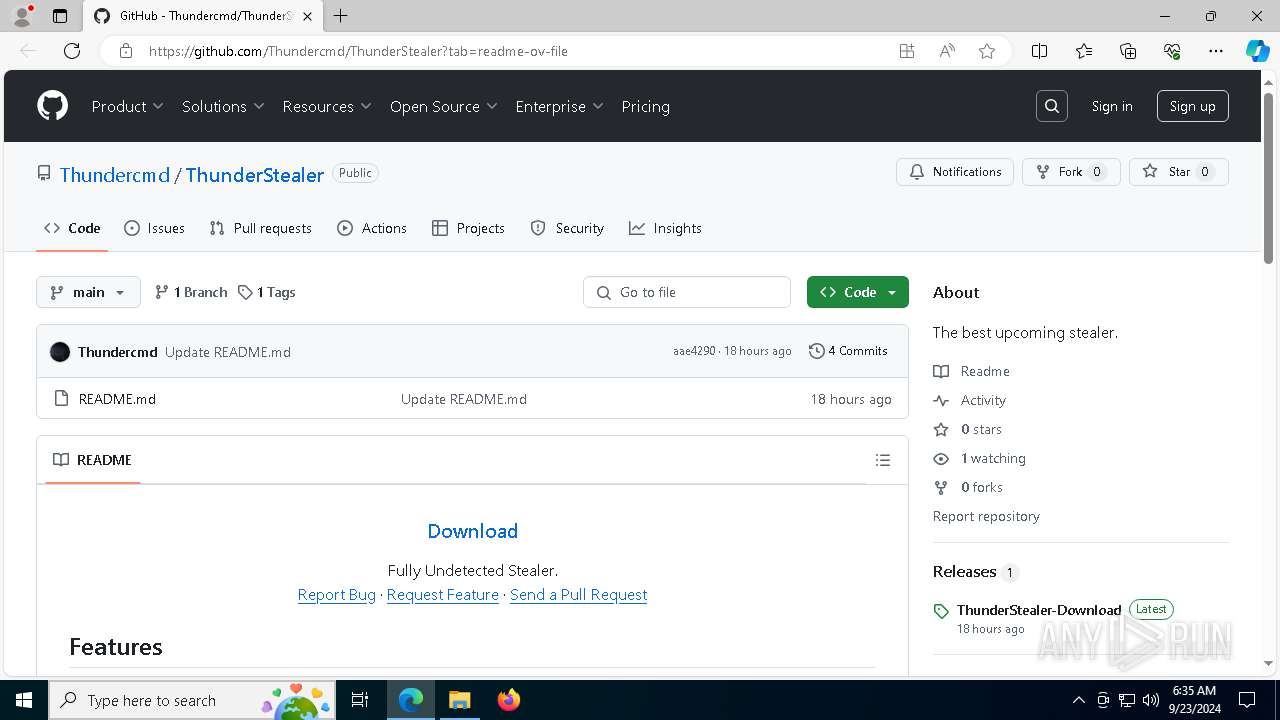
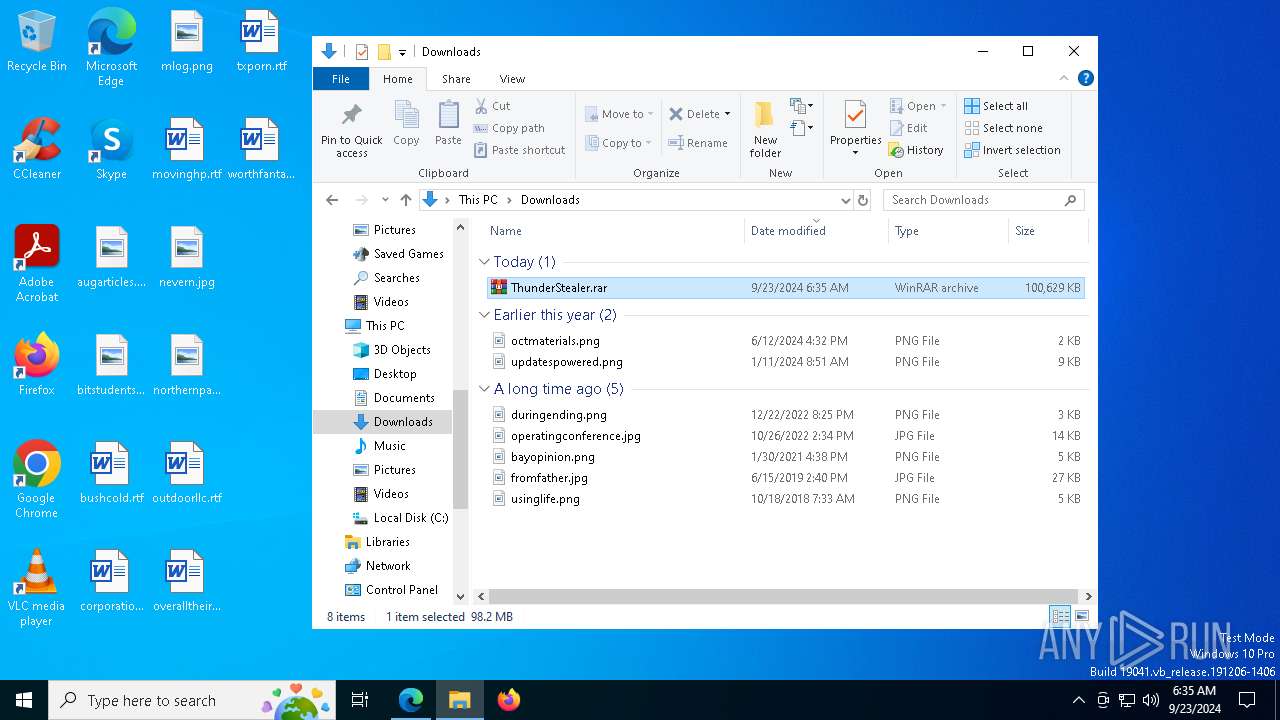
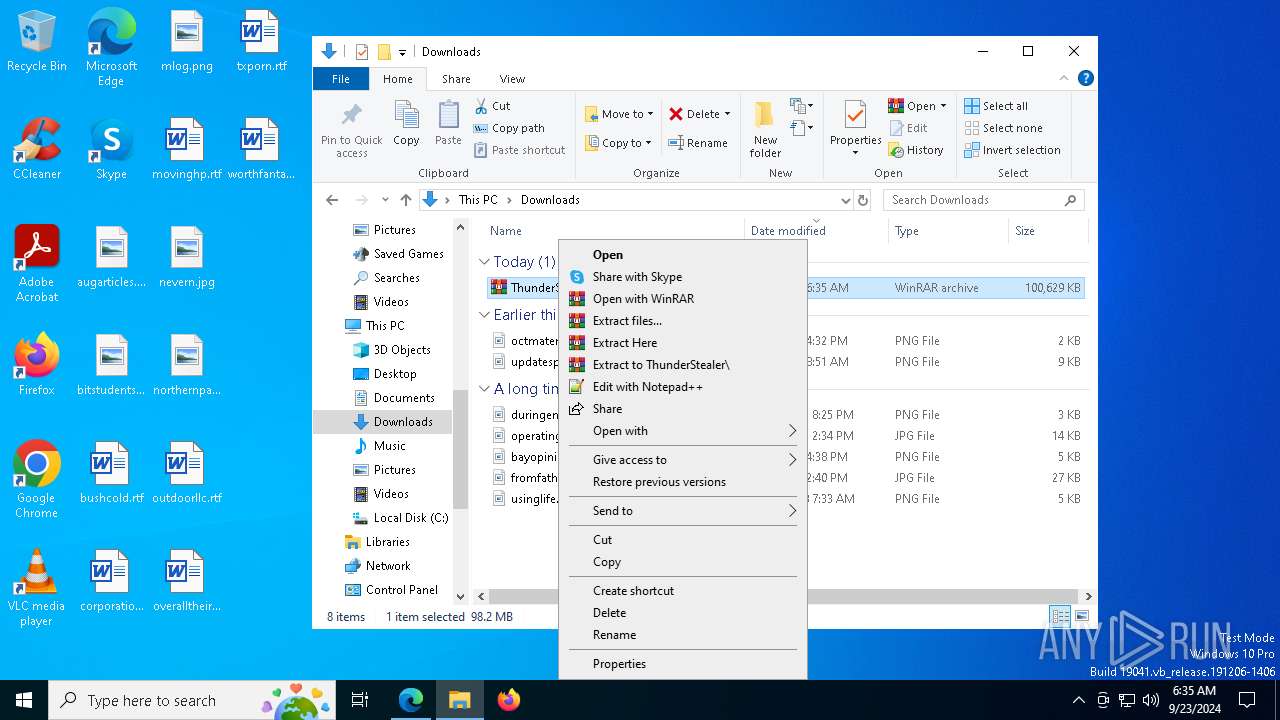
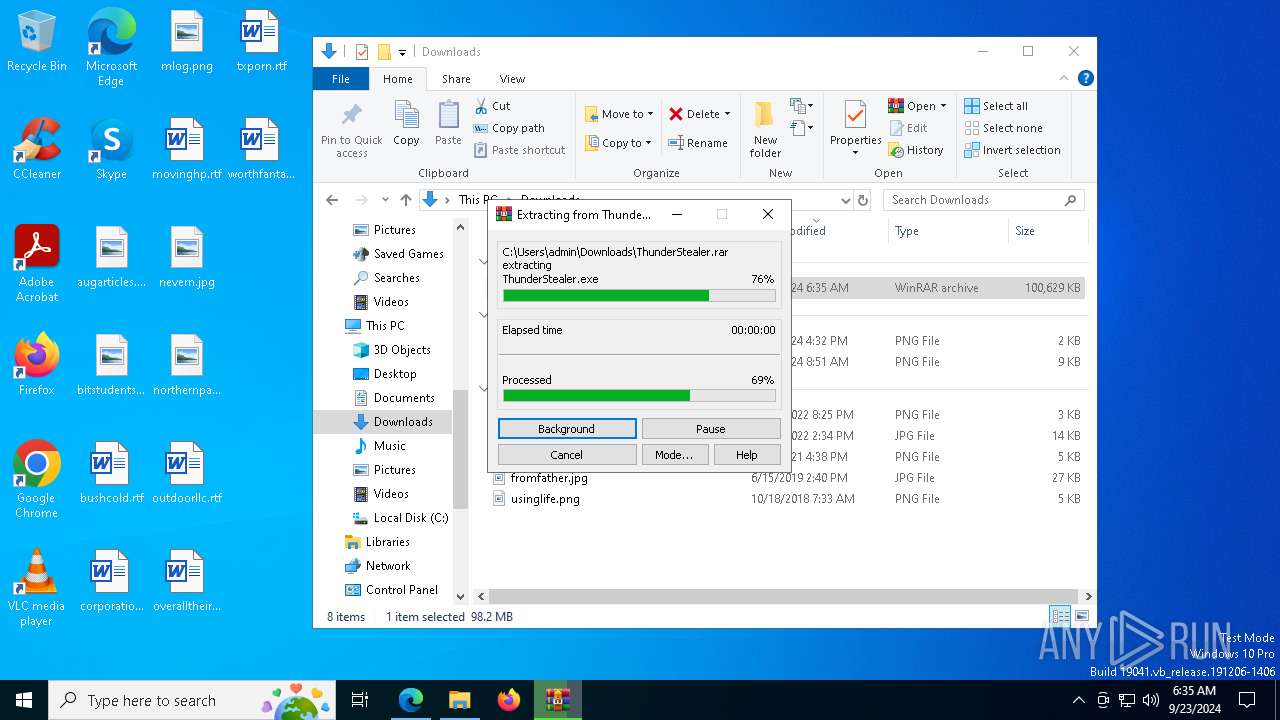
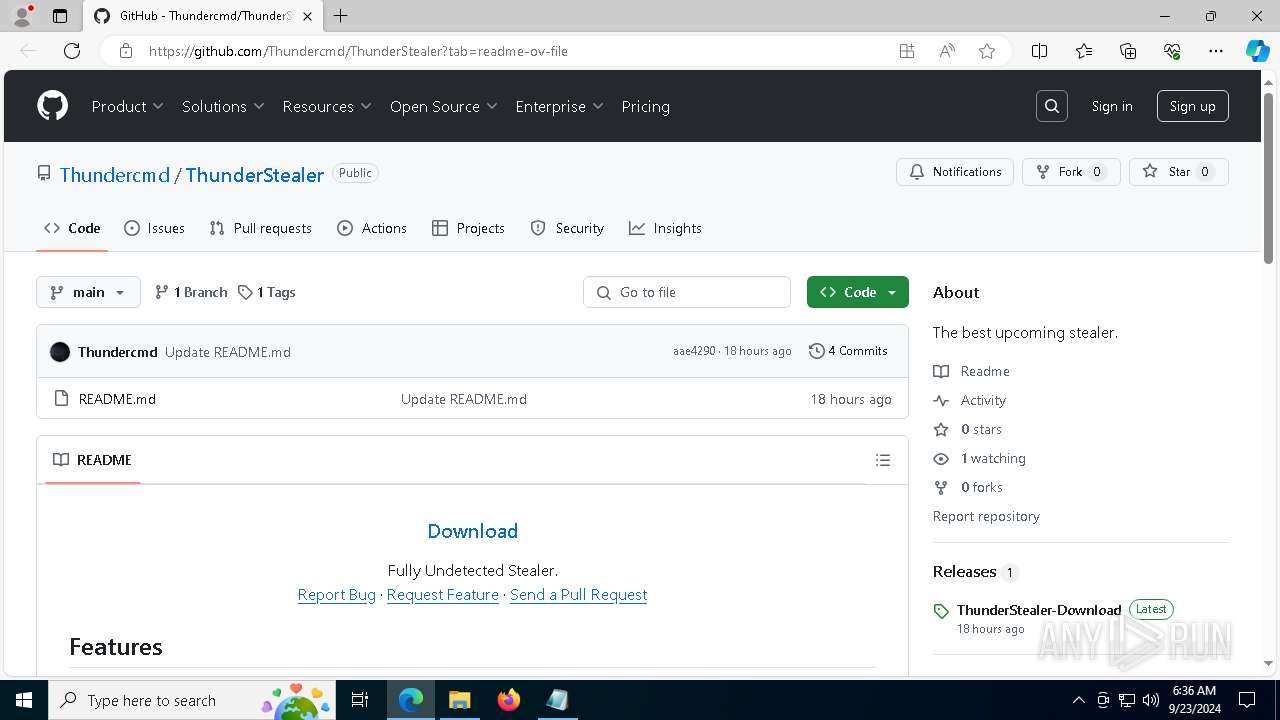
| URL: | https://github.com/Thundercmd/ThunderStealer |
| Full analysis: | https://app.any.run/tasks/551e6846-4658-412e-82bc-970361cc5bf9 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | September 23, 2024, 06:34:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 24DA265E23EA140936F41A80705E69E8 |
| SHA1: | 5ED8FB8B1ACD514BDB83E7CBBAD8BF5CAECD16F5 |
| SHA256: | 3554C3ACCF29A44F054A026D46618A42DDCD1519D14118E76893C5C90D0C2192 |
| SSDEEP: | 3:N8tEdSwGey2c:2uh3yt |
MALICIOUS
DISCORDGRABBER has been detected (YARA)
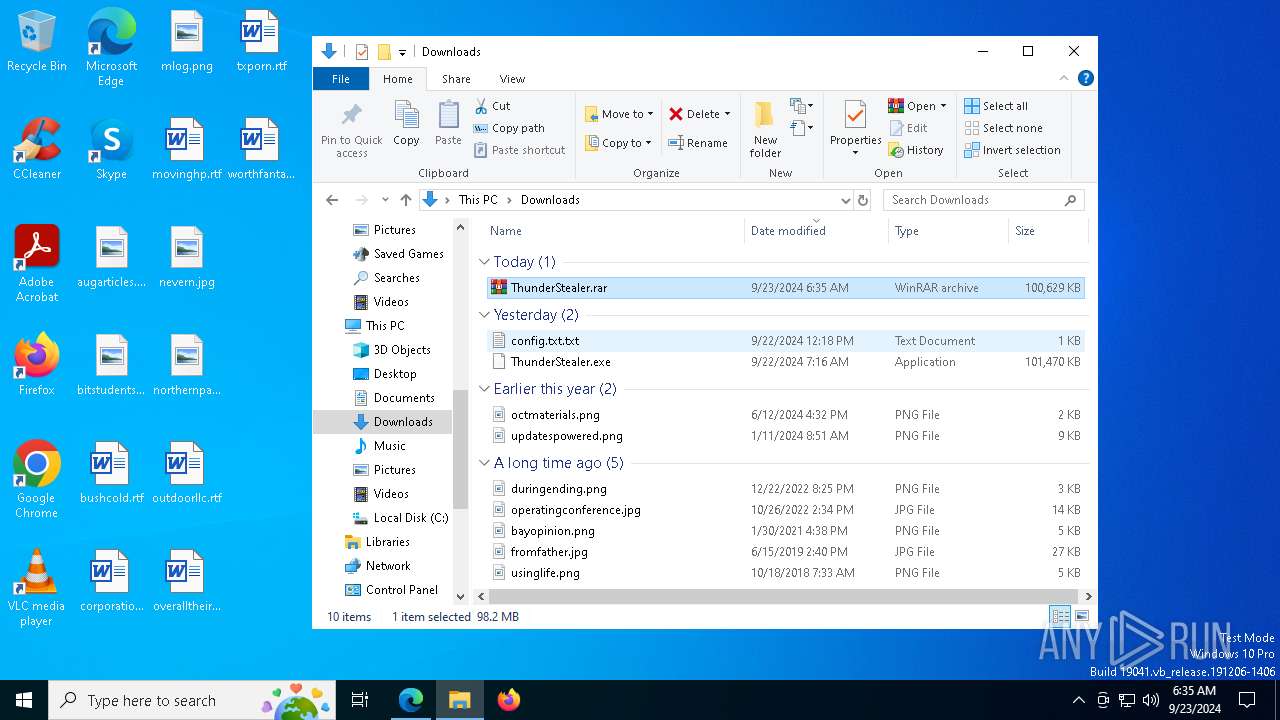
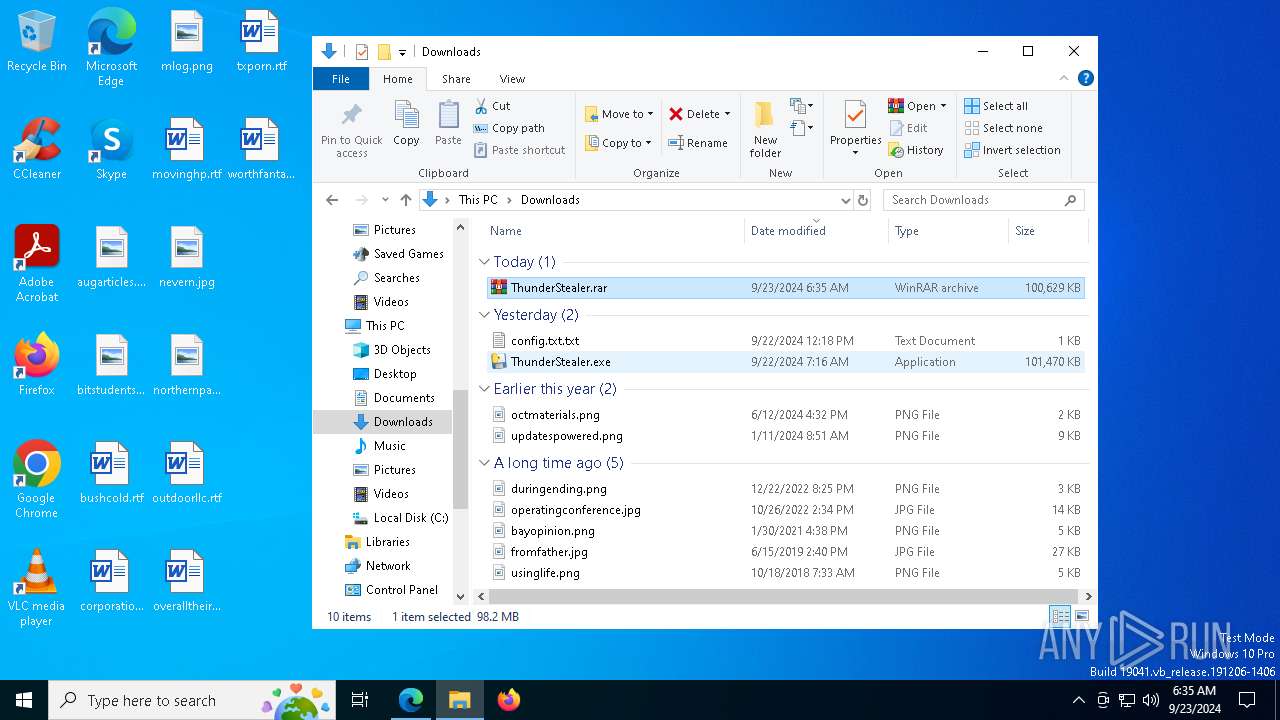
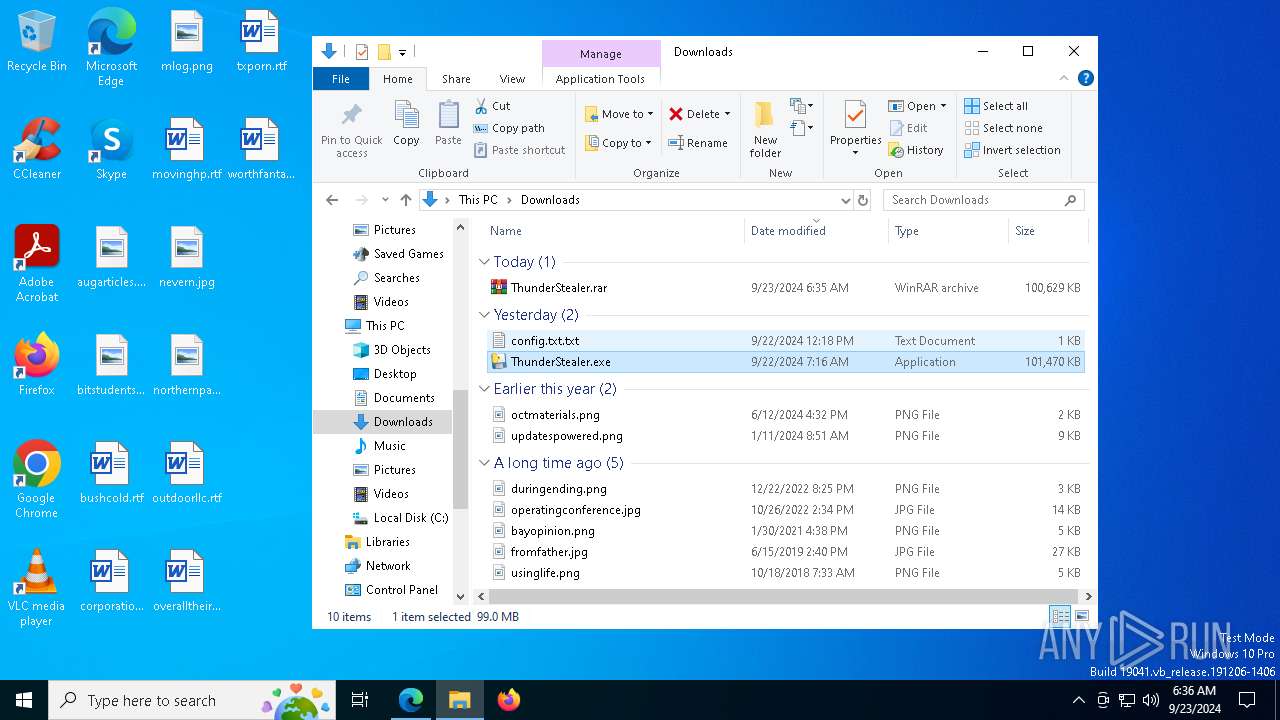
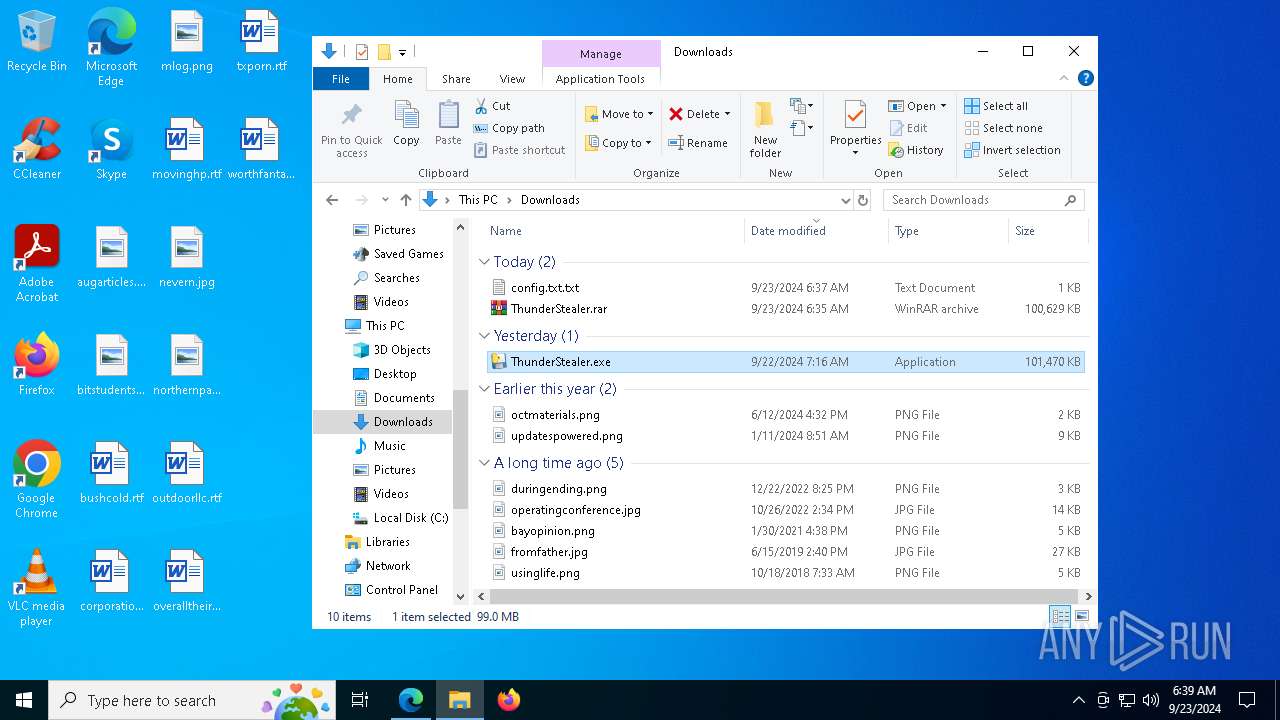
- ThunderStealer.exe (PID: 7304)
- ThunderStealer.exe (PID: 5212)
- ThunderStealer.exe (PID: 4520)
SUSPICIOUS
Process drops python dynamic module
- ThunderStealer.exe (PID: 7672)
- ThunderStealer.exe (PID: 6648)
- ThunderStealer.exe (PID: 7912)
Executable content was dropped or overwritten
- ThunderStealer.exe (PID: 7672)
- ThunderStealer.exe (PID: 6648)
- ThunderStealer.exe (PID: 7912)
Process drops legitimate windows executable
- ThunderStealer.exe (PID: 7672)
- ThunderStealer.exe (PID: 6648)
- ThunderStealer.exe (PID: 7912)
The process drops C-runtime libraries
- ThunderStealer.exe (PID: 7672)
- ThunderStealer.exe (PID: 6648)
- ThunderStealer.exe (PID: 7912)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3476)
- cmd.exe (PID: 5160)
- cmd.exe (PID: 7820)
- cmd.exe (PID: 6392)
- cmd.exe (PID: 4288)
- cmd.exe (PID: 6296)
Starts CMD.EXE for commands execution
- ThunderStealer.exe (PID: 7304)
- ThunderStealer.exe (PID: 5212)
- ThunderStealer.exe (PID: 4520)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6592)
- cmd.exe (PID: 7456)
- cmd.exe (PID: 5768)
Possible usage of Discord/Telegram API has been detected (YARA)
- ThunderStealer.exe (PID: 7304)
- ThunderStealer.exe (PID: 5212)
- ThunderStealer.exe (PID: 4520)
Application launched itself
- ThunderStealer.exe (PID: 6648)
- ThunderStealer.exe (PID: 7672)
- ThunderStealer.exe (PID: 7912)
Checks for external IP
- ThunderStealer.exe (PID: 7304)
- ThunderStealer.exe (PID: 5212)
INFO
Checks supported languages
- identity_helper.exe (PID: 7428)
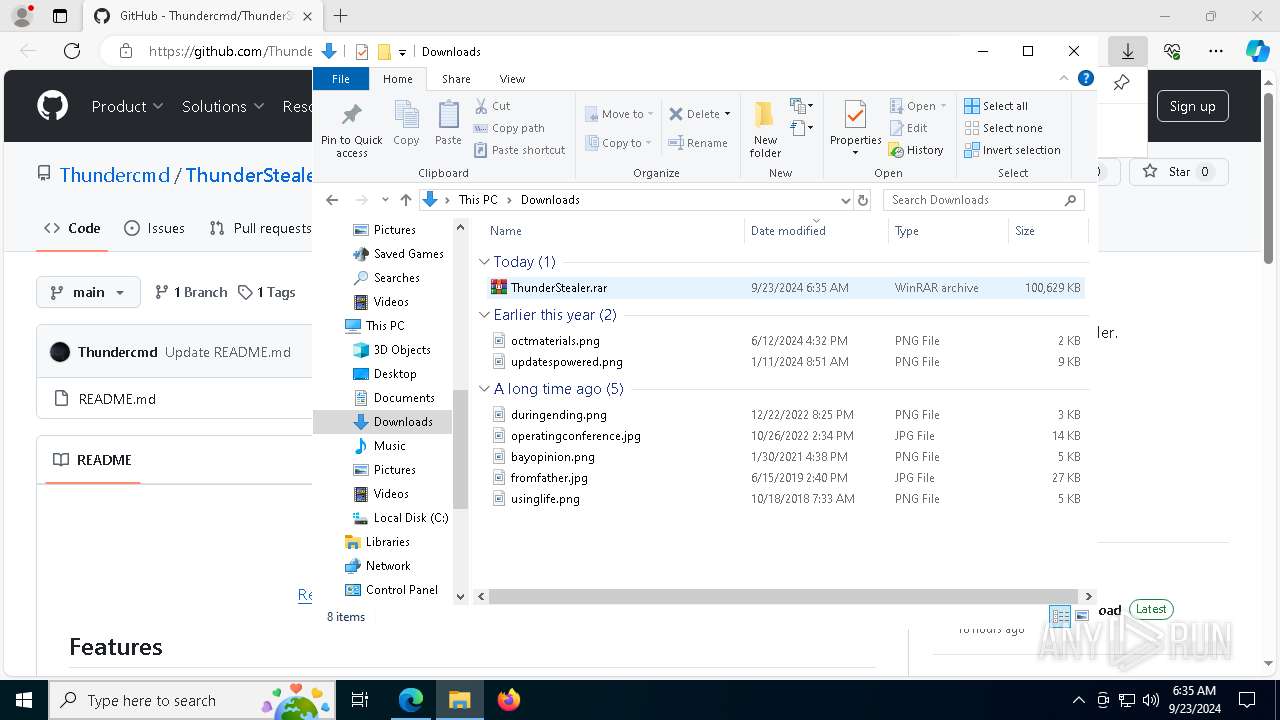
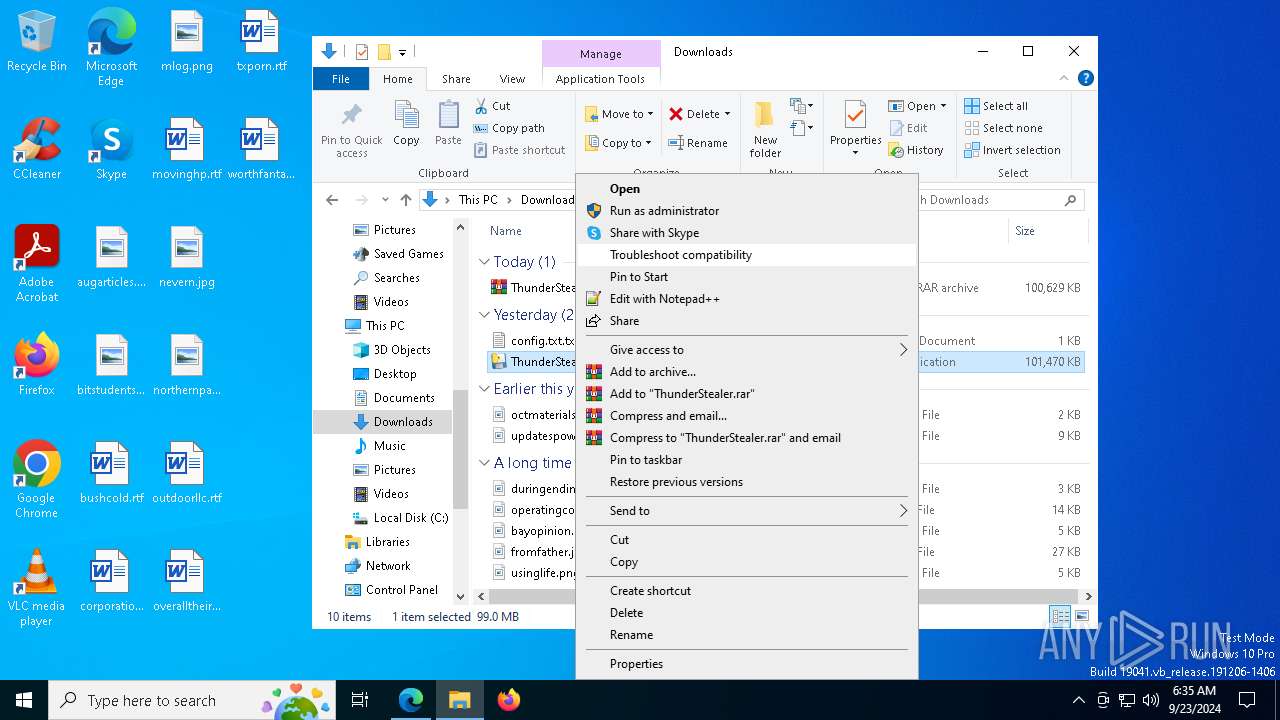
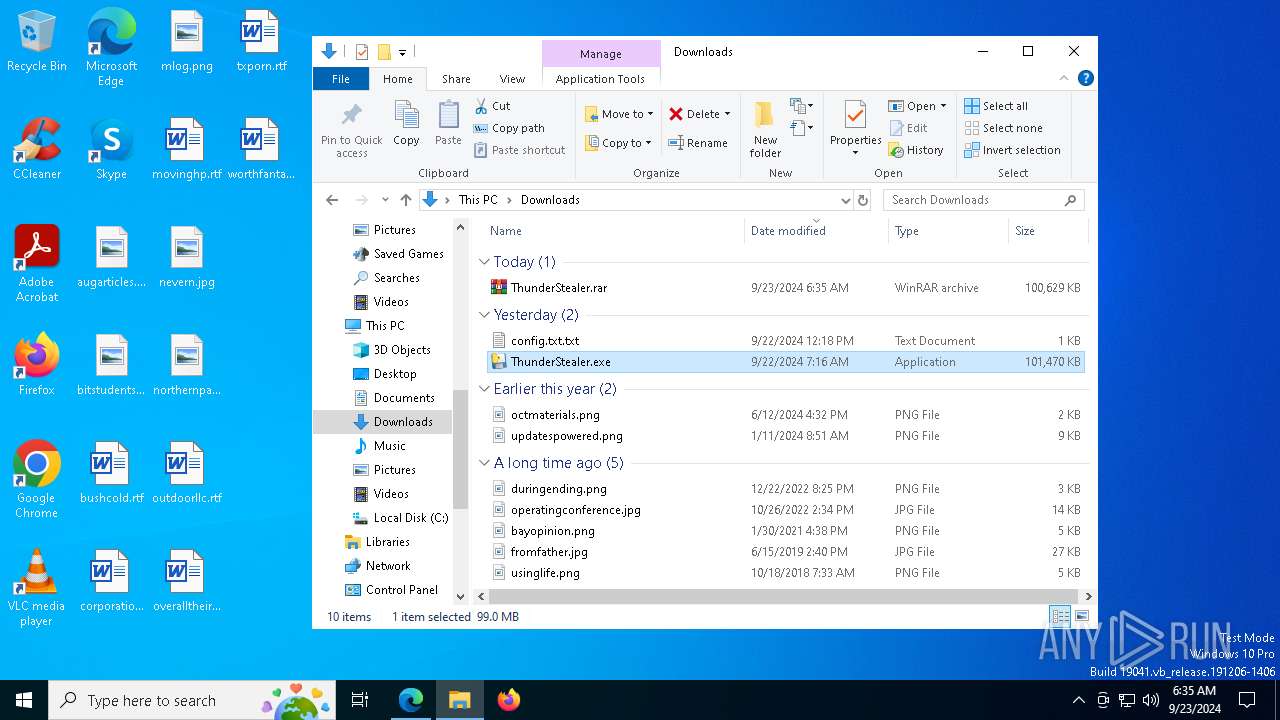
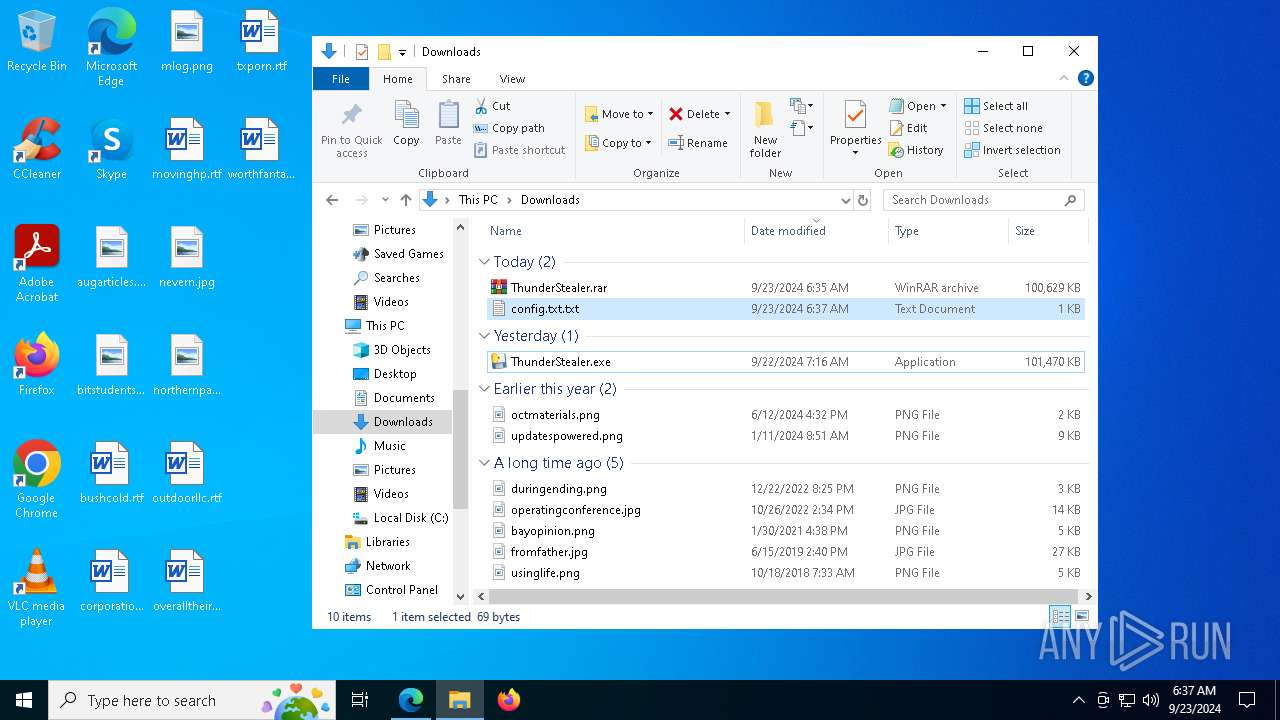
Manual execution by a user
- WinRAR.exe (PID: 7756)
- ThunderStealer.exe (PID: 7672)
- ThunderStealer.exe (PID: 6648)
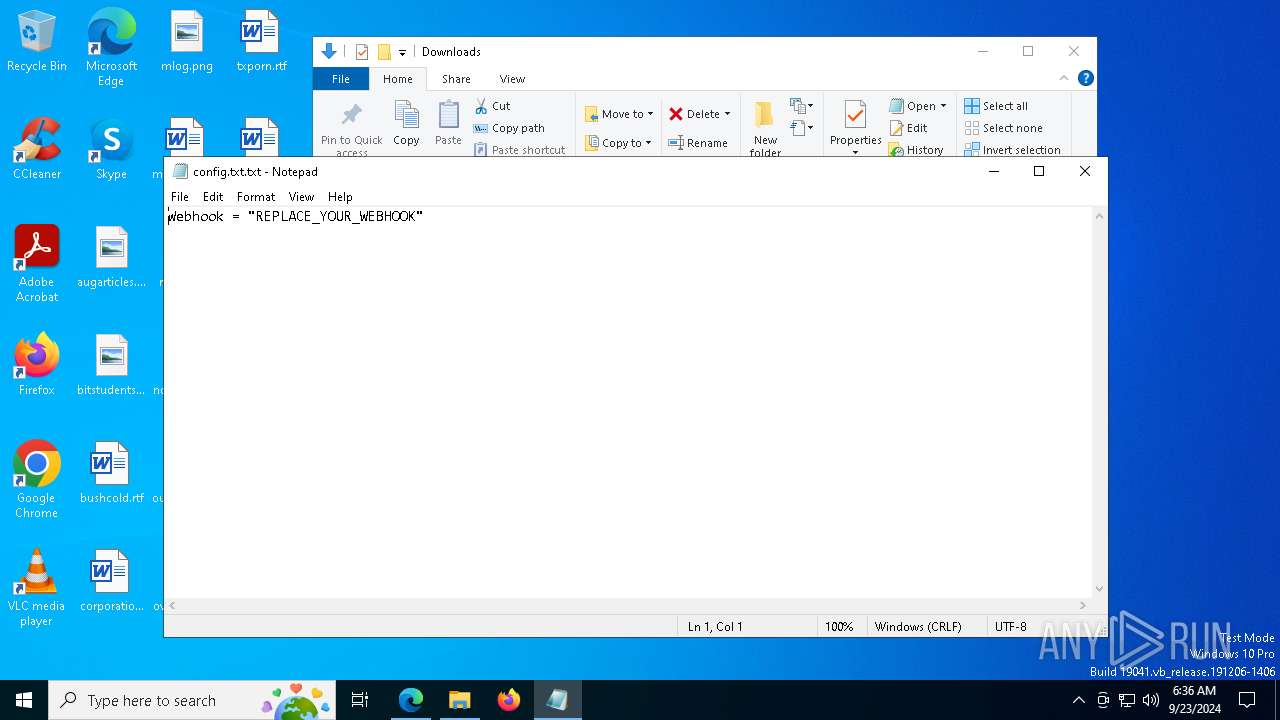
- notepad.exe (PID: 5048)
- ThunderStealer.exe (PID: 7912)
Reads the computer name
- identity_helper.exe (PID: 7428)
The process uses the downloaded file
- msedge.exe (PID: 8012)
- WinRAR.exe (PID: 7756)
PyInstaller has been detected (YARA)
- ThunderStealer.exe (PID: 7672)
- ThunderStealer.exe (PID: 6648)
- ThunderStealer.exe (PID: 7304)
- ThunderStealer.exe (PID: 5212)
- ThunderStealer.exe (PID: 7912)
- ThunderStealer.exe (PID: 4520)
Application launched itself
- msedge.exe (PID: 6452)
Executable content was dropped or overwritten
- msedge.exe (PID: 644)
Attempting to use instant messaging service
- ThunderStealer.exe (PID: 7304)
- ThunderStealer.exe (PID: 5212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7304) ThunderStealer.exe
Discord-Webhook-Tokens (1)1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Discord-Info-Links
1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Get Webhook Infohttps://discord.com/api/webhooks/1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments
id1287663993577537598
filenameBrowser_admin.zip
size3905
urlhttps://cdn.discordapp.com/attachments/1287308085936783371/1287663993577537598/Browser_admin.zip?ex=66f25e0b&is=66f10c8b&hm=cdc49e99baa9f8b8713a0a103ffa515bb4d85bd5f43368501c4c9179074ba7d8&
proxy_urlhttps://media.discordapp.net/attachments/1287308085936783371/1287663993577537598/Browser_admin.zip?ex=66f25e0b&is=66f10c8b&hm=cdc49e99baa9f8b8713a0a103ffa515bb4d85bd5f43368501c4c9179074ba7d8&
content_typeapplication/zip
embeds
typerich
titleBrowser Steal `admin "193.176.86.40"`:
descriptionFound In **Google Chrome**, **Microsoft Edge**:```📂 - Browser_admin
├── 📄 - Cards_admin.txt (0.27 kb)
├── 📄 - Cookies_admin.txt (0.13 kb)
├── 📄 - Downloads_admin.txt (0.40 kb)
├── 📄 - History_admin.txt (2.18 kb)
└── 📄 - Passwords_admin.txt (0.27 kb)```
color11011333
footer
textRedTiger Ste4ler | https://github.com/loxyteck/RedTiger-Tools
icon_urlhttps://cdn.discordapp.com/attachments/1268900329605300234/1276010081665683497/RedTiger-Logo.png?ex=66f2287e&is=66f0d6fe&hm=cf60ae6097801b901108daf364a1fc4ed6c87589ef1ee9757f59aa6673bfc04a&
proxy_icon_urlhttps://media.discordapp.net/attachments/1268900329605300234/1276010081665683497/RedTiger-Logo.png?ex=66f2287e&is=66f0d6fe&hm=cf60ae6097801b901108daf364a1fc4ed6c87589ef1ee9757f59aa6673bfc04a&
timestamp2024-09-23T06:36:59.634000+00:00
edited_timestampnull
flags0
components (0)
id1287663993263099969
channel_id1287308085936783371
author
id1287308102294569000
usernameRedTiger Ste4ler
avatarnull
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1287308102294569000
(PID) Process(5212) ThunderStealer.exe
Discord-Webhook-Tokens (1)1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Discord-Info-Links
1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Get Webhook Infohttps://discord.com/api/webhooks/1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
(PID) Process(4520) ThunderStealer.exe
Discord-Webhook-Tokens (1)1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Discord-Info-Links
1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Get Webhook Infohttps://discord.com/api/webhooks/1287308102294569000/CLMzUoBDjfe60zBpTmiTnDeNN22w250Y1991WYoLAsQpuGVS73ZqxhIDfIx17bJRVEs6
Total processes
252
Monitored processes
119
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5304 --field-trial-handle=2428,i,3742147368040796791,16250623700319271235,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5684 --field-trial-handle=2428,i,3742147368040796791,16250623700319271235,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 740 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2408 --field-trial-handle=2428,i,3742147368040796791,16250623700319271235,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 752 | C:\Windows\System32\wbem\WMIC.exe csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 880 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7140 --field-trial-handle=2428,i,3742147368040796791,16250623700319271235,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1520 --field-trial-handle=2428,i,3742147368040796791,16250623700319271235,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5660 --field-trial-handle=2428,i,3742147368040796791,16250623700319271235,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
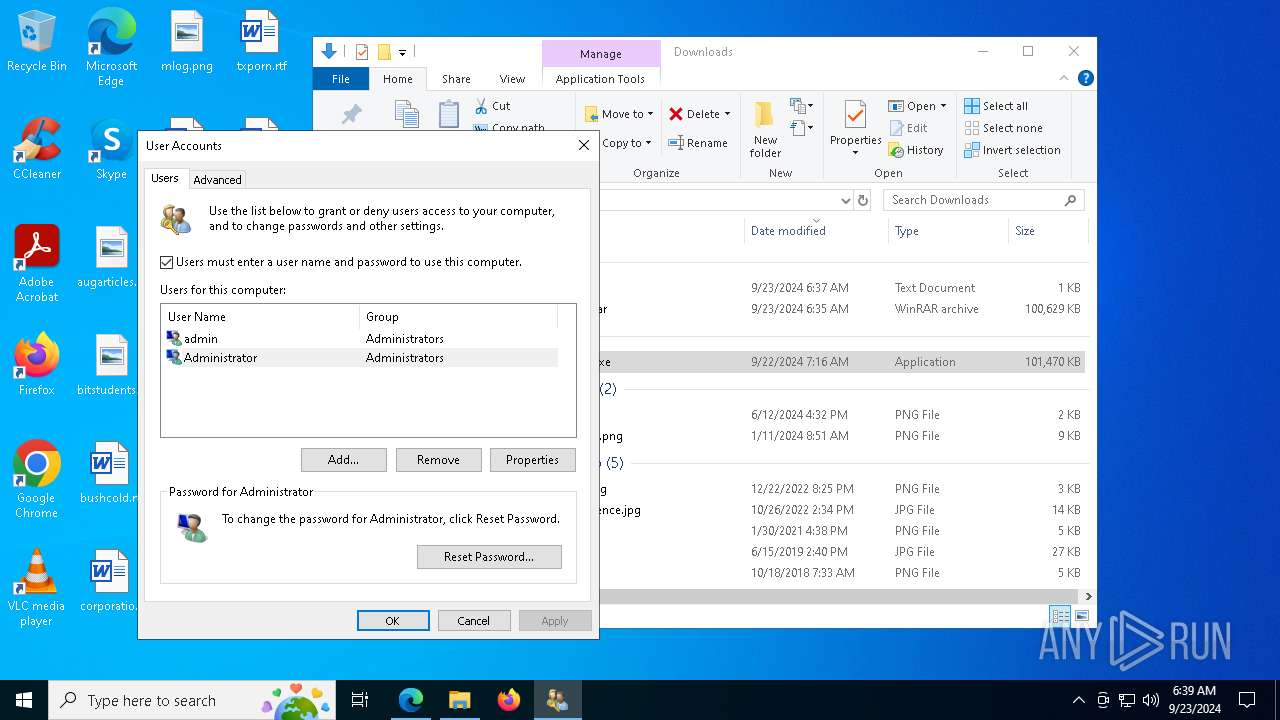
| 1792 | "C:\WINDOWS\system32\netplwiz.exe" | C:\Windows\System32\Netplwiz.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Advanced User Accounts Control Panel Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2264 | C:\Windows\System32\wbem\WMIC.exe csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
9 343
Read events
9 294
Write events
48
Delete events
1
Modification events
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 0E310ADD59812F00 | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: F5F012DD59812F00 | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328642 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9CCDC1E0-D8C6-4DFD-9AFC-830F974166C6} | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328642 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DFB73070-B8C1-4D7D-9409-A60DBC1F03BE} | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328642 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5AC75F8C-B05F-43F2-BE9E-CDA46B2A034F} | |||
| (PID) Process: | (6452) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328642 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {100DF5B9-D161-4FD6-BDE5-93264CABCFA9} | |||
Executable files
576
Suspicious files
1 129
Text files
3 422
Unknown types
109
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1fba31.TMP | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1fba7f.TMP | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1fba7f.TMP | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1fba8f.TMP | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6452 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF1fba7f.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
149
DNS requests
143
Threats
44
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2844 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1727399905&P2=404&P3=2&P4=b4%2b1UWsJSjlTkxIPyVqScVnjLiivhqSWld6uwpanJS3XSF%2bS7wqHRJh3y1U8V4oAhG7oXAMP9cxGC%2f2ffkQ3HA%3d%3d | unknown | — | — | whitelisted |
3116 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2844 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1727399905&P2=404&P3=2&P4=b4%2b1UWsJSjlTkxIPyVqScVnjLiivhqSWld6uwpanJS3XSF%2bS7wqHRJh3y1U8V4oAhG7oXAMP9cxGC%2f2ffkQ3HA%3d%3d | unknown | — | — | whitelisted |
2844 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1727399905&P2=404&P3=2&P4=b4%2b1UWsJSjlTkxIPyVqScVnjLiivhqSWld6uwpanJS3XSF%2bS7wqHRJh3y1U8V4oAhG7oXAMP9cxGC%2f2ffkQ3HA%3d%3d | unknown | — | — | whitelisted |
2844 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1727399905&P2=404&P3=2&P4=b4%2b1UWsJSjlTkxIPyVqScVnjLiivhqSWld6uwpanJS3XSF%2bS7wqHRJh3y1U8V4oAhG7oXAMP9cxGC%2f2ffkQ3HA%3d%3d | unknown | — | — | whitelisted |
2844 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1727399905&P2=404&P3=2&P4=b4%2b1UWsJSjlTkxIPyVqScVnjLiivhqSWld6uwpanJS3XSF%2bS7wqHRJh3y1U8V4oAhG7oXAMP9cxGC%2f2ffkQ3HA%3d%3d | unknown | — | — | whitelisted |
2844 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1727399905&P2=404&P3=2&P4=b4%2b1UWsJSjlTkxIPyVqScVnjLiivhqSWld6uwpanJS3XSF%2bS7wqHRJh3y1U8V4oAhG7oXAMP9cxGC%2f2ffkQ3HA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 52.182.143.213:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6604 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2096 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7068 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | shared |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| shared |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
github.githubassets.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
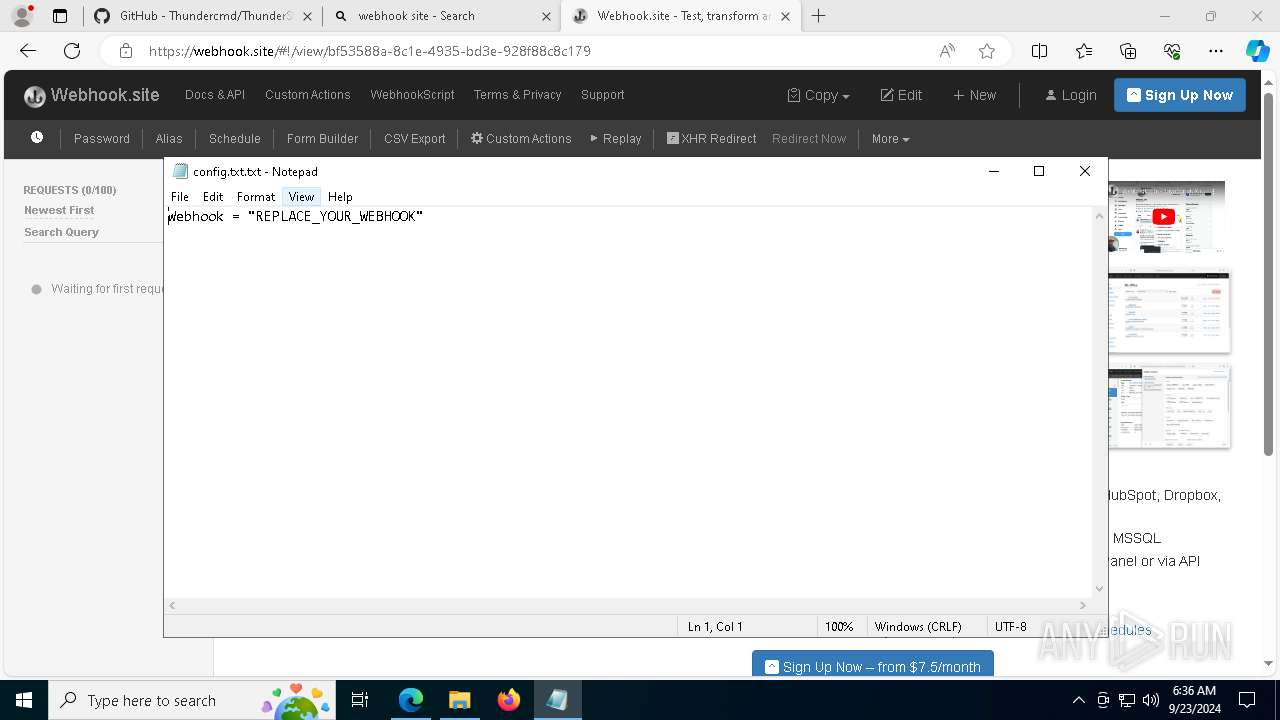
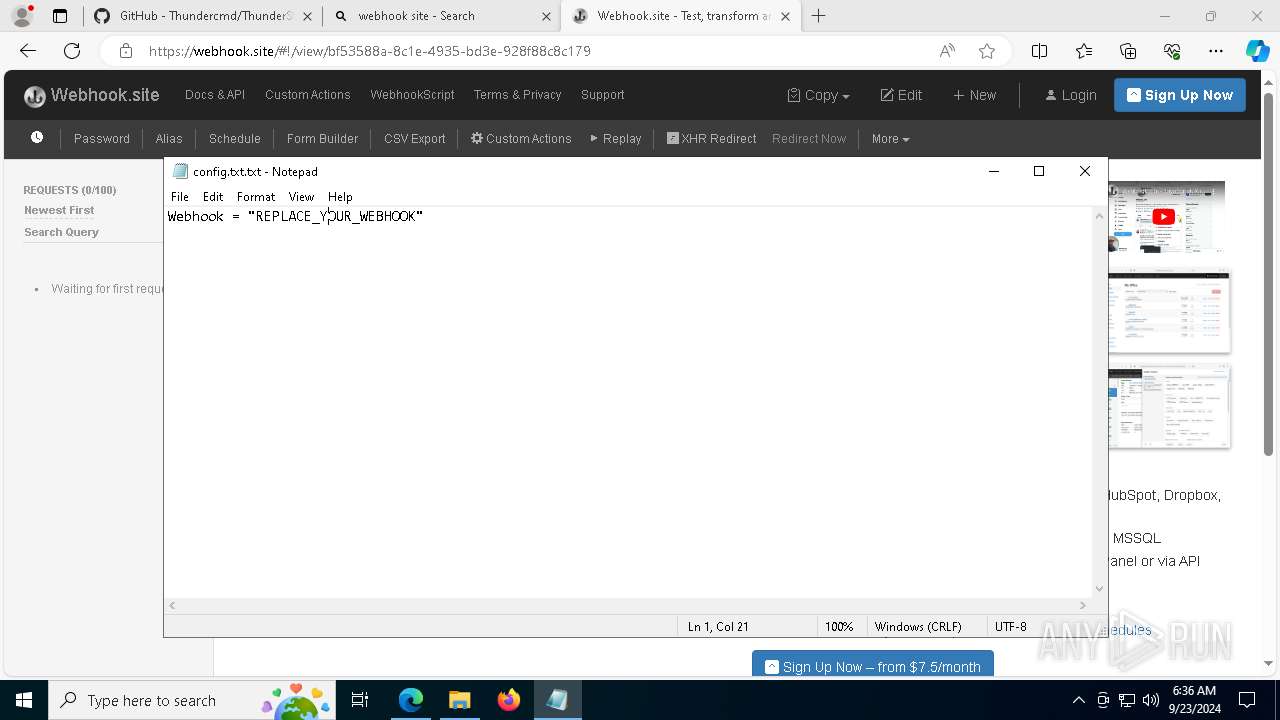
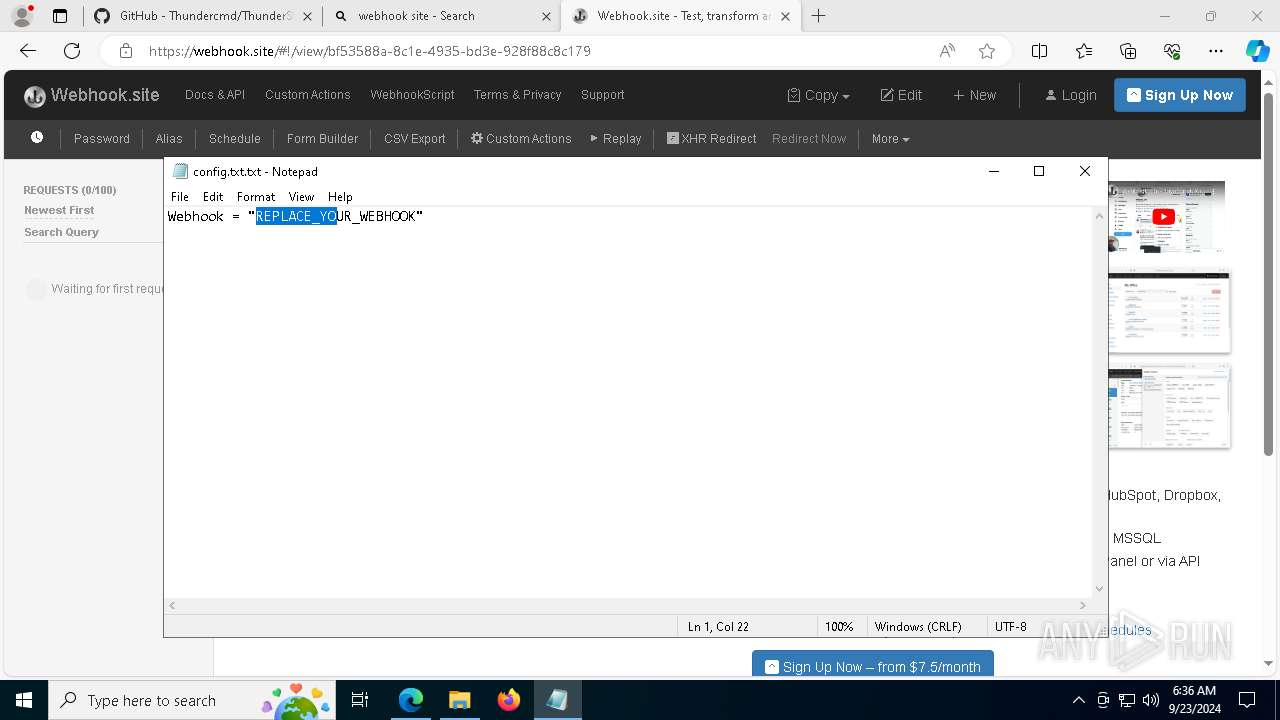
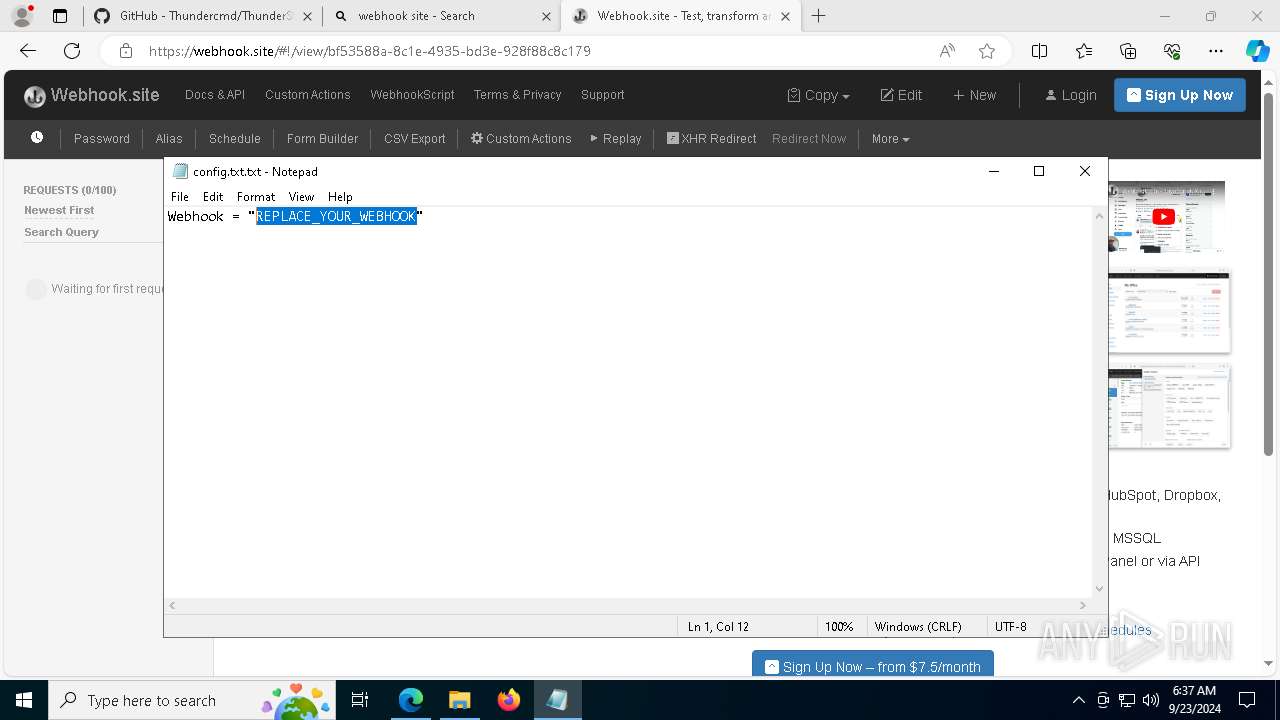
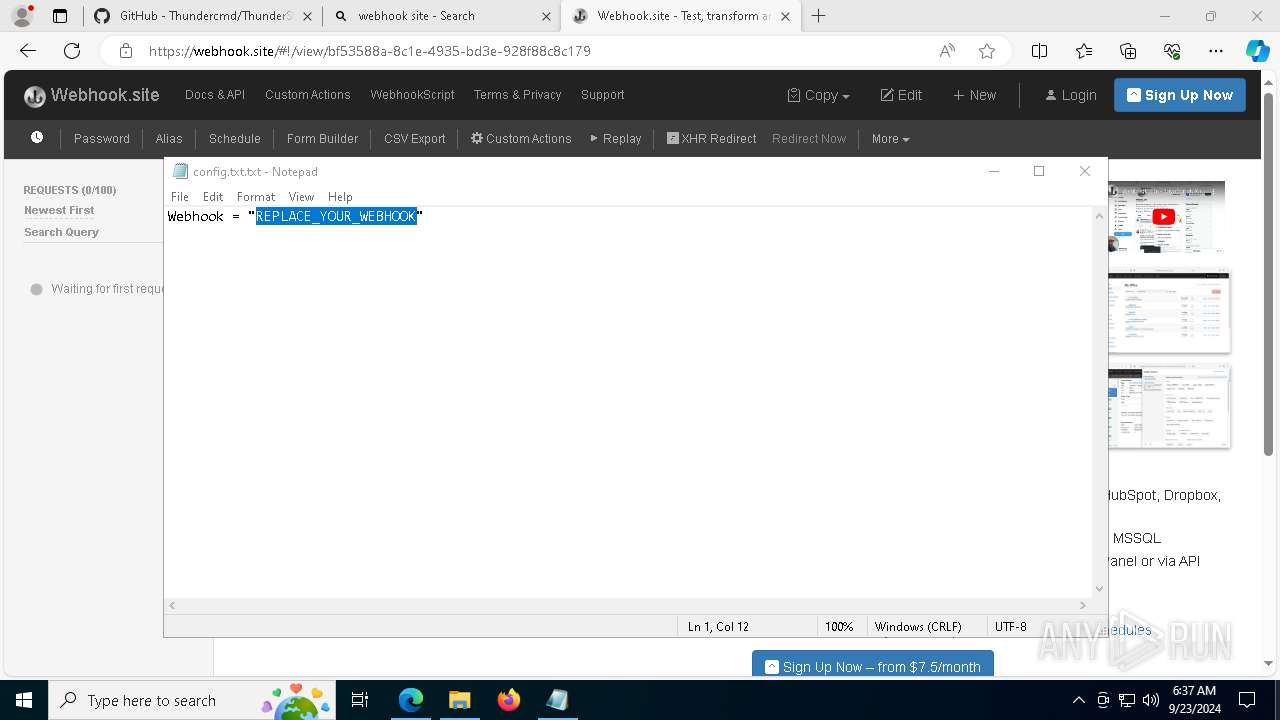
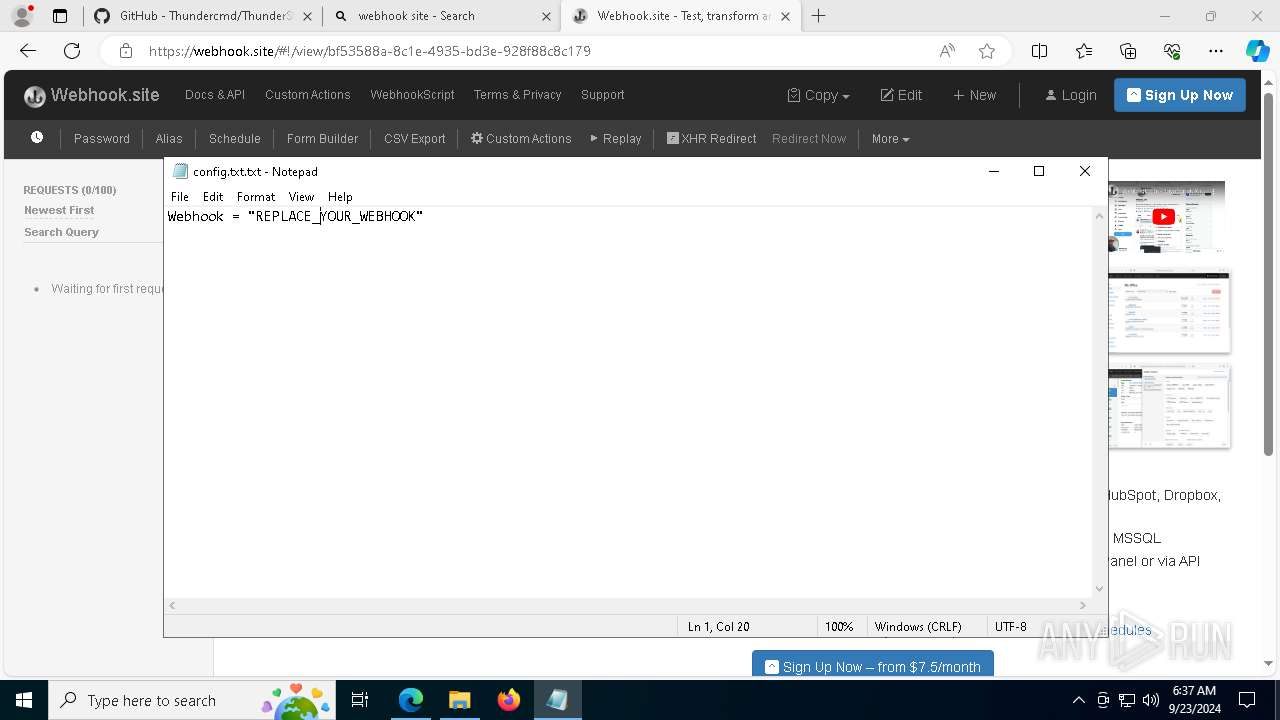
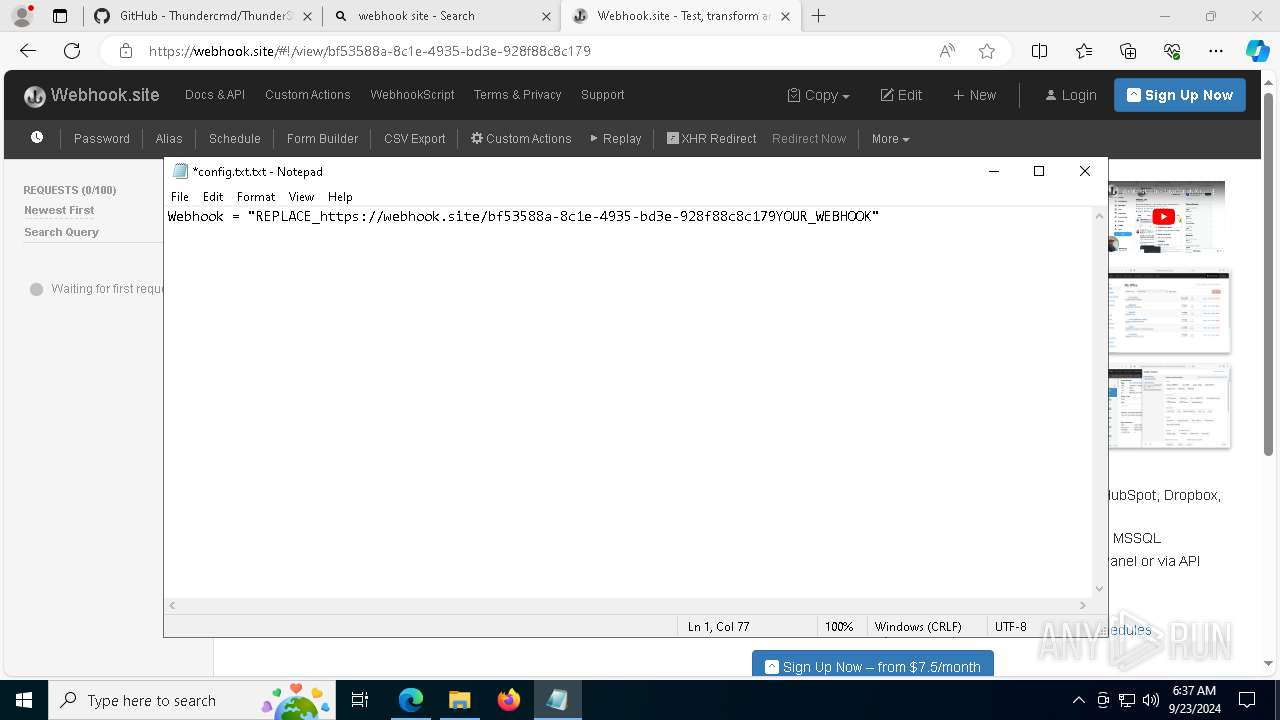
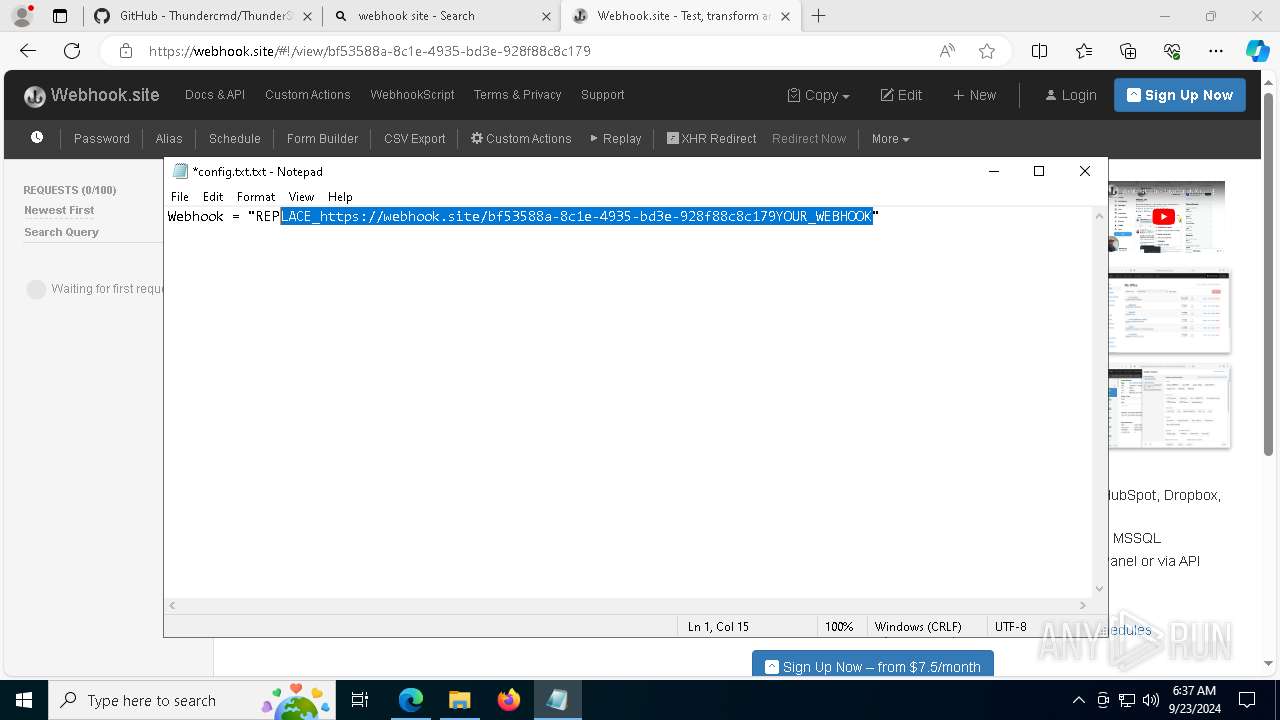
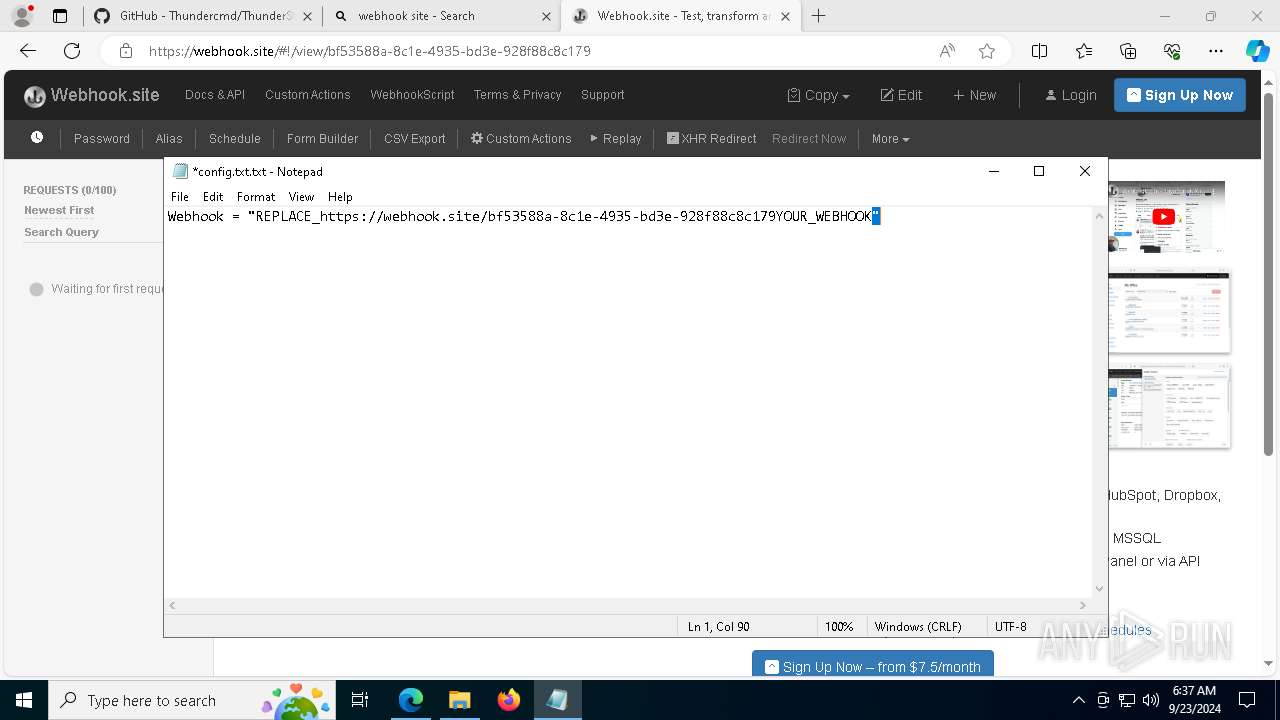
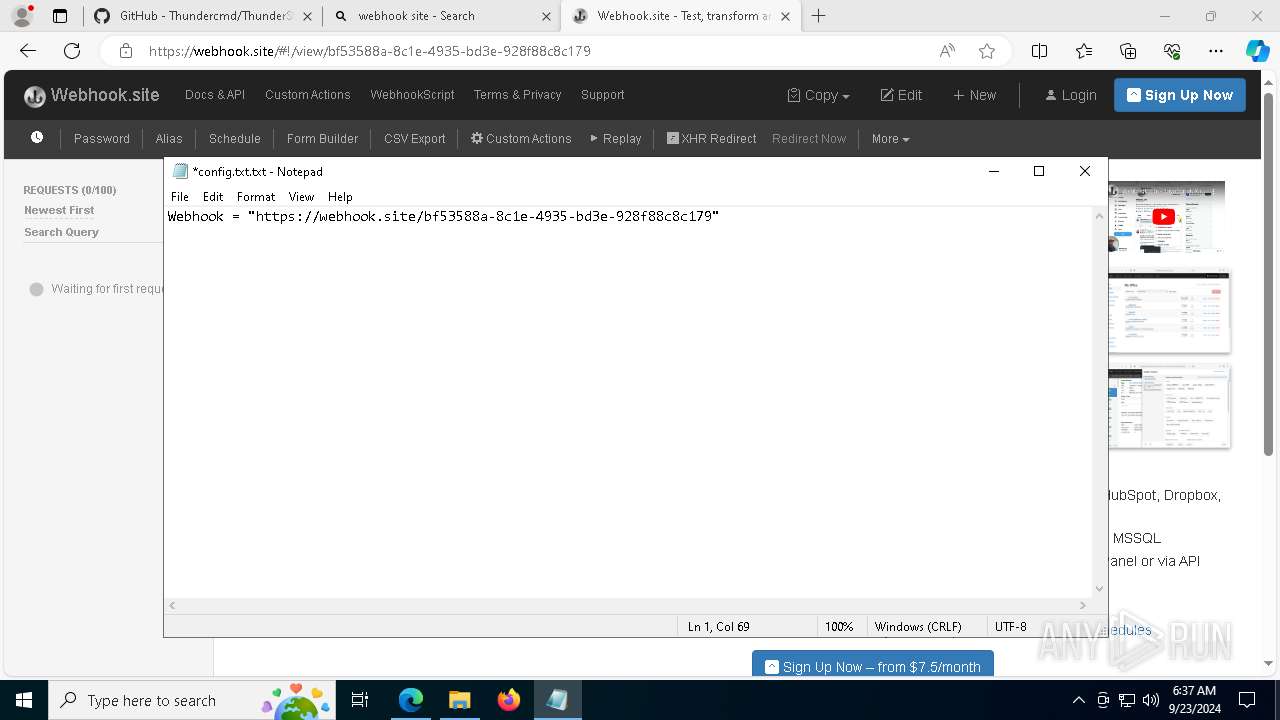
7068 | msedge.exe | Misc activity | ET INFO DNS Query for Webhook/HTTP Request Inspection Service (webhook .site) |
7068 | msedge.exe | Misc activity | ET INFO DNS Query for Webhook/HTTP Request Inspection Service (webhook .site) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |
7068 | msedge.exe | Misc activity | ET INFO Webhook/HTTP Request Inspection Service Domain (webhook .site in TLS SNI) |