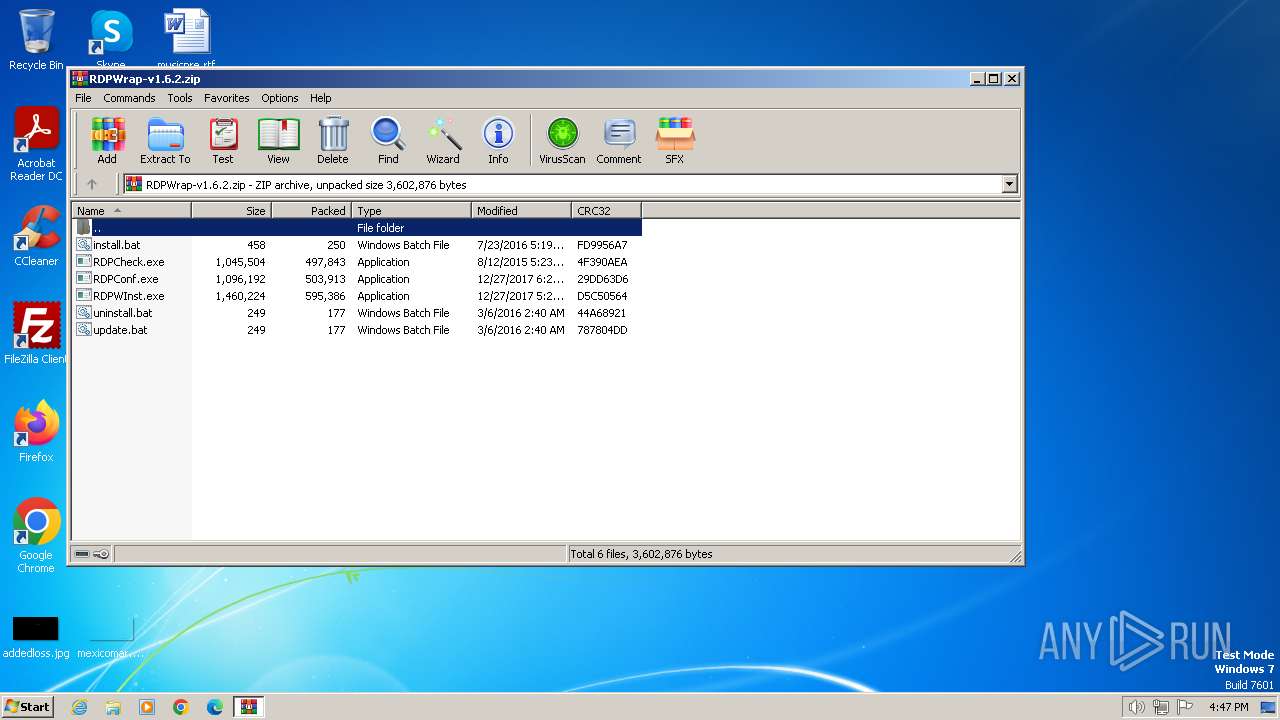
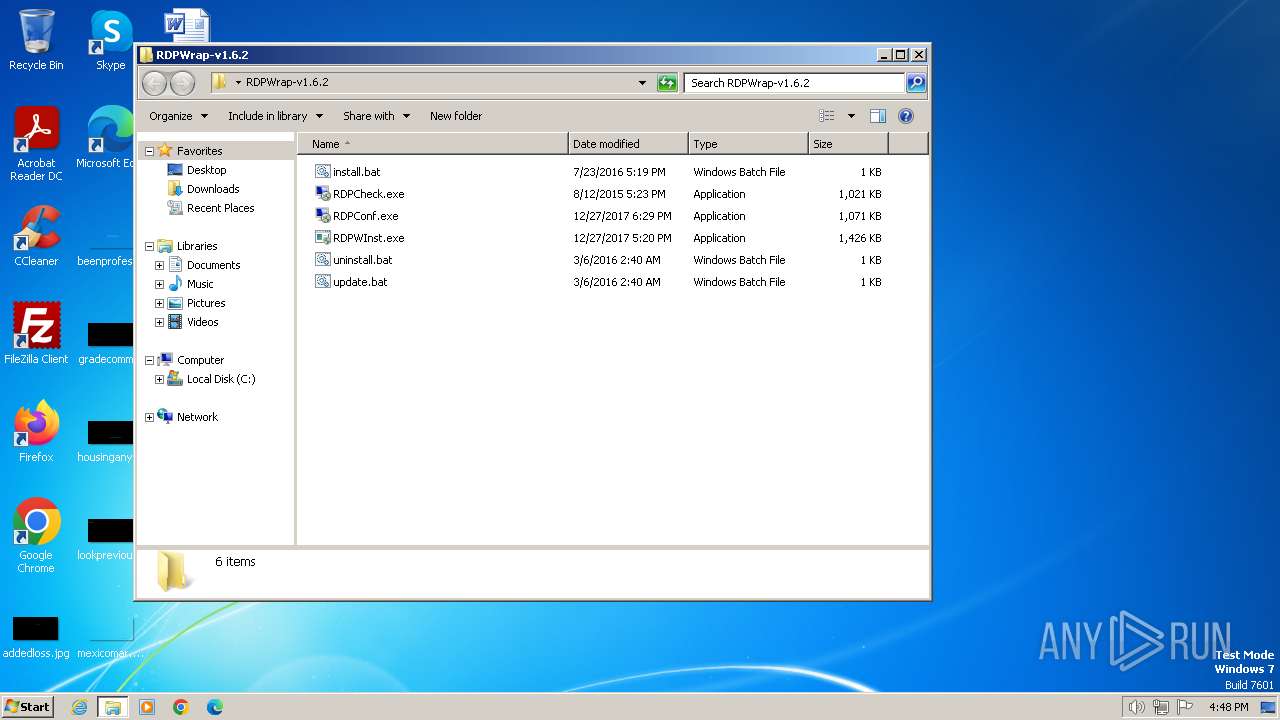
| File name: | RDPWrap-v1.6.2.zip |
| Full analysis: | https://app.any.run/tasks/12db962f-0109-4e0a-a336-6b288ea09cfc |
| Verdict: | Malicious activity |
| Analysis date: | March 15, 2024, 16:47:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C26A2C5F6154225E8D83C4000306F162 |
| SHA1: | 67C586CEDBF0852AA52268311841CBAC5C96FDF8 |
| SHA256: | 35A9481DDBED5177431A9EA4BD09468FE987797D7B1231D64942D17EB54EC269 |
| SSDEEP: | 49152:cPEbpqUPr0OMPjmNgyV24OXxr2/NV0CA7QUmu4LnB:cPEbpPPrC4gWFOBr4Wfg |
MALICIOUS
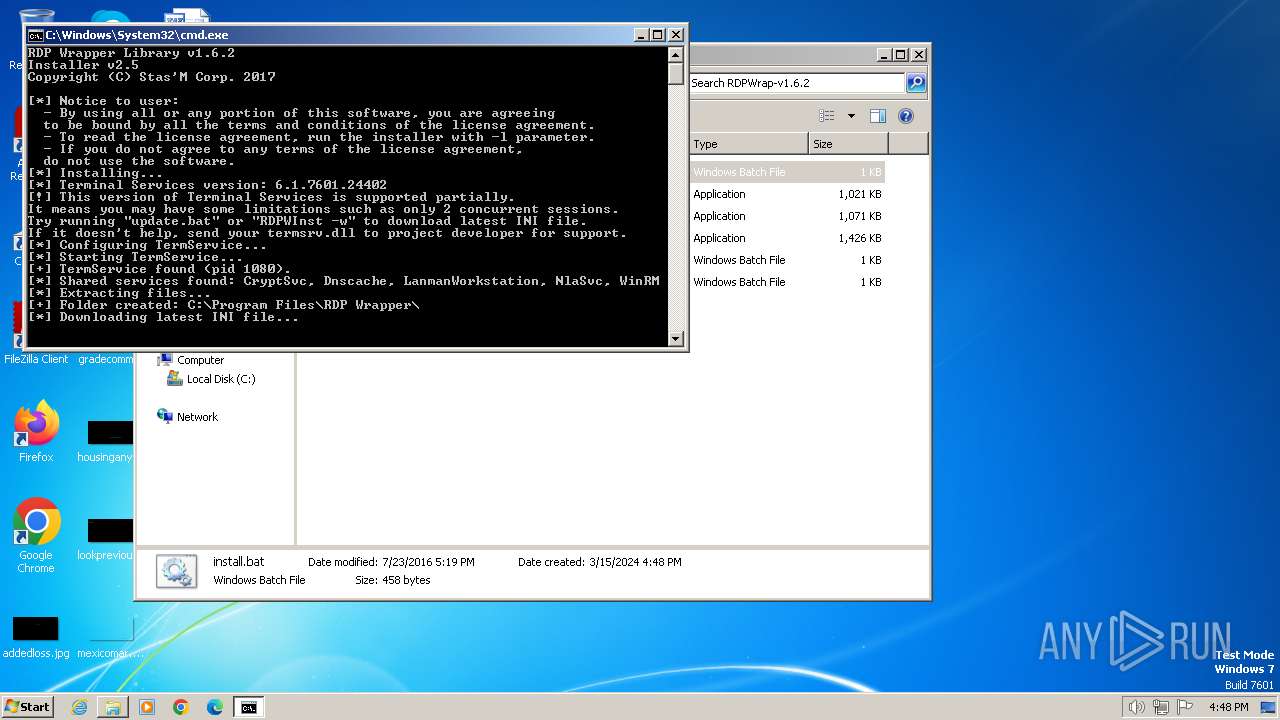
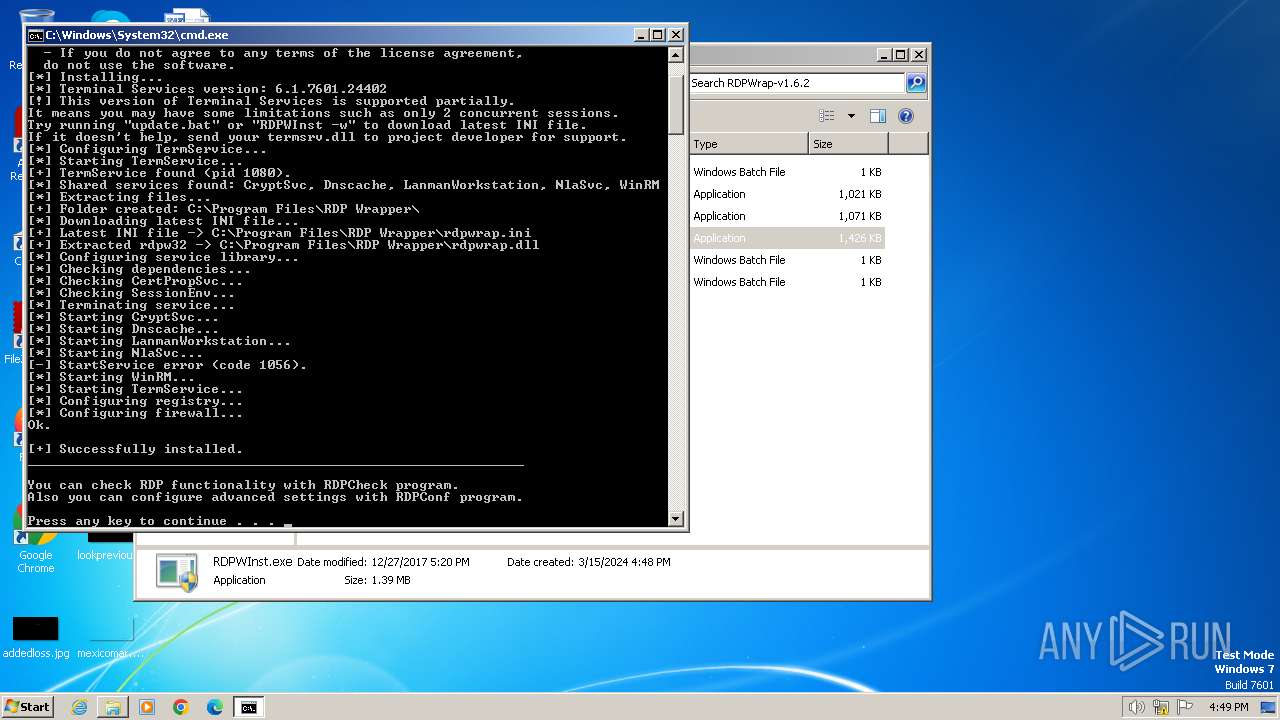
Drops the executable file immediately after the start
- rundll32.exe (PID: 3500)
- RDPWInst.exe (PID: 2100)
Creates or modifies Windows services
- RDPWInst.exe (PID: 2100)
SUSPICIOUS
Reads the Internet Settings
- RDPWInst.exe (PID: 2100)
- mstsc.exe (PID: 3576)
Reads security settings of Internet Explorer
- RDPWInst.exe (PID: 2100)
Reads settings of System Certificates
- RDPWInst.exe (PID: 2100)
- mstsc.exe (PID: 3576)
Checks Windows Trust Settings
- RDPWInst.exe (PID: 2100)
- drvinst.exe (PID: 4072)
Executable content was dropped or overwritten
- RDPWInst.exe (PID: 2100)
Uses NETSH.EXE to add a firewall rule or allowed programs
- RDPWInst.exe (PID: 2100)
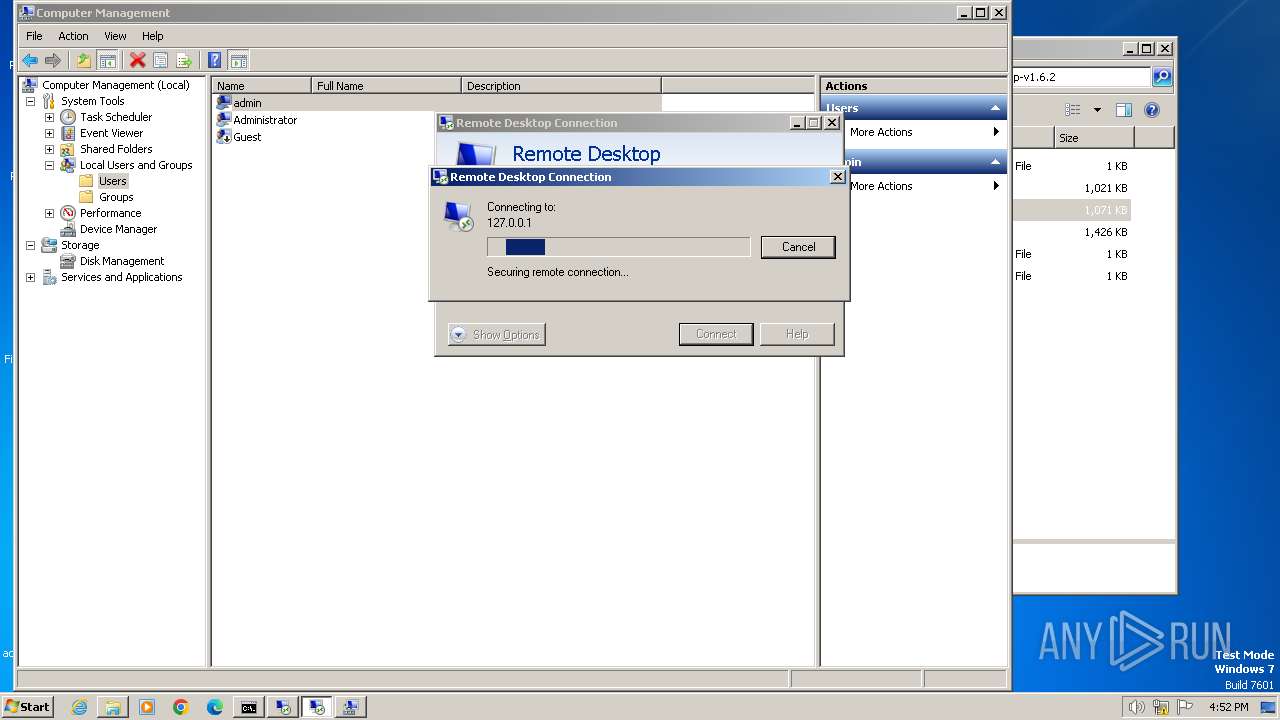
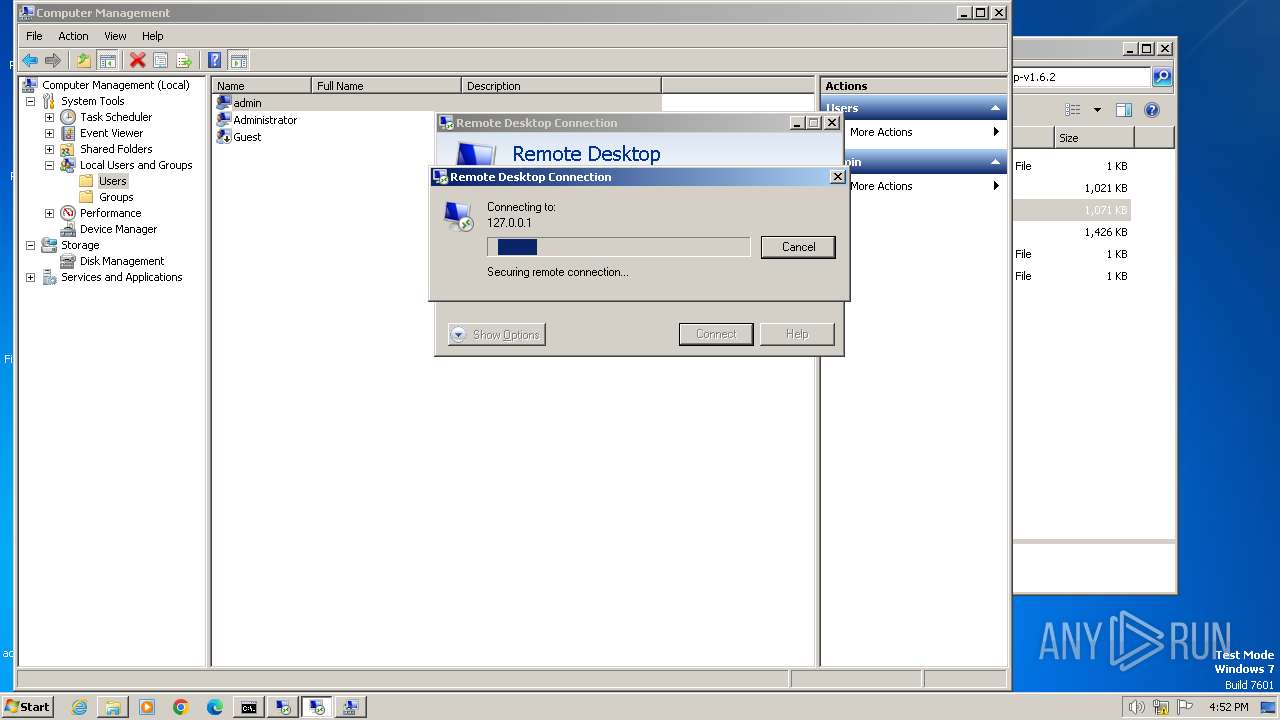
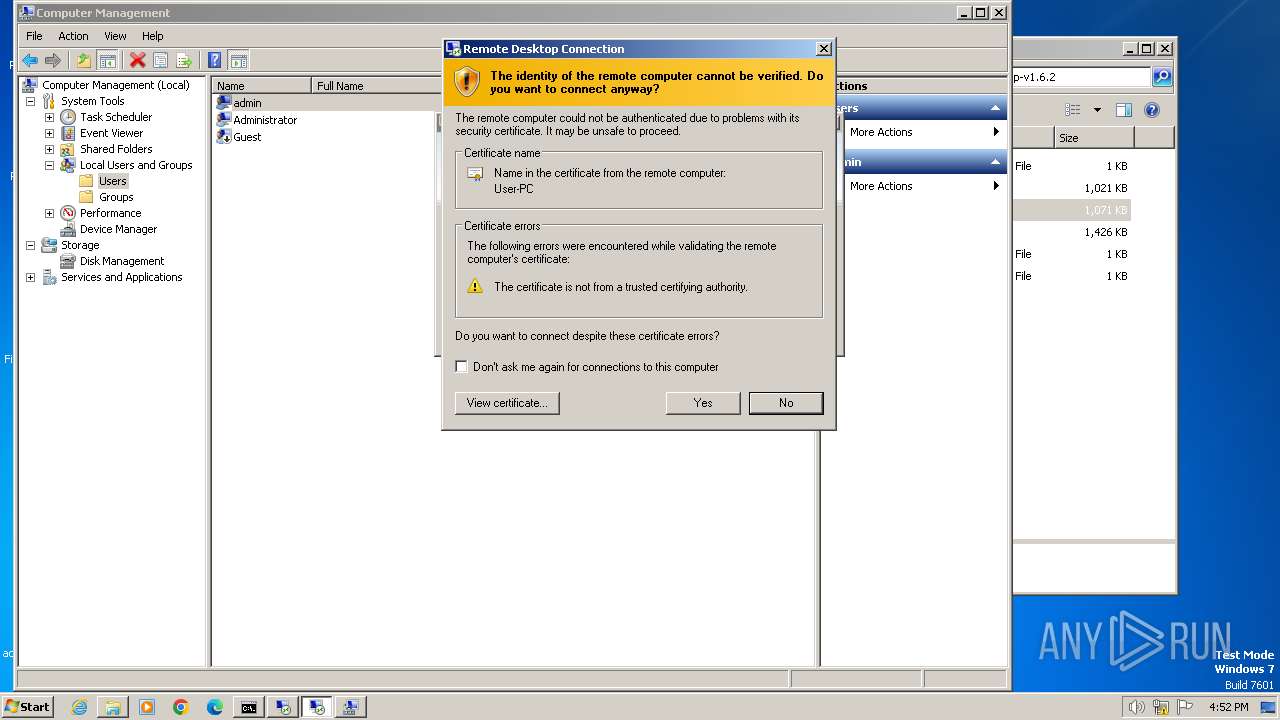
Reads the history of recent RDP connections
- mstsc.exe (PID: 3576)
INFO
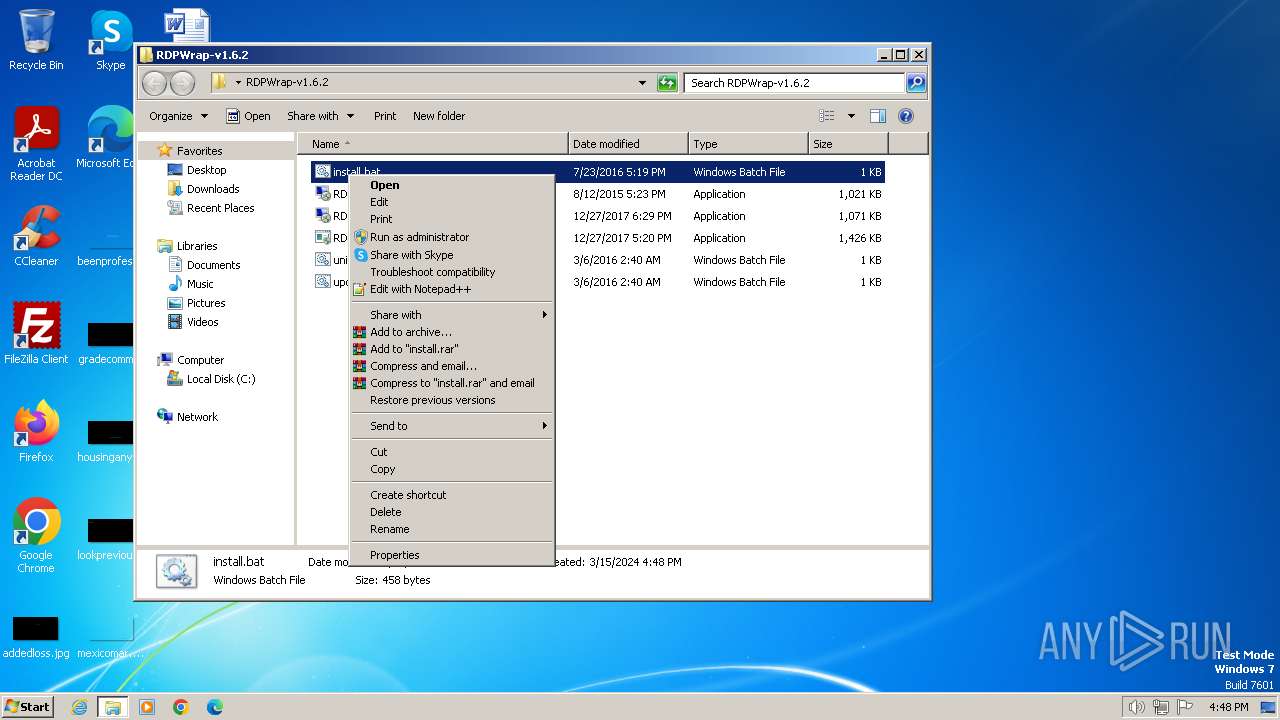
Manual execution by a user
- WinRAR.exe (PID: 1824)
- WinRAR.exe (PID: 4044)
- cmd.exe (PID: 2900)
- wmpnscfg.exe (PID: 1796)
- wmpnscfg.exe (PID: 2424)
- notepad.exe (PID: 1816)
- wmpnscfg.exe (PID: 948)
- mmc.exe (PID: 3920)
- cmd.exe (PID: 3808)
- RDPConf.exe (PID: 2740)
- RDPConf.exe (PID: 1376)
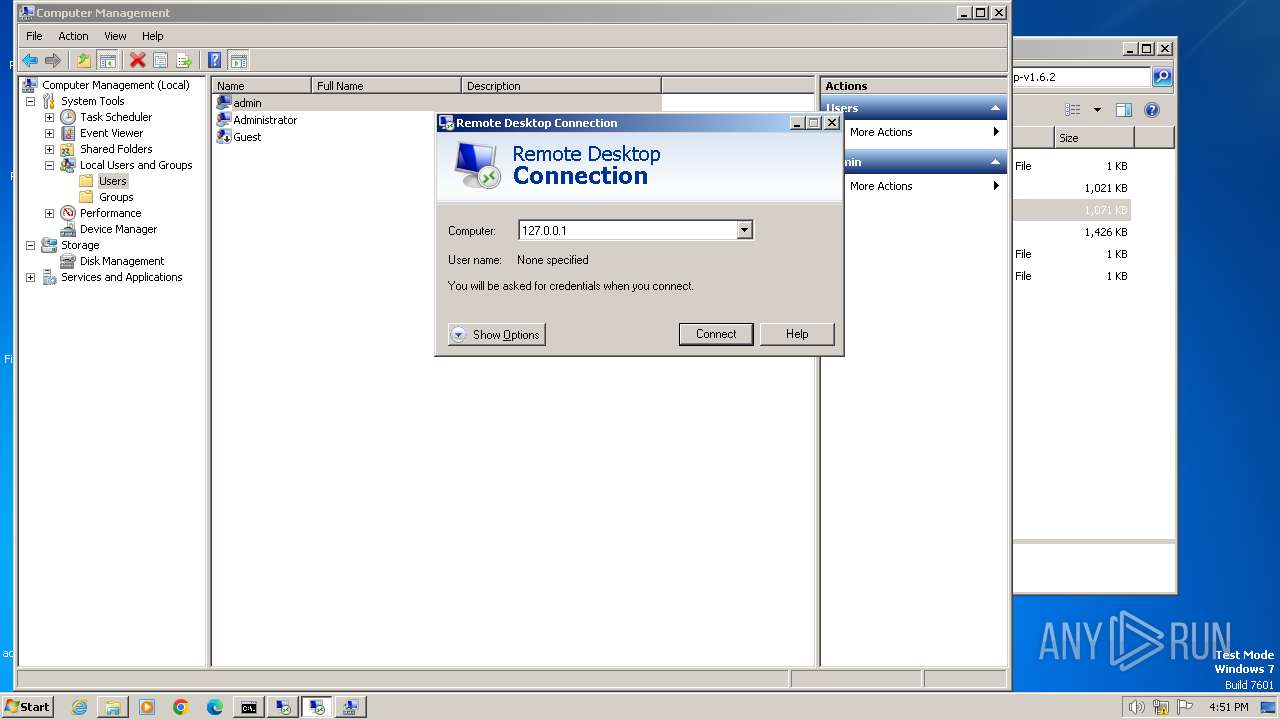
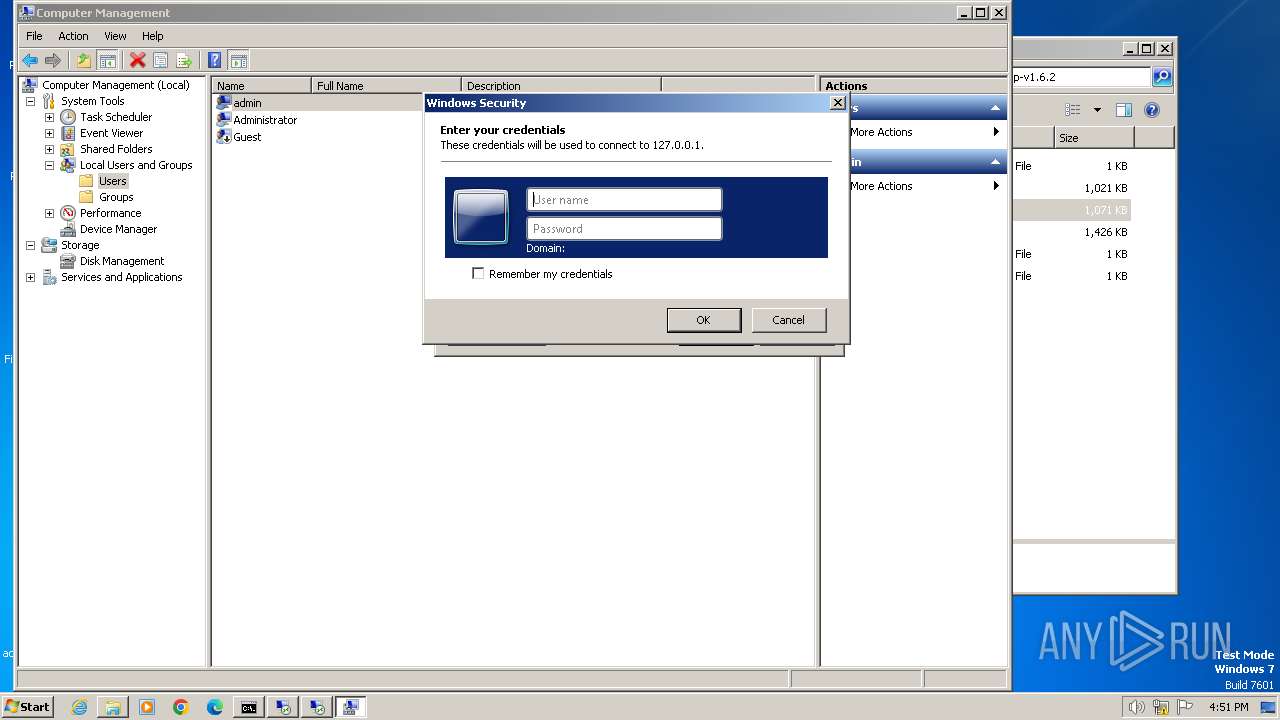
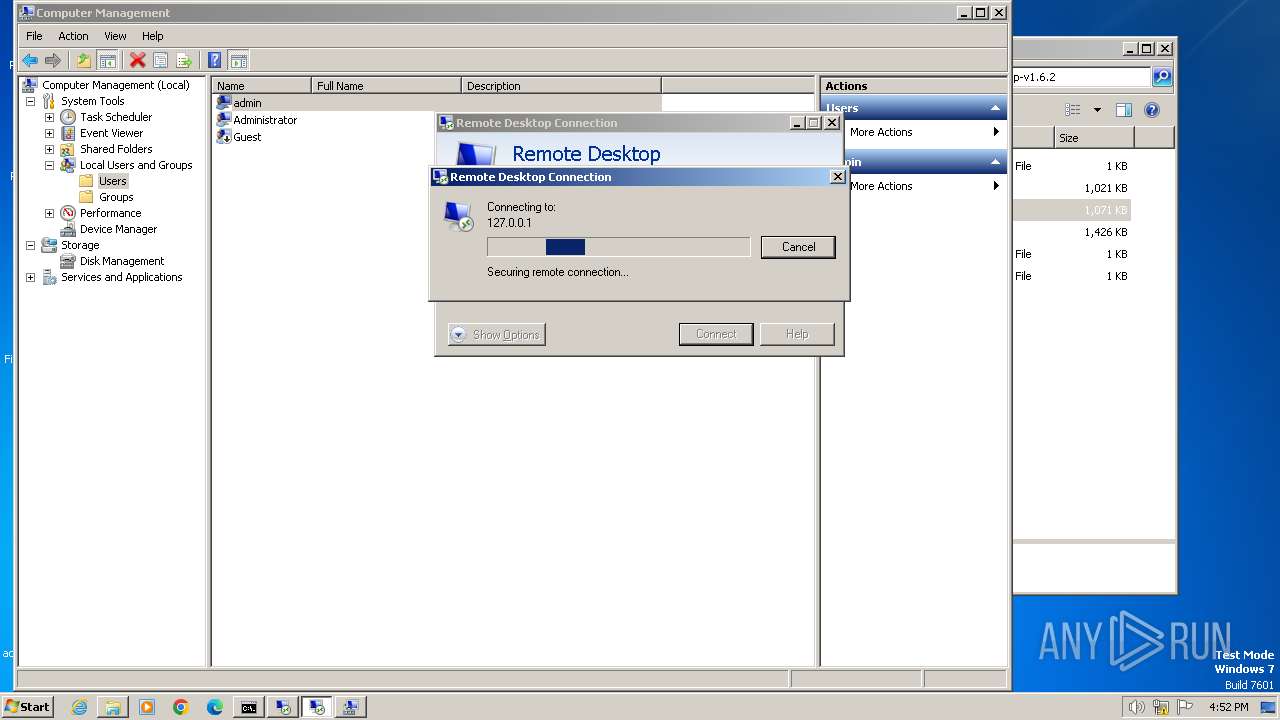
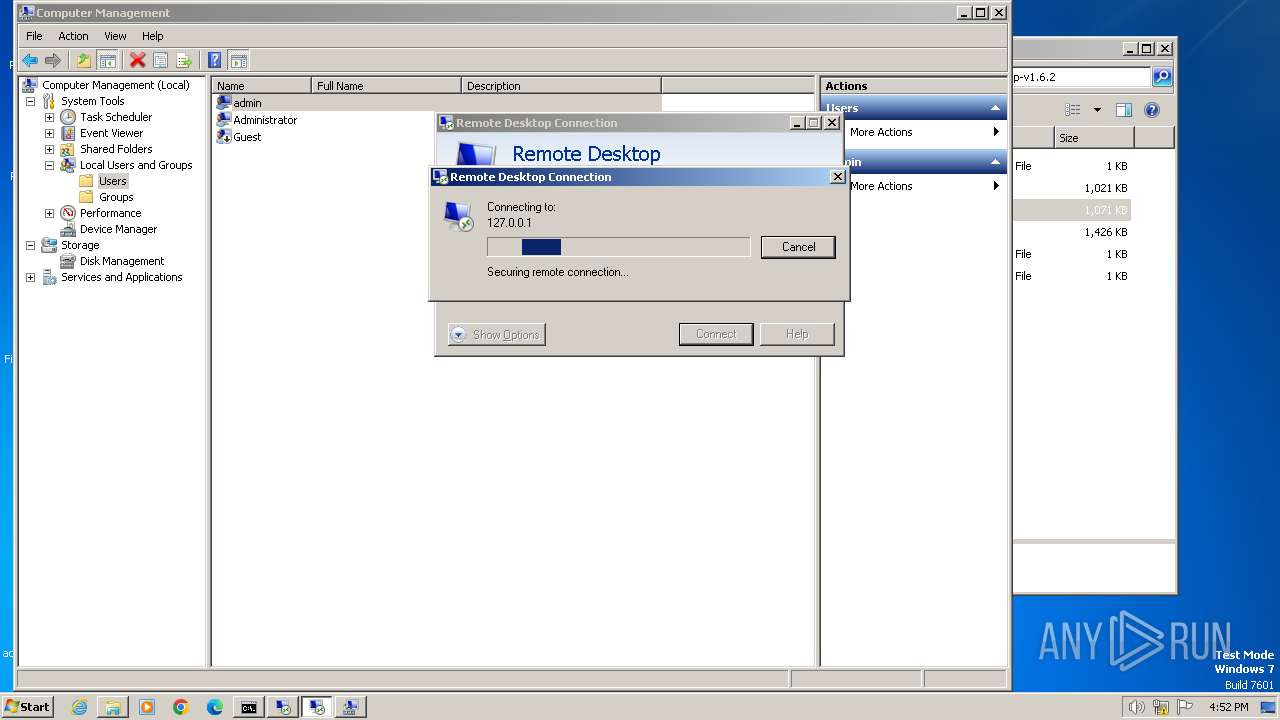
- mstsc.exe (PID: 3576)
- wmpnscfg.exe (PID: 3172)
- mmc.exe (PID: 2444)
Reads the computer name
- RDPWInst.exe (PID: 2100)
- wmpnscfg.exe (PID: 1796)
- wmpnscfg.exe (PID: 2424)
- drvinst.exe (PID: 4072)
- RDPConf.exe (PID: 1376)
- wmpnscfg.exe (PID: 948)
- wmpnscfg.exe (PID: 3172)
Checks proxy server information
- RDPWInst.exe (PID: 2100)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1824)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1824)
Checks supported languages
- RDPWInst.exe (PID: 2100)
- wmpnscfg.exe (PID: 2424)
- wmpnscfg.exe (PID: 1796)
- wmpnscfg.exe (PID: 3172)
- drvinst.exe (PID: 4072)
- RDPConf.exe (PID: 1376)
- wmpnscfg.exe (PID: 948)
Reads the machine GUID from the registry
- RDPWInst.exe (PID: 2100)
- drvinst.exe (PID: 4072)
Creates files in the program directory
- RDPWInst.exe (PID: 2100)
- mmc.exe (PID: 2444)
Reads the software policy settings
- RDPWInst.exe (PID: 2100)
- drvinst.exe (PID: 4072)
- mstsc.exe (PID: 3576)
Creates files or folders in the user directory
- RDPWInst.exe (PID: 2100)
- mstsc.exe (PID: 3576)
Create files in a temporary directory
- mstsc.exe (PID: 3576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:07:23 19:19:08 |
| ZipCRC: | 0xfd9956a7 |
| ZipCompressedSize: | 250 |
| ZipUncompressedSize: | 458 |
| ZipFileName: | install.bat |
Total processes
77
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 948 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
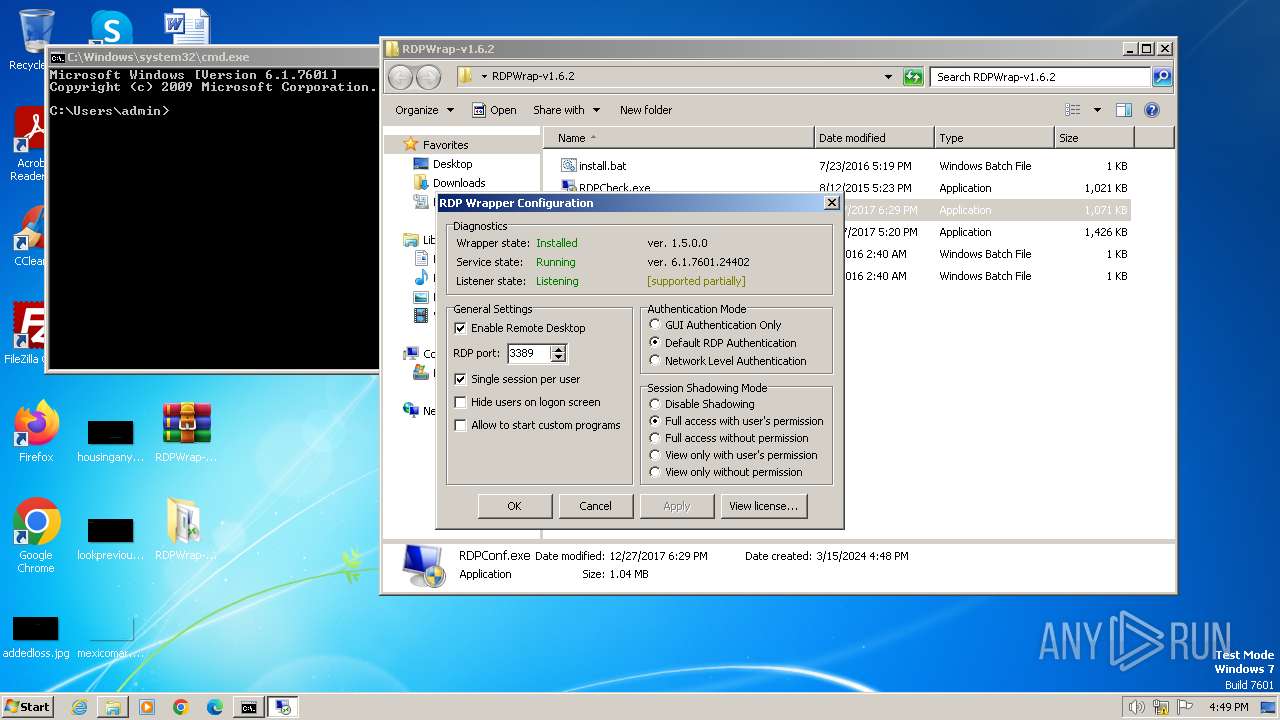
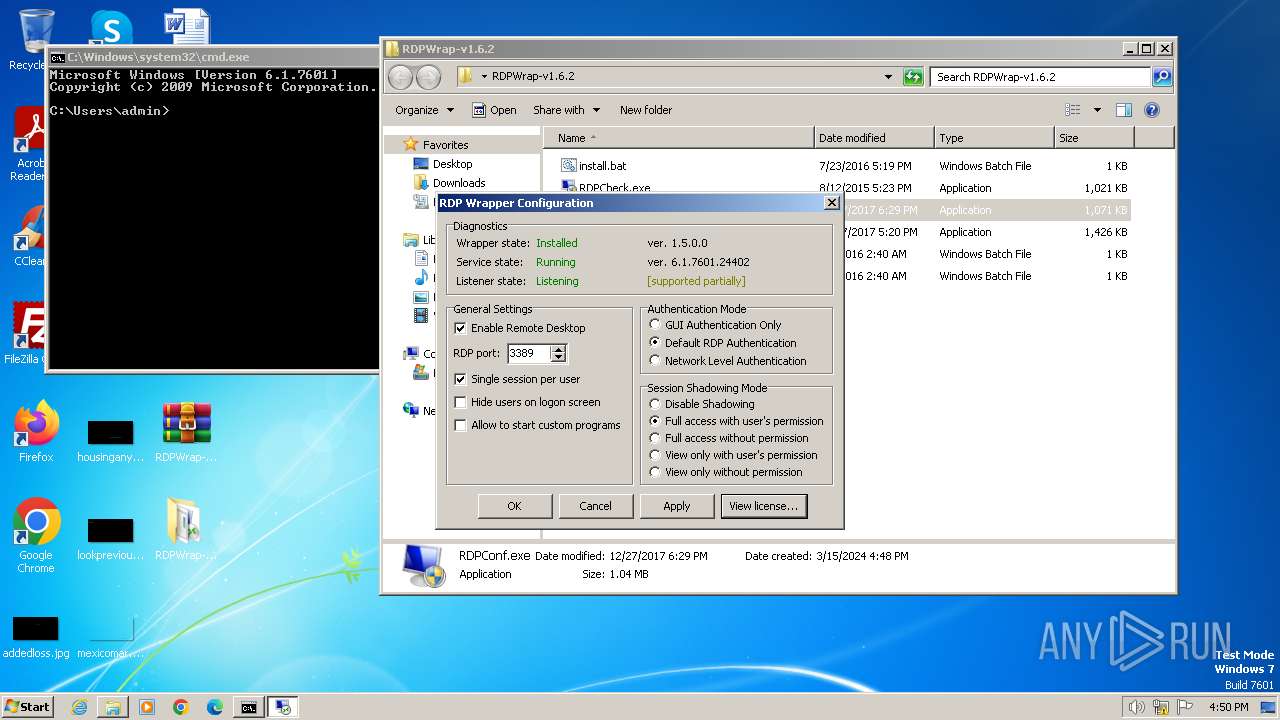
| 1376 | "C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPConf.exe" | C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPConf.exe | explorer.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: HIGH Description: RDP Configuration Program Exit code: 0 Version: 1.4.0.0 Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
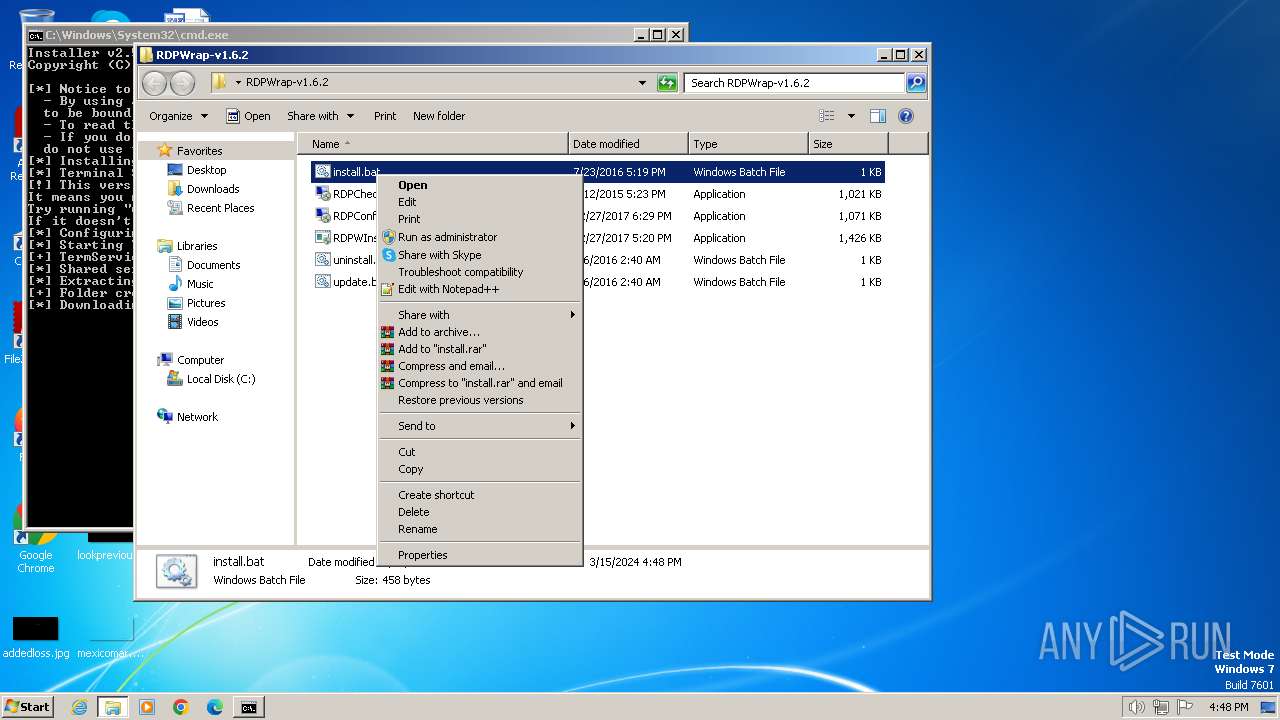
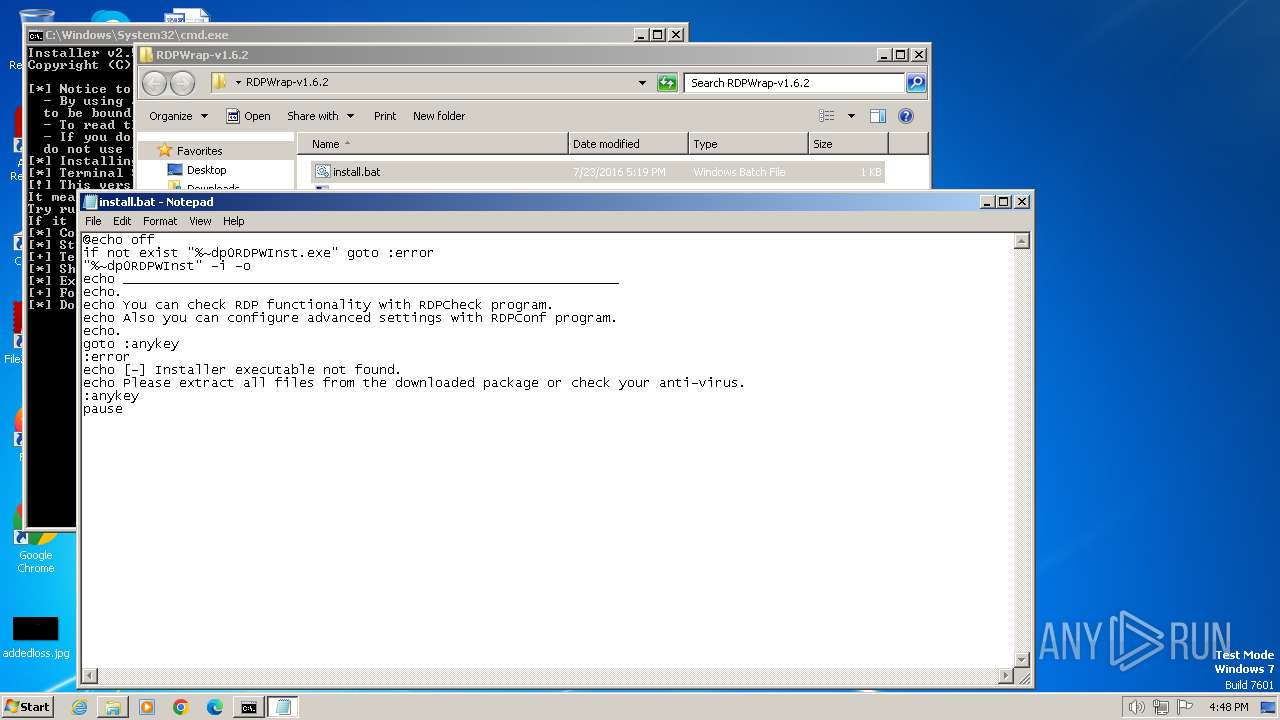
| 1816 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\RDPWrap-v1.6.2\install.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
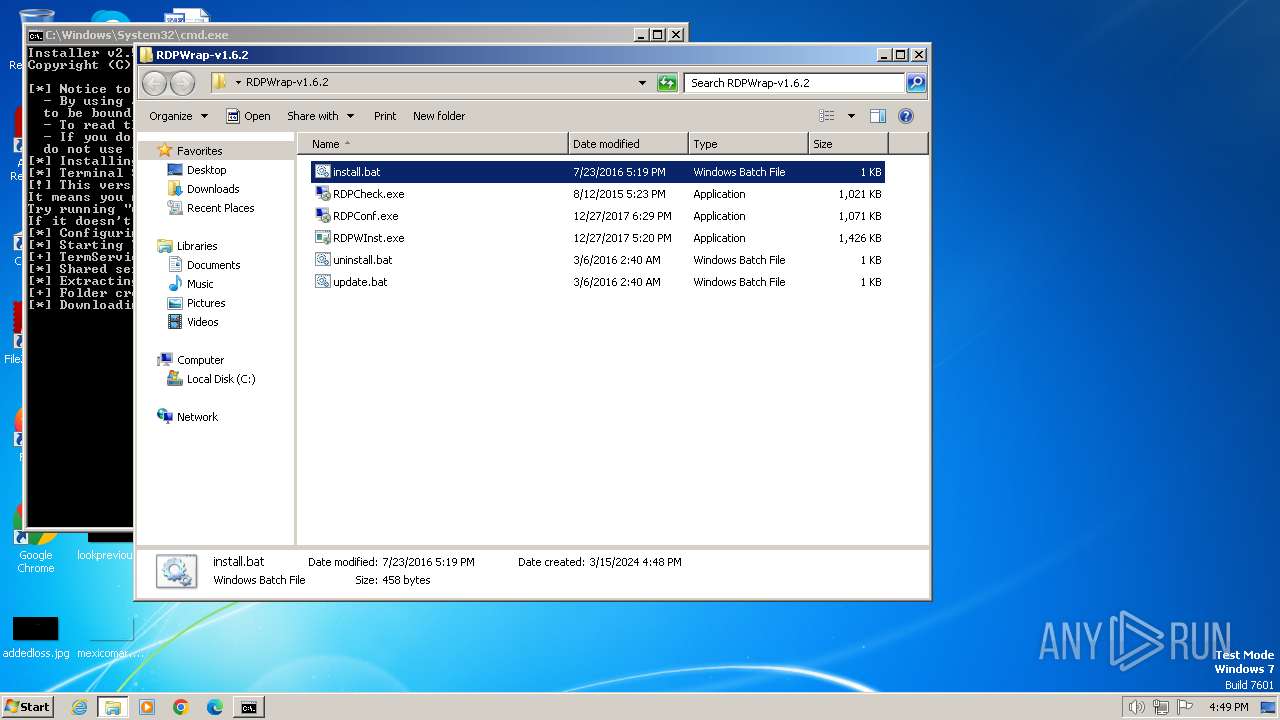
| 1824 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\RDPWrap-v1.6.2.zip" C:\Users\admin\Desktop\RDPWrap-v1.6.2\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
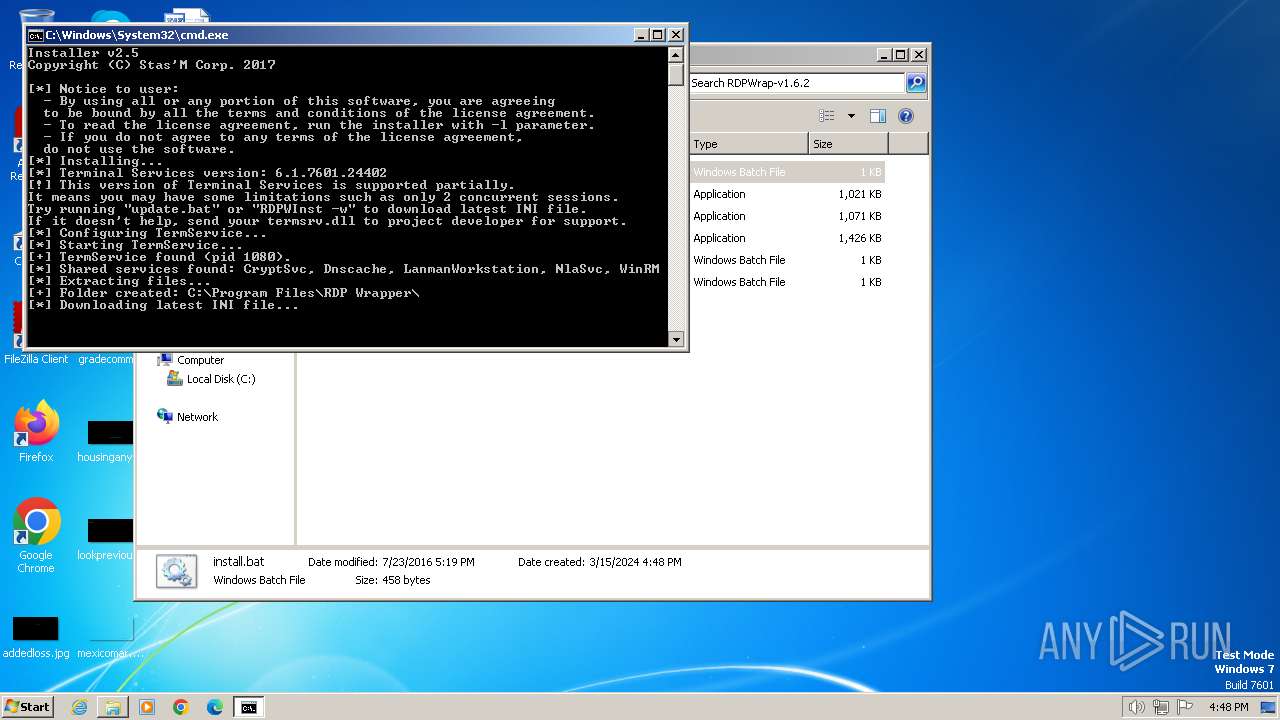
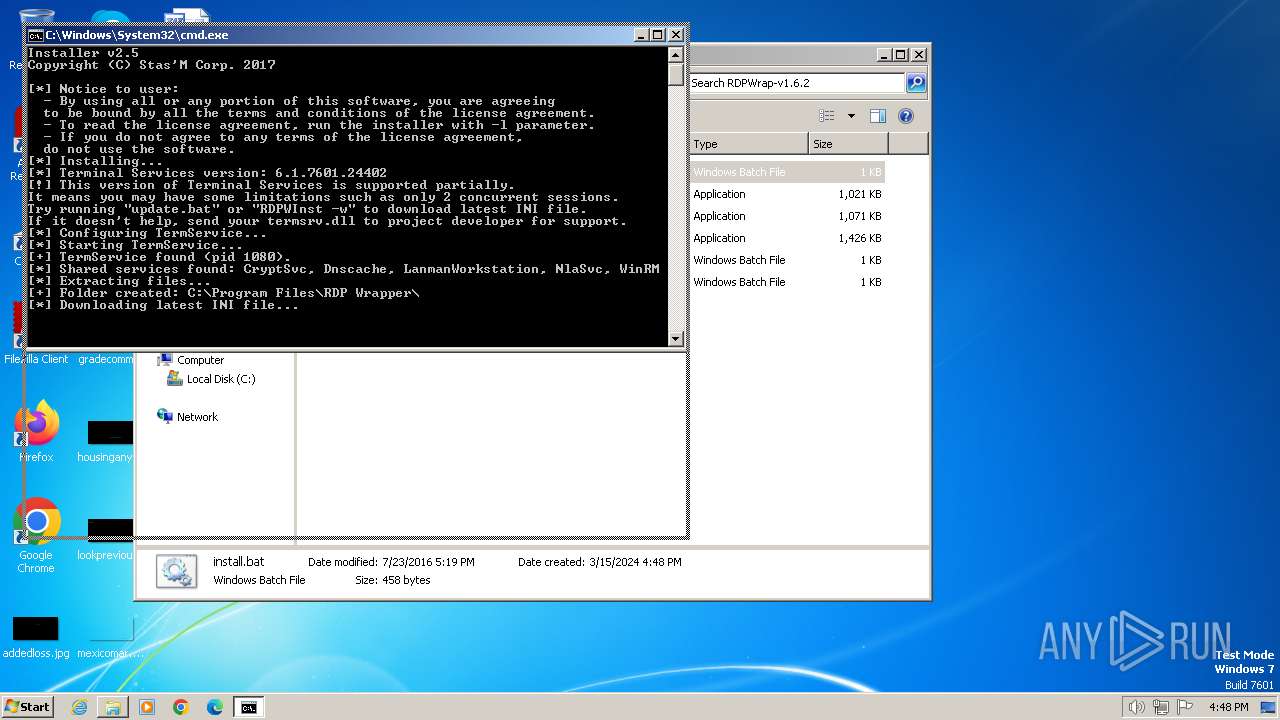
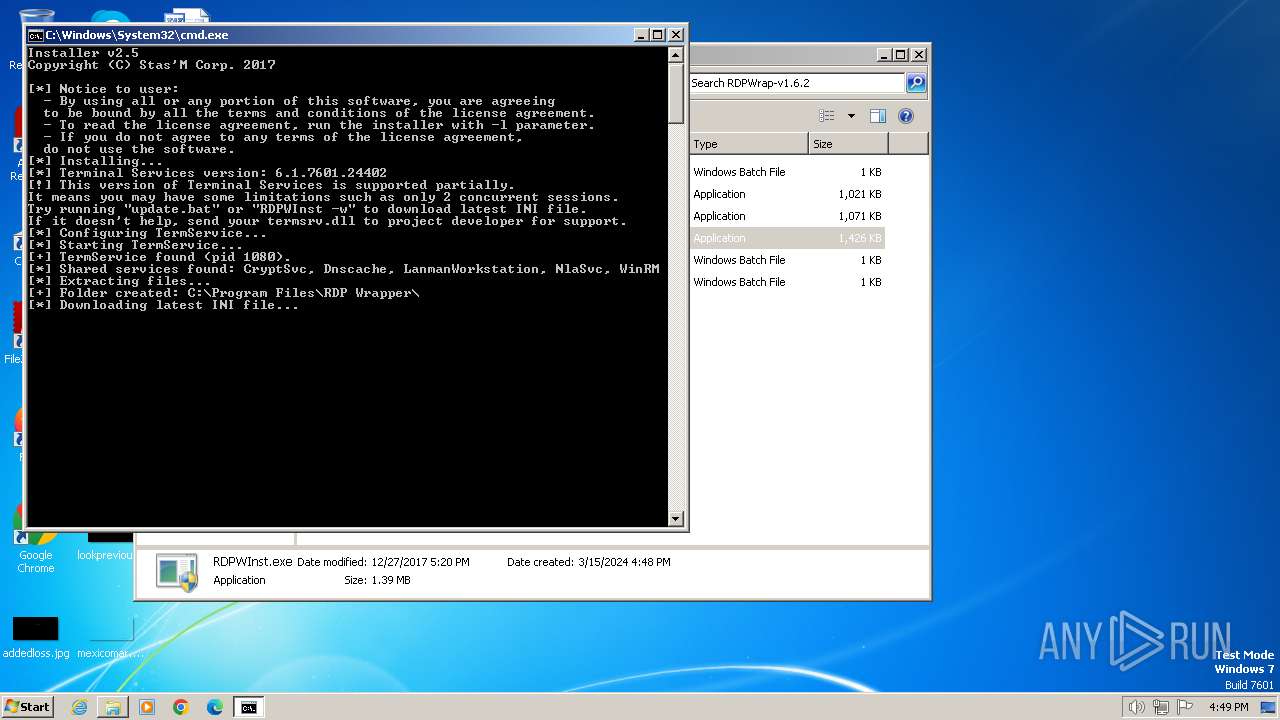
| 2100 | "C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPWInst" -i -o | C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPWInst.exe | cmd.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: HIGH Description: RDP Wrapper Library Installer Exit code: 0 Version: 2.5.0.0 Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\compmgmt.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | "C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPConf.exe" | C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPConf.exe | — | explorer.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Configuration Program Exit code: 3221226540 Version: 1.4.0.0 Modules
| |||||||||||||||
| 2900 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\RDPWrap-v1.6.2\install.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
21 510
Read events
21 308
Write events
179
Delete events
23
Modification events
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\RDPWrap-v1.6.2.zip | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
6
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
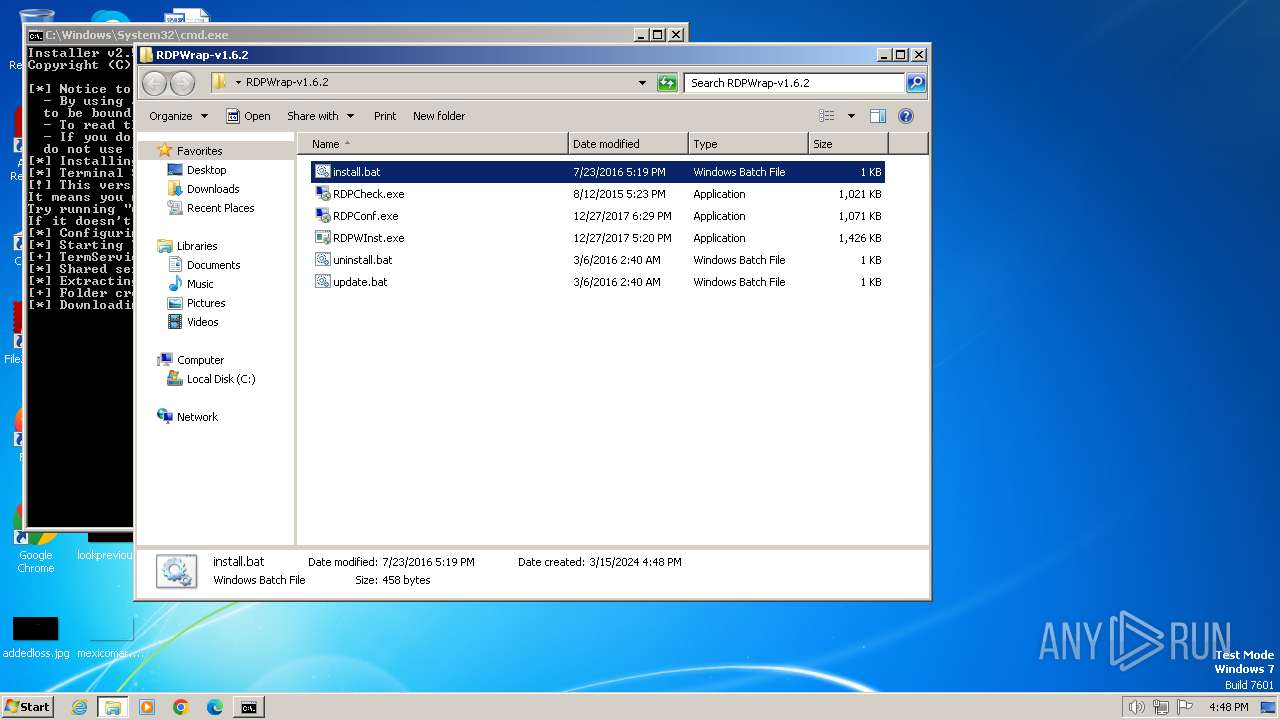
| 1824 | WinRAR.exe | C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPCheck.exe | executable | |
MD5:8F82226B2F24D470C02F6664F67F23F7 | SHA256:5603338A1F8DBB46EFB8E0869DB3491D5DB92F362711D6680F91ECC5D18BFADF | |||
| 3576 | mstsc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 3576 | mstsc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:D9CAD12F755391DAE41B19F8DE524EBB | SHA256:95736C733D0A405FE1475B2B6F70393BC34CF36760311A30C21305FF91102C4D | |||
| 2100 | RDPWInst.exe | C:\Program Files\RDP Wrapper\rdpwrap.ini | binary | |
MD5:DDDD741AB677BDAC8DCD4FA0DDA05DA2 | SHA256:7D5655D5EC4DEFC2051AA5F582FAC1031B142040C8EEA840FF88887FE27B7668 | |||
| 4072 | drvinst.exe | C:\Windows\INF\setupapi.ev3 | binary | |
MD5:9EBC654990CE1A767CA8B0FEC40AA488 | SHA256:9238AE2D3B756EB9BA37056F7F2869B460C7EA3AEAB6FE5831D2E00A51FBBC4F | |||
| 1824 | WinRAR.exe | C:\Users\admin\Desktop\RDPWrap-v1.6.2\RDPWInst.exe | executable | |
MD5:3288C284561055044C489567FD630AC2 | SHA256:AC92D4C6397EB4451095949AC485EF4EC38501D7BB6F475419529AE67E297753 | |||
| 1824 | WinRAR.exe | C:\Users\admin\Desktop\RDPWrap-v1.6.2\uninstall.bat | text | |
MD5:ECCB8A01D0427EF29C2380D7DDA399F3 | SHA256:083CD340C800CC021D4A59388680CE0E7AB0F8B998E67DEF6A507070E7FA01B7 | |||
| 3576 | mstsc.exe | C:\Users\admin\AppData\Local\Temp\Cab3E97.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 4072 | drvinst.exe | C:\Windows\INF\setupapi.ev1 | binary | |
MD5:410454B516EC73EFC622BDC454B409AD | SHA256:3B491F237F9AC6071EAF22CB866C8D7926A50BAA4E41C8733CAB49BC952D9D24 | |||
| 2100 | RDPWInst.exe | C:\Program Files\RDP Wrapper\rdpwrap.dll | executable | |
MD5:9C6A68742EA7ABF802940E7F1502E20F | SHA256:861AD4BBF682B35AFFDA23FAB92C8DB945F3FA34F78177843C87802D1FD02020 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
16
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
488 | lsass.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e124cf71ae330eb0 | unknown | — | — | unknown |
3576 | mstsc.exe | GET | 200 | 184.24.77.206:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?da41654eef2f24d2 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2100 | RDPWInst.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2100 | RDPWInst.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2100 | RDPWInst.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2100 | RDPWInst.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2100 | RDPWInst.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2992 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
856 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
dns.msftncsi.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerExtension
|