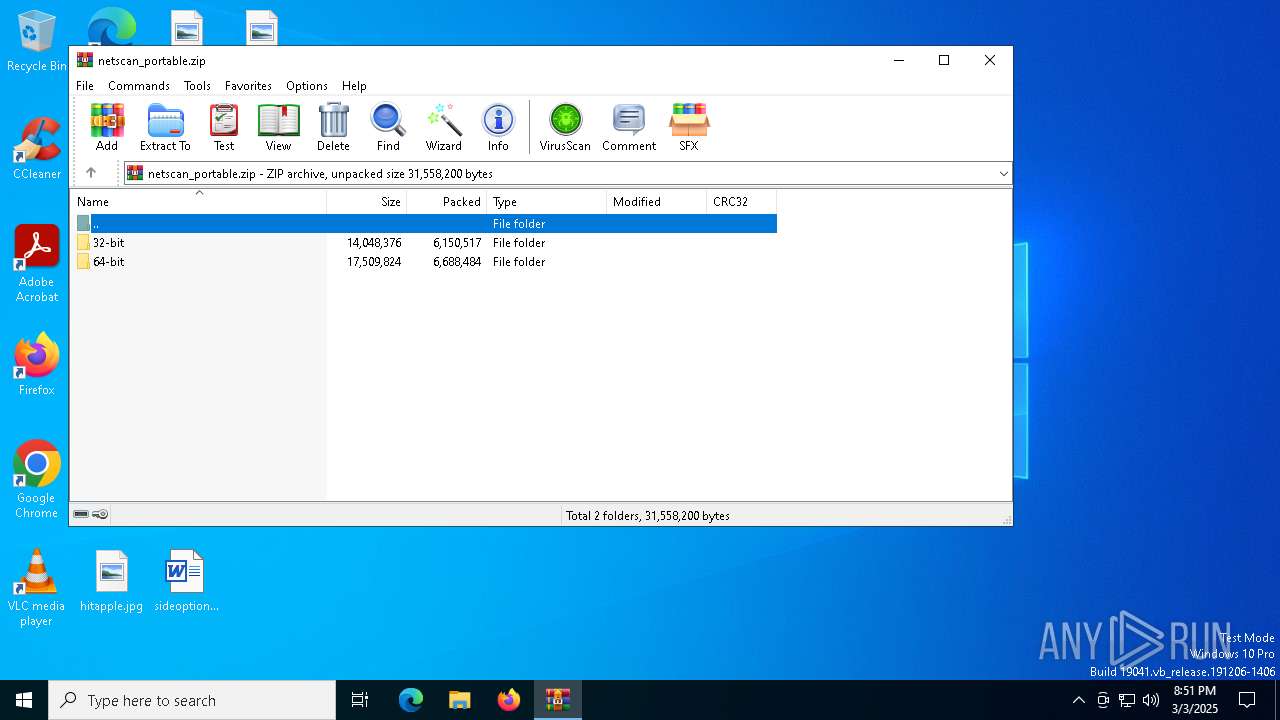
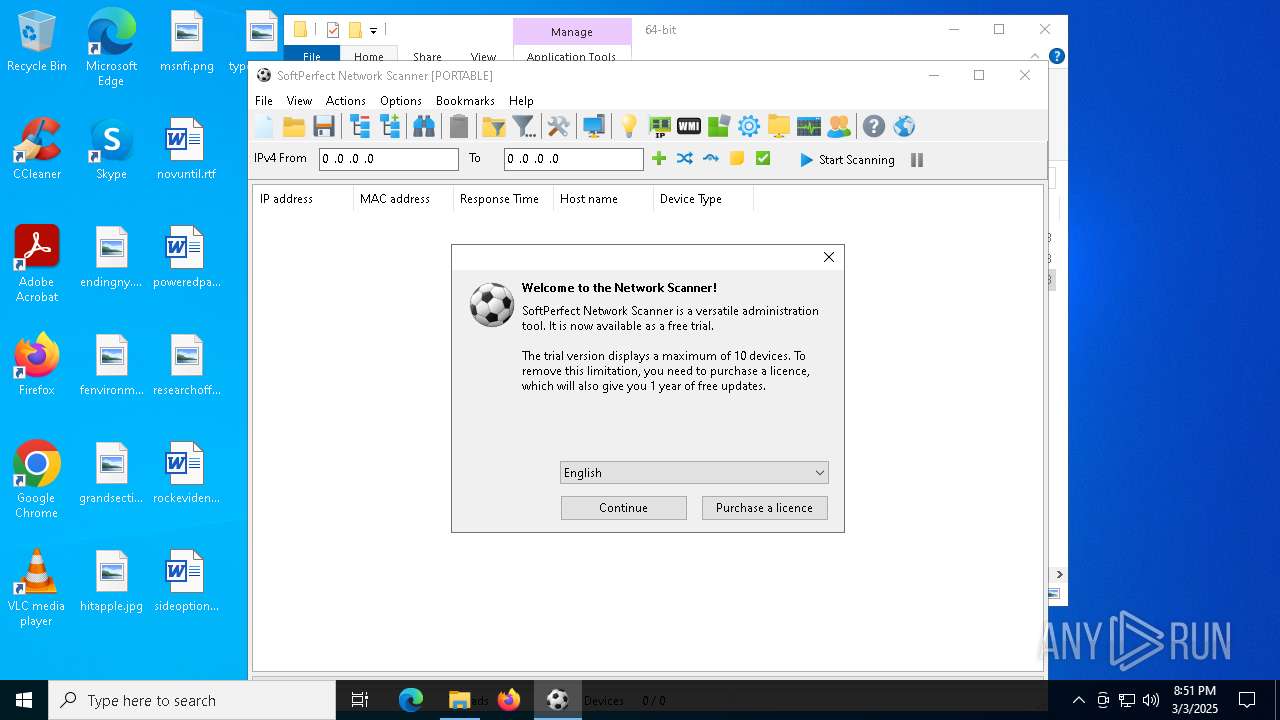
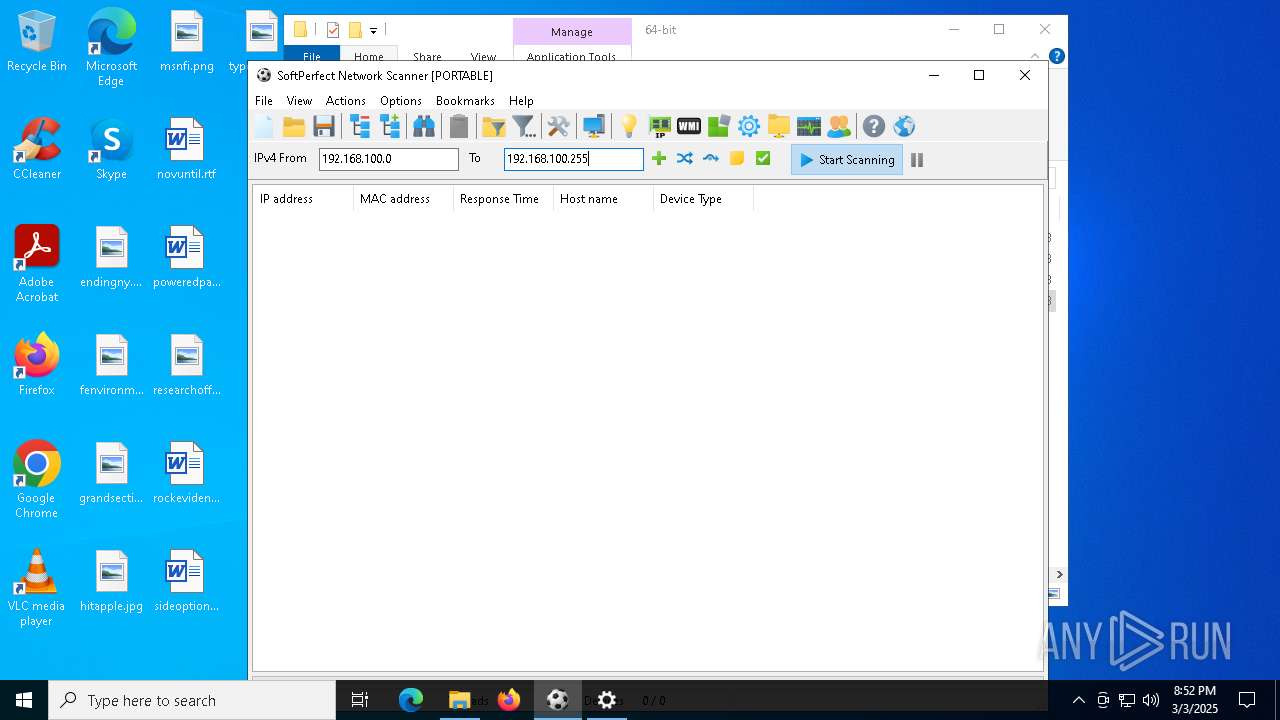
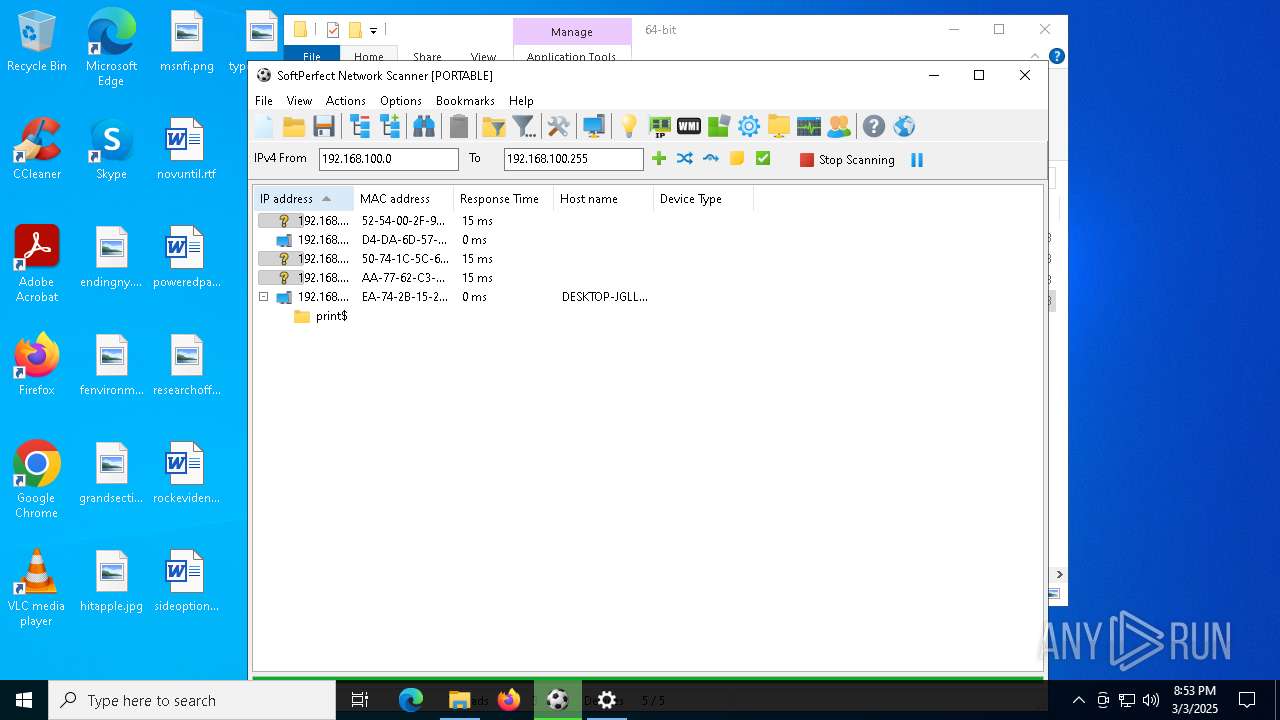
| File name: | netscan_portable.zip |
| Full analysis: | https://app.any.run/tasks/94f4bfce-6a20-4f37-84e2-1fe756a762e0 |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2025, 20:51:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 16291DBBA3C2554F0ACB56D34F8284DB |
| SHA1: | 86E24F237815B0D9B8D9F2BB5CF563F5F0C3A322 |
| SHA256: | 3557FA22D2085567288ECD8AE5758DFDECB44CB8619E7D675E2AC562AFFBFCB2 |
| SSDEEP: | 98304:H+tNzPtjg6rtwiLauzXalZc9RX2pMEErRhKNWCrwMuTAGWp5QiZtGn5TMZN6LlXO:1/SiprTViKdeYdfExrmSHI |
MALICIOUS
Executing a file with an untrusted certificate
- netscan.exe (PID: 7196)
SUSPICIOUS
There is functionality for communication over UDP network (YARA)
- netscan.exe (PID: 7196)
There is functionality for taking screenshot (YARA)
- netscan.exe (PID: 7196)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 2284)
Uses pipe srvsvc via SMB (transferring data)
- netscan.exe (PID: 7196)
INFO
Checks supported languages
- netscan.exe (PID: 7196)
- ShellExperienceHost.exe (PID: 2284)
- SystemSettings.exe (PID: 5332)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7404)
The sample compiled with english language support
- WinRAR.exe (PID: 7404)
Manual execution by a user
- netscan.exe (PID: 7196)
Reads the computer name
- ShellExperienceHost.exe (PID: 2284)
- netscan.exe (PID: 7196)
- SystemSettings.exe (PID: 5332)
Compiled with Borland Delphi (YARA)
- netscan.exe (PID: 7196)
Reads the machine GUID from the registry
- SystemSettings.exe (PID: 5332)
Disables trace logs
- SystemSettings.exe (PID: 5332)
Reads the software policy settings
- slui.exe (PID: 7560)
- SystemSettings.exe (PID: 5332)
- slui.exe (PID: 7744)
Checks proxy server information
- slui.exe (PID: 7744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (60) |
|---|---|---|
| .zip | | | ZIP compressed archive (40) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:28 09:44:00 |
| ZipCRC: | 0xb1e1cfc5 |
| ZipCompressedSize: | 6300806 |
| ZipUncompressedSize: | 16366872 |
| ZipFileName: | 64-bit/netscan.exe |
Total processes
144
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2284 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7180 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
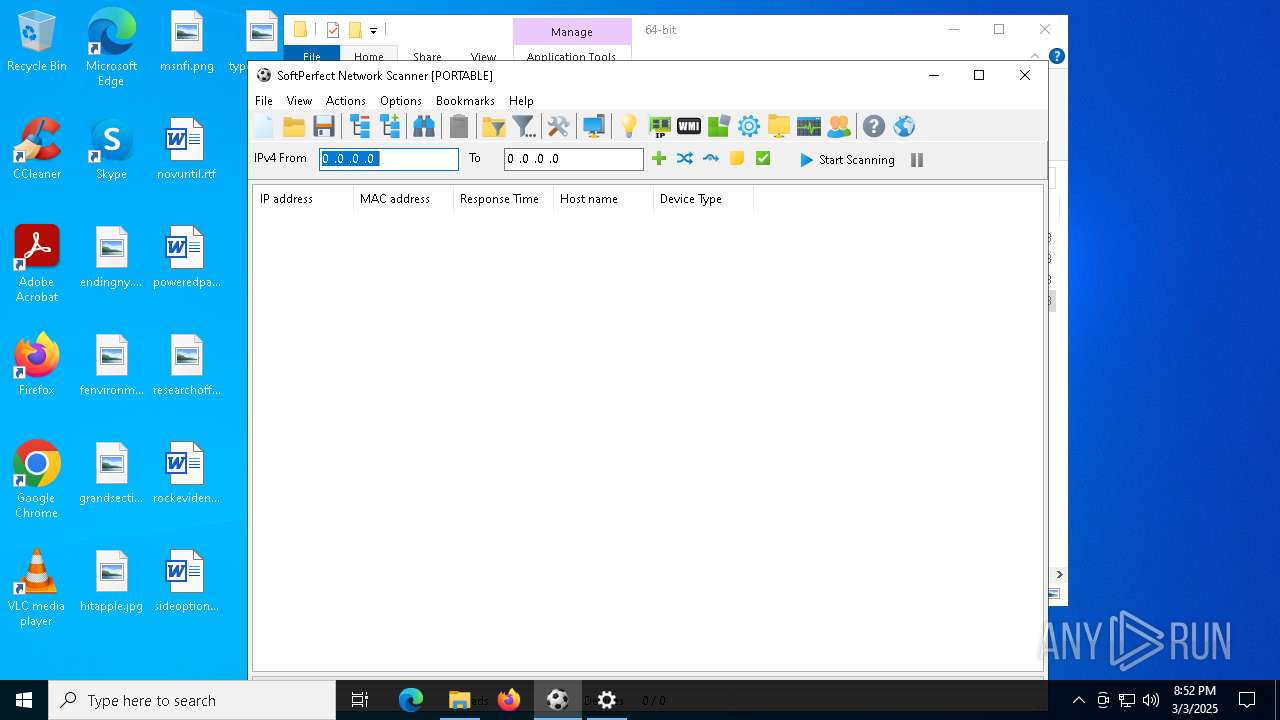
| 7196 | "C:\Users\admin\Desktop\64-bit\netscan.exe" | C:\Users\admin\Desktop\64-bit\netscan.exe | explorer.exe | ||||||||||||
User: admin Company: SoftPerfect Pty Ltd Integrity Level: MEDIUM Description: Application for scanning networks Version: 8.2.3.0 Modules
| |||||||||||||||
| 7404 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\netscan_portable.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7528 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7560 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7744 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 071
Read events
7 048
Write events
23
Delete events
0
Modification events
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\netscan_portable.zip | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
3
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5332 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\f18460fded109990.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7404.41345\64-bit\libsmb2.dll | executable | |
MD5:BF655300998BC4DA0604F833190B3DE7 | SHA256:5B15D8AB73DE1619CB8EC31F0F015A3FDFB5B3F25FB14827D167D6F0C3D80233 | |||
| 7196 | netscan.exe | C:\Users\admin\Desktop\64-bit\netscan.dbm-journal | binary | |
MD5:F486014A2DEF751780FFE4827672901B | SHA256:7512B6796D0490A80F9D2D8C30F94177940E54D861F7ECFC073E4B812E6EB5A0 | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7404.41345\64-bit\libsmi2.dll | executable | |
MD5:FE3345D78EC8D8160318DE0B7F0F868B | SHA256:ABF1CDE6346970B76A34C143250AC6F2A673463A08AC95B577466FED81A3C9EC | |||
| 7404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7404.41345\64-bit\netscan.exe | executable | |
MD5:7388E44F27B8E88EC23D571B4DFF2D7F | SHA256:45F68843D9EB87606F197CA8BBC2D1DF6D2E3109947B1E816C78F5A9B4DD222A | |||
| 5332 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7IHI68V6KNMEANX7PGIJ.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 5332 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\f18460fded109990.customDestinations-ms~RF113853.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
75
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7860 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5256 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5256 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7860 | backgroundTaskHost.exe | 20.74.19.45:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7860 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4156 | SystemSettings.exe | 92.123.104.6:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |