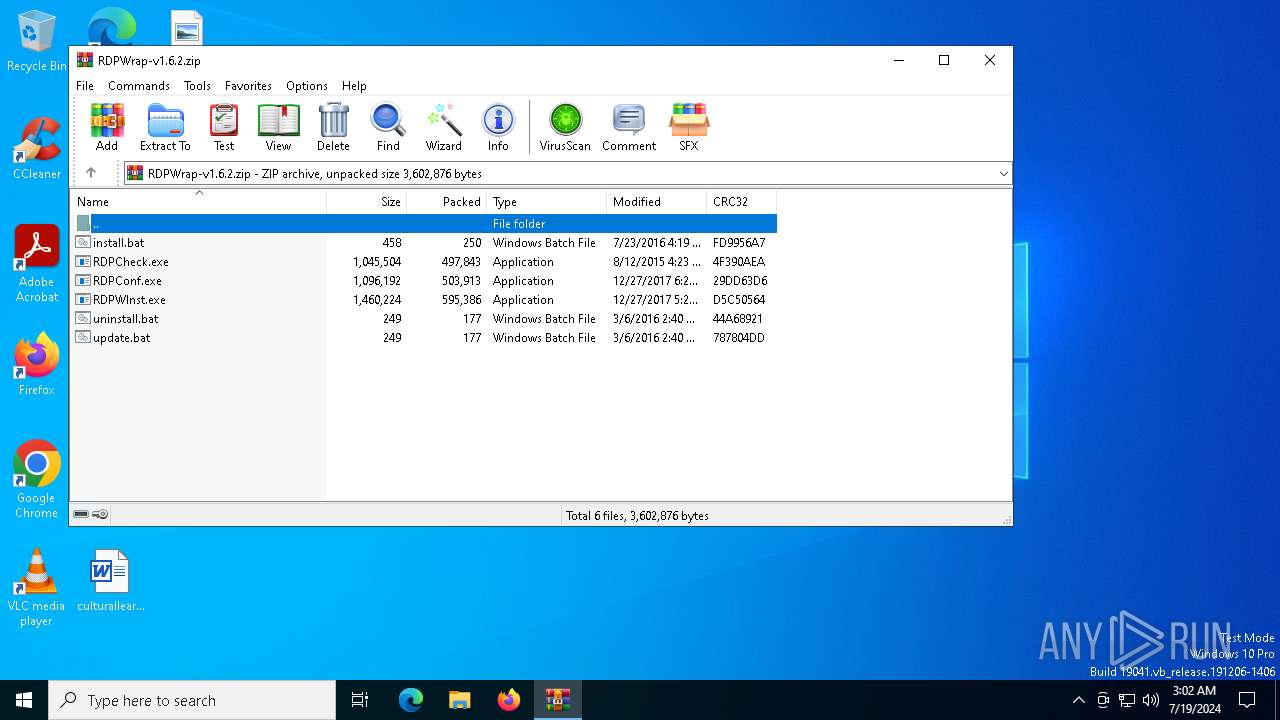
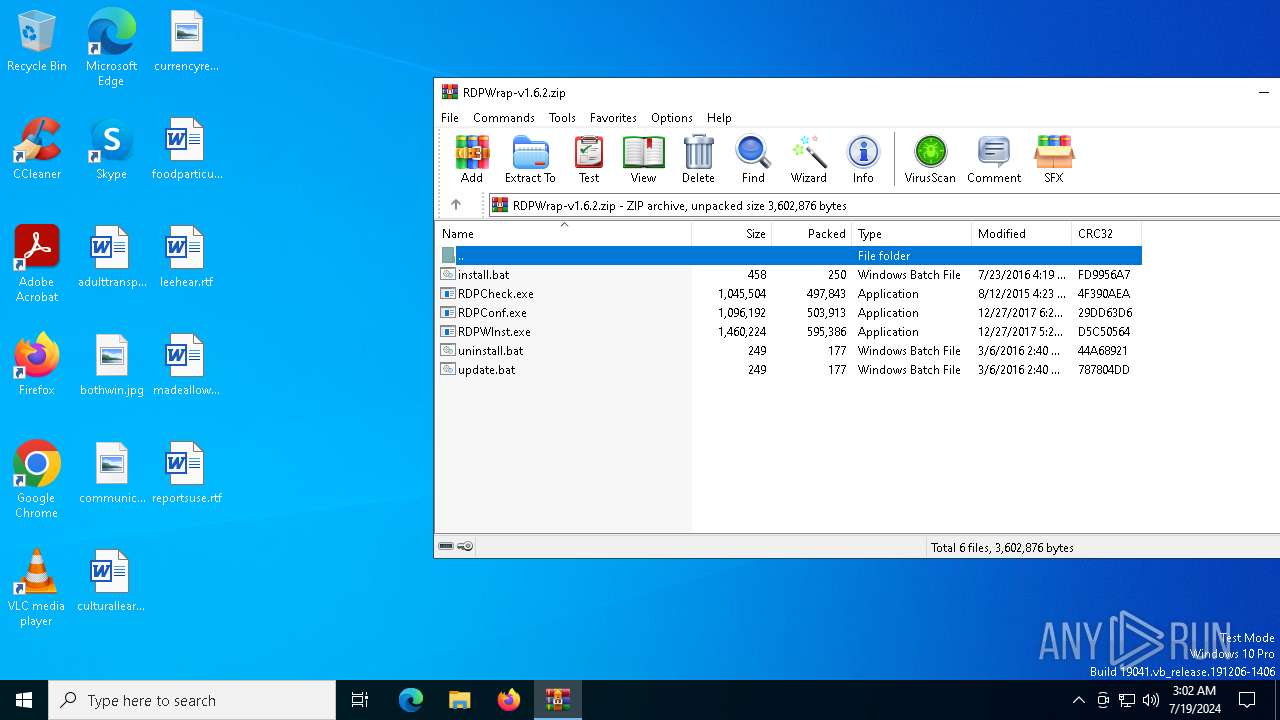
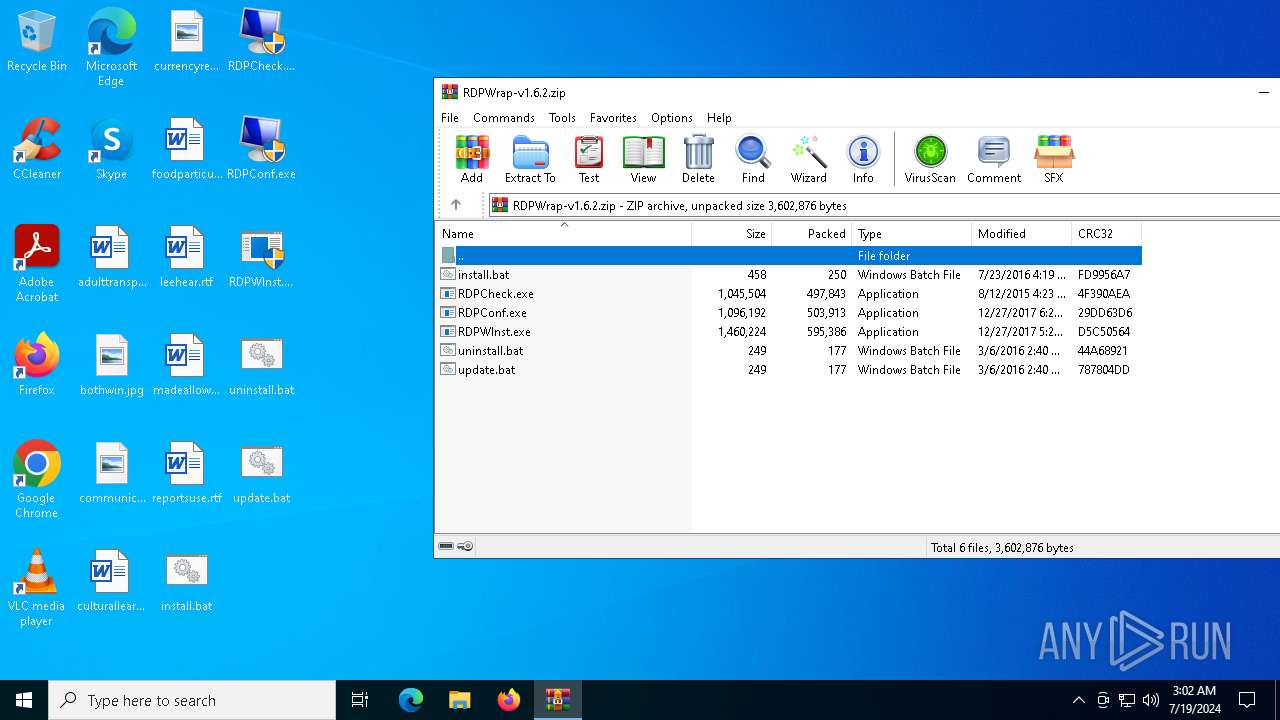
| File name: | RDPWrap-v1.6.2.zip |
| Full analysis: | https://app.any.run/tasks/125067f9-f2a5-4430-aca6-21da973e99b0 |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 03:02:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C26A2C5F6154225E8D83C4000306F162 |
| SHA1: | 67C586CEDBF0852AA52268311841CBAC5C96FDF8 |
| SHA256: | 35A9481DDBED5177431A9EA4BD09468FE987797D7B1231D64942D17EB54EC269 |
| SSDEEP: | 49152:cPEbpqUPr0OMPjmNgyV24OXxr2/NV0CA7QUmu4LnB:cPEbpPPrC4gWFOBr4Wfg |
MALICIOUS
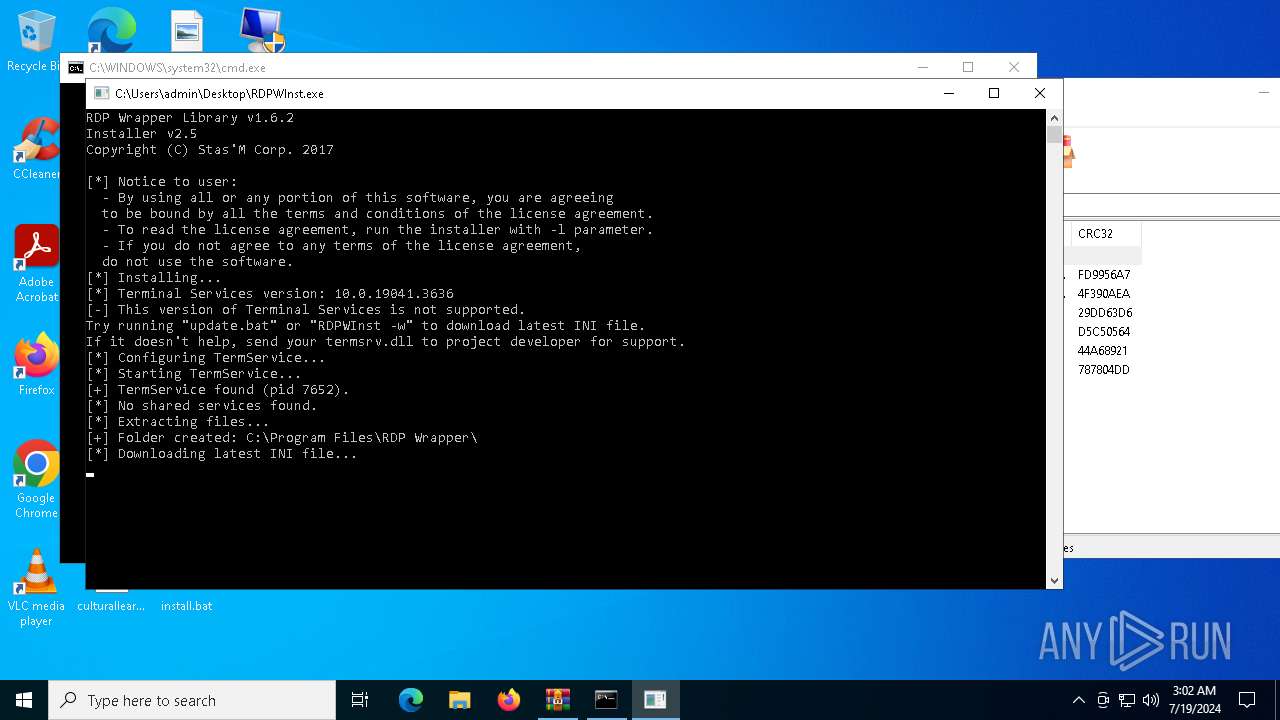
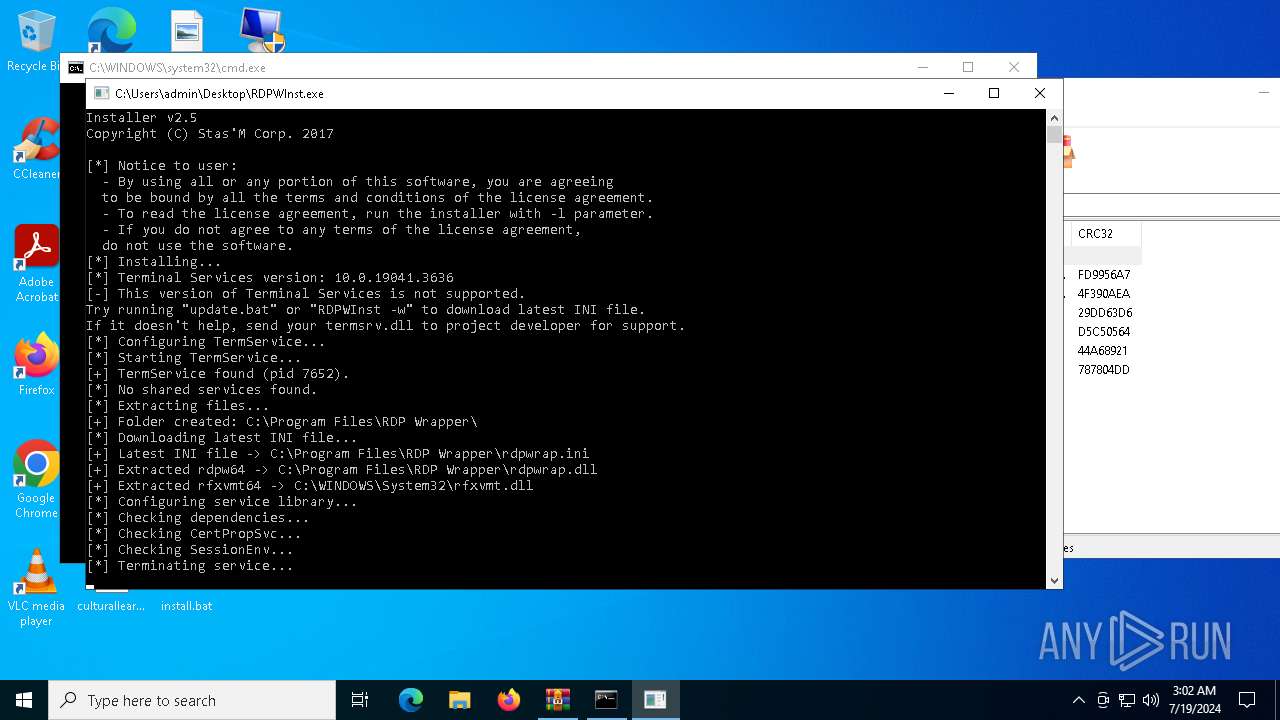
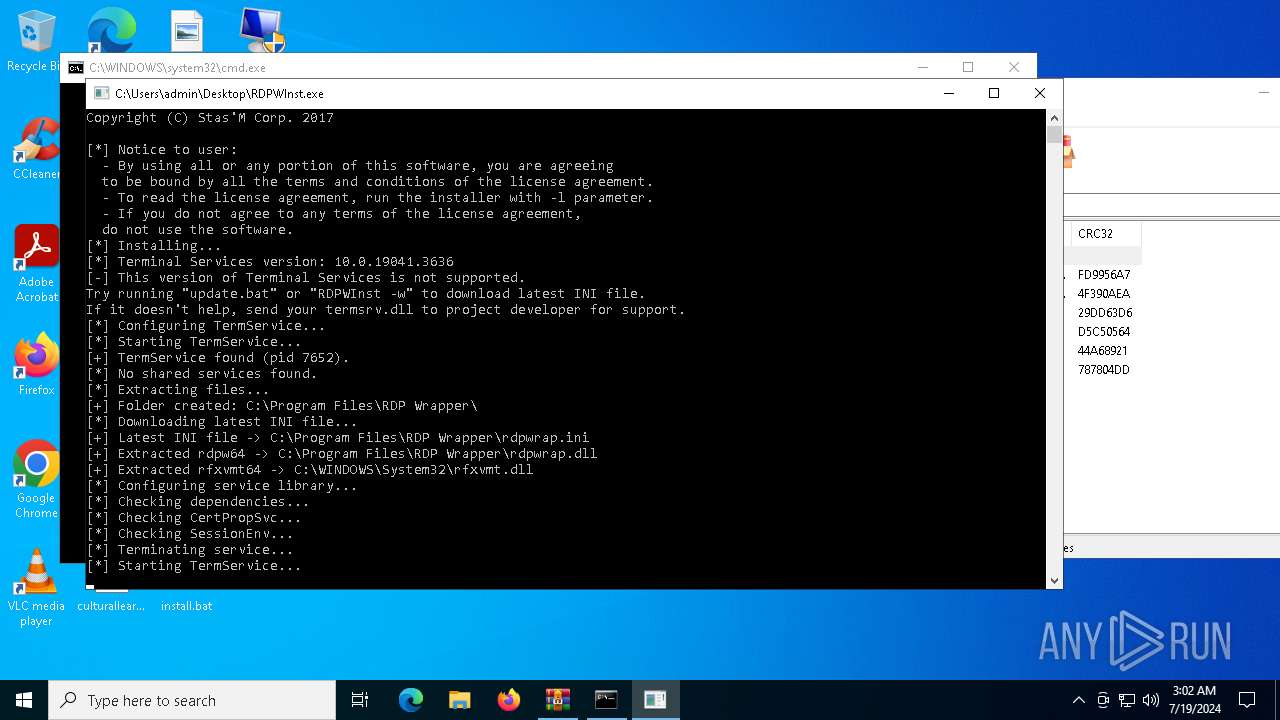
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7976)
- RDPWInst.exe (PID: 4872)
Creates a writable file in the system directory
- RDPWInst.exe (PID: 4872)
Creates or modifies Windows services
- RDPWInst.exe (PID: 4872)
SUSPICIOUS
Reads security settings of Internet Explorer
- RDPWInst.exe (PID: 4872)
Checks Windows Trust Settings
- RDPWInst.exe (PID: 4872)
Process drops legitimate windows executable
- RDPWInst.exe (PID: 4872)
Executable content was dropped or overwritten
- RDPWInst.exe (PID: 4872)
Uses NETSH.EXE to add a firewall rule or allowed programs
- RDPWInst.exe (PID: 4872)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7976)
Manual execution by a user
- cmd.exe (PID: 5020)
- RDPConf.exe (PID: 6660)
- RDPConf.exe (PID: 6396)
Checks supported languages
- RDPWInst.exe (PID: 4872)
- RDPConf.exe (PID: 6396)
Reads the computer name
- RDPWInst.exe (PID: 4872)
- RDPConf.exe (PID: 6396)
Creates files in the program directory
- RDPWInst.exe (PID: 4872)
Checks proxy server information
- RDPWInst.exe (PID: 4872)
Reads the machine GUID from the registry
- RDPWInst.exe (PID: 4872)
Reads the software policy settings
- RDPWInst.exe (PID: 4872)
Creates files or folders in the user directory
- RDPWInst.exe (PID: 4872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:07:23 19:19:08 |
| ZipCRC: | 0xfd9956a7 |
| ZipCompressedSize: | 250 |
| ZipUncompressedSize: | 458 |
| ZipFileName: | install.bat |
Total processes
136
Monitored processes
10
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1284 | "C:\Users\admin\Desktop\RDPWInst" -i -o | C:\Users\admin\Desktop\RDPWInst.exe | — | cmd.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Wrapper Library Installer Exit code: 3221226540 Version: 2.5.0.0 Modules
| |||||||||||||||
| 1832 | "C:\Users\admin\Desktop\RDPWInst.exe" -i -o | C:\Users\admin\Desktop\RDPWInst.exe | — | cmd.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Wrapper Library Installer Exit code: 3221226540 Version: 2.5.0.0 Modules
| |||||||||||||||
| 2080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RDPWInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3328 | netsh advfirewall firewall add rule name="Remote Desktop" dir=in protocol=tcp localport=3389 profile=any action=allow | C:\Windows\System32\netsh.exe | — | RDPWInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4872 | "C:\Users\admin\Desktop\RDPWInst.exe" -i -o | C:\Users\admin\Desktop\RDPWInst.exe | cmd.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: HIGH Description: RDP Wrapper Library Installer Exit code: 0 Version: 2.5.0.0 Modules
| |||||||||||||||
| 5020 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\install.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
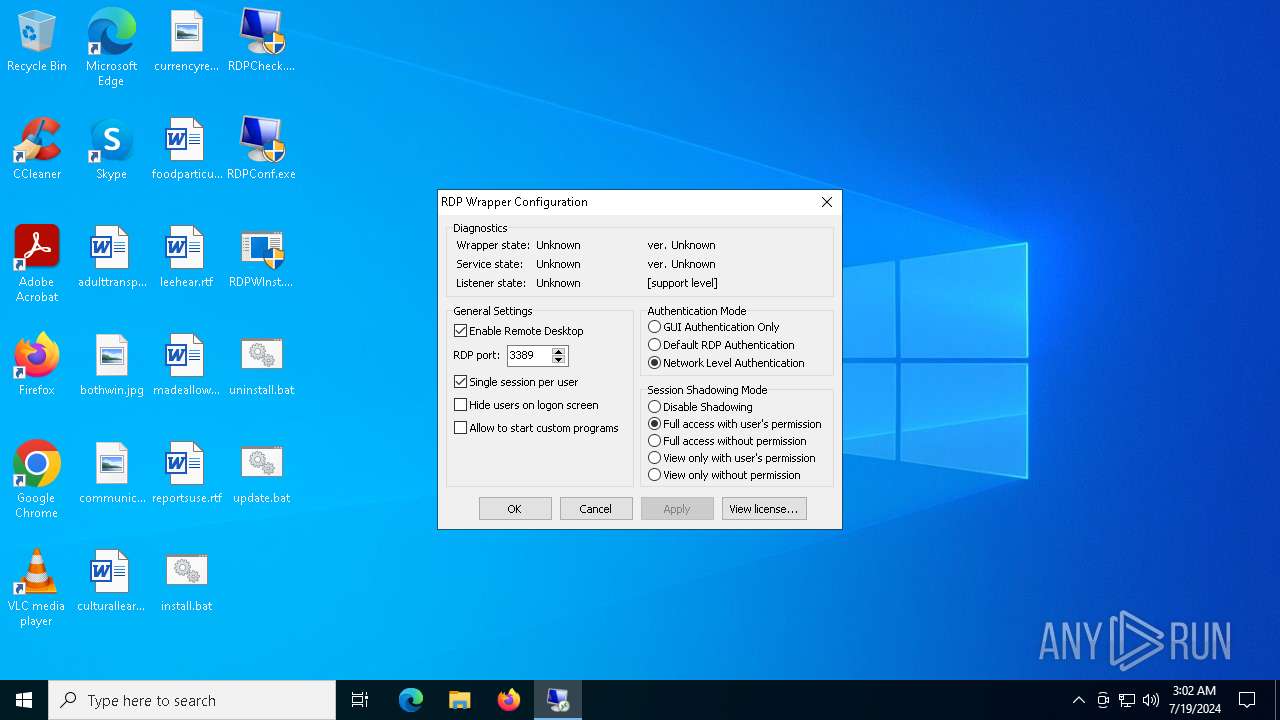
| 6396 | "C:\Users\admin\Desktop\RDPConf.exe" | C:\Users\admin\Desktop\RDPConf.exe | explorer.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: HIGH Description: RDP Configuration Program Version: 1.4.0.0 Modules
| |||||||||||||||
| 6660 | "C:\Users\admin\Desktop\RDPConf.exe" | C:\Users\admin\Desktop\RDPConf.exe | — | explorer.exe | |||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: RDP Configuration Program Exit code: 3221226540 Version: 1.4.0.0 Modules
| |||||||||||||||
| 7976 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\RDPWrap-v1.6.2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 716
Read events
7 672
Write events
44
Delete events
0
Modification events
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RDPWrap-v1.6.2.zip | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (7976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
5
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7976 | WinRAR.exe | C:\Users\admin\Desktop\RDPConf.exe | executable | |
MD5:03FB8E478F4BA100D37A136231FA2F78 | SHA256:3C0E5D6863B03283AFDA9BD188501757D47DC57FC4BBA2BDBB0D9BAA34487FE0 | |||
| 7976 | WinRAR.exe | C:\Users\admin\Desktop\install.bat | text | |
MD5:CBAD5B2CA73917006791882274F769E8 | SHA256:022364EE1FCE61C8A867216C79F223BF47692CD648E3FD6B244FC615B86E4C58 | |||
| 7976 | WinRAR.exe | C:\Users\admin\Desktop\uninstall.bat | text | |
MD5:ECCB8A01D0427EF29C2380D7DDA399F3 | SHA256:083CD340C800CC021D4A59388680CE0E7AB0F8B998E67DEF6A507070E7FA01B7 | |||
| 7976 | WinRAR.exe | C:\Users\admin\Desktop\RDPWInst.exe | executable | |
MD5:3288C284561055044C489567FD630AC2 | SHA256:AC92D4C6397EB4451095949AC485EF4EC38501D7BB6F475419529AE67E297753 | |||
| 7976 | WinRAR.exe | C:\Users\admin\Desktop\update.bat | text | |
MD5:29CA1C35075247B035AF75C11CAB78F1 | SHA256:353F2DC17A4E80564CAA175F7170DBEDC1B40F704444520AE671F78A5D1F2B6D | |||
| 4872 | RDPWInst.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | der | |
MD5:7D75ED3CD9736924946143AB968B5B63 | SHA256:0BD7D77BEA3917C008980EF175B95B04918222AD603D1ACADDB020F7B9CFBFE7 | |||
| 4872 | RDPWInst.exe | C:\WINDOWS\System32\rfxvmt.dll | executable | |
MD5:E3E4492E2C871F65B5CEA8F1A14164E2 | SHA256:32FF81BE7818FA7140817FA0BC856975AE9FCB324A081D0E0560D7B5B87EFB30 | |||
| 4872 | RDPWInst.exe | C:\Program Files\RDP Wrapper\rdpwrap.dll | executable | |
MD5:461ADE40B800AE80A40985594E1AC236 | SHA256:798AF20DB39280F90A1D35F2AC2C1D62124D1F5218A2A0FA29D87A13340BD3E4 | |||
| 4872 | RDPWInst.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:D28BEC13E9A2B7522453A4E882A9EC4C | SHA256:AE92FA4E59066EE3FFE0B4F5AE91102A716396A8DF7240395436459E3029D72B | |||
| 4872 | RDPWInst.exe | C:\Program Files\RDP Wrapper\rdpwrap.ini | binary | |
MD5:DDDD741AB677BDAC8DCD4FA0DDA05DA2 | SHA256:7D5655D5EC4DEFC2051AA5F582FAC1031B142040C8EEA840FF88887FE27B7668 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
15
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4872 | RDPWInst.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4716 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3616 | backgroundTaskHost.exe | 20.74.47.205:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3616 | backgroundTaskHost.exe | 20.31.169.57:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6500 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
google.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |