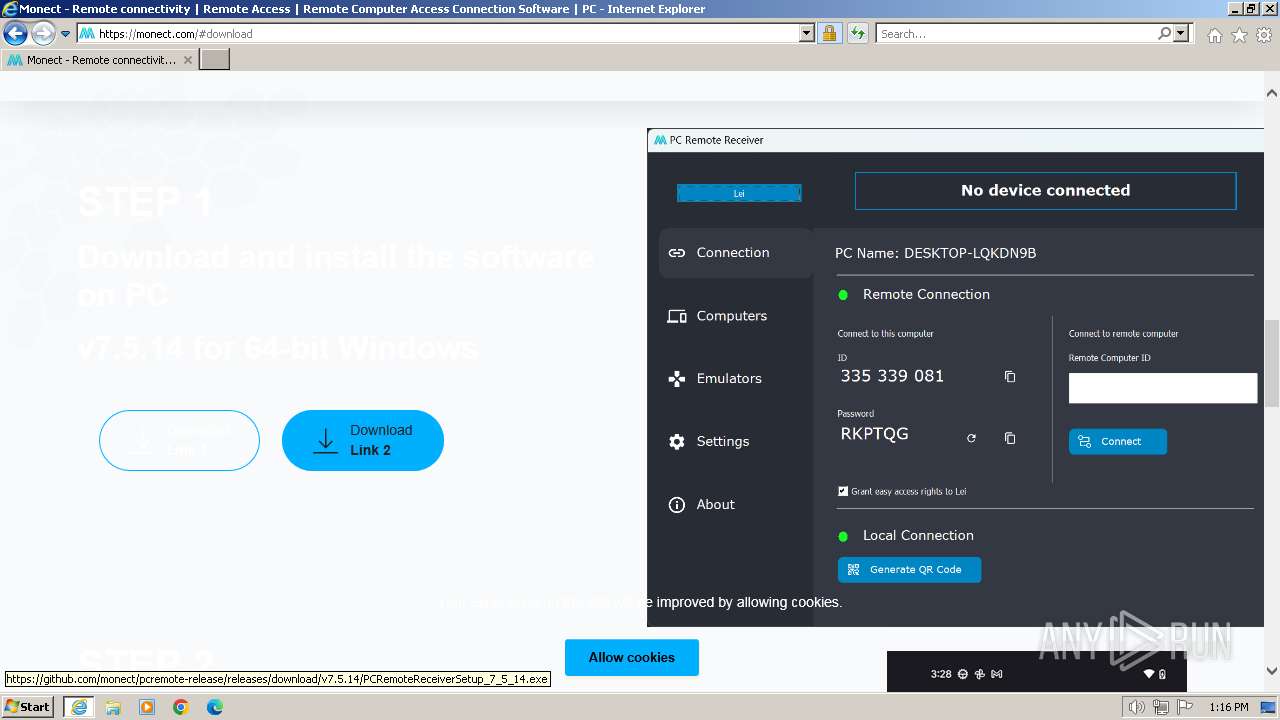
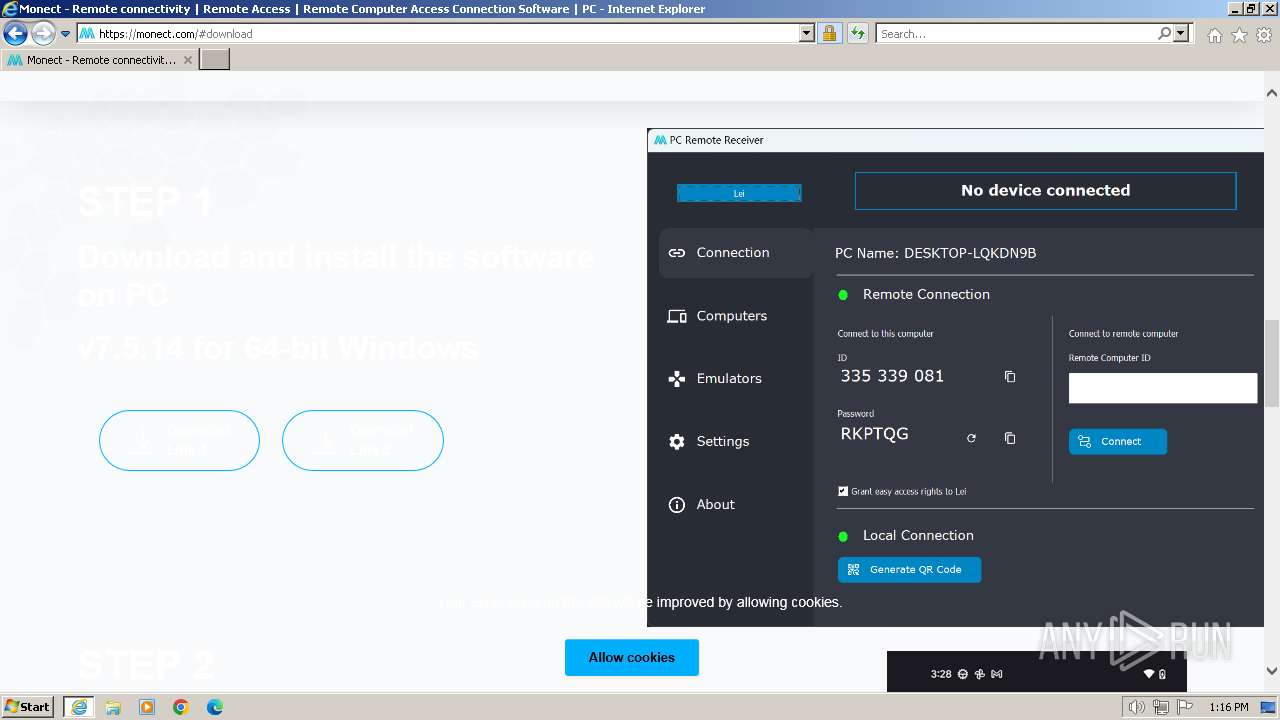
| URL: | https://monect.com |
| Full analysis: | https://app.any.run/tasks/69348647-02b4-4b24-b173-3c8db70a1de3 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2024, 13:16:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C7F79DAB2E42B3EBD54EA6B48BBAB72E |
| SHA1: | EFD565C152915D21576BED42C3CA0C5C0D6B4151 |
| SHA256: | 357E2F94846528AE9517ED3CA55261DBC356709291CC00A1BE2B79A5F0B30313 |
| SSDEEP: | 3:N8ptLK:2e |
MALICIOUS
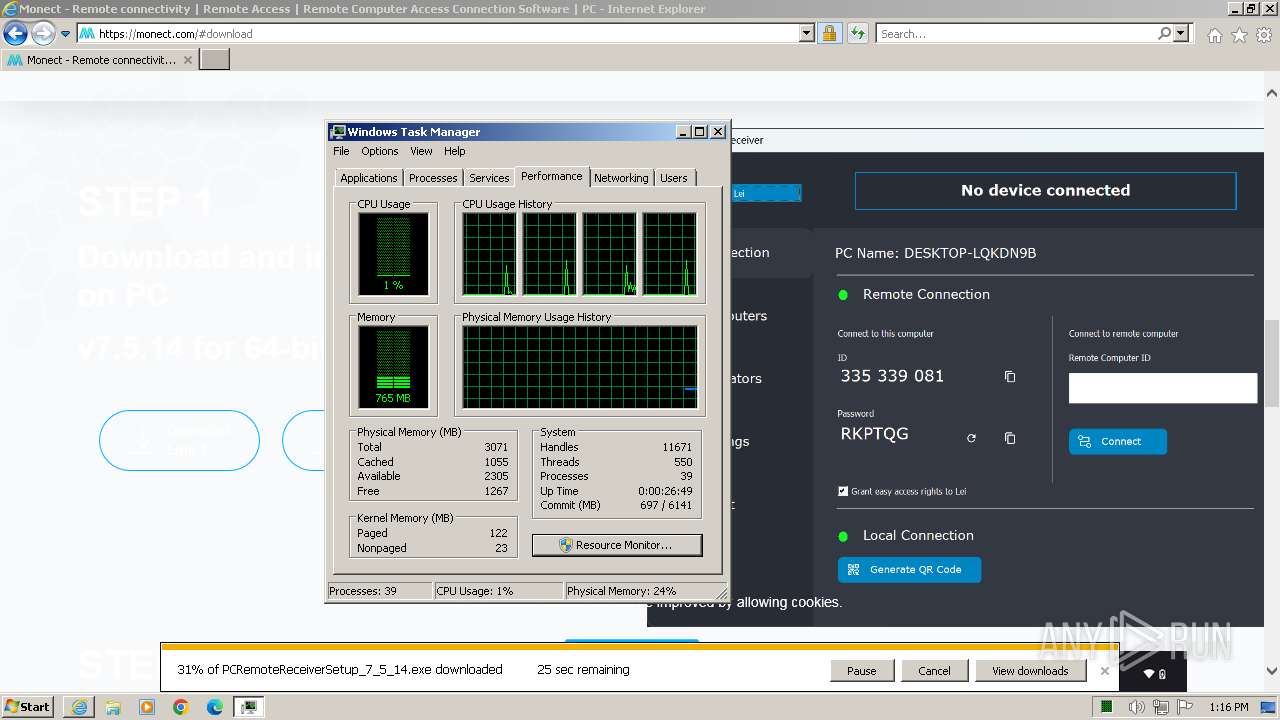
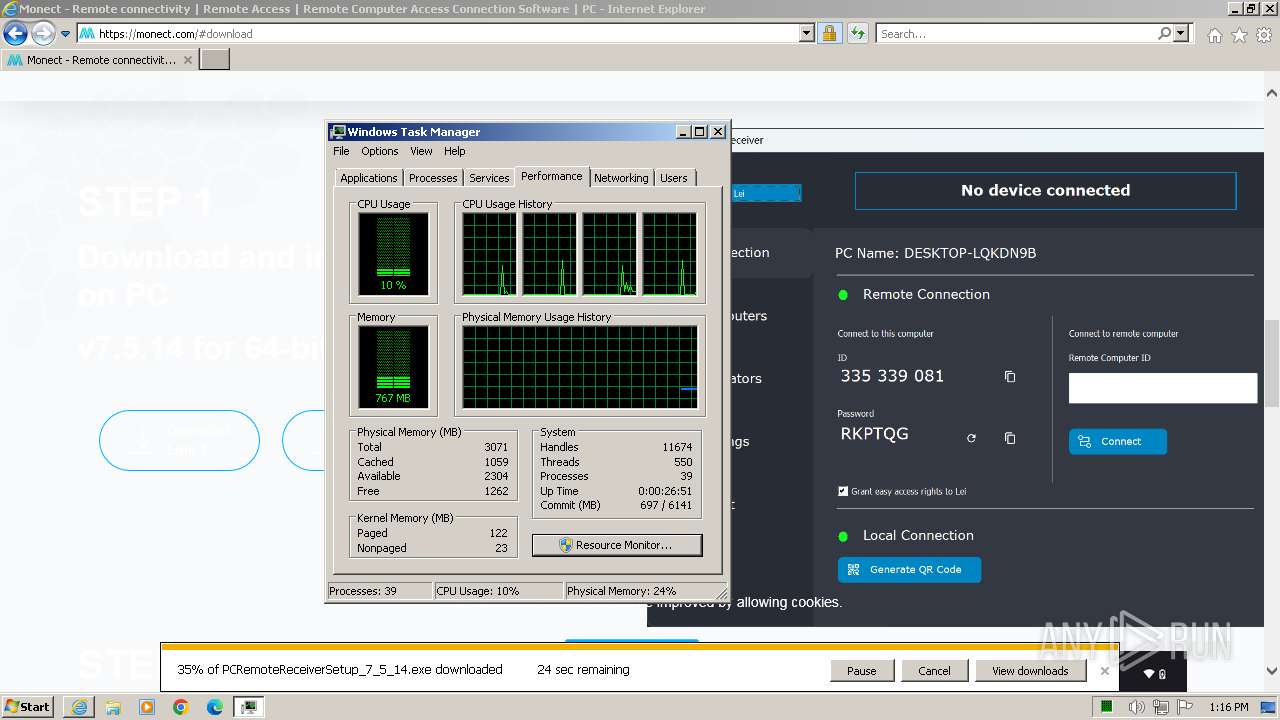
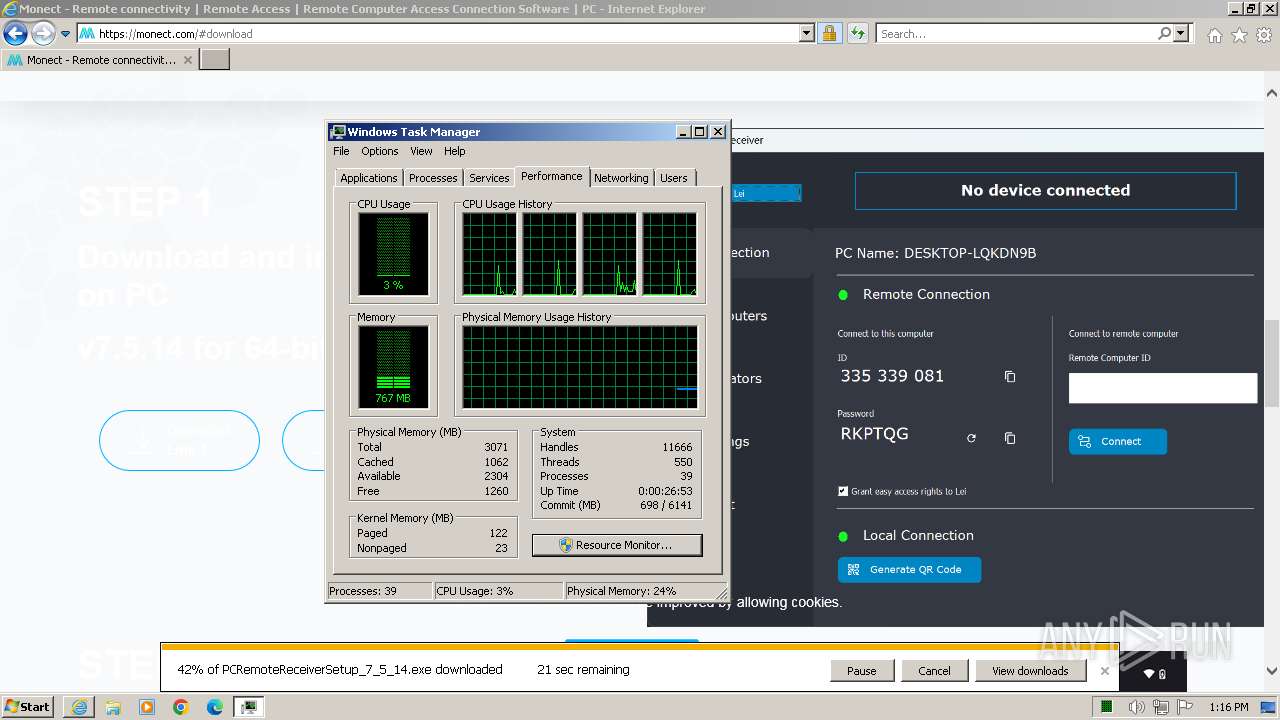
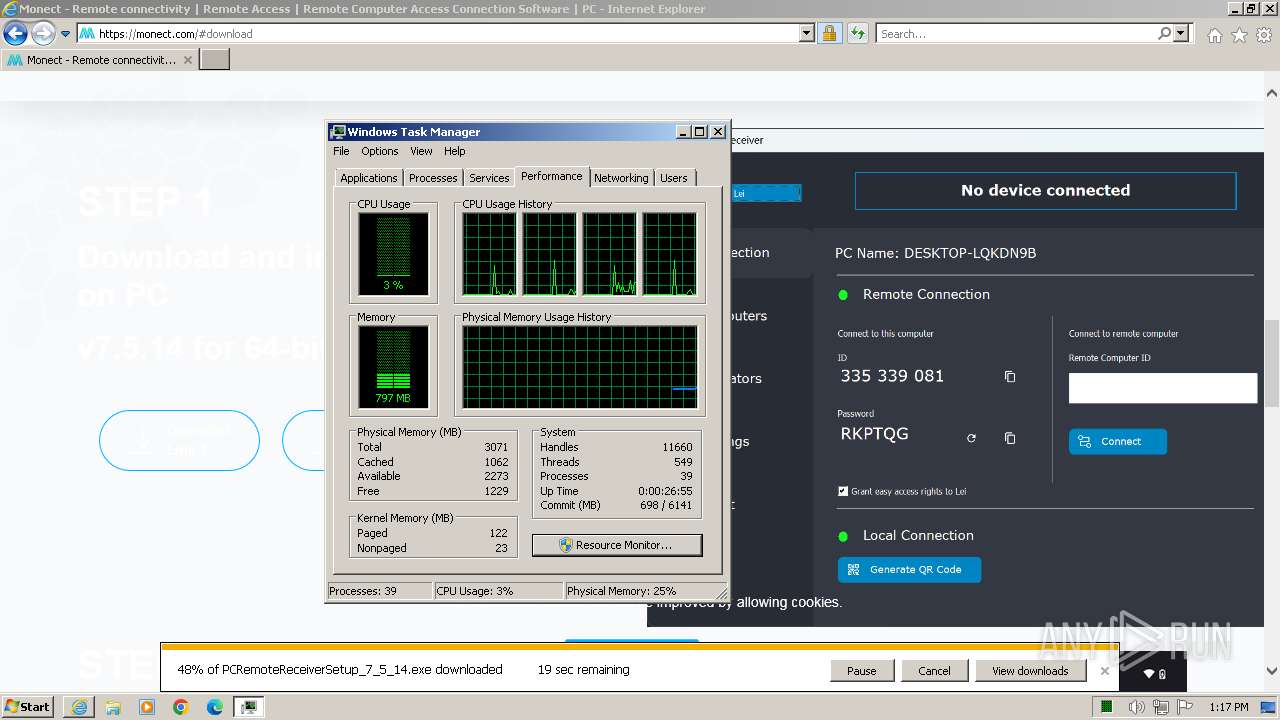
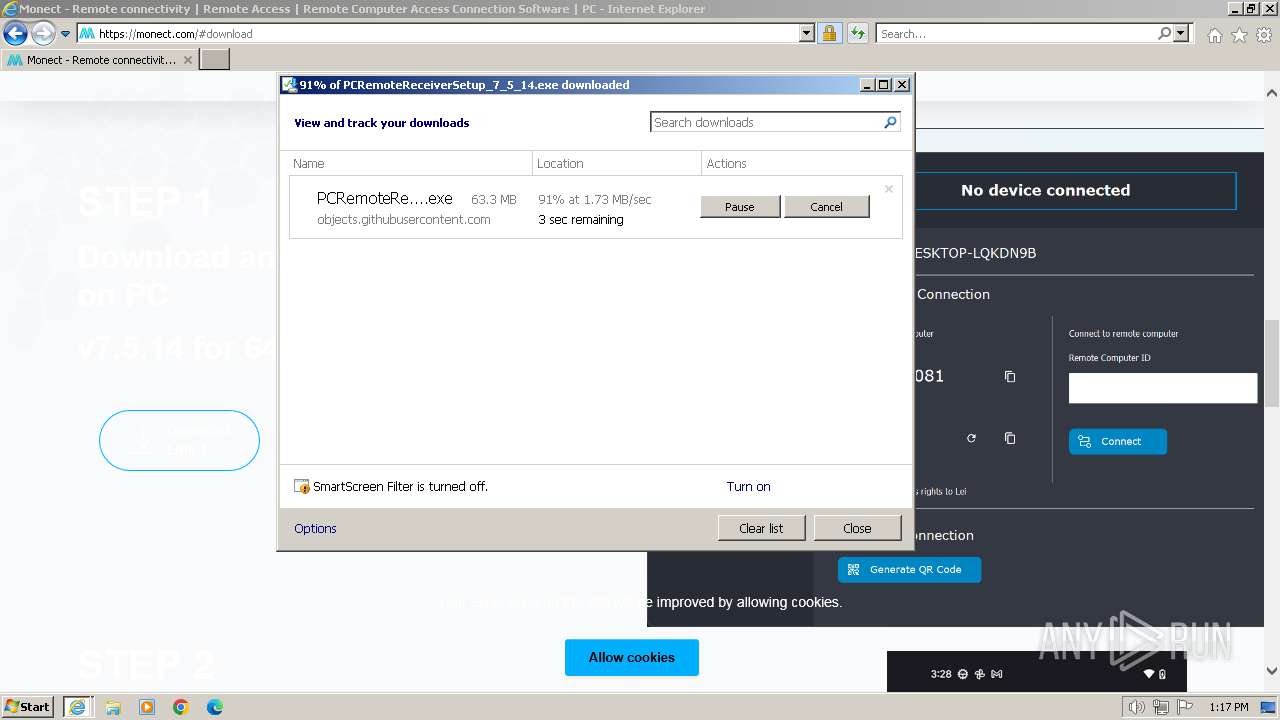
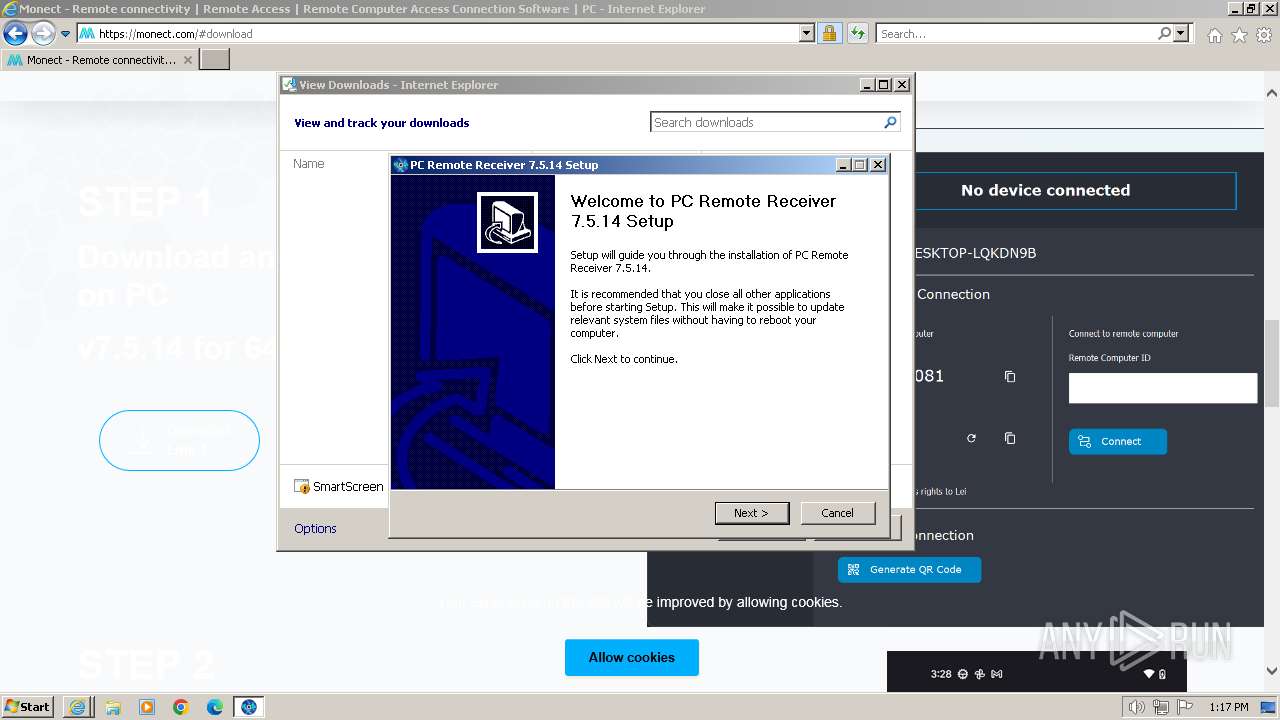
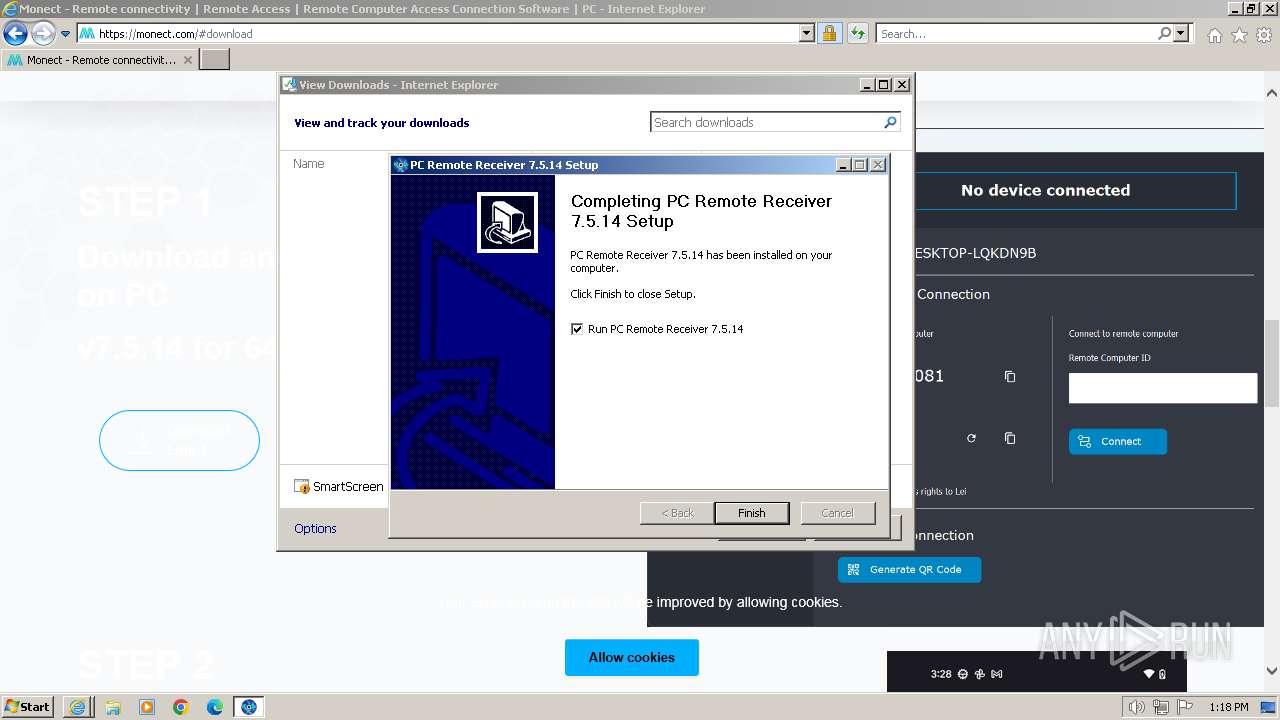
Drops the executable file immediately after the start
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
- vc_redist.x64.exe (PID: 3600)
- vc_redist.x64.exe (PID: 2032)
SUSPICIOUS
Reads the Internet Settings
- taskmgr.exe (PID: 2804)
Executable content was dropped or overwritten
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
- vc_redist.x64.exe (PID: 3600)
- vc_redist.x64.exe (PID: 2032)
Uses TASKKILL.EXE to kill process
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
Drops a system driver (possible attempt to evade defenses)
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
Process drops legitimate windows executable
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
- vc_redist.x64.exe (PID: 2032)
The process creates files with name similar to system file names
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
Searches for installed software
- vc_redist.x64.exe (PID: 3600)
Malware-specific behavior (creating "System.dll" in Temp)
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
Starts a Microsoft application from unusual location
- vc_redist.x64.exe (PID: 3600)
INFO
Application launched itself
- iexplore.exe (PID: 2120)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2120)
Manual execution by a user
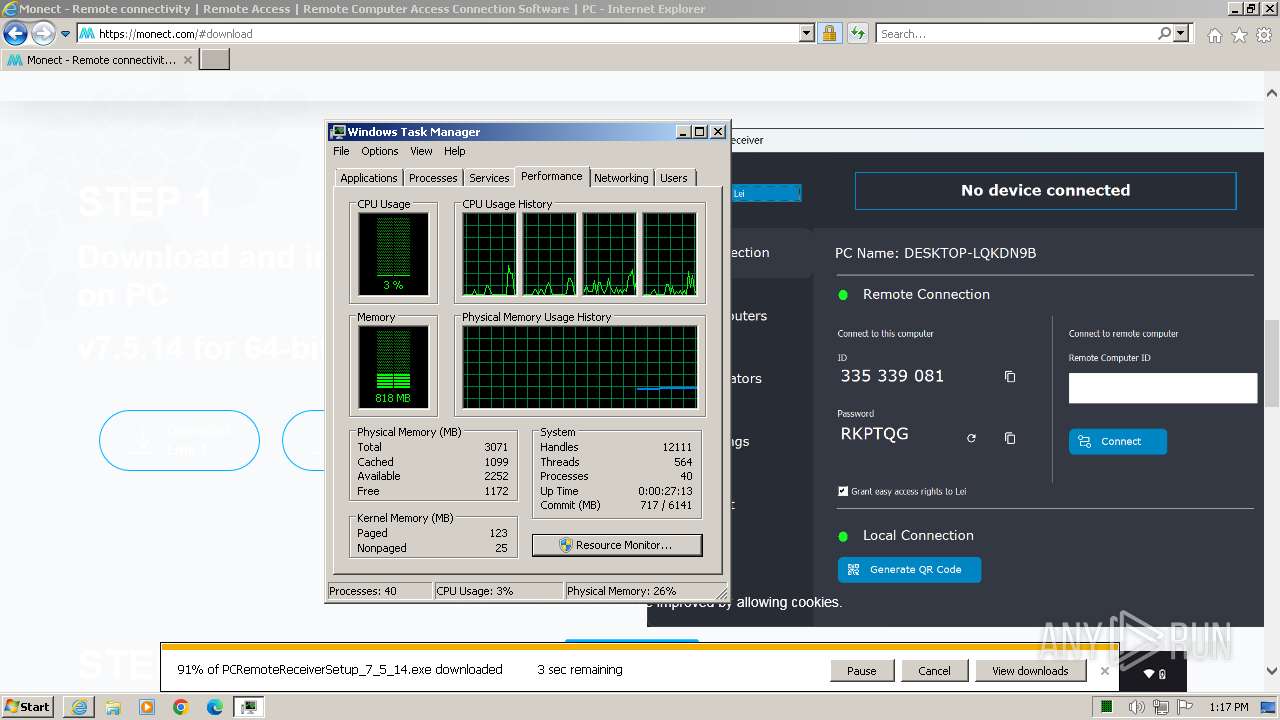
- taskmgr.exe (PID: 2804)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3276)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3276)
Reads security settings of Internet Explorer
- taskmgr.exe (PID: 2804)
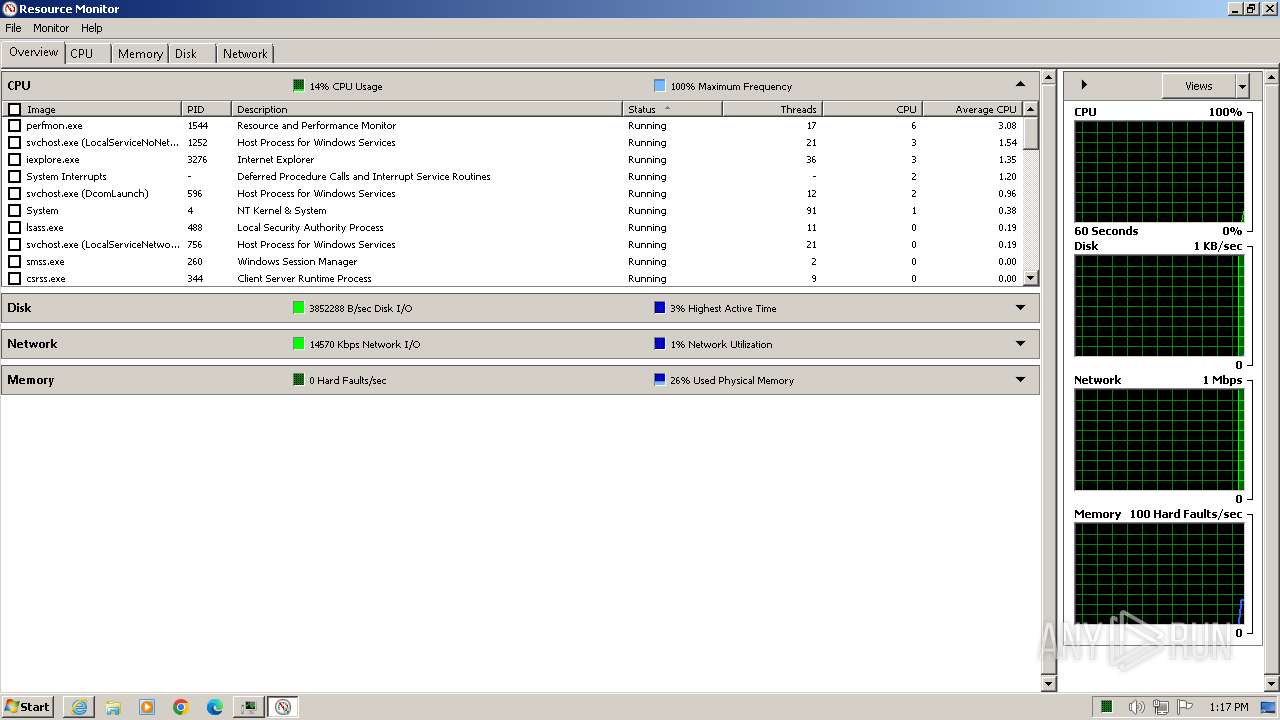
Reads the time zone
- perfmon.exe (PID: 1544)
Creates files or folders in the user directory
- perfmon.exe (PID: 1544)
Checks supported languages
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
- vc_redist.x64.exe (PID: 2032)
- vc_redist.x64.exe (PID: 3600)
Reads the computer name
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
- vc_redist.x64.exe (PID: 3600)
The process uses the downloaded file
- iexplore.exe (PID: 2120)
Create files in a temporary directory
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
- vc_redist.x64.exe (PID: 3600)
Creates files in the program directory
- PCRemoteReceiverSetup_7_5_14.exe (PID: 2748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
66
Monitored processes
14
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
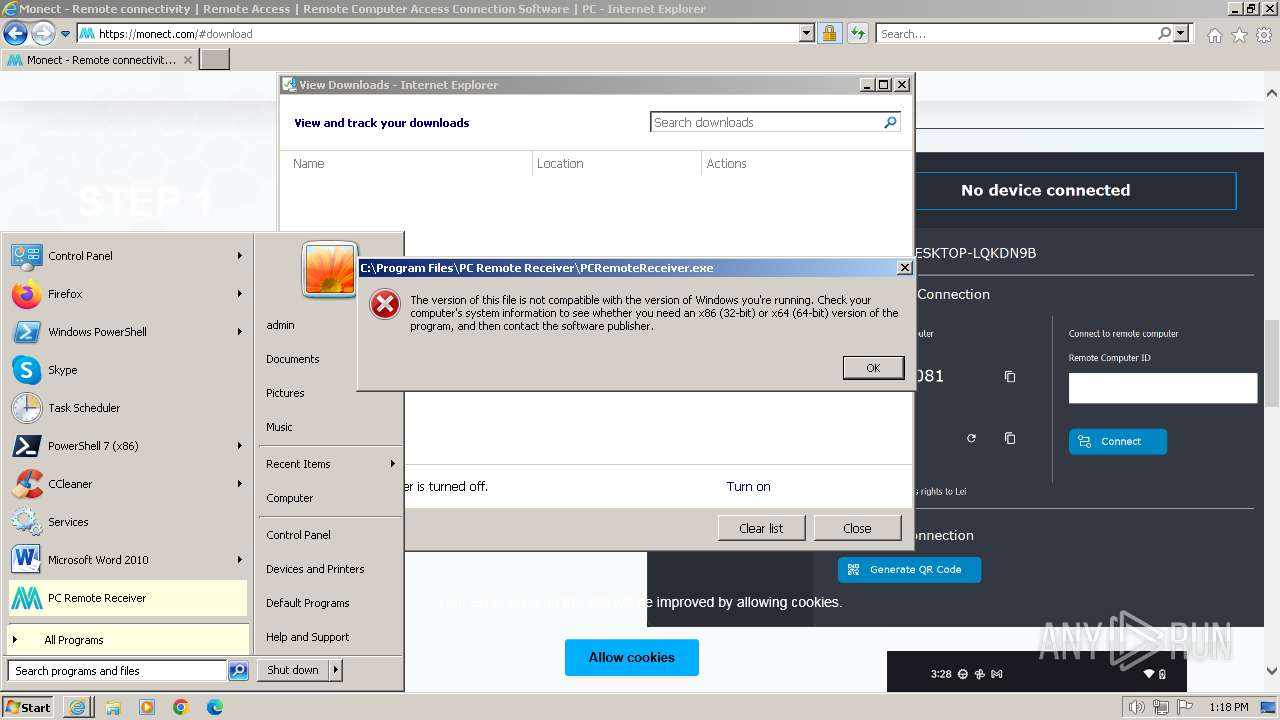
| 552 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PCRemoteReceiverSetup_7_5_14.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PCRemoteReceiverSetup_7_5_14.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 896 | TaskKill /IM MonectMediaCenter.exe /F /T | C:\Windows\System32\taskkill.exe | — | PCRemoteReceiverSetup_7_5_14.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | TaskKill /IM MonectRuntimeCheck.exe /F /T | C:\Windows\System32\taskkill.exe | — | PCRemoteReceiverSetup_7_5_14.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | TaskKill /IM MonectServerService.exe /F /T | C:\Windows\System32\taskkill.exe | — | PCRemoteReceiverSetup_7_5_14.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | "C:\Windows\System32\perfmon.exe" /res | C:\Windows\System32\perfmon.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Resource and Performance Monitor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2032 | "C:\Program Files\PC Remote Receiver\Packages\vc_redist.x64.exe" /install /quiet /norestart | C:\Program Files\PC Remote Receiver\Packages\vc_redist.x64.exe | PCRemoteReceiverSetup_7_5_14.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2019 Redistributable (x64) - 14.25.28508 Exit code: 1 Version: 14.25.28508.3 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://monect.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2748 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PCRemoteReceiverSetup_7_5_14.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PCRemoteReceiverSetup_7_5_14.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2804 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3020 | TaskKill /IM driververifyx64.exe /F /T | C:\Windows\System32\taskkill.exe | — | PCRemoteReceiverSetup_7_5_14.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
30 703
Read events
30 535
Write events
116
Delete events
52
Modification events
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31095697 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 204106142 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31095698 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
46
Suspicious files
93
Text files
80
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:BAD315A2253B989B5C3413446AF41842 | SHA256:B15BF5B7F9105D8C7F8FB4D3FB10674276AFF215B20D481DDD23FE7170644D64 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\B4IJF2UR.txt | text | |
MD5:6D27F7B9584D80A7113FBAFA17E3CAB5 | SHA256:250DA78EA98CE39AEC7DCC26FF39094976E7947CCD141CCB82BB85C74C1F1F6F | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\4LVPXIH0.htm | html | |
MD5:3B01CDB0C75C4C0D35E567303C18B52D | SHA256:4AAD5B8DBE5DB5435789F3BB037AAFCBD21B066A0EF32E8D6DCBFE47D370AC2F | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_9F6005AF34C7906F717D420F892FD6D0 | binary | |
MD5:02D3ADE4EE34192D6911EC2ECA569287 | SHA256:2EA38BDAEA1FB36BD503E9E0C608F31123DD75E0ED8AFDB721A0FC43CD24C2F4 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\js[1].js | text | |
MD5:5FC7B80160F48C98AA7689394D74FB19 | SHA256:725142B61A4AEB1FD4D51028DD2AF09F45265FBC2E97EDF08961A0D0CA5157F1 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\js[1].js | text | |
MD5:96E0C6180F75145ADF825728C8B1700D | SHA256:F561BCB64EAE03A1AE5806C79191833B698951232268585FFB4F947B8DCF078E | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:7202528E67C3B5557F0979684F0F6D7F | SHA256:4EA485782A3B34E0D5FD3B27D8B414371AD3FBF7DD2E6D9960D45492B0DAE92E | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_99430B8B5F4E113F6193E2BF9312EF16 | binary | |
MD5:A5770A46F8655E9E0A9D686AFE9FCDC2 | SHA256:43E2CB81A9DBD3E6E9C29A3AFFE7CAA6C75FFEFC697A956A090DB4C3F55152D3 | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4B7XVM18.txt | text | |
MD5:F3A6E25661A6BA4CEF9B4E7229204E4D | SHA256:D83C436DF147D78B4DCC812887C456F4ACEC47C35B453D751BC322169E2BBCDD | |||
| 3276 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\XNAH8ISR.txt | text | |
MD5:57BDD8390074C499035340C3CD035011 | SHA256:52E1D3CC5D19BB3B826694CC2F338256D546BF07C065220102177C01016A7F51 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
65
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3276 | iexplore.exe | GET | 304 | 23.32.238.179:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5259f1aa84763c8c | unknown | — | — | unknown |
3276 | iexplore.exe | GET | 304 | 23.32.238.179:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7f30423e8f7249ff | unknown | — | — | unknown |
3276 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA9iL28hwv9dUh9yOh1H1i0%3D | unknown | binary | 471 b | unknown |
3276 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3276 | iexplore.exe | GET | 200 | 108.138.2.173:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
3276 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3276 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD6BeWhIbleexId20FpK0af | unknown | binary | 472 b | unknown |
3276 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC%2BP0iGO7o7nQoIudW3BwdU | unknown | binary | 472 b | unknown |
3276 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | binary | 1.37 Kb | unknown |
3276 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDvxruPIA7HMxBTUJjmrhMX | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3276 | iexplore.exe | 20.119.8.26:443 | monect.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3276 | iexplore.exe | 23.32.238.179:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2120 | iexplore.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3276 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3276 | iexplore.exe | 142.250.185.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
3276 | iexplore.exe | 18.66.112.73:443 | cloudfront.monect.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
monect.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
cloudfront.monect.com |
| unknown |
o.ss2.us |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |