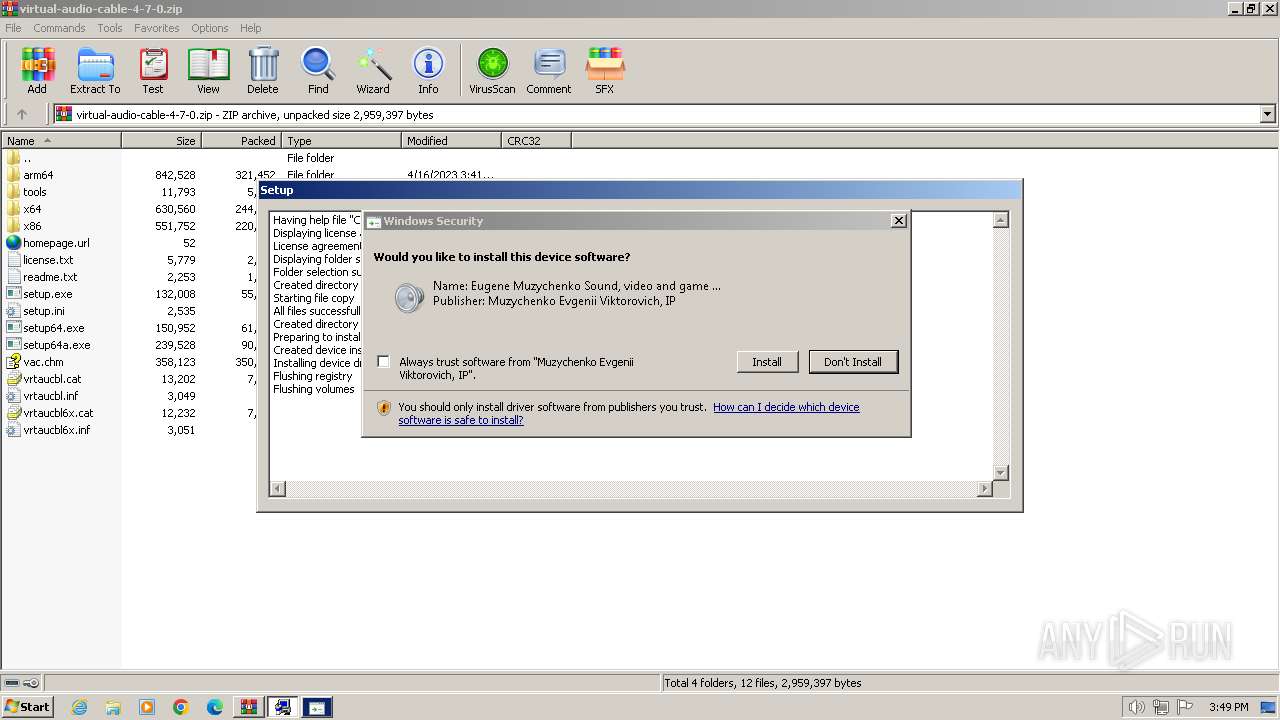
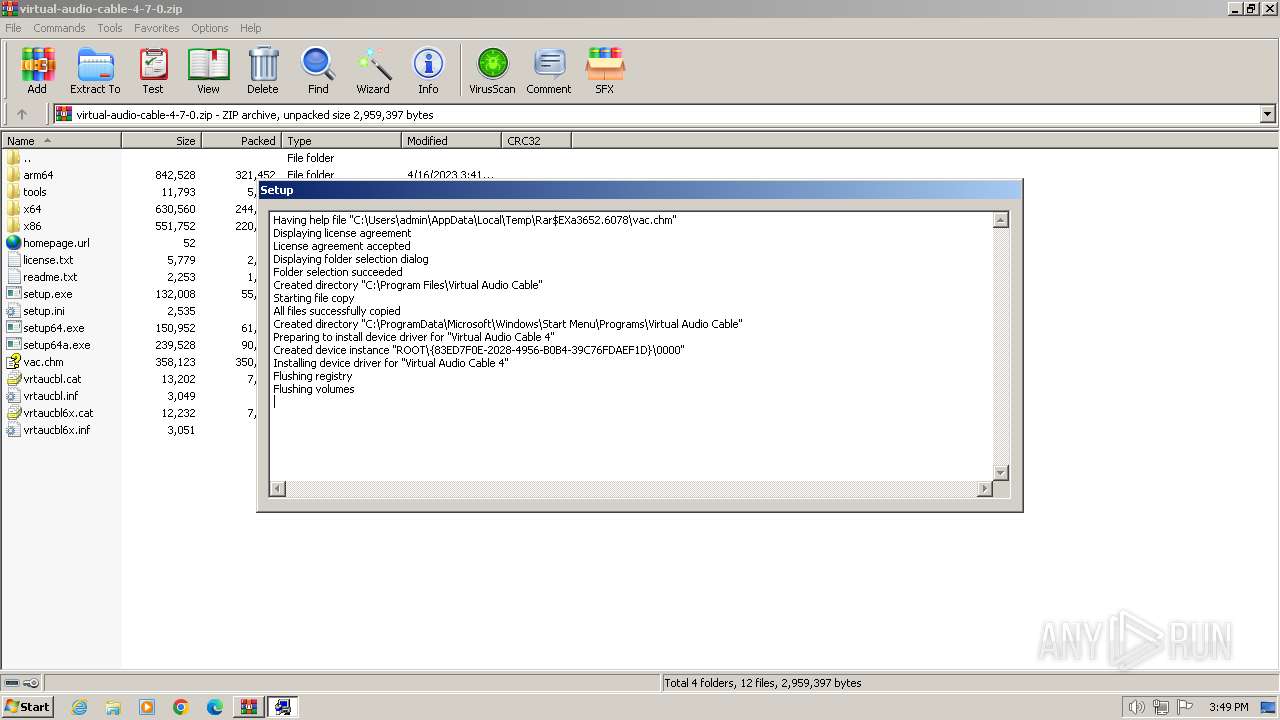
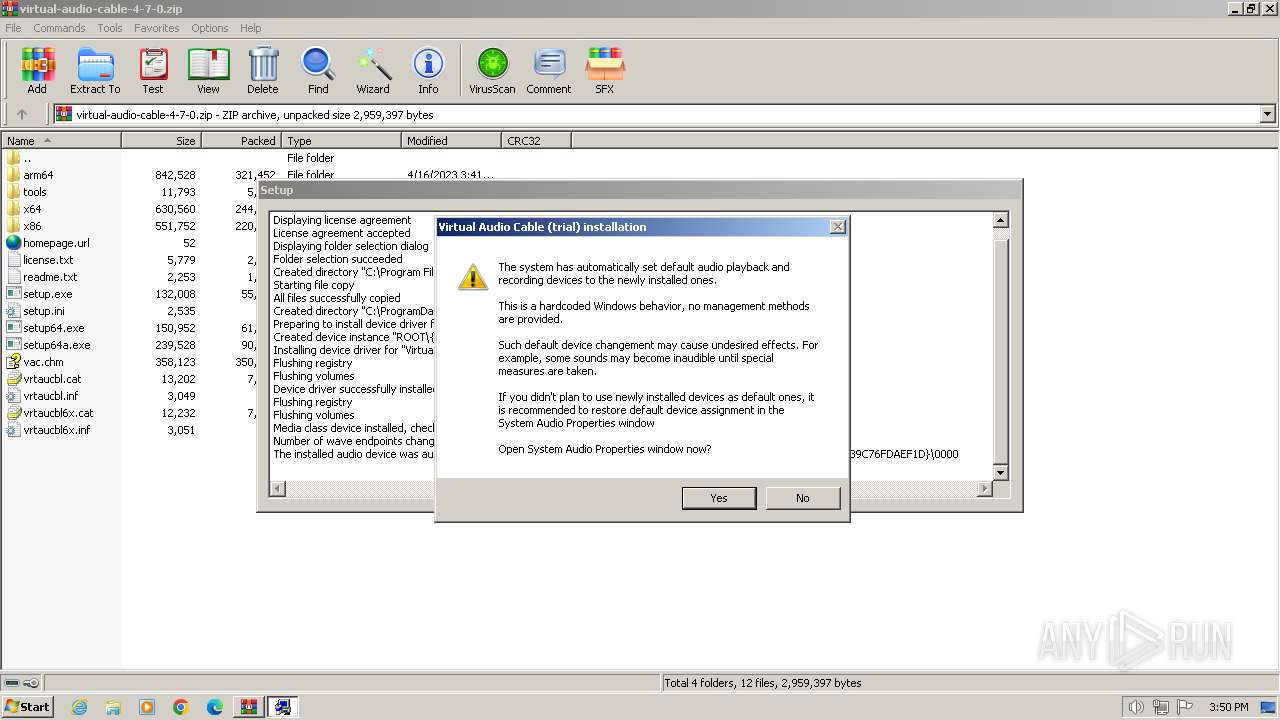
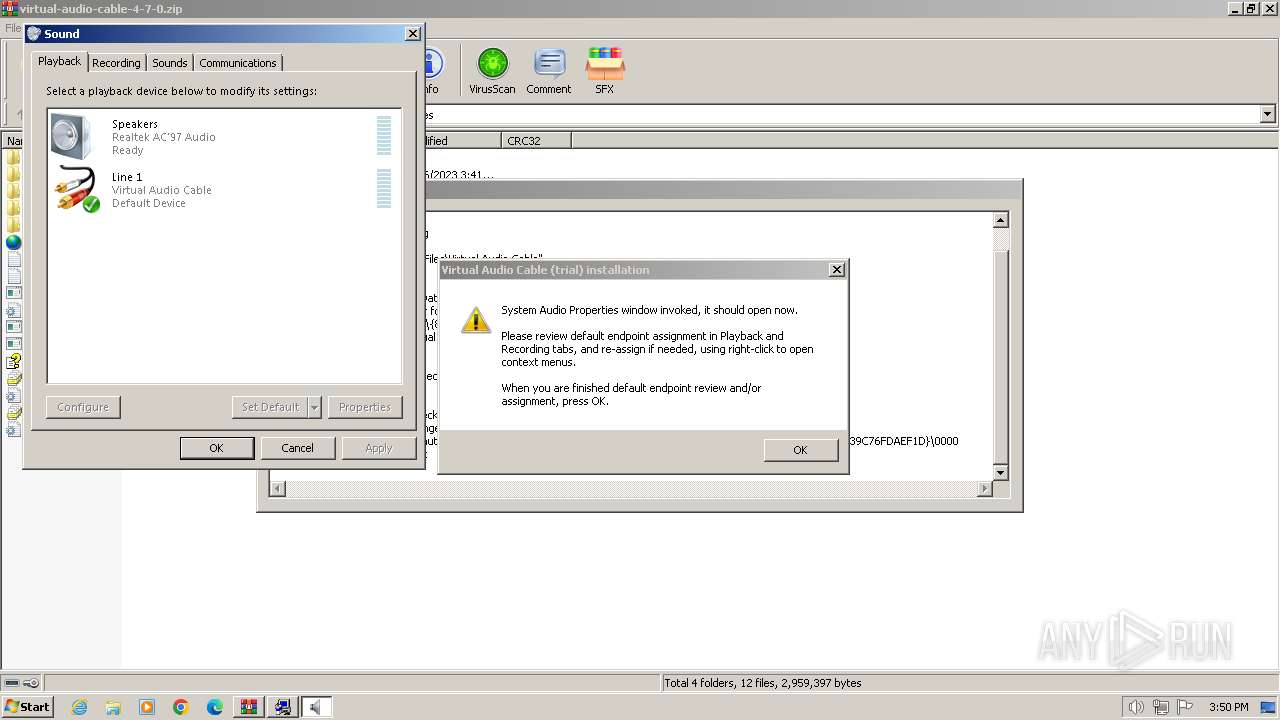
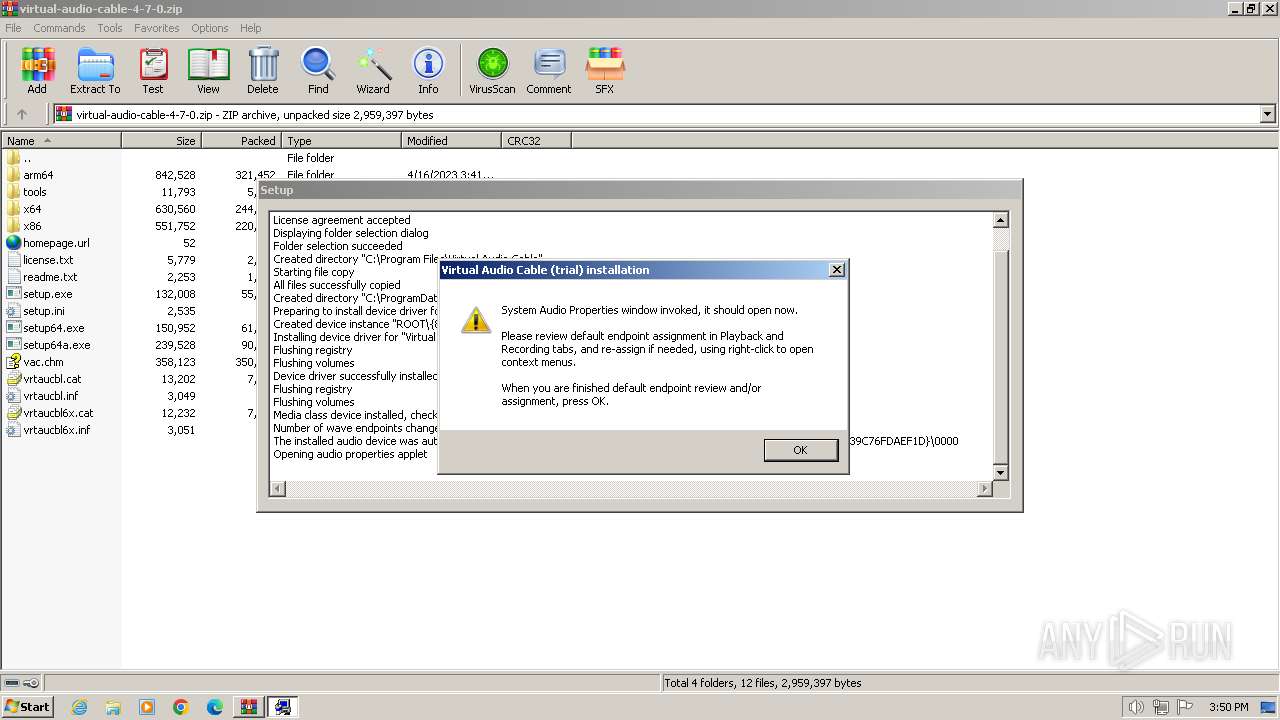
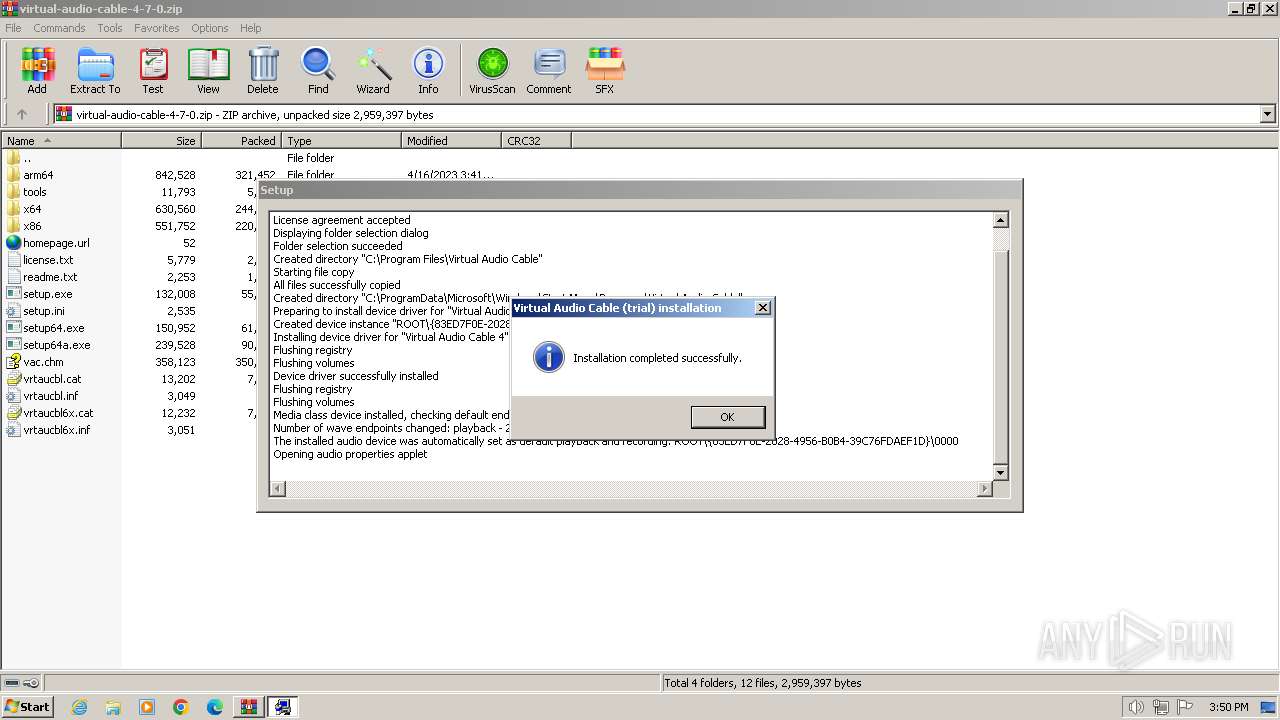
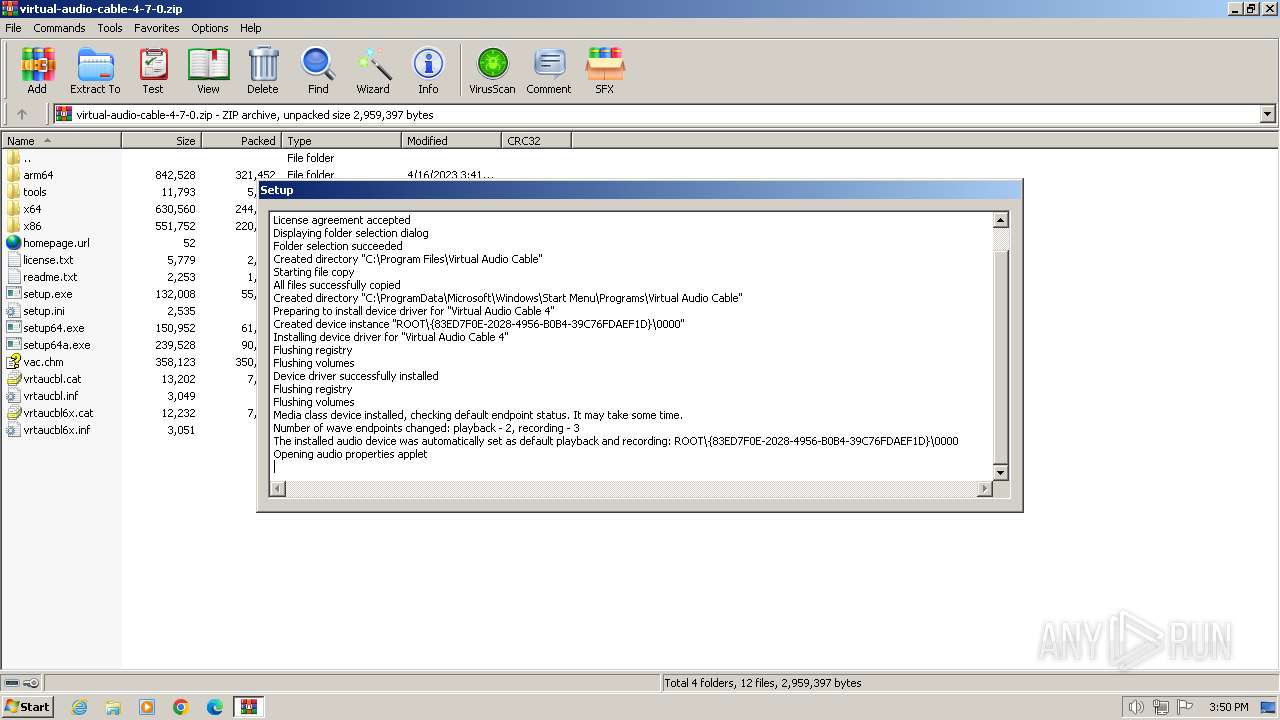
| File name: | virtual-audio-cable-4-7-0.zip |
| Full analysis: | https://app.any.run/tasks/72936a4a-1aeb-4a02-b6c1-7ef889449889 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 15:49:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 5D7CD30D38C8825E93D7B9C0F13327DA |
| SHA1: | B0D7B07007A147A04C6DCC43C24D95DC62CED2FA |
| SHA256: | 356B616EE9F4E72EEE39726301A13B479431D5D8774B88E9100D21303D4E7BD4 |
| SSDEEP: | 49152:3qq6lgTyzEtsDKtMi2ffqbKru0UzWwXm1O4HljrqYG2vPdxPtl0kVXff9eviGxfj:L6lcy4tsDKtzufq2K0UzWE8fVlxPzxVi |
MALICIOUS
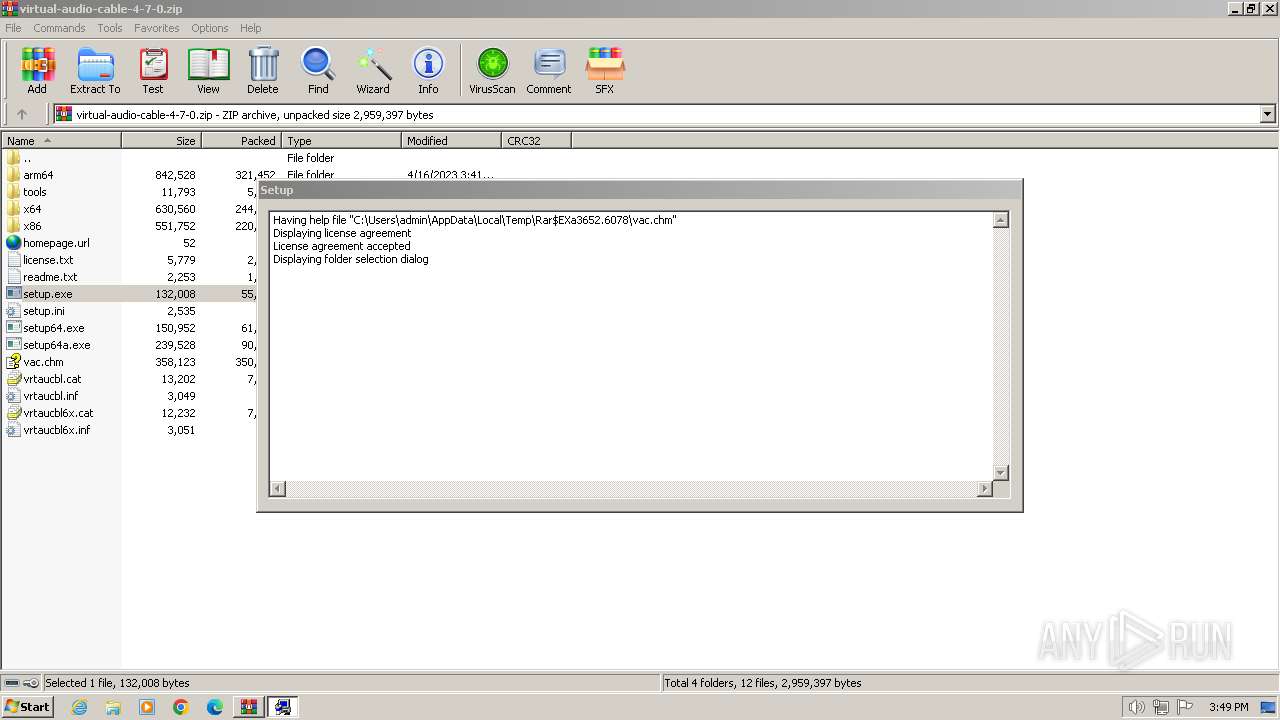
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3652)
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
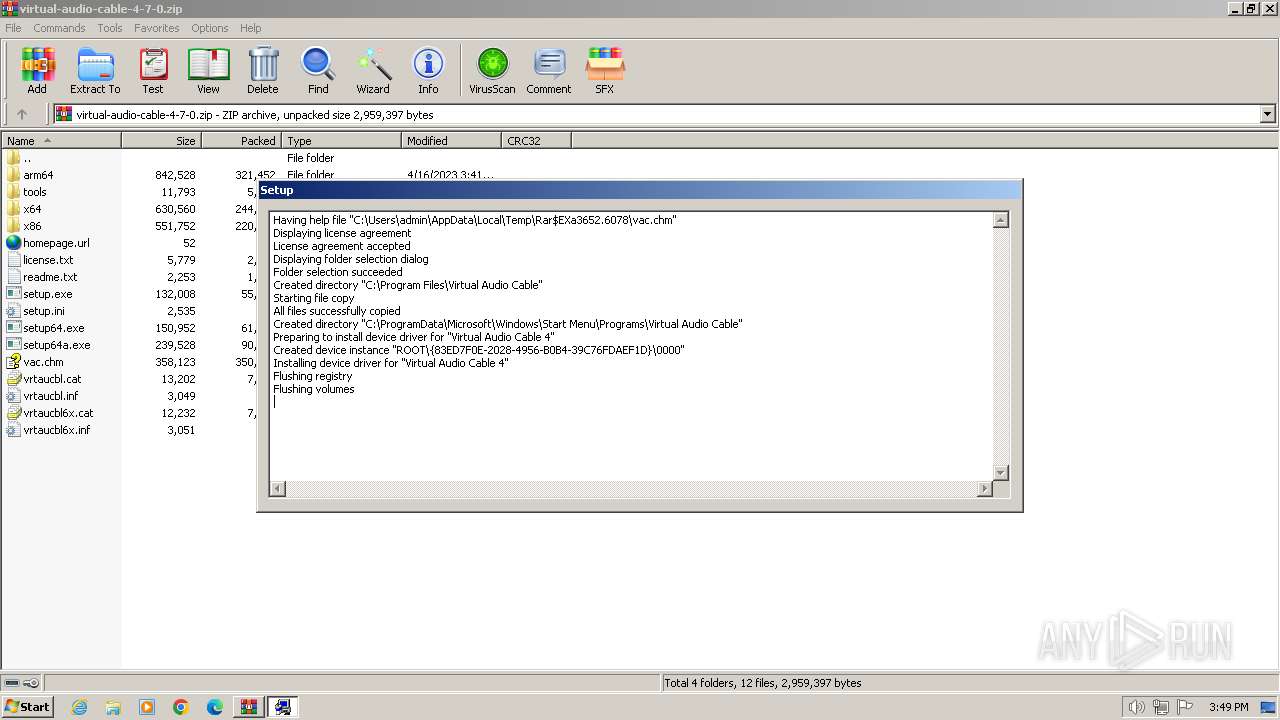
Creates a writable file in the system directory
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3652)
- setup.exe (PID: 2304)
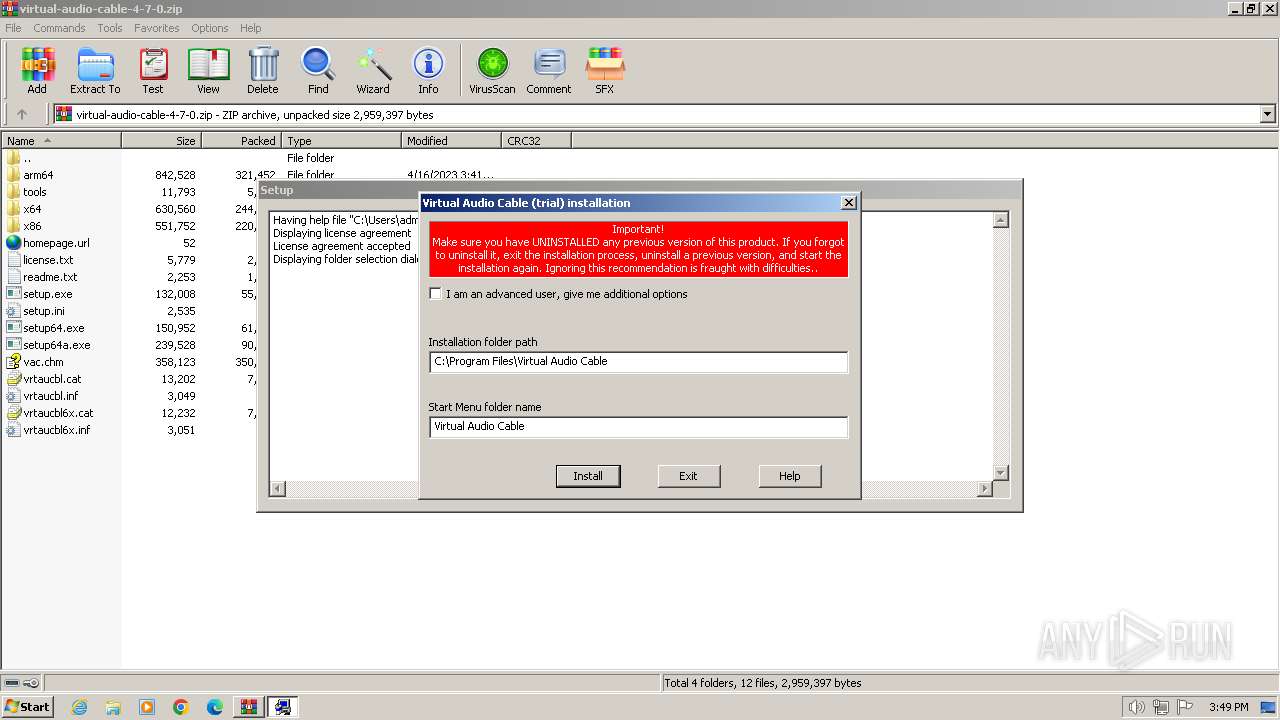
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3652)
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
Creates files in the driver directory
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
Executable content was dropped or overwritten
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
Creates a software uninstall entry
- setup.exe (PID: 2304)
Checks Windows Trust Settings
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
- drvinst.exe (PID: 1644)
Reads settings of System Certificates
- setup.exe (PID: 2304)
- rundll32.exe (PID: 1836)
Adds/modifies Windows certificates
- setup.exe (PID: 2304)
Reads the Internet Settings
- control.exe (PID: 2504)
- setup.exe (PID: 2304)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2504)
Executes as Windows Service
- VSSVC.exe (PID: 4000)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3668)
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
- drvinst.exe (PID: 1644)
Reads the computer name
- wmpnscfg.exe (PID: 3668)
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
- drvinst.exe (PID: 1644)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3652)
Create files in a temporary directory
- setup.exe (PID: 2304)
Creates files in the program directory
- setup.exe (PID: 2304)
Reads the machine GUID from the registry
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
- drvinst.exe (PID: 1644)
Reads the software policy settings
- setup.exe (PID: 2304)
- drvinst.exe (PID: 3500)
- rundll32.exe (PID: 1836)
- drvinst.exe (PID: 1644)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1836)
- control.exe (PID: 2504)
Manual execution by a user
- WINWORD.EXE (PID: 1792)
- chrome.exe (PID: 2404)
Application launched itself
- chrome.exe (PID: 2404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:04:16 16:41:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | arm64/ |
Total processes
66
Monitored processes
26
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3952 --field-trial-handle=1172,i,6305073039228908656,716492260683338932,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=3936 --field-trial-handle=1172,i,6305073039228908656,716492260683338932,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1644 | DrvInst.exe "2" "211" "ROOT\{83ED7F0E-2028-4956-B0B4-39C76FDAEF1D}\0000" "C:\Windows\INF\oem2.inf" "vrtaucbl6x.inf:DevSection.NTx86:DevInst:4.70.0.13050:virtualaudiocable_83ed7f0e-2028-4956-b0b4-39c76fdaef1d" "6646d1453" "000003F8" "000005EC" "000005F0" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1792 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\antiok.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1836 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{6112db5c-716f-5436-777d-771641c0f80e} Global\{0a6a5ee5-a965-2d5a-1475-dd2d68f50305} C:\Windows\System32\DriverStore\Temp\{4f74202f-bc6a-69d5-018c-9764a327586d}\vrtaucbl6x.inf C:\Windows\System32\DriverStore\Temp\{4f74202f-bc6a-69d5-018c-9764a327586d}\vrtaucbl6x.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Eugene V. Muzychenko Integrity Level: HIGH Description: Software setup application Exit code: 0 Version: 1.14.0.1020 Modules
| |||||||||||||||
| 2396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bb38b38,0x6bb38b48,0x6bb38b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2504 | "C:\Windows\System32\control.exe" mmsys.cpl | C:\Windows\System32\control.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2152 --field-trial-handle=1172,i,6305073039228908656,716492260683338932,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
39 988
Read events
38 879
Write events
781
Delete events
328
Modification events
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\virtual-audio-cable-4-7-0.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
26
Suspicious files
32
Text files
96
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\arm64\audiorepeater_ks.exe | executable | |
MD5:63111275986F328FF9E552760EF8A574 | SHA256:7EEAF015E8C0D45FA0BD5356DB7B08569959E02B0CAD1AEE84B5951C13A3422B | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\setup64a.exe | executable | |
MD5:52ABF119CFBD7CF7217D6C07C33813EB | SHA256:A14CD452427481999B920D7C5A5D9272AD41C861CFF457432EA582C68FB814DE | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\setup.exe | executable | |
MD5:EA21FA3E3F8A5D5360B324B9B9D9AEF0 | SHA256:DF8F07C9574B1C21ECCDE4FDAF2F93EFCA6018B9D4FB066A13505F07C58F99F7 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\arm64\vcctlpan.exe | executable | |
MD5:908840BC55AEA5A3DCAD291E599AA6FF | SHA256:0397C10618A931518CCEE0B26D14D25FAD4CC47A235881CF0B13C0B4A14D9BED | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\tools\delete_phantom.cmd | text | |
MD5:189D19C1CE30A19C0198E9C1D54BE209 | SHA256:7DFE264D2CA361319600F6C4FBABCE8F8A5EDC0F103DC4C1B0436C5E37585A39 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\tools\delete_service.cmd | text | |
MD5:220E73F4D596C64A6EDA4FFAA4B019B8 | SHA256:51412A773C235AFE1FC4D81C25FDCDBDD945CD62FDAFB9C7FBFBE26A17386C12 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\tools\setvars.cmd | text | |
MD5:869073747B866F9A36E284591A2849A0 | SHA256:F49D3BFE2A143E95D78AB6E2BD672426BDF190C90752AE44CC6F203E9CDB5797 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\setup64.exe | executable | |
MD5:916726FF61899725B5569659F3C96E06 | SHA256:A89C0F9A69A2B79E26C7929ABED3D30CF51439162680E09503797C03C8CD6700 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\tools\open_audio_properties.cmd | text | |
MD5:86B1B83E41DAEDF21583DA7CB953B158 | SHA256:E57726A4A11D650647FF812034C9CE76B4484F47E0EBB2EC88D4BC54C207C5D0 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.6078\tools\set_audiodg_instance_count_report.cmd | text | |
MD5:7FA47D3F7B3A11689CF7F085E3BEAAF0 | SHA256:A3D53E4C0B75000F051DF9938277D285FDEF3D8ECB2CE8C45D2C64BCC66DE528 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
24
DNS requests
28
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2404 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
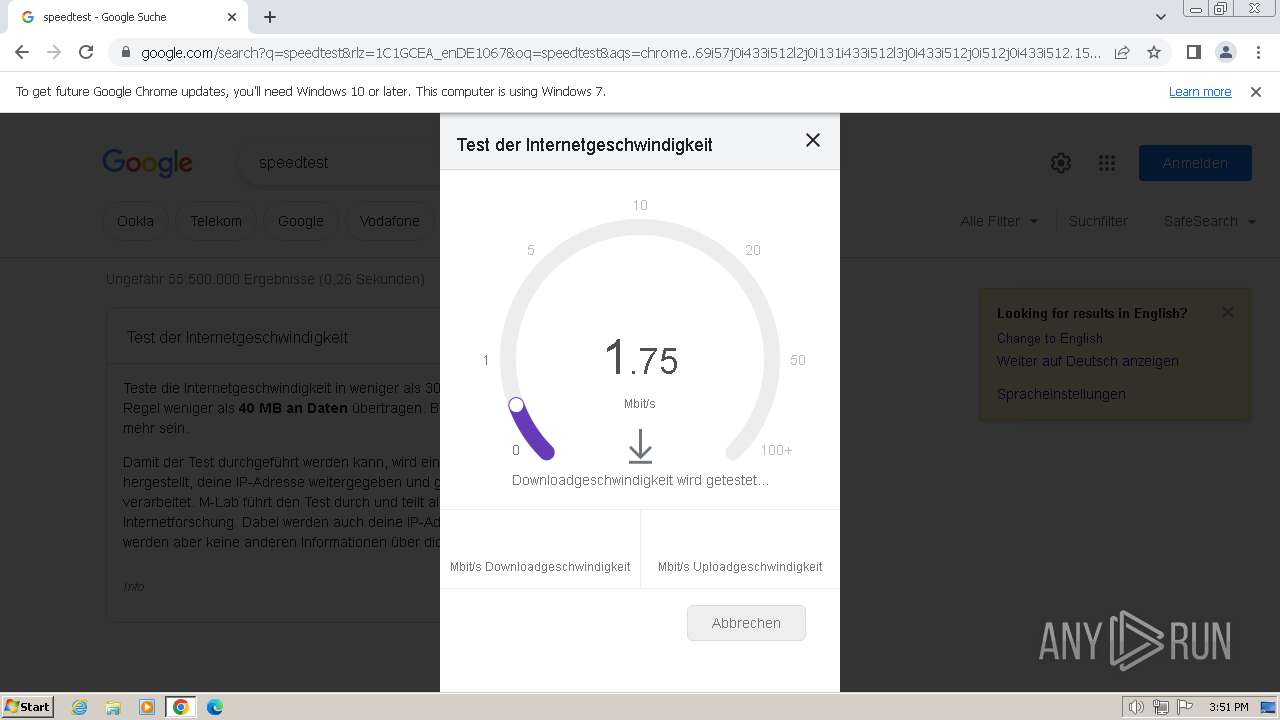
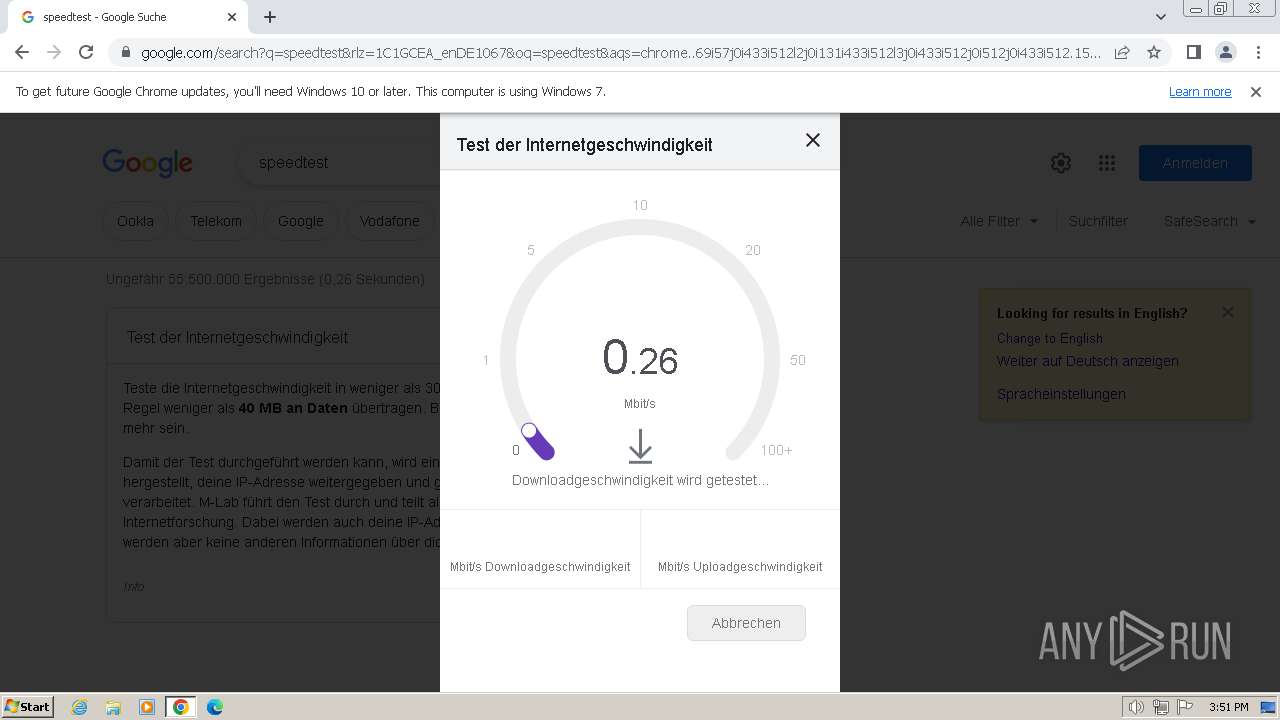
3272 | chrome.exe | 142.250.185.163:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3272 | chrome.exe | 74.125.71.84:443 | accounts.google.com | GOOGLE | US | unknown |
3272 | chrome.exe | 172.217.18.4:443 | www.google.com | GOOGLE | US | whitelisted |
3272 | chrome.exe | 142.250.185.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3272 | chrome.exe | 142.250.186.78:443 | apis.google.com | GOOGLE | US | whitelisted |
3272 | chrome.exe | 172.217.16.206:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
consent.google.com |
| shared |
locate.measurementlab.net |
| malicious |