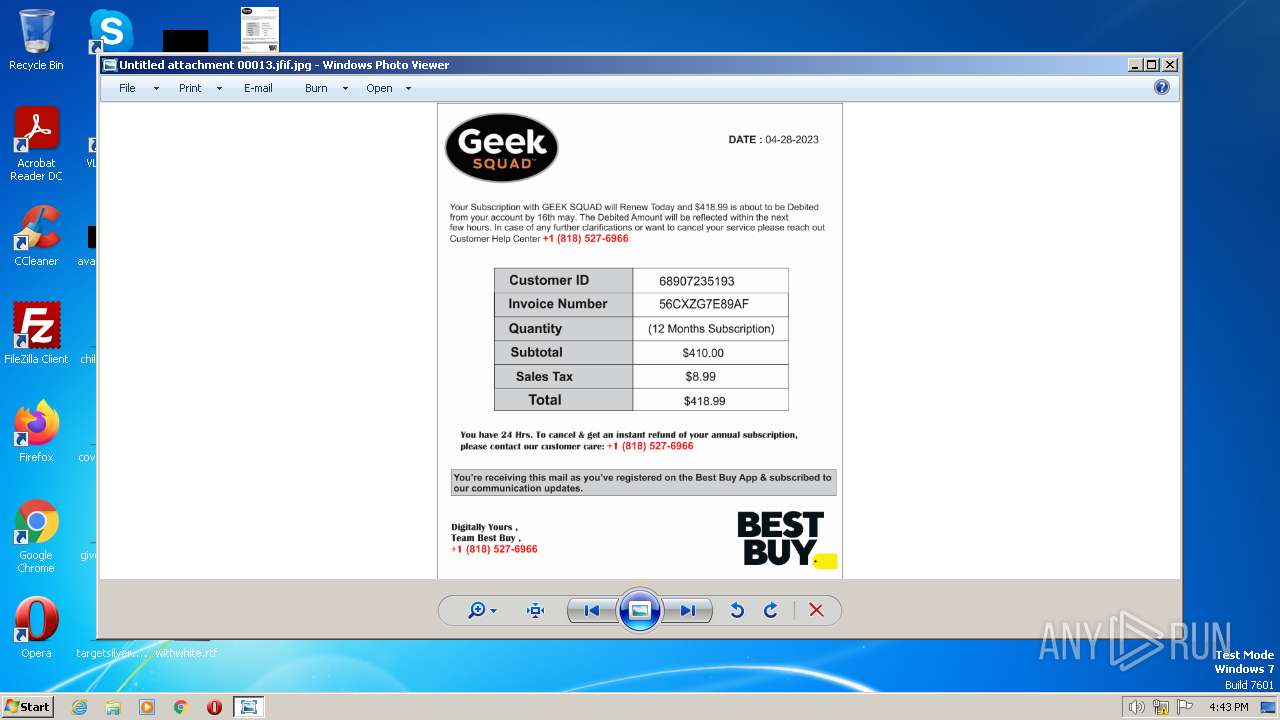
| File name: | Untitled attachment 00013.jfif |
| Full analysis: | https://app.any.run/tasks/aa410247-e5d4-49f3-8d66-d68c0ab4b877 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2023, 15:43:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | image/jpeg |
| File info: | JPEG image data, JFIF standard 1.01, resolution (DPI), density 300x300, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=4], baseline, precision 8, 2500x2940, components 4 |
| MD5: | 8585F3C454617DD519F757E45DC6F0C0 |
| SHA1: | E2764C41ED6E118BB21596E053913054988F6057 |
| SHA256: | 3555BA8BBE586DF1E260CE2234A57CE60AEAFEA68120D6A185C5610E5085C97B |
| SSDEEP: | 49152:q/FluraLpM+FWnklp8IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIZU8vA:qburmMnklpIU8o |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 3944)
INFO
The process checks LSA protection
- dllhost.exe (PID: 1964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF-EXIF JPEG Bitmap (38.4) |
|---|---|---|
| .jpg | | | JFIF JPEG bitmap (30.7) |
| .jpg | | | JPEG bitmap (23) |
| .mp3 | | | MP3 audio (7.6) |
EXIF
Composite
| SubSecDateTimeOriginal: | 2023:04:12 02:16:54.05 |
|---|---|
| SubSecCreateDate: | 2023:04:12 02:16:54.05 |
| Megapixels: | 7.3 |
| ImageSize: | 2500x2940 |
XMP
| Creator: | ADDY |
|---|---|
| CreateDate: | 2023:04:12 02:16:54.051 |
| About: | uuid:faf5bdd5-ba3d-11da-ad31-d33d75182f1b |
Photoshop
| DisplayedUnitsY: | inches |
|---|---|
| YResolution: | 300 |
| DisplayedUnitsX: | inches |
| XResolution: | 300 |
ICC_Profile
| Gamut: | (Binary data 37009 bytes, use -b option to extract) |
|---|---|
| BToA2: | (Binary data 145588 bytes, use -b option to extract) |
| BToA1: | (Binary data 145588 bytes, use -b option to extract) |
| BToA0: | (Binary data 145588 bytes, use -b option to extract) |
| AToB1: | (Binary data 41478 bytes, use -b option to extract) |
| AToB2: | (Binary data 41478 bytes, use -b option to extract) |
| AToB0: | (Binary data 41478 bytes, use -b option to extract) |
| MediaWhitePoint: | 0.7084 0.73595 0.57104 |
| ProfileCopyright: | Copyright 2000 Adobe Systems, Inc. |
| ProfileDescription: | U.S. Web Coated (SWOP) v2 |
| ProfileID: | - |
| ProfileCreator: | Adobe Systems Inc. |
| ConnectionSpaceIlluminant: | 0.9642 1 0.82491 |
| RenderingIntent: | Perceptual |
| DeviceAttributes: | Reflective, Glossy, Positive, Color |
| DeviceModel: | - |
| DeviceManufacturer: | Adobe Systems Inc. |
| CMMFlags: | Not Embedded, Independent |
| PrimaryPlatform: | Apple Computer Inc. |
| ProfileFileSignature: | acsp |
| ProfileDateTime: | 2000:07:26 05:41:53 |
| ProfileConnectionSpace: | Lab |
| ColorSpaceData: | CMYK |
| ProfileClass: | Output Device Profile |
| ProfileVersion: | 2.1.0 |
| ProfileCMMType: | Adobe Systems Inc. |
EXIF
| Padding: | (Binary data 2060 bytes, use -b option to extract) |
|---|---|
| XPAuthor: | ADDY |
| SubSecTimeDigitized: | 05 |
| SubSecTimeOriginal: | 05 |
| CreateDate: | 2023:04:12 02:16:54 |
| DateTimeOriginal: | 2023:04:12 02:16:54 |
| Artist: | ADDY |
APP14
| ColorTransform: | Unknown (RGB or CMYK) |
|---|---|
| APP14Flags1: | (none) |
| APP14Flags0: | (none) |
| DCTEncodeVersion: | 100 |
JFIF
| YResolution: | 300 |
|---|---|
| XResolution: | 300 |
| ResolutionUnit: | inches |
| JFIFVersion: | 1.01 |
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1964 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3944 | "C:\Windows\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen "C:\Users\admin\Desktop\Untitled attachment 00013.jfif.jpg" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
246
Read events
244
Write events
2
Delete events
0
Modification events
| (PID) Process: | (3944) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1964) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3408 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |