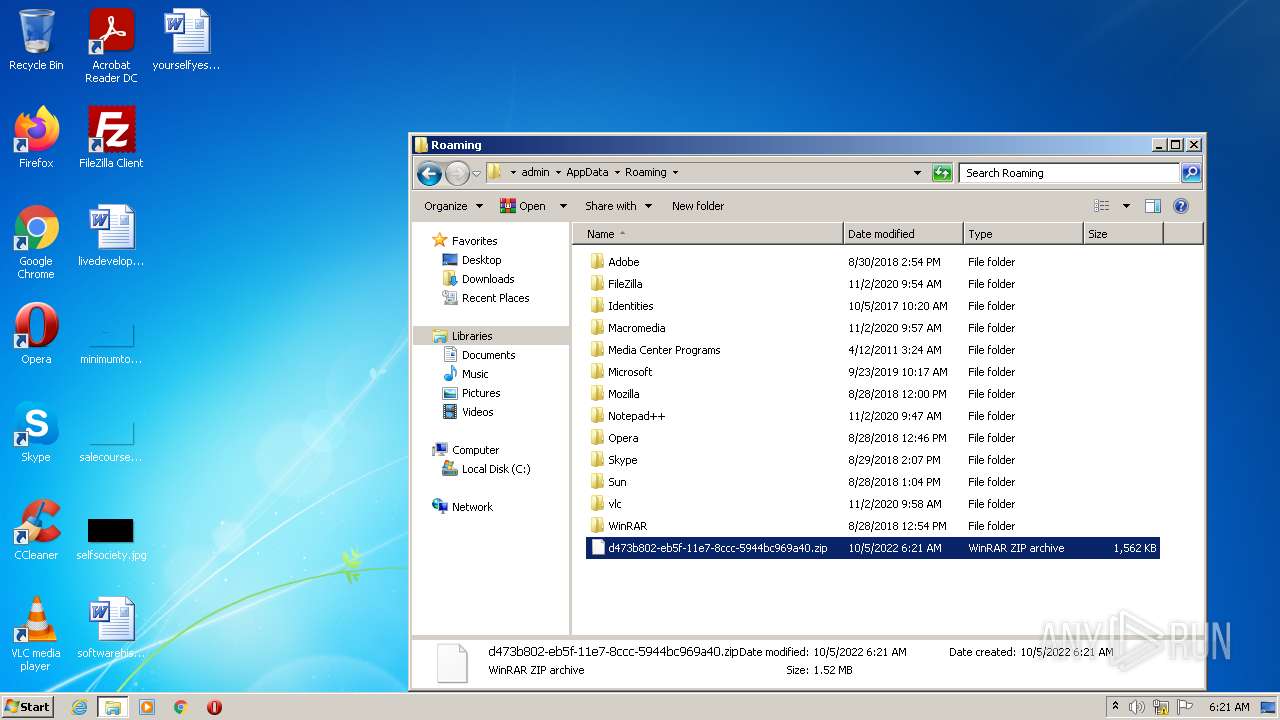
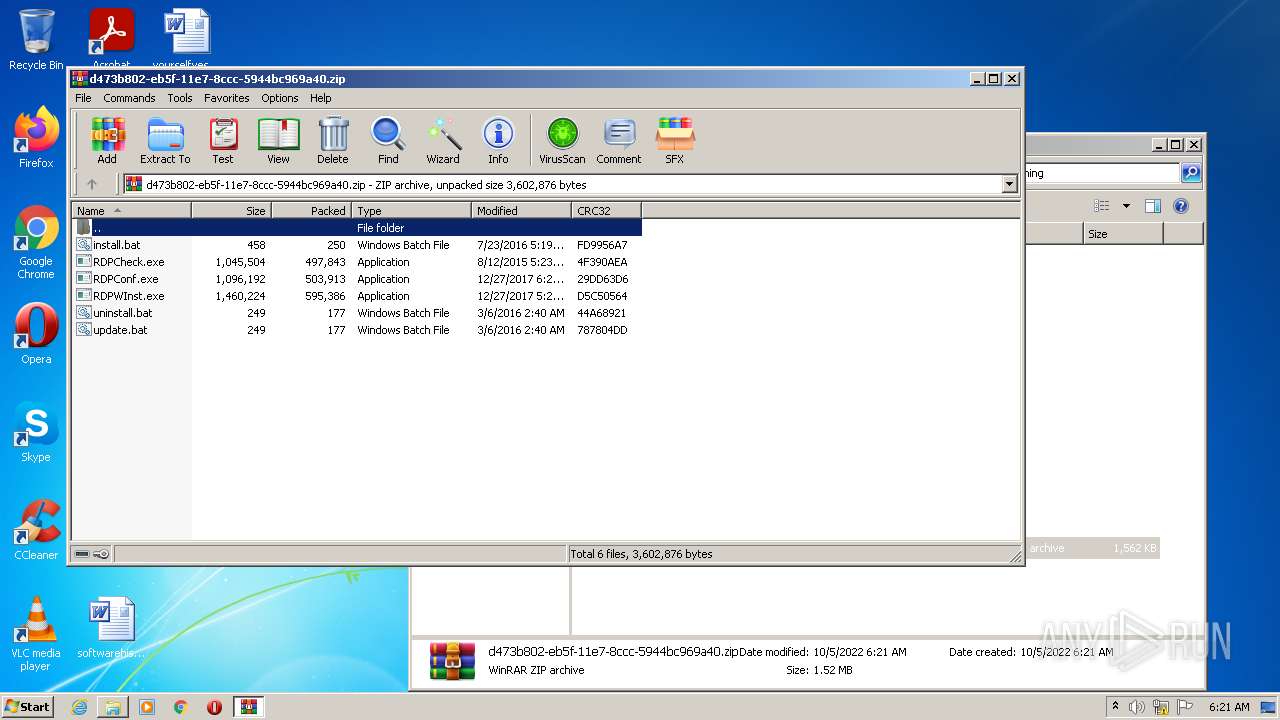
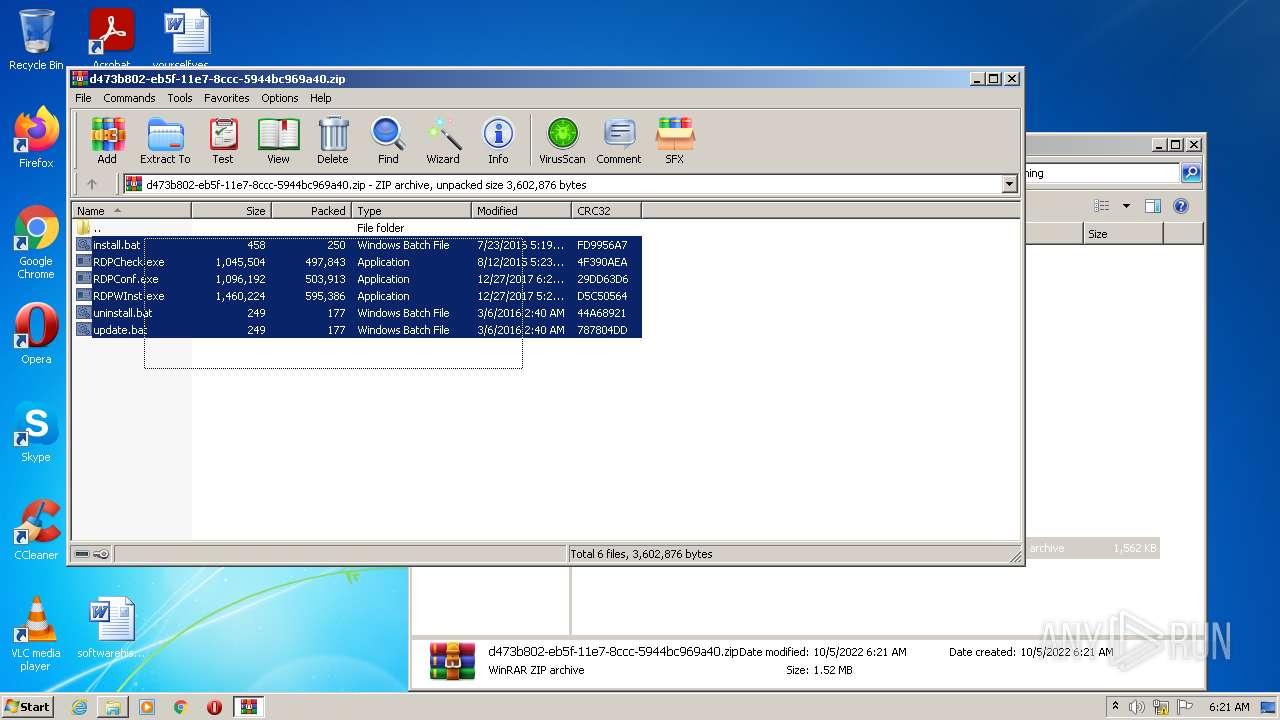
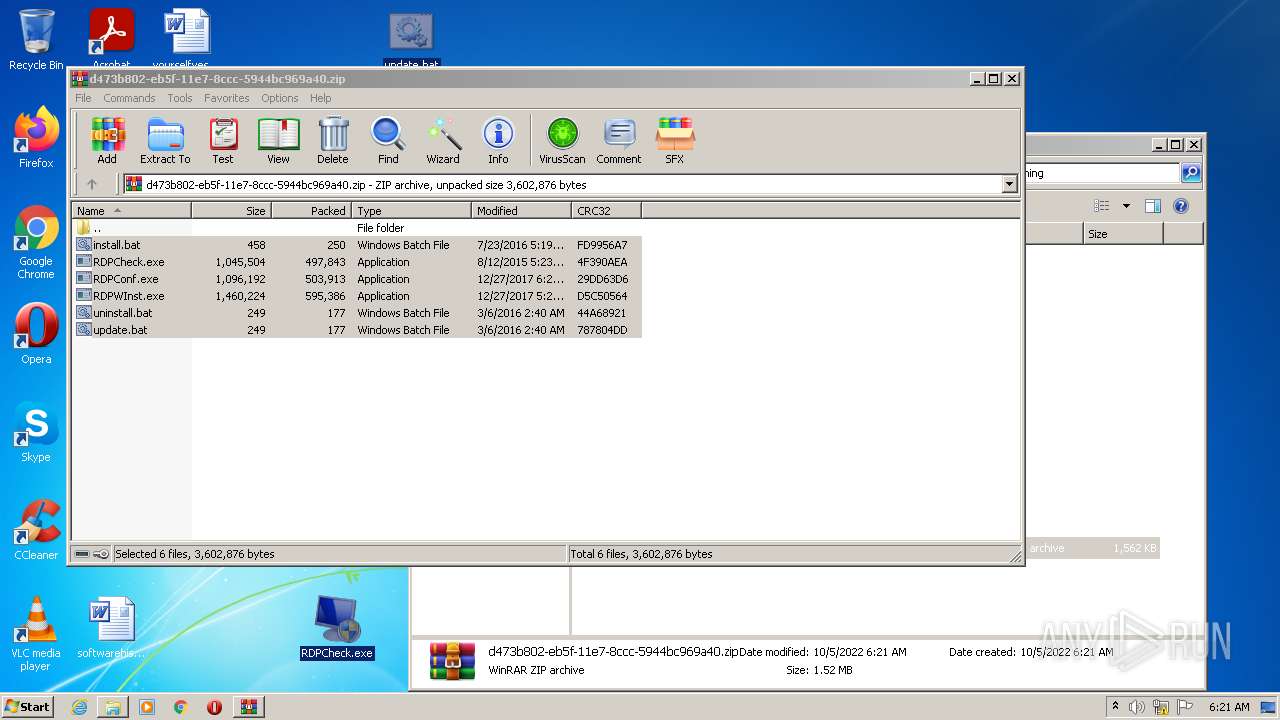
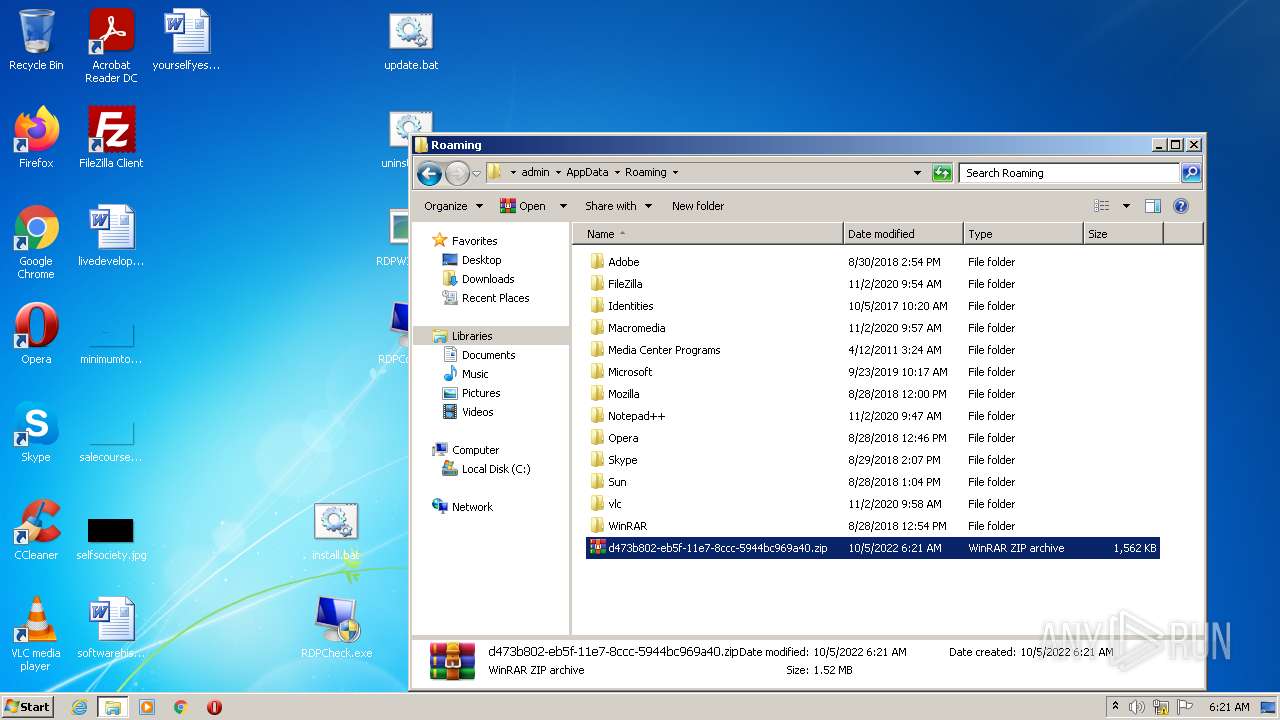
| File name: | d473b802-eb5f-11e7-8ccc-5944bc969a40 |
| Full analysis: | https://app.any.run/tasks/2eefce09-516e-416b-8949-f6cd51d5638d |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 05:21:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C26A2C5F6154225E8D83C4000306F162 |
| SHA1: | 67C586CEDBF0852AA52268311841CBAC5C96FDF8 |
| SHA256: | 35A9481DDBED5177431A9EA4BD09468FE987797D7B1231D64942D17EB54EC269 |
| SSDEEP: | 49152:cPEbpqUPr0OMPjmNgyV24OXxr2/NV0CA7QUmu4LnB:cPEbpPPrC4gWFOBr4Wfg |
MALICIOUS
Loads dropped or rewritten executable
- svchost.exe (PID: 2496)
- spoolsv.exe (PID: 896)
Application was dropped or rewritten from another process
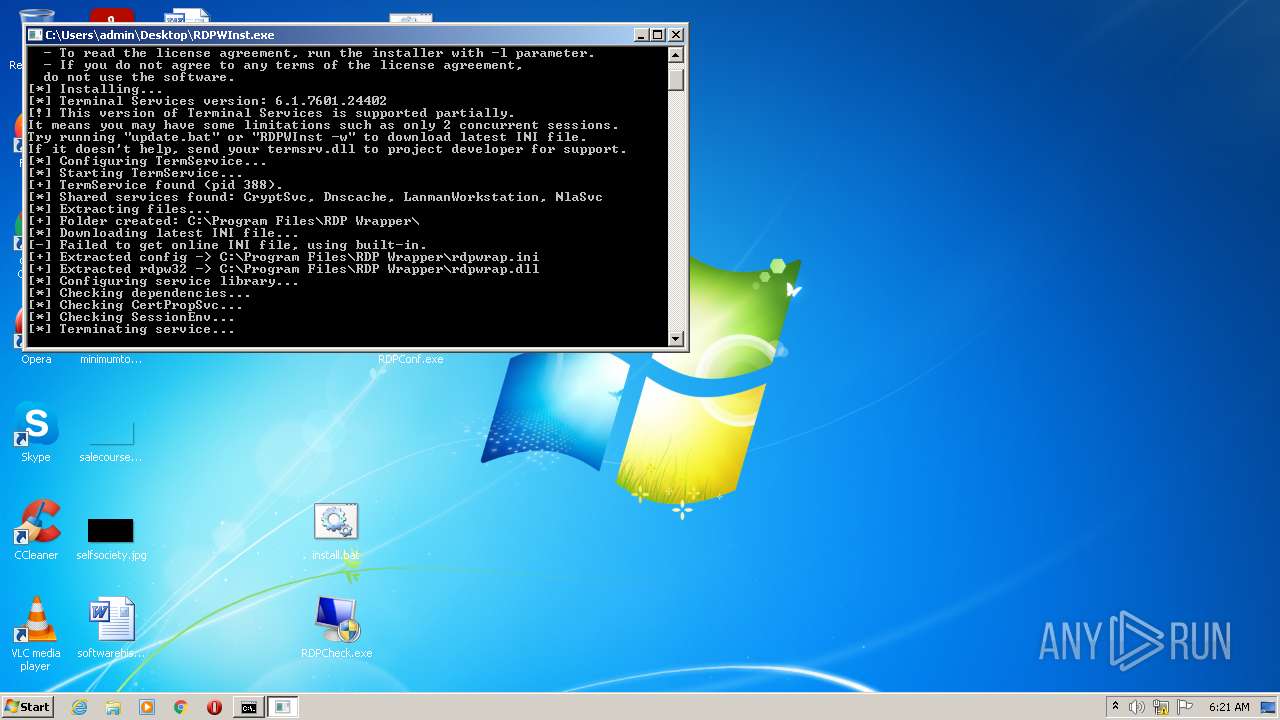
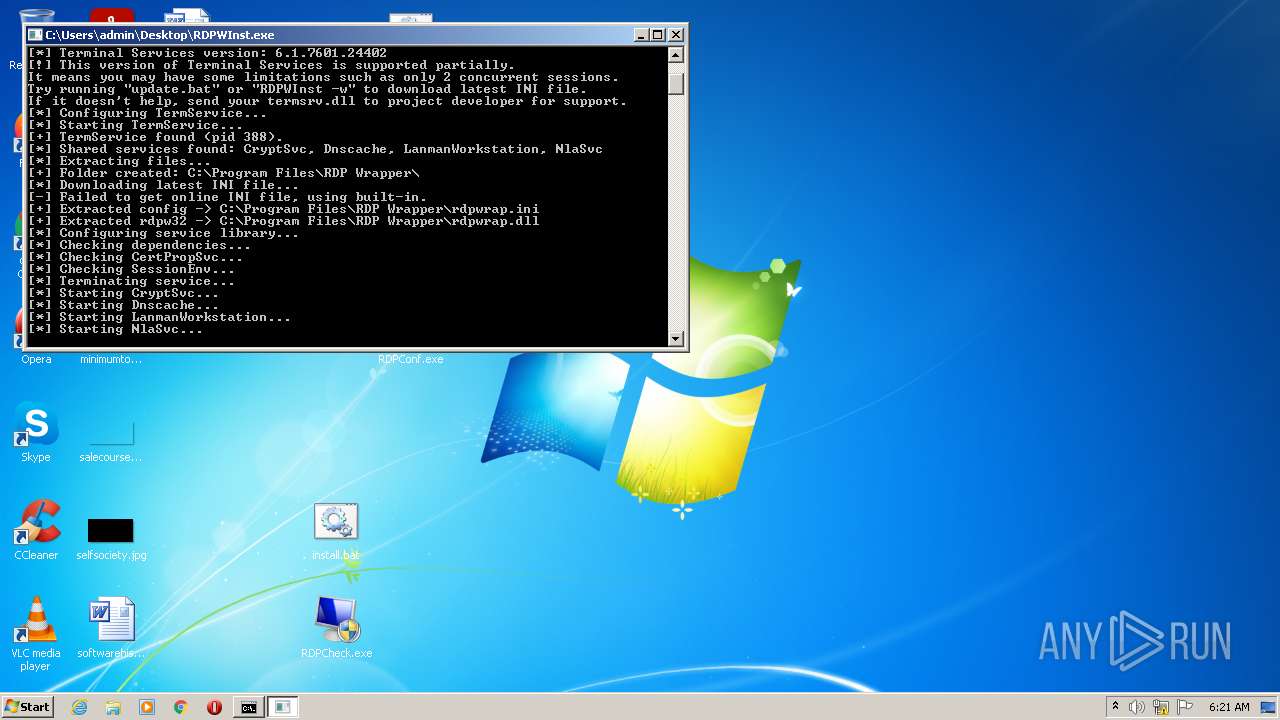
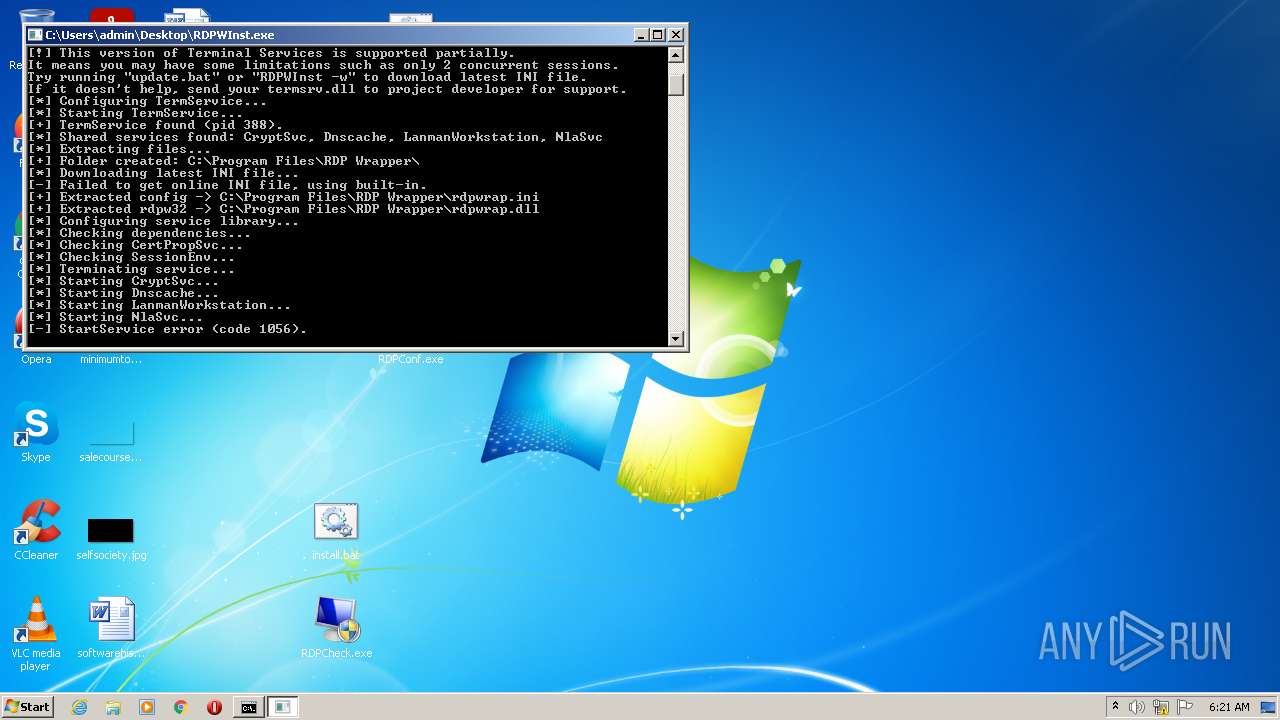
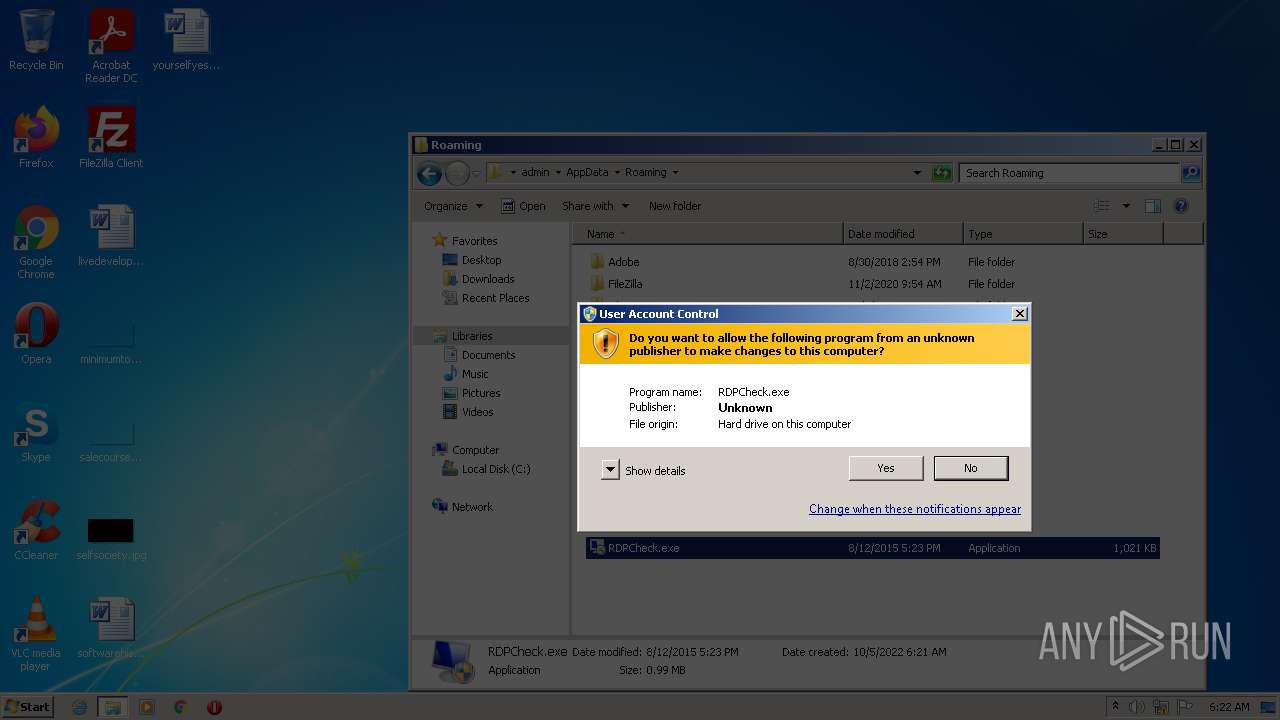
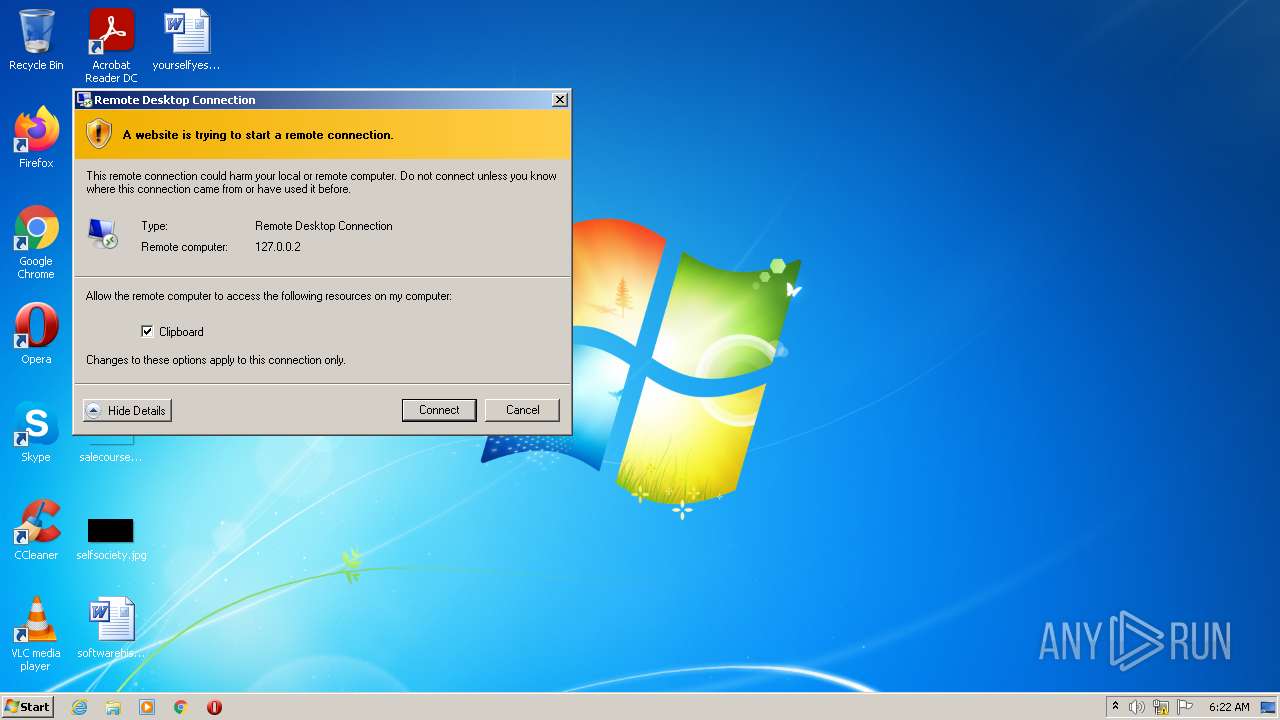
- RDPWInst.exe (PID: 3384)
- RDPWInst.exe (PID: 2576)
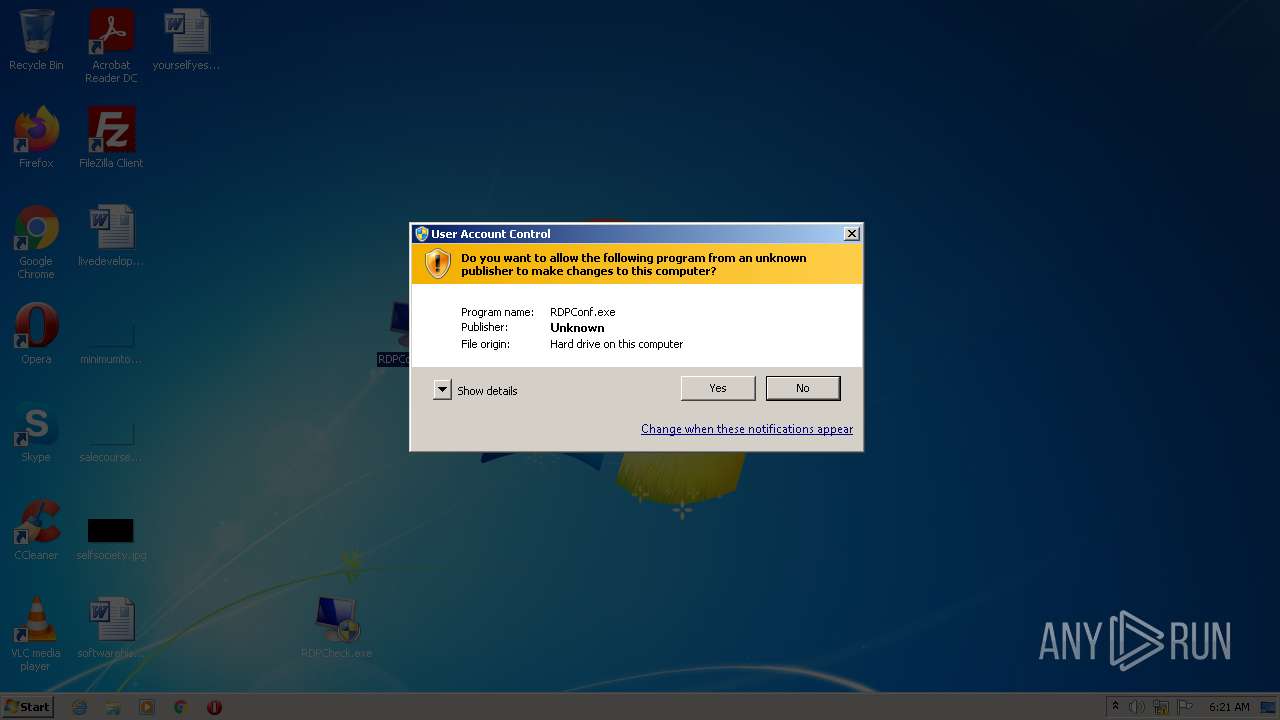
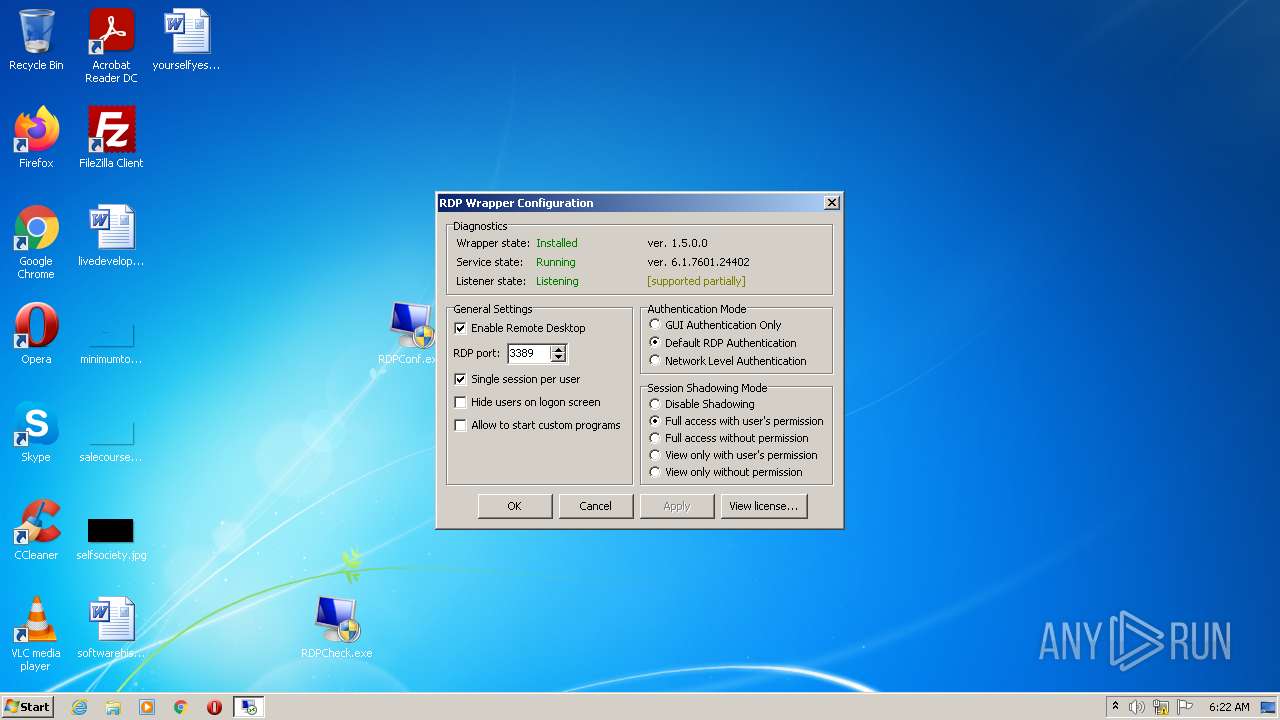
- RDPConf.exe (PID: 3640)
- RDPWInst.exe (PID: 2800)
- RDPCheck.exe (PID: 3360)
- RDPConf.exe (PID: 2408)
- RDPCheck.exe (PID: 3304)
SUSPICIOUS
Application launched itself
- chrmstp.exe (PID: 1432)
- ie4uinit.exe (PID: 4088)
- rundll32.exe (PID: 2648)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
Total processes
107
Monitored processes
41
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | C:\Windows\System32\ie4uinit.exe -ClearIconCache | C:\Windows\System32\ie4uinit.exe | — | ie4uinit.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
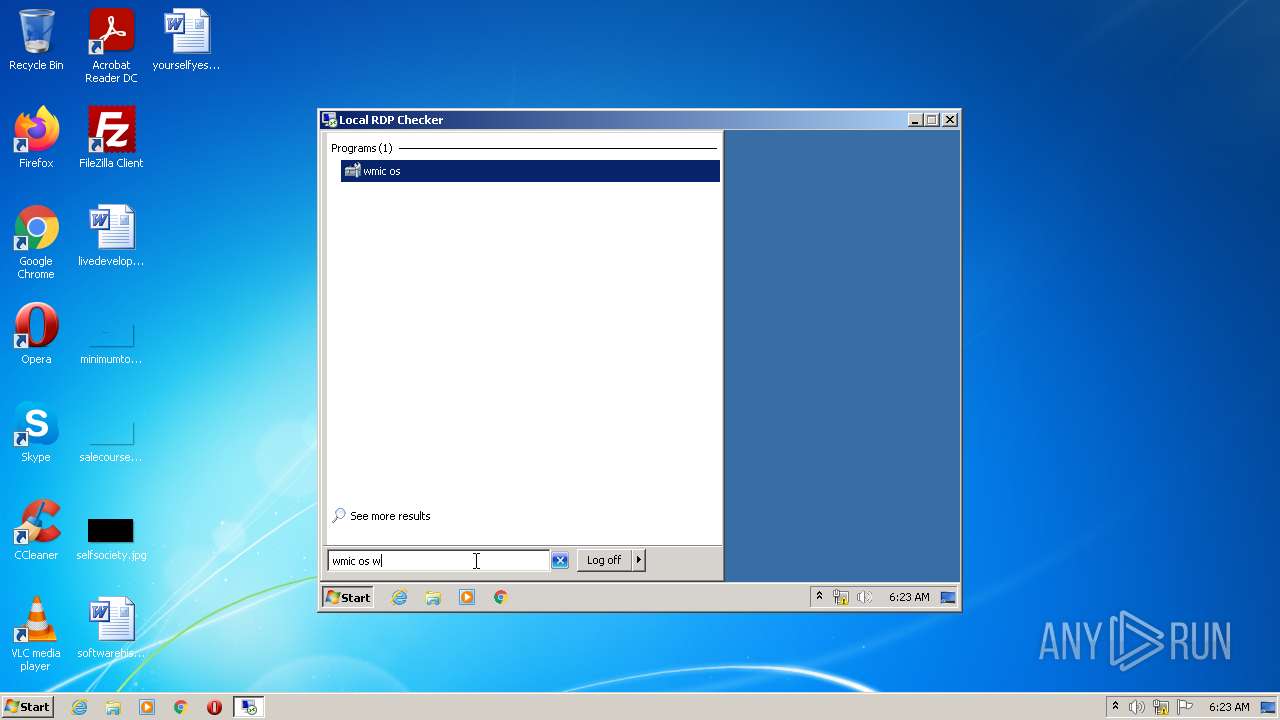
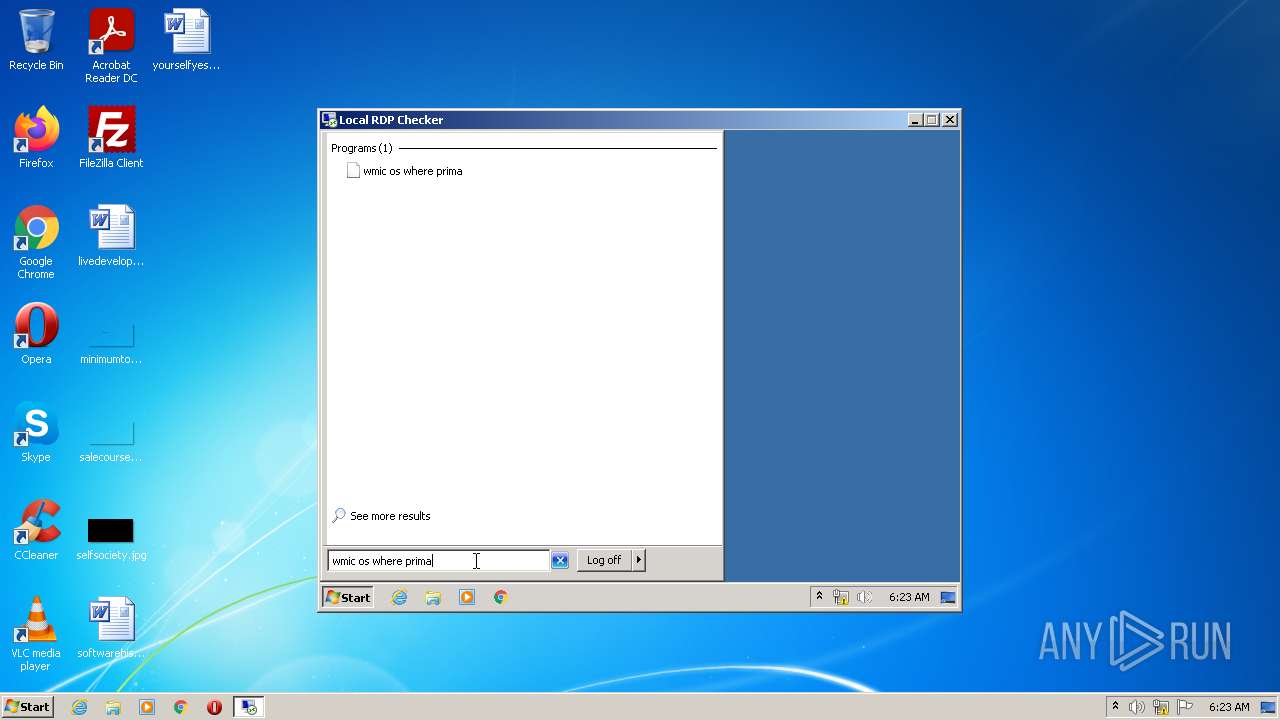
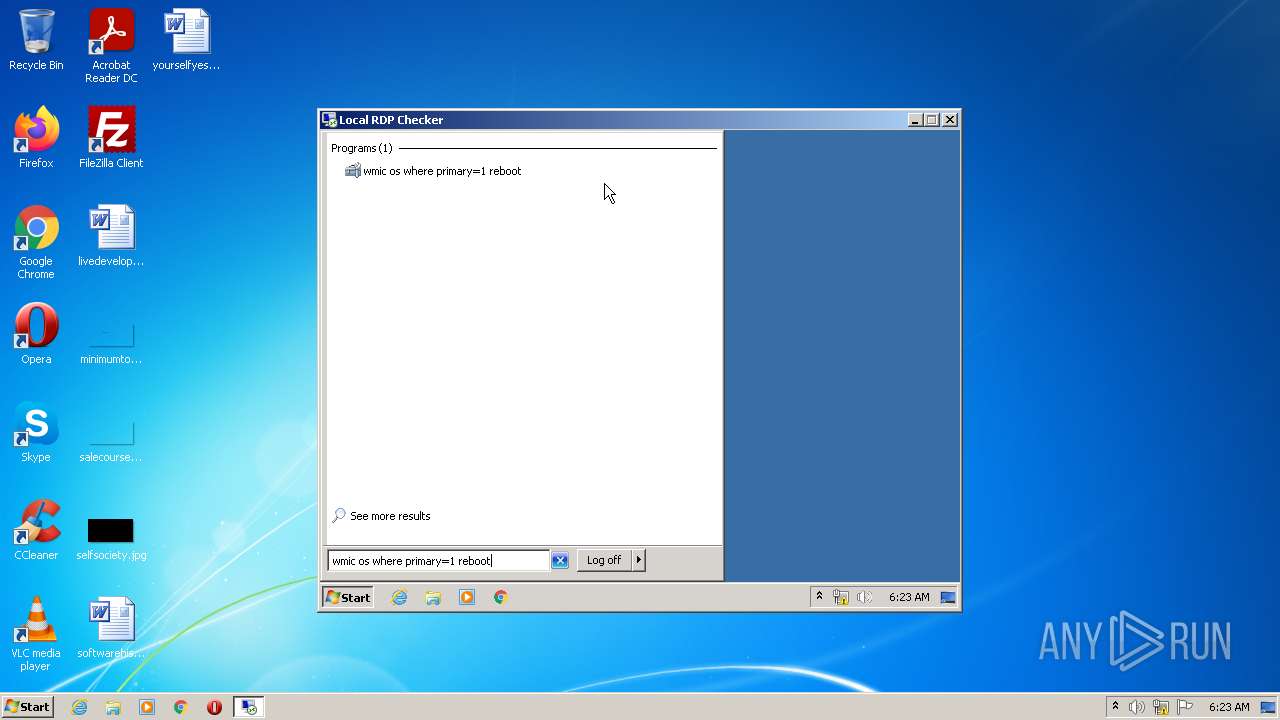
| 808 | "C:\Windows\System32\Wbem\wmic.exe" os where primary=1 reboot | C:\Windows\System32\Wbem\wmic.exe | — | Explorer.EXE | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 888 | C:\Windows\system32\RunDll32.exe C:\Windows\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m /0 | C:\Windows\system32\RunDll32.exe | — | rundll32.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 896 | C:\Windows\System32\spoolsv.exe | C:\Windows\System32\spoolsv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Spooler SubSystem App Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1120 | "C:\Windows\System32\unregmp2.exe" /FirstLogon /Shortcuts /RegBrowsers /ResetMUI | C:\Windows\System32\unregmp2.exe | — | Explorer.EXE | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\install.bat" " | C:\Windows\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Google\Chrome\Application\86.0.4240.198\Installer\chrmstp.exe" --configure-user-settings --verbose-logging --system-level | C:\Program Files\Google\Chrome\Application\86.0.4240.198\Installer\chrmstp.exe | — | Explorer.EXE | |||||||||||
User: Administrator Company: Google LLC Integrity Level: HIGH Description: Google Chrome Installer Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1584 | C:\Windows\system32\TSTheme.exe -Embedding | C:\Windows\system32\TSTheme.exe | — | svchost.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: TSTheme Server Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
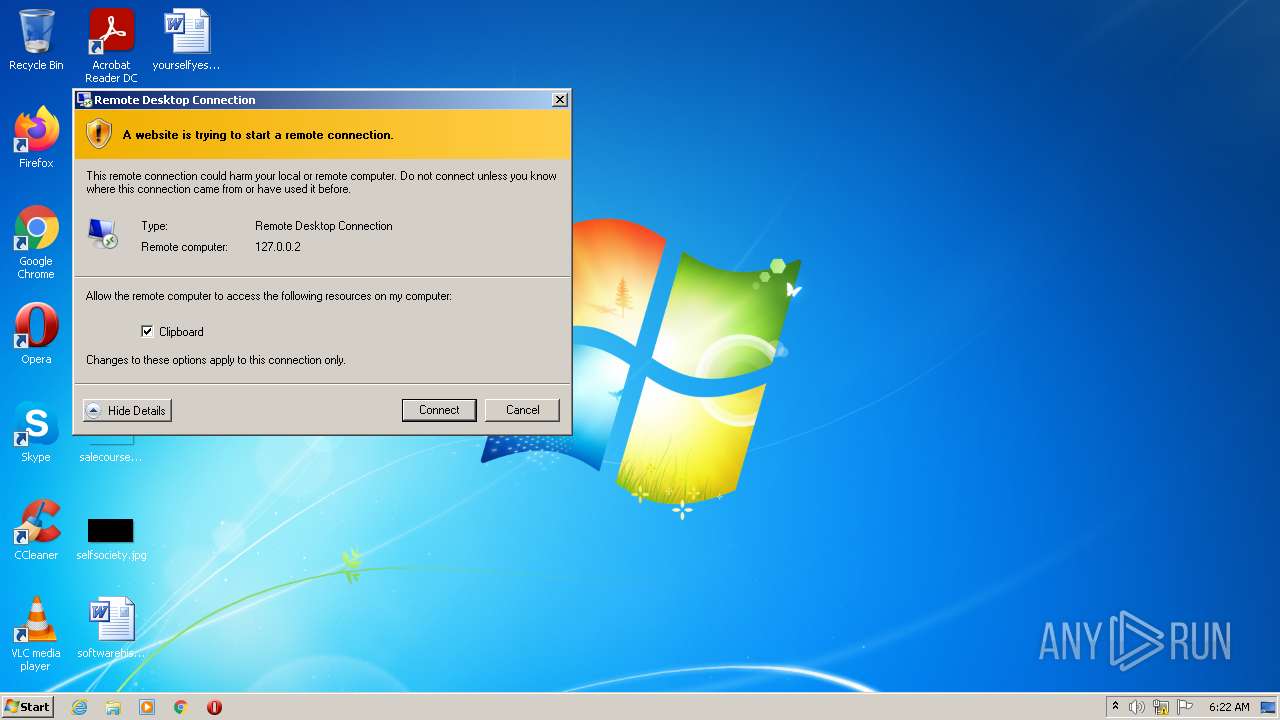
| 1864 | rdpclip | C:\Windows\System32\rdpclip.exe | — | svchost.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: RDP Clip Monitor Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,Control_RunDLL C:\Windows\System32\main.cpl ,1 | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
17 293
Read events
15 832
Write events
1 455
Delete events
6
Modification events
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Roaming\d473b802-eb5f-11e7-8ccc-5944bc969a40.zip | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
12
Suspicious files
21
Text files
76
Unknown types
119
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2496 | svchost.exe | C:\Windows\system32\CatRoot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\catdb | — | |
MD5:— | SHA256:— | |||
| 2496 | svchost.exe | C:\Windows\system32\CatRoot2\edb.log | binary | |
MD5:— | SHA256:— | |||
| 2496 | svchost.exe | C:\Windows\system32\CatRoot2\edb.chk | binary | |
MD5:— | SHA256:— | |||
| 2496 | svchost.exe | C:\Windows\system32\CatRoot2\{127D0A1D-4EF2-11D1-8608-00C04FC295EE}\catdb | edb | |
MD5:— | SHA256:— | |||
| 2600 | DrvInst.exe | C:\Windows\INF\setupapi.ev3 | binary | |
MD5:— | SHA256:— | |||
| 2600 | DrvInst.exe | C:\Windows\INF\setupapi.ev1 | binary | |
MD5:— | SHA256:— | |||
| 896 | spoolsv.exe | C:\Windows\System32\DriverStore\FileRepository\faxcn002.inf_x86_neutral_29a66691dd7a46a5\faxcn002.PNF | pnf | |
MD5:— | SHA256:— | |||
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.45329\RDPConf.exe | executable | |
MD5:03FB8E478F4BA100D37A136231FA2F78 | SHA256:3C0E5D6863B03283AFDA9BD188501757D47DC57FC4BBA2BDBB0D9BAA34487FE0 | |||
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.45329\RDPCheck.exe | executable | |
MD5:8F82226B2F24D470C02F6664F67F23F7 | SHA256:5603338A1F8DBB46EFB8E0869DB3491D5DB92F362711D6680F91ECC5D18BFADF | |||
| 3576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3576.45329\install.bat | text | |
MD5:CBAD5B2CA73917006791882274F769E8 | SHA256:022364EE1FCE61C8A867216C79F223BF47692CD648E3FD6B244FC615B86E4C58 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2724 | sipnotify.exe | HEAD | 404 | 23.205.225.13:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133094245573670000 | NL | — | — | whitelisted |
2800 | RDPWInst.exe | GET | 404 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?db2ef270b67036c9 | US | xml | 341 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2800 | RDPWInst.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | malicious |
2800 | RDPWInst.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
2724 | sipnotify.exe | 23.205.225.13:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report